Introduction to Dynamic Routing on Palo Alto Networks Firewalls
Palo Alto Networks Next-Generation Firewalls (NGFWs) are capable of participating in complex network environments by supporting various dynamic routing protocols. This allows the firewall to learn about network topology changes automatically and make intelligent forwarding decisions without manual static route configuration.
Dynamic routing is essential for scalability, redundancy, and efficient traffic flow in modern networks. PAN-OS, the operating system powering these firewalls, integrates routing capabilities within its Virtual Router (VR) or Logical Router (LR, with the Advanced Routing Engine) framework.
This document explores the dynamic routing protocols supported by PAN-OS, the concept of route redistribution between protocols, and common administrative tasks associated with managing routing on the firewall.
Virtual Routers (VRs) / Logical Routers (LRs)
The foundation of routing in PAN-OS is the Virtual Router (VR) or, with the Advanced Routing Engine, the Logical Router (LR). Think of a VR/LR as a virtual routing instance within the firewall, similar to a VRF (Virtual Routing and Forwarding) instance on traditional routers.
Key aspects of VRs/LRs include:
- Each Layer 3 interface (Ethernet, VLAN, Loopback, Tunnel) must belong to a single VR/LR.
- Each VR/LR maintains its own independent routing table (RIB - Routing Information Base) and forwarding table (FIB - Forwarding Information Base). Routes are generally not shared between VRs/LRs unless explicitly configured (e.g., using inter-VR/LR routing techniques).
- Multiple routing protocols (BGP, OSPF, RIP) and static routes can be configured within a single VR/LR.
- The firewall determines the destination zone for traffic based on the outgoing interface identified by the VR/LR's route lookup.
- Routing between VRs/LRs is possible, often using loopback interfaces and iBGP peering or static routes with a "next-vr" hop type.
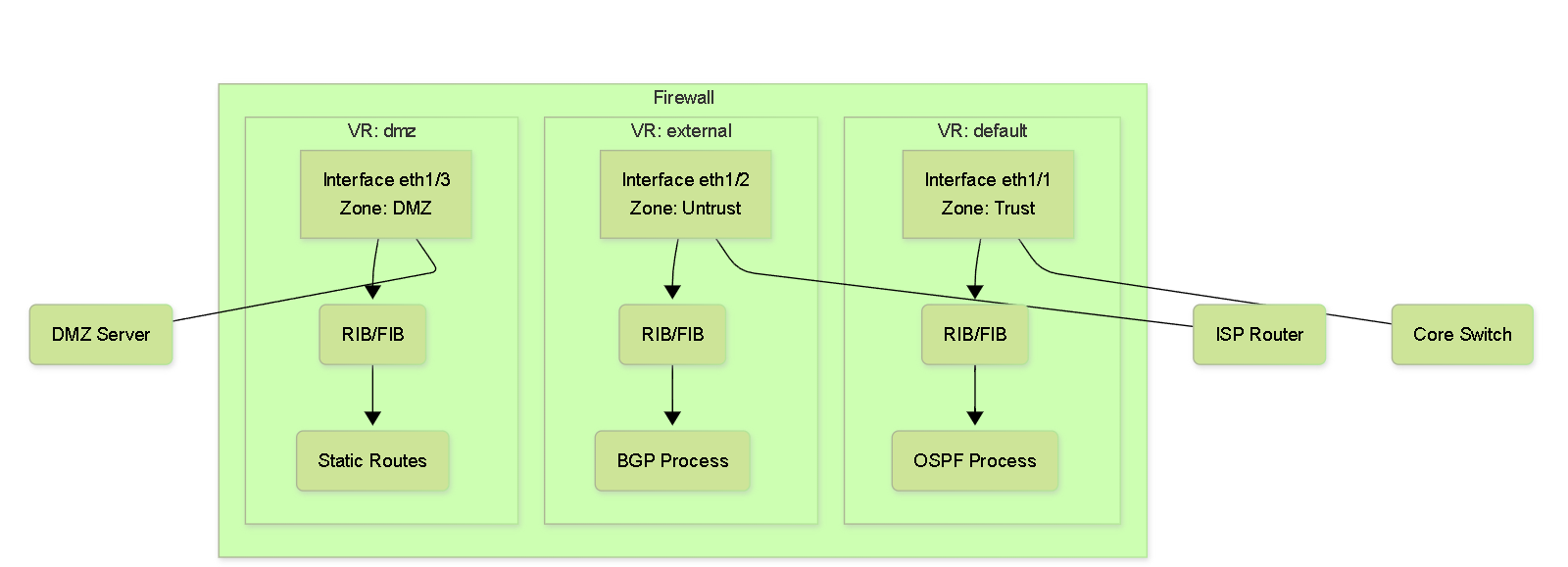
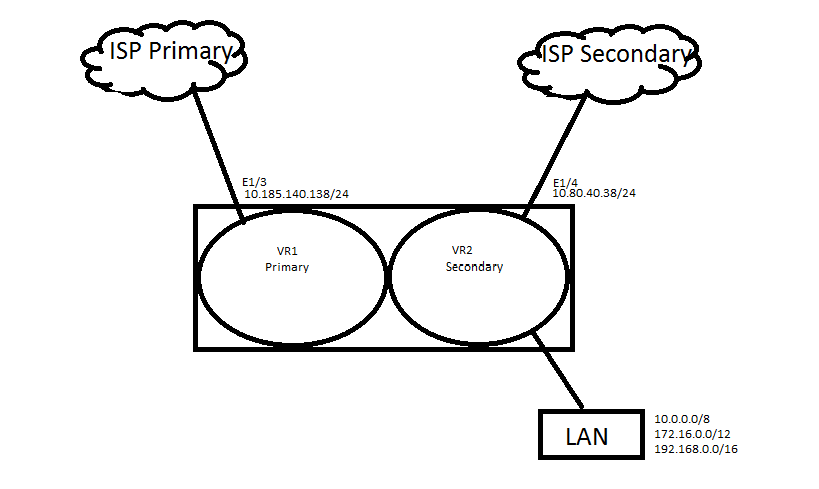
Simplified illustration of multiple Virtual Routers within a Palo Alto Networks firewall, each with its own interfaces, zones, routing table, and potentially different routing protocols.
