Prioritize Network Traffic using QoS
What is Quality of Service (QoS)?
Quality of Service (QoS) is a set of technologies used to manage network traffic and ensure the performance of critical applications. By prioritizing specific types of traffic, QoS helps maintain desired service levels, especially for applications sensitive to delays or data loss.
With QoS, you can:
- Assign the order in which packets are handled.
- Allot bandwidth to ensure preferred treatment for selected traffic, applications, and users.
- Optimize levels of performance based on configurable parameters.
Key service quality measurements subject to a QoS implementation include:
- Bandwidth: The maximum rate of data transfer across a given path.
- Throughput: The actual rate of data transfer achieved.
- Latency: The delay experienced by data as it travels from source to destination.
- Jitter: The variation in latency between packets.
The ability to shape and control these measurements makes QoS particularly important for high-bandwidth, real-time traffic such as Voice over IP (VoIP), video conferencing, and video-on-demand, which are highly sensitive to latency and jitter.
Benefits of Implementing QoS
Implementing QoS on a Palo Alto Networks firewall offers several advantages for network management and performance:
- Traffic Prioritization: Guarantee high priority to important network and application traffic while limiting non-essential traffic. This ensures that business-critical applications receive the necessary resources.
- Equitable Bandwidth Sharing: Achieve fair bandwidth distribution among different subnets, classes of service, or users within a network.
- Flexible Bandwidth Allocation: Allocate bandwidth externally (upload), internally (download), or both. QoS can be applied to either or both directions of traffic flow.
- Low Latency for Critical Services: Ensure minimal delay for customer-facing and revenue-generating traffic in enterprise environments, enhancing user experience and productivity.
- Traffic Profiling and Control: Perform traffic profiling of applications to monitor and ensure appropriate bandwidth usage, preventing any single application or user from monopolizing network resources.
Core QoS Components in Palo Alto Networks Firewalls
A full QoS solution on a Palo Alto Networks firewall is built upon three primary configuration components:
-
QoS Profile: This defines the bandwidth and priority settings for up to eight distinct QoS classes. Each class within a profile can have its own guaranteed and maximum bandwidth, as well as a priority level (real-time, high, medium, low). The profile also specifies the total bandwidth for all its classes combined.
-
QoS Policy: QoS policy rules are used to identify specific traffic that should receive QoS treatment. These rules match traffic based on criteria like applications, users, source/destination zones and addresses, services, and DSCP values. Matched traffic is then assigned a QoS class defined in a QoS profile.
-
QoS Egress Interface: This is the physical interface on the firewall where the QoS policies and profiles are enforced as traffic exits the firewall. QoS is always applied on the egress interface of a traffic flow.
These components work together to optimize and prioritize traffic flow, allocating and ensuring bandwidth according to the configured parameters.
For congestion management, PAN-OS utilizes a Weighted Random Early Detection (WRED) algorithm. When a queue is filling faster than it can be emptied, WRED proactively drops packets based on a probability function tied to the average queue depth, rather than waiting for the queue to be full (tail dropping).
Each firewall model supports a maximum number of ports that can be configured with QoS. Refer to the specific firewall model's spec sheet or the product comparison tool for details.
QoS Traffic Flow
The following diagram illustrates how traffic flows from the source, is processed and shaped by the firewall with QoS enabled, and is ultimately prioritized and delivered to its destination.
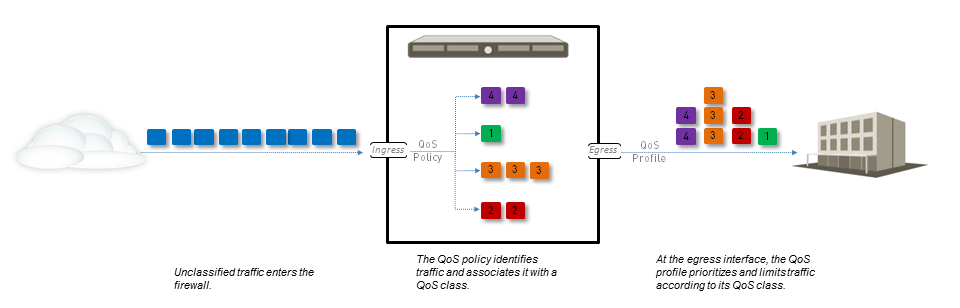
The QoS configuration options allow you to control and define the traffic flow at different points:
- A QoS policy rule identifies the traffic that you want to receive QoS treatment and assigns that traffic a specific QoS class.
- The traffic matching the QoS policy is then shaped based on the settings defined in the QoS profile for that assigned class.
- This shaping (priority queuing and bandwidth management) occurs as the traffic exits the physical QoS egress interface .
Each QoS configuration component influences the others, allowing for either a granular QoS implementation or a simpler setup with minimal administrator action.
QoS for Applications and Users
Palo Alto Networks firewalls extend the power of QoS beyond basic network or subnet-based control by integrating App-ID and User-ID features. This allows for granular classification and shaping of traffic based on specific applications and users.
- App-ID: Identifies applications traversing the network, regardless of port, protocol, or encryption. This enables QoS policies to prioritize or limit bandwidth for specific applications (e.g., giving higher priority to SAP while limiting YouTube).
- User-ID: Integrates with directory services (like Active Directory) to identify users and groups. This allows QoS policies to be applied based on user identity, ensuring that critical users or departments receive appropriate bandwidth and priority.
By leveraging App-ID and User-ID, administrators can create highly specific QoS policies that align network resource allocation with business priorities. For example, you can guarantee bandwidth for a critical business application used by the finance department.
Configuring QoS Policy
A QoS policy rule is used to define the traffic that will receive QoS treatment (either preferential treatment or bandwidth-limiting) and assigns such traffic a QoS class of service.
You can define a QoS policy rule to match traffic based on:
- Applications and application groups (via App-ID).
- Source zones, source addresses, and source users (via User-ID).
- Destination zones and destination addresses.
- Services and service groups (limited to specific TCP and/or UDP port numbers).
- URL categories, including custom URL categories.
- Differentiated Services Code Point (DSCP) and Type of Service (ToS) values.
Multiple QoS policy rules can be set up (under Policies > QoS ) to associate different types of traffic with different QoS classes.
Configuring QoS Profiles & Classes
A QoS profile defines the specific treatment for up to eight QoS classes. It dictates priority queuing and bandwidth management for traffic assigned to these classes.
QoS Profile
With a QoS profile (configured under Network > Network Profiles > QoS Profile ), you can:
- Define individual bandwidth (Egress Max, Egress Guaranteed) and priority settings (real-time, high, medium, low) for up to eight QoS classes.
- Set the total combined bandwidth allotted for all eight classes within that profile.
- Attach one or more QoS profiles to a physical interface to apply the defined settings to traffic exiting that interface.
A default QoS profile is available, but its classes do not have predefined bandwidth limits.
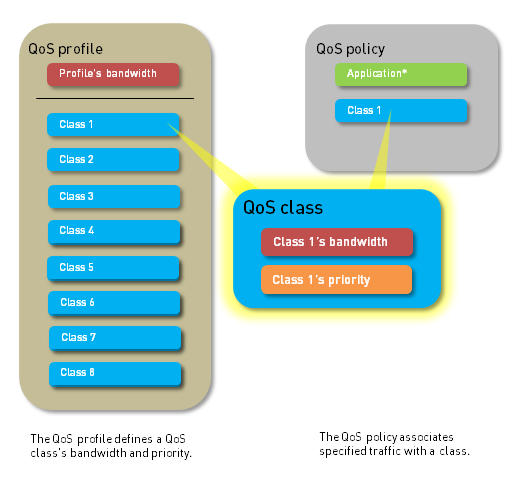
QoS Classes
A QoS class, defined within a QoS profile, determines the priority and bandwidth for traffic matching a QoS policy rule.
