Understanding NPTv6 on Palo Alto Networks Firewalls (PCNSE Focus)
NPTv6 (Network Prefix Translation for IPv6), formally defined in RFC 6296, offers a distinct approach to IPv6 address translation compared to traditional NAT or NAT64.
As IPv6 adoption grows, understanding NPTv6 becomes increasingly important for network engineers. For the PCNSE exam, familiarity with its concepts, configuration on PAN-OS, use cases, and key differences from other NAT mechanisms is essential.
What is NPTv6?
NPTv6 is an IPv6-to-IPv6 Network Prefix Translation mechanism. Its core goal is to translate one IPv6 prefix to another while leaving the Interface Identifier (host portion) of the address unchanged.
Key Characteristics:
- Stateless (Checksum-Neutral Algorithm): NPTv6 uses an algorithmic approach to translate prefixes. This algorithm is designed to be "checksum-neutral," meaning the IPv6 header checksum calculation remains valid after the prefix translation, reducing the need for the translating device (firewall) to recalculate it. While the firewall still tracks sessions for security policy enforcement, the NPTv6 translation itself doesn't require per-session state in the same way as traditional NAT.
- 1:1 Address Mapping: Every address within the original internal prefix maps uniquely to a corresponding address within the translated external prefix, and vice versa. There is no address overloading or pooling.
- Prefix Translation Only: Only the network bits (defined by the prefix length, e.g., /48 or /64) are modified. The remaining bits, representing the host's Interface Identifier, are copied directly.
- No Port Translation: NPTv6 operates purely at the IP layer and does *not* modify TCP/UDP port numbers.
- Transport Agnostic: Because it only modifies the IP prefix and maintains checksum validity, it generally doesn't interfere with transport layer protocols (TCP, UDP, ICMPv6) or higher-layer protocols that might embed address information (unlike some forms of traditional NAT).
Key Differences: NPTv6 vs. NAT44/NAT64
Understanding how NPTv6 differs from more familiar NAT mechanisms is crucial:
| Feature | NPTv6 | NAT44 (PAT/DIPP) | NAT64 (NAPT64) |
|---|---|---|---|
| Translation Type | IPv6 Prefix <-> IPv6 Prefix | IPv4 Address <-> IPv4 Address | IPv6 Address <-> IPv4 Address |
| Address Mapping | 1:1 (within prefixes) | Many-to-One or Many-to-Few | Many-to-One or Many-to-Few |
| Statefulness (NAT level) | Stateless (Algorithmic) | Stateful | Stateful |
| Translates Ports? | No | Yes (PAT/DIPP) | Yes (NAPT64) |
| Translates Interface ID? | No (Preserved) | N/A (IPv4 concept) | N/A (Translates entire address) |
| Checksum Recalculation | Generally Avoided (Checksum Neutral) | Required | Required |
| Primary Purpose | Prefix Independence, Multi-homing, Renumbering | IPv4 Address Conservation, Basic Security | IPv6 -> IPv4 Transition |
NPTv6 Use Cases
NPTv6 addresses specific challenges in IPv6 network management:
- ISP Multi-homing: An organization receives unique IPv6 prefixes from two different ISPs. They use a stable internal prefix (like a ULA or a primary GUA). NPTv6 rules translate the internal prefix to ISP A's prefix for traffic going out via ISP A, and to ISP B's prefix for traffic going out via ISP B. This allows seamless failover or load balancing without re-addressing internal hosts.
- Network Renumbering / ISP Change: If an organization changes its ISP and receives a new public IPv6 prefix, only the NPTv6 translation rule on the border firewall needs to be updated. All internal hosts can keep their existing stable addresses, drastically simplifying the renumbering process compared to re-addressing every host.
-
Provider Independence with ULAs:
Organizations can use Unique Local Addresses (ULAs,
fd00::/8) for internal addressing, which are not globally routable but provide stable internal numbering. NPTv6 can then translate the ULA prefix to a globally routable GUA prefix provided by the ISP for external communication. - Consistent Internal Addressing: Even if using GUAs internally, NPTv6 allows the use of a stable GUA prefix internally while translating to potentially different GUAs assigned at the edge for external access.
