Mastering NAT Session Identification in Palo Alto Networks PAN-OS
Understanding Network Address Translation (NAT) and how to identify which NAT rule applies to a specific traffic session is a fundamental skill for any network security professional working with Palo Alto Networks Next-Generation Firewalls (NGFWs). This guide provides a comprehensive, in-depth exploration of the tools and techniques available within PAN-OS to accurately pinpoint NAT rule associations, crucial for troubleshooting, verification, and ensuring security policy enforcement. This knowledge is also vital for PCNSE certification aspirants.
Understanding NAT in the PAN-OS Context
Palo Alto Networks NGFWs perform NAT by modifying the IP address and/or port information in packet headers as they traverse the firewall. PAN-OS supports several types of NAT, each serving distinct purposes:
-
Source NAT (SNAT):
Typically used to translate private internal IP addresses to one or more public IP addresses, allowing internal hosts to access external resources like the internet. PAN-OS supports:
- Dynamic IP and Port (DIPP): Translates multiple private IPs to a single public IP, using different source ports to distinguish sessions. This is the most common form of SNAT for internet access. The translated address is typically the IP address of the firewall's external interface.
- Dynamic IP (DIP): Translates multiple private IPs to a pool of public IPs. A session uses one IP from the pool until the pool is exhausted.
- Static IP: Maps a specific internal IP address to a specific public IP address. This is often used for servers that need a consistent public IP for inbound access but also initiate outbound connections.
-
Destination NAT (DNAT):
Translates a public destination IP address (and often port) to a private internal IP address (and port). This is commonly used to allow external users to access internal services (e.g., web servers, mail servers). PAN-OS supports:
- Static IP: Maps a public IP/port to a specific internal IP/port.
- Dynamic IP and Port (DIPP) for Destination (Port Translation only): While less common for the IP itself, DIPP logic can apply to port translation where a single public IP and port combination is translated to different internal ports on the same or different internal servers, though typically static mapping is preferred for clarity for DNAT. More commonly, DNAT uses Static IP for the address and can optionally translate the destination port.
- No-NAT: Specifies traffic that should not have NAT applied, even if it matches criteria that would otherwise cause it to be NATted. Useful for VPN traffic or specific internal routing scenarios.
- U-Turn NAT: A scenario where an internal user attempts to access an internal resource using its external public IP address. The firewall must correctly NAT the traffic "out" and then back "in." This requires both SNAT and DNAT rules, or a specific U-Turn NAT rule configuration.
Using the Web Interface (GUI) to Identify NAT Rules for Active Sessions
The PAN-OS web interface provides the Session Browser, a powerful tool for real-time inspection of active traffic sessions, including their NAT status.
-
Access the Session Browser:
-
Navigate to
Monitor > Session Browserin the PAN-OS web interface.
-
Navigate to
-
Filter Sessions:
- The Session Browser can display thousands of sessions on a busy firewall. Effective filtering is key.
- Click the "Filter" icon (looks like a funnel) or the "Add Filter" button to open the filter builder.
-
Common and useful filter criteria for NAT investigation include:
- Source IP: The original source IP address of the client.
- Destination IP: The original destination IP address.
- Application: If you know the application (e.g., `ssl`, `web-browsing`).
- Destination Port: The original destination port.
- NAT Rule: If you suspect a particular NAT rule, you can filter by its name.
- NAT: A boolean filter, you can select "yes" to show only sessions that have NAT applied.
- Post-NAT Source IP: The IP address after SNAT.
- Post-NAT Destination IP: The IP address after DNAT.
- Example filter: `( ( source eq 192.168.1.100 ) and ( nat eq yes ) )` to find NATted sessions from a specific internal IP.
-
View Session Details:
- Once you locate the session of interest in the filtered list, click on the magnifying glass icon (🔍) in the "Details" column next to that session.
-
Inspect NAT Information in Session Details:
-
The "Session Details" window provides a wealth of information. For NAT, look for these key fields:
- NAT Rule: Displays the name of the NAT policy rule that was matched for this session. This is the most direct indicator.
- Source Address (Original): The source IP before any NAT.
- Source Address (Post-NAT): The source IP after SNAT. If SNAT occurred, this will differ from the original source.
- Destination Address (Original): The destination IP before any NAT.
- Destination Address (Post-NAT): The destination IP after DNAT. If DNAT occurred, this will differ from the original destination.
- Source Port (Post-NAT): The source port after SNAT (PAT).
- Destination Port (Post-NAT): The destination port after DNAT (Port Translation).
