Comprehensive Guide to PAN-OS Security Policy
Overview and Purpose
Palo Alto Networks Next-Generation Firewalls (NGFWs) utilize Security Policy rules as the cornerstone for controlling network traffic and enforcing comprehensive threat prevention. These rules are evaluated during the session setup phase (fast path for existing sessions) to decide whether to permit or deny traffic based on a rich set of defined criteria. The fundamental operational principle is top-down, first match : the firewall processes rules sequentially from the top of the policy rulebase. The very first rule that comprehensively matches all its defined criteria for a given session is applied, and no subsequent rules are evaluated for that specific session. This makes rule order and specificity paramount for effective security posture.
Security Policy Fundamentals
Core Matching Criteria
For a Security Policy rule to match a session, *all* configured criteria within that rule must be met. Palo Alto Networks NGFWs offer a granular set of matching conditions:
-
Source Zone / Destination Zone:
Logical containers for network interfaces. Zones represent segments of your network (e.g., Trust, Untrust, DMZ, VPN-Users, Servers). Traffic must flow between or within zones to be evaluated by security policy. Common zone types include Layer 3, Layer 2, Virtual Wire, Tap, and Tunnel.- Layer 3 Zones: For routed interfaces.
- Layer 2 Zones: For switchports or VLAN interfaces in a transparent bridge.
- Virtual Wire Zones: For interfaces deployed in a bump-in-the-wire fashion.
- Tunnel Zones: For interfaces terminating VPN tunnels (IPSec, GlobalProtect).
-
Source Address / Destination Address:
Matches on the original (pre-NAT) IP addresses, subnets, or ranges. Palo Alto Networks strongly encourages the use of:- Address Objects: Named representations of single IPs, subnets, ranges, or FQDNs (which resolve dynamically).
- Address Groups: Collections of Address Objects or other Address Groups.
-
Dynamic Address Groups (DAGs):
Address groups whose membership is dynamically updated based on tags. Tags can be assigned manually, by User-ID, by VM Information Sources (e.g., VMware vCenter, AWS VM tags), Panorama, or via the API. This allows policies to adapt automatically to changing network environments (e.g., new VMs, user logins).
PCNSE/PCNSA Exam Note (Palo Alto Networks): Understand how DAGs are populated (tags from Panorama, User-ID, VM Information Sources, auto-tagging based on logs) and their benefit in creating dynamic, scalable policies.
- External Dynamic Lists (EDLs): Lists of IPs, URLs, or domains hosted on an external web server, which the firewall periodically fetches and uses in policy. Useful for threat intelligence feeds or frequently changing lists.
-
Application (App-ID):
Palo Alto Networks' patented App-ID technology identifies applications irrespective of port, protocol, SSL/TLS encryption, or evasive tactics.- Mechanism: App-ID uses multiple identification techniques: application signatures, protocol decoding, heuristics, and information from decrypted sessions.
-
Granularity:
Can match specific applications (e.g.,
facebook-base,ms-rdp), broader Application Filters (e.g., "collaboration", "storage-backup"), or custom Application Groups. - Custom Applications: If a proprietary or uncommon application isn't in the standard App-ID database, you can define a custom application based on signatures, ports, or IP protocols.
-
Application Override:
For traffic that App-ID cannot identify or misidentifies, or for specific cases like tunneling applications, an Application Override policy can be used to manually classify traffic based on ports. This is a Layer 4 control and bypasses Layer 7 App-ID inspection for that specific traffic. Use with extreme caution.
Gotcha! (Palo Alto Networks): Application Override policies are processed *before* Security Policies. If an Application Override rule matches, it dictates the application identity, and Security Policies will then match based on this overridden application, not the App-ID'd one. This can bypass intended security inspections if not carefully managed.
Integrates with directory services (e.g., Active Directory, LDAP, eDirectory) and other sources to map IP addresses to users and user groups. This enables granular, user-based security policies.
-
Sources for IP-to-User Mapping:
- PAN-OS Integrated User-ID Agent (queries domain controllers for security event logs).
- Windows-based User-ID Agent (similar to integrated, but on a separate server).
- Syslog monitoring (parsing logs from other authentication systems).
- GlobalProtect client logins.
- Captive Portal (web-based authentication for unknown users).
- XML API for custom integrations.
- RADIUS, SAML, Kerberos SSO.
- Group Mapping: User-ID retrieves group memberships, allowing policies to be applied to entire departments or roles (e.g., 'Sales', 'Engineering-Admins').
Defines the Layer 4 transport protocol (TCP/UDP/ICMP) and destination port(s).
-
application-default: This is the Palo Alto Networks recommended best practice. It restricts the application identified by App-ID to its standard, well-known ports (e.g., DNS on UDP/53, HTTPS on TCP/443). If an application attempts to use a non-standard port, it won't match a rule usingapplication-default. -
Specific Service Objects/Groups:
Allows specifying custom TCP/UDP ports or predefined service objects (e.g.,
service-http,service-https). Useful for custom applications or when needing to allow an application on a non-standard port (though this should be carefully evaluated). -
any: Allows any port for the matched application. This significantly weakens security and should generally be avoided.
Matches traffic based on the category of the destination URL (e.g., Malware, Phishing, Social-Networking, Gambling). Requires a URL Filtering license (typically PAN-DB). For HTTPS traffic, URL category visibility often requires SSL Decryption.
- PAN-DB: Palo Alto Networks' cloud-based URL categorization service, providing dynamic updates.
- Custom URL Categories: Administrators can define their own categories and populate them with specific URLs or use EDLs for URL lists.
Used with GlobalProtect to assess the security posture of remote endpoints (e.g., OS patch level, antivirus status, disk encryption). Security policies can then enforce access based on whether an endpoint matches a required HIP Profile.
Rule Evaluation Order: Top-Down, First Match
PAN-OS evaluates Security Policy rules sequentially from rule #1 downwards. The first rule whose criteria *all* match the session's characteristics is applied. Once a match is found, no further rules in the Security Policy rulebase are evaluated for that specific session. This "first match" logic is critical.
Rule Shadowing
Rule shadowing occurs when a broader, more general rule is placed higher in the rulebase than a more specific rule. If the general rule matches traffic that the specific rule was intended to handle, the specific rule will never be evaluated for that traffic, effectively being "shadowed."