PAN-OS NPTv6 Configuration Details
NPTv6 is configured using NAT Policies on the Palo Alto Networks firewall.
-
Create NAT Rule:
Navigate to
Policies > NATand click "Add". -
General Tab:
- Name: Descriptive (e.g., `NPTv6_Internal_to_External`).
-
NAT Type: Select
nptv6. - Ensure Rule is Enabled.
-
Original Packet Tab:
Defines the traffic flow requiring prefix translation.
- Source Zone: Zone of the source prefix (e.g., `Zone_Internal_v6`).
- Destination Zone: Zone towards which translated traffic flows (e.g., `Zone_External_v6`).
-
Source Address: The
Internal IPv6 Prefix
(e.g.,
fd00:aaaa:bbbb::/48). Must be an Address Object of type 'IP Netmask'. - Destination Address: Typically `any` (::/0) unless translation is only needed for specific destinations.
- Service: Usually `any`.
-
Translated Packet Tab:
This tab defines the bidirectional mapping.
-
Source Address Translation:
-
Type:
Static IP(This seems counter-intuitive but is correct for NPTv6 prefix mapping). -
Translated Address: The
External IPv6 Prefix
(e.g.,
2001:db8:100::/48). Must be an Address Object of the same prefix length as the Internal Prefix. - Purpose: Translates the source prefix for outbound traffic.
-
Type:
-
Destination Address Translation:
-
Type:
Static IP. -
Translated Address: The
Internal IPv6 Prefix
(e.g.,
fd00:aaaa:bbbb::/48). Must be an Address Object of the same prefix length as the External Prefix. - Purpose: Translates the destination prefix for inbound (return) traffic.
-
Type:
- No Bi-directional Checkbox: Unlike NAT44 Static IP, there is no 'Bi-directional' checkbox for NPTv6. The bidirectional translation is implicitly handled by configuring both Source and Destination translation within this single rule.
-
Source Address Translation:
- Click OK and Commit.
NPTv6 Traffic Flow Example
Let's trace a packet with these prefixes defined in an NPTv6 rule:
-
Internal Prefix:
fd00:aaaa:bbbb::/48(Source Address in Original Packet, Destination Address in Translated Packet) -
External Prefix:
2001:db8:100::/48(Source Address in Translated Packet) -
Internal Client:
fd00:aaaa:bbbb::1234 -
External Server:
2001:db8:ffff::5678
Forward Path (Internal Client -> External Server)
-
Client sends packet:
-
Source IP:
fd00:aaaa:bbbb::1234 -
Destination IP:
2001:db8:ffff::5678
-
Source IP:
- Firewall receives packet.
- NAT rule lookup matches NPTv6 rule (Original Src Addr = fd00:aaaa:bbbb::/48).
- Security Policy lookup (based on original IPs).
-
NPTv6 Applied at Egress:
-
Source Prefix
fd00:aaaa:bbbb::/48translated to2001:db8:100::/48. -
Interface ID
::1234is preserved. -
Destination IP remains
2001:db8:ffff::5678(Not affected by source translation).
-
Source Prefix
-
Firewall sends packet:
-
Source IP:
2001:db8:100::1234 -
Destination IP:
2001:db8:ffff::5678
-
Source IP:
Return Path (External Server -> Internal Client)
-
Server sends reply packet:
-
Source IP:
2001:db8:ffff::5678 -
Destination IP:
2001:db8:100::1234(The address the server saw)
-
Source IP:
- Firewall receives packet.
-
NAT rule lookup: Packet destination
2001:db8:100::1234matches the External Prefix defined in the NPTv6 rule's "Source Address Translation" section (which implicitly defines the inbound mapping target). - Security Policy lookup (based on original IPs - firewall derives original destination fd00:aaaa:bbbb::1234 for policy lookup based on state/NPTv6 rule).
-
Reverse NPTv6 Applied at Egress (towards Internal):
-
Destination Prefix
2001:db8:100::/48translated back tofd00:aaaa:bbbb::/48(using the Destination Address Translation config in the rule). -
Interface ID
::1234is preserved. -
Source IP remains
2001:db8:ffff::5678(Not affected by destination translation).