- Up to eight definable QoS classes (Class 1 to Class 8) exist in a single QoS profile.
- Unless otherwise configured, traffic that does not match a QoS policy rule (and thus isn't assigned a specific class) is typically assigned to Class 4 by default.
QoS Priority Queuing
One of four priorities can be enforced for a QoS class:
- Real-time: Highest priority, typically used for applications extremely sensitive to latency, such as voice and video.
- High: For important traffic that needs precedence over standard traffic.
- Medium: For general traffic that requires better than best-effort.
- Low: For non-critical or bulk traffic that can tolerate delays.
Packets in the outgoing traffic flow are queued based on their priority until the network is ready to process them.
QoS Bandwidth Management
Bandwidth management allows control over traffic flows to prevent network congestion and allocate specific bandwidth for different types of traffic, applications, or users.
- Egress Guaranteed: The amount of bandwidth guaranteed for matching traffic. When this guaranteed bandwidth is exceeded, the firewall passes traffic on a best-effort basis. Unused guaranteed bandwidth remains available for other traffic.
- Egress Max: The overall maximum bandwidth allocation for matching traffic. The firewall will drop traffic that exceeds this limit.
These limits can be set for individual QoS classes within a profile, and also for the total traffic handled by the profile.
When configuring Egress Guaranteed and Egress Max values in percentages within a QoS Profile's classes:
- The Egress Guaranteed (%) per class is calculated using the QoS Profile's overall Egress Max value, not the Profile's Egress Guaranteed value.
- The Profile's total Egress Guaranteed (in Mbps/Gbps) effectively becomes the sum of (Egress Guaranteed (%) per class * Profile Egress Max).
Configuring QoS Egress Interface
Enabling a QoS profile on the egress interface of the traffic identified for QoS treatment completes a QoS configuration.
- The ingress interface for QoS traffic is where traffic enters the firewall.
- The egress interface for QoS traffic is where traffic leaves the firewall. QoS is always enabled and enforced on this egress interface.
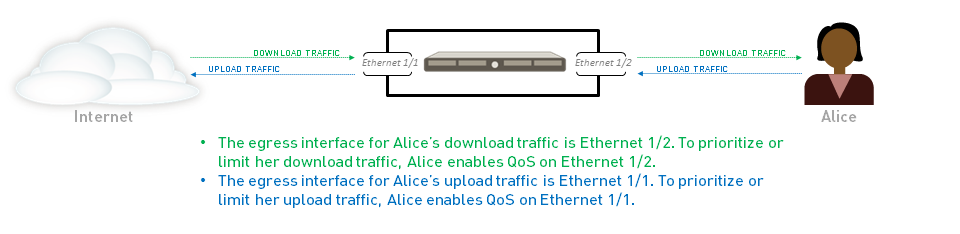
The egress interface in a QoS configuration can be either an external-facing or internal-facing interface of the firewall, depending on the direction of the traffic flow being managed.
Example:
- If you are limiting employees’ download traffic from a specific website, the traffic flow is from the Internet, through the firewall, to your company network. The egress interface for QoS configuration is the firewall’s internal interface.
- If you are limiting employees’ upload traffic to the same website, the traffic flow is from your company network, through the firewall, to the Internet. The egress interface for QoS configuration is the firewall’s external interface.
As stated before, QoS policy rules are applied after other security policies (including NAT), but QoS rules are evaluated based on original packet details (pre-NAT source IP/zone, post-NAT destination zone).
QoS for Clear Text and Tunneled Traffic
When enabling QoS on an interface, you must select a default QoS profile that defines bandwidth and priority settings for clear text traffic egressing that interface. However, you can apply more granular QoS settings.
Clear Text Traffic
For clear text traffic, beyond the default profile, you can:
- Set overall Egress Guaranteed and Egress Max bandwidths specifically for all clear text traffic on that interface.
- Apply different QoS profiles to clear text traffic based on its source interface and source subnet . This allows for varied QoS treatment for traffic originating from different internal segments even if it exits the same physical interface.
Tunneled Traffic
QoS preferential treatment and bandwidth limiting can also be enforced for tunneled traffic. On Palo Alto Networks firewalls, tunneled traffic typically refers to tunnel interface traffic, specifically IPSec traffic in tunnel mode.
For tunneled traffic, you can:
- Select a default QoS profile to apply to all tunneled traffic exiting the interface.
- Set overall Egress Guaranteed and Egress Max bandwidths specifically for all tunneled traffic on that interface.
- Apply specific QoS profiles to individual tunnel interfaces . This allows fine-grained control over the bandwidth and priority of traffic traversing specific VPN tunnels.
Step-by-Step QoS Configuration Guide
Follow these general steps to configure Quality of Service (QoS) on a Palo Alto Networks firewall. This example focuses on limiting web browsing.
-
Identify the traffic you want to manage with QoS.
Use the Application Command Center ( ACC ) to view trends and traffic related to applications, URL filtering, etc. Click an application name for details.
-
Identify the egress interface for the target applications.
The egress interface depends on traffic flow (internal for downloads, external for uploads).
View Traffic logs ( Monitor > Logs > Traffic ). Filter for the application. The Egress I/F column shows the egress interface.
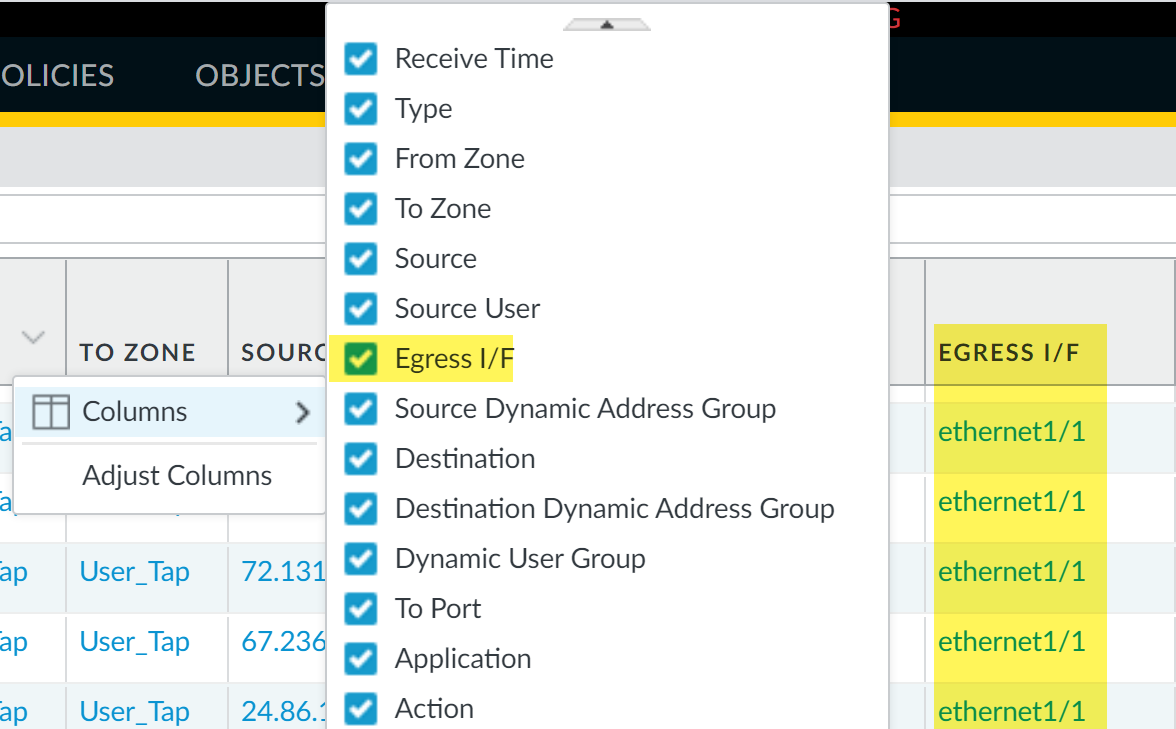
Adding Egress I/F column to Traffic Logs 
Detailed Log View with Egress Interface -
Add a QoS policy rule. ( Policies > QoS > Add )
- General tab: Give a descriptive Name.
