Palo Alto Networks: Mastering QoS and Security Policy Interaction for PCNSE Success
Effective network performance and security are paramount in modern IT infrastructures. Palo Alto Networks Next-Generation Firewalls (NGFWs) provide robust Quality of Service (QoS) capabilities that, when intricately woven with Security Policies, allow for granular control over application traffic. This guide offers an in-depth exploration of this interaction, crucial for day-to-day network administration and indispensable knowledge for the Palo Alto Networks Certified Network Security Engineer (PCNSE) certification.
Core Concepts: QoS and Security Policies in PAN-OS
Quality of Service (QoS) in Palo Alto Networks
QoS on Palo Alto Networks firewalls is designed to manage network bandwidth and prioritize traffic to ensure that critical applications receive the necessary resources, especially during periods of congestion. PAN-OS implements QoS through QoS Profiles and their application to network interfaces and traffic flows.
A QoS Profile defines how traffic belonging to different QoS Classes should be treated. PAN-OS supports eight standard QoS classes:
- Class 1 (Highest Priority): Typically reserved for network control, routing updates, or extremely sensitive real-time traffic.
- Class 2: Often used for voice (VoIP) traffic.
- Class 3: Suitable for interactive video or other high-priority business applications.
- Class 4: Common for critical data applications, enterprise applications (e.g., SAP, Oracle).
- Class 5: General business applications, web browsing.
- Class 6: Less critical applications, large file transfers (non-urgent).
- Class 7: Low-priority traffic, recreational applications.
- Class 8 (Lowest Priority - Default): Best-effort traffic; any traffic not explicitly classified falls into this class by default.
Within a QoS Profile, configured under Network > QoS Profile , you can specify for each class:
- Guaranteed Bandwidth: The minimum amount of bandwidth allocated to this class when the link is congested. This is a crucial parameter for ensuring performance for critical applications.
- Maximum Bandwidth: The upper limit of bandwidth this class can consume, preventing it from starving other classes.
- Priority: Determines the order in which queues are serviced. Higher priority classes are serviced before lower priority ones.
- DSCP/ToS Marking (Optional): The firewall can mark IP packet headers (DSCP or IP Precedence) to signal desired QoS treatment to downstream network devices. This is configured under Network > Network Profiles > QoS Profile > [Profile Name] > Class Bandwidth Settings and then selecting a QoS Policy for advanced marking, or implicitly by class priority. Palo Alto Networks standard QoS Profiles primarily use priority and bandwidth settings; explicit DSCP marking is more tied to QoS Policy objects (under Policies > QoS).
Security Policies: The Gatekeepers of Traffic
Security Policies are the foundational elements of traffic control in PAN-OS. Configured under Policies > Security , they are evaluated sequentially from top to bottom. The first rule that matches the traffic's parameters (source/destination zone, address, user, application, service, etc.) is applied, and no further rules are processed for that session.
The action defined in the matching Security Policy rule (e.g., allow, deny, drop) determines the fate of the traffic. Crucially for QoS, the Security Policy rule is also where you associate specific application flows with a QoS Profile.
The Crucial Link: Security Policies Driving QoS
The interaction between Security Policies and QoS in Palo Alto Networks firewalls is direct and deterministic: QoS treatment is assigned based on the Security Policy rule that permits the traffic.
Here's the typical flow:
- A new session's first packet arrives at an ingress interface.
- The firewall performs a Security Policy lookup.
- App-ID identifies the application (potentially over multiple packets).
- User-ID (if configured) identifies the user.
- If a matching Security Policy rule is found that permits the traffic, the firewall checks the rule's Action tab .
- If a QoS Profile is specified in the Action tab of that Security Policy rule, the session is "tagged" or marked with that QoS Profile and assigned to the corresponding QoS Class defined within that profile.
- As traffic for this session egresses an interface where QoS is enabled, the firewall enforces the bandwidth guarantees, limits, and priority defined for its assigned QoS Class.
