Mastering Destination-Based Service Routes in Palo Alto Networks Firewalls
1. Introduction to Service Routes and Firewall-Generated Traffic
Palo Alto Networks Next-Generation Firewalls (NGFWs) not only inspect and control transit traffic passing through them but also generate their own traffic for various operational and security services. This firewall-generated (or firewall-sourced) traffic includes:
- DNS Queries: For resolving FQDNs used in policies, EDLs, or service lookups.
- NTP Updates: To synchronize the firewall's clock.
- Palo Alto Networks Services: Communication with Panorama, WildFire, Cortex Data Lake, content/threat update servers, and licensing servers.
- Authentication Services: Queries to RADIUS, TACACS+, LDAP, or Kerberos servers.
- Logging: Sending logs to external syslog servers or Cortex Data Lake.
- External Dynamic Lists (EDLs): Fetching updates for IP address lists, URL lists, or domain lists.
- SNMP Traps and Email Alerts.
By default, the firewall uses its management (MGT) interface for many of these services. However, for services that need to egress through a data plane interface, or when more granular control is required, Service Routes come into play.
There are two main types of service routes in PAN-OS:
- Standard Service Routes: These allow you to specify the source interface and IP address for predefined services (e.g., DNS, NTP, Panorama, WildFire). You select the service type from a list.
- Destination-Based Service Routes: These provide even more granular control by allowing you to define a specific source interface and IP address for traffic destined to a *particular external IP address*, regardless of the service type. This is particularly useful for custom services or overriding default routing for specific destinations.
This guide focuses in-depth on Destination-Based Service Routes , exploring their purpose, configuration, use cases, and implications within the Palo Alto Networks ecosystem.
2. Overview of Destination-Based Service Routes
Destination-based service routes in Palo Alto Networks firewalls allow administrators to explicitly define the source interface and source IP address that the firewall will use when initiating traffic to a specific external destination IP address. This capability is crucial for scenarios where the firewall's default routing behavior for its own traffic (often via the MGT interface or a data plane default route) is not suitable or needs to be overridden for particular external services.
Key characteristics:
- Granular Control: Targets specific destination IP addresses.
-
Source Specification:
Allows selection of a data plane interface (e.g.,
ethernet1/1,ae1) or the MGT interface, and a source IP address associated with that interface. - FIB Override: For firewall-generated traffic to the specified destination, these routes take precedence over the standard FIB (Forwarding Information Base) lookup that would typically determine the egress interface.
-
Global Configuration:
Configured under
Device > Setup > Services > Service Route Configuration > Destination. These settings are global to the firewall device and apply to all Virtual Systems (VSYS) if configured. They cannot be configured on a per-VSYS basis.
3. Common Use Cases for Destination-Based Service Routes
Destination-based service routes address several specific routing challenges for firewall-generated traffic:
-
Accessing Custom or Unlisted External Services:
When the firewall needs to connect to an external service (e.g., a proprietary threat intelligence feed, a specific partner API, a non-standard logging server) that is not among the predefined services in PAN-OS, a destination-based service route can ensure traffic to that service's IP address originates from the correct interface and IP.
Example: Forcing firewall communication to a custom vulnerability scanner at203.0.113.75to egress viaethernet1/4using IP10.10.40.5. -
Precise Egress Control in Multi-VR or Multi-ISP Environments:
In firewalls with multiple Virtual Routers (VRs) or connections to multiple ISPs, the default route for firewall-generated traffic might not always be the desired path for all external services. Destination-based service routes allow you to pinpoint the egress path for specific destinations.
Example: If VR-Default routes via ISP-A, but communication to a specific Panorama regional collector (e.g.,198.51.100.100) must use ISP-B connected viaethernet1/2(associated with VR-ISP-B), a destination service route can enforce this. -
Overriding General FIB Entries for Specific Firewall-Sourced Traffic:
Even if a general service route (e.g., for "Palo Alto Networks Updates") is configured to use a particular interface, you might need to send update traffic destined to a *specific* update server IP address (e.g., a private update server within the organization) via a different path. A destination-based service route for that specific IP will take precedence. -
Dedicated Path for Critical Infrastructure Communication:
Ensuring that firewall communication to critical external systems, like a Security Operations Center (SOC) log collector or a specific authentication server, uses a highly available or preferred network path, distinct from general internet-bound firewall traffic. -
Using Data Interfaces for MGT-like Services:
While the MGT interface is often used for management services, some security policies or network designs might require certain "management-like" traffic (e.g., NTP, specific syslog destinations) to egress via a data plane interface for reasons like network segmentation, higher bandwidth, or specific routing needs.