Border Gateway Protocol (BGP)
BGP (specifically BGP4) is the de facto standard inter-Autonomous System (AS) routing protocol used on the internet. Palo Alto Networks firewalls support BGP, allowing them to peer with ISP routers or other BGP speakers in an enterprise environment.
Key Characteristics & Configuration Points:
- Protocol: BGP4.
- Transport: Uses TCP port 179 for neighbor communication.
- Peering Types: Supports both eBGP (External BGP, between different AS numbers) and iBGP (Internal BGP, within the same AS). Confederation support might also be available depending on the PAN-OS version and engine.
- Configuration Hierarchy: Configured within a Virtual Router/Logical Router. Key elements include enabling BGP, setting the Router ID and local AS number, defining Peer Groups, and configuring individual Peers within those groups.
- Peer Groups: Templates to apply common settings (like remote AS, timers, address families, route reflection options) to multiple BGP neighbors.
- Neighbor Adjacency: BGP peers must be manually configured; there's no automatic discovery.
- Path Attributes: Supports standard BGP path attributes (AS_PATH, NEXT_HOP, LOCAL_PREF, MED, Community, etc.) for influencing route selection and policy.
- Route Advertisement: Requires explicit configuration (Export Rules, Redistribution) to advertise routes into BGP. By default, learned routes might not be installed in the main routing table unless "Install Route" is enabled.
- Security Policy: BGP traffic (TCP/179) must be explicitly allowed by security policies, as it operates over TCP.
- BFD Support: Bidirectional Forwarding Detection (BFD) can be enabled for faster failure detection with BGP peers.
- Advanced Features (Advanced Routing Engine): May include features like route maps, prefix lists, AS path lists, improved convergence, and IPv6 BGP enhancements.
BGP Neighbor States:
BGP neighbors transition through several states during session establishment. Understanding these states is crucial for troubleshooting peering issues.
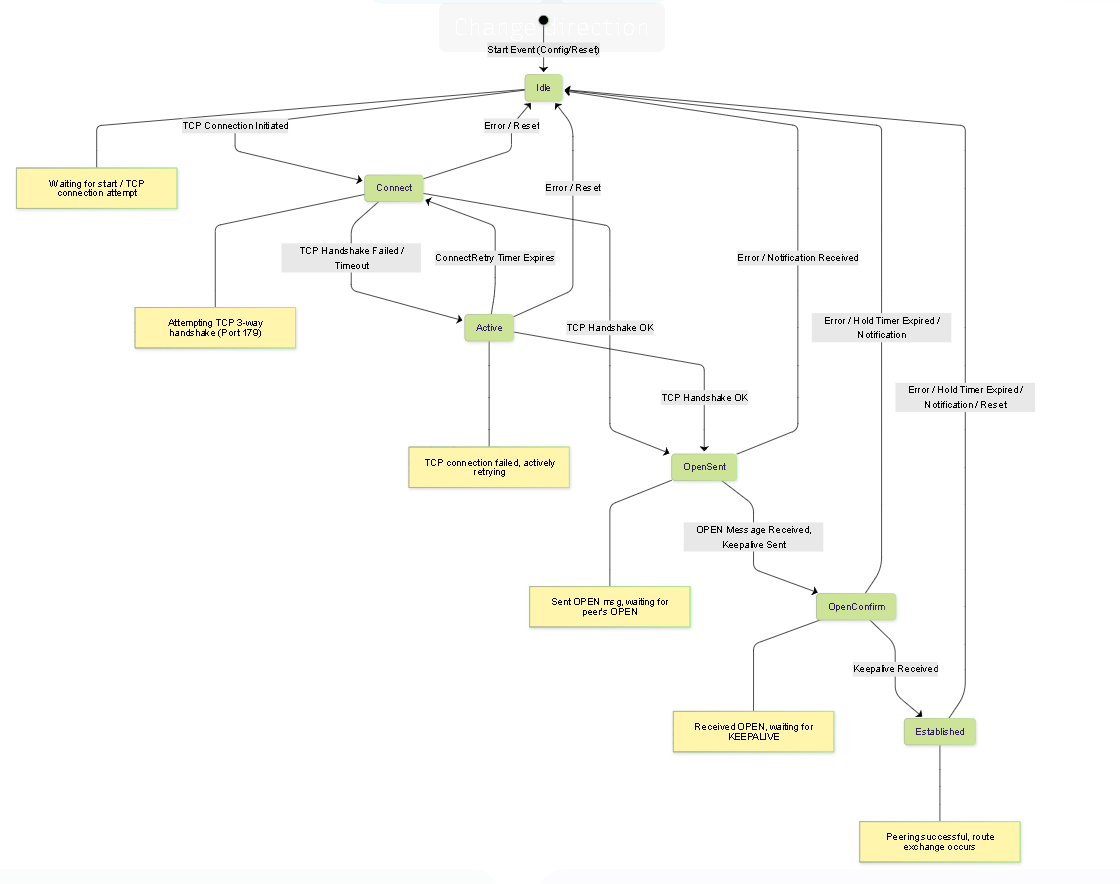
BGP Finite State Machine (FSM) showing neighbor states and transitions.