Example of Shadowing:
- Rule 1: Source: ANY, Destination: ANY, Application: ANY, Service: ANY, Action: Allow (Broad Rule)
- Rule 2: Source: Internal-Users, Destination: DMZ-Servers, Application: ms-rdp, Service: application-default, Action: Deny (Specific Rule)
In this scenario, RDP traffic from Internal-Users to DMZ-Servers would be matched by Rule 1 and allowed, completely bypassing the intended deny action in Rule 2.
Best Practice: Place the most specific rules at the top of the rulebase and gradually move towards more general rules. Cleanup rules (explicit deny) should be at the bottom, just above the implicit default rules.
Packet Lifecycle and Policy Evaluation in PAN-OS
Understanding the sequence of operations within the Palo Alto Networks NGFW for a new session is crucial for designing and troubleshooting policies.
- Ingress & Initial Packet Processing: Packet arrives at an ingress interface. Basic sanity checks are performed. The ingress interface and its associated zone are identified.
-
Session Lookup / Creation:
The firewall checks if an existing session matches the packet (based on source/destination IP, port, protocol, and ingress zone).
- If a session exists (fast path), existing security parameters are applied, and packet processing is expedited.
- If no session exists (slow path), a new session setup process begins.
-
NAT Policy Lookup (for new sessions):
The firewall consults the NAT policy rulebase to determine if any Source NAT (SNAT) or Destination NAT (DNAT) rules apply.
- DNAT is critical as it changes the destination IP, which impacts routing. DNAT evaluation occurs very early. The original destination IP is stored for security policy matching.
- SNAT translation decision is also made here, but the actual IP change often happens later, just before egress.
- Decryption Policy Lookup (for new SSL/TLS sessions): If the traffic is SSL/TLS encrypted, the Decryption Policy is evaluated to determine if the session should be decrypted (SSL Forward Proxy or SSL Inbound Inspection). Decryption is necessary for App-ID to accurately identify applications within encrypted flows and for Security Profiles to inspect content.
- Authentication Policy Lookup (for new sessions, if applicable): If traffic requires authentication (e.g., to identify an unknown user for User-ID via Captive Portal or to enforce MFA), Authentication Policy is evaluated.
-
Route Lookup / Policy Based Forwarding (PBF):
The firewall determines the egress interface and zone.
- It first checks PBF rules. If a PBF rule matches, it overrides the FIB (Forwarding Information Base) lookup.
- If no PBF rule matches, a standard route lookup in the FIB is performed using the destination IP (post-DNAT if DNAT applied).
-
Security Policy Lookup (for new sessions):
This is the core step. The firewall evaluates Security Policy rules top-down.
- Matching is performed against the Pre-NAT Source IP and Pre-NAT Destination IP .
- Other criteria include Source/Destination Zone (destination zone determined by route lookup), App-ID (potentially identified after decryption), User-ID, Service, URL Category, etc.
-
Action Enforcement & Post-NAT Processing:
-
If the matched Security Policy rule's action is
Allow
:
- NAT is applied (SNAT if configured). The source IP is changed at this stage.
- Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire, Data Filtering) attached to the Allow rule are applied to the (now potentially NATted and decrypted) traffic.
- QoS policy is applied.
- The packet is forwarded via the determined egress interface.
- If the matched rule's action is Deny, Drop, or Reset : The packet is discarded (optionally sending a TCP reset or ICMP unreachable). Session is logged as denied/dropped.
-
If the matched Security Policy rule's action is
Allow
:
-
Default Rules:
If no user-defined Security Policy rule matches the traffic, the appropriate pre-defined default rule is applied:
-
intrazone-default(traffic within the same zone): Action is Allow . -
interzone-default(traffic between different zones): Action is Deny .
-
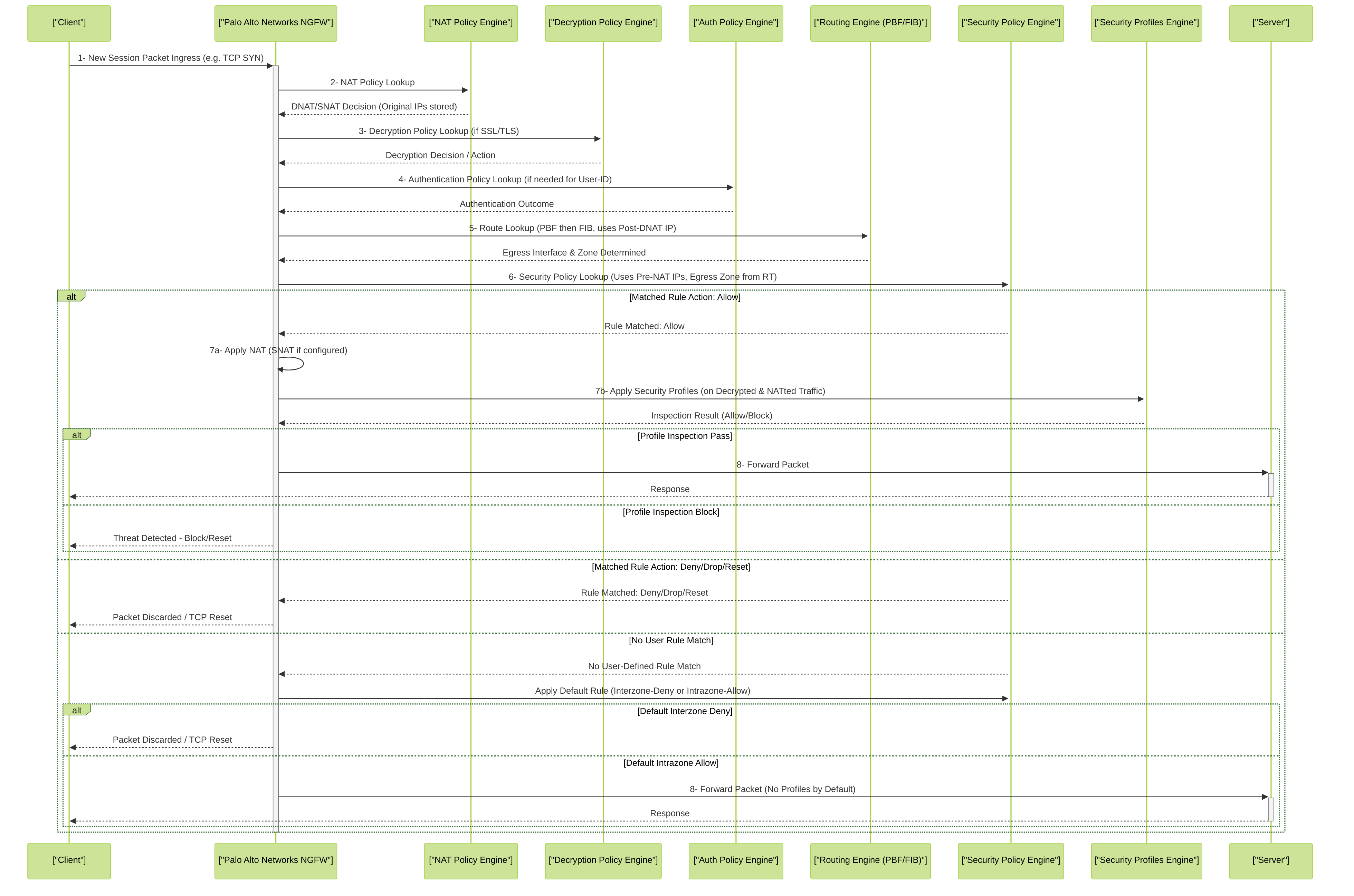
Simplified Palo Alto Networks NGFW packet flow for a new session, highlighting key policy evaluation stages.
