Understanding Source NAT on Palo Alto Networks Firewalls
Network Address Translation (NAT) is a fundamental networking technology that allows private IP addresses within a local network to be mapped to one or more public IP addresses. This is essential for enabling multiple devices on a private network to share a single public IP address to access the internet, conserving IPv4 address space, and providing a layer of privacy by hiding internal network structure.
NAT comes in two primary forms: Source NAT (SNAT) and Destination NAT (DNAT).
- Source NAT (SNAT): Modifies the source IP address of a packet as it traverses the firewall, typically when traffic initiates from an internal network and goes to an external network (e.g., the internet).
- Destination NAT (DNAT): Modifies the destination IP address of a packet, typically when traffic initiates from an external network and is directed towards a server or resource on an internal network (e.g., port forwarding).
This article focuses specifically on **Source NAT** within the context of Palo Alto Networks firewalls, covering its purpose, different types, configuration examples, the concept of oversubscription, and key points relevant to PCNSE and PCNSA certifications.
What is Source NAT?
Source NAT is primarily used to translate private IP addresses used within a local network (like 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16) into public IP addresses when the traffic leaves the network, usually heading towards the internet. Without SNAT, devices with private IP addresses would not be able to communicate with resources on the public internet because private IP addresses are not routable globally.
The core function is simple: when an internal host sends a packet destined for the internet, the firewall intercepts it and changes the packet's source IP address from the internal private address to a public address owned by the firewall. The firewall keeps track of this translation in a NAT table so that return traffic destined for the public address can be correctly translated back to the original internal private address.
Key Use Cases and Scenarios for Source NAT
Scenario 1: Internet Access for an Internal LAN
This is the most common scenario. Multiple computers, phones, and other devices on a corporate LAN or home network use private IP addresses. To access websites, email, or cloud services on the internet, all these devices need to appear as if they are coming from one or a few public IP addresses assigned to the organization or ISP. SNAT makes this possible, conserving public IPv4 addresses.
Scenario 2: Mergers and Acquisitions (Overlapping IP Space)
When two companies merge, they often have overlapping private IP address ranges (e.g., both use 192.168.1.0/24). If devices from one network need to communicate with devices on the other, SNAT can be used to translate the source addresses from one network into a unique range before they traverse the interconnecting firewall. This avoids routing conflicts.
Scenario 3: Accessing Partner Networks or Cloud Services
Similar to M&A, you might need to communicate with resources in a partner network or certain cloud environments that require your traffic to come from a specific, non-overlapping IP range. SNAT can translate your internal addresses to an approved range.
Scenario 4: Enforcing a Consistent Outbound IP
Even if you have enough public IPs for all your internal hosts (rare with IPv4), you might want all outbound traffic to appear to originate from a single public IP address for easier logging, firewalling (on the destination side), or compliance reasons.
Source NAT Operation Steps
A packet originating from an internal host goes through a process on the firewall:
- Internal host (e.g., 192.168.1.10) sends a packet to an external server (e.g., 8.8.8.8). The packet has Source IP: 192.168.1.10, Source Port: 12345, Dest IP: 8.8.8.8, Dest Port: 53.
- The packet arrives at the firewall's internal interface.
- The firewall performs a route lookup based on the Destination IP (8.8.8.8). If an exit interface and next hop are found, it proceeds.
- The firewall looks for a matching NAT policy rule. If a rule matches the source zone (Internal), destination zone (External), source address (192.168.1.0/24), destination address (Any/8.8.8.8), service (DNS/53), and has a Source NAT translation type configured.
-
If a Source NAT rule matches, the firewall translates the Source IP (and potentially the Source Port) according to the rule.
- Original: Src=192.168.1.10:12345, Dst=8.8.8.8:53
- Translated: Src=Public_IP:New_Port, Dst=8.8.8.8:53
- The firewall adds an entry to its NAT session table mapping the original source (192.168.1.10:12345) to the translated source (Public_IP:New_Port).
- The packet with the translated Source IP/Port is forwarded out the appropriate external interface.
- The external server (8.8.8.8) receives the packet and responds, sending a packet back to Public_IP:New_Port, Dest IP: Public_IP, Dest Port: New_Port.
- The return packet arrives at the firewall's external interface.
- The firewall looks up the Destination IP (Public_IP) and Dest Port (New_Port) in its NAT session table. It finds the matching entry for the original 192.168.1.10:12345 session.