- Specify traffic: Use Source, Destination, Application, Service/URL Category, DSCP/ToS tabs. For example, add 'web-browsing' to the Application tab.
- Other Settings tab: Assign a QoS Class (e.g., Class 2 for web browsing).
- Click OK .
Remember: If matching on source, use pre-NAT source information in the QoS policy. -
Add a QoS profile. ( Network > Network Profiles > QoS Profile > Add )
- Enter a Profile Name .
- Set overall profile bandwidth limits: Egress Max and Egress Guaranteed .
-
Classes section:
Add classes (e.g., Class 2). For each class:
- Select Priority (real-time, high, medium, low).
- Enter Egress Max and Egress Guaranteed bandwidth for the class.
- Click OK .
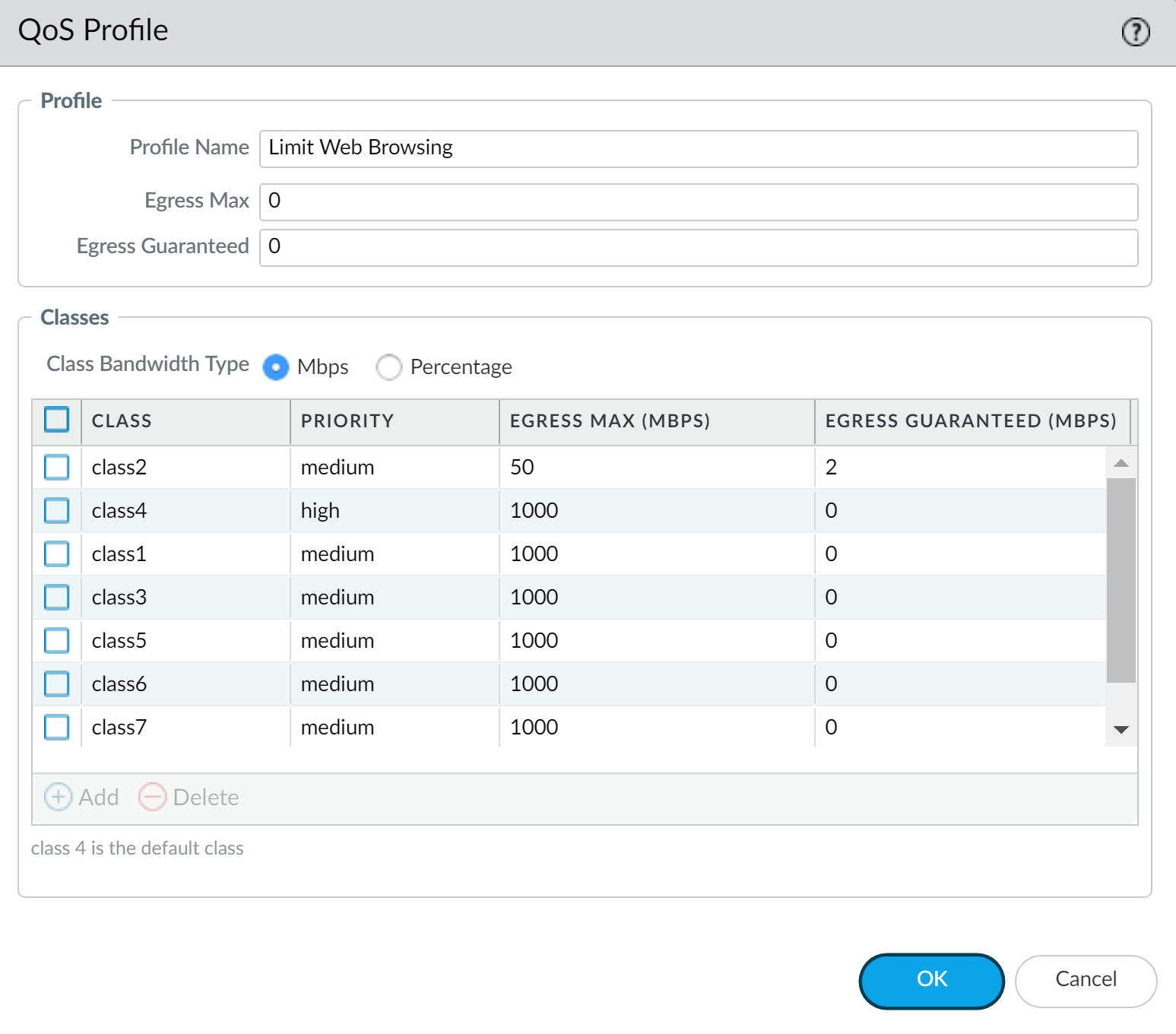
Example QoS Profile: Limit Web Browsing -
Enable QoS on a physical interface. ( Network > QoS > Add )
- Physical Interface tab: Select the Interface Name (the egress interface identified in Step 2).
- Set the Egress Max bandwidth for all traffic exiting this interface. (Best practice!)
- Check Turn on QoS feature on this interface .
- Default Profile section: Select a QoS profile (created in Step 4) for Clear Text traffic.
- (Optional) Select a default QoS profile for tunneled traffic.