Security Rule Actions
When a Security Policy rule matches traffic, one of the following actions is taken:
- Allow: Permits the traffic to pass through the firewall. This is the only action to which Security Profiles can be attached for threat inspection and content filtering.
- Deny: Actively blocks the traffic. By default, the firewall sends a TCP reset to the source for TCP traffic or an ICMP port unreachable for UDP traffic. This behavior can be modified. The session is logged as denied.
- Drop: Silently discards the traffic without sending any notification back to the source. This can make troubleshooting more difficult but may be preferred to prevent revealing firewall presence to scanners. The session is logged as dropped.
- Reset Client: Sends a TCP reset to the client-side of the connection.
- Reset Server: Sends a TCP reset to the server-side of the connection.
- Reset Both: Sends a TCP reset to both the client and server. This is similar to the default 'Deny' action for TCP.
For all actions, logging should be enabled (typically "Log at Session End", and "Log at Session Start" for troubleshooting specific flows) to provide visibility into traffic patterns and policy enforcement. Log Forwarding profiles should be configured to send these logs to Panorama, a SIEM, or other log management systems.
Advanced Inspection and Control
Security Profiles and Profile Groups
Security Profiles provide the deep packet inspection capabilities of Palo Alto Networks NGFWs. They are applied *only* to Security Policy rules with an 'Allow' action, as inspection occurs on traffic permitted by the policy.
Key Security Profiles include:
- Antivirus Profile: Scans allowed traffic for viruses, worms, trojans, and other malware in various file types and protocols (HTTP, SMTP, IMAP, POP3, FTP, SMB). Uses stream-based scanning and WildFire signature updates.
- Anti-Spyware Profile: Detects and blocks spyware downloads. It also identifies and blocks C2 (Command-and-Control) traffic from already compromised hosts attempting to communicate with malicious servers. Uses DNS Signatures and DNS Security features to block known malicious domains.
- Vulnerability Protection Profile: Protects against known exploits targeting system vulnerabilities in applications and operating systems. It inspects traffic for patterns matching exploit signatures (e.g., buffer overflows, code execution attempts). Rules within the profile can be set to alert, block, or reset.
- URL Filtering Profile: Controls access to websites based on their PAN-DB URL category (e.g., Malware, Phishing, Adult, Social-Networking) or custom URL categories. Actions include alert, allow, block, continue (warn user, then allow), or override (require password). Requires SSL Decryption for visibility into HTTPS URLs.
- File Blocking Profile: Blocks or alerts on specific file types being uploaded or downloaded across various applications (e.g., executables over web, specific document types in email). Can also block based on file direction (upload/download).
-
WildFire Analysis Profile:
Forwards unknown files and email links (that are not identified by other security engines) to the Palo Alto Networks WildFire cloud or an on-premise WF-500 appliance for sandboxing and analysis. WildFire returns a verdict (benign, grayware, malware, phishing). The firewall can then be configured to block newly identified malware based on these verdicts.
- WildFire Inline ML: Newer PAN-OS versions leverage machine learning models directly on the firewall dataplane to analyze PE (Portable Executable) files and provide near real-time verdicts for certain types of malware without requiring cloud submission for every file. This significantly speeds up detection for known patterns.
- Data Filtering Profile: Prevents sensitive data (e.g., credit card numbers, social security numbers, custom data patterns) from leaving the network. Requires careful configuration of data patterns and is most effective with SSL Decryption.
- DoS Protection Profile: Mitigates Denial-of-Service attacks by setting thresholds for connection rates, session counts, etc. Can be applied via a DoS Protection policy rule or directly within a Security Profile Group to protect specific allowed applications.
Security Profile Groups
To simplify management and ensure consistent security posture, individual Security Profiles can be bundled into a Security Profile Group . This group can then be attached to multiple 'Allow' Security Policy rules. Modifying the group updates protection across all associated rules. This is a Palo Alto Networks best practice.