-
Destination Prefix
-
Firewall sends packet:
-
Source IP:
2001:db8:ffff::5678 -
Destination IP:
fd00:aaaa:bbbb::1234
-
Source IP:
NPTv6 Interaction with Security Policy
Configuring security policy for NPTv6 traffic is generally straightforward because NPTv6 aims for transparency.
Key Principle: Security Policy rules match on the original (pre-translation) source and destination addresses and zones.
Unlike DNAT (including NAT64), where the destination *zone* used in the security policy is the post-NAT zone, NPTv6 primarily affects the source prefix on egress and the destination prefix on ingress *after* the main security policy check for the original flow has occurred (similar to SNAT logic).
Example Security Rule
Given:
- Internal Zone: `Zone_Internal_v6`
-
Internal Prefix (Source):
fd00:1111:2222::/48 - External Zone: `Zone_External_v6`
-
NPTv6 Rule: Translates
fd00:1111:2222::/48<->2001:db8:abc::/48
Security Rule to Allow Outbound:
- Name: `Allow_Internal_v6_Outbound`
- Source Zone: `Zone_Internal_v6`
-
Source Address:
fd00:1111:2222::/48(Original Internal Prefix) - Destination Zone: `Zone_External_v6`
- Destination Address: `any` (or specific external IPv6 destinations)
- Application/Service: `any` (or specific)
- Action: `Allow`
Security Rule to Allow Inbound (Example: Allowing External to reach specific internal host):
- Name: `Allow_External_To_InternalHost`
- Source Zone: `Zone_External_v6`
- Source Address: `any` (or specific external source)
- Destination Zone: `Zone_Internal_v6`
-
Destination Address:
fd00:1111:2222::100(The specific *internal* host address) - Application/Service: `any` (or specific)
- Action: `Allow`
2001:db8:abc::100
), the security policy allowing the inbound traffic must match the final, *internal* destination address (
fd00:1111:2222::100
) and the internal destination zone. The firewall determines this intended internal destination based on the NPTv6 rule and session state before the Security Policy lookup for the return/inbound initiation.
NPTv6 NDP Proxy Requirement
A critical requirement for NPTv6 to function correctly on Palo Alto Networks firewalls is the configuration of NDP Proxy (Neighbor Discovery Protocol Proxy).
Why is it needed?
-
NPTv6 translates prefixes. When an external host tries to reach an internal host using its translated (external prefix) address (e.g.,
2001:db8:100::1234), routers on the external network will send Neighbor Solicitation (NS) messages asking "Who has2001:db8:100::1234?". -
The internal host (
fd00:aaaa:bbbb::1234) will not respond to NS messages for its translated address. - NDP Proxy configured on the firewall's external interface allows the firewall to respond to these NS messages on behalf of the internal hosts, providing its own MAC address. This directs traffic destined for the translated external prefix addresses towards the firewall, enabling it to perform the NPTv6 translation back to the internal prefix for inbound traffic.
Configuration
-
Enable NDP Proxy under:
Network > Interfaces > [Your External IPv6 Interface] > IPv6 Tab > NDP Proxy. - Click "Enable NDP Proxy".
- You typically do *not* need to add specific target addresses unless required for very specific scenarios; enabling the proxy function itself is usually sufficient for NPTv6.
- Commit changes.
