Understanding Service Routes on Palo Alto Networks Firewalls
Palo Alto Networks firewalls are complex devices that require connectivity to various external services to function optimally. These services include retrieving software updates, licenses, threat intelligence updates, contacting logging destinations, and interacting with management platforms like Panorama.
By default, traffic destined for these services originates from the firewall's dedicated Management (MGT) interface. However, network designs often dictate that the MGT interface resides on a separate, isolated network segment which may not have routing access to all necessary external services. This is where Service Routes become essential.
Management Interface vs. Data Plane Interface Traffic
The Palo Alto Networks firewall operates with two main planes: the Management Plane and the Data Plane.
- Management Plane: Handles administrative traffic, GUI/CLI access (SSH, HTTPS), logging, reporting, and service traffic like updates, licenses, and Panorama communication by default. It uses the MGT interface as its default gateway.
- Data Plane: Processes user traffic, applies security policies, performs NAT, routing, etc. It uses configured data interfaces (Ethernet, Aggregate Ethernet, VLAN interfaces) which are associated with virtual routers.
While the Management Plane typically handles service traffic, Service Routes allow you to explicitly direct specific service traffic to originate from a Data Plane interface instead. This is crucial when the external service (like a DNS server, Panorama, or update server) is only reachable through the network segments connected to your data interfaces.
Using a Data Plane interface for service traffic means that traffic will traverse the Data Plane's routing table (specifically, the virtual router associated with the chosen interface) to reach its destination. This allows service traffic to follow the same network paths as user traffic if necessary, overcoming limitations of the MGT network.
Core Concepts and Configuration
Purpose of Service Routes
The primary purpose of service routes is to enable the firewall's management plane to reach external services when the default routing via the Management interface is not suitable or possible. This is necessary when external services are not reachable via the MGT interface but are accessible through in-band data interfaces (interfaces configured within a virtual router).
Default Behavior
By default, the Management (MGT) interface is the source and egress interface for all service-related traffic originating from the firewall itself. This relies on the MGT interface having a default gateway configured that can route traffic to the internet or internal service hosts.
Configuration Steps
Configuring service routes involves specifying which service traffic should use a different source interface and potentially a different source IP address than the default MGT interface settings. The configuration is performed within the Device tab.
The general steps are:
- Navigate to Device > Setup > Services .
- Locate the Service Route Configuration section.
- Click Customize .
- Select the specific service you want to modify (e.g., DNS, NTP, Panorama, Updates).
- Choose the desired Source Interface from the available data plane interfaces. This interface must be configured and be part of a virtual router.
- (Optional) Specify a Source IP Address if you need the traffic to originate from a specific IP on that interface (e.g., a secondary IP or the interface's primary IP if not automatically selected).
- Some services might require manually adding the destination server address if not present in the firewall's database.
- Commit the changes.
Service Route Customization
You can customize routes for various specific services. The interface chosen for the service route must be a layer 3 interface configured in a virtual router. The firewall will then use the routing table of that virtual router to determine the actual next hop and egress interface for the service traffic.
Global vs. Per-VSYS Service Routes
In deployments utilizing Virtual Systems (VSYS), service route configuration has additional considerations.
Global Service Routes
Service routes configured at the global level (when logged into the shared environment or VSYS1 if no other VSYS exist) apply to the entire firewall and all configured Virtual Systems by default.
Per-VSYS Service Routes
In a multi-VSYS environment, each virtual system inherits global service route settings by default. However, administrators can customize service routes specifically for individual VSYS instances.
This is important for scenarios such as:
- Supporting multiple tenants with distinct external service needs (e.g., different DNS servers, different Panorama instances).
- Ensuring service traffic for a specific VSYS follows particular network paths only accessible within that VSYS's routing domain.
Interaction with Routing
Regardless of whether the service route is Global or Per-VSYS, the firewall determines the actual egress interface and next hop for the service traffic based on the routing table:
- Global Service Route: Uses the routing table of the virtual router associated with the Source Interface selected in the configuration.
- Per-VSYS Service Route: Uses the routing table of the Virtual Router explicitly selected in the VSYS's service route configuration.
Importance and Use Cases
Service routes are fundamental for ensuring the Palo Alto Networks firewall can connect to critical external services necessary for its proper operation, security functions, and management. Key use cases and the services involved include:
Accessing External Services
Service routes are fundamental for enabling the firewall to connect to critical external services required for its operation and security updates.
Dynamic Updates
Ensuring the firewall can download and install dynamic content and software updates is a crucial use case. Services requiring connectivity often include:
- PAN-OS Software Updates: New firewall operating system versions.
- Licenses: Retrieving and validating firewall licenses.