-
The firewall translates the Destination IP (Public_IP) back to the original Source IP (192.168.1.10) and the Dest Port (New_Port) back to the original Source Port (12345).
- Original Return: Src=8.8.8.8:53, Dst=Public_IP:New_Port
- Translated Return: Src=8.8.8.8:53, Dst=192.168.1.10:12345
- The packet with the translated Destination IP/Port is forwarded to the internal host (192.168.1.10).
This process is stateless for the initial packet lookup but stateful for the return traffic lookup via the NAT session table.
Source NAT Flavors (IPv4)
Palo Alto Networks firewalls offer several types of Source NAT translations for IPv4 traffic. The choice depends on the available public IP addresses and the specific requirements.
1. Dynamic IP and Port (DIPP)
This is the most common type of Source NAT, also known as Port Address Translation (PAT) or NAT Overload. It maps multiple private IP addresses and their ports to a single public IP address and unique source ports. This is how most home routers work.
- Original Packet: Source IP: Private_IP, Source Port: Original_Port
- Translated Packet: Source IP: Public_IP, Source Port: Translated_Port
- The firewall tracks the mapping (Private_IP:Original_Port <-> Public_IP:Translated_Port) in its NAT table.
- Requires only one public IP address to support many internal hosts.
- The number of possible simultaneous connections per internal host is limited by the number of available ports on the public IP address (typically 65535, minus reserved ports). However, the firewall manages this efficiently.
2. Dynamic IP (No Port Translation)
This method translates a private IP address to one of a pool of public IP addresses. The source port is NOT translated. This is less common for typical internet access from a large internal network because it requires a pool of public IP addresses at least equal in size to the maximum number of internal hosts needing concurrent connections using this rule.
- Original Packet: Source IP: Private_IP, Source Port: Original_Port
- Translated Packet: Source IP: Public_Pool_IP, Source Port: Original_Port
- A mapping is created between Private_IP and one of the Public_Pool_IPs for the duration of the session.
- Less efficient than DIPP for conserving public IP addresses.
- Could be useful in specific scenarios where the source port must be preserved end-to-end.
3. Dynamic Pool
Similar to Dynamic IP, this method translates a private IP address to one IP address from a configured pool of public IP addresses. However, like DIPP, it *also* performs port translation (PAT). This allows multiple internal hosts to map to multiple public IPs, further increasing the total number of available source ports and connections compared to DIPP using a single public IP.
- Original Packet: Source IP: Private_IP, Source Port: Original_Port
- Translated Packet: Source IP: Public_Pool_IP, Source Port: Translated_Port
- The firewall selects an available IP from the pool and an available port on that IP.
- Offers a balance between IP conservation (better than Dynamic IP) and scalability (more connections than DIPP with a single IP).
- Utilizes both multiple IPs and port translation.
4. Static IP
While primarily associated with Destination NAT (mapping a single public IP/port to a single private IP/port for incoming connections), Static IP can also be used for Source NAT in specific cases. It provides a one-to-one, persistent mapping between an internal private IP address and a public IP address.
- Original Packet: Source IP: Private_IP, Source Port: Original_Port
- Translated Packet: Source IP: Dedicated_Public_IP, Source Port: Original_Port
- This is a 1:1 mapping. The source port is NOT translated.
- Typically used when an internal server or host needs a consistent public IP address for outbound connections (e.g., accessing services that require whitelisting of source IPs).
- Requires one public IP address per internal host needing this type of static outbound NAT.
- Less common for general internet browsing traffic from a large internal network.
Source NAT Flavors (IPv6)
With the vast address space of IPv6, Source NAT is generally less common and less needed for basic internet access compared to IPv4. The intention of IPv6 is often end-to-end routability without translation. However, NAT is still sometimes used in specific IPv6 scenarios, primarily for transition mechanisms or policy reasons.
Palo Alto Networks firewalls support NAT64 and NAT66:
1. NAT64 (Translating IPv6 to IPv4)
This is a transition mechanism that allows IPv6-only clients to communicate with IPv4-only servers on the internet. It requires a NAT64 device (the firewall) to translate the IPv6 source address of the client to an IPv4 source address.