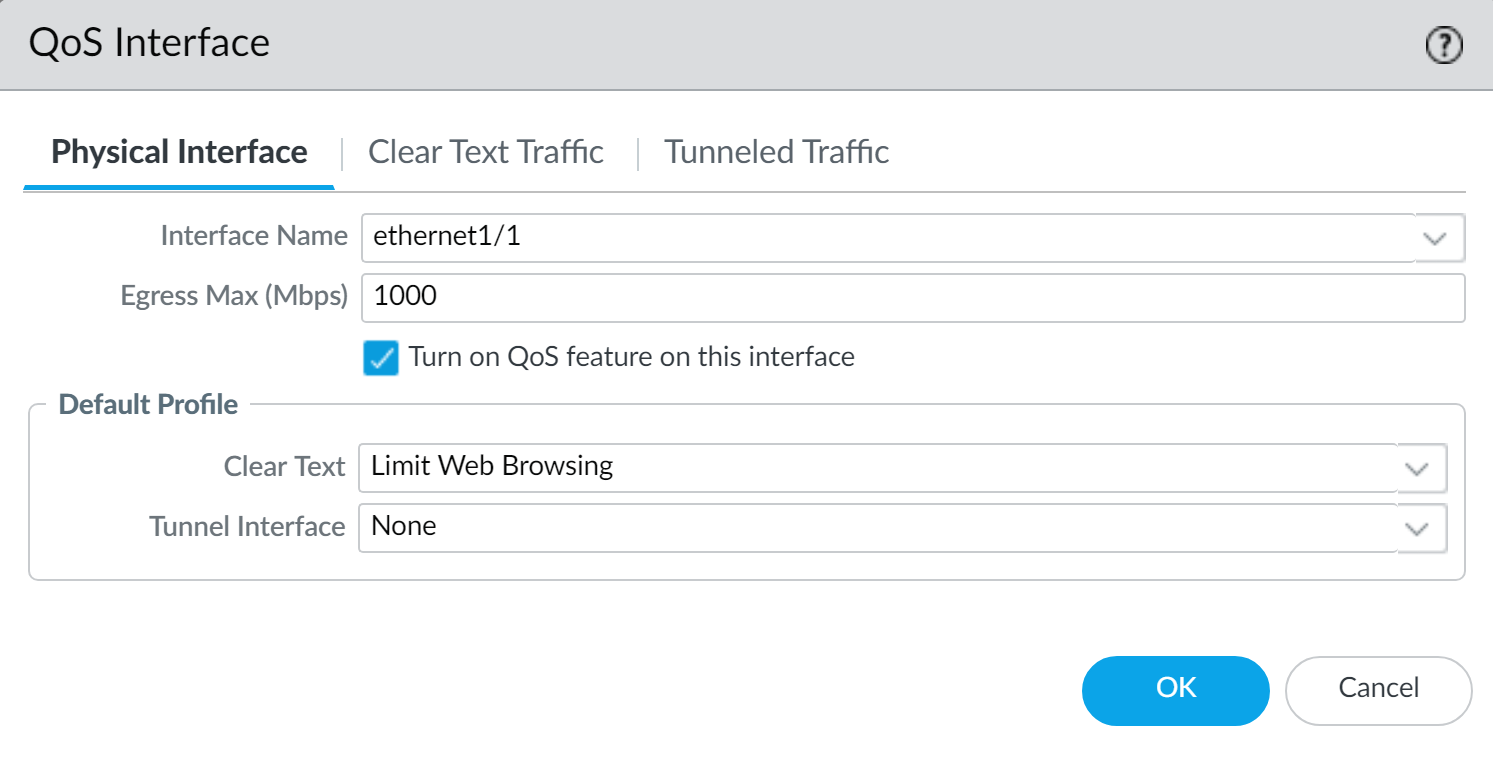
Enabling QoS on an Ethernet Interface - (Optional) Clear Text Traffic / Tunneled Traffic tabs: Configure more granular settings, overriding defaults.
- Click OK .
For PA-3200, PA-5200, PA-5450, PA-7000 Series: If applying QoS to a subinterface, you must also select a destination interface in the QoS policy rule. -
Commit your changes. (Click Commit )
-
Verify a QoS configuration.
Select Network > QoS > Statistics . View bandwidth, active sessions, and applications for selected QoS classes/interfaces.
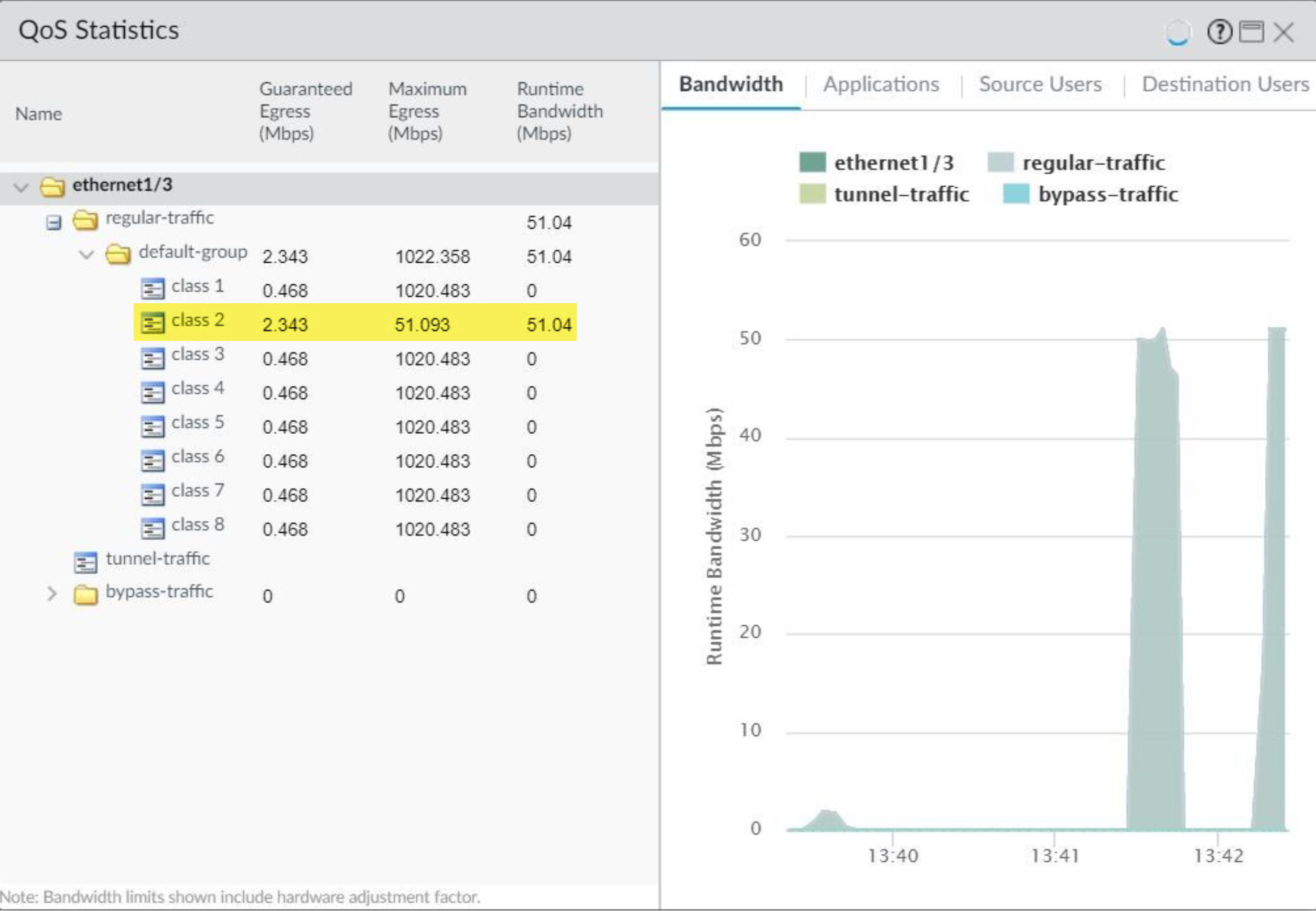
QoS Statistics for an Interface Bandwidth limits shown on the QoS Statistics window include a hardware adjustment factor.
Lockless QoS
Palo Alto Networks firewalls support two types of QoS:
- Legacy QoS: The traditional QoS mode, shaping QoS traffic.
- Lockless QoS (PAN-OS 10.2.5 and later): Designed for firewalls with higher bandwidth QoS requirements. It dedicates CPU cores to the QoS function, improving performance (throughput and latency). Packets from the same interface (or port) are shaped by the same core.
Considerations for Lockless QoS:
- In LAG (Link Aggregation Group) configurations, members are mapped to the same core, so overall LAG QoS throughput is limited by per-core throughput.