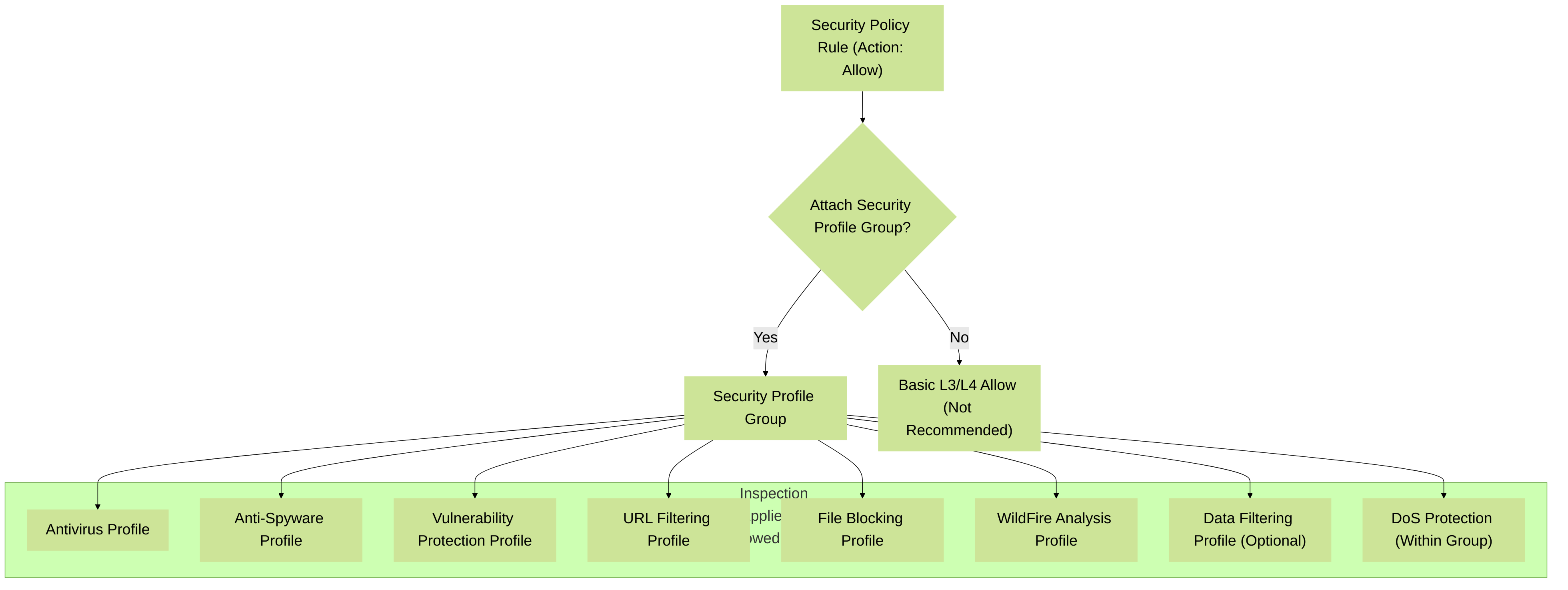
Attaching a Security Profile Group to an 'Allow' rule applies multiple layers of inspection.
Application Override Policies
Application Override policies are used to manually classify traffic based on protocol and port (Layer 4 information), bypassing the standard App-ID (Layer 7) inspection for that specific traffic.
Purpose and Use Cases:
-
Non-Standard Ports:
For trusted, internal applications that are known to use non-standard ports and for which App-ID might struggle or identify as
unknown-tcp/udp. - Custom Applications without Signatures: When a custom application cannot be accurately identified by a custom App-ID signature.
- Encrypted Traffic Tunnels: For traffic that is tunneled within another protocol (e.g., SSH tunneling other applications), where App-ID cannot see the inner application without decryption. Application Override can classify the outer tunnel.
- Performance-Sensitive Traffic (Rare): In very specific, high-performance scenarios where the overhead of App-ID is a concern for known, trusted traffic (this is rare and should be a last resort).
Processing Order:
Application Override policies are evaluated *before* Security Policies. If traffic matches an Application Override rule, the application specified in that rule is used for subsequent Security Policy matching.
Configuration:
Found under
Policies > Application Override
. Rules specify source/destination zones, addresses, port, protocol, and the application to assign to the traffic.
Decryption Policy Interaction
SSL/TLS Decryption is a critical enabler for many of the Palo Alto Networks NGFW's advanced security features. Without decryption, traffic encrypted with SSL/TLS remains opaque to App-ID (for fine-grained application identification like distinguishing between different Google services) and most Security Profiles (like Antivirus, File Blocking, Data Filtering, and detailed URL Filtering).
Types of Decryption:
- SSL Forward Proxy: Decrypts outbound SSL/TLS traffic initiated by internal clients to external servers (e.g., users browsing HTTPS websites). The firewall acts as a "man-in-the-middle," re-signing server certificates with its own Forward Trust certificate (which clients must trust).
- SSL Inbound Inspection: Decrypts inbound SSL/TLS traffic destined for internal servers (e.g., users accessing an organization's secure web portal). Requires uploading the server's private key and certificate to the firewall.
- SSH Proxy: Decrypts SSH traffic for visibility and control over tunneled commands or file transfers (less common).
Decryption Policy and Security Policy:
Decryption Policy rules determine *what* traffic to decrypt. Once decrypted:
-
App-ID
can accurately identify the specific application within the SSL/TLS tunnel (e.g.,
facebook-chatinstead of justssl). - Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire, Data Filtering) can inspect the cleartext payload for threats and sensitive content.
If Decryption Policy specifies 'no-decrypt' for certain traffic (e.g., financial, healthcare sites due to privacy concerns), then App-ID will only identify the traffic as generic
ssl
or
tls
, and Security Profiles will have limited to no visibility into the payload.
Configuration:
Found under
Policies > Decryption
. Rules specify criteria similar to Security Policy (source/dest zones, addresses, URL categories, service) and an action (decrypt or no-decrypt). Decryption Profiles control protocol versions, key exchange algorithms, and certificate checking.
Specialized Rule Considerations
Universal, Interzone, and Intrazone Rules
Security Policy rules can be configured with a "Rule Type" that defines their scope based on zone interaction:
- Universal (Default): Applies to traffic regardless of whether the source and destination zones are the same or different. This is the most common type.
- Interzone: Applies *only* when the source zone and destination zone are different. Useful for creating policies specifically governing traffic crossing zone boundaries.
- Intrazone: Applies *only* when the source zone and destination zone are the same. Useful for controlling traffic *within* a single zone (e.g., restricting communication between servers in the same server zone).
Default Rules
PAN-OS includes two non-configurable default Security Policy rules located at the very bottom of the rulebase. They cannot be deleted or modified, except for their logging settings.
-
intrazone-default:- Rule Type: Intrazone
- Action: Allow
- Purpose: Matches traffic originating and destined for the same zone if no explicit user-defined intrazone or universal rule above it matches. By default, logging is disabled.
-
interzone-default:- Rule Type: Interzone
- Action: Deny
- Purpose: Matches traffic flowing between different zones if no explicit user-defined interzone or universal rule above it matches. By default, logging is disabled.
Best Practice: While the default rules exist, it's a strong security best practice to create explicit "cleanup" rules just above the defaults:
-
An explicit
intrazone-deny-allrule (Source Zone: any, Destination Zone: any, Rule Type: intrazone, Action: Deny, Log: Enabled). -
An explicit
interzone-deny-allrule (Source Zone: any, Destination Zone: any, Rule Type: interzone, Action: Deny, Log: Enabled).