- Original Packet (Internal): Source IP: IPv6_Client_Address, Dest IP: IPv4_Server_Address (embedded or synthesized IPv6 representation)
- Translated Packet (External): Source IP: IPv4_Public_Address, Dest IP: IPv4_Server_Address
- The firewall maintains state to translate return IPv4 traffic back to the correct IPv6 client.
- Uses an algorithm to map IPv6 addresses to IPv4 addresses, often involving a well-known prefix (like 64:ff9b::/96).
In PAN-OS, NAT64 involves configuring a NAT rule where the source zone contains IPv6 clients and the destination zone contains IPv4 destinations, with a NAT type of NAT64.
2. NAT66 (Translating IPv6 to IPv6)
This is IPv6-to-IPv6 network address translation. It's less common than NAT44 (IPv4-to-IPv4 NAT) but can be used for reasons like:
- Hiding internal IPv6 network topology.
- Renumbering IPv6 networks without changing internal addressing.
- Connecting overlapping IPv6 networks (rare).
Similar to IPv4 NAT, NAT66 can involve translating to a single IPv6 address with port translation (Dynamic IP and Port) or to addresses from a pool (Dynamic Pool).
- Original Packet: Source IP: Private_IPv6_Address, Source Port: Original_Port
- Translated Packet: Source IP: Public_IPv6_Address (or Pool_IPv6_Address), Source Port: Translated_Port (for DIPP/Dynamic Pool) or Original_Port (for Static/Dynamic IP - less common in IPv6)
In PAN-OS, NAT66 rules are configured with IPv6 addresses and interfaces, specifying the appropriate translation type (typically Dynamic IP and Port or Dynamic Pool to a public IPv6 range).
NAT Oversubscription (PAT)
NAT Oversubscription, also known as Port Address Translation (PAT) or NAT Overload, is a crucial concept when using Dynamic IP and Port or Dynamic Pool Source NAT. It allows multiple internal hosts to share a single public IP address (or a limited pool of public IP addresses) for outbound connections.
Instead of assigning a unique public IP to each internal host (which is Static NAT), oversubscription works by translating both the source IP address AND the source port of outgoing packets.
When a host
192.168.1.10
initiates a connection from source port
10000
to an external server, and host
192.168.1.20
simultaneously initiates a connection from source port
10000
to the *same* external server, the firewall translates their source addresses to the same public IP but must use different source ports for the outgoing packets to maintain uniqueness.
- Host A: 192.168.1.10:10000 -> Translated to Public_IP: 20001
- Host B: 192.168.1.20:10000 -> Translated to Public_IP: 20002
- Host C: 192.168.1.30:15000 -> Translated to Public_IP: 20003
The firewall keeps track of these unique mappings in its NAT session table. When return traffic arrives destined for
Public_IP:20001
, the firewall knows it belongs to the session initiated by
192.168.1.10:10000
and translates the destination accordingly.
Benefits of Oversubscription:
- IPv4 Conservation: The primary benefit. Allows thousands of internal devices to share internet access using just one or a few public IPv4 addresses.
- Cost Reduction: Reduces the number of public IP addresses an organization needs to lease from an ISP.
- Simplified Network Management: Internal networks can use private, non-routable IP addresses without concern for global uniqueness.
Risk: Port Exhaustion
The main risk with oversubscription is port exhaustion . If a single public IP address is used for many internal hosts, the firewall must provide a unique source port for each outgoing connection. A TCP/UDP connection is uniquely identified by the 5-tuple: (Source IP, Source Port, Destination IP, Destination Port, Protocol). If the Source IP (Public_IP), Destination IP, Destination Port, and Protocol are the same for many simultaneous connections, the firewall must assign a unique Source Port for each. There are approximately 65,535 available ports per IP address per protocol (TCP/UDP). If too many internal hosts simultaneously initiate connections to the same external destination (especially common destinations like popular websites on port 80/443), the firewall might run out of available unique source ports on the public IP(s).
When port exhaustion occurs, new connections originating from the internal network and attempting to use that public IP and destination cannot be established until existing connections terminate and free up ports. This manifests as intermittent connectivity issues or failures for users.
Mitigating Port Exhaustion:
- Use a Dynamic Pool: Translate to a pool of public IP addresses instead of a single one. Each additional IP in the pool provides another 65535 potential source ports, exponentially increasing capacity.