- QoS throughput on high-speed ports (100G, 40G, 25G) is limited to a single core's throughput.
- If multiple ports are mapped to a single core, its QoS throughput is shared.
- Supported on specific models (e.g., PA-3400 Series, PA-5400 Series). Maximum bandwidth allocation at port/profile level is typically 10G for these platforms with Lockless QoS.
CLI commands for Lockless QoS:
-
set lockless-qos yes: Enable Lockless QoS (requires commit and reboot). -
set lockless-qos no: Disable Lockless QoS (requires commit and reboot). -
show lockless-qos enable: View enable status. -
show lockless-qos if-core-mapping: View port-to-core mapping. -
show lockless-qos core-num(PAN-OS 11.1.3+): View number of CPU cores allocated for Lockless QoS.
QoS for Virtual Systems (VSYS)
QoS can be configured independently for each virtual system (VSYS) on a Palo Alto Networks firewall. Since a VSYS acts as an independent firewall, its QoS configuration is separate.
Key considerations for QoS in a VSYS environment:
- Configuration is similar to a physical firewall but requires careful specification of source and destination of traffic (zones, interfaces) because VSYS boundaries are logical.
- Traffic might span multiple VSYS, so QoS policies must be scoped correctly.
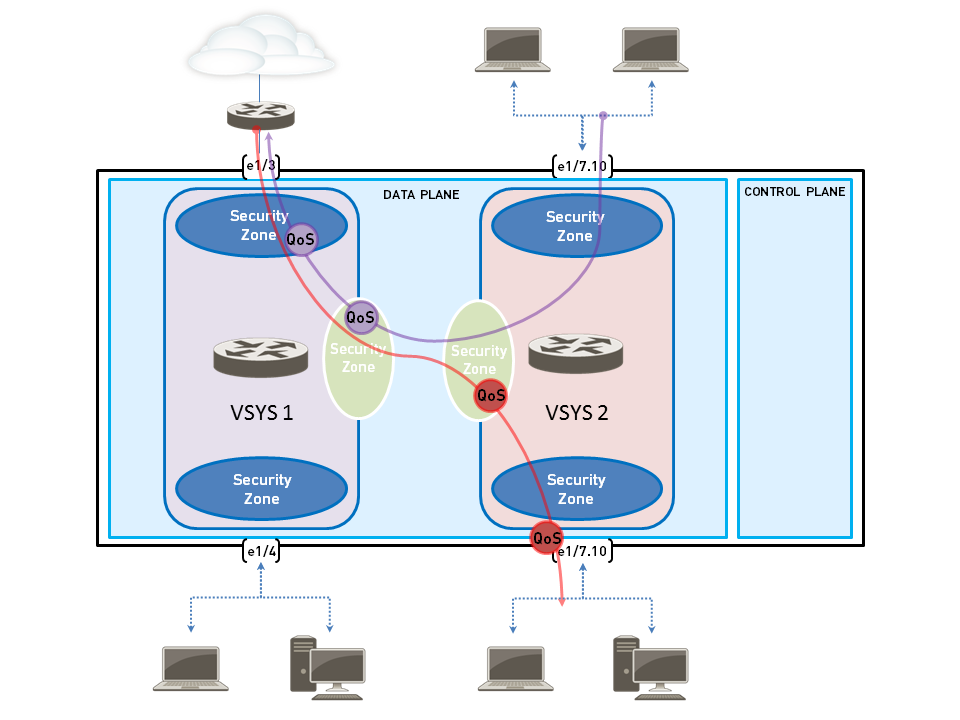
Configuration steps are broadly similar to standard QoS:
- Confirm interfaces, virtual routers, and zones are correctly associated with each VSYS.
-
Identify traffic for QoS within the specific VSYS (use ACC with VSYS filter).
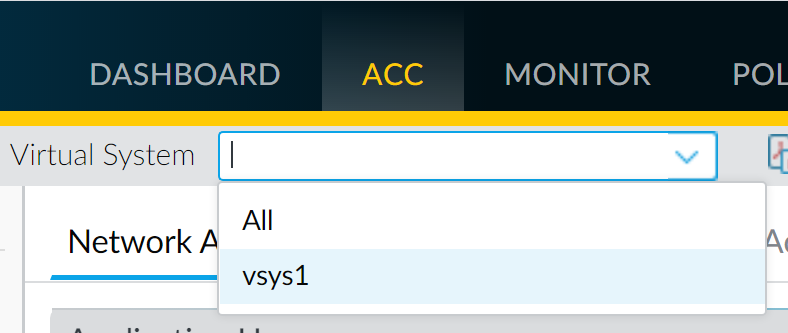
Filtering ACC by Virtual System - Identify the egress interface for this traffic (Monitor > Logs > Traffic, filter by VSYS). Egress point could be a physical interface or a zone.
- Create a QoS Profile (as described previously).
-
Create a QoS Policy.
Crucially, when defining the QoS Policy for a VSYS, you must define traffic based on source and destination zones within that VSYS to ensure traffic is prioritized/shaped only for that virtual system.
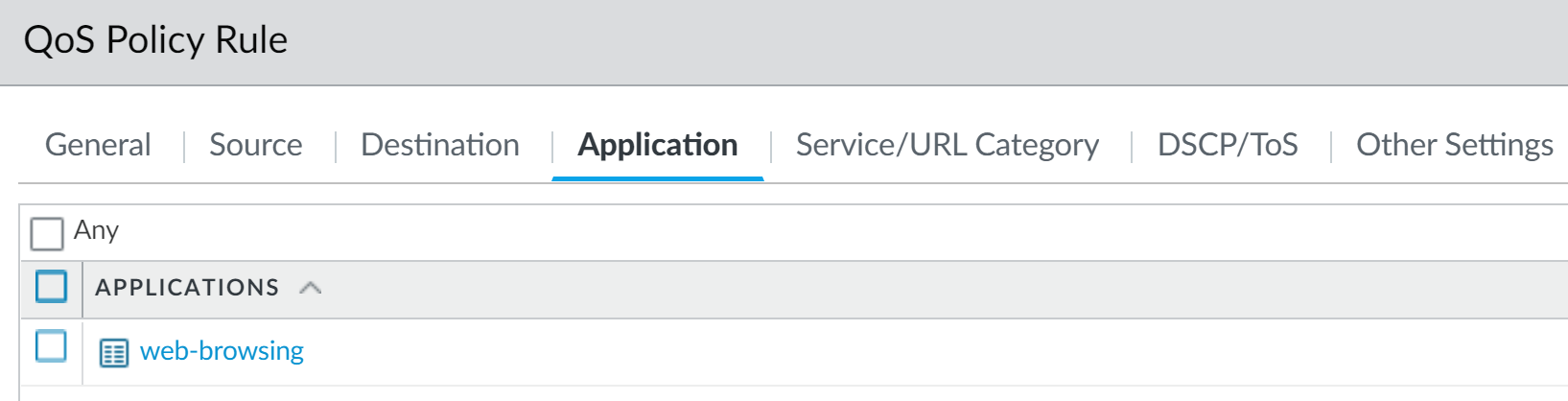
QoS Policy - Matching Application (e.g., web-browsing) 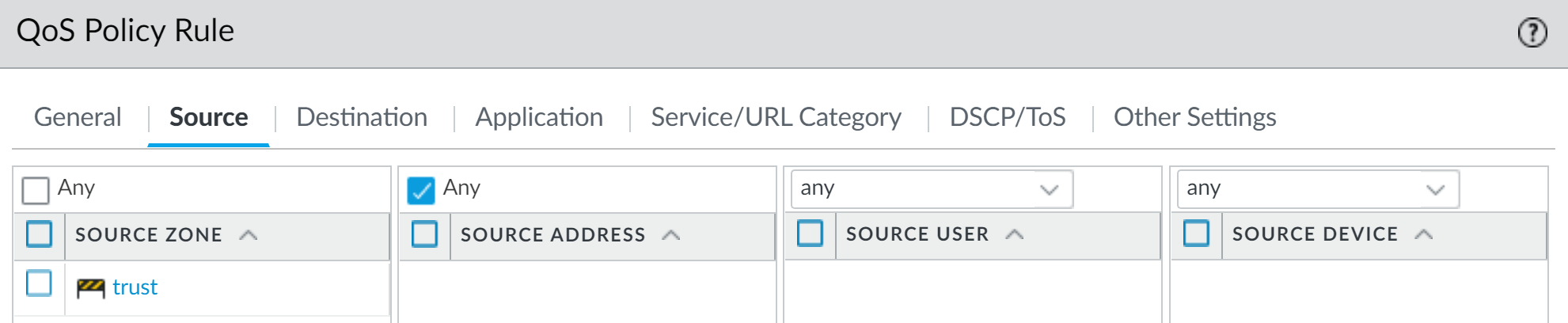
QoS Policy - Matching Source Zone for VSYS 
QoS Policy - Matching Destination Zone for VSYS 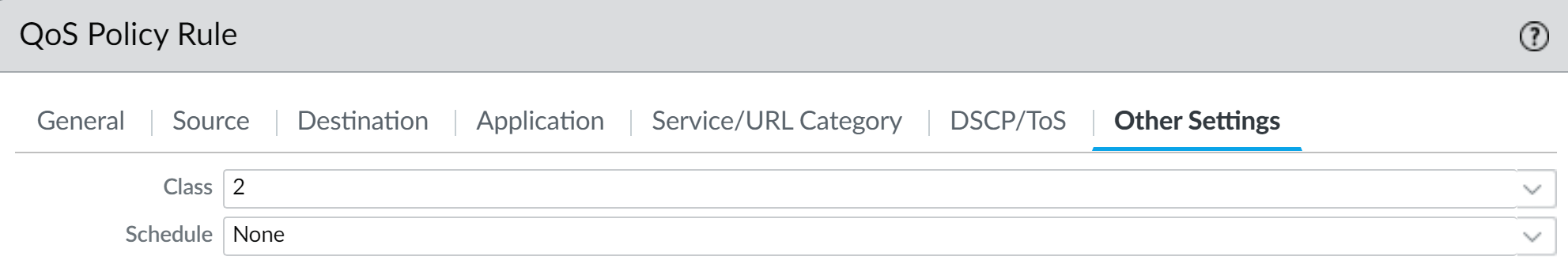
QoS Policy - Assigning QoS Class - Enable the QoS Profile on the relevant physical interface associated with the VSYS traffic's egress path.