Common Administrative Tasks:
- Configuring peers and peer groups.
- Defining redistribution profiles and rules to inject routes into BGP.
- Creating export rules to control which routes are advertised to peers.
-
Monitoring neighbor status:
show routing protocol bgp peerorshow advanced-routing bgp neighbor(ARE). -
Viewing received routes (RIB-In):
show routing protocol bgp loc-riborshow advanced-routing bgp rib-in(ARE). -
Viewing advertised routes (RIB-Out):
show routing protocol bgp rib-outorshow advanced-routing bgp rib-out(ARE).
Open Shortest Path First (OSPF)
OSPF is a widely used Interior Gateway Protocol (IGP) based on link-state technology. Palo Alto Networks firewalls support OSPFv2 (for IPv4) and OSPFv3 (for IPv6), allowing them to integrate seamlessly into OSPF routing domains.
Key Characteristics & Configuration Points:
- Protocol Versions: OSPFv2 (IPv4) and OSPFv3 (IPv6). (Note: OSPFv3 support might require the Advanced Routing Engine).
- Protocol Type: Link-State. Routers build a complete map (LSDB) of the network topology within an area.
- Transport: Uses IP protocol 89 directly. Sends Hellos to multicast addresses (224.0.0.5 for AllSPFRouters, 224.0.0.6 for AllDRouters).
- Configuration Hierarchy: Enabled within a Virtual Router/Logical Router. Key elements include enabling OSPF, setting a unique Router ID, defining Areas, and configuring interfaces to participate in specific areas.
- Areas: Supports standard OSPF area types (Normal/Standard, Stub, NSSA). Area IDs are typically configured in dotted-decimal format (e.g., 0.0.0.0 for the backbone area).
- Interface Configuration: Interfaces are added to specific OSPF areas. Parameters like network type (broadcast, point-to-point), timers (Hello/Dead intervals), cost, and authentication can be configured per interface.
- Neighbor Adjacency: OSPF neighbors are discovered dynamically by exchanging Hello packets on connected links.