- Increase the Port Range: Ensure the NAT policy allows using a wide range of source ports (e.g., 1024-65535 is common, but sometimes 1-65535 is used with careful consideration).
- Monitor NAT Session Usage: Palo Alto Networks firewalls provide visibility into NAT session usage, allowing administrators to monitor the number of sessions and detect potential exhaustion issues before they impact users significantly.
- Limit Sessions per Host: Configure session limits on the firewall to prevent a single misbehaving or malicious host from consuming excessive NAT resources.
show running resource-monitor
or dashboard widgets).
PAN-OS Source NAT Configuration
Source NAT is configured under Policies > NAT in the Palo Alto Networks firewall web interface or CLI. NAT rules are processed from top to bottom, and the first matching rule is applied.
Key Elements of a Source NAT Rule:
When creating a Source NAT rule, you define:
- General: Rule Name, Description, Enable/Disable.
-
Original Packet:
-
Source Zone:
The zone where the original traffic originates (e.g.,
internal-lan). -
Destination Zone:
The zone the original traffic is heading towards (e.g.,
untrust). -
Source Address:
The original source IP address(es) or network(s) (e.g.,
192.168.1.0/24or an address group). -
Destination Address:
The original destination IP address(es) or network(s) (e.g.,
anyfor internet access, or a specific group for partner access). -
Service:
The original port/protocol (e.g.,
any,service-http,application-default). Note: While service is part of the *match* criteria, the service port itself is usually NOT translated in SNAT except in specific ALG scenarios. What gets translated is the Source IP and potentially the Source Port. - Source Interface (Optional): The incoming interface.
- Destination Interface (Optional): The outgoing interface before NAT translation.
-
Source Zone:
The zone where the original traffic originates (e.g.,
-
Translated Packet:
- Translation Type: Specifies the type of NAT to perform (Source NAT, Destination NAT, or Bi-Directional NAT). For SNAT, choose "Dynamic IP and Port" or "Dynamic IP" or "Dynamic Pool".
-
Source Address Translation:
- Type: Dynamic IP and Port, Dynamic IP, Dynamic Pool, Static IP.
- Address Type: Interface Address, IP Address, Address Pool.
- Translated Address: The specific IP, Interface, or Address Pool to translate the source address(es) to.
- Destination Address Translation: (Leave as "None" for Source NAT)
Configuration Example: Dynamic IP and Port (DIPP)
This is the most common SNAT configuration, translating all internal traffic going to the internet to the firewall's external interface IP address, using port translation.
Scenario: Default Internet Access for Internal Network
Internal network (192.168.1.0/24) in zone
internal-lan
needs to access the internet (any destination in zone
untrust
). The external interface (e.g.,
ethernet1/1
) has a public IP address.
NAT Rule Configuration Steps (WebUI):
- Navigate to Policies > NAT .
- Click Add to create a new rule.
-
General Tab:
-
Name:
SNAT-Internal-to-Untrust-DIPP - Description: Allow internal hosts to access internet via DIPP.
- Enabled: Yes
-
Name:
-
Original Packet Tab:
-
Source Zone:
Select
internal-lan. -
Destination Zone:
Select
untrust. -
Source Address:
Add the internal network address object (e.g.,
192.168.1.0/24). -
Destination Address:
Select
any. -
Service:
Select
any. - Source Interface (Optional): Select the internal interface(s).
- Destination Interface (Optional): Select the external interface(s).
-
Source Zone:
Select
-
Translated Packet Tab:
- Translation Type: Select Source NAT .
-
Source Address Translation:
- Type: Select Dynamic IP and Port .
- Address Type: Select Interface Address .
-
Interface:
Select the external interface connected to the internet (e.g.,
ethernet1/1). -
IP Address:
Select the IP address of that interface (e.g.,
ipfor the primary IP, oripv6-ipfor the primary IPv6 address).
- Destination Address Translation: Leave as None .
- Click OK and Commit the changes.
CLI Example (Equivalent):
configure
set policy nat SNAT-Internal-to-Untrust-DIPP from internal-lan to untrust
set policy nat SNAT-Internal-to-Untrust-DIPP source 192.168.1.0/24
set policy nat SNAT-Internal-to-Untrust-DIPP destination any
set policy nat SNAT-Internal-to-Untrust-DIPP service any
set policy nat SNAT-Internal-to-Untrust-DIPP translated-address-type dynamic-ip-and-port
set policy nat SNAT-Internal-to-Untrust-DIPP dynamic-ip-and-port interface ethernet1/1 ip ip
commit
Configuration Example: Dynamic Pool
This configuration uses a pool of public IP addresses for Source NAT, typically to increase the number of available ports for oversubscription and mitigate port exhaustion.
