Understanding U-Turn NAT on Palo Alto Networks Firewalls
Welcome to this comprehensive guide on U-Turn NAT, also known as Hairpin NAT or Internal NAT. This is a crucial concept for managing internal network traffic that needs to traverse the firewall, particularly when internal clients try to access internal servers using their public IP address or external DNS name.
This article will provide a deep dive into U-Turn NAT, explaining why it's necessary, detailing common scenarios, illustrating the packet flow, guiding you through the configuration on Palo Alto Networks firewalls, highlighting key points for the PCNSE/PCNSA exams, and offering troubleshooting tips.
What is U-Turn NAT?
U-Turn NAT, often referred to as Hairpin NAT, is a NAT technique used when a client on an internal network attempts to access a server (also on an internal network or DMZ) using that server's public IP address or hostname. Without U-Turn NAT, this traffic pattern would typically fail because the firewall (or router) doesn't know how to route the response packet back to the client.
Consider a scenario:
- An internal client (e.g., on the LAN zone) has a private IP (192.168.1.10).
- An internal server (e.g., also on the LAN zone) has a private IP (192.168.1.50) but is accessible from the internet via a public IP (e.g., 203.0.113.10) using Destination NAT (DNAT).
- The internal client tries to connect to the server using its public IP (203.0.113.10).
Without U-Turn NAT, the firewall would receive the packet from the client (Source: 192.168.1.10, Destination: 203.0.113.10). The firewall would apply the standard Internet-facing DNAT rule, changing the destination to the server's private IP (192.168.1.50). The server receives the packet (Source: 192.168.1.10, Destination: 192.168.1.50). When the server replies, it sends a packet directly back to the client's private IP (Source: 192.168.1.50, Destination: 192.168.1.10) because they are on the same network. This response packet does NOT go back through the firewall, so the firewall's NAT session is unaware of the response, and the client never receives it, causing the connection to fail.
U-Turn NAT solves this by applying Source NAT (SNAT) to the client's private IP as the traffic traverses the firewall towards the server. This forces the server's reply packet to return to the firewall's SNAT address, allowing the firewall to track the session and send the response back to the client's original private IP.
Why is U-Turn NAT Needed? Common Scenarios
U-Turn NAT is essential in environments where internal users access resources that are published externally via public IP addresses or external DNS names. Here are the most common scenarios:
Scenario 1 Overview: Internal Clients Accessing Internal Servers by Public IP/DNS
This is the classic U-Turn scenario. You have internal servers (e.g., web servers, application servers) that users both inside and outside the organization need to access. External users access them via a public IP and standard DNAT. Internal users are accustomed to using the same public IP or external FQDN (which resolves to the public IP via public DNS) as the external users.
Example: Internal Web Server
- Internal Client IP: 192.168.10.10
- Internal Web Server Private IP: 192.168.10.50
- Web Server Public IP: 203.0.113.10 (DNAT'd on Firewall to 192.168.10.50)
- External DNS Name: www.mycompany.com (resolves to 203.0.113.10 publicly)
Internal users type
www.mycompany.com
into their browser. Their internal DNS might return the public IP (common setup for simplicity or when internal DNS isn't aware of internal IPs for external names). Their request goes to the firewall with Destination IP 203.0.113.10.
Without U-Turn NAT, the firewall correctly translates the destination but the server replies directly back to the client's private IP, bypassing the firewall on the return path, breaking the session.
Scenario 2 Overview: Services on DMZ Accessed by Internal Clients Using Public IP/DNS
Similar to Scenario 1, but the server resides in a different zone (DMZ) than the client (LAN). While routing might be different, the core problem remains: the client uses the public IP, the firewall DNATs it, but the server might try to route the reply directly back to the client if they are on the same Layer 3 segment behind the firewall, or if the firewall's route back is simpler than traversing back through the NAT layer correctly without SNAT.
Example: DMZ Application Server
- Internal Client IP: 192.168.10.10 (LAN Zone)
- DMZ App Server Private IP: 10.10.10.50 (DMZ Zone)
- App Server Public IP: 203.0.113.20 (DNAT'd on Firewall to 10.10.10.50)
- External DNS Name: app.mycompany.com (resolves to 203.0.113.20 publicly)
Internal clients try to access
app.mycompany.com
(resolving to 203.0.113.20). The firewall DNATs 203.0.113.20 to 10.10.10.50. The client traffic goes from LAN to DMZ zone.
