Palo Alto Best Practice Assessment (BPA) for Security Profiles
Objective
This guide explains how to configure Palo Alto Networks Security Profiles in accordance with the Best Practice Assessment (BPA) recommendations.
Running the BPA regularly helps ensure your firewall configuration adheres to security best practices, reducing your attack surface. You can run the BPA directly from Strata Cloud Manager (formerly AIOps for NGFW).
- For devices not associated with AIOps: On Demand BPA Report
- For devices associated with AIOps: AIOps Best Practices
BPA results often highlight Security Profiles that fail checks if not configured according to best practices. This document provides configuration examples and screenshots to simplify adherence.
Refer to the official documentation for comprehensive details: Security Policy Best Practices .
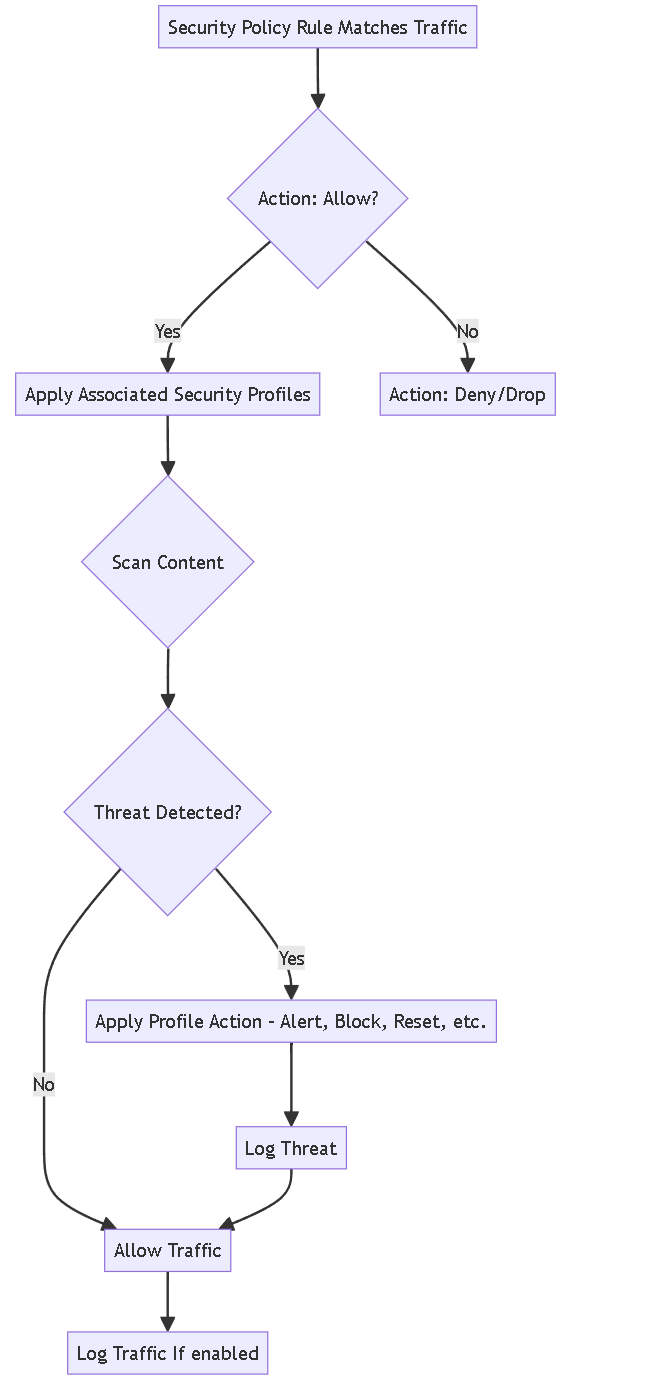
Flowchart illustrating how Security Profiles integrate with Security Policy rules.
Security Profiles Overview
While Security policy rules enable you to allow or block traffic on your network, Security Profiles help you define an allow but scan rule. This scans allowed applications for threats, such as viruses, malware, spyware, and DDoS attacks. When traffic matches the allow rule defined in the Security policy rule, the Security Profile(s) attached to the rule are applied for further content inspection.
Security Profiles are not used in the match criteria of a traffic flow. They are applied after the application or category is allowed by the Security policy rule.
The firewall provides default Security Profiles that you can use out of the box. However, for optimal protection aligned with best practices, creating custom profiles is recommended.
- See Set Up a Basic Security Policy for using default profiles.
- See Create Best Practice Security Profiles for the Internet Gateway for creating custom profiles based on BPA.
You can bundle commonly used profiles into Security Profile Groups for easier application to policies.
Common Security Profile Types
The following sections detail the configuration recommendations for core Security Profiles based on BPA.
| Profile Type | Description |
|---|---|
| Antivirus Profiles | Protects against viruses, worms, trojans, and spyware downloads using stream-based malware prevention. Scans various file types and protocols. Integrates with WildFire for advanced threat signatures. |
| Anti-Spyware Profiles | Blocks spyware on compromised hosts from communicating with external command-and-control (C2) servers. Detects malicious traffic leaving the network. Includes DNS Sinkholing capabilities. |
| Vulnerability Protection Profiles | Stops attempts to exploit system flaws (e.g., buffer overflows, illegal code execution) entering the network. Protects against threats targeting known vulnerabilities. |
| URL Filtering Profiles | Monitors and controls user access to websites over HTTP and HTTPS based on URL categories and custom lists (allow/block). Includes features like credential submission control. |
| Data Filtering Profiles | Prevents sensitive information (e.g., credit card numbers, SSNs, keywords, file properties) from leaving the network. Supports predefined and custom patterns. |
| File Blocking Profiles | Blocks specified file types based on application and direction (upload/download). Can alert, block, or require user continuation. Includes predefined profiles for basic and strict blocking. |
| WildFire Analysis Profiles | Forwards unknown files or email links to the WildFire cloud or a local WF-500 appliance for analysis to detect zero-day malware. |
| DoS Protection Profiles | Protects against Denial of Service attacks, including flood protection (SYN, UDP, ICMP) and resource exhaustion protection (session limits). Applied via DoS Policy Rules. |
| Zone Protection Profiles | Applies packet-based attack protection (flood, reconnaissance, packet-based attacks) to entire network zones to protect the zone infrastructure itself. |
| Security Profile Group | A container to group multiple Security Profiles together for easier application to Security Policy Rules. A group named "default" is automatically applied to new rules. |
Antivirus Profile (BPA Recommended)
Antivirus profiles protect against viruses, worms, trojans, and spyware downloads. Palo Alto Networks recommends specific settings for optimal protection.
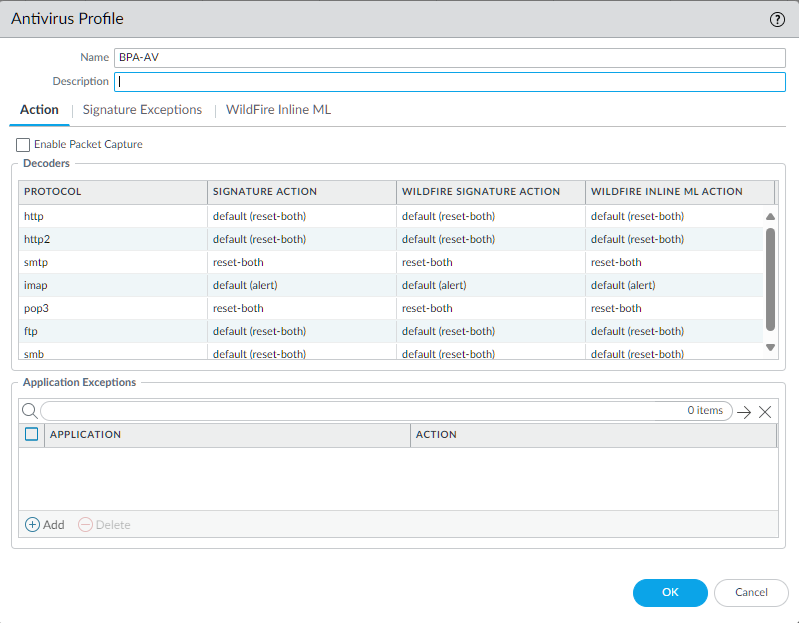
- Enable scanning for relevant protocols (HTTP, SMTP, IMAP, POP3, FTP, SMB).
- Set appropriate actions (often 'reset-both' or 'block' for web protocols, 'alert' for email initially).
- Enable WildFire Inline ML for real-time analysis of PE (Portable Executable) files.
- Set WildFire actions to 'block' for malware verdicts.
- Consider enabling packet capture for analysis (See Packet Capture Tip ).
The
default
action uses the action specified by Palo Alto Networks for that specific signature, typically 'alert' or 'reset-both'.
Actions available include:
- Default: Uses Palo Alto Networks predefined action.
- Allow: Permits traffic (no logs generated for this threat).
- Alert: Generates a threat log entry.
- Drop: Drops the offending packet/connection silently.
- Reset Client: Sends TCP RST to the client.
- Reset Server: Sends TCP RST to the server.
- Reset Both: Sends TCP RST to both client and server.
Anti-Spyware Profile (BPA Recommended)
Anti-Spyware profiles block spyware C2 communications and detect malicious traffic leaving the network.
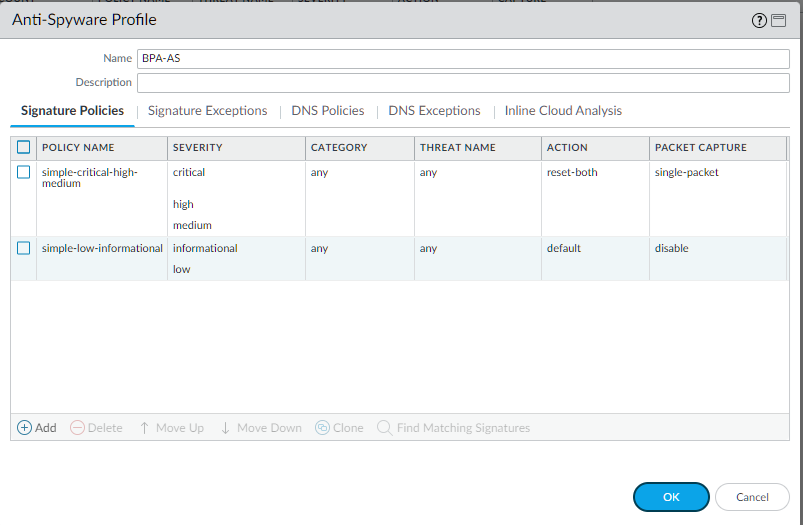
- Use the 'strict' predefined profile as a base or create a custom profile.