Scenario: Internet Access with Multiple Public IPs
Internal network (192.168.2.0/24) in zone
internal-server-vlan
needs internet access, and you have a block of public IP addresses (e.g., 203.0.113.100 - 203.0.113.109) available for NAT.
NAT Rule Configuration Steps (WebUI):
-
First, define the Address Pool object:
Objects > Addresses > Add
.
-
Name:
SNAT-Public-Pool-Servers - Type: Range
-
IP Netmask:
203.0.113.100-203.0.113.109 - Click OK .
-
Name:
- Navigate to Policies > NAT .
- Click Add to create a new rule.
-
General Tab:
-
Name:
SNAT-Servers-to-Untrust-Pool - Description: Allow servers to access internet via public IP pool.
- Enabled: Yes
-
Name:
-
Original Packet Tab:
-
Source Zone:
Select
internal-server-vlan. -
Destination Zone:
Select
untrust. -
Source Address:
Add the server network address object (e.g.,
192.168.2.0/24). -
Destination Address:
Select
any. -
Service:
Select
any.
-
Source Zone:
Select
-
Translated Packet Tab:
- Translation Type: Select Source NAT .
-
Source Address Translation:
- Type: Select Dynamic Pool .
- Address Type: Select Address Pool .
-
Translated Address:
Select the address pool object created earlier (e.g.,
SNAT-Public-Pool-Servers).
- Destination Address Translation: Leave as None .
- Click OK and Commit the changes.
CLI Example (Equivalent):
configure
set address SNAT-Public-Pool-Servers ip-range 203.0.113.100-203.0.113.109
set policy nat SNAT-Servers-to-Untrust-Pool from internal-server-vlan to untrust
set policy nat SNAT-Servers-to-Untrust-Pool source 192.168.2.0/24
set policy nat SNAT-Servers-to-Untrust-Pool destination any
set policy nat SNAT-Servers-to-Untrust-Pool service any
set policy nat SNAT-Servers-to-Untrust-Pool translated-address-type dynamic-pool
set policy nat SNAT-Servers-to-Untrust-Pool dynamic-pool SNAT-Public-Pool-Servers
commit
Configuration Example: Static IP (for Reference)
While Static IP NAT is less common for general Source NAT scenarios and more associated with Destination NAT, understanding its application as a source translation type is useful. It provides a persistent 1:1 mapping.
Scenario: Internal Server Requires Consistent Outbound IP
An internal server (192.168.2.50) needs to connect to external services that require the server's source IP to always be a specific public IP address (e.g., 203.0.113.110) for access control lists or licensing.
NAT Rule Configuration Steps (WebUI):
-
First, define the public IP Address object:
Objects > Addresses > Add
.
-
Name:
Server-Outbound-Public-IP - Type: IP-Netmask
-
IP Netmask:
203.0.113.110/32 - Click OK .
-
Name:
- Navigate to Policies > NAT .
- Click Add to create a new rule.
-
General Tab:
-
Name:
SNAT-Server-Static-Outbound - Description: Static SNAT for specific server outbound.
- Enabled: Yes
-
Name:
-
Original Packet Tab:
-
Source Zone:
Select
internal-server-vlan. -
Destination Zone:
Select
untrustor a specific external zone. -
Source Address:
Add the internal server address object (e.g.,
192.168.2.50/32). -
Destination Address:
Select
anyor specific required destinations. -
Service:
Select
anyor specific required services.
-
Source Zone:
Select
-
Translated Packet Tab:
- Translation Type: Select Source NAT .
-
Source Address Translation:
- Type: Select Static IP .
-
Translated Address:
Select the public IP address object (e.g.,
Server-Outbound-Public-IP).
- Destination Address Translation: Leave as None .
- Click OK and Commit the changes.
Note: Because this is a 1:1 static translation, the source port is not translated. This NAT type consumes one public IP address per internal host using the rule.
NAT Oversubscription Configuration Details
When using Dynamic IP and Port or Dynamic Pool, oversubscription is inherent. There aren't specific checkboxes for "oversubscription"; it's the nature of the translation type.