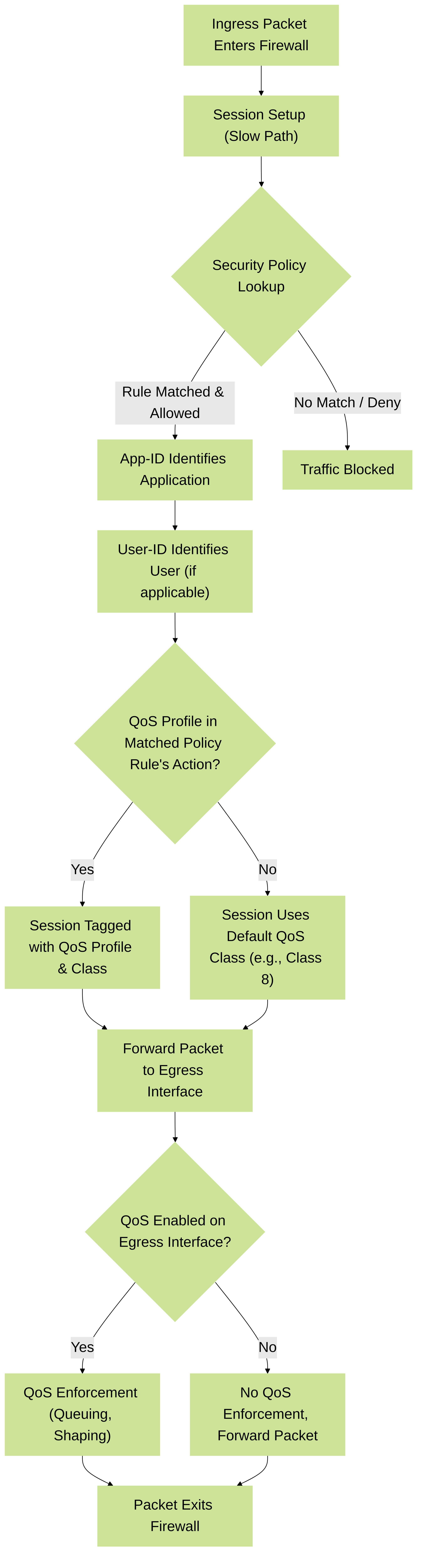
Detailed packet flow illustrating Security Policy lookup and QoS profile assignment in Palo Alto Networks PAN-OS.
Key Implications of this Interaction:
- Policy Order is King: The most critical aspect. A specific Security Policy rule intended to provide special QoS treatment (e.g., for VoIP identified by App-ID `sip` and `rtp`) MUST be placed above any broader rules that might also match the VoIP traffic but have a different (or no) QoS profile. If VoIP traffic hits a general "allow web and SSL" rule first, it will get the QoS profile of that general rule.
- App-ID's Role: Accurate application identification by App-ID is vital. If App-ID misclassifies an application, the traffic might match an unintended Security Policy rule, leading to incorrect QoS treatment.
- Egress Enforcement: QoS marking happens based on the policy match, but the actual bandwidth management (queuing, shaping, policing) is performed on the egress interface where QoS has been explicitly enabled and configured. This is done under Network > Interfaces > [Interface Type] > [Interface Name] > QoS tab . Here, you apply an interface-level QoS profile which defines the queue structure for that interface. The session's QoS class (from the security policy) determines which of these queues it uses.
- Default QoS Treatment: If a session matches a Security Policy rule that does *not* specify a QoS profile, or if no Security Policy rule explicitly allows the traffic and it falls to an implicit allow (not recommended) or an intra-zone default allow, the traffic will typically be assigned to the default QoS class (Class 8, unless the interface's default QoS profile specifies otherwise).