- Set actions for Critical, High, and Medium severity spyware signatures to an appropriate blocking action (e.g., 'reset-both', 'drop', or 'block-ip').
- Set actions for Low and Informational severity spyware signatures to 'default' or 'alert' for visibility without potentially blocking legitimate (but noisy) traffic. Setting these to 'block' can sometimes cause issues with legitimate applications.
- Enable DNS Sinkholing for known malicious domains to identify infected internal hosts. Configure a sinkhole IP address (often a non-routable internal IP).
- Consider enabling packet capture ('single-packet' or 'extended-capture') for troubleshooting.
The
Strict
profile overrides the default action to 'block' for critical, high, and medium threats, while using the default action for low and informational.
Actions are similar to Antivirus, with the addition of:
- DNS Sinkhole: Forges a DNS response for malicious domains, redirecting the client to a specified sinkhole IP.
- Block IP: Blocks the source IP (or source/destination pair) for a configurable duration.
Vulnerability Protection Profile (BPA Recommended)
Vulnerability Protection profiles stop attempts to exploit system flaws entering the network.
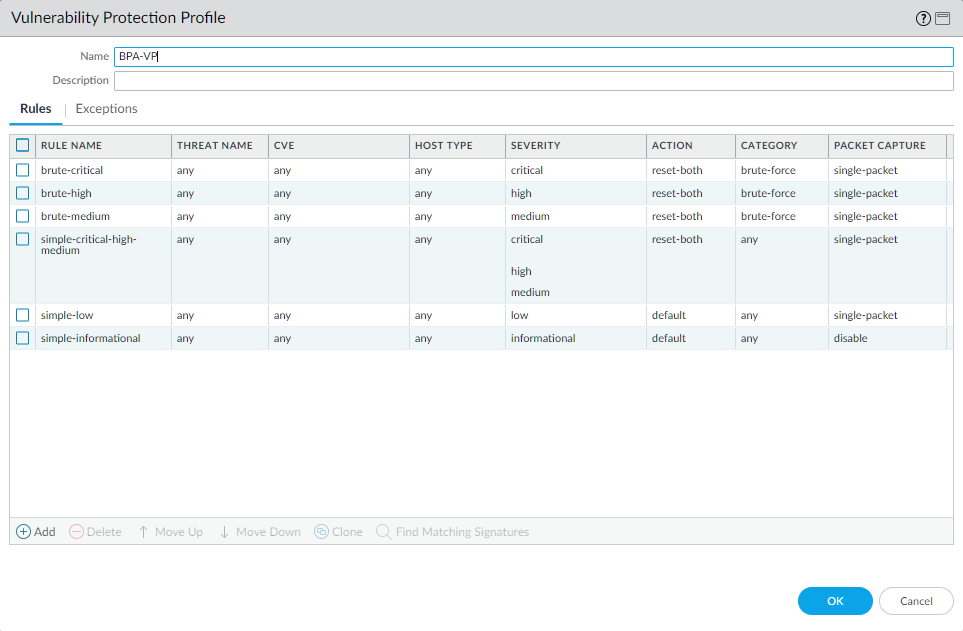
- Apply rules to protect both clients and servers.
- Set actions for Critical, High, and Medium severity vulnerability signatures to an appropriate blocking action (e.g., 'reset-both', 'drop', or 'block-ip').
- Set actions for Low and Informational severity vulnerability signatures to 'default' or 'alert'. Blocking low/info severity can break applications relying on non-standard but legitimate behavior.
- Create exceptions only when necessary and make them as specific as possible (e.g., specific IP address, specific threat ID). Use the Threat Exception Scope technique.
- Consider enabling packet capture for troubleshooting false positives.
Actions are the same as for Anti-Spyware profiles (excluding DNS Sinkhole).
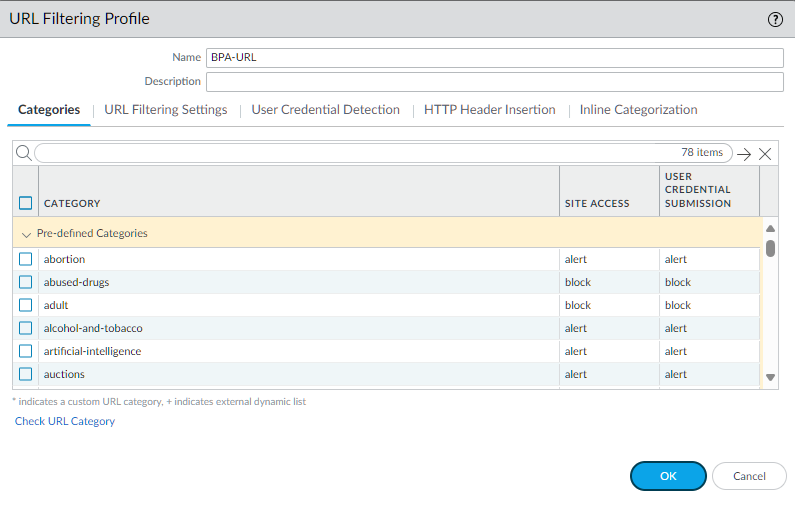
URL Filtering Profile (BPA Recommended)
URL Filtering profiles monitor and control web access based on URL categories.
-
Block high-risk categories:
abused-drugs,adult,command-and-control,copyright-infringement,dynamic-dns,encrypted-dns,extremism,gambling,grayware,hacking,malware,newly-registered-domain,not-resolved,parked,peer-to-peer,phishing,proxy-avoidance-and-anonymizers,questionable,ransomware,scanning-activity,unknown,weapons. -
Set most other categories to
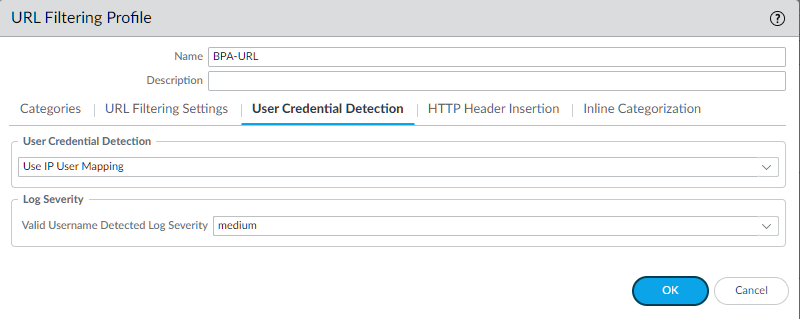
alertfor visibility. Adjust based on corporate policy (e.g., blockgames,social-networking). - Enable User Credential Detection ('Use Domain Credential Filter') to prevent users from submitting corporate credentials to non-corporate sites.
-
Set User Credential Submission action to
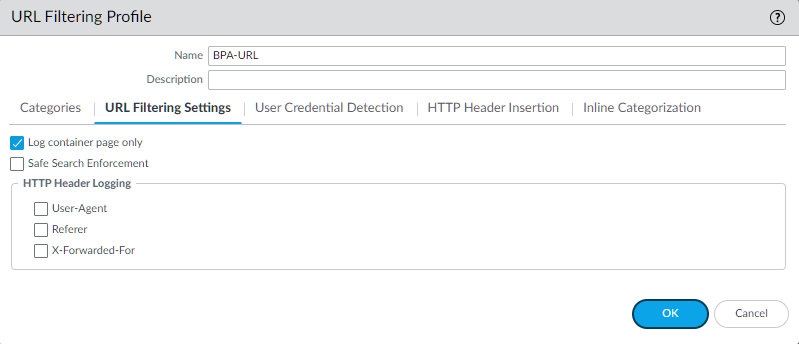
blockfor risky categories (same list as blocked site access) andalertfor others. - Configure Safe Search Enforcement if required.
- Enable HTTP Header Logging for User-Agent, Referer, and X-Forwarded-For for better visibility in logs.
-
Consider setting
high-risk,medium-risk, andlow-riskcategories to alert initially, then adjust based on traffic patterns and risk tolerance. - Enable URL Filtering Inline ML Model Action (if licensed/available) for enhanced detection.
Comprehensive Category Actions (CLI format example)
This shows the typical BPA recommendations in CLI format. Adjust according to your organization's policy.
set profiles url-filtering BPA-URL alert [ abortion alcohol-and-tobacco artificial-intelligence auctions business-and-economy computer-and-internet-info content-delivery-networks cryptocurrency dating educational-institutions entertainment-and-arts financial-services games government health-and-medicine high-risk home-and-garden hunting-and-fishing internet-communications-and-telephony internet-portals job-search legal low-risk marijuana medium-risk military motor-vehicles music news nudity online-storage-and-backup personal-sites-and-blogs philosophy-and-political-advocacy private-ip-addresses real-estate real-time-detection recreation-and-hobbies reference-and-research religion search-engines sex-education shareware-and-freeware shopping social-networking society sports stock-advice-and-tools streaming-media swimsuits-and-intimate-apparel training-and-tools translation travel web-advertisements web-based-email web-hosting ]
set profiles url-filtering BPA-URL block [ abused-drugs adult command-and-control copyright-infringement dynamic-dns encrypted-dns extremism gambling grayware hacking insufficient-content malware newly-registered-domain not-resolved parked peer-to-peer phishing proxy-avoidance-and-anonymizers questionable ransomware scanning-activity unknown weapons ]
set profiles url-filtering BPA-URL credential-enforcement alert [ abortion alcohol-and-tobacco artificial-intelligence auctions business-and-economy computer-and-internet-info content-delivery-networks cryptocurrency dating educational-institutions entertainment-and-arts financial-services games government health-and-medicine home-and-garden hunting-and-fishing internet-communications-and-telephony internet-portals job-search legal low-risk marijuana medium-risk military motor-vehicles music news nudity online-storage-and-backup personal-sites-and-blogs philosophy-and-political-advocacy private-ip-addresses real-estate real-time-detection recreation-and-hobbies reference-and-research religion search-engines sex-education shareware-and-freeware shopping social-networking society sports stock-advice-and-tools streaming-media swimsuits-and-intimate-apparel training-and-tools translation travel web-advertisements web-based-email web-hosting ]
set profiles url-filtering BPA-URL credential-enforcement block [ abused-drugs adult command-and-control copyright-infringement dynamic-dns encrypted-dns extremism gambling grayware hacking high-risk insufficient-content malware newly-registered-domain not-resolved parked peer-to-peer phishing proxy-avoidance-and-anonymizers questionable ransomware scanning-activity unknown weapons ]
File Blocking Profiles
File blocking profiles prevent specific file types from being uploaded or downloaded based on application and direction.