- Commit and Verify.
Enforce QoS Based on DSCP Classification
A Differentiated Services Code Point (DSCP) is a value in the IP packet header used to request a certain level of service, like high priority or best-effort delivery. Palo Alto Networks firewalls can use DSCP for QoS in two main ways:
- Honoring Incoming DSCP: Apply QoS treatment based on the DSCP value of incoming traffic.
- Marking Outgoing DSCP: Mark session traffic with a DSCP value as it exits the firewall. This is often done to match the DSCP value detected at the beginning of the session (Session-Based DSCP Classification).
This enables continuous QoS treatment as traffic flows through your network, as intermediate devices can also honor these DSCP markings.
Common DSCP marking types:
- Expedited Forwarding (EF): For low loss, low latency, guaranteed bandwidth (highest priority).
- Assured Forwarding (AF): Provides reliable delivery, higher priority than best-effort. AF has different drop precedence levels (e.g., AF11, AF22).
- Class Selector (CS): For backward compatibility with IP Precedence.
- IP Precedence (ToS): Legacy marking.
- Custom Codepoint: Define custom DSCP values.
Steps to enable Session-Based DSCP Classification:
- Perform preliminary QoS configuration steps (Profile, Interface).
-
Define QoS Policy based on DSCP:
- In the QoS Policy rule ( Policies > QoS ), go to the DSCP/ToS tab.
- Add Codepoints: Select the Type (e.g., Assured Forwarding) and specific Codepoint (e.g., AF11).
- On the Other Settings tab, assign a QoS Class to this DSCP-matched traffic.
-
Define QoS Profile for the DSCP-mapped Class:
- In the QoS Profile ( Network > Network Profiles > QoS Profile ), configure the priority and bandwidth for the QoS Class assigned in step 2.
- Enable QoS on an Interface (as described previously).
-
Enable DSCP Marking on Security Policy:
- Edit the relevant Security Policy rule ( Policies > Security ).
- Go to the Actions tab.
- In the QoS Marking drop-down, choose Follow Client-to-Server Flow . This tells the firewall to mark return traffic with the same DSCP value detected at the beginning of the session (from client to server).
- Commit the configuration.
QoS Mermaid Diagrams
Overall QoS Process Flow
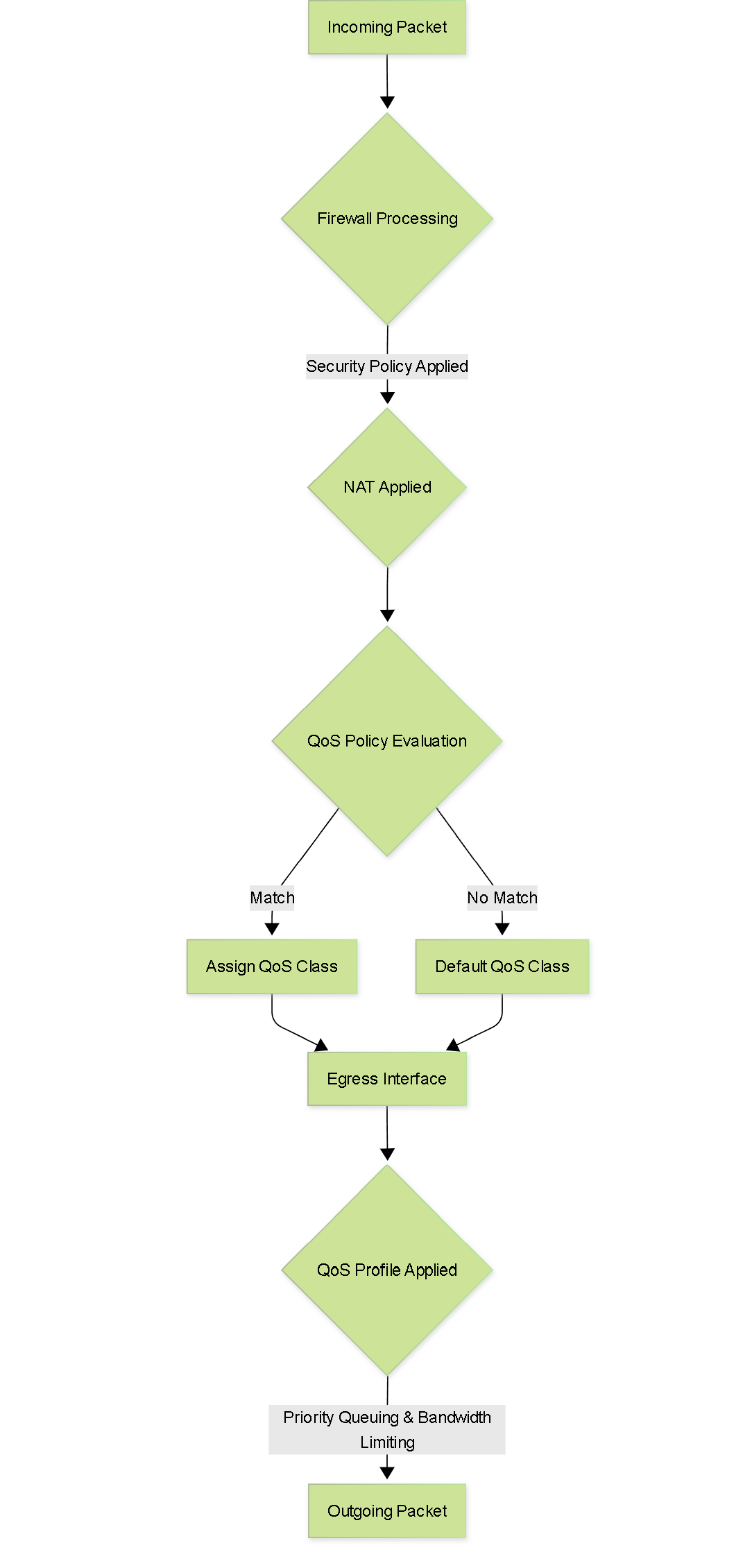
Flowchart illustrating the general packet processing path with QoS.