4. Configuration Steps (PAN-OS GUI and CLI)
Configuring destination-based service routes involves specifying the target destination IP and the desired source interface and IP address on the firewall.
4.1. PAN-OS Web Interface (GUI)
- Navigate to Device > Setup > Services .
- In the "Service Route Configuration" section, click the gear icon or Edit (text may vary slightly by PAN-OS version).
- Select the Destination tab. (The default "Service" tab is for standard service routes).
- Click Add to create a new destination-based service route.
-
In the "Destination Service Route" dialog:
-
Destination:
Enter the specific IPv4 or IPv6 address of the external service the firewall needs to reach. This must be a host address (e.g.,
198.51.100.10/32or simply198.51.100.10). Network addresses with masks other than /32 (IPv4) or /128 (IPv6) are not typically used here as it's for specific destinations. - Source Interface: Select the firewall interface from which this traffic should originate. This can be a physical Ethernet interface, an Aggregate Ethernet (AE) interface, a VLAN interface, a Tunnel interface, or the MGT interface.
-
Source Address:
- Choose an IP address configured on the selected "Source Interface."
- You can often select "Use Interface IP Address" if the interface has a single primary IP, or select a specific IP if multiple are configured (e.g., secondary IPs on the interface).
- For the MGT interface, it will typically be its configured IP address.
-
Destination:
Enter the specific IPv4 or IPv6 address of the external service the firewall needs to reach. This must be a host address (e.g.,
- Click OK to save the route.
- Click OK again in the "Service Route Configuration" window.
- Commit the changes to the firewall.
Device > Setup > Services > Service Route Configuration > Destination
. Know the parameters required: Destination IP, Source Interface, and Source Address.
4.2. PAN-OS Command Line Interface (CLI)
You can also configure destination-based service routes using PAN-OS CLI commands.
configure set deviceconfig system service route destination <destination_ip_address> interface <source_interface_name> source-address <source_ip_address> # Example for IPv4: set deviceconfig system service route destination 198.51.100.50 interface ethernet1/1 source-address 10.1.1.254 # Example for IPv6: set deviceconfig system service route destination 2001:db8::100 interface ethernet1/2 source-address 2001:db8:0:2::1 # To view configured destination service routes: show deviceconfig system service route destination # To remove a destination service route: delete deviceconfig system service route destination <destination_ip_address> # After configuration, commit the changes: commit
Replace
<destination_ip_address>
,
<source_interface_name>
(e.g.,
ethernet1/1
,
mgt
), and
<source_ip_address>
with your specific values. The
source-address
should be an IP configured on the chosen
source-interface
.
5. Routing Logic and Precedence for Firewall-Generated Traffic
Understanding how PAN-OS selects an egress path for its own traffic is critical when implementing any type of service route. For traffic generated by the firewall to an external destination, PAN-OS evaluates routing options in a specific order:
-
Management (MGT) Interface Routes:
- If the MGT interface is configured with an IP address and default gateway, services hardcoded or configured to use the MGT interface (like Panorama by default, or DNS/NTP if source interface is set to MGT) will attempt to use this path.
- If a static route is defined specifically for the destination IP via the MGT interface's routing table, that will be preferred for MGT-sourced traffic.
-
Destination-Based Service Routes:
- If a destination-based service route exists for the *exact destination IP address* the firewall is trying to reach, this route will be used. This takes high precedence for data plane interfaces.
- This allows for very specific overrides.
-
Standard Service Routes (by Service Type):
- If no matching destination-based service route is found, the firewall checks if a standard service route is configured for the *type of service* generating the traffic (e.g., DNS, NTP, WildFire, Palo Alto Networks Updates).
- If a matching service-type route exists, the firewall uses the source interface and IP specified in that route.