- Define rules specifying file types, applications (e.g., web-browsing, ftp), direction (upload, download, both), and action.
-
Actions include:
-
Alert: Log the file transfer. -
Block: Prevent the transfer and show a block page (customizable). -
Continue: Show a customizable warning page requiring user acknowledgement before proceeding (web traffic only).
-
-
Palo Alto Networks provides predefined profiles:
-
basic file blocking: Blocks common malicious/risky types (.scr, .pif, .exe, .bat, .vbe, .jar, .7z, .rar, etc.) and prompts for encrypted archives. Alerts on others. Good for general use. -
strict file blocking: Blocks everything 'basic' does, plus flash, .tar, multi-level encoding, .cab, .msi, and encrypted archives. Use for sensitive applications/zones.
-
- Apply these profiles to Security Policy rules similar to other Security Profiles.
To get started, see Set Up File Blocking .
WildFire Analysis Profiles
WildFire Analysis profiles control which unknown files or email links are forwarded to the WildFire cloud or a local WF-500 appliance for analysis to detect zero-day threats.
- Define rules based on application, file type, and direction (upload/download).
-
Specify the analysis location:
public-cloud,private-cloud(WF-500), ornone. - Forwarding to the public cloud also submits files matching known AV signatures for broader intelligence gathering.
- Allows for hybrid deployments: analyze sensitive files locally (e.g., PDF on WF-500) and less sensitive or unsupported types (e.g., PE, APK) in the public cloud.
- WildFire verdicts (malware, grayware, phishing, benign) are used to generate signatures distributed via content updates.
Apply WildFire Analysis profiles within Security Profile Groups or directly to Security Policy rules.
See Forward Files for WildFire Analysis for configuration details.
DoS Protection Profiles
DoS Protection profiles configure thresholds and actions for Denial of Service (DoS) attacks, applied via DoS Protection policy rules (not Security Policy rules).
-
Protects against two main types of DoS attacks:
-
Flood Protection: Detects SYN, UDP, ICMP floods that overwhelm resources with connection requests (often using spoofed IPs). Configured with Activate/Alarm thresholds (packets/sec). Actions: SYN Cookies, Random Early Drop (RED). -
Resource Protection: Prevents session exhaustion from numerous legitimate (often botnet) clients establishing full sessions. Configured based on maximum concurrent sessions per source/destination IP. Action: Protect (blocks new sessions exceeding limit).
-
- Profiles define thresholds (Classified or Aggregate) and actions.
-
Classifiedprofiles apply thresholds based on source/destination IP, whileAggregateprofiles apply to all traffic matching the DoS rule. - Applied via Policies > DoS Protection , not within Security Policy rules.
DoS thresholds require careful tuning based on legitimate traffic baselines to avoid blocking valid users.
See DoS Protection Against Flooding for details.
Zone Protection Profiles
Zone Protection Profiles apply network-level defenses to entire zones, protecting the firewall and zone infrastructure itself from reconnaissance and packet-based attacks.
- Applied directly to network zones under Network > Zones .
-
Provides protection against:
-
Flood Protection: TCP SYN, UDP, ICMP, ICMPv6, Other IP floods (based on packets per second thresholds). Actions: SYN Cookies, RED. -
Reconnaissance Protection: TCP/UDP port scans, host sweeps. Action: Alert or Block source IP. -
Packet Based Attack Protection: IP spoofing, malformed packets, TCP/IP options filtering, non-SYN TCP flood, etc.
-
- Thresholds are critical and must be tuned based on the zone's expected traffic levels.
Incorrectly configured Zone Protection thresholds can easily disrupt legitimate traffic.
See Zone Protection Profiles for configuration details.
Security Profile Groups
A Security Profile Group bundles multiple Security Profiles (Antivirus, Anti-Spyware, URL Filtering, etc.) into a single unit that can be easily applied to Security policy rules.
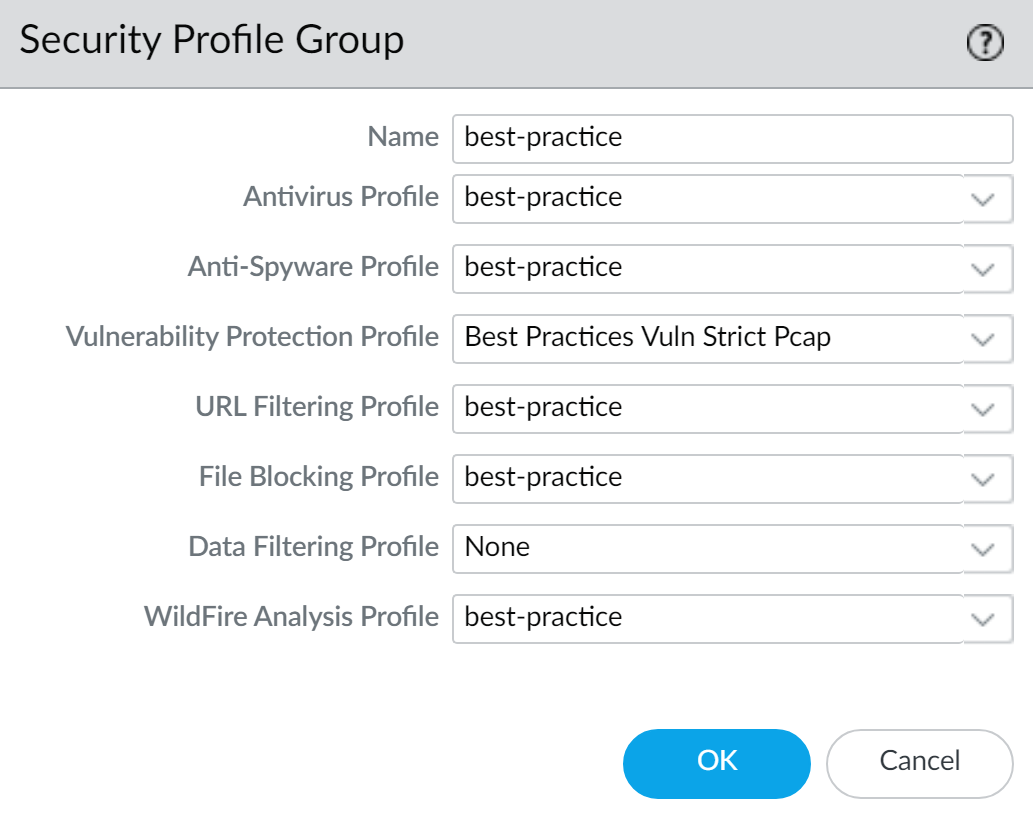
- Simplifies policy creation and management by applying a standard set of protections consistently.
- Reduces the chance of forgetting to apply a necessary profile to a rule.
- Facilitates easier updates – modify the group, and all rules using it inherit the changes (after commit).
Creating a Security Profile Group
-
Navigate to
Objects > Security Profile Groups. -
Click
Add. -
Provide a descriptive
Name(e.g., "Standard-Web-Access", "Strict-Server-Protection"). -
(Multi-VSYS/Panorama) Choose if it should be
Shared. - Add the desired Security Profiles from the dropdown lists (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, etc.).
-
Click
OK.
Applying a Security Profile Group
-
Edit or create a Security Policy rule (
Policies > Security). -
Go to the
Actionstab. -
Set
Profile Setting > Profile TypetoGroup. -
Select your created group from the
Group Profiledropdown.

Click
OK
and
Commit
the changes.
Default Security Profile Group
You can designate one Security Profile Group to be the default group. This group will automatically be applied to any new Security policy rules you create, ensuring a baseline level of protection is always included.
-
Create or modify a Security Profile Group (
Objects > Security Profile Groups). -
Name the group exactly
default(lowercase). - Add the desired baseline Security Profiles to this group.
-
Click
OKandCommit.
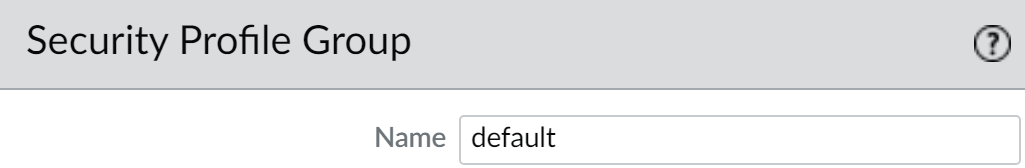
Now, when you add a new Security policy rule, the 'Actions' tab will automatically have the 'Profile Type' set to 'Group' and the 'Group Profile' set to 'default'.

Overriding the Default
Even if a default group is set, you can always change the profile settings for any specific rule. Simply go to the rule's
Actions
tab and either select a different Group Profile or change the Profile Type to 'Profiles' to select individual Security Profiles.
Data Filtering Overview
Data Filtering profiles help prevent sensitive, confidential, or proprietary information from leaving your network. This is a key component of Data Loss Prevention (DLP).
- Filter based on Predefined Data Patterns (e.g., Credit Card Numbers, Social Security Numbers for various countries, compliance patterns like HIPAA, GDPR).
- Filter based on Custom Regular Expressions (Regex) to match specific sensitive keywords, project names, or internal identifiers.
- Filter based on File Properties (e.g., Author, Title, custom metadata tags applied by third-party DLP solutions like Titus or Azure Information Protection labels).
-
Specify the direction (
upload,download,both), applications, and file types to scan. - Set thresholds for alerting and blocking based on the number of pattern matches found within a file.
Setting up Data Filtering typically involves:
-
Creating
Data Pattern Objects
(
Objects > Custom Objects > Data Patterns) to define what to look for (using predefined patterns, regex, or file properties). -
Creating a
Data Filtering Profile
(
Objects > Security Profiles > Data Filtering) where you attach the Data Pattern objects and specify applications, file types, direction, and thresholds/actions. - Applying the Data Filtering profile to relevant Security Policy rules (usually those governing outbound traffic).
For enhanced capabilities, consider Palo Alto Networks Enterprise DLP cloud service.
Creating a Data Filtering Profile
This outlines the steps to set up data filtering.
Step 1: Define Data Pattern Object
-
Go to
Objects > Custom Objects > Data Patternsand clickAdd. -
Enter a descriptive
Name. -
(Optional) Select
Sharedfor multi-VSYS/Panorama. -
(Optional - Panorama) Select
Disable overrideif needed. -
(Optional) Enable
Data Captureto log the blocked data (requires password setup underDevice > Setup > Content-ID > Manage Data Protection). -
Choose
Pattern Type: Predefined, Regular Expression, or File Properties. -
Click
Addwithin the pattern object to define rules: -
Predefined:
Select the desired pattern from the
Namedropdown. -
Regular Expression:
Provide a rule
Name, selectFile Type(s), enter the regexData Pattern. -
File Properties:
Provide a rule
Name, selectFile Type,File Property(e.g., 'TITUS GUID', 'Microsoft MIP Label'), and enter the expectedProperty Value. -
Click
OKto save the Data Pattern Object.