- Route Advertisement: Networks are typically advertised using `network` commands (in traditional OSPF) or by enabling OSPF on interfaces. Redistribution is used to inject routes from other protocols or static routes into OSPF.
- Security Policy: Basic neighbor adjacency using multicast Hellos often works without security policies. However, the exchange of Database Description (DBD) packets and Link State Updates (LSUs) might occur using unicast between neighbors, requiring an explicit security policy allowing the 'ospf' application, especially if a default deny rule exists.
- BFD Support: BFD can be enabled for OSPF interfaces for faster link failure detection. BFD is supported with the DR/BDR on broadcast segments and directly with neighbors on point-to-point links. BFD is not supported over OSPF virtual links.
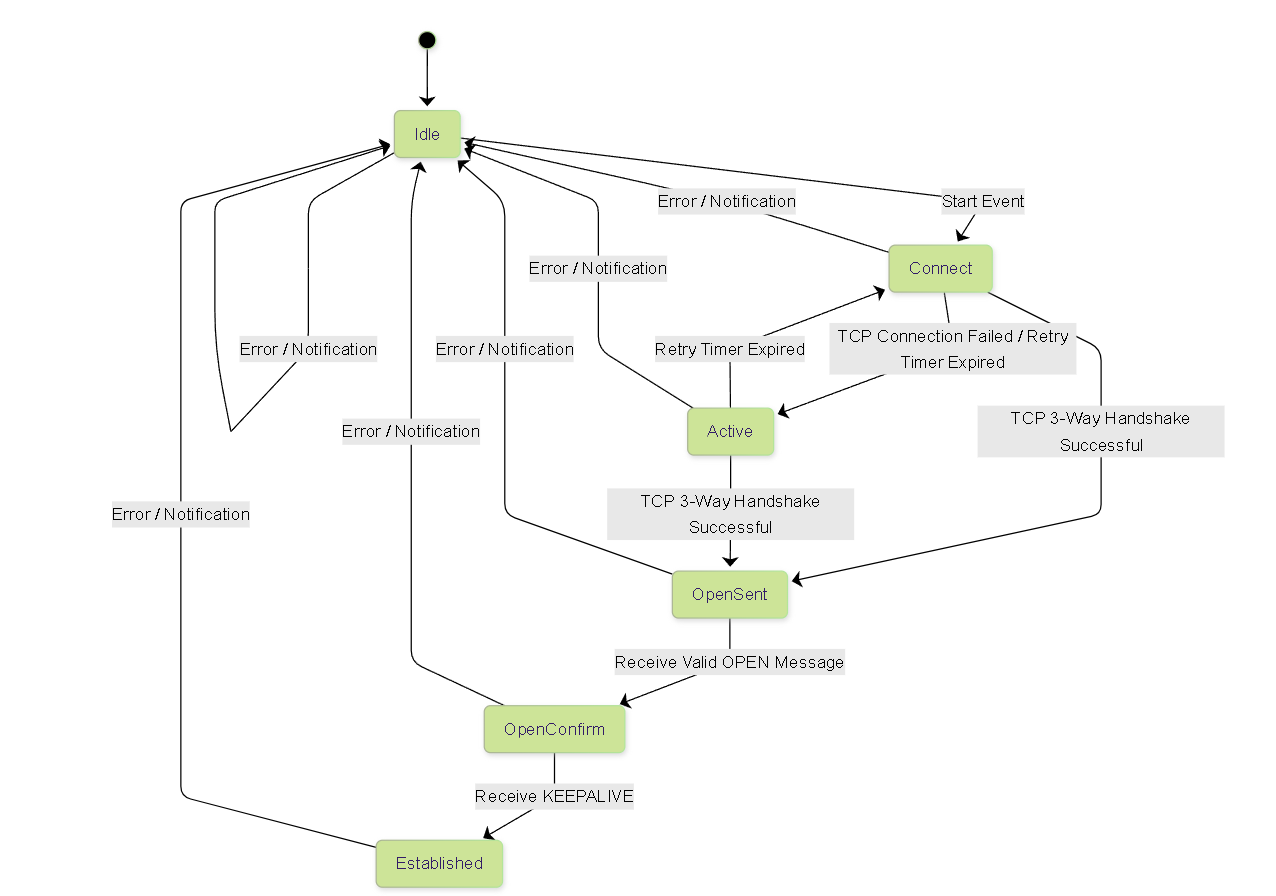
OSPF Neighbor States:
OSPF routers progress through several states to form adjacencies and synchronize their Link-State Databases (LSDBs).
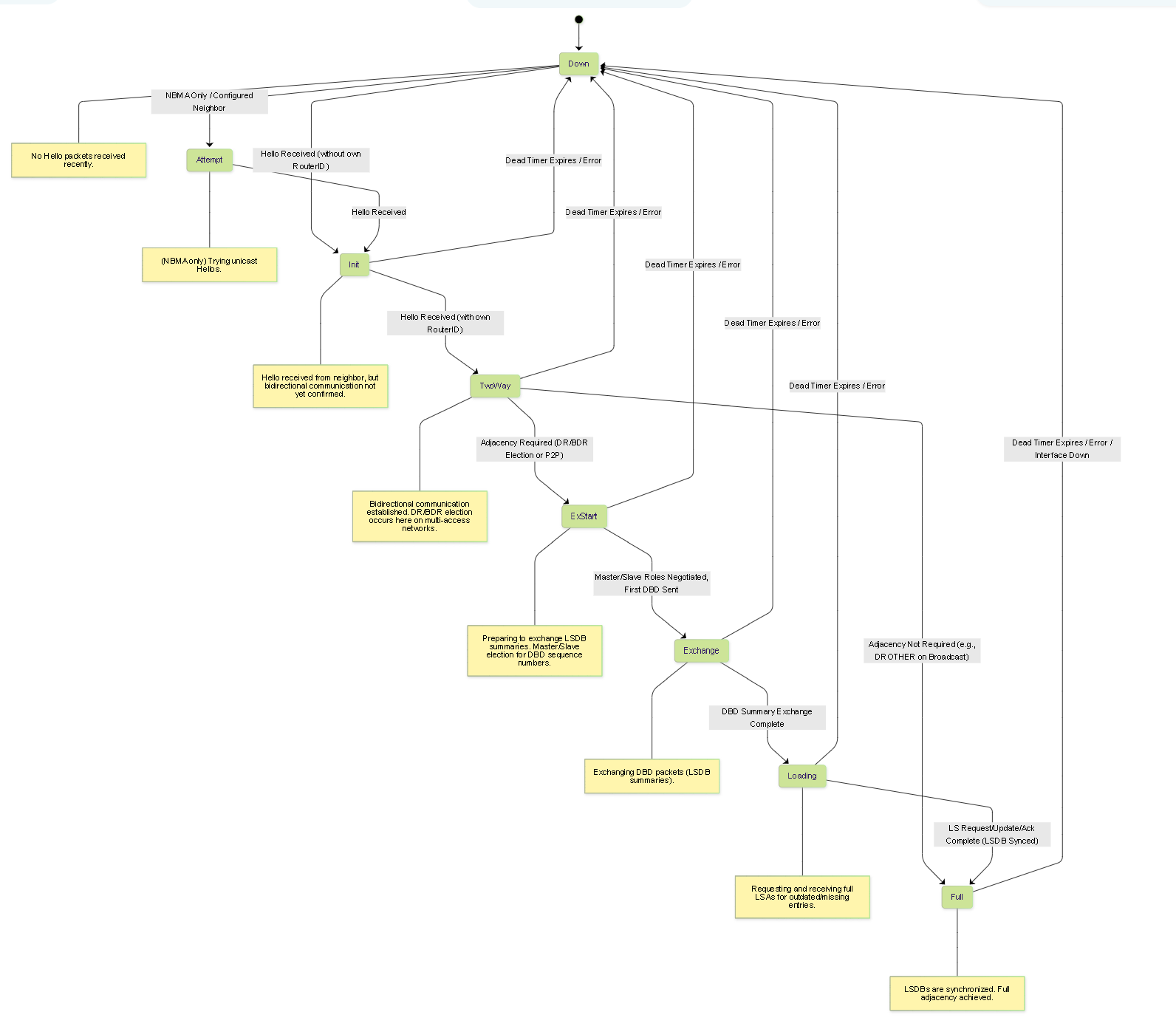
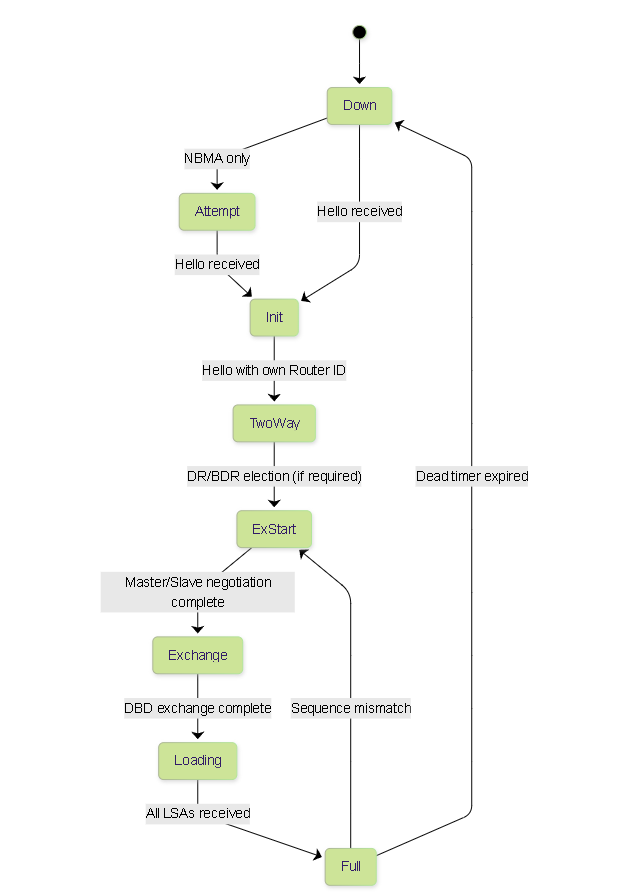
OSPF Neighbor State Machine showing common adjacency formation states.
Common Administrative Tasks:
- Enabling OSPF and configuring the Router ID.
- Defining OSPF areas and their types.
- Assigning interfaces to OSPF areas and configuring interface parameters.
- Configuring route redistribution into OSPF (using Export Rules and Redistribution Profiles).
-
Verifying neighbor status:
show routing protocol ospf neighbororshow advanced-routing ospf neighbor(ARE). -
Viewing the OSPF Link-State Database (LSDB):
show routing protocol ospf lsdborshow advanced-routing ospf lsdb(ARE). -
Viewing OSPF-learned routes in the routing table:
show routing routeorshow advanced-routing route(ARE), filtering for OSPF routes (Flag 'O').
Routing Information Protocol (RIP)
RIP is an older distance-vector routing protocol. Palo Alto Networks firewalls support RIPv2, which offers improvements over RIPv1, such as support for Variable Length Subnet Masks (VLSM) and multicast updates. While less common in modern networks compared to OSPF or BGP, it might be required for interoperability with legacy systems.