-
Data Plane FIB Lookup (Default Route):
- If none of the above specific routes match, the firewall will perform a lookup in the Forwarding Information Base (FIB) of the Virtual Router associated with the data plane interface it would typically use by default (often the VR tied to its default outbound data path, or the VR chosen by an internal selection logic if multiple exist).
- This usually results in the traffic using the default route configured in that Virtual Router. The source IP will be selected based on the egress interface's IP.
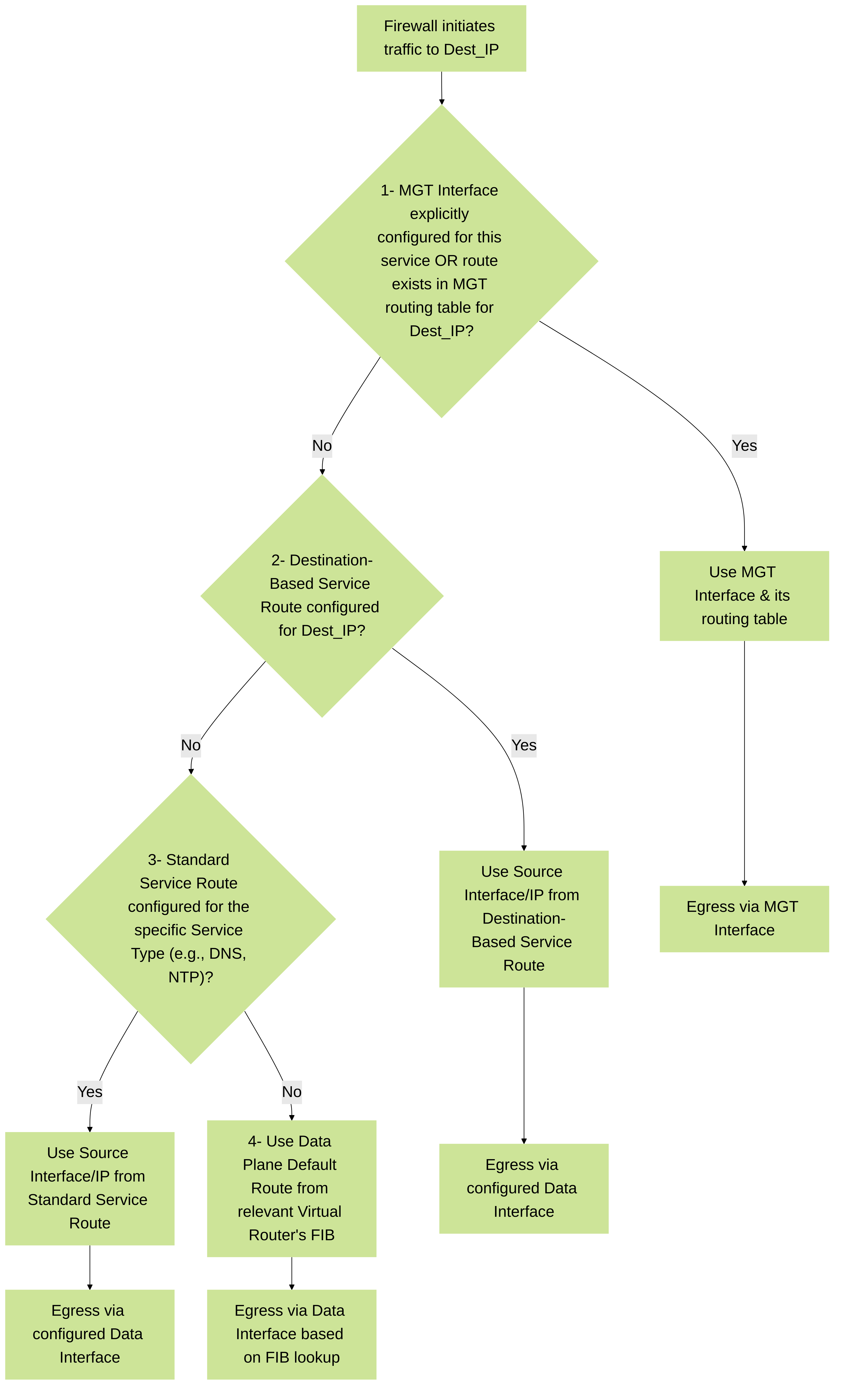
Simplified decision flow for routing firewall-generated traffic in PAN-OS. This illustrates the precedence of MGT interface routing, destination-based service routes, standard service routes, and finally, the data plane FIB.