U-Turn NAT (applying SNAT) ensures the server's reply comes back to the firewall's SNAT address, which allows the firewall to reverse both the SNAT and DNAT translations correctly and route the packet back to the original client on the LAN zone, maintaining session state.
Scenario 1: Internal Clients to Internal Servers (Same Zone)
Let's detail the classic U-Turn scenario where the client and server are in the same zone (e.g., both on the LAN zone) but in different IP subnets, and the client uses the server's public IP.

Setup:
- Client: IP 192.168.1.10, Zone: Trust, Interface: ethernet1/2
- Server: IP 192.168.2.50, Zone: Trust, Interface: ethernet1/2
- Server Public IP: 203.0.113.10
- Firewall Interface (Trust Zone): ethernet1/2 (Gateway for 192.168.1.0/24 and 192.168.2.0/24)
- Firewall Interface (Untrust Zone): ethernet1/1
The Problem (Without U-Turn NAT):
- Client 192.168.1.10 sends packet: SRC: 192.168.1.10, DST: 203.0.113.10
- Packet arrives at firewall (ingress interface: ethernet1/2, ingress zone: Trust).
- Firewall performs route lookup for 203.0.113.10. It has a DNAT rule for 203.0.113.10 translating to 192.168.2.50.
- Packet after DNAT: SRC: 192.168.1.10, DST: 192.168.2.50 .
- Firewall performs security policy lookup (Trust zone to Trust zone). If allowed, it forwards the packet out the ingress interface (ethernet1/2) towards the 192.168.2.0/24 network.
- Server 192.168.2.50 receives packet: SRC: 192.168.1.10, DST: 192.168.2.50 .
- Server 192.168.2.50 replies: SRC: 192.168.2.50, DST: 192.168.1.10 .
- Since 192.168.1.10 and 192.168.2.50 are within networks whose gateway is the firewall's ethernet1/2 interface, the server sends the reply packet directly to that interface.
- The reply packet arrives at the firewall (ingress interface: ethernet1/2, ingress zone: Trust). However, this is the reverse of the original packet flow. The firewall expects the reply for the session initiated by 192.168.1.10 -> 203.0.113.10 to come from 192.168.2.50 (the translated destination) and ideally arrive back through the NAT mechanism. Since the server replies directly to the original source IP, bypassing the NAT state on the return, the firewall doesn't recognize this as a valid reply to the existing session, and the packet is dropped.
Scenario 2: Internal Clients to DMZ Servers
This scenario involves a client and server in different zones behind the firewall, but the client still uses the server's public IP/DNS.
Setup:
- Client: IP 192.168.1.10, Zone: Trust, Interface: ethernet1/2
- Server: IP 10.10.10.50, Zone: DMZ, Interface: ethernet1/3
- Server Public IP: 203.0.113.20
- Firewall Interface (Trust Zone): ethernet1/2 (Gateway for 192.168.1.0/24)
- Firewall Interface (DMZ Zone): ethernet1/3 (Gateway for 10.10.10.0/24)
- Firewall Interface (Untrust Zone): ethernet1/1
The Problem (Without U-Turn NAT):
- Client 192.168.1.10 sends packet: SRC: 192.168.1.10, DST: 203.0.113.20 .
- Packet arrives at firewall (ingress interface: ethernet1/2, ingress zone: Trust).
- Firewall performs route lookup for 203.0.113.20. It has a DNAT rule for 203.0.113.20 translating to 10.10.10.50.
- Packet after DNAT: SRC: 192.168.1.10, DST: 10.10.10.50 .
- Firewall performs security policy lookup (Trust zone to DMZ zone). If allowed, it forwards the packet out the ethernet1/3 interface towards the DMZ.
- Server 10.10.10.50 receives packet: SRC: 192.168.1.10, DST: 10.10.10.50 .
- Server 10.10.10.50 replies: SRC: 10.10.10.50, DST: 192.168.1.10 .
- The server 10.10.10.50 has a route for 192.168.1.0/24 pointing to its default gateway (firewall's ethernet1/3 interface). So, the reply packet goes back to the firewall.