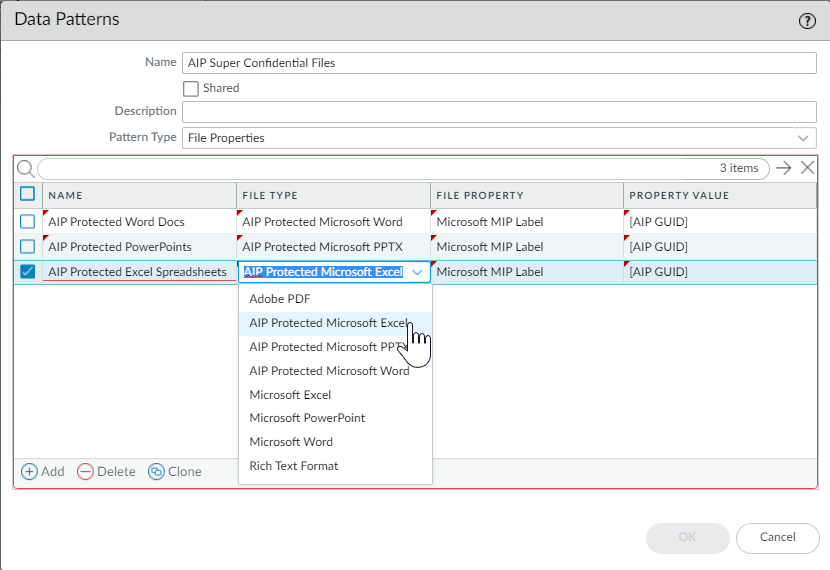
Step 2: Create Data Filtering Profile
-
Go to
Objects > Security Profiles > Data Filteringand clickAdd. -
Enter a descriptive
Name. -
Click
Addto create a profile rule. -
Select the
Data Patternobject created in Step 1. -
Specify
Applications,File Types, andDirection(upload/download). Ensure File Types align with those specified in the Data Pattern object! -
Set
Alert Threshold(matches to trigger alert). -
Set
Block Threshold(matches to trigger block). -
Set
Log Severity. -
Click
OKto save the Data Filtering Profile.
Step 3: Apply Profile to Policy
-
Edit a Security Policy rule (
Policies > Security). -
Go to the
Actionstab. -
Ensure Profile Type is
Profiles(or use a Group containing the profile). - Select your Data Filtering profile in the corresponding dropdown.
-
Click
OK.
Step 4: (Recommended) Disable HTTP Partial Response
This prevents browsers from resuming downloads of files blocked by Data Filtering.
-
Go to
Device > Setup > Content-IDand editContent-ID Settings. -
Uncheck
Allow HTTP partial response. -
Click
OK.
Step 5: Monitor
View logs under
Monitor > Logs > Data Filtering
.
Predefined Data Filtering Patterns
Palo Alto Networks provides numerous predefined data patterns to help meet compliance requirements and protect common sensitive information types.
Access these when creating a Data Pattern Object (
Objects > Custom Objects > Data Patterns
) by setting the
Pattern Type
to
Predefined Pattern
and selecting from the
Name
dropdown in the rule configuration.
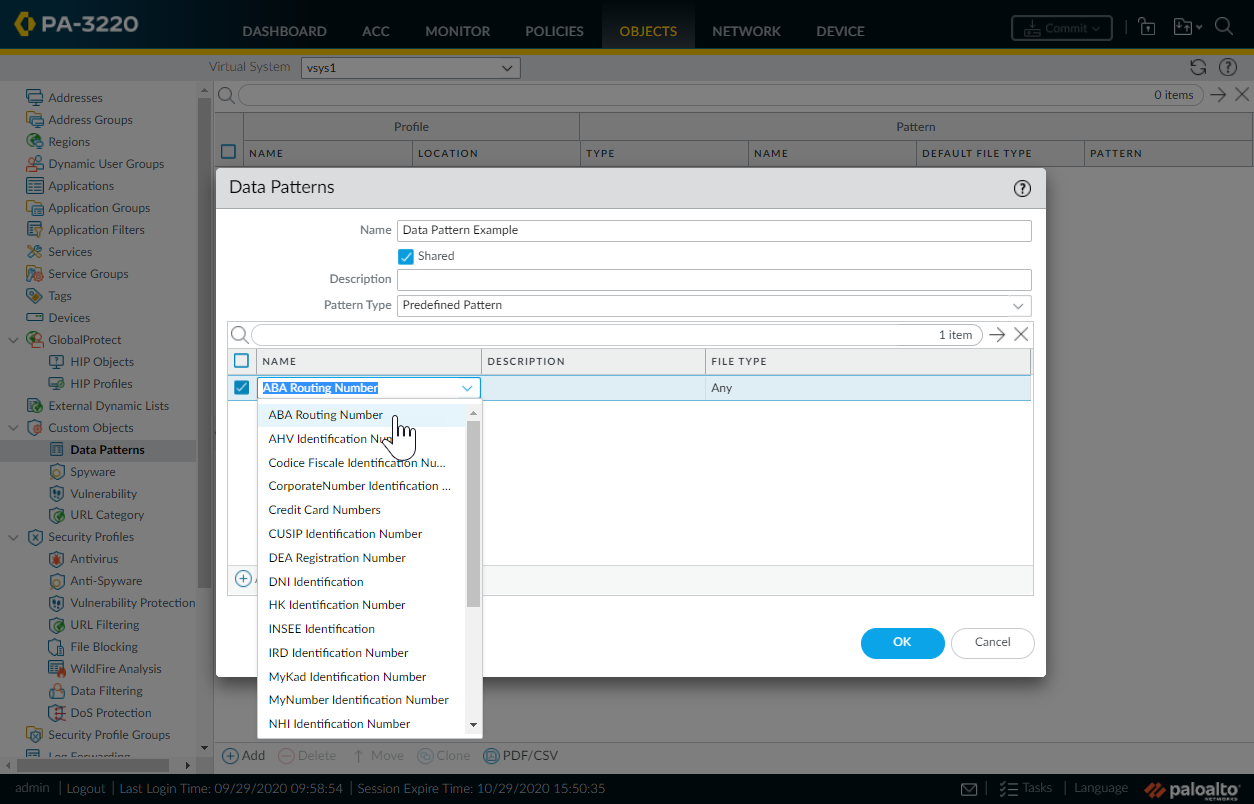
If specific needs aren't met, use regular expressions for custom patterns.
List of Common Predefined Patterns:
| Pattern Name | Description |
|---|---|
| Credit Card Numbers | 16-digit credit card numbers |
| Social Security Numbers | 9-digit SSNs with dashes |
| Social Security Numbers (without dash separator) | 9-digit SSNs without dashes |
| ABA Routing Number | American Banking Association Routing Number |
| AHV Identification Number | Swiss AHV Number |
| Codice Fiscale Identification Number | Italian Fiscal Tax Code |
| CorporateNumber Identification Number | Japanese Corporate Number |
| CUSIP Identification Number | Committee on Uniform Security Identification Procedures Number |
| DEA Registration Number | U.S. Drug Enforcement Administration Number |
| DNI Identification Number | Spanish National Identity Document Number |
| HK Identification Number | Hong Kong Residents Identification Number |
| INSEE Identification Number | French National Statistics ID Number |
| IRD Identification Number | New Zealand Inland Revenue Department Number |
| MyKad Identification Number | Malaysia Identity Card Number |
| MyNumber Identification Number | Japanese Social Security/Tax Number |
| NHI Identification Number | New Zealand National Health Index Number |
| NIF Identification Number | Spanish Tax Identification Number |
| NIN Identification Number | Taiwan Identification Card Number |
| NRIC Identification Number | Singapore National Registration Identity Card Number |
| Permanent Account Identification Number | India Permanent Account Number (PAN) |
| PRC Identification Number | People's Republic of China Resident ID Number |
| PRN Identification Number | Republic of South Korea Resident Registration Number |
Tips & Tricks: Enable Packet Captures on Security Profiles
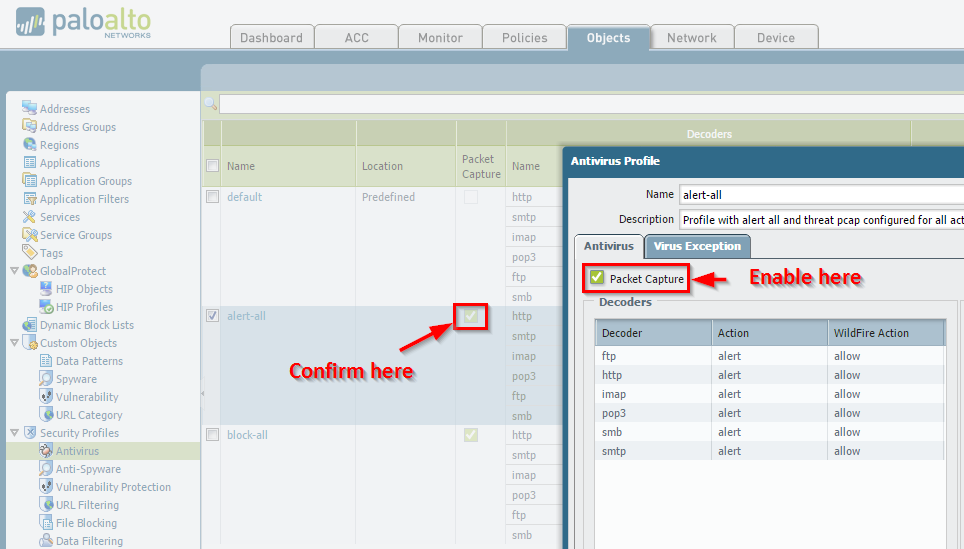
Enabling "Packet Capture" within Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection) is useful for troubleshooting false positives or understanding threat behavior.

Enabling Packet Capture
Navigate to
Objects > Security Profiles
and edit the relevant profile.