X.X.X.X
will override a standard service route (e.g., for "DNS") if the DNS server's IP is
X.X.X.X
. The most specific match (destination IP) wins. If multiple service routes (standard or destination-based) could potentially apply, the most specific one for the *destination IP* takes precedence if it's a destination-based route.
6. Advanced Considerations and Best Practices
- Global Scope Implication: Since destination-based service routes are global, they apply across all VSYS on the firewall. If you have a multi-VSYS environment and need different source IPs for the same destination IP from different VSYS, this feature cannot achieve that directly. You might need to consider architectural alternatives or ensure the global setting meets the needs of all VSYS.
- Source IP Address Selection: Always ensure the "Source Address" chosen for the service route is a valid IP address configured on the selected "Source Interface" and that this IP is routable towards the destination. Using an incorrect source IP can lead to communication failures.
- Interaction with NAT: Service routes determine the source IP and egress interface *before* any potential Source NAT (SNAT) that might apply to firewall-generated traffic. Typically, for firewall-originated traffic, you control the source IP via the service route itself, and SNAT is not usually applied unless there's a very specific scenario.
- High Availability (HA): In an HA active/passive pair, service route configurations are synchronized. The active firewall will use the service routes. Ensure that the source IPs and interfaces specified are valid and operational on both HA peers (or that interface IP addressing is consistent, e.g., using floating IPs where appropriate for the interface type if the service route refers to such an IP).
-
Monitoring and Verification:
-
Use session logs (
Monitor > Logs > Traffic) to verify the source IP and egress interface for firewall-generated traffic. Filter by the firewall's IP addresses as source or destination. -
For specific services like DNS, check the System logs (
Monitor > Logs > System).
-
Use session logs (
-
Troubleshooting:
If traffic is not egressing as expected:
- Double-check the destination IP in the service route configuration for typos.
- Verify the selected source interface is up and has correct IP addressing.
- Ensure the chosen source IP is correct for that interface.
- Check upstream routing from the chosen egress interface to the destination.
-
Use CLI commands like
test routing fib-lookup ip <destination_ip> virtual-router <vr_of_the_source_interface>to see how the firewall would route to the destination from the perspective of the VR that owns the service route's source interface. Note: this command checks the data plane FIB, service routes are a pre-FIB decision for firewall's own traffic. A better test for firewall-sourced traffic is often to generate the traffic (e.g.,ping source <service_route_source_ip> host <destination_ip>) and check session details. -
Run a packet capture on the firewall for the specific traffic flow (
Monitor > Packet Capture).
- Use Sparingly and Specifically: While powerful, overuse of destination-based service routes can make routing for firewall-generated traffic complex to manage. Use them when necessary for specific requirements that cannot be met by MGT interface routing or standard service routes.
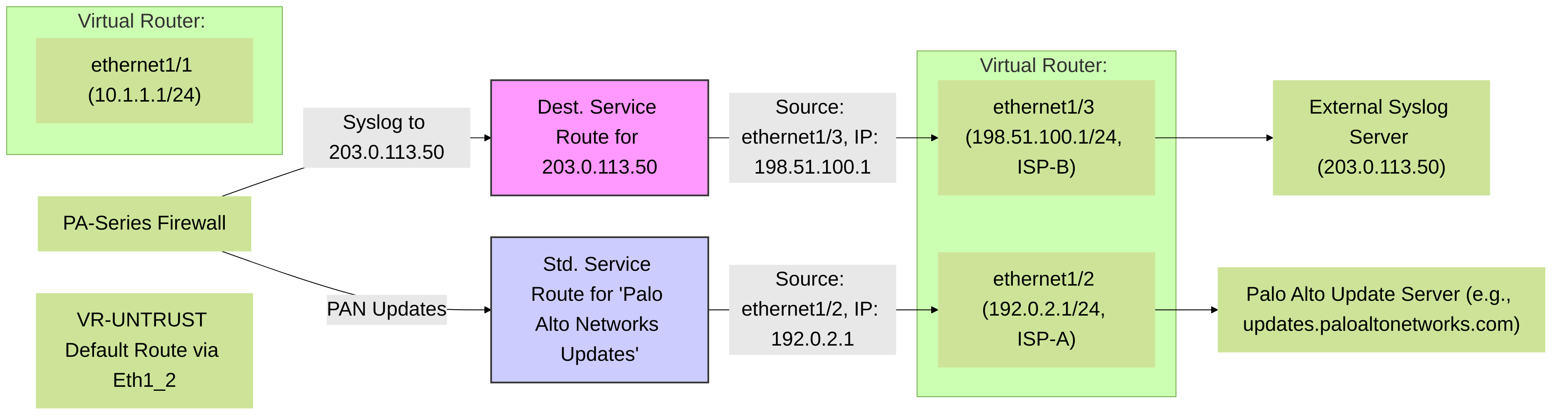
Example scenario: Firewall uses a destination-based service route to send syslog traffic to `203.0.113.50` via `ethernet1/3` (ISP-B), while standard service routes direct Palo Alto Networks updates via `ethernet1/2` (ISP-A). This overrides the default route in VR-UNTRUST for the specific syslog destination.