Key Characteristics & Configuration Points:
- Protocol Version: RIPv2.
- Protocol Type: Distance-Vector. Uses hop count as the metric.
- Transport: Uses UDP port 520. RIPv2 uses multicast address 224.0.0.9 for updates.
- Configuration Hierarchy: Enabled within a Virtual Router/Logical Router. Configuration involves enabling the protocol and specifying which interfaces will participate.
- Authentication: RIPv2 supports plain-text and MD5 authentication for updates.
- Timers: Relies on timers for updates, route invalidation, and flushing routes.
- Route Advertisement: Typically advertises connected networks on participating interfaces. Redistribution is used to inject routes from other sources.
- Security Policy: RIPv2 uses multicast for its primary communication, so it often works without explicit security policies, similar to OSPF Hellos.
- BFD Support: BFD can be enabled for RIP interfaces for faster failure detection.
- Limitations: Maximum hop count of 15, slower convergence compared to link-state protocols, less granular metric.
Common Administrative Tasks:
- Enabling RIP within a Virtual Router/Logical Router.
- Configuring interfaces to participate in RIP.
- Setting up authentication (if required).
- Configuring route redistribution into or out of RIP.
-
Verifying RIP status and routes:
show routing protocol rip database,show routing protocol rip interface, or corresponding `show advanced-routing rip` commands (ARE).
Route Redistribution
Route redistribution is the process of exchanging routing information between different routing protocols (including static routes and connected interfaces) operating within the same Virtual Router/Logical Router. This is crucial for ensuring end-to-end connectivity in networks that utilize multiple routing methods.
For example, you might learn routes via OSPF from your internal network and need to advertise them to an external partner via BGP, or you might want to advertise a static default route into your OSPF domain.