Table: Key Palo Alto Networks Components in QoS Implementation
| Component | Palo Alto Networks Configuration Path | Primary Role in QoS |
|---|---|---|
| QoS Profile | Network > QoS Profile | Defines QoS classes, bandwidth (guaranteed/max), and priority for each class. This is the "template" for QoS treatment. |
| Security Policy Rule | Policies > Security > [Rule Name] > Action tab | Assigns a specific QoS Profile (and thus a QoS class via profile settings) to traffic matching the rule's criteria (App-ID, User-ID, zones, addresses, services). |
| Interface QoS Settings | Network > Interfaces > [Interface Name] > QoS tab | Enables QoS on the physical/logical egress interface. An interface-level QoS Profile is applied here to establish the queue structure and default class behaviors for traffic exiting this interface. |
| App-ID | N/A (Core engine feature) | Accurately identifies applications, enabling granular Security Policy matching which is the basis for QoS profile assignment. |
| QoS Policy (Advanced) | Policies > QoS | Used for more complex scenarios, often involving differentiated services based on DSCP markings, or for Hierarchical QoS (HQoS). Security Policy-based QoS is more common for standard application prioritization. |
Configuring Policy-Based QoS: A Step-by-Step Overview
1. Define QoS Profiles: * Navigate to Network > QoS Profile . * Create a new profile (e.g., `VoIP-Priority-Profile`). * For each relevant class (e.g., Class 2 for VoIP), set Guaranteed Bandwidth (e.g., 2 Mbps), Maximum Bandwidth (e.g., 5 Mbps), and Priority (e.g., high). * Configure other classes as needed for other types of traffic. 