Antivirus Profile
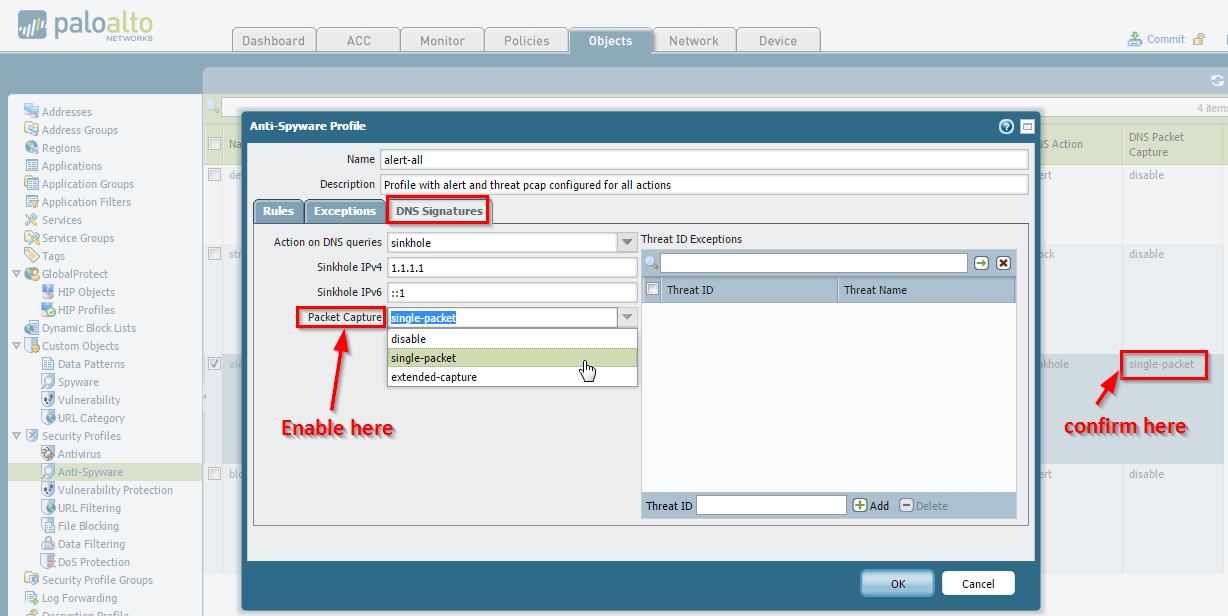
Anti-Spyware Profile
Available under the
DNS Signatures
tab and within specific rule exceptions.
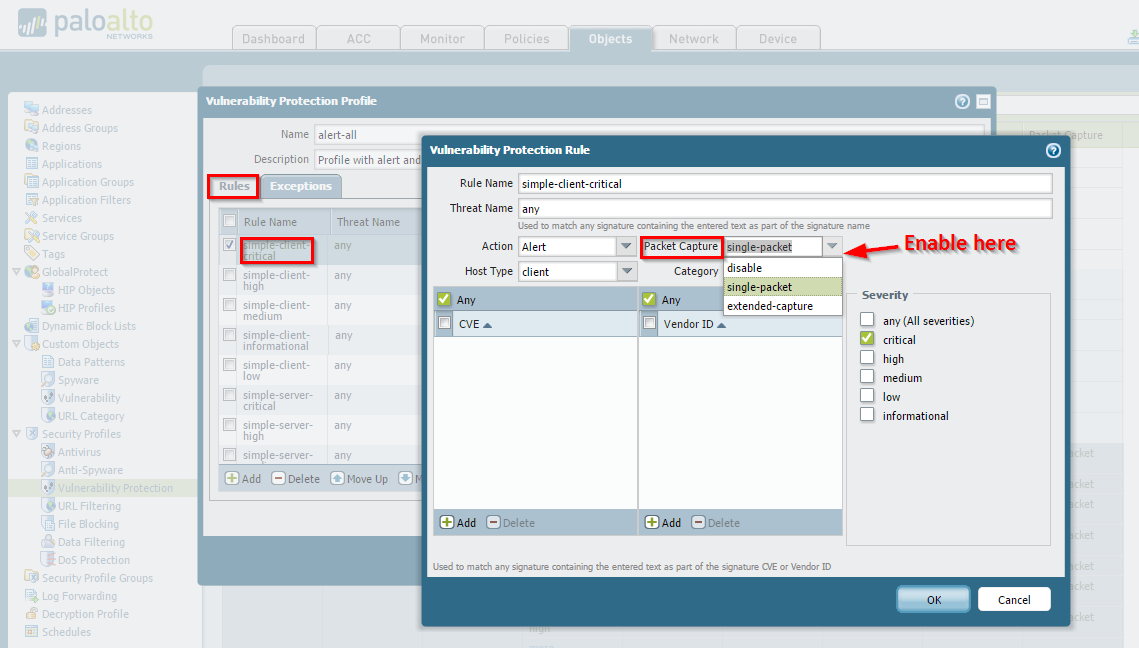
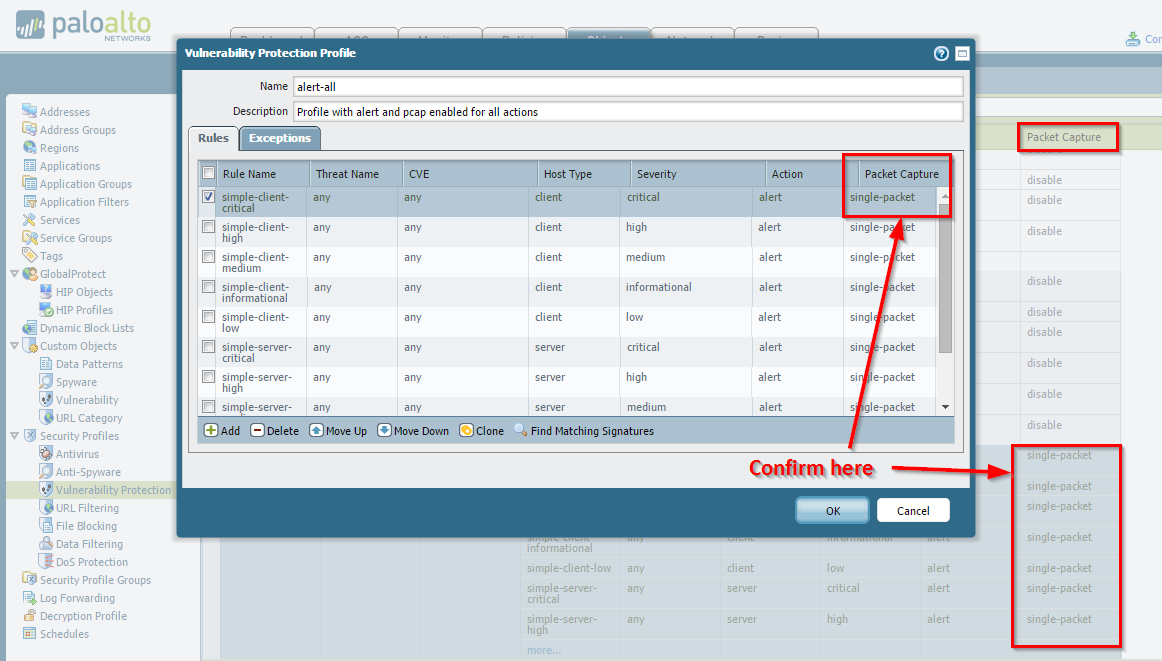
Vulnerability Protection Profile
Available within specific rule exceptions.
Capture Options (Anti-Spyware & Vuln Protection)
-
Disabled: No capture. -
Single-packet: Captures one packet when the threat is detected. -
Extended-capture: Captures multiple packets (configurable number) providing more context. Recommended for detailed analysis.
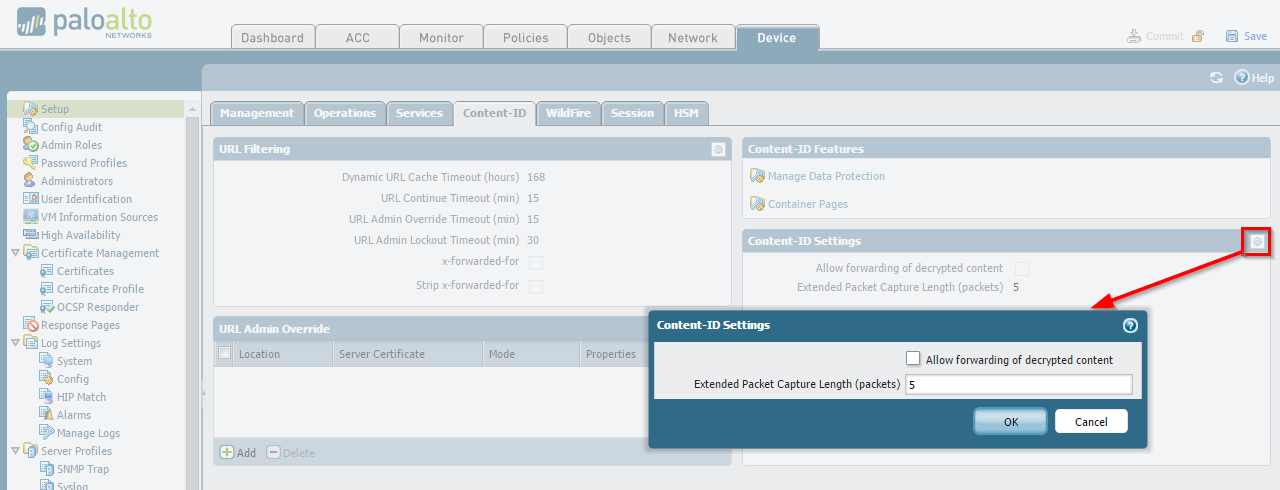
Configuring Extended Capture Length
Set the number of packets for 'extended-capture' under
Device > Setup > Content-ID
, edit
Threat Detection Settings
.
Viewing Packet Captures
Go to
Monitor > Logs > Threat
. Find the relevant log entry and click the green down arrow (packet capture icon) in the second column to download the pcap file.