-
Threat Intelligence Updates:
- WildFire (malware analysis and signatures)
- Antivirus signatures
- Spyware signatures
- Vulnerability signatures
- URL Filtering database
- Applications and Threats database
- GlobalProtect Data File
- Correlation Objects
Network Services
Several essential network services rely on service routes if their destinations are not reachable via the default Management route:
- DNS (Domain Name System): Used by the firewall to resolve hostnames for various services (updates, Panorama, URL filtering lookups, etc.). Correct DNS resolution is vital.
- NTP (Network Time Protocol): For time synchronization, which is critical for accurate logging, certificate validation, and correlation of events.
- Authentication Services: Connectivity to external LDAP, RADIUS, TACACS+, and SAML servers for administrator or user authentication.
- Syslog: Forwarding logs to external syslog servers for centralized logging and analysis.
Panorama Connectivity
If the firewall is managed by Panorama, it must be able to connect to the Panorama appliance. A service route might be needed if the Panorama IP is not reachable via the MGT interface.
Security and Segmentation
Using dedicated data interfaces for services can enhance security and align with network segmentation strategies. Instead of exposing the MGT network to paths required for production services, you can route service traffic via specific data plane interfaces configured within more appropriate network segments.
Routing service traffic via a data plane interface also means that traffic will be processed by the Data Plane to some extent. While it bypasses security policies (service traffic is typically generated by the Management Plane), it will use the routing table, NAT configuration (if applicable to the source IP/interface), and potentially features like QoS or path monitoring configured on that interface's virtual router.
Benefits and Disadvantages of Service Routes
Implementing service routes offers several advantages but also introduces potential complexities.
Benefits:
- Reachability: Enables the firewall to access critical external and internal services that are not reachable via the isolated Management network. This is the primary benefit.
- Network Segmentation Alignment: Allows service traffic to follow the designed network architecture and segmentation strategy by using appropriate data plane interfaces and routing domains.
- Flexibility: Provides granular control over which services use which network paths, adapting to complex network designs.
- Enhanced Security (via segmentation): By routing service traffic off the dedicated management network, you reduce the need for complex routing or firewall holes into the management segment from other networks.
- Utilization of Data Plane Features: Service traffic can implicitly benefit from routing, NAT (if configured on the source interface/VR), and potentially other network features within the data plane's virtual router.
Disadvantages:
- Configuration Complexity: Requires explicit configuration for each service route, adding overhead compared to relying solely on the MGT interface default gateway.
- Potential for Misconfiguration: Errors in selecting the source interface, source IP, or ensuring the virtual router has the correct route can lead to service outages (e.g., updates failing, logging stopping).
- Troubleshooting Difficulty: Issues can be harder to diagnose as traffic is no longer simply exiting the known MGT interface but following complex data plane routing paths. Requires understanding which interface/VR is being used and its routing table.
- Dependency on Data Plane Health: If the data plane interface or the network path through its virtual router fails, the service traffic will also fail, even if the Management plane is operational.
Troubleshooting Service Routes
When services are failing (updates not downloading, Panorama showing disconnected, logs not arriving), service routes are a common area to investigate, especially if the MGT interface doesn't have direct internet access.
Verifying Service Routes
The first step is to confirm if a service route is configured for the problematic service and that the configuration is as expected (correct source interface/virtual router). This is done in the GUI (Device > Setup > Services > Service Route Configuration > Customize) or via the CLI.
CLI Commands for Debugging
The CLI is invaluable for verifying the operational state of service routes and diagnosing underlying routing issues.
-
Viewing Configured Service Routes:
> show running service-routeThis command shows the service routes configured in the candidate or running configuration.
-
Viewing Operational Service Routes (Management Plane perspective):
> debug dataplane internal vif routeReplace
<destination_IP>with the IP address of the service host (e.g., Panorama IP, update server IP, DNS server IP). This command shows how the Management Plane intends to route traffic to that specific destination based on configured service routes and the underlying data plane routing tables.Be aware of thedebug dataplane internal vif route <destination_IP>command. This is a critical command to verify which interface/VR the management plane will use for a specific service destination IP.The output ofdebug dataplane internal vif routeshows the routing from the Management Plane's perspective, but relies on the Data Plane's routing tables. It will indicate the chosen virtual router and the resulting egress interface/next hop from that VR's table. A missing route in the VR will show up here. -
Viewing Data Plane Routing Table:
> show routing route virtual-routerUse this to verify that the virtual router associated with your service route (either via the source interface for Global, or directly configured for Per-VSYS) actually has a valid route to the service destination IP.