2. Enable QoS on Egress Interface(s): * Navigate to Network > Interfaces . Select the relevant egress interface. * Go to the QoS tab . * Check "Enable QoS". * Apply a QoS Profile to the interface (e.g., a default profile or one that defines the overall queue structure for that link). This establishes the hardware queues and their basic parameters. The important part for policy-based QoS is that QoS is *enabled*. The Security Policy will then direct specific traffic to specific classes within this enabled QoS framework. * (Optional) For subinterfaces, QoS is typically enabled on the physical interface, and subinterfaces inherit this. Specific QoS settings can be applied per subinterface. 3. Assign QoS Profile in Security Policy Rules: * Navigate to Policies > Security . * Create or edit a Security Policy rule for the traffic you want to prioritize (e.g., a rule allowing `sip` and `rtp` applications from `Trust` zone to `Untrust` zone for VoIP). * In the rule's Action tab , under "QoS Marking," select the QoS Profile you created (e.g., `VoIP-Priority-Profile`). * Specify the QoS Class from that profile to apply (e.g., `class2`). * Ensure this specific rule is ordered correctly (higher than broader rules). 4. Commit Changes: * Commit the configuration to the firewall.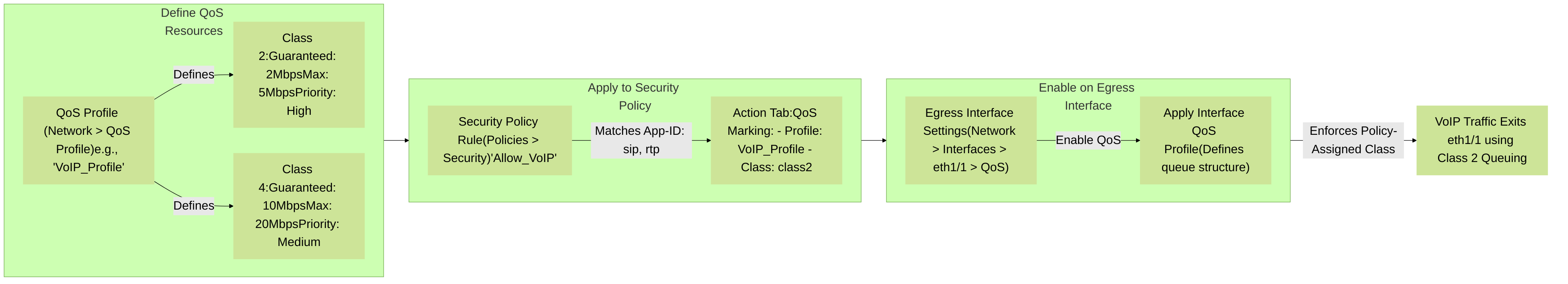
Palo Alto Networks configuration linkage: QoS Profile definition, assignment in Security Policy, and enablement on the egress interface.
Illustrative Examples (Mermaid Diagrams Expanded)
Sequence Diagram: Packet Processing & QoS (PAN-OS Detail)