Configuration Concept (PAN-OS):
Redistribution in PAN-OS typically involves two main components configured within the Virtual Router/Logical Router:
-
Redistribution Profile:
- Defines *which* routes are eligible for redistribution based on their source protocol (e.g., static, connected, OSPF, BGP, RIP) and potentially other filters (e.g., specific prefixes, OSPF path types, BGP communities).
- Each profile has a Priority (1-255, lower value is higher priority). The firewall evaluates profiles in order of priority.
- Specifies an Action : `redist` (redistribute matching routes) or `no-redist` (do not redistribute matching routes, often used to create exceptions).
- Can include filters based on destination prefixes, next-hops, interfaces, OSPF attributes (area, path type, tag), or BGP attributes (community, extended community, AS path - depending on engine/version).
-
Protocol-Specific Export/Redistribution Rules:
- This associates a Redistribution Profile with a *target* routing protocol (the protocol *receiving* the redistributed routes).
- For example, under the BGP configuration, you define "Redist Rules" that reference a specific Redistribution Profile.
- Under OSPF configuration, you use "Export Rules" that reference a Redistribution Profile.
- These rules allow you to set attributes for the redistributed routes as they enter the target protocol (e.g., setting the BGP origin type, metric, local preference, or community; setting the OSPF metric, metric type, or tag).
- You can often enable an option here to specifically allow the redistribution of the default route (0.0.0.0/0).
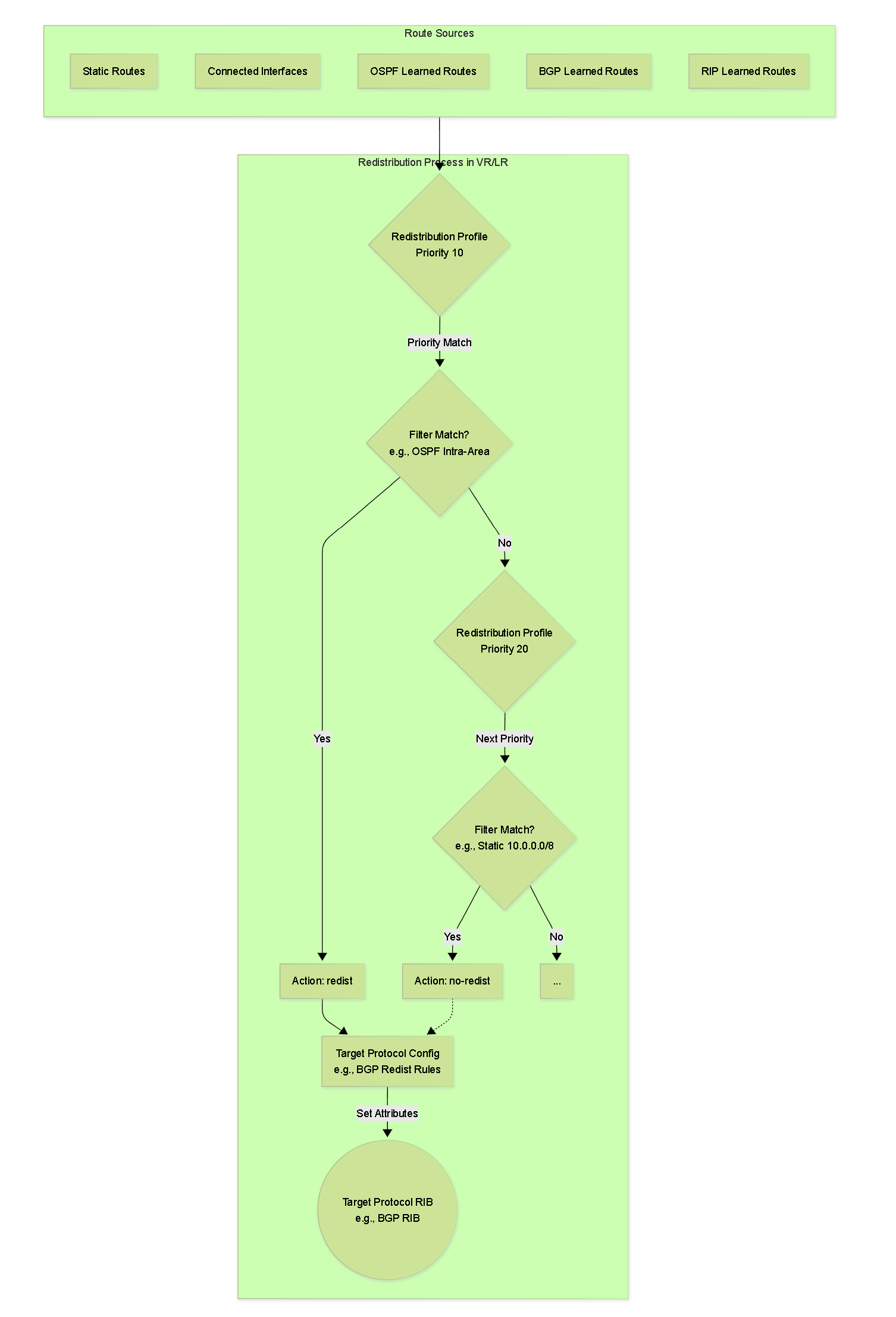
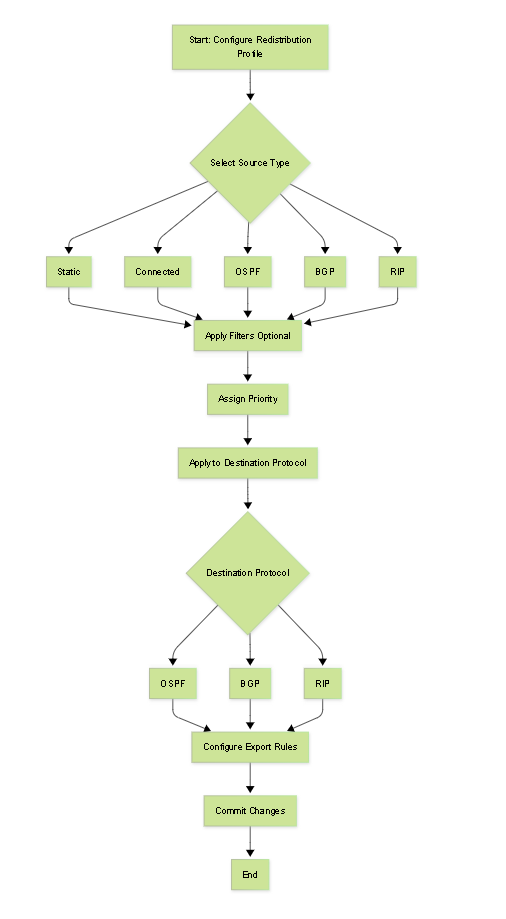
Conceptual flowchart of route redistribution logic in PAN-OS.
Key Considerations:
- Administrative Distance (AD): Redistributed routes inherit the default AD of the protocol they are redistributed *into*, unless modified. Be mindful of AD values to prevent routing loops and ensure preferred paths are chosen.
- Metrics: When redistributing, you often need to define a seed metric for the target protocol, as metrics don't always translate directly between protocols.
- Filtering: Use filters (prefix lists, access lists, route maps in ARE) judiciously to control exactly which routes are redistributed, preventing unnecessary routes from entering a routing domain.
- Routing Loops: Careless redistribution, especially two-way redistribution between protocols with different convergence properties or ADs, can lead to routing loops. Careful planning and filtering are essential.