-
Pinging from a Data Plane Interface (Requires license/specific versions):
> ping sourcehost or
> ping sourcehost This can help verify basic Layer 3 connectivity from the chosen source interface/IP that your service route is configured to use.
Common Issues
- Incorrect Source Interface/Virtual Router: Selecting an interface or VR that doesn't have a valid route to the service destination.
- Missing Route in Virtual Router: The VR associated with the service route doesn't have a specific or default route covering the service destination IP.
- Firewall/ACLs Blocking Traffic: An external firewall or ACL is blocking the service traffic originating from the data plane interface's source IP. Remember, while policy bypasses security *rules*, external devices might still filter based on source/destination/port.
- NAT Issues: If the service destination requires communication with a specific source IP and NAT is incorrectly configured (or not configured when needed) on the data plane interface.
- DNS Resolution Failure: If the service route is for DNS itself, or if the firewall needs to resolve the service destination hostname (e.g., update server FQDN), and the specified DNS server is unreachable or incorrect.
debug dataplane internal vif route
, and verifying basic connectivity (ping).
Log Analysis
Firewall logs can provide clues. System logs may show errors related to failed updates, license retrieval, or Panorama connection issues. Traffic logs might show sessions initiated from the firewall's source IP towards service destinations, indicating if traffic is hitting a block somewhere downstream (though service traffic often doesn't appear in standard traffic logs in the same way user traffic does).
Illustrations
Understanding how service routes interact with the different planes and routing tables is key. Here are some conceptual diagrams illustrating the traffic flow.
Flowchart: Default Service Traffic Flow (No Service Route)
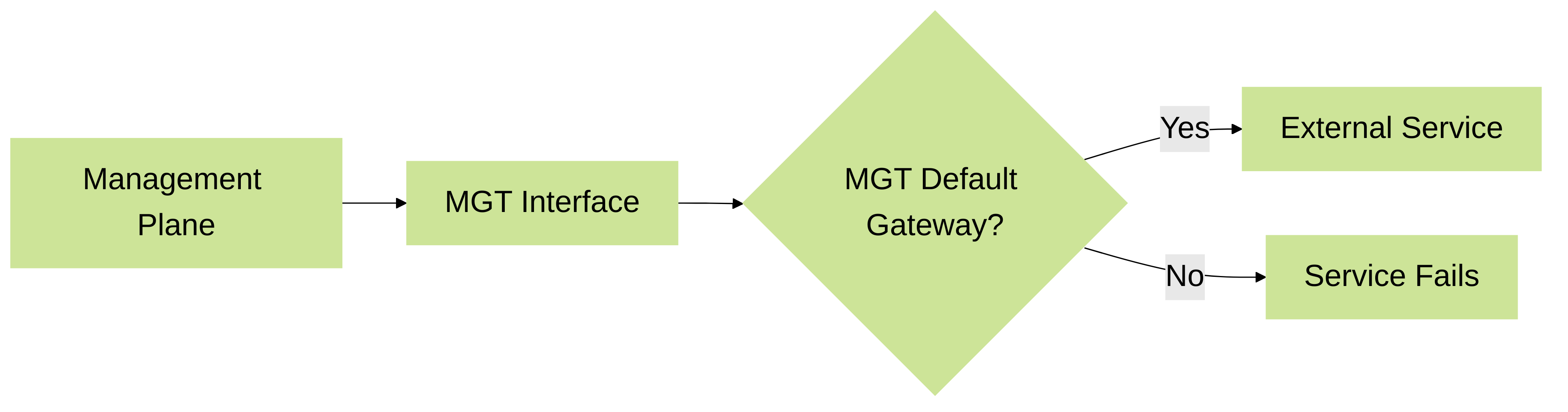
Illustration of service traffic flow using the default Management interface.