- The reply packet arrives at the firewall (ingress interface: ethernet1/3, ingress zone: DMZ). The firewall looks up the session table for a session initiated by 192.168.1.10 -> 203.0.113.20. The reply packet (10.10.10.50 -> 192.168.1.10) does not match the expected reverse flow for the session (which would involve 192.168.2.50 replying *back* to the firewall's SNAT address, if SNAT were applied). Even though the packet returns to the firewall, without U-Turn NAT (specifically SNAT), the firewall cannot correlate this reply with the outgoing session initiated by 192.168.1.10 and drops it.
While the server reply returns to the firewall in this inter-zone scenario, the fundamental issue is the lack of Source NAT on the initial packet from the client. This prevents the server from sending the reply back to a translated IP on the firewall, which is necessary for the firewall to reverse the NAT process and return the packet to the original client.
How U-Turn NAT Works (Packet Flow)
U-Turn NAT on a Palo Alto Networks firewall involves applying both Destination NAT (DNAT) and Source NAT (SNAT) simultaneously to the traffic flow.
Let's revisit Scenario 1 (Internal Client -> Internal Server, Same Zone) and trace the packet flow with U-Turn NAT configured.
Setup:
- Client: IP 192.168.1.10, Zone: Trust
- Server: IP 192.168.2.50, Zone: Trust
- Server Public IP: 203.0.113.10
-
U-Turn NAT Rule:
- Original Packet:
- Source Zone: Trust
- Destination Zone: Trust
- Destination Address: 203.0.113.10 (Server Public IP)
- Service: (e.g., http/80)
- Translated Packet:
- Destination Address: 192.168.2.50 (Server Private IP) - DNAT
- Source Address: Interface Address (or a specific IP) - SNAT
Packet Flow with U-Turn NAT:
- Client 192.168.1.10 sends packet: SRC: 192.168.1.10, DST: 203.0.113.10 .
- Packet arrives at firewall (ingress interface: ethernet1/2, ingress zone: Trust).
- Firewall performs route lookup for 203.0.113.10.
- Firewall performs NAT policy lookup. It matches the U-Turn NAT rule (Source Zone Trust, Dest Zone Trust, Dest Address 203.0.113.10).
-
Based on the U-Turn NAT rule, the firewall applies
both DNAT and SNAT
.
- Destination is translated from 203.0.113.10 to 192.168.2.50.
- Source is translated from 192.168.1.10 to the firewall's Trust zone interface IP (e.g., 192.168.1.1, or another specified IP). Let's assume Interface Address.
- Packet after NAT: SRC: 192.168.1.1 (Firewall Trust IP), DST: 192.168.2.50 . The firewall records this session in its NAT session table.
- Firewall performs security policy lookup (Trust zone to Trust zone). The rule must allow traffic from the Firewall's Trust IP (or the translated source) to the Server's Private IP (the translated destination) for the specific application/service. If allowed, the packet is forwarded out the ethernet1/2 interface towards the 192.168.2.0/24 network.
- Server 192.168.2.50 receives packet: SRC: 192.168.1.1, DST: 192.168.2.50 . It sees the connection as coming from the firewall.
- Server 192.168.2.50 replies: SRC: 192.168.2.50, DST: 192.168.1.1 . This reply packet is sent to the firewall's Trust interface IP.
- The reply packet arrives at the firewall (ingress interface: ethernet1/2, ingress zone: Trust).
- Firewall performs NAT policy lookup. It finds the existing session in its NAT session table for 192.168.1.1 -> 192.168.2.50.
-
Based on the session state, the firewall reverses the NAT translations:
- Source is translated back from 192.168.2.50 to 203.0.113.10 (the original destination).
- Destination is translated back from 192.168.1.1 to 192.168.1.10 (the original source).
- Packet after Reverse NAT: SRC: 203.0.113.10 (Server Public IP), DST: 192.168.1.10 .
- Firewall performs security policy lookup (Trust zone to Trust zone - this lookup happened on the forward path, but the flow is checked against the session). If allowed, the packet is forwarded out the ethernet1/2 interface towards the 192.168.1.0/24 network.
- Client 192.168.1.10 receives packet: SRC: 203.0.113.10, DST: 192.168.1.10 . The connection is successful.
U-Turn NAT Diagrams
Visualizing the packet flow and state changes can greatly enhance understanding. Here are some diagrams illustrating U-Turn NAT.