QoS Configuration Steps
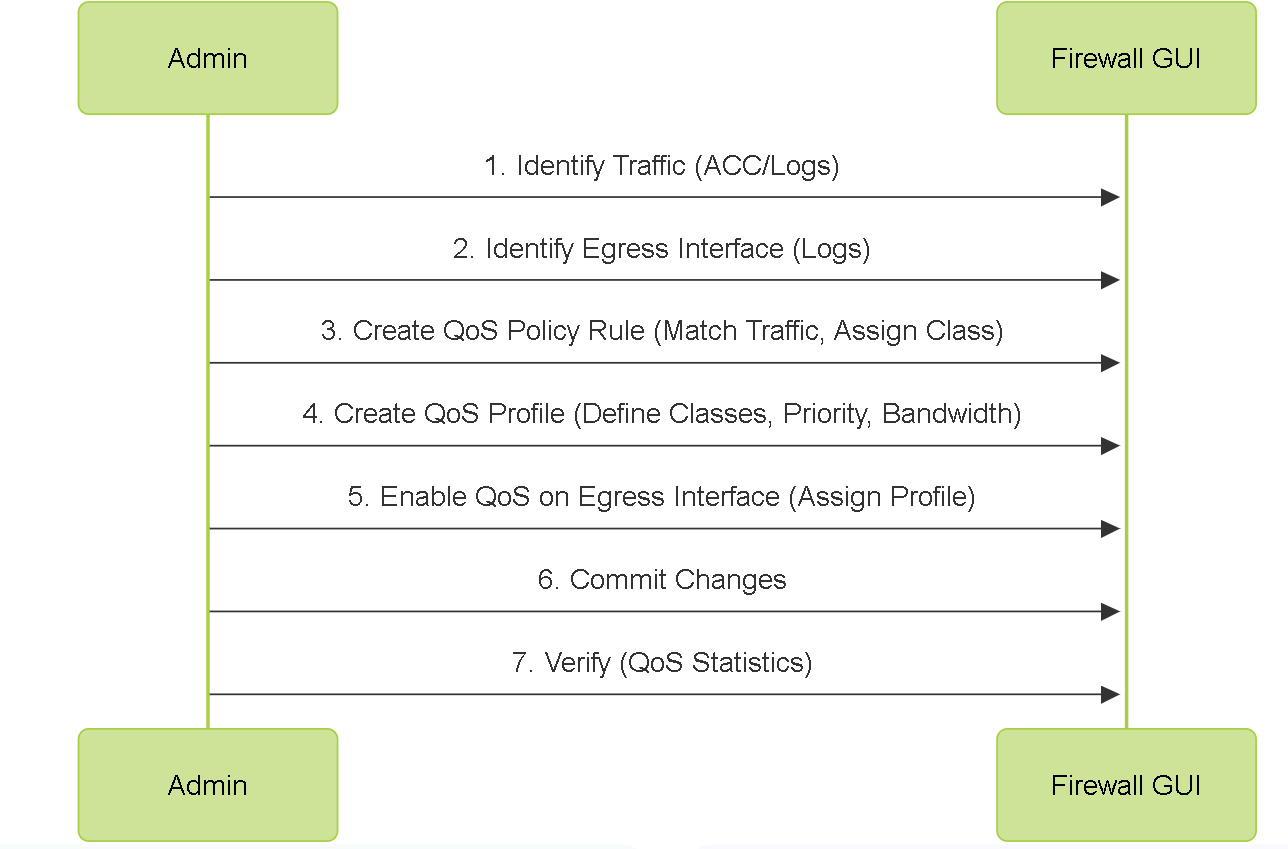
Sequence diagram showing the typical administrative steps for configuring QoS.
QoS Policy Rule Logic
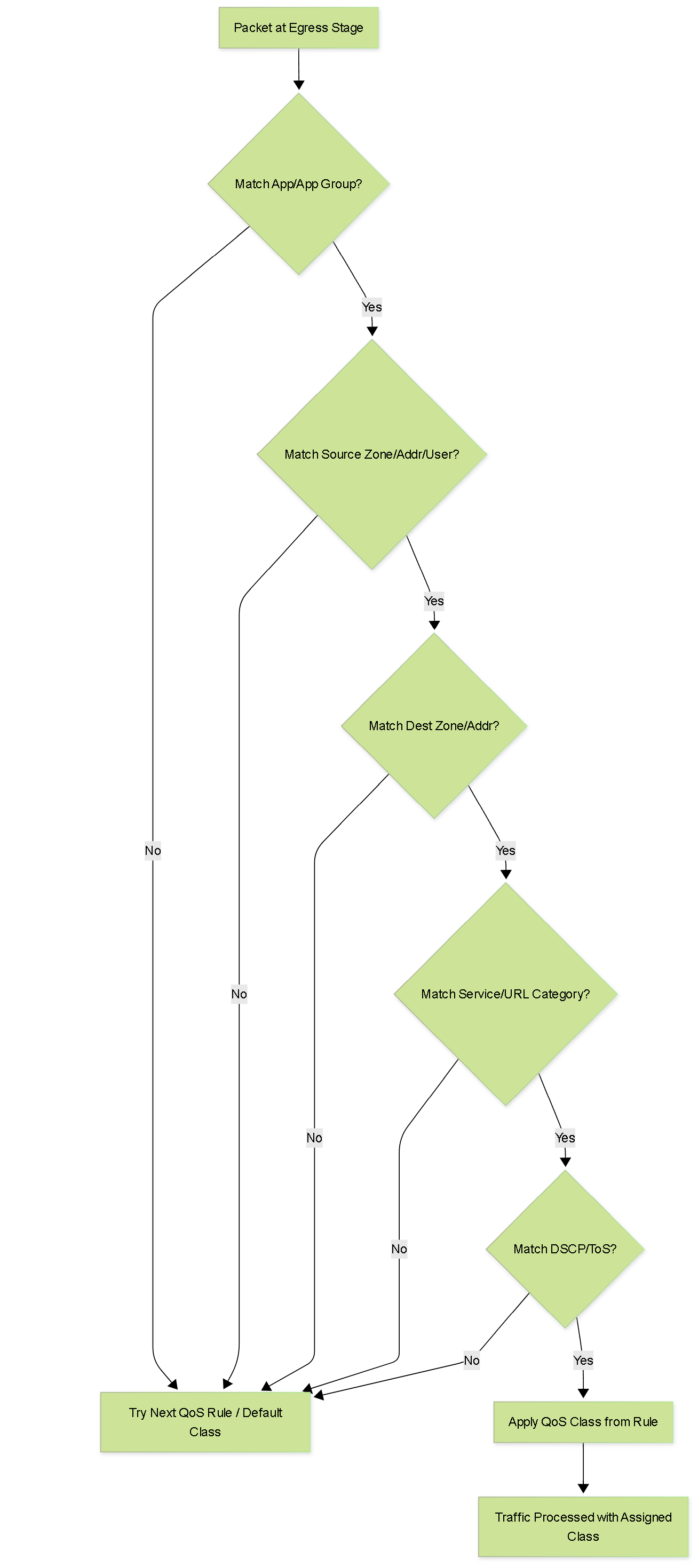
Flowchart detailing the matching logic within a QoS policy rule.