Diagram: Sequence - NPTv6 Traffic Flow
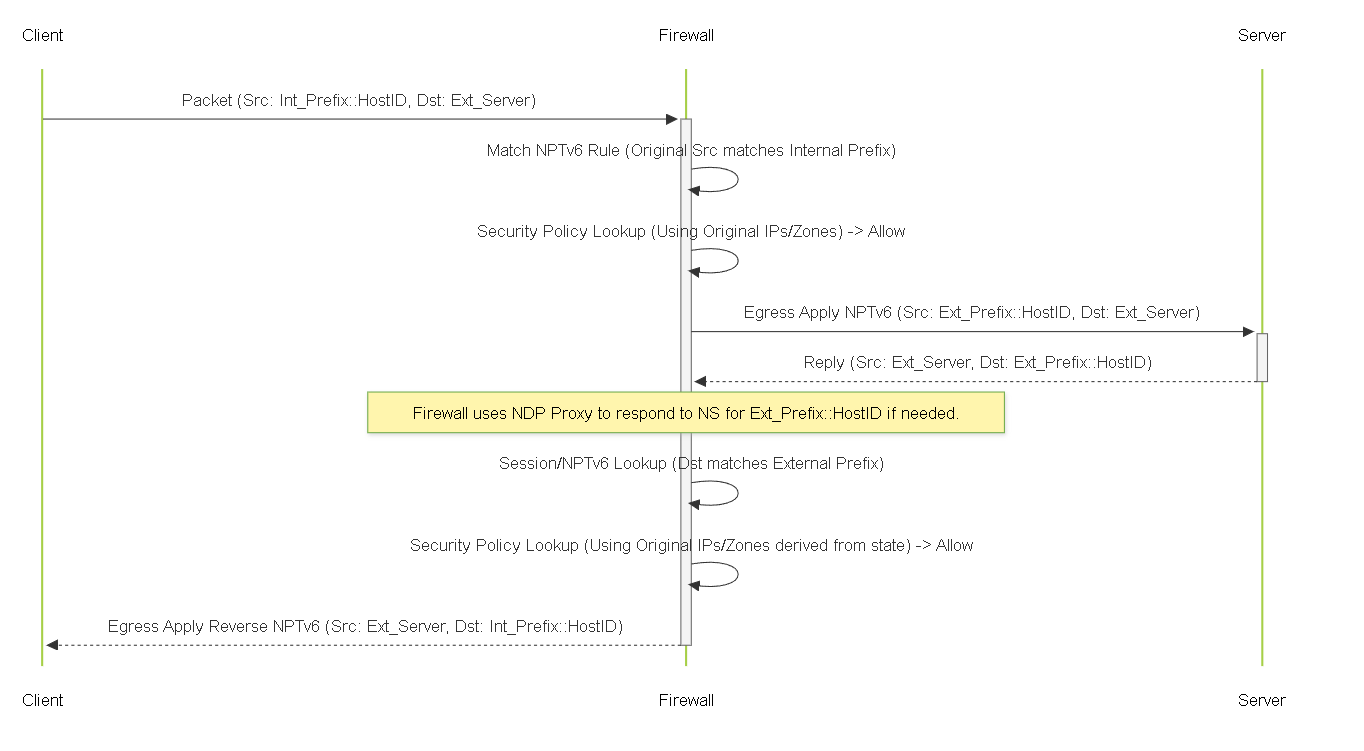
Sequence diagram illustrating NPTv6 translation for both outbound source and inbound destination prefixes.
Diagram: Graph - NPTv6 Prefix Mapping