Simplified Flowchart
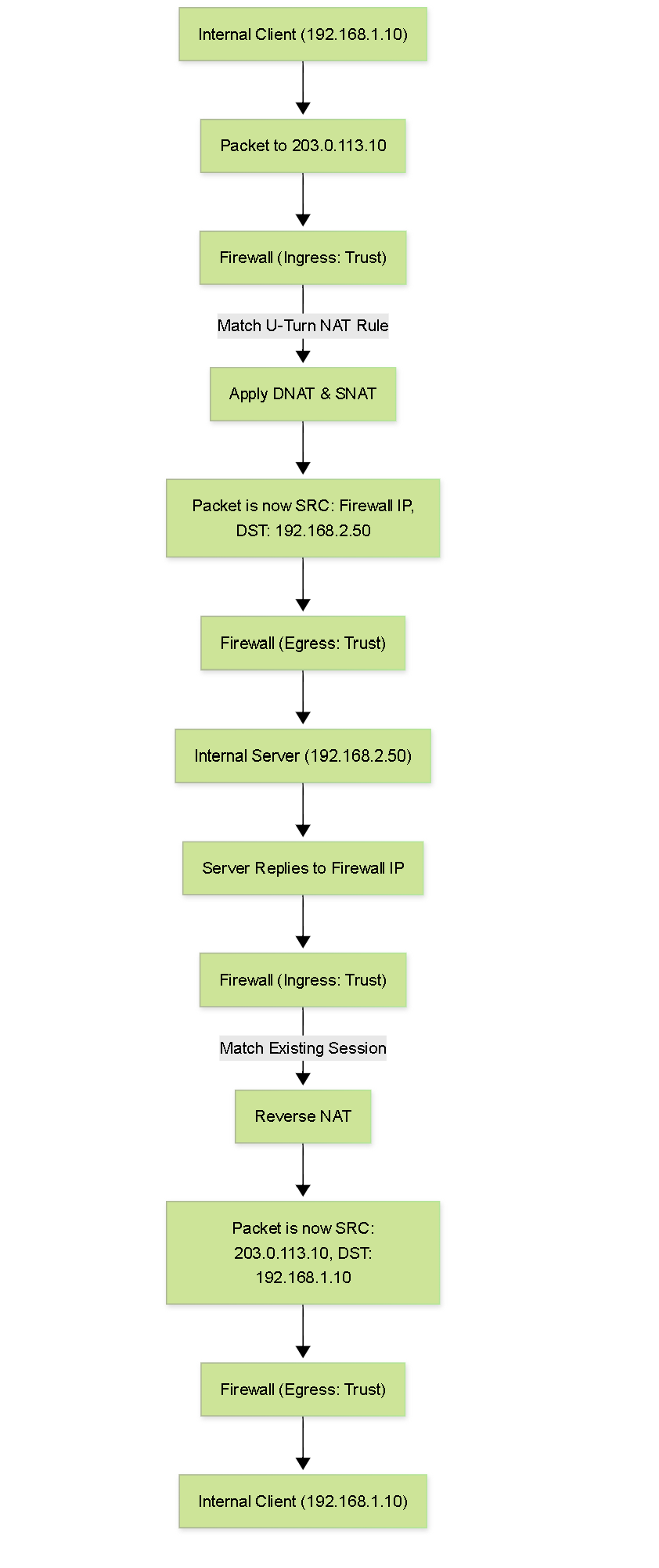
Simplified flowchart illustrating the steps in U-Turn NAT packet processing.