However, you can configure aspects related to oversubscription:
Configuring Port Translation (Implicit with DIPP/Dynamic Pool)
For Dynamic IP and Port and Dynamic Pool NAT rules, the firewall automatically translates the source port to ensure sessions are unique on the translated IP(s). By default, PAN-OS uses a wide range of ports (often 1024-65535) but can utilize the full range if necessary. You can specify the Translated Port Range in the NAT rule if required, but this is usually left as default.
In the "Translated Packet" tab for Dynamic IP and Port or Dynamic Pool:
- Under "Source Address Translation", when "Type" is Dynamic IP and Port or Dynamic Pool, the option for "Translated Port" appears.
- By default, this is set to "Port Range" 1024-65535.
- You can change this if needed, but typically the default is sufficient unless there's a specific application requirement.
Monitoring NAT Sessions and Port Usage
Monitoring is key to managing oversubscription and avoiding port exhaustion. Palo Alto Networks provides tools for this:
- WebUI Dashboard Widgets: Add widgets for "NAT Pool Utilization" or "Session Info" filtered by NAT rules.
-
CLI Commands:
-
show running resource-monitor ingress-nat detail: Shows NAT pool utilization for each configured pool/interface. -
show session all filter policy-type navigate nat-rule <rule-name>: Shows active sessions hitting a specific NAT rule. -
show session info: Provides system-wide session information, including NAT usage. -
clear session all nat-rule <rule-name>: Can be used to clear sessions associated with a NAT rule (use with caution!).
-
# Example of checking NAT pool utilization for a rule translating to an interface IP
show running resource-monitor ingress-nat detail rule SNAT-Internal-to-Untrust-DIPP