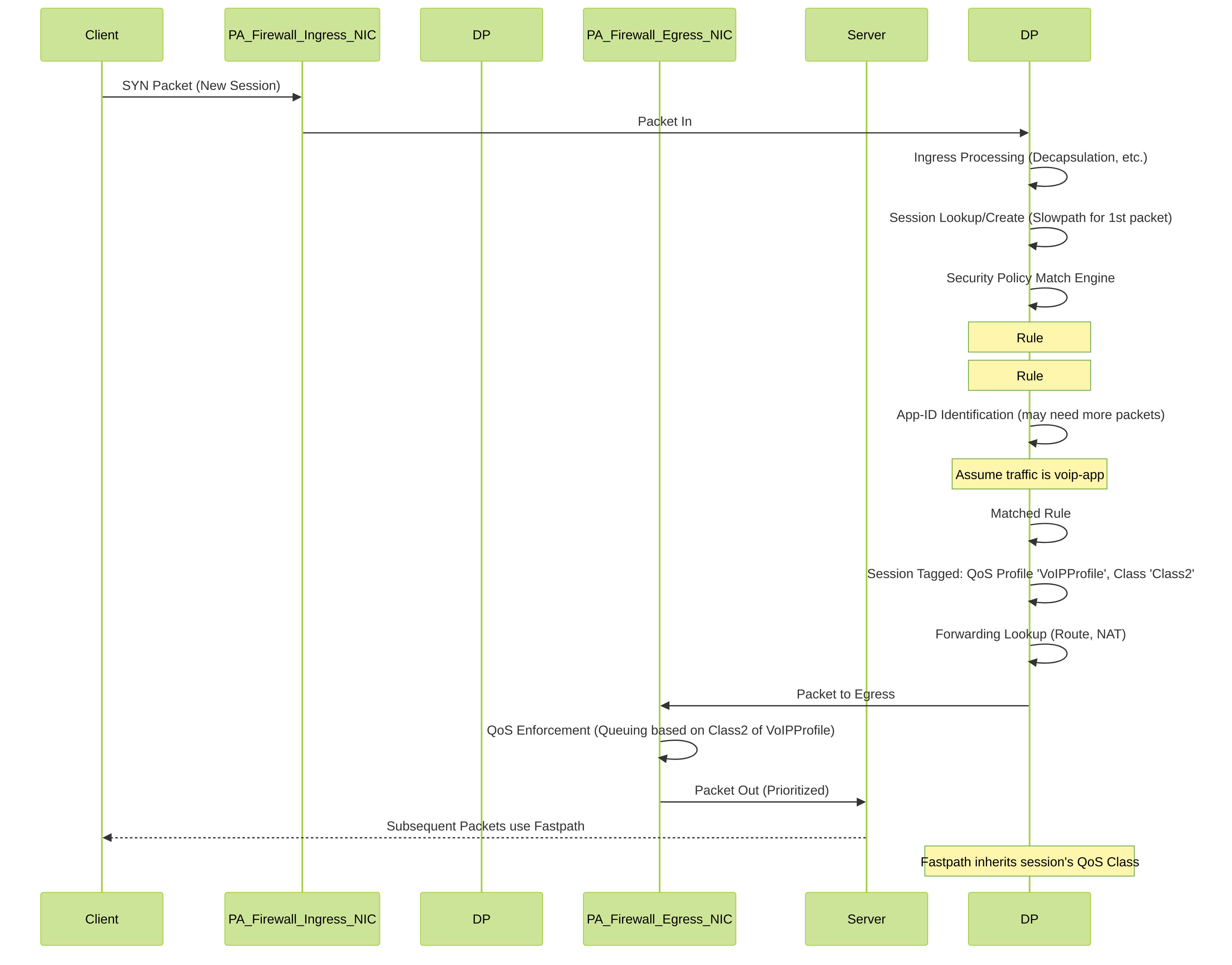
Detailed sequence showing PAN-OS packet processing for a new session, highlighting Security Policy match, App-ID, and QoS profile assignment leading to egress QoS enforcement.
Flowchart: Security Policy Decision & QoS (Refined for PAN-OS)
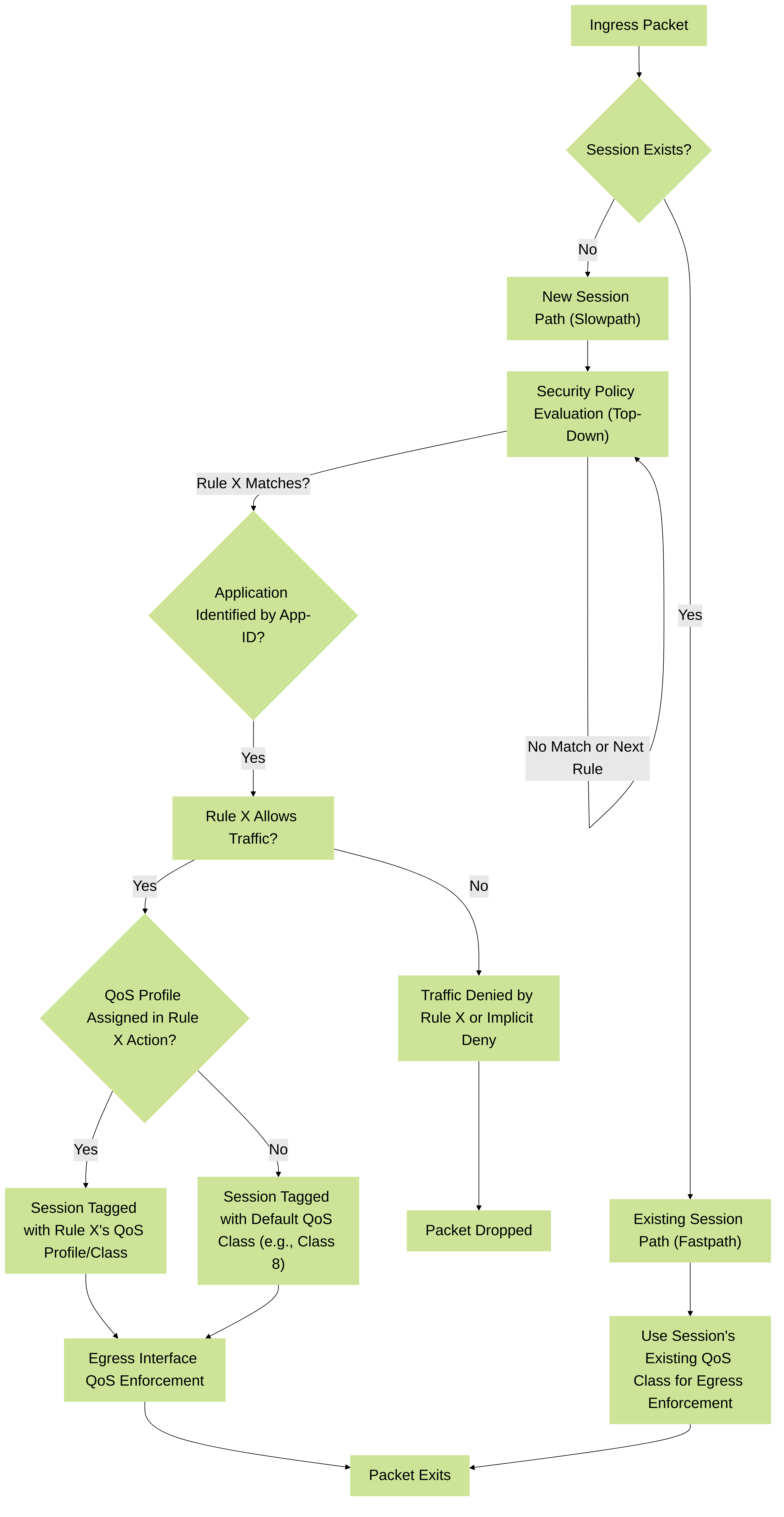
Refined flowchart for PAN-OS illustrating Security Policy decision points, App-ID influence, and QoS assignment for both new and existing sessions.
State Diagram: Session State & QoS Relevance (PAN-OS Context)
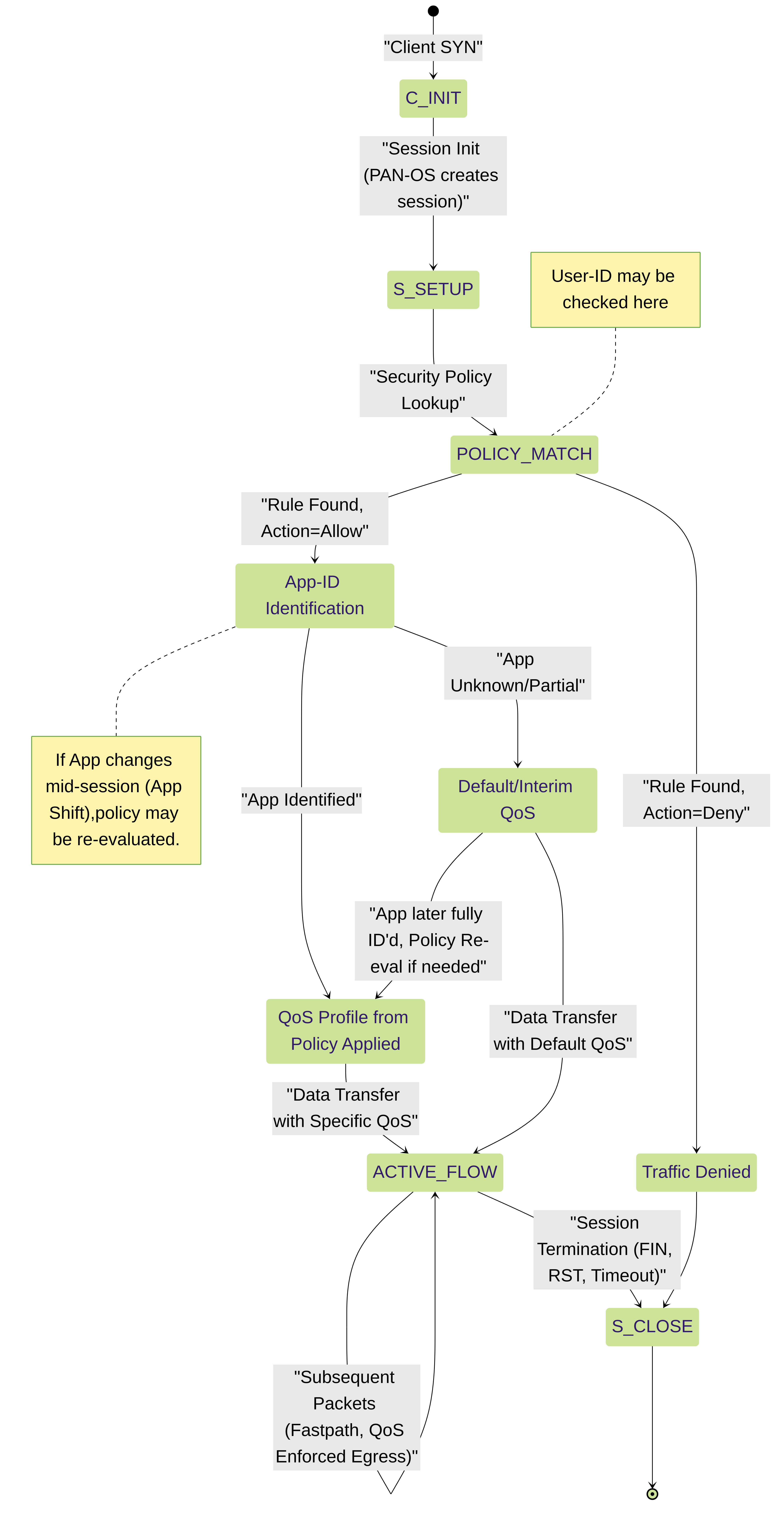
PAN-OS session lifecycle state diagram emphasizing points of Security Policy match, App-ID, and QoS profile assignment.
PCNSE Focus: Key Considerations, Gotchas, and Advanced Topics
Key PCNSE Concepts for QoS & Security Policies
- Policy Rule Order Supremacy: Hammer this home. Specific rules (e.g., for `ms-rpd` with high QoS) above general rules (e.g., allow `ssl` with standard QoS).
- QoS Profile Components: Know what Guaranteed Bandwidth, Maximum Bandwidth, and Priority mean and how they affect traffic. Understand the 8 PAN-OS QoS classes.
- Interface QoS Enablement: Traffic is only QoS-managed if QoS is enabled on the egress interface. The interface QoS profile sets up the queues.
- Security Policy Action Tab: This is where the QoS Profile and Class are explicitly assigned to application flows.
- App-ID and QoS: App-ID's accuracy is fundamental to correct QoS policy application. If `web-browsing` is actually `salesforce`, QoS may be wrong.
- Verification and Monitoring: Know the CLI commands (`show qos interface`, `test security-policy-match`, `show session id`) and GUI locations (ACC, Monitor tab logs) to check QoS.