These explicit deny rules ensure all traffic not explicitly permitted is logged, providing better visibility than relying solely on the non-logging defaults.
Security Policy for GlobalProtect Users
GlobalProtect extends the NGFW's security policies to remote users, whether they are connecting from laptops, mobile devices, or other endpoints. Security policies for GlobalProtect users leverage User-ID and HIP profiles for granular control.
- Source Zone: Traffic from GlobalProtect users typically originates from a dedicated Tunnel zone associated with the GlobalProtect gateway.
- User-ID Integration: GlobalProtect client logins provide immediate IP-to-user mapping, allowing policies to be based on specific users or AD groups.
-
HIP (Host Information Profile) Checks:
- GlobalProtect agents collect host information (e.g., OS version, patch level, AV status, disk encryption).
- This information is matched against HIP Objects and HIP Profiles configured on the firewall.
- Security Policy rules can then use HIP Profiles as a matching criterion, ensuring that only compliant devices are granted access to specific resources. For example, a rule might allow access to sensitive servers only if the connecting endpoint matches the "Compliant-Endpoints" HIP Profile.
-
Split Tunneling vs. Full Tunneling:
- Full Tunneling: All traffic from the GlobalProtect client is routed through the firewall. This allows consistent policy enforcement and inspection for all user traffic (internet-bound and internal). Security policies for internet access would use the Tunnel zone as source and an "Untrust" or "Internet" zone as destination.
- Split Tunneling: Only traffic destined for specified internal networks is routed through the firewall. Internet-bound traffic goes directly from the client. This requires careful policy definition for the tunneled traffic. You might have rules allowing access from the Tunnel zone to "Trust" or "Server" zones.
- Application Access: App-ID, Security Profiles, and URL Filtering are applied to GlobalProtect user traffic just like any other traffic traversing the firewall, ensuring consistent threat prevention.
Security Policy in High Availability (HA) Context
In a Palo Alto Networks High Availability (HA) cluster (Active/Passive or Active/Active), Security Policies, along with most other configurations, are synchronized from the active (or active-primary in A/A) device to the passive (or active-secondary) device.
- Configuration Synchronization: When you commit changes on the active firewall, the configuration (including Security Policies, objects, profiles, NAT rules, etc.) is automatically synchronized to the HA peer. This ensures policy consistency upon failover.
-
Session Synchronization:
- For stateful failover, session information is also synchronized between HA peers. This allows existing sessions to continue uninterrupted if a failover occurs.
- Security Policy decisions made for a session on the active device are inherently part of the session state that gets synchronized.
- Policy Management: Policies are managed on the active device (or through Panorama targeting the HA pair). There's generally no need to configure policies separately on the passive peer, as it will receive them via HA sync.
- Path Monitoring & Failover: While not directly Security Policy, HA path monitoring ensures that if an interface or path used by traffic matching a Security Policy fails, the firewall can failover to the peer, which will enforce the same synchronized policies.
-
Active/Active Considerations:
In an Active/Active HA setup, both firewalls actively process traffic.
- Session Owner: One firewall owns the session based on a hash of packet information. This firewall handles all policy lookups (NAT, Security, Decryption) for that session.
- Session Setup: The firewall that receives the first packet of a flow becomes the session owner and performs initial policy lookups.
- Forwarding Chip/Device (ASICs): In some A/A scenarios with specific hardware, one device might handle session setup and policy, while the other handles forwarding if the traffic ingresses/egresses on its interfaces (asymmetric flows). However, the policy decision is made by the session owner.
- Policy consistency is still maintained via configuration synchronization.
Relationship with Other PAN-OS Functions
Security Policy is central to the NGFW's operation but interacts closely with several other PAN-OS policy engines and features.
- NAT Policy: As covered, NAT Policy (Source NAT, Destination NAT, No NAT) is evaluated *before* Security Policy. Security Policy always matches on pre-NAT IP addresses . The NAT rulebase decision informs the firewall about address translation, but the original IPs are retained for the Security Policy lookup.
- Authentication Policy: Used to trigger authentication challenges (e.g., MFA, Captive Portal) for users whose identity is not yet known via User-ID. This lookup occurs *before* Security Policy if the goal is to populate User-ID mappings that Security Policy rules might depend on. For example, an Authentication Policy rule can redirect unauthenticated HTTP/HTTPS users to a Captive Portal. Once authenticated, their IP is mapped to a user, and subsequent traffic from that IP will be evaluated by Security Policies using this new User-ID information.
- Policy Based Forwarding (PBF): PBF rules allow administrators to override the firewall's standard FIB routing decisions for specific traffic flows. PBF is evaluated during the routing phase, *before* Security Policy is fully evaluated (though PBF itself uses criteria like source/destination IP, application, service to match traffic). If a PBF rule matches, it dictates the next-hop and egress interface, which then determines the destination zone for Security Policy evaluation.
- QoS Policy: Quality of Service (QoS) policies are applied *after* traffic has been allowed by a Security Policy rule and has passed Security Profile inspection. QoS is used to classify, mark, and prioritize or limit bandwidth for specific applications or users.

High-level interaction of Security Policy with other key PAN-OS policy engines.
Security Policy Management and Optimization
Policy Optimizer
The Policy Optimizer, integrated into PAN-OS and Panorama, is a powerful tool for analyzing and refining Security Policy rulebases. Its key functions include:
-
Identify Port-Based Rules:
Detects rules that use specific service ports instead of App-ID (e.g., TCP/80 instead of
web-browsing). It analyzes traffic logs for these rules and suggests App-ID based equivalents, allowing administrators to migrate to more secure, application-aware policies. - Identify Unused Rules and Objects: Highlights rules that have not matched any traffic over a specified period (hit count is zero). This helps clean up obsolete rules, reducing clutter and potential security risks. It also identifies unused address, service, or application objects.
- Rule Usage Analysis (Hit Counts): Provides detailed statistics on how often each rule is matched, helping to understand traffic patterns and validate rule necessity. Rules with unexpectedly low or high hit counts may warrant investigation.
- Identify Shadowed Rules: While not its primary function (Panorama's validation check is better for this pre-commit), analyzing traffic that *only* hits broad rules can sometimes indirectly point to specific rules below them not getting traffic as expected.