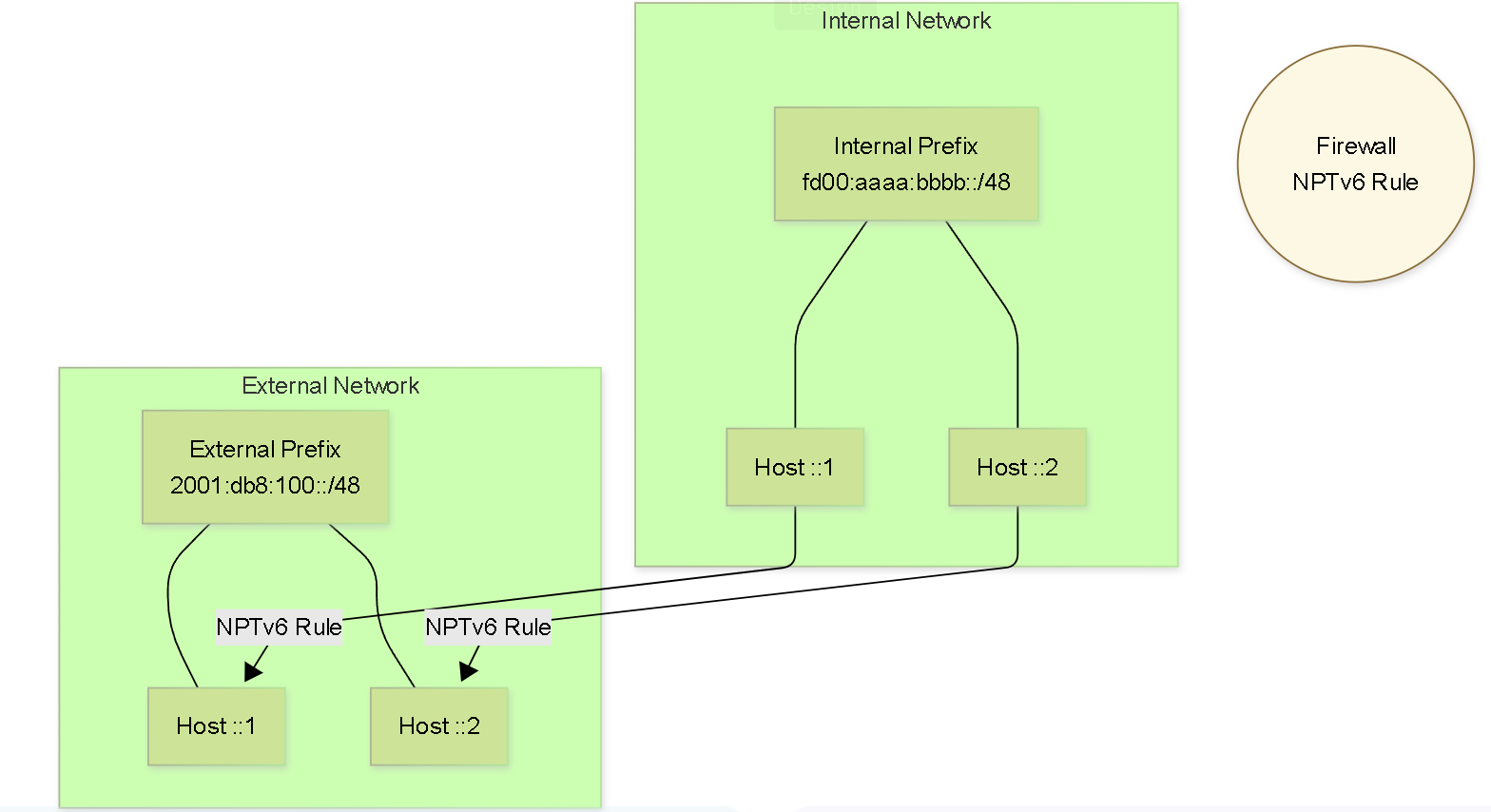
Graph illustrating the 1:1 mapping created by NPTv6. The prefix changes (fd00:aaaa:bbbb -> 2001:db8:100), but the Interface ID (::1, ::2) is preserved.