Detailed Sequence Diagram
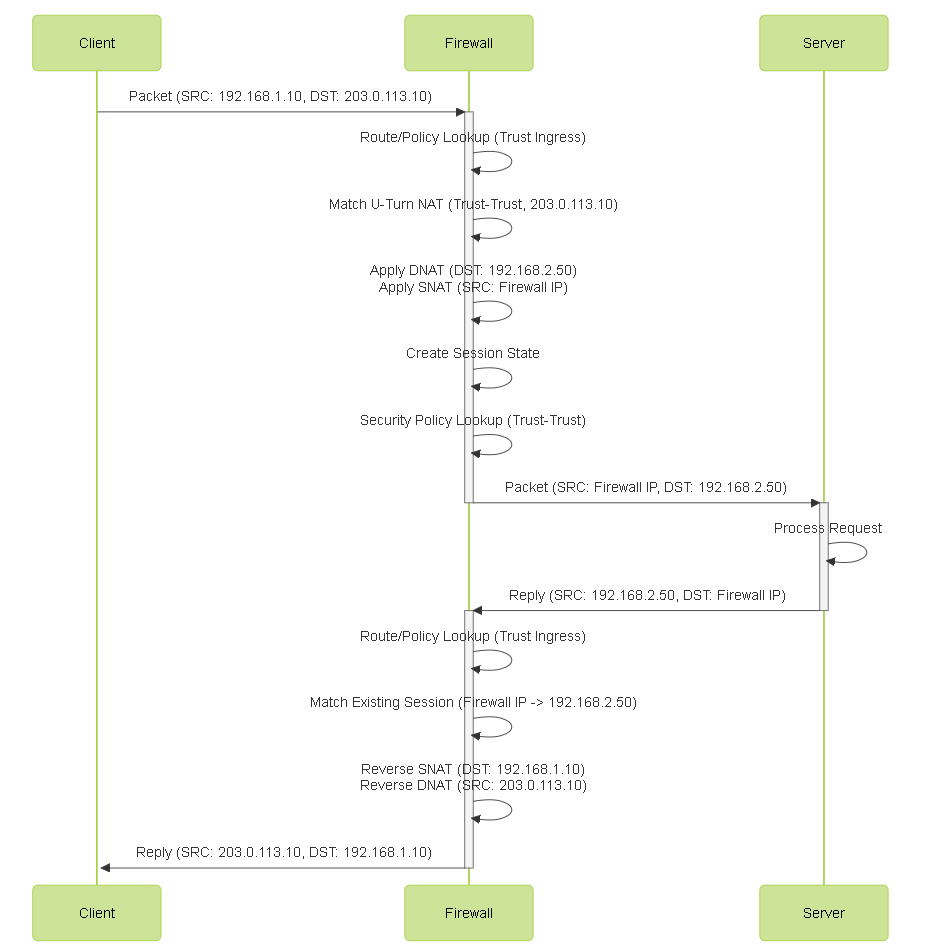
Sequence diagram showing the packet exchange and NAT translations between client, firewall, and server.
Firewall Session State Diagram (Simplified)
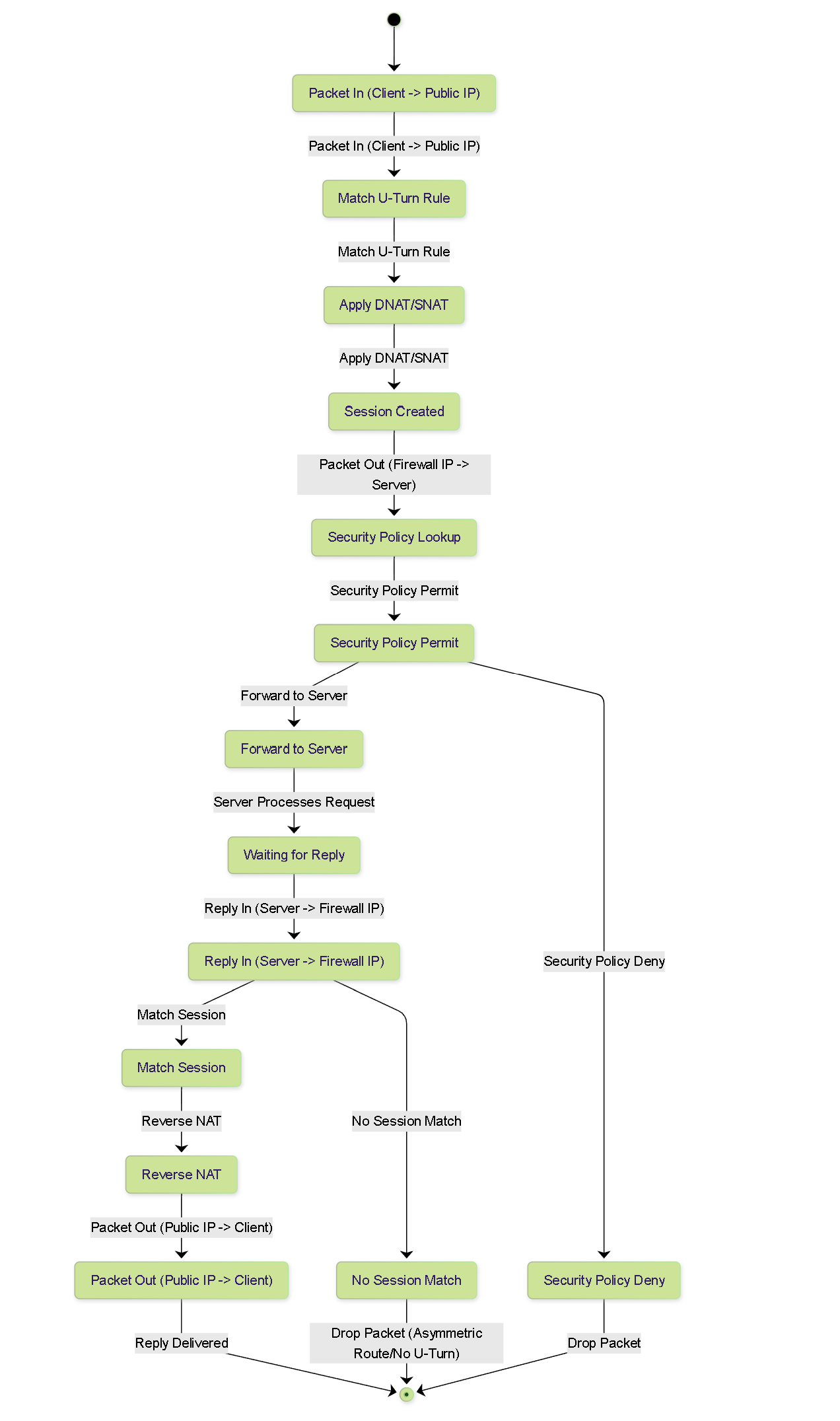
State diagram showing key states and transitions for a session undergoing U-Turn NAT on the firewall.
Configuration on Palo Alto Networks Firewalls
Configuring U-Turn NAT on PAN-OS involves creating a specific NAT policy rule and ensuring corresponding security policies allow the traffic.
Key Configuration Steps:
- Define Zones and Interfaces: Ensure your internal and potentially DMZ zones are correctly configured on interfaces.
- Create Addresses: Define address objects for your internal client subnets, the internal server's private IP, and the server's public IP.
- Create Services: Define service objects for the ports/protocols used (e.g., TCP/80, TCP/443).
- Create NAT Policy Rule: This is the core of U-Turn NAT.
- Create Security Policy Rule(s): Allow the U-Turn traffic based on the translated addresses and zones.
U-Turn NAT Policy Rule on PAN-OS
The U-Turn NAT rule requires specific settings:
- NAT Type: Destination and Source
-
Original Packet Tab:
- Source Zone: The zone where the internal client resides (e.g., 'Trust').
- Destination Zone: The zone where the server resides (e.g., 'Trust' or 'DMZ'). Note: For classic U-Turn (client and server same zone), both Source and Destination zones are the same.