- Application Usage in Port-Based Rules: For rules currently using specific ports, Policy Optimizer shows which applications (identified by App-ID) are actually flowing through that rule. This data is crucial for safely converting port-based rules to App-ID based rules.
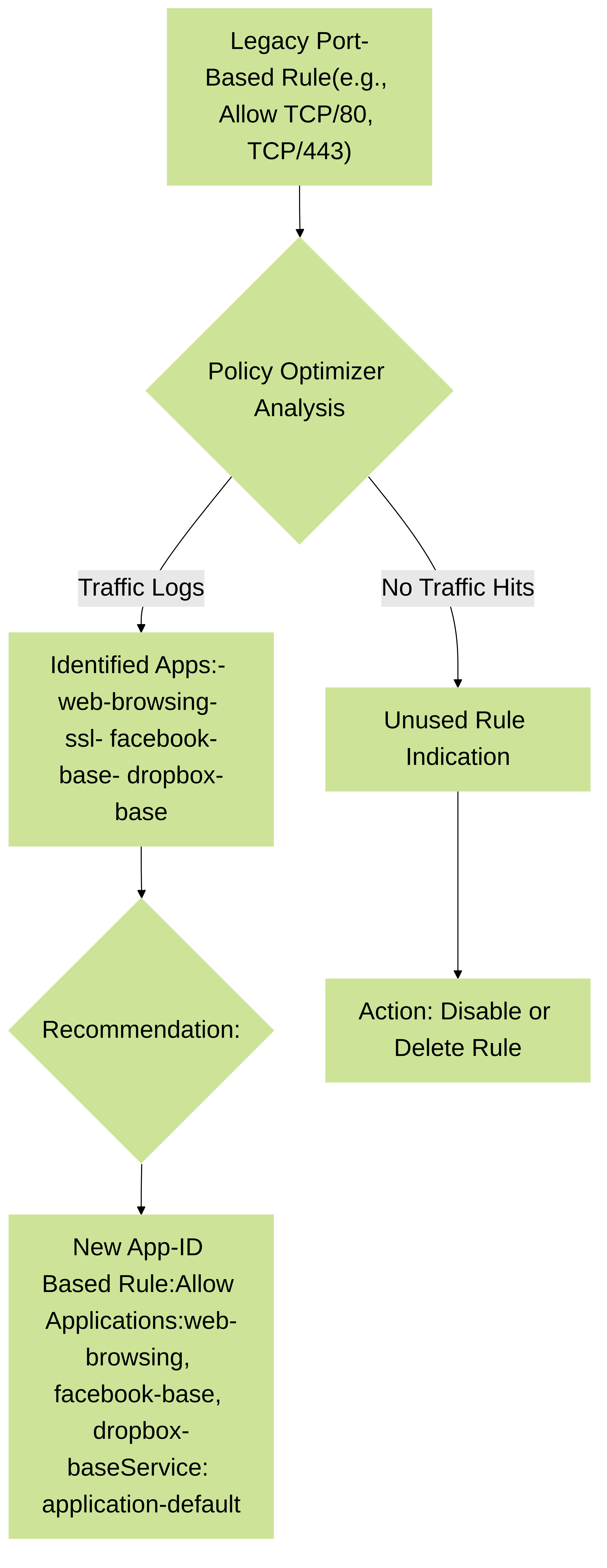
Policy Optimizer workflow for converting port-based rules to App-ID based rules.
Security Policy Best Practices
-
Clear Naming Convention:
Use a consistent, descriptive naming scheme for rules (e.g.,
TRUST-to-UNTRUST_CorpUsers_Allow-WebBrowsing-SocialMedia). Include source zone, destination zone, primary users/sources, and allowed applications/purpose. - Detailed Descriptions: Always fill in the Description field. Explain the rule's business justification, requestor, related change ticket number, and date of creation/last modification.
- Strategic Use of Tags: Use tags to categorize rules for easier filtering, searching, and understanding. Color-code tags for visual organization in the GUI. Tags are also fundamental for Dynamic Address Groups.
- Principle of Least Privilege (Specificity): Be as specific as possible. Avoid using 'any' for zones, addresses, applications, or services unless absolutely necessary and well-justified. The more granular the rule, the smaller the attack surface.
-
Prefer
application-defaultfor Services: Useapplication-defaultin the Service field whenever possible. This ensures App-ID accurately identifies the application and restricts it to its standard ports, preventing abuse of non-standard ports. -
Regular Auditing and Review:
- Periodically review rule hit counts. Investigate rules with zero hits or unexpectedly high hits.
- Use Policy Optimizer to identify unused rules/objects and opportunities for App-ID adoption.
- Check for shadowed rules before committing changes (Panorama and PAN-OS GUI show warnings).
- Consistent Threat Prevention with Security Profile Groups: Apply appropriate Security Profile Groups to all 'Allow' rules to ensure comprehensive threat inspection. Standardize these groups for different traffic profiles (e.g., a "Strict" group for DMZ servers, a "Standard" group for user internet access).
- Comprehensive Logging: Enable logging (at minimum "Log at Session End") for all rules, especially for deny rules and critical allow rules. Forward logs to Panorama and/or a SIEM for analysis, alerting, and retention. Consider "Log at Session Start" for troubleshooting specific flows but be mindful of log volume.
- Explicit Cleanup Rules: Implement explicit "deny all" cleanup rules (both intrazone and interzone) at the bottom of the rulebase (just above the implicit defaults) with logging enabled. This ensures any traffic not explicitly permitted is logged and denied.
- Change Management: Follow a formal change management process for all policy modifications. Document changes, test thoroughly, and have a rollback plan. Use commit comments to track changes.
- Regular PAN-OS and Content Updates: Keep PAN-OS, Applications and Threats, WildFire, and other content versions up to date to benefit from the latest App-IDs, threat signatures, and features.
Managing Policies with Panorama
Palo Alto Networks Panorama provides centralized network security management for multiple NGFWs. It significantly simplifies policy administration across a large deployment.
-
Device Groups and Templates/Template Stacks:
-
Device Groups:
Firewalls are organized into Device Groups. Policies (Security, NAT, QoS, Decryption, etc.) and Objects can be pushed to entire Device Groups.
- Hierarchy: Device Groups can be nested, allowing for a hierarchical policy structure (e.g., a parent "Global" Device Group with common policies, and child "Regional" Device Groups with more specific policies).