Flowchart: Service Traffic Flow (With Service Route)
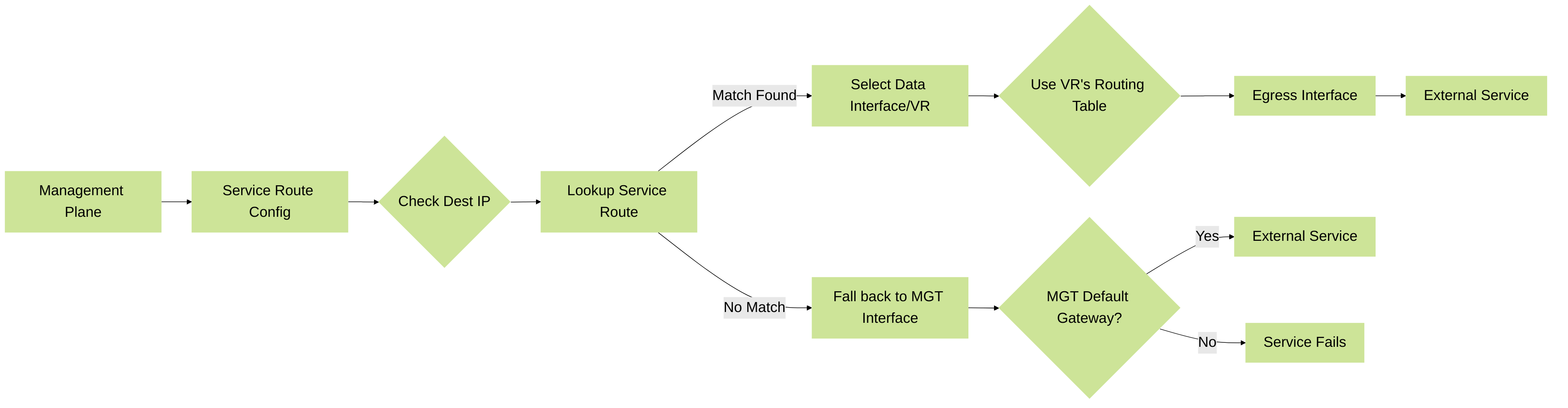
Illustration of service traffic flow when a service route is configured.
Sequence Diagram: Service Route Lookup
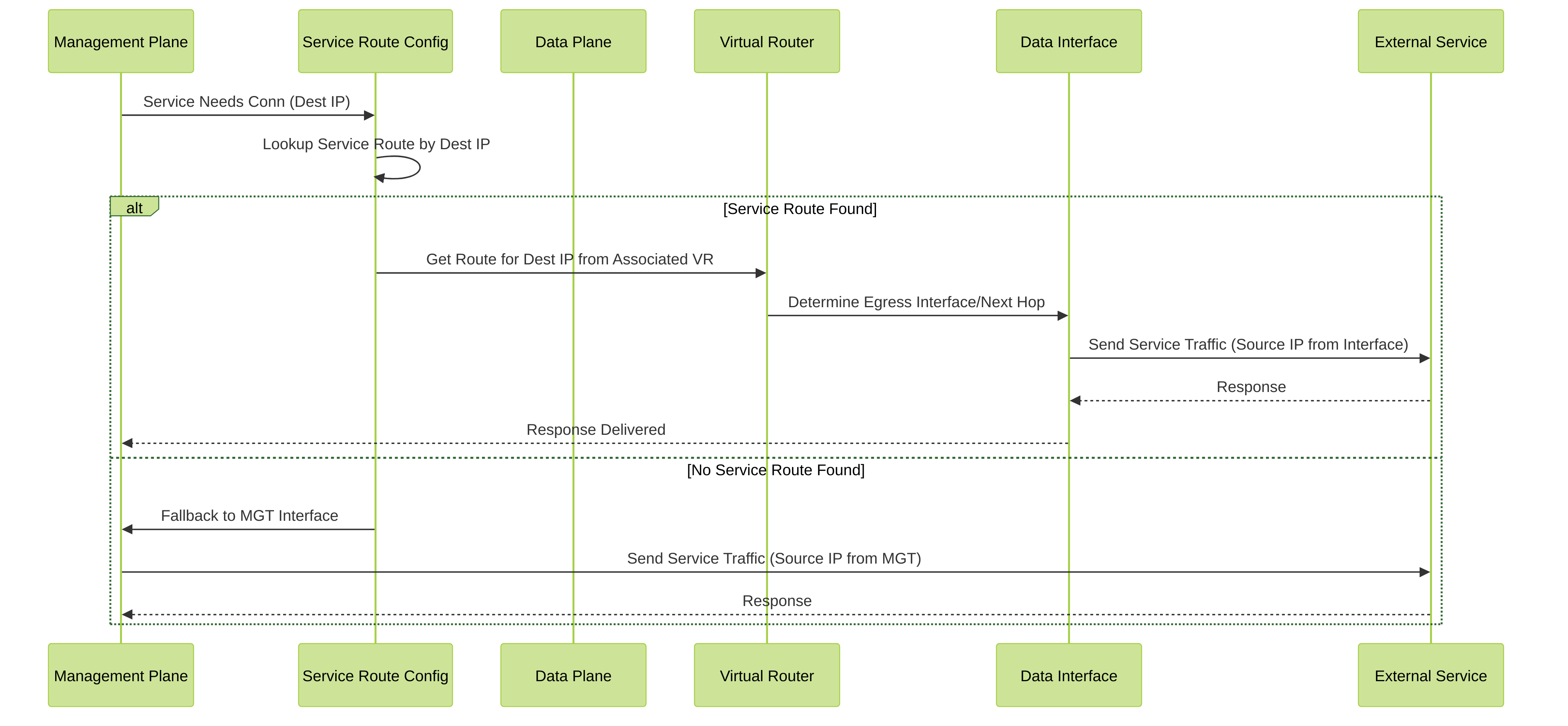
Sequence of operations when the firewall determines the path for service traffic.