- Clear Text vs. Tunneled Traffic: QoS can be applied to traffic inside tunnels (e.g., GlobalProtect, IPsec). Security policies would match traffic destined for or emerging from tunnel interfaces. The QoS profile would be applied based on the de-capsulated (inner) traffic characteristics if policies are set up to inspect it.
Common Palo Alto Networks Gotchas
-
Incorrect Security Policy Match:
The #1 culprit. Traffic hits a broader, earlier rule. Use
test security-policy-matchreligiously. - QoS Not Enabled on Egress Interface: As stated, essential. Double-check Network > Interfaces > [Interface] > QoS tab .
-
QoS Profile Misconfiguration:
- Guaranteed bandwidth exceeding interface capacity.
- Max bandwidth set too low for an application's needs.
- Incorrect priority for classes.
- Interface vs. Policy QoS Profile Confusion: The profile on the interface sets up the general queueing mechanism. The profile in the security policy directs specific traffic (e.g., `salesforce`) to a particular class (e.g., `class3`) within that mechanism.
- Default QoS Class Overwhelm: If many applications are not explicitly classified by a security policy with a QoS profile, they all fall into Class 8, potentially overwhelming it and impacting all unprioritized traffic.
- NAT and Egress Interface Determination: Security policy match often uses pre-NAT destination IP and pre-NAT destination zone. However, the actual egress interface (where QoS is enforced) is determined *after* NAT and routing. Ensure your QoS-enabled interface is the true final exit point.