- Pre-rules and Post-rules: Within a Device Group hierarchy, you can define "Pre-rules" (evaluated before local firewall rules or rules from lower-level Device Groups) and "Post-rules" (evaluated after). This allows for enforcing global standards while permitting local customization. Pre-rules are typically for universal deny or mandatory allow rules, while Post-rules often serve as cleanup rules.
- Templates/Template Stacks: Used to manage network and device settings (interfaces, zones, server profiles, HA settings, etc.) rather than policies.
-
Device Groups:
Firewalls are organized into Device Groups. Policies (Security, NAT, QoS, Decryption, etc.) and Objects can be pushed to entire Device Groups.
-
Shared vs. Local Policies:
- Shared Policies (Panorama): Defined in Panorama and pushed to Device Groups. These are centrally managed.
- Local Policies (Firewall): Defined directly on an individual firewall. These are evaluated in conjunction with policies received from Panorama, based on the Pre-rule/Post-rule structure.
- Centralized Logging and Reporting: Panorama collects logs from all managed firewalls, providing a central repository for analysis, reporting, and threat correlation. The Application Command Center (ACC) in Panorama offers comprehensive visibility across the entire network.
- Policy Optimizer in Panorama: Policy Optimizer can be run from Panorama to analyze rulebases across multiple managed firewalls or specific Device Groups.
- Configuration Management: Panorama provides robust configuration management, versioning, and rollback capabilities for policies and settings pushed to firewalls.
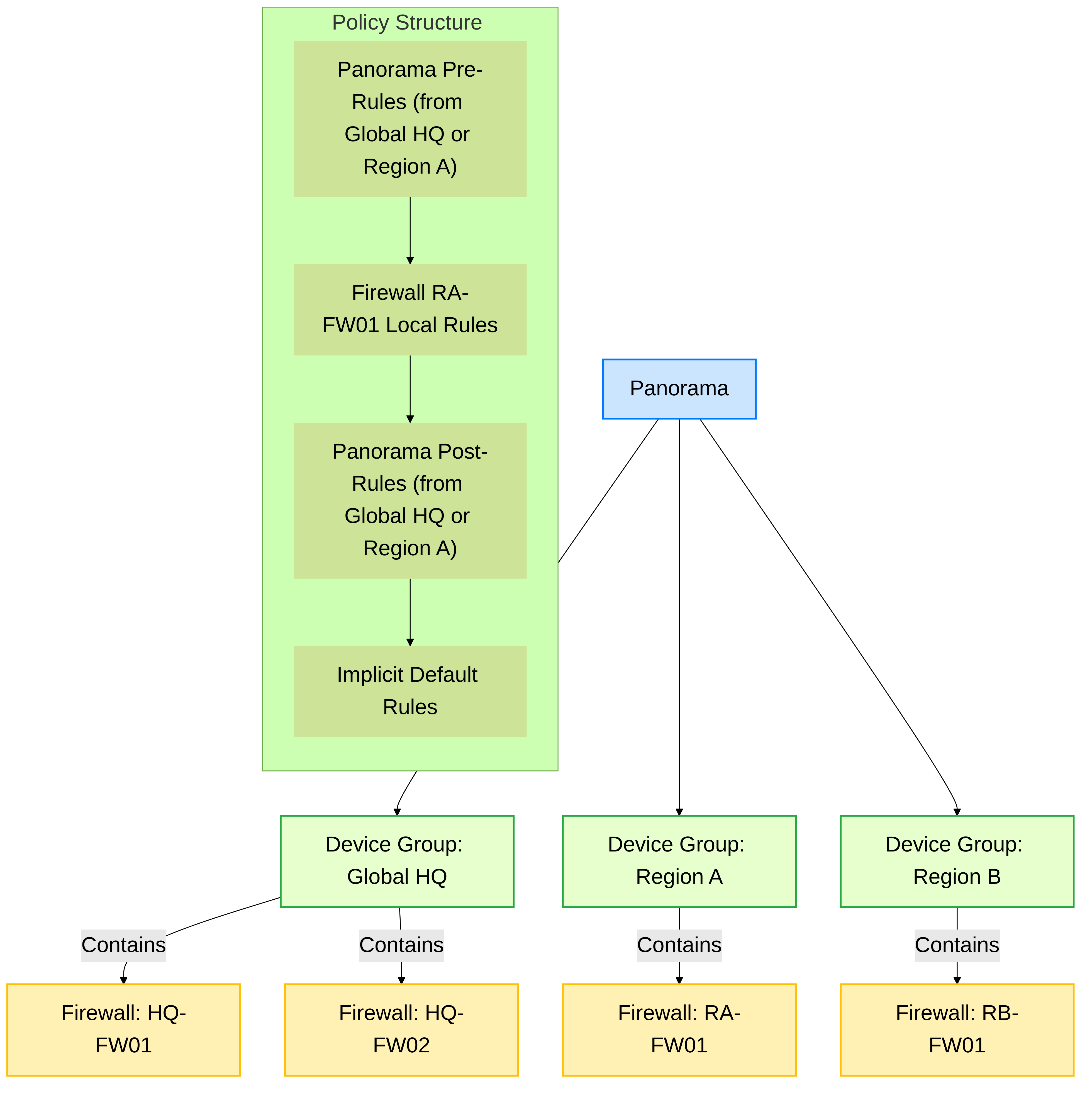
Panorama managing firewalls in Device Groups with hierarchical policy structure (Pre/Post rules).
Using the PAN-OS XML/REST API for Automation
Palo Alto Networks firewalls and Panorama offer comprehensive XML and RESTful APIs that allow for automation of configuration tasks, including Security Policy management.
- Capabilities: The API can be used to create, read, update, and delete Security Policy rules, address objects, service objects, Security Profiles, and virtually any other configuration element. It can also be used to retrieve operational data and logs.
-
Use Cases:
- Automated rule provisioning based on external triggers (e.g., a new server deployment in a CMDB).
- Integration with SIEM/SOAR platforms for automated response actions (e.g., adding an IP to a block list via an EDL or a Dynamic Address Group tag based on a threat alert).
- Bulk policy changes and migrations.
- Custom reporting and monitoring scripts.
-
Tools and Libraries:
Palo Alto Networks provides an official Python SDK (
pan-os-python) and Ansible modules (paloaltonetworks.panoscollection) that simplify interaction with the API. - Security Considerations: API access should be secured using API keys with least privilege, and communication should be over HTTPS.
Troubleshooting Security Policies
Common Issues
- Rule Shadowing: A specific rule is not being hit because a broader rule above it is matching the traffic.
- Incorrect Zone Configuration: Traffic is not matching because the source or destination zone in the rule is incorrect, or interfaces are not in the expected zones.
- Pre-NAT vs. Post-NAT Confusion: Security policy uses pre-NAT IPs. Ensure rule addresses match original IPs, not translated ones.
-
App-ID Misidentification:
App-ID may identify traffic as
unknown-tcp/udpor an unexpected application due to encryption (needs decryption), evasive techniques, or lack of signatures for custom apps.- Troubleshooting: Check traffic logs for application details. Use packet captures. Consider custom App-ID signatures or Application Override if necessary (with caution).
-
User-ID Mapping Issues:
User-based rules not working if User-ID is not correctly mapping IPs to users.
-
Troubleshooting:
Check User-ID agent status, server monitoring, group mapping. Use CLI commands like
show user ip-user-mapping ip <ip_address>.
-
Troubleshooting:
Check User-ID agent status, server monitoring, group mapping. Use CLI commands like
-
Service Mismatch (
application-default): Application is using a non-standard port and the rule usesapplication-defaultfor service.- Troubleshooting: Check traffic logs for identified App-ID and reported port. Decide whether to allow the non-standard port (by creating a custom service and a specific rule) or enforce standard port usage.
- Security Profile Blocking Traffic: An 'Allow' rule is in place, but traffic is still blocked by a Security Profile (e.g., Antivirus, URL Filtering). Check Threat logs, URL logs, WildFire Submissions logs, etc.
- Missing Decryption: App-ID or Security Profiles are ineffective because necessary SSL/TLS traffic is not being decrypted.
Essential Logs for Troubleshooting
- Traffic Logs (Monitor > Logs > Traffic): The primary source for seeing if traffic is matching rules, what action is taken, session duration, bytes transferred, and importantly, the "Session End Reason." Look for hit counts on rules. Filter by source/destination IP, port, application, etc.
- Threat Logs (Monitor > Logs > Threat): Shows threats detected and blocked by Antivirus, Anti-Spyware, and Vulnerability Protection profiles. Indicates which Security Profile and rule were involved.
- URL Filtering Logs (Monitor > Logs > URL Filtering): Shows URLs accessed, their categories, and actions taken by the URL Filtering profile.
- Data Filtering Logs (Monitor > Logs > Data Filtering): Shows instances where Data Filtering profiles detected and acted on sensitive data patterns.
- WildFire Submissions Logs (Monitor > Logs > WildFire Submissions): Tracks files and links submitted to WildFire and their verdicts.
- System Logs (Monitor > Logs > System): General firewall operational messages, including commit successes/failures, HA events, etc.
Useful PAN-OS CLI Commands
# Check if a hypothetical session would match a security policy test security-policy-match source <src_ip> destination <dst_ip> protocol <number> destination-port <port> source-zone <zone_name> destination-zone <zone_name> application <app_name> user <user_name> # Show all active sessions (can be filtered extensively) show session all show session all filter source <src_ip> destination <dst_ip> destination-port <port> show session all filter application <app_name> show session id <session_id> # Detailed view of a specific session # Show User-ID mappings show user ip-user-mapping ip <ip_address> show user user-group-mapping user <domain\user> show user group list # Show App-ID cache for a specific IP and port show FPA application-block ip <ip_address> dp0 sport <src_port> dport <dst_port> proto <protocol_num> # Debug and packet diagnostics (use with caution, can impact performance) debug dataplane packet-diag set filter match source <ip> destination <ip> destination-port <port> debug dataplane packet-diag set filter on debug dataplane packet-diag show filter debug dataplane packet-diag clear filter all debug dataplane packet-diag set capture on show counter global filter packet-filter yes delta yes # See if packets are hitting ASIC/NP clear session id <session_id> # Clear a specific problematic session to force re-evaluation
test security-policy-match
, ensure you provide accurate zone information. The destination zone is particularly important and depends on the routing decision for the given destination IP. If you are unsure, perform a route lookup first:
test routing fib-lookup virtual-router <vr_name> ip <destination_ip>
.
PCNSE Exam Focus Summary
Mastery of Security Policy is absolutely critical for success on the PCNSE exam. Pay close attention to:
- Packet Flow and Policy Evaluation Order: Know the precise sequence: NAT lookup (pre-NAT for policy), Decryption, Authentication, Route lookup (PBF/FIB for egress zone), then Security Policy lookup (using pre-NAT IPs, App-ID, User-ID, etc.), and finally Security Profile application (post-NAT) on allowed traffic.
- Pre-NAT vs. Post-NAT Context: Security Policy rules match on pre-NAT IPs . Security Profiles inspect traffic after NAT has been applied.
-
Core Matching Criteria:
Understand each criterion in depth – Zones (types), Addresses (Objects, Groups, DAGs, EDLs), App-ID (how it works, custom apps, override), User-ID (agents, mapping, groups), Service (
application-defaultimportance), URL Category (PAN-DB, custom), HIP Profiles. -
App-ID:
Its mechanisms, benefits, handling of unknown/evasive apps, and the role of
application-default. Understand the difference between App-ID and Application Override. - Rule Shadowing: Why it happens and how to prevent it (specific rules higher, general rules lower). How Policy Optimizer helps.
-
Rule Types and Default Rules:
Universal, Interzone, Intrazone. Know the behavior of
intrazone-default(allow) andinterzone-default(deny) and the best practice of explicit cleanup rules. - Security Profiles & Groups: Purpose of each major profile (AV, AS, VP, URL, File, WildFire, Data Filtering), why they are only on 'Allow' rules, and the efficiency of using Security Profile Groups. Role of WildFire and its verdicts.
- Interaction with Other Policies: How Security Policy works alongside NAT, Decryption (essential for visibility), Authentication Policy, PBF, and QoS.
- Policy Optimizer: Its key features (port-to-App-ID migration, unused rule identification).
- Panorama Management: Device Groups, Pre-rules/Post-rules concept.
-
Troubleshooting:
Common issues, key logs (Traffic, Threat, URL), and essential CLI commands like
test security-policy-matchandshow session all filter ....