Administrative Tasks & Verification
Managing dynamic routing involves ongoing monitoring, verification, and troubleshooting. PAN-OS provides both GUI and CLI tools for these tasks.
Viewing Routing Tables:
-
Routing Information Base (RIB):
Contains all routes learned via dynamic protocols, static configuration, and connected interfaces before path selection.
- GUI: Network > Virtual Routers > (Select VR) > More Runtime Stats > Routing > Route Table.
-
CLI (Legacy):
show routing route [virtual-router <vr_name>] -
CLI (ARE):
show advanced-routing route logical-router <lr_name>
-
Forwarding Information Base (FIB):
Contains the routes actively used for forwarding traffic after the best path selection process.
- GUI: Network > Virtual Routers > (Select VR) > More Runtime Stats > Routing > FIB.
-
CLI (Legacy):
show routing fib [virtual-router <vr_name>] -
CLI (ARE):
show advanced-routing fib logical-router <lr_name>
- Flags in Routing Table Output: Indicate the route's source and status (A-Active, C-Connect, S-Static, O-OSPF, B-BGP, R-RIP, ?-Installed in FIB, etc.).
Protocol-Specific Verification:
Use protocol-specific commands to check neighbor status, learned routes, databases, and protocol parameters.
-
BGP:
-
CLI (Legacy):
show routing protocol bgp ...(e.g.,peer,summary,loc-rib,rib-out) -
CLI (ARE):
show advanced-routing bgp ...(e.g.,neighbor,summary,rib-in,rib-out)
-
CLI (Legacy):
-
OSPF:
-
CLI (Legacy):
show routing protocol ospf ...(e.g.,neighbor,interface,lsdb,summary) -
CLI (ARE):
show advanced-routing ospf ...orospfv3 ...
-
CLI (Legacy):
-
RIP:
-
CLI (Legacy):
show routing protocol rip ...(e.g.,database,interface,peer) -
CLI (ARE):
show advanced-routing rip ...
-
CLI (Legacy):
Path Selection: Administrative Distance (AD) & Metrics
When a Virtual Router/Logical Router learns the same prefix from multiple sources, it selects the best path based on:
- Administrative Distance (AD): A measure of the trustworthiness of the routing source. Lower AD values are preferred. Default AD values in PAN-OS are generally standard (e.g., Connected: 0, Static: 10, eBGP: 20, iBGP: 200, OSPF: 110, RIP: 120), but can often be customized, especially for static routes.
- Metric: If multiple paths have the same lowest AD, the protocol-specific metric is used as a tie-breaker (e.g., OSPF cost, RIP hop count, BGP path attributes like Weight (PAN-OS specific), Local Preference, AS_PATH length, MED).