DSCP-based QoS and Marking Flow
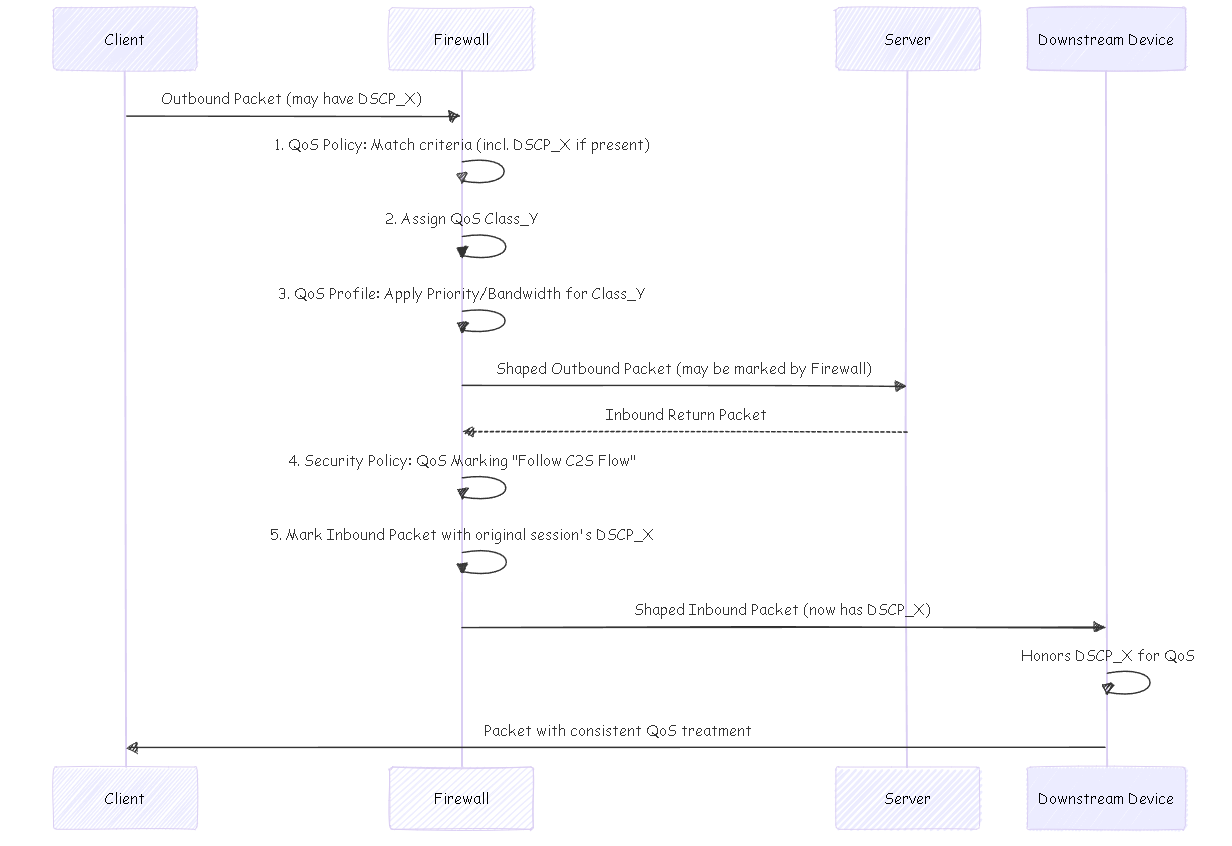
Sequence diagram illustrating how DSCP values are honored and applied for end-to-end QoS.
PCNSE Exam Focus for QoS
Quality of Service is an important topic for the PCNSE exam. Focus on these key areas:
- Core Components: Understand the distinct roles and interaction of QoS Profiles, QoS Policies, and QoS Egress Interfaces.
-
Traffic Flow and Enforcement:
- QoS is always enforced at the egress interface .
- QoS policy is evaluated after Security policy and NAT.
- QoS policy matching uses original packet information (pre-NAT source IP/zone, post-NAT destination zone). Do not use post-NAT source IP in QoS policies.
-
Bandwidth Management:
- Differentiate between Egress Max (hard limit, drops excess) and Egress Guaranteed (minimum assured, unused is available).
- The sum of Egress Guaranteed bandwidth for classes in a profile should not exceed the Egress Max on the interface.
- Default QoS class for unmatched traffic is typically Class 4.
- Application and User-Based QoS: Know how App-ID and User-ID integrate with QoS to provide granular control.
-
DSCP Marking and Honoring:
- How to match traffic based on DSCP values in QoS Policy.
- How to mark traffic using the "Follow Client-to-Server Flow" option in Security Policy actions.
- QoS/DSCP cannot be applied to SSL Forward Proxy, SSL Inbound Inspection, or SSH Proxy traffic.
- Clear Text vs. Tunneled Traffic: Understand that QoS can be applied differently to these traffic types, including per-tunnel interface QoS.
-
Lockless QoS:
- Purpose: Improved performance for high-bandwidth QoS.
- A reboot is required to enable/disable.
- Awareness of supported platforms and potential limitations (e.g., LAG throughput).
-
QoS for Virtual Systems (VSYS):
- QoS is configured independently per VSYS.
- QoS Policies must use source/destination zones for proper VSYS scoping.
- Verification: Know where to check QoS statistics (Network > QoS > Statistics). Hardware adjustment factor in reported stats.
- Congestion Avoidance: PAN-OS uses WRED (Weighted Random Early Detection).
Common Gotchas:
Egress Interface Identification: Misidentifying the egress interface is a common mistake. Always trace the specific traffic flow you want to control. Download traffic egresses an internal interface; upload traffic egresses an external interface.
Pre-NAT vs. Post-NAT: Using post-NAT source IP addresses in QoS policies will lead to match failures. QoS policies use pre-NAT source details.
SSL-Decrypted Traffic Limitations: QoS and DSCP marking do not apply to certain types of SSL-decrypted/proxied traffic.
Order of Operations: Remember Security Policy & NAT -> QoS Policy Evaluation -> QoS Enforcement at Egress.