- Destination Interface: Typically 'Any' or the firewall interface facing the internet (Untrust zone). While the packet ingress is internal, the *destination* IP is the public one associated with the Untrust interface. Setting this to 'Any' or the Untrust interface is common.
- Service: The application service/port(s) being accessed (e.g., 'service-tcp-80').
- Source Address: The internal client subnet(s) (e.g., 'Internal-Clients-Subnet').
- Destination Address: The server's public IP address object (e.g., 'Server-Public-IP'). This is the address the client is attempting to reach.
-
Translated Packet Tab:
-
Destination Address Translation:
- Translation Type: Static IP
- Translated Address: The server's private IP address object (e.g., 'Server-Private-IP').
-
Source Address Translation:
- Translation Type: Interface Address (or Static IP/Dynamic IP And Port if needed, but Interface Address is common and simplest for U-Turn)
- Interface: The firewall interface in the server's zone (e.g., ethernet1/2 for Trust, ethernet1/3 for DMZ).
- IP Address: The IP of the chosen interface. If using Static IP, specify the desired translation IP.
-
Destination Address Translation:
Example Configuration (Scenario 1 - Trust to Trust):
Example Configuration (Scenario 2 - Trust to DMZ):
U-Turn Security Policy Rules on PAN-OS
Once the NAT rule is configured, you need security policy rules that allow the traffic based on the translated addresses and zones.