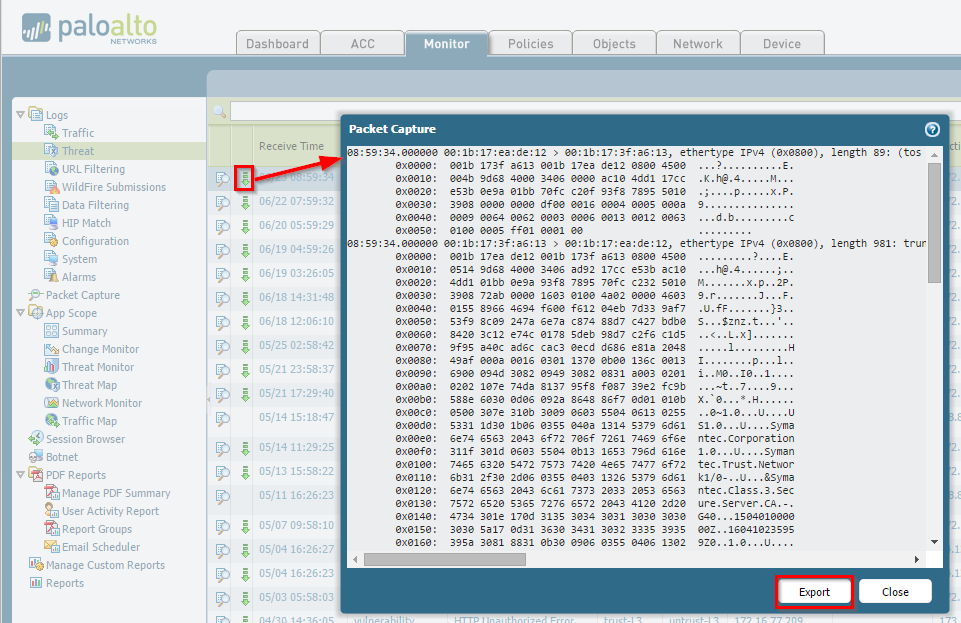
Packet captures are only generated if the profile action is set to 'allow' or 'alert' . If the action is 'block', 'drop', or any 'reset' variation, the session is terminated immediately, and no (or minimal) capture occurs for that specific threat trigger.
Tips & Tricks: Narrowing the Scope of Threat Exceptions
When a threat signature causes a false positive for legitimate traffic, creating a threat exception is necessary. However, applying a broad exception can inadvertently reduce security. This method provides a more granular approach.
Objective
To apply a threat exception only to the specific traffic causing the false positive, minimizing the impact on overall security.
Procedure
-
Identify Existing Rule & Profile:
Determine the Security Policy rule and the attached Security Profile (e.g., Vulnerability Protection) that is triggering the false positive log.
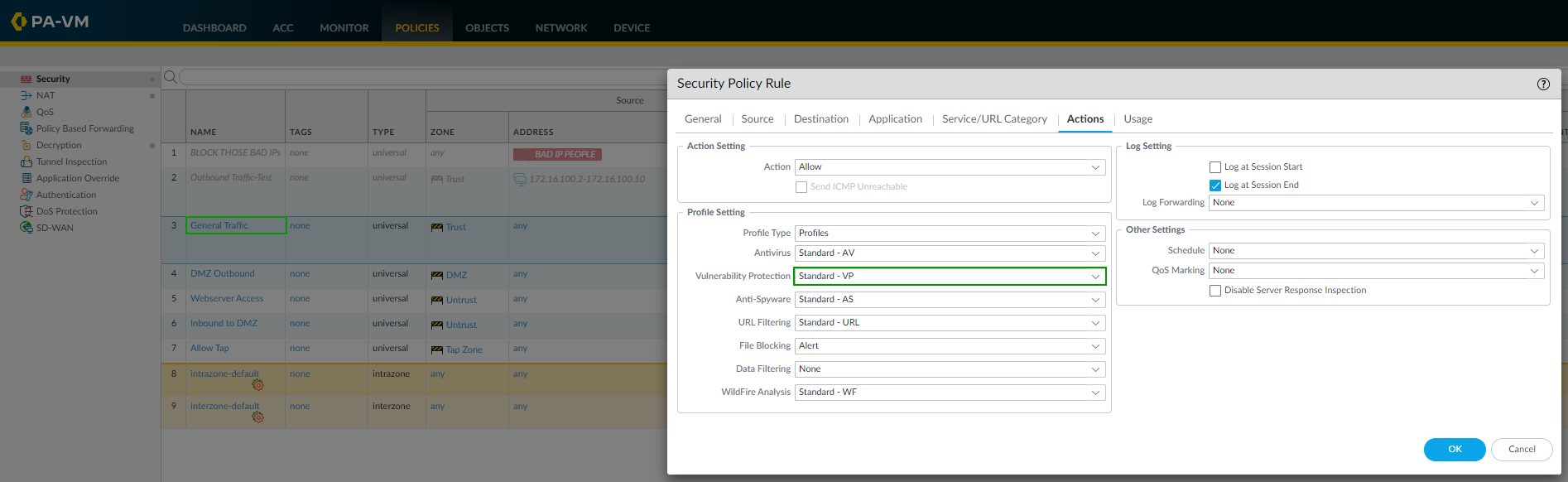
Example: Original Security Rule ('Allow Web') using the 'VP-Strict' profile. -
Clone Security Policy Rule:
Clone the identified rule. Rename the clone descriptively (e.g., "Allow Web - Exception") and place it
immediately above
the original rule.
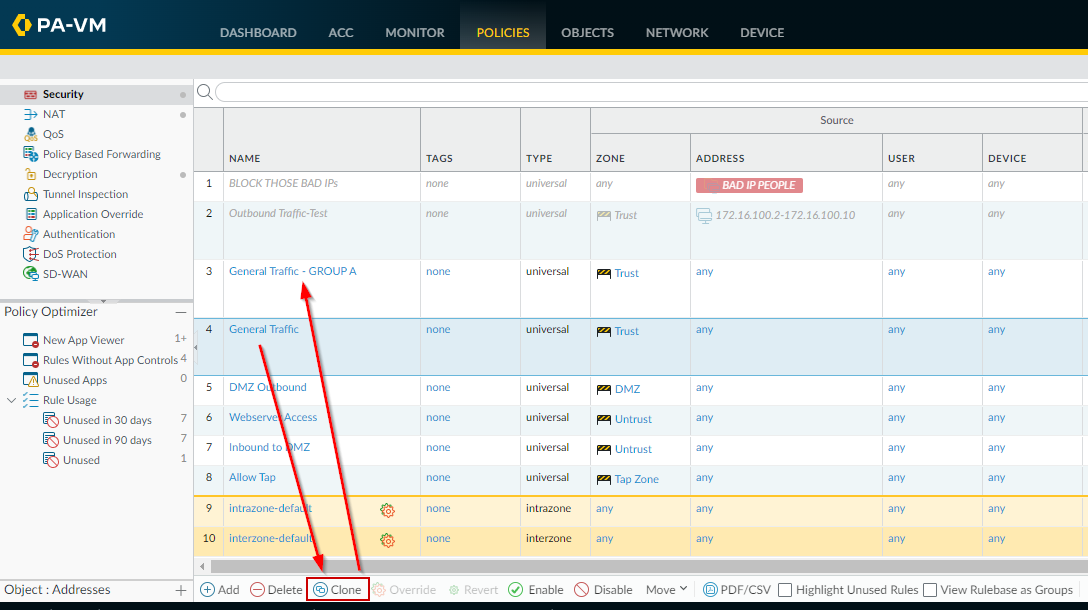
Cloning the 'Allow Web' rule. -
Narrow Cloned Rule Scope:
Modify the cloned rule's Source, Destination, Application, or Service fields to match