# Example output snippet might look like:
# Ingress NAT Rule: SNAT-Internal-to-Untrust-DIPP
# IP address: 203.0.113.1 (ethernet1/1 primary)
# Ports (total, in-use, available): 65535, 15000, 50535
# Utilization (%): 22.89
# Sessions: 15000
Mermaid Diagrams for Source NAT Flow
NAT Policy Lookup Flowchart
This flowchart illustrates the general decision process a Palo Alto Networks firewall uses for NAT policy lookup in the packet flow.
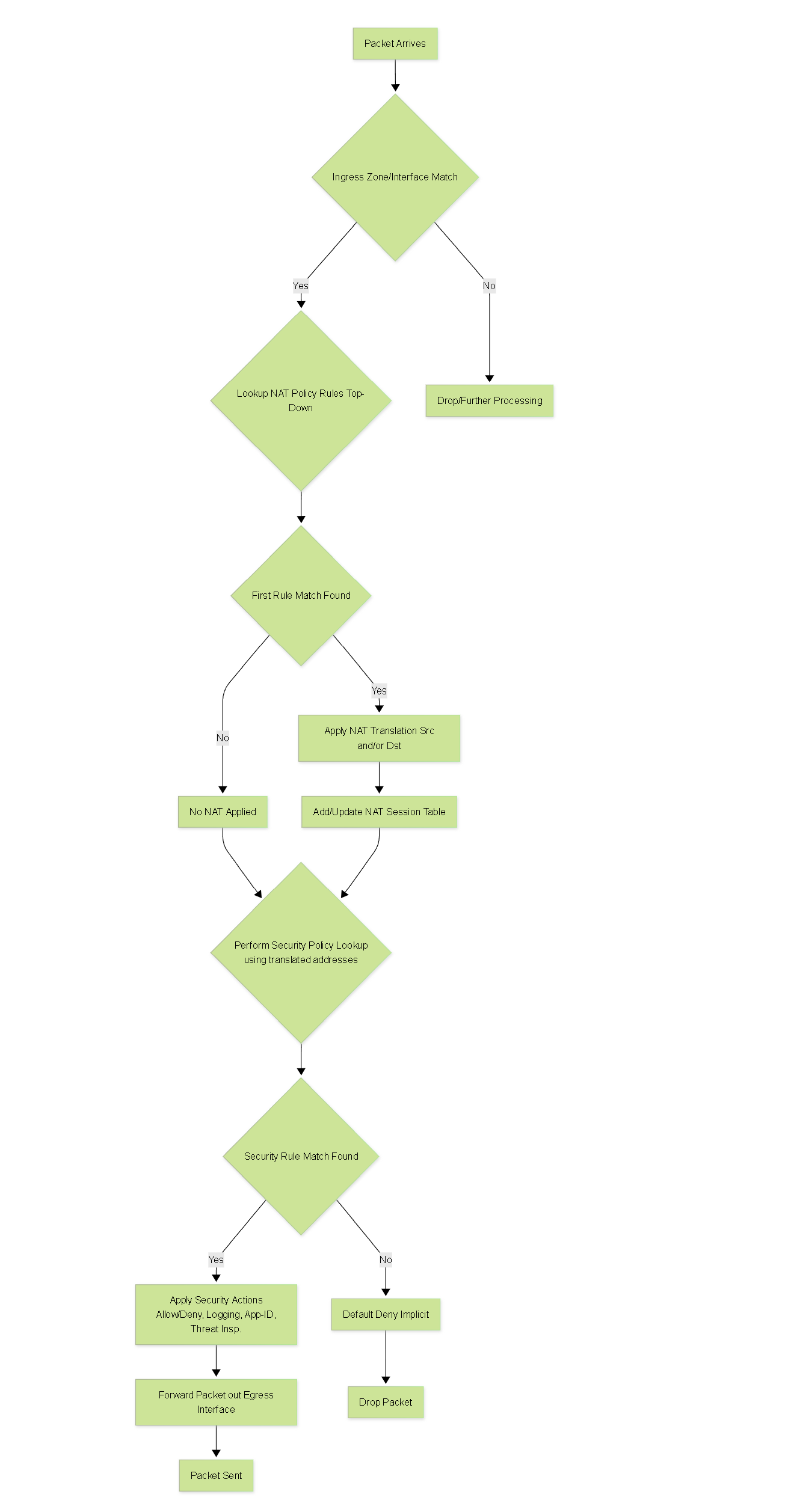
Simplified NAT Policy Lookup Flow on Palo Alto Networks Firewalls. NAT occurs early in the packet processing sequence.
Source NAT Sequence Diagram (Dynamic IP and Port)
This diagram shows the sequence of events for an internal host accessing an external server via Source NAT with port translation.
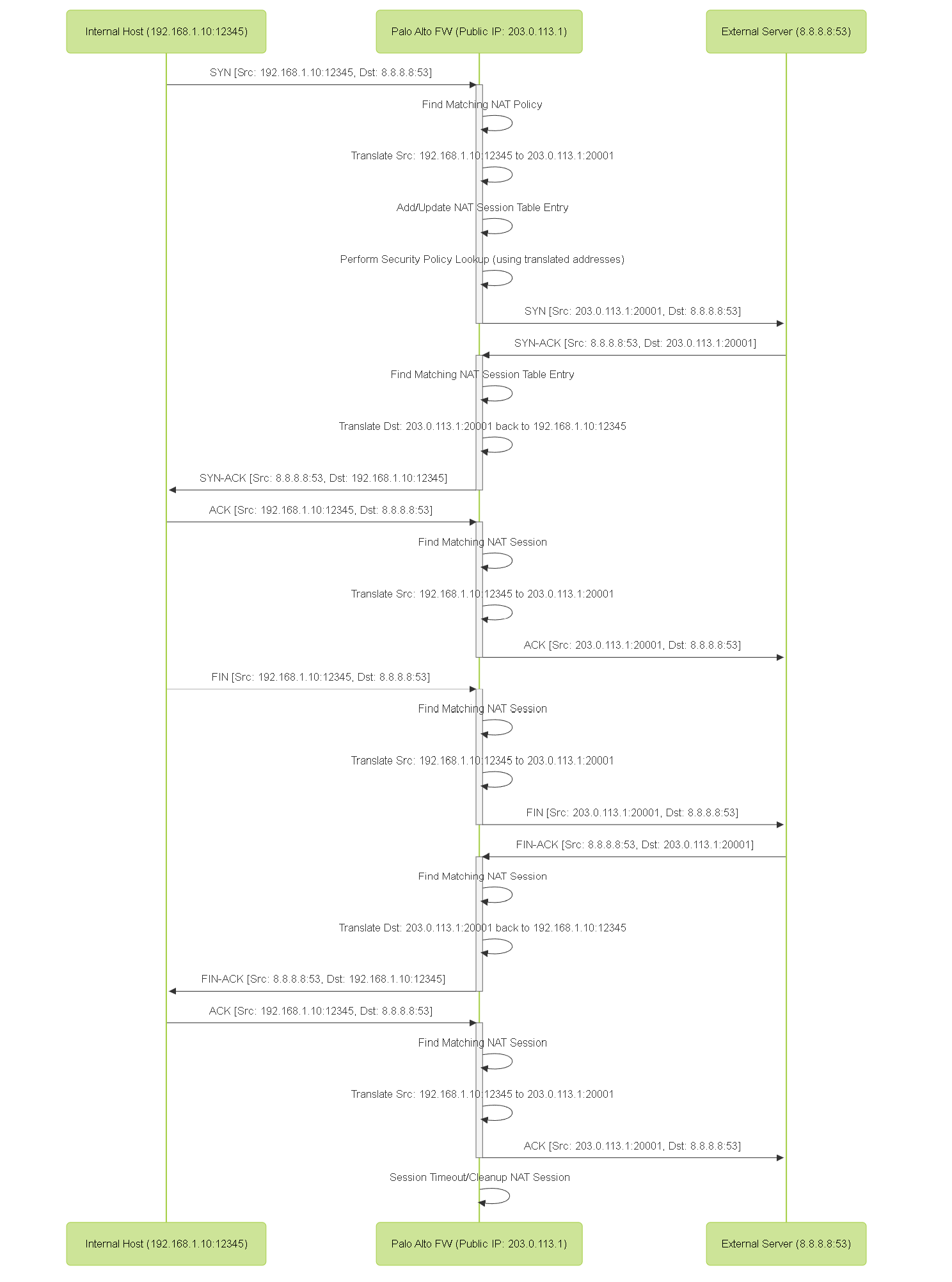
Sequence diagram showing the flow of a TCP connection with Dynamic IP and Port Source NAT.
Note: While State Diagrams and general Graphs were mentioned, they are less common or intuitive for illustrating the fundamental NAT translation process compared to Flowcharts and Sequence Diagrams. The core "state" is the NAT session table entry, which is implicitly covered in the sequence diagram. A network graph could show devices, but not the NAT translation logic itself.
Source NAT and PCNSE/PCNSA Exam Points
Source NAT is a foundational topic for both the PCNSA and PCNSE exams. Here are some key concepts and configurations you should be familiar with:
- Order of Operations: Understand that NAT policy is evaluated *before* Security policy. Traffic must match a NAT rule and be translated (if configured) before the Security policy rules are applied using the *translated* source/destination addresses and zones. This is critical.