- SSL Decryption Impact: If SSL/TLS Decryption is enabled, App-ID (and thus policy matching for QoS) is more accurate as it sees the decrypted application. QoS is applied post-decryption to the clear text traffic.
- Subinterface QoS: When using subinterfaces, QoS is typically configured and enabled on the parent physical interface. The subinterfaces share the parent's QoS queuing mechanism. You can apply different QoS treatment to traffic on different subinterfaces by directing their traffic to different QoS classes via security policies.
Hierarchical QoS (HQoS) and QoS Policy Objects
While Security Policy-based QoS is the most common method for application prioritization, PAN-OS also supports more advanced QoS configurations using QoS Policy objects found under Policies > QoS . These are typically used for:
- Hierarchical QoS (HQoS): Allows for multi-level scheduling, often used in service provider environments or complex enterprise networks to provide granular bandwidth allocation to different customers, departments, or services sharing a common link. For example, an outer policy might allocate bandwidth to a department, and inner policies might further divide that department's bandwidth among its applications.
- DSCP-Based Classification and Re-marking: QoS Policy rules can match traffic based on existing DSCP markings and then re-mark packets or assign them to specific QoS classes. This is useful for integrating with existing QoS schemes in the network.
- Per-Session Bandwidth Control (Advanced): While QoS Profiles define class-based limits, more granular per-session limits might be part of advanced QoS policy configurations in some specific PAN-OS versions or scenarios.
For most enterprise use cases covered by PCNSE, assigning a QoS Profile via the Security Policy is the primary method. However, being aware of dedicated QoS Policies for advanced scenarios is beneficial.
Debugging QoS with PAN-OS CLI Commands
The CLI is invaluable for verifying and troubleshooting QoS.
> show qos interface <interface_name>
Example:
> show qos interface ethernet1/1
Displays the QoS profile applied to the interface, current bandwidth usage (bps, pps) per class, queue depths, and crucially, dropped packets per class due to QoS limits. This is your primary command for checking QoS enforcement health.
ethernet1/1 (Max BW: 1000 Mbps, Path: /hw:ethernet1_1/qos, Qos RUNNING) QoS Profile: default (id 10001) Class BW Guaranteed BW Max Priority Pkt Queued Pkt Dropped Throughput(Kbps) 1 0 1000000 real-time 0 0 0 2 0 1000000 high 0 0 0 3 0 1000000 high 0 0 0 4 0 1000000 medium 5 1205 15000 5 0 1000000 medium 0 0 8000 6 0 1000000 low 0 0 0 7 0 1000000 low 0 0 0 8 0 1000000 low 150 85000 450000
> test security-policy-match source <ip> destination <ip> protocol <num> destination-port <port> application <app> from <zone> to <zone>
Example:
> test security-policy-match from L3-Trust to L3-Untrust source 192.168.1.100 destination 8.8.8.8 protocol 6 destination-port 443 application ssl
Indicates which Security Policy rule the specified traffic flow will match. Essential to confirm if the traffic is hitting the rule with the intended QoS profile. The output will show the rule name and ID.
> show session id <session_id>
Displays detailed information about a specific session, including the
QoS class
it has been assigned. You can find session IDs from
show session all filter ...
.
Session 67890 ... qos node: ethernet1/1, qos profile VoIPQoS, class 2 ...
> show session all filter policy-qos-class <class_number> interface <egress_interface>
Example:
> show session all filter policy-qos-class 2 interface ethernet1/1
Shows all active sessions that have been assigned to a specific QoS class (e.g., class 2) by a security policy and are egressing a particular interface. Useful for seeing what traffic is currently in a specific class.
> show counter global filter aspect qos
Displays global QoS-related counters, which can provide insights into overall QoS processing and potential issues at a high level.
> clear qos statistics interface <interface_name>
Clears the QoS statistics for the specified interface, allowing you to observe fresh counts for troubleshooting.
Advanced Debugging (Use with EXTREME caution in production):
> debug dataplane packet-diag set filter match source <ip> destination <ip>
> debug dataplane packet-diag set filter on
> debug dataplane packet-diag set log feature flow qos on
(or other relevant features)
> show counter global filter packet_based yes delta yes
(to see packet processing counters)
> less mp-log DpPdkQosStats.log
(or other relevant debug logs like `less mp-log flow_basic.log` after enabling basic flow debug)
These commands can generate voluminous output and significantly impact performance. They should only be used under guidance from Palo Alto Networks support or by experienced engineers in a controlled environment. Always remember to turn off debugging:
debug dataplane packet-diag set filter off
.