only
the specific traffic causing the false positive. Be as granular as possible (e.g., specify source/destination IPs, specific application).
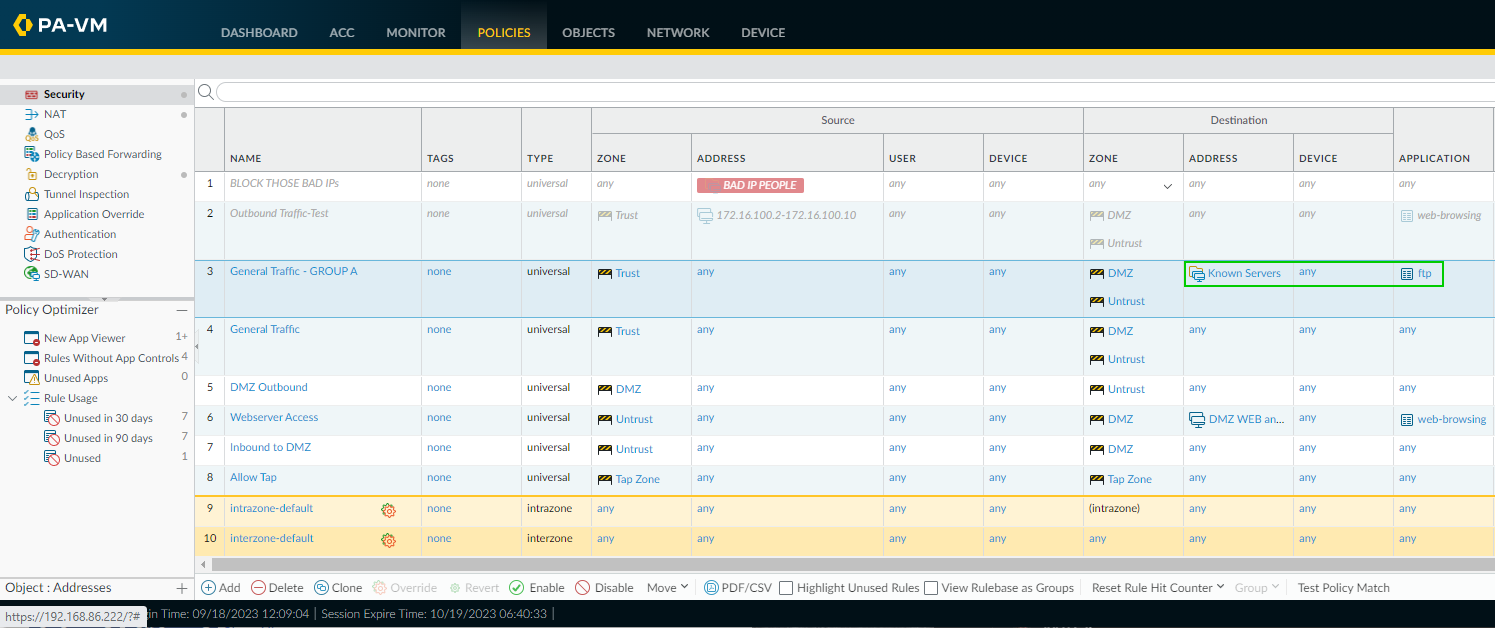
Modifying the cloned rule ('Allow Web - Exception') to apply only to a specific destination IP (10.0.0.1). -
Clone Security Profile:
Go to
Objects > Security Profilesand clone the profile associated with the original rule (e.g., clone 'VP-Strict'). Rename it descriptively (e.g., "VP-Strict-With-Exception").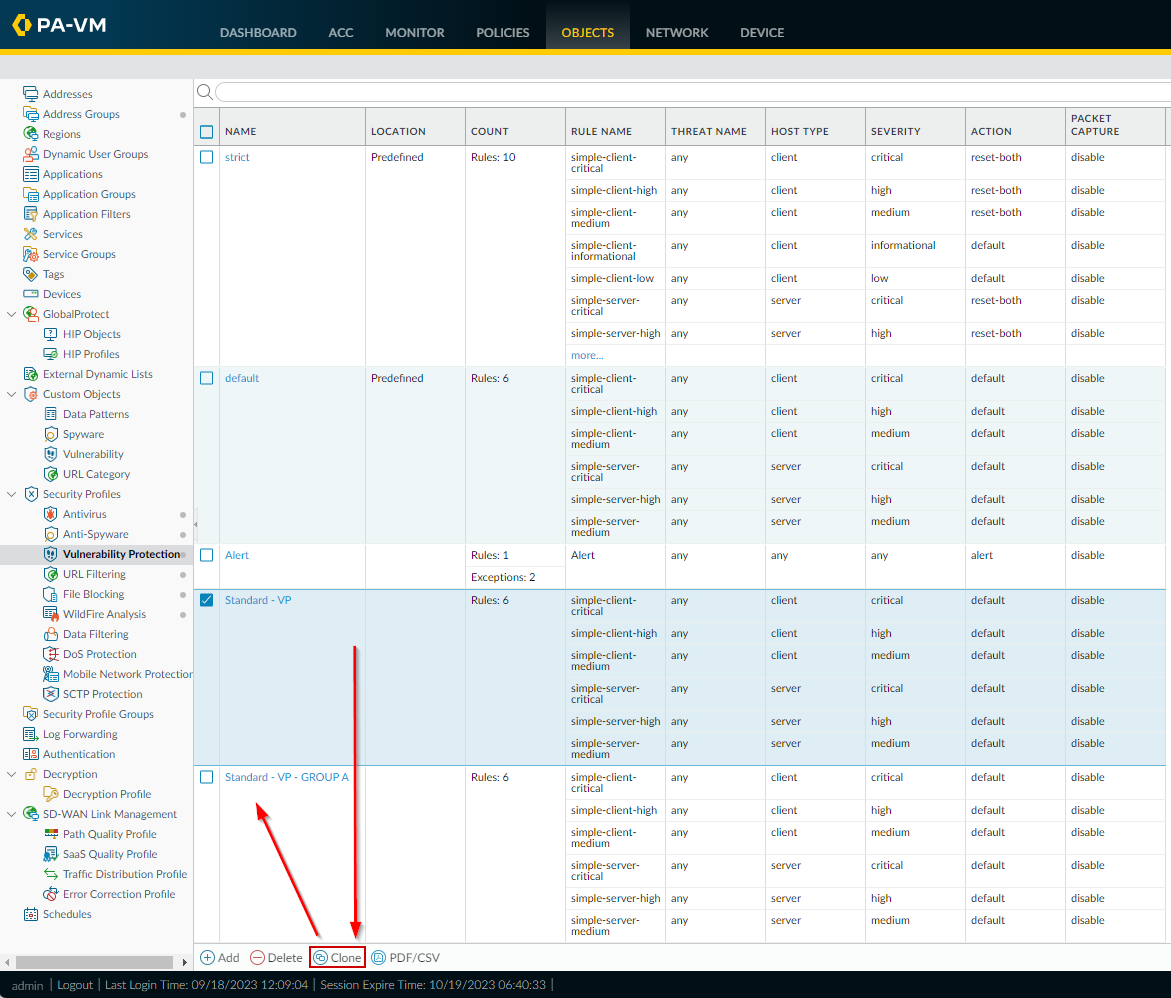
Cloning the 'VP-Strict' profile to create 'VP-Strict-With-Exception'. -
Add Exception to Cloned Profile:
Edit the newly cloned profile ("VP-Strict-With-Exception"). Go to the 'Exceptions' tab and add the specific Threat ID that needs to be bypassed, setting its action to 'allow' or 'alert'.
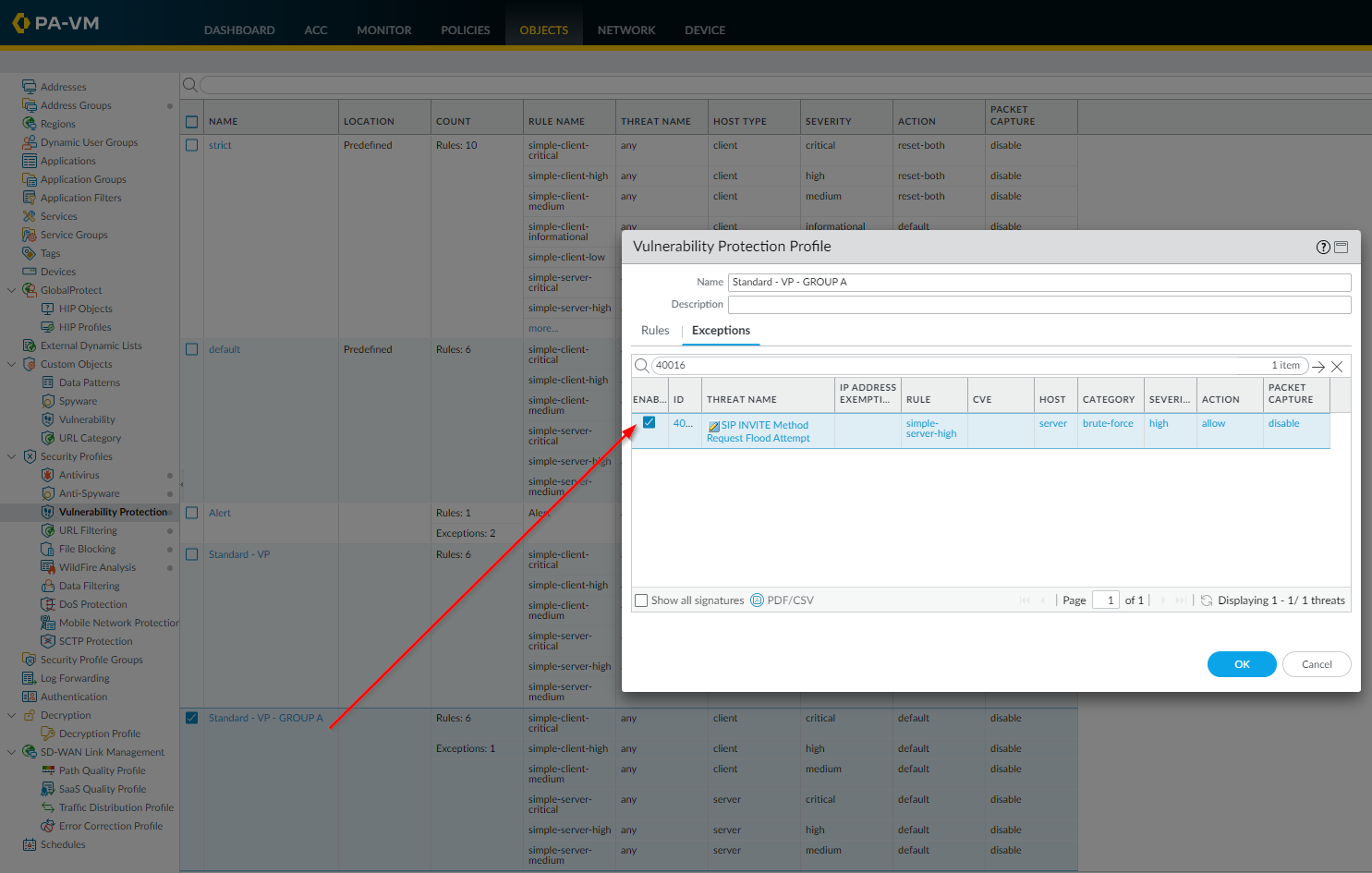
Adding Threat ID 12345 as an exception with 'allow' action in the 'VP-Strict-With-Exception' profile. -
Associate Cloned Profile with Cloned Rule:
Go back to the cloned Security Policy rule ("Allow Web - Exception") and change its Action > Group Profile or Profile setting to use the newly cloned profile ("VP-Strict-With-Exception").
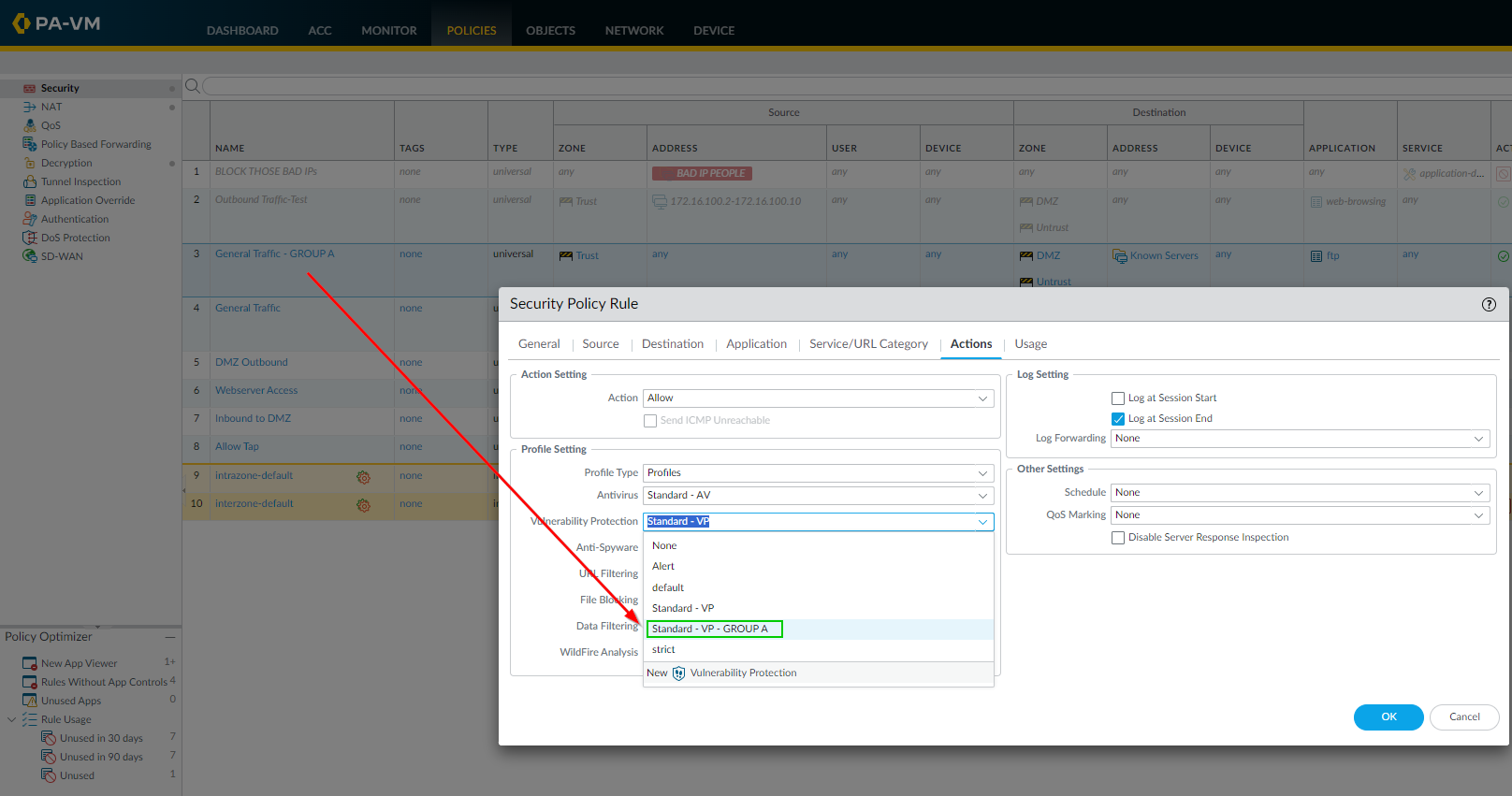
Applying the 'VP-Strict-With-Exception' profile to the 'Allow Web - Exception' rule. -
Commit Changes:
Commit the configuration.