For the U-Turn NAT rule above (Scenario 1 - Trust to Trust), the packet after NAT looks like: SRC: Firewall IP (192.168.1.1), DST: Server Private IP (192.168.2.50) , going from Trust zone to Trust zone.
Required Security Policy Rule (Scenario 1 - Trust to Trust):
- Source Zone: Trust
- Destination Zone: Trust
- Source Address: Firewall Interface IP object (or the specific translated IP if Static SNAT was used) - (e.g., 'Trust-Interface-IP' or 192.168.1.1)
- Destination Address: The server's private IP address object (e.g., 'Internal-Web-Server-Private-IP' or 192.168.2.50)
- Application: The specific application(s) (e.g., 'web-browsing', 'ssl')
- Service: application-default (or the specific service objects used in NAT, e.g., service-tcp-80, service-tcp-443)
- Action: Allow
For the U-Turn NAT rule above (Scenario 2 - Trust to DMZ), the packet after NAT looks like: SRC: Firewall IP (10.10.10.1), DST: Server Private IP (10.10.10.50) , going from Trust zone to DMZ zone.
Required Security Policy Rule (Scenario 2 - Trust to DMZ):
- Source Zone: Trust
- Destination Zone: DMZ
- Source Address: Firewall DMZ Interface IP object (or the specific translated IP if Static SNAT was used) - (e.g., 'DMZ-Interface-IP' or 10.10.10.1)
- Destination Address: The server's private IP address object (e.g., 'DMZ-App-Server-Private-IP' or 10.10.10.50)
- Application: The specific application(s) (e.g., 'custom-app-8080')
- Service: application-default (or the specific service object, e.g., service-tcp-8080)
- Action: Allow
PCNSE/PCNSA Key Points for U-Turn NAT
U-Turn NAT is a frequently tested concept on Palo Alto Networks certification exams (PCNSA, PCNSE). Pay close attention to these points:
- NAT Rule Type: U-Turn NAT requires a rule with Type: Destination and Source . This is crucial for applying both translations in a single rule match.
-
Original Packet Match Criteria:
Understand the criteria used to match the initial client packet:
- Source Zone: Internal client zone.
- Destination Zone: Server zone (often the same as Source Zone for classic U-Turn).
- Destination Address: The server's public IP.
-
Translated Packet Settings:
Know what happens after a match:
- Destination Address: Translated to the server's private IP (DNAT).
- Source Address: Translated to the firewall's interface IP in the server's zone (or a specified IP) (SNAT).
- Security Policy Matching: Security policies evaluate traffic based on the translated addresses and original zones . A common mistake is to write the security policy based on the original (client -> public IP) addresses, which will fail. The security rule must permit traffic from the translated source IP (Firewall IP) to the translated destination IP (Server Private IP) within the original Source/Destination zones.
- Packet Flow Order: Remember the high-level packet processing order: Packet In -> Zone Protection/DDoS -> Flow Lookup -> Session Lookup -> NAT Policy (Ingress) -> Tunnel Decryption -> App-ID -> Content-ID (Security Policy) -> Routing -> NAT Policy (Egress - for SNAT) -> Packet Out. U-Turn NAT's DNAT/SNAT happens early in the flow, influencing the security policy match.
- Asymmetric Routing: U-Turn NAT prevents asymmetric routing issues where the reply bypasses the firewall's NAT state. The SNAT ensures the reply comes back to the firewall.
- Alternatives: Be aware that split-DNS (internal DNS resolving the external FQDN to the server's internal IP) is often a simpler alternative to U-Turn NAT if you manage internal DNS. However, U-Turn NAT is necessary if split-DNS is not feasible or if clients use the public IP directly.
Troubleshooting U-Turn NAT Issues
Troubleshooting U-Turn NAT often involves verifying NAT and Security policy configurations and tracing the packet flow.
Common troubleshooting steps and areas to check:
-
Verify DNS Resolution:
Ensure the client is resolving the public FQDN to the correct public IP address. Use
nslookupordigfrom the client. If it resolves to the private IP, U-Turn NAT isn't needed (this is the Split-DNS solution). -
Check Firewall Traffic Logs:
Look for traffic logs matching the client's source IP, destination public IP, and service.
- Action: Drop? If dropped, look at the 'Action' and 'Rule' columns. Is it dropped by a Security Policy? Or implicitly dropped?