7. Verification and Troubleshooting CLI Commands
Several CLI commands are invaluable for verifying and troubleshooting service route configurations and their effects on firewall-generated traffic.
| Command | Purpose and Usage |
|---|---|
show deviceconfig system service route destination
|
Displays all configured destination-based service routes. Shows destination IP, source interface, and source IP. |
show deviceconfig system service route service all
|
Displays all configured standard service routes (for predefined services). Useful to see the complete picture of service routing. |
show session all filter source <firewall_service_route_source_ip> destination <external_destination_ip>
|
Checks active sessions originating from the firewall using the specified service route source IP to the target destination. Verifies if traffic is indeed using the configured path. |
show session id <session_id>
|
Provides detailed information about a specific session, including ingress/egress interface and source/destination IPs. Useful after identifying a relevant session ID. |
test routing fib-lookup ip <destination_ip> virtual-router <vr_name>
|
Shows how the specified Virtual Router would route traffic to the destination IP. While service routes override this for firewall-generated traffic, it's useful for understanding the underlying data plane routing. The
<vr_name>
should be the VR associated with the service route's source interface.
|
ping source <service_route_source_ip> host <destination_ip>
|
Tests connectivity from the firewall using the specific source IP defined in the service route. This is a direct way to test if the service route is functioning for ICMP. |
show counter global filter delta yes aspect mgmt_plane_routing_decision
(May vary by PAN-OS version or require debug)
|
Can show counters related to routing decisions made by the management plane. More advanced and might require TAC assistance for interpretation. |
debug routing pbf basic yes
debug routing pbf detail yes
(Followed by traffic generation and then
undebug all
)
|
While PBF is for transit traffic, some routing debugs can provide insights into how the firewall is processing path selection. Use with caution in production. Service route decisions are usually made before PBF evaluation for firewall-originated traffic. More specific debugs for the management plane routing (
debug management-server process general routing detail
or similar, depending on PAN-OS version and process) might be needed for deep dives, often guided by Palo Alto Networks TAC.
|
show deviceconfig system service route destination
and how to interpret its output. Understanding how to use
ping source
for verification is also valuable.