State Diagram: Service Route State
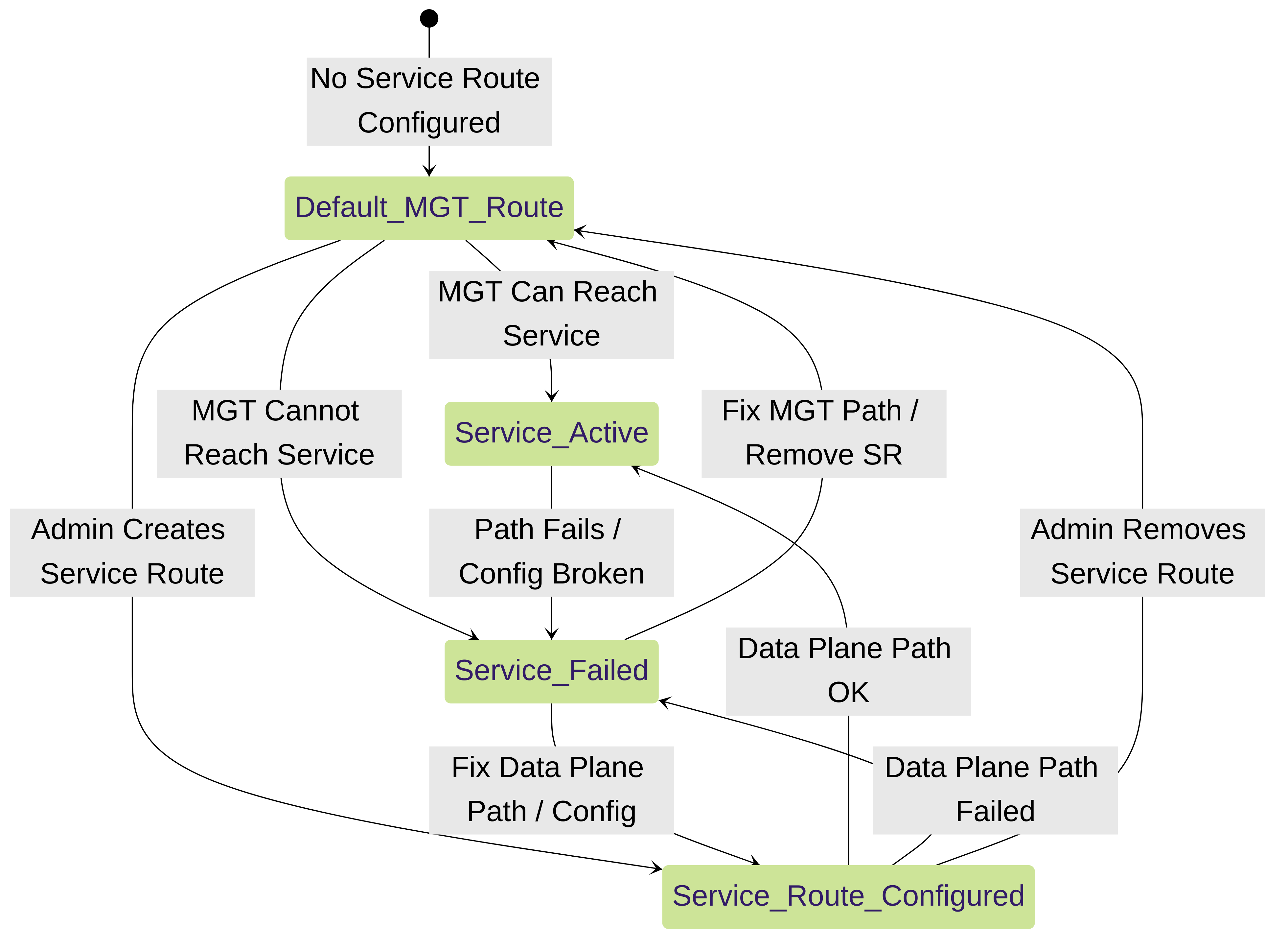
Simplified state transitions based on service route configuration and path reachability.
Service Routes Quiz
Test your understanding of Palo Alto Networks Service Routes with these questions, typical of what might be found in a PCNSE exam.