Diagram: State - NPTv6 Address Translation State
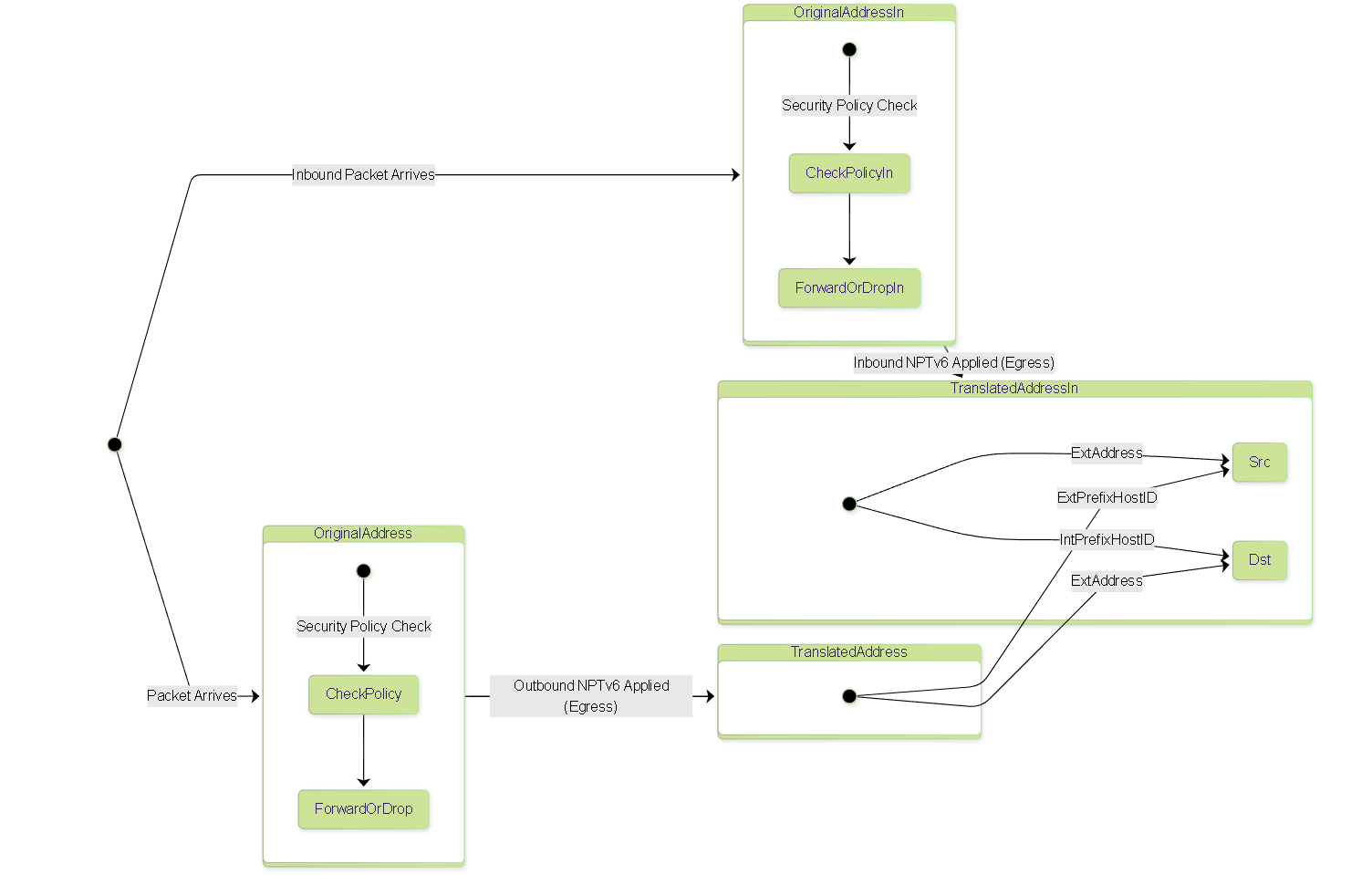
Simplified state diagram showing how NPTv6 affects source (outbound) and destination (inbound) addresses based on rule configuration.
PCNSE Exam Focus Summary (NPTv6)
Key NPTv6 concepts and configurations for the PCNSE exam:
- Purpose & Characteristics: Know NPTv6 is stateless (at NAT level), 1:1 IPv6 prefix translation, preserves host ID, checksum-neutral, no port translation.
- Use Cases: Recognize multi-homing, simplified renumbering, and ULA-to-GUA translation as primary drivers.
-
PAN-OS Configuration:
- NAT Policy Type: `nptv6`.
- Original Packet: Matches the source internal prefix .
- Translated Packet: Configures both Source Translation (to external prefix) and Destination Translation (back to internal prefix) using "Static IP" type.
- Prefix Lengths: Internal and External prefixes in the rule must have the same length.
- Security Policy Interaction: Security rules generally match on original (pre-NPTv6) addresses and zones.
- NDP Proxy: Understand that NDP Proxy is required on the external interface for inbound NPTv6 translation to work correctly.
- Comparison: Clearly distinguish NPTv6 from stateful NAT44 and stateful NAT64.
PCNSE Style Quiz: NPTv6
Test your understanding with these 20 questions focused on NPTv6: