Palo Alto Networks Service Routes: Mastering Firewall-Sourced Traffic for Optimal Performance and Security
Service Routes are a fundamental aspect of configuring how a Palo Alto Networks Next-Generation Firewall (NGFW) interacts with network services essential for its own operation. Understanding and correctly configuring service routes is crucial for network stability, security, and ensuring the firewall has access to critical resources like DNS servers, NTP servers, Palo Alto Networks update services, and more. This guide provides an in-depth exploration of service routes within the Palo Alto Networks ecosystem, focusing on PAN-OS, with practical examples and PCNSE exam-relevant insights.
1. Understanding Palo Alto Networks Service Routes
In PAN-OS, a Service Route dictates which network interface and source IP address the firewall uses when initiating traffic for specific, predefined system services. This is distinct from the data plane forwarding path for transit traffic (traffic passing *through* the firewall). Service routes are concerned with traffic *originating from* the firewall's management plane or control plane.
Key characteristics of Palo Alto Networks Service Routes:
- Firewall-Sourced Traffic: They apply exclusively to traffic generated by the firewall itself for services like DNS resolution, NTP synchronization, fetching updates (Antivirus, Threat Prevention, App-ID, WildFire), syslog forwarding, Panorama communication, User-ID agent connections, etc.
- Interface Selection: By default, the dedicated Management (MGT) interface is used. However, service routes allow administrators to redirect this traffic through data plane interfaces (e.g., Ethernet, Aggregate Ethernet, VLAN, Tunnel, Loopback interfaces).
- Source IP Control: Along with the interface, a specific source IP address can be configured for the outgoing service traffic. This can be the IP address of the chosen interface or a different IP assigned to that interface (e.g., a secondary IP on a loopback).
- Granular Control: Service routes can be configured on a per-service basis, offering fine-grained control over how the firewall accesses different network resources.
2. Default Service Route Configuration in PAN-OS
By default, a Palo Alto Networks firewall will use its Management (MGT) interface to source traffic for all system services. The MGT interface is typically connected to an out-of-band (OOB) management network, isolated from regular data traffic.
Services that utilize the MGT interface by default include (but are not limited to):
- DNS: For resolving FQDNs for updates, services, and URL categories.
- NTP (Network Time Protocol): For time synchronization, critical for logging, certificate validation, and HA.
- Syslog: For sending logs to external syslog servers.
- SNMP Traps: For sending SNMP alerts to Network Management Systems (NMS).
- Email (SMTP): For sending email notifications and reports.
-
Palo Alto Networks Services:
- Software Updates (PAN-OS versions).
- Content Updates (Applications and Threats, Antivirus, WildFire).
- PAN-DB URL Filtering database updates.
- Licensing and subscription activation/renewal.
- Telemetry data uploads.
- AutoFocus / Cortex Data Lake communication.
- Panorama: Communication with a Panorama management server (e.g., heartbeats, log forwarding, configuration pushes if initiated from firewall).
- User-ID: Communication with User-ID agents, domain controllers (for WMI probing), and redistribution of User-ID information.
- Authentication Services: RADIUS, TACACS+, LDAP, Kerberos requests for authenticating administrators or users (e.g., for GlobalProtect).
Implications of Default Behavior:
- Simplicity: Easy initial setup, as long as the MGT interface has reachability to required services.
- Security (Out-of-Band): Keeping management traffic separate from data plane traffic is a security best practice.
- Reachability Limitations: If the MGT interface is on a highly restricted network or an isolated OOB network without access to necessary internal or external services (e.g., internal DNS, internal NTP, Panorama), then default service routes will fail.
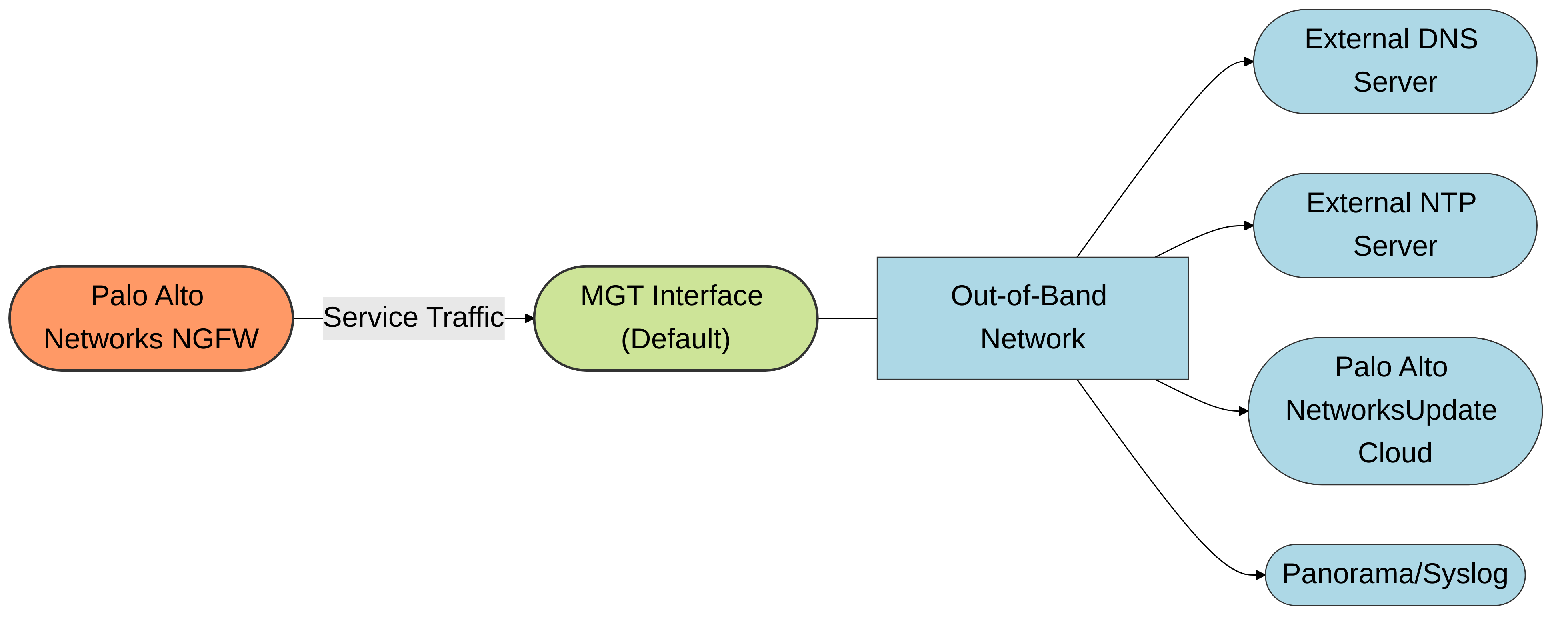
Diagram 1: Default service traffic flow using the MGT interface on a Palo Alto Networks NGFW. Firewall-originated traffic for services like DNS, NTP, and Palo Alto Networks updates exits via the MGT interface, typically to an out-of-band management network.
3. Why Customize Service Routes? Key Use Cases
Customizing service routes offers significant flexibility and is often necessary in various network designs:
- MGT Interface Isolation: In highly secure environments, the MGT interface might be completely isolated, lacking access to any internal or external services. Custom service routes allow these services to be accessed via in-band data interfaces.
-
Service Reachability:
- Internal Services: Internal DNS, NTP, Syslog servers, or Panorama might only be reachable via data plane interfaces connected to internal network segments.
- External Services with Specific Egress: Company policy might dictate that all internet-bound traffic, including firewall updates, must egress through a specific data interface or VR, not the MGT interface.
- Dedicated Service Virtual Routers (VRs): For enhanced segmentation, a dedicated VR might be created for management traffic. Service routes would then direct service traffic to an interface within this dedicated VR.
- Using Loopback Interfaces: Configuring a loopback interface as the source for service traffic provides a stable, always-on IP address, which is beneficial in HA (High Availability) scenarios or when physical interface IPs might change. The loopback must be part of a VR that has routes to the destination service.
- Traffic Segmentation and Policy Enforcement: By directing service traffic through a data interface, it becomes subject to security policies applied to that zone/interface, allowing for more granular control and visibility.
- High Availability (HA) Considerations: While the service route configuration itself is synced between HA peers, the actual path taken depends on which firewall is active and the reachability from its interfaces. Using loopback interfaces with floating IPs can simplify service reachability in HA.
- Panorama Connectivity: Ensuring reliable communication with Panorama, especially if Panorama is deployed in a location not directly reachable via the MGT interface.
- Cloud Service Integration: For firewalls connecting to Palo Alto Networks cloud services (like Cortex Data Lake), service routes can ensure traffic to these services uses an appropriate path.
4. Customizing Service Routes in PAN-OS
Service routes are configured in PAN-OS via the WebUI or CLI.
4.1. GUI Configuration (Device > Setup > Services)
- Navigate to Device > Setup > Services .
-
In the "Services" tab, locate the
Service Route Configuration
section and click
Customize
.
PCNSE/PCNSA Exam Note (Palo Alto Networks): Remember this navigation path. It's a common point of reference in exam questions.
-
The "Service Route Configuration" dialog appears, listing predefined services.
By default, all services are set to use the "Default (Management Interface)" option. -
To customize a service:
- Select the tab for the service category (e.g., DNS, NTP, Palo Alto Networks Services).
- Find the specific service you want to modify (e.g., "DNS Primary Server," "WildFire Updates").
-
From the
Source Interface
dropdown, select the desired interface. This list will include:
-
Physical Ethernet interfaces (e.g.,
ethernet1/1) - Aggregate Ethernet (AE) interfaces
- VLAN interfaces
- Tunnel interfaces
- Loopback interfaces
-
Physical Ethernet interfaces (e.g.,
-
From the
Source Address
dropdown:
- Use Interface IP Address: The firewall will use the primary IP address configured on the selected Source Interface.
- Specific IP Address: Allows you to choose any IP address configured on the selected interface (including secondary IPs if configured, or IPs on subinterfaces). This is useful if an interface has multiple IPs and you need to source from a specific one.
-
Custom Services/Destinations:
- If a service or specific destination IP is not listed under the predefined service tabs, you can use the Destination tab.
- Click Add under the Destination tab.
- Enter the IP Address or FQDN of the custom destination service.
- Select the Source Interface and Source Address as described above for this custom destination.
- This is commonly used for internal syslog servers, specific LDAP servers, or other internal management tools.
- Click OK to save the changes in the dialog.
- Commit the changes to the firewall for them to take effect.
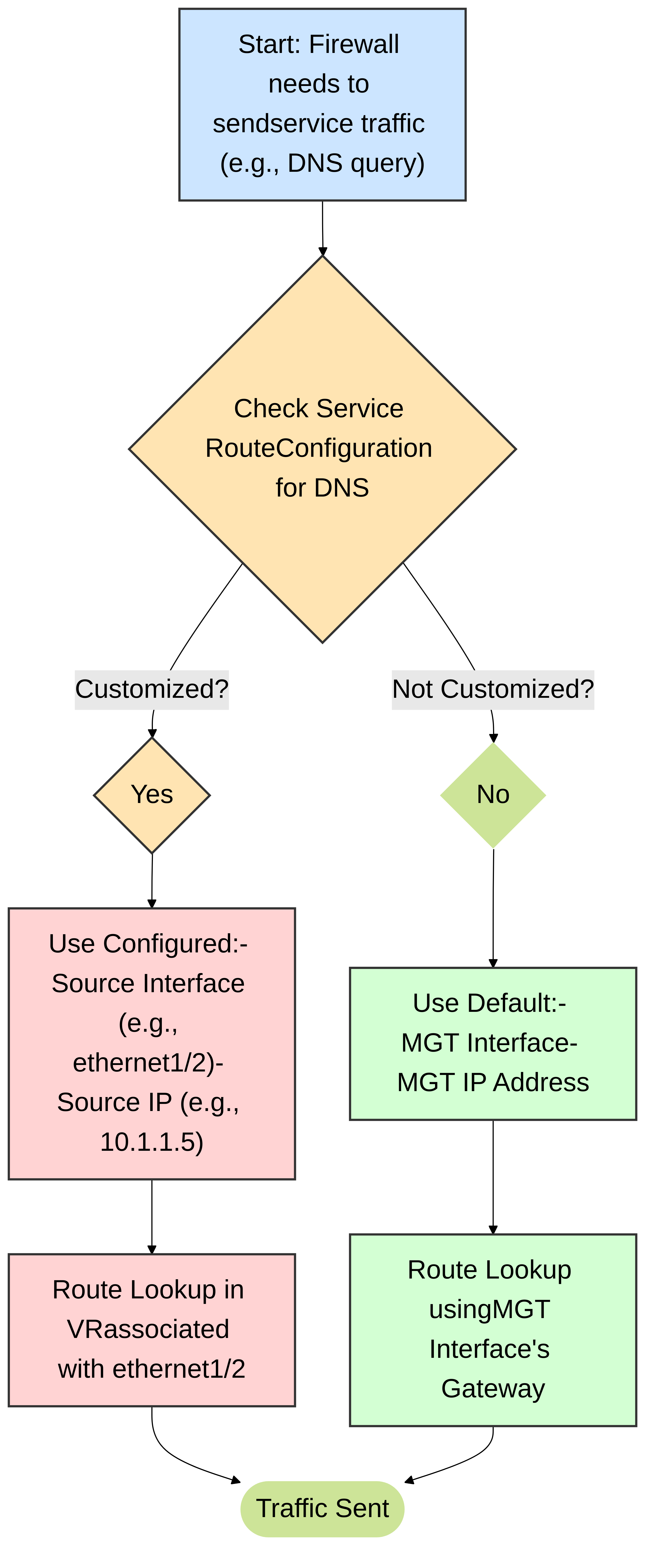
Diagram 2: Conceptual decision logic for service routing in PAN-OS. The firewall checks if a custom service route is defined for the specific service. If yes, it uses the configured interface and source IP; otherwise, it defaults to the MGT interface.
4.2. CLI Configuration (PAN-OS)
Service routes can also be configured using the PAN-OS CLI. This is useful for automation or quick changes.
Basic Syntax:
set deviceconfig system route service <service_name> source interface <interface_name> address <ip_address | use-interface-ip>
set deviceconfig system route service destination <ip_address_or_fqdn> source interface <interface_name> address <ip_address | use-interface-ip>
Examples:
-
Configure DNS to use ethernet1/1 and its primary IP:
admin@PA-VM> configure Entering configuration mode [edit] admin@PA-VM# set deviceconfig system route service dns source interface ethernet1/1 address use-interface-ip [edit] admin@PA-VM# commit -
Configure Syslog to use loopback.1 with a specific IP 10.100.100.1 (assuming this IP is configured on loopback.1):
admin@PA-VM# set deviceconfig system route service syslog source interface loopback.1 address 10.100.100.1 -
Configure a custom destination (e.g., an internal NTP server 192.168.1.254) to use ethernet1/2:
admin@PA-VM# set deviceconfig system route service destination 192.168.1.254 source interface ethernet1/2 address use-interface-ip
Viewing Service Route Configuration via CLI:
admin@PA-VM> show running SCMGR_SERVICE_ROUTE_CONFIG
admin@PA-VM> show routing service-routes
The `show routing service-routes` command is particularly useful as it displays the currently effective service routes being used by the system for various services.
5. Interaction with Virtual Routers (VRs) and Routing Table
When a service route is configured to use a data interface, the firewall relies on the Virtual Router (VR) associated with that interface to find a path to the service's destination.
- VR Assignment: Each data interface (physical, VLAN, loopback, tunnel) must be assigned to a VR.
- Route Lookup: When the firewall initiates traffic for a service (e.g., DNS query to 8.8.8.8) using a data interface specified in a service route (e.g., `ethernet1/1`), it performs a route lookup in the VR to which `ethernet1/1` belongs.
- Reachability is Key: The VR must have a route (static, OSPF, BGP, etc.) that directs traffic destined for the service's IP address out of an appropriate interface. If no such route exists in the VR, the service communication will fail.
- MGT Interface Routing: When using the default MGT interface, routing is typically handled by the default gateway configured for the MGT interface (Device > Setup > Management > Management Interface Settings). The MGT interface has its own isolated routing context, separate from data plane VRs.
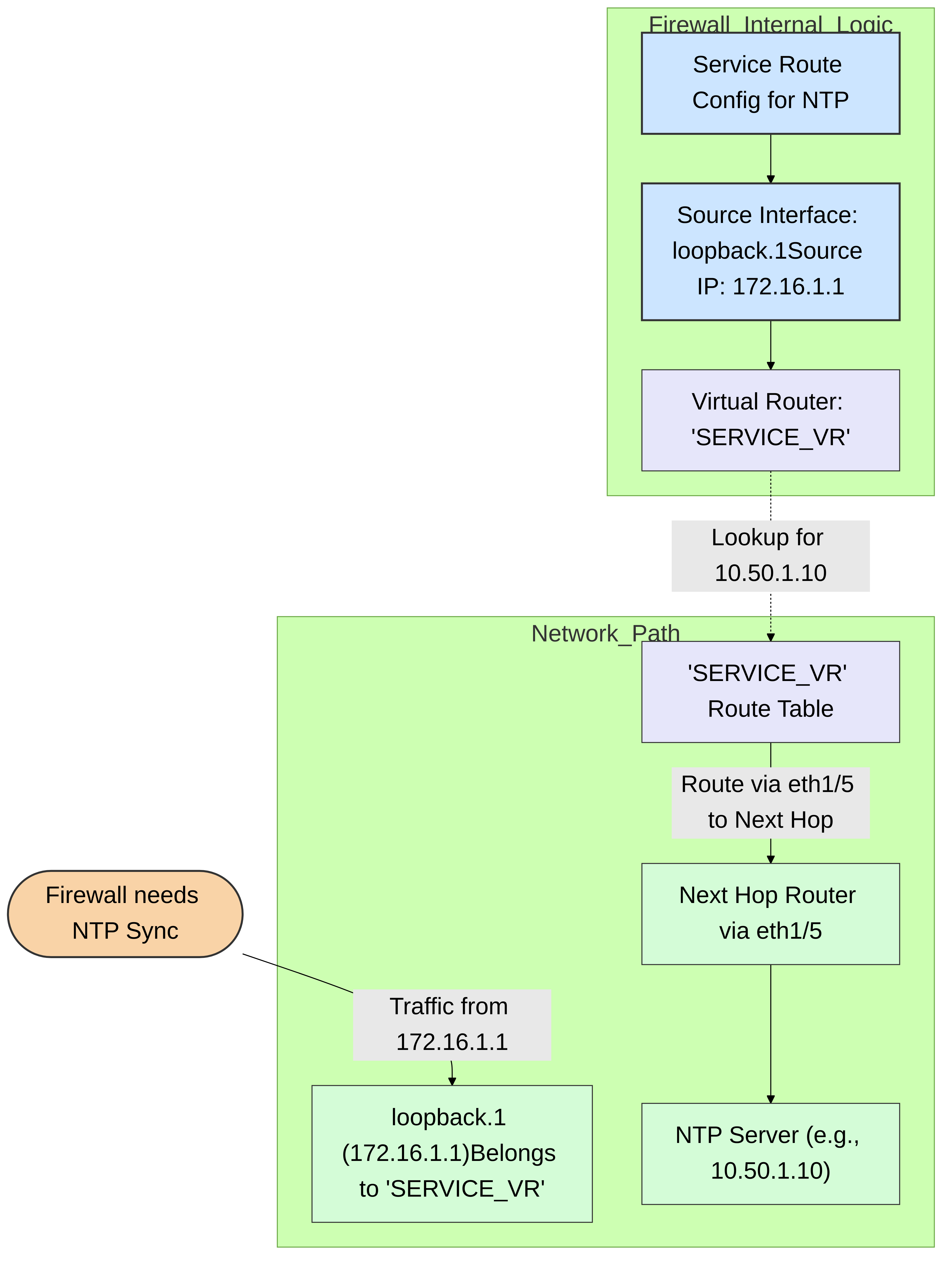
Diagram 3: Service route using a loopback interface within a specific Virtual Router ('SERVICE_VR'). The firewall sources NTP traffic from `loopback.1`. The 'SERVICE_VR' must have a route to the NTP server for communication to succeed.
6. Key Services and Specific Service Route Considerations
Different services have unique considerations when configuring service routes:
-
DNS:
- Importance: Essential for resolving FQDNs for Palo Alto Networks updates (updates.paloaltonetworks.com), URL filtering categories, WildFire, etc.
- Consideration: If internal DNS servers are used, ensure the firewall can reach them via the chosen service route interface and VR. If using public DNS, ensure internet reachability.
-
NTP:
- Importance: Critical for accurate timestamps in logs, certificate validation (TLS/SSL decryption, GlobalProtect), and HA synchronization. Time skew can cause numerous issues.
- Consideration: Prioritize reliable NTP servers. Internal NTP servers are often preferred for stability and security.
-
Palo Alto Networks Updates (Content-ID, App-ID, AV, WildFire, PAN-DB):
- Importance: Keeps security protections up-to-date.
- Consideration: These services typically require internet access to Palo Alto Networks update servers (e.g., `updates.paloaltonetworks.com`, `wildfire.paloaltonetworks.com`). The chosen interface must have a path to the internet. Consider proxy settings if direct internet access is not allowed (`Device > Setup > Services > Service Route Configuration > Proxy Server`).
-
Panorama:
- Importance: For centralized management, logging, and reporting.
- Consideration: If Panorama is managed in-band, ensure the service route for Panorama uses an interface that can reach the Panorama IP address. This includes Device Group and Template pushes initiated from Panorama to the firewall as well as log forwarding and heartbeats from the firewall to Panorama.
-
Syslog:
- Importance: Sending logs to external SIEMs or log collectors.
- Consideration: Ensure the firewall can reach the syslog server(s) IP address and port (typically UDP/514 or TCP/6514 for secure syslog) via the chosen interface and VR.
-
User-ID (LDAP, AD Monitor, Agent Communication):
- Importance: For mapping users to IP addresses for policy enforcement.
- Consideration: If the firewall needs to connect to domain controllers (for agentless User-ID) or User-ID agents, the service route for LDAP (for server monitoring) or custom destinations (for agents) must use an interface with reachability to these components.
-
RADIUS/TACACS+/LDAP (Admin Authentication):
- Importance: For authenticating administrators accessing the firewall.
- Consideration: The interface chosen for these service routes must be able to reach the respective authentication servers.
7. Advanced Scenarios and Best Practices
-
Using Loopback Interfaces for Stability:
- Configure a loopback interface, assign it an IP address, and place it in an appropriate VR.
- Use this loopback interface and its IP as the source for critical services (NTP, Syslog, Panorama).
- Benefit: The loopback interface is always "up" as long as the firewall is operational and its IP address remains stable, even if physical interfaces go down or change. This is particularly valuable in HA environments.
-
Service Routes in Multi-VR Environments:
- If using multiple VRs, carefully plan which VR will handle specific firewall-sourced services.
- For instance, general internet-bound updates might go through a "WAN_VR," while internal management services (Syslog, internal NTP) might use an interface in an "INTERNAL_MGMT_VR."
- Ensure inter-VR routing or appropriate interface placement if a service in one VR needs to reach a destination accessible only via another VR (though direct interface placement in the correct VR is simpler).
-
Security Policies for Service Traffic:
- When service traffic is routed through a data interface, it becomes subject to the Security Policy rules of the zone that interface belongs to.
- Ensure you have appropriate "allow" rules if your default inter-zone or intra-zone policy is "deny." For example, if DNS traffic is sourced from an interface in the "TRUST" zone to an external DNS server in the "UNTRUST" zone, a policy allowing DNS from TRUST to UNTRUST for the firewall's source IP would be needed.
- However, traffic originating from the firewall and egressing an interface is often implicitly allowed or handled by specific rules related to firewall-sourced traffic, but it's good practice to be aware of zone protection profiles and security policy implications. For traffic *to* the firewall (like an NTP server responding), security policies apply.
-
High Availability (HA) and Service Routes:
- Service route configurations are synchronized between HA peers.
- If using interface IP addresses, ensure the active firewall's interface has connectivity.
- Using loopback interfaces with floating IPs (if applicable and configured) can provide more seamless failover for services sourced from them, as the floating IP moves to the active peer.
- Test service functionality after HA failover.
- Order of Operations: Service routes are specific overrides for firewall-sourced traffic. They are checked *before* the firewall consults its main MGT interface routing settings for these services.
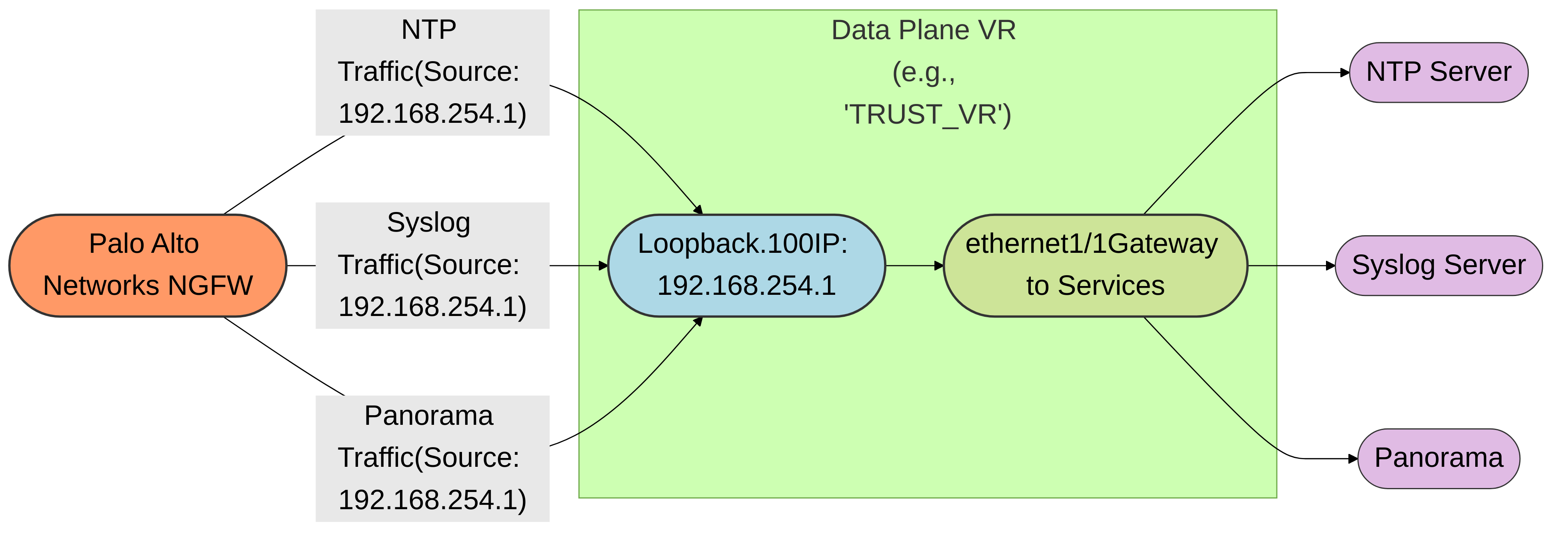
Diagram 4: Using a Loopback interface as a stable source for multiple services. Traffic for NTP, Syslog, and Panorama originates from the Loopback interface's IP address, and is then routed through the Data Plane VR.
8. Troubleshooting Service Route Issues
If firewall services are failing (e.g., not getting updates, time not syncing), service routes are a key area to investigate.
-
Verify Service Route Configuration:
- GUI: Device > Setup > Services > Service Route Configuration. Check if the intended service is customized and points to the correct interface and source IP.
-
CLI:
`show routing service-routes`. This command shows the *effective* routes the system is currently using for each service. This is very helpful to confirm your configured settings are active.
admin@PA-VM> show routing service-routes Service Source Interface Source IP Destination ---------------- ---------------- ----------------- ------------------------------ dns ethernet1/1 10.1.1.10 (configured DNS servers) ntp loopback.1 172.16.0.1 (configured NTP servers) updates management 192.168.1.100 updates.paloaltonetworks.com syslog ethernet1/2 10.1.2.10 10.10.10.5
-
Check Interface Status:
-
Ensure the chosen source interface (MGT or data) is up and has the configured IP address.
admin@PA-VM> show interface <interface_name> admin@PA-VM> show interface management
-
Ensure the chosen source interface (MGT or data) is up and has the configured IP address.
-
Verify Routing from the Source VR:
-
If using a data interface, verify the VR associated with that interface has a route to the service destination.
admin@PA-VM> test routing fib-lookup virtual-router <vr_name> ip <destination_ip_of_service>This command will show the egress interface and next-hop used to reach the destination from that VR. If it shows "no route," then routing is the issue. -
For the MGT interface, check its default gateway: `Device > Setup > Management > Management Interface Settings`. Ping the gateway from the firewall CLI: `ping source
host `.
-
If using a data interface, verify the VR associated with that interface has a route to the service destination.
-
Test Connectivity from Firewall CLI:
-
Use `ping`, `traceroute`, or service-specific test commands from the firewall CLI, specifying the source interface or IP if possible.
admin@PA-VM> ping source <source_ip_from_service_route> host <destination_ip_of_service> admin@PA-VM> test dns-proxy dns-req fqdn updates.paloaltonetworks.com server <dns_server_ip> admin@PA-VM> test ntp-sync admin@PA-VM> show ntp
-
Use `ping`, `traceroute`, or service-specific test commands from the firewall CLI, specifying the source interface or IP if possible.
-
Check Traffic Logs:
- If service traffic is routed through a data interface, it might generate entries in the Traffic log (Monitor > Logs > Traffic). Filter by the firewall's source IP and the service's destination IP/port. This can show if traffic is being allowed or denied by security policies.
-
Packet Captures:
-
Take packet captures on the expected egress interface (MGT or data) to see if the firewall is attempting to send traffic and if responses are being received.
admin@PA-VM> debug dataplane packet-diag set capture stage firewall file mycap.pcap interface <interface_name> admin@PA-VM> debug dataplane packet-diag set capture filter match source <source_ip> destination <dest_ip> destination-port <port> admin@PA-VM> debug dataplane packet-diag set capture on ... perform test ... admin@PA-VM> debug dataplane packet-diag set capture off # Then view the capture file (e.g., by exporting it)
-
Take packet captures on the expected egress interface (MGT or data) to see if the firewall is attempting to send traffic and if responses are being received.
-
System Logs:
- Check Monitor > Logs > System for errors related to specific services (e.g., "Failed to resolve FQDN," "NTP server unreachable").
9. Service Routes vs. Management Interface Settings
It's important to distinguish between Service Route Configuration and Management Interface Settings:
-
Management Interface Settings (Device > Setup > Management):
- Defines the IP address, netmask, and default gateway for the dedicated MGT interface.
- Controls which services are permitted *to* the MGT interface (e.g., HTTPS, SSH, SNMP).
- This is about configuring the MGT port itself and its basic network connectivity.
-
Service Route Configuration (Device > Setup > Services):
- Determines which interface (MGT or a data interface) and source IP the firewall uses when *initiating* traffic for specific system services (DNS, NTP, updates, etc.).
- Overrides the default behavior of using the MGT interface for these outbound connections.
While the MGT interface settings provide the default path if service routes are not customized, service routes offer a more granular mechanism to redirect this specific firewall-originated traffic through other interfaces as needed.