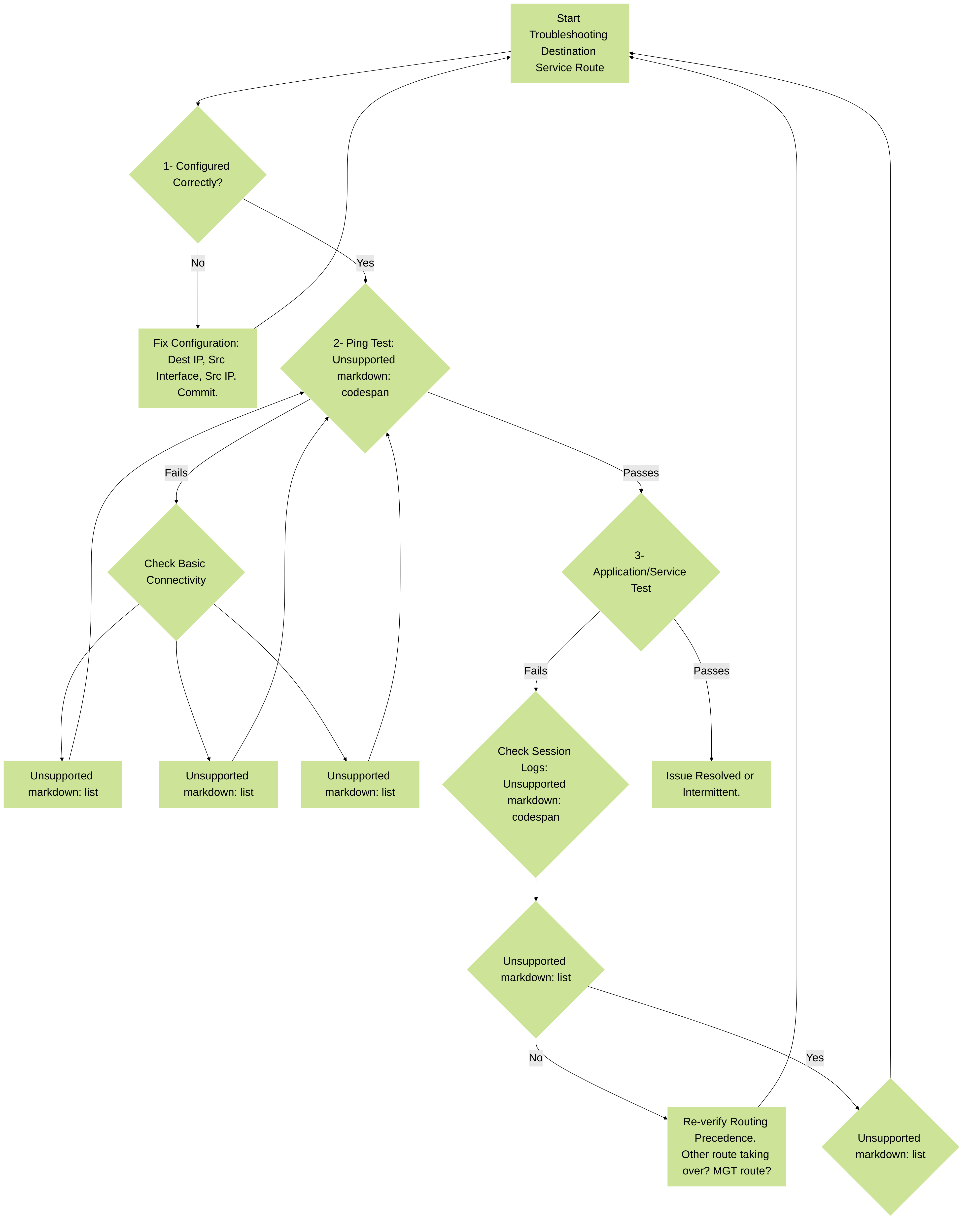
A simplified troubleshooting flowchart for destination-based service routes on Palo Alto Networks firewalls.
8. PCNSE Exam Key Takeaways
For the Palo Alto Networks Certified Network Security Engineer (PCNSE) exam, a solid understanding of destination-based service routes is essential. Key points to focus on include:
- Purpose: Primarily for controlling the source interface/IP for firewall-generated traffic to *specific destination IPs*, especially for custom services or overriding default paths.
-
Scope:
Global configuration (
Device > Setup > Services). Not per-VSYS. - Precedence: Understand where destination-based service routes fit in the firewall's egress path selection logic (MGT routes -> Destination Service Routes -> Standard Service Routes -> FIB).
- Configuration Elements: Know the required parameters (Destination IP, Source Interface, Source IP).
-
CLI vs. GUI:
Be familiar with both configuration methods. Key CLI command:
set deviceconfig system service route destination.... -
Verification:
Know how to verify using session logs and CLI commands like
show deviceconfig system service route destinationandping source. - Distinction from other routing mechanisms: Clearly differentiate from Virtual Router static/dynamic routes (for transit traffic) and Policy-Based Forwarding (PBF, also for transit traffic).
- Use Cases: Recognize common scenarios where they are applied, such as accessing unlisted external services or forcing traffic for a specific IP out a non-default path.