Troubleshooting QoS - A Decision Tree Approach
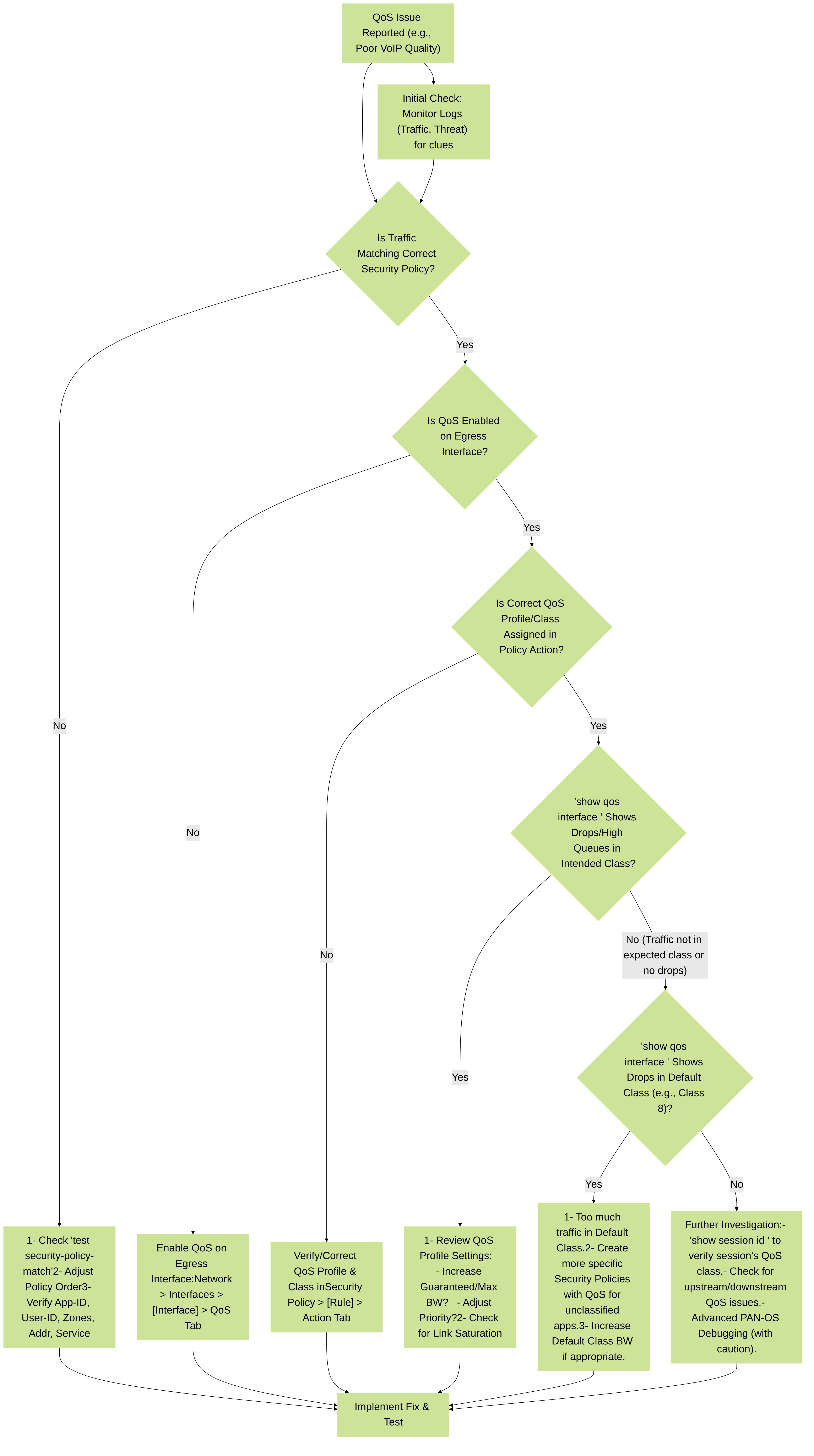
A decision tree for troubleshooting common QoS issues on Palo Alto Networks firewalls.
Conclusion
The interaction between Security Policies and QoS is a cornerstone of effective traffic management on Palo Alto Networks NGFWs. By correctly identifying applications with App-ID, structuring Security Policies logically, and defining appropriate QoS Profiles, network administrators can ensure that critical applications receive the network resources they need. For PCNSE candidates, a deep understanding of this interplay, including configuration, verification, and troubleshooting, is essential for exam success and for deploying robust, high-performing secure networks.