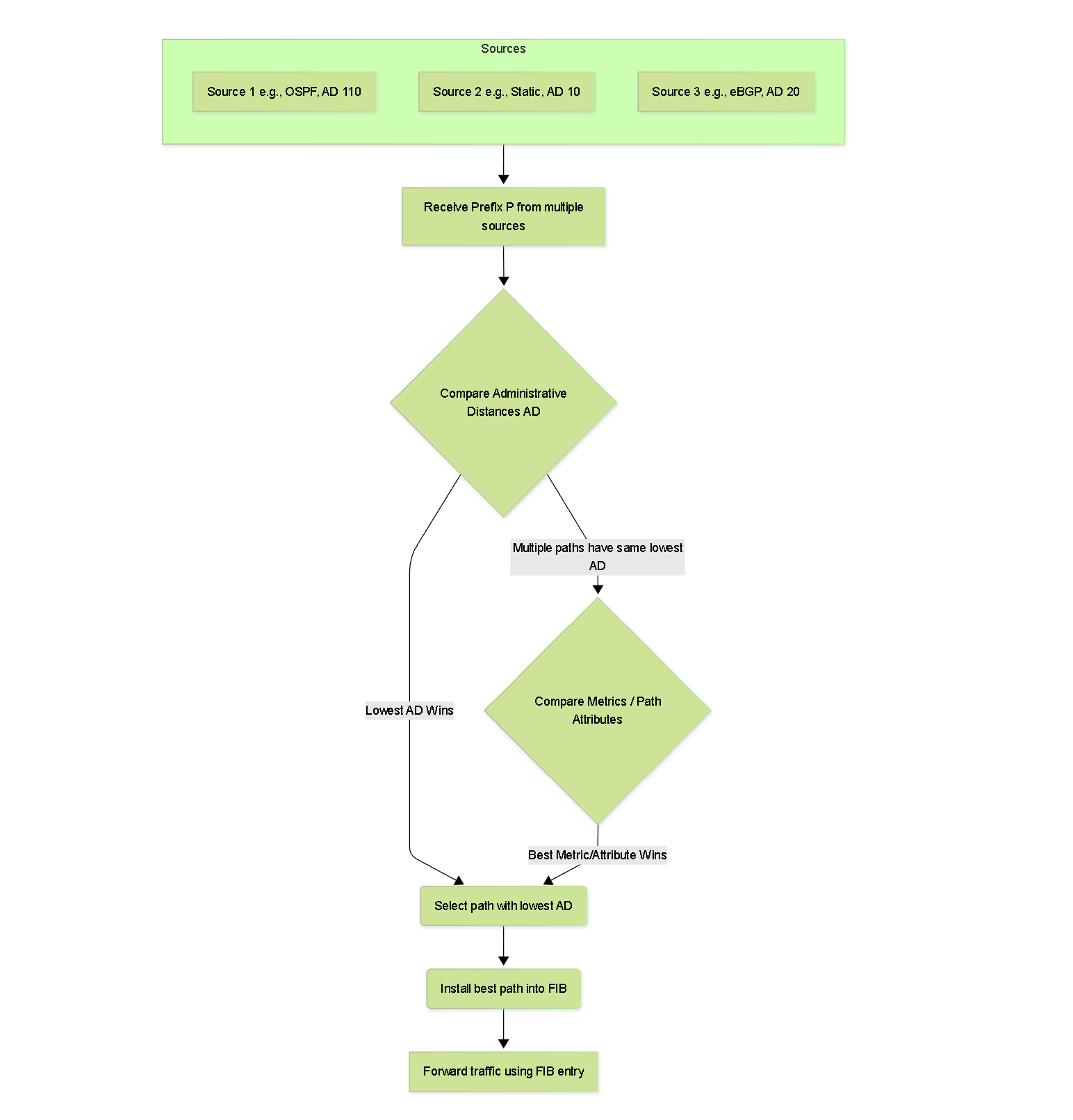
Simplified route selection process based on AD and Metric.
Troubleshooting:
- Connectivity: Ensure basic IP connectivity between potential neighbors (ping, traceroute).
- Security Policies: Verify that necessary traffic (e.g., BGP TCP/179, OSPF unicast DBDs/LSUs) is permitted by security policies, especially in intra-zone or inter-zone scenarios.
- Configuration Mismatches: Check for mismatched parameters like AS numbers (BGP), area IDs, timers, authentication keys (OSPF, RIP).
- Neighbor States: Analyze BGP or OSPF neighbor states using `show` commands to pinpoint adjacency formation problems.
- Debugging: Use `debug routing ...` (Legacy) or `debug advanced-routing ...` (ARE) commands cautiously to view detailed protocol operations.
- Packet Captures: Configure packet captures filtered for specific routing protocols or neighbors to analyze exchanged packets.
> show routing fib virtual-router external
> show routing protocol bgp peer virtual-router external
> show routing protocol ospf neighbor virtual-router default
> debug routing BGP detail
# (Remember to turn debugs off: undebug routing BGP all)
Conclusion
Palo Alto Networks firewalls provide robust support for dynamic routing protocols, including BGP, OSPF (v2/v3), and RIPv2. These capabilities are managed within the Virtual Router (or Logical Router) framework, allowing for network segmentation and tailored routing policies.
Understanding how to configure these protocols, manage route redistribution between them, and utilize the available verification and troubleshooting tools is essential for leveraging the firewall effectively in dynamic network environments. The introduction of the Advanced Routing Engine further enhances these capabilities, aligning PAN-OS more closely with traditional routing platforms while maintaining its integrated security posture.