- NAT Policy Matching: Know the criteria used to match a NAT rule: Source Zone, Destination Zone, Source Address, Destination Address, Service, (Optional) Source Interface, (Optional) Destination Interface.
- Source NAT Types: Be able to distinguish between Dynamic IP and Port (DIPP/PAT), Dynamic IP, Dynamic Pool, and Static IP translations for Source NAT. Understand when to use each and their implications (e.g., address conservation, port exhaustion).
- Interface vs. IP Address Translation: Know how to configure Dynamic IP and Port/Dynamic Pool using either the interface's IP address or a specific IP address/pool object.
- NAT Oversubscription (PAT) and Port Exhaustion: Understand the concept of oversubscription, how it works with DIPP and Dynamic Pool, the risk of port exhaustion, and how using a Dynamic Pool mitigates this risk.
-
Monitoring NAT Sessions:
Be familiar with CLI commands or WebUI features to monitor NAT session usage, especially for identifying potential port exhaustion issues (e.g.,
show running resource-monitor ingress-nat detail). - Bi-Directional NAT: Understand that Bi-Directional NAT rules create both a Source NAT and a Destination NAT entry simultaneously, often used for mapping internal servers to public IPs. While this section focuses on SNAT, recognize this combined type.
- NAT Rule Placement: Static NAT rules are often placed higher than broader Dynamic rules to ensure the static translation takes precedence for specific traffic.
- IPv6 NAT (NAT64, NAT66): While less emphasis than IPv4 NAT, understand the basics of NAT64 as an IPv6-to-IPv4 transition mechanism and the concept of NAT66.
Source NAT Quiz
Test your knowledge of Source NAT concepts on Palo Alto Networks firewalls with these questions.