- If Action is Drop by Security Policy: The security rule is misconfigured. Check the translated source and destination IPs shown in the session or packet details ('pkt-info' in CLI) and ensure your security rule permits that translated traffic between the original zones.
- If Action is Allow: Check the session details. Is the NAT rule being applied correctly (both DNAT and SNAT)?
- Check Firewall NAT Logs: Look for NAT logs matching the client's source IP and the public destination IP. Verify that the correct U-Turn NAT rule is being hit and that both destination and source translations are happening as expected.
-
Use the Session Browser (CLI):
The command
show session all filter source <client-ip> destination <public-server-ip>can show the session state. Check the translated IPs and ports. If no session exists, the packet is likely being dropped early (routing, zone protection, or failing NAT policy match).> show session all filter source 192.168.1.10 destination 203.0.113.10 > show session id <session-id> detail # Use the session ID from the previous command > show session id <session-id> pkt-info # Detailed packet information for the session -
Use Packet Capture:
Capture packets on the relevant firewall interfaces (internal interface ingress/egress, potentially DMZ interface). This shows the packets before and after NAT and routing.
> set cli config-output on > debug dataplane packet-diag set capture on > debug dataplane packet-diag set filter match source 192.168.1.10 destination 203.0.113.10 protocol 6 # TCP > debug dataplane packet-diag set capture stage drop on > debug dataplane packet-diag set capture stage firewall on > debug dataplane packet-diag set capture stage receive on > debug dataplane packet-diag set capture stage transmit on > debug dataplane packet-diag set capture stage flow on > debug dataplane packet-diag set capture stage proxy on > debug dataplane packet-diag set capture stage decrypt on > debug dataplane packet-diag set capture stage encrypt on > debug dataplane packet-diag set capture stage forward on > debug dataplane packet-diag set capture stage nat on > debug dataplane packet-diag set capture stage policy on > debug dataplane packet-diag set capture stage route on > debug dataplane packet-diag set capture stage lookup on > debug dataplane packet-diag set capture stage app-id on > debug dataplane packet-diag set capture stage content-id on > debug dataplane packet-diag set capture stage vulnerability on > debug dataplane packet-diag set capture stage wildfire on > debug dataplane packet-diag set capture stage url on > debug dataplane packet-diag set capture stage file on > debug dataplane packet-diag set capture stage user on > debug dataplane packet-diag set capture stage qos on > debug dataplane packet-diag set capture stage zone-protection on > debug dataplane packet-diag set capture stage dos on > debug dataplane packet-diag set capture stage decryption-policy on > debug dataplane packet-diag set capture stage security-policy on > debug dataplane packet-diag set capture stage nat-policy on # Trigger the traffic from the client > debug dataplane packet-diag set capture off > debug dataplane packet-diag show capture all > panos_uturn_capture.pcap # Download the pcap file using SCP/WinSCP/Cyberduck
- Route Lookups: Verify the routing table (`show routing fib`) on the firewall for both the original destination public IP and the translated private IP. Ensure the firewall routes traffic correctly to the server's network segment.
- Server-Side Firewall: If there's a host-based firewall or security group on the server, ensure it's configured to allow traffic from the firewall's SNAT IP (the translated source IP).
- Check for Duplicate DNAT Rules: Ensure your U-Turn NAT rule is matched before any broader DNAT rule for the same public IP that might apply to traffic coming from the internal zone.
U-Turn NAT Quiz
Test your understanding of U-Turn NAT concepts and configuration on Palo Alto Networks firewalls with these 20 questions.
Conclusion
U-Turn NAT is a powerful solution for a specific, yet common, network challenge on Palo Alto Networks firewalls: allowing internal clients to access internal or DMZ resources using the same public IP or DNS name that external users employ. By applying both Destination and Source NAT translations simultaneously, the firewall ensures that the server's reply traffic is directed back through the firewall, maintaining session state and enabling the connection.
Understanding the packet flow, the specific configuration requirements for both NAT and security policies, and how to troubleshoot common issues is vital, particularly for those pursuing PCNSA or PCNSE certifications. While alternatives like Split-DNS exist, U-Turn NAT remains a necessary technique in many environments.
By mastering U-Turn NAT, you gain deeper insight into firewall packet processing, NAT rule evaluation, and the interaction between NAT and security policies, skills that are fundamental to network security and firewall administration.