Commit the configuration changes.
Result: The specific false-positive traffic will now match the narrow, cloned rule ("Allow Web - Exception") and hit the cloned profile ("VP-Strict-With-Exception") where the threat is allowed. All other traffic previously matching the original rule ("Allow Web") will continue to be processed by the original, stricter profile ('VP-Strict') without the exception.
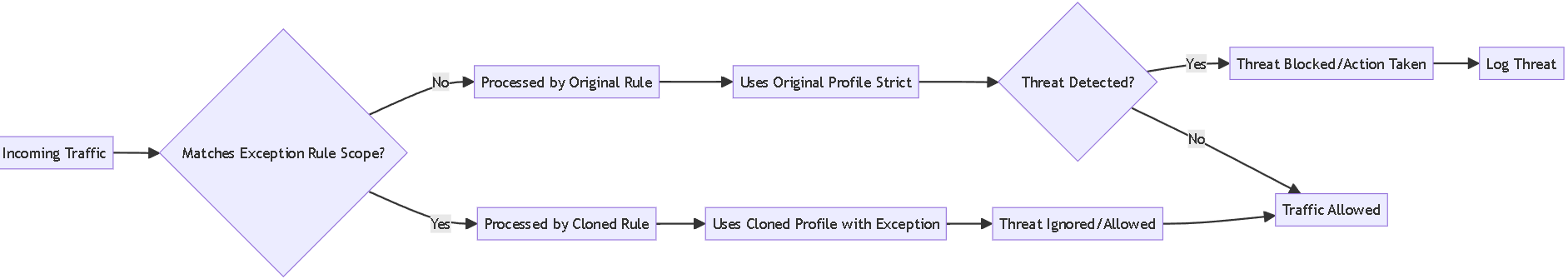
Flowchart illustrating the logic of using cloned rules and profiles for targeted exceptions.
Common BPA Check Fails for Security Profiles
If Security Profiles are not configured according to Best Practice Assessment recommendations, you might see the following failures in your BPA report:
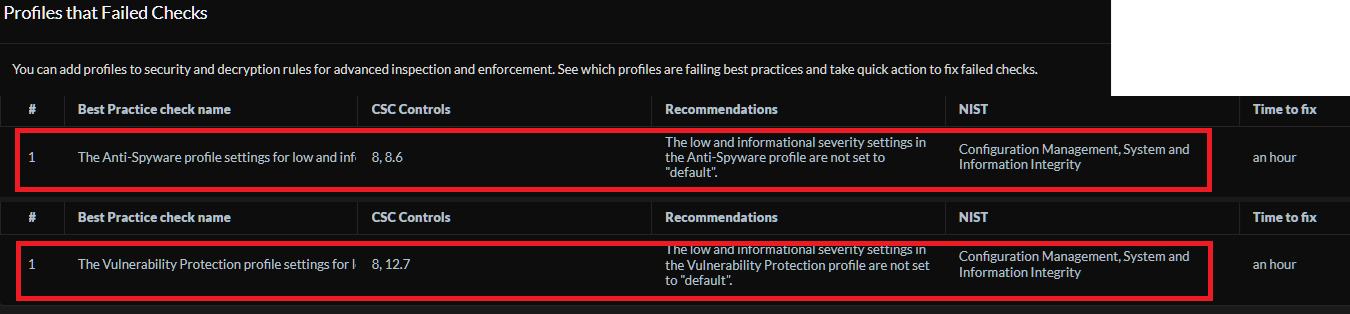
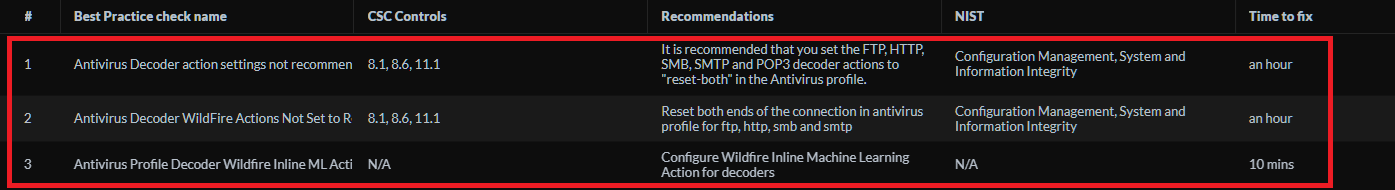
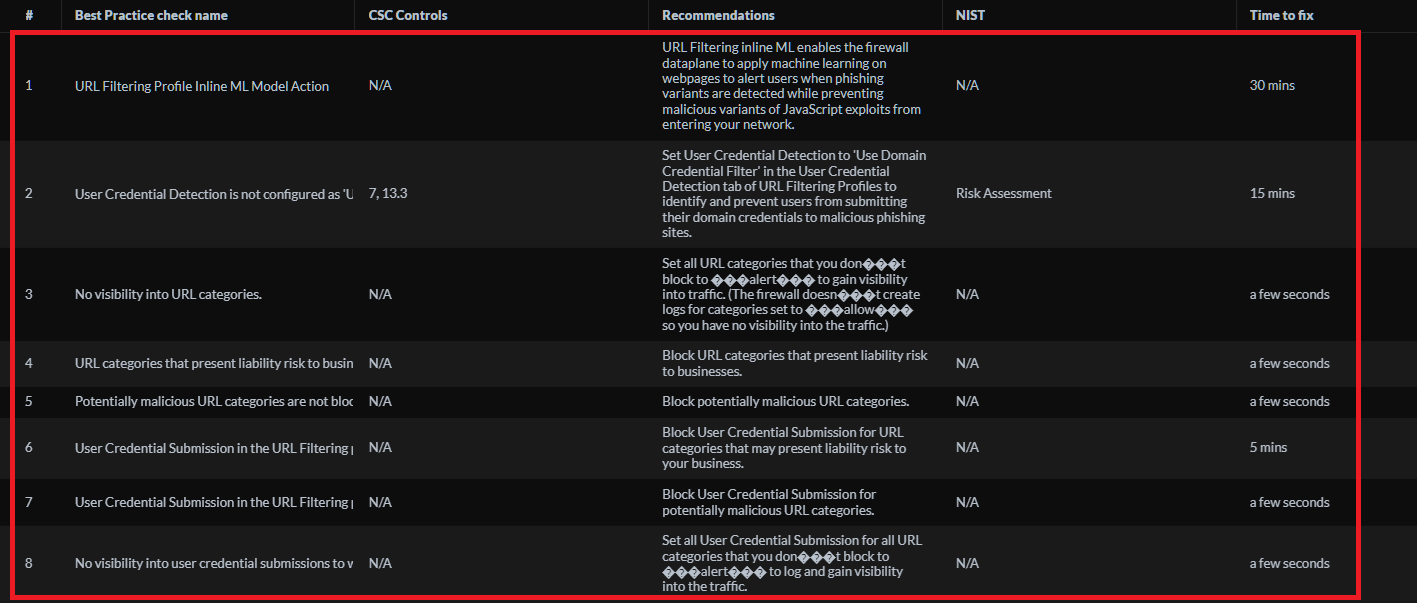
Common BPA Check Names and Reasons:
- The Anti-Spyware profile settings for low and informational severity events are not set to "default" : Blocking these severities can cause false positives. BPA recommends 'default' or 'alert'.
- The Vulnerability Protection profile settings for low and informational severity events are not set to "default" : Similar to Anti-Spyware, blocking these can break legitimate applications. BPA recommends 'default' or 'alert'.
- Antivirus Decoder action settings not recommended : Actions for protocols like HTTP, SMB should generally be blocking, while email might be alerting.
- Antivirus Decoder WildFire Actions Not Set to Recommended : WildFire verdicts (malware) should typically trigger a 'block' action.
- Antivirus Profile Decoder Wildfire Inline ML Action : BPA recommends enabling WildFire Inline ML for PE files with an appropriate action.
- URL Filtering Profile Inline ML Model Action : BPA recommends enabling the URL Filtering Inline ML model action if available/licensed.
- User Credential Detection is not configured as 'Use Domain Credential Filter' in a URL Filtering Profile : This is the recommended setting to prevent corporate credential reuse on non-corporate sites.
- No visibility into URL categories. : This often means many categories are set to 'allow' instead of 'alert'.
- URL categories that present liability risk to businesses are not blocked. : Categories like 'adult', 'gambling', 'extremism' should be blocked per BPA.
- Potentially malicious URL categories are not blocked. : Categories like 'malware', 'phishing', 'command-and-control', 'unknown' should be blocked per BPA.
- User Credential Submission in the URL Filtering profile is not blocked for categories that may present liability risk... : Credential submission should be blocked for risky categories.
- User Credential Submission in the URL Filtering profile is not blocked for categories that are potentially malicious... : Credential submission should definitely be blocked for malicious categories.
- No visibility into user credential submissions to websites. : Credential submission action for non-blocked categories should be set to 'alert'.
Addressing these BPA findings significantly improves your security posture.
Interactive Quiz: Security Profiles & BPA
Test your understanding of Palo Alto Networks Security Profiles and Best Practice Assessment recommendations.