-
The "Session Details" window provides a wealth of information. For NAT, look for these key fields:
Workflow for identifying NAT rule information for an active session using the PAN-OS Session Browser in the web interface.
Using the Command Line Interface (CLI) to Identify NAT Rules
The PAN-OS CLI offers powerful commands for session inspection, often preferred by advanced users for its speed and scripting capabilities.
-
Filter Sessions:
-
The primary command is
show session all. To make its output manageable, use thefilterkeyword.admin@PA-VM> show session all filter source <source_ip> destination <destination_ip> admin@PA-VM> show session all filter nat yes source <source_ip> admin@PA-VM> show session all filter nat-rule <name_of_nat_rule>
-
You can filter on numerous parameters. Use `show session all filter ?` to see available options. Key options for NAT:
-
source <ip>: Original source IP. -
destination <ip>: Original destination IP. -
source-nat-ip <ip>: Post-SNAT IP. -
destination-nat-ip <ip>: Post-DNAT IP. -
nat yes | no: Show only NATted or non-NATted sessions. -
nat-rule <rule_name>: Filter by the name of the NAT rule. -
protocol <number>: (e.g., 6 for TCP, 17 for UDP). -
dport <port_number>: Original destination port.
-
-
The output will provide a summary of matching sessions, including session IDs. Note the ID of the session you want to investigate further.
admin@PA-VM> show session all filter source 192.168.1.50 destination 8.8.8.8 -------------------------------------------------------------------------------- ID Application State Type VSYS Source Zone Destination Zone -------------------------------------------------------------------------------- 12345 dns ACTIVE FLOW vsys1 Trust Untrust Source IP Port Translated IP Port Destination IP Port Translated IP Port 192.168.1.50 54321 203.0.113.10 10001 8.8.8.8 53 8.8.8.8 53 Protocol NAT Rule Timeout Time_left Additional_info 6 Outbound-Internet 3600 3598 N/A -------------------------------------------------------------------------------- Total entries: 1
-
The primary command is
-
View Specific Session Details:
-
Once you have the session ID, use
show session id <session_id>for comprehensive details.admin@PA-VM> show session id 12345
-
The output of this command is extensive. Look for the following NAT-related lines:
Session 12345 ... Source 192.168.1.50 [Trust] dst 8.8.8.8 [Untrust] ... State active ... NAT source 203.0.113.10 (Internet-NAT-Rule) NAT destination 8.8.8.8 NAT type ipv4 NAT rule Internet-NAT-Rule (id: 7) ... session agetimeout : 3600 sec session lifetime : 86400 sec -
Key fields in
show session idoutput for NAT:-
NAT source: Shows the post-SNAT IP address. It may also show the NAT rule name in parentheses if available in that part of the output (behavior can vary slightly by PAN-OS version). -
NAT destination: Shows the post-DNAT IP address. -
NAT type: Indicates the type of NAT (e.g., ipv4). -
NAT rule: Explicitly states the name of the NAT rule and its internal ID (e.g., `Internet-NAT-Rule (id: 7)`). This is a definitive indicator. - If DIPP (PAT) is used, the translated port will be visible in the flow details section (e.g., `sport_xlate`, `dport_xlate`).
-
-
Once you have the session ID, use
Streamlined workflow for investigating NAT information for a specific session using PAN-OS CLI commands.
Leveraging Traffic Logs for NAT Investigation
While the Session Browser and CLI commands are excellent for active sessions, Traffic Logs are invaluable for historical analysis of NAT behavior.
-
Navigate to Traffic Logs:
-
Go to
Monitor > Logs > Trafficin the PAN-OS web interface.
-
Go to
-
Customize Log Columns:
- By default, all NAT-related columns might not be visible. Click the "Columns" button (or the small gear icon in some versions) to customize the displayed columns.
-
Ensure the following columns are selected and visible:
- Source Address (Original Source IP)
- Destination Address (Original Destination IP)
- NAT Source IP (Post-SNAT IP)
- NAT Source Port (Post-SNAT Port)
- NAT Destination IP (Post-DNAT IP)
- NAT Destination Port (Post-DNAT Port)
- NAT Rule (Name of the matched NAT rule)
- Session ID (Useful for correlating with `show session id` if the session was recent or for advanced troubleshooting)
-
Filter Traffic Logs:
- Use the filter builder (similar to the Session Browser) to find relevant log entries.
- You can filter on any of the original or post-NAT IP addresses/ports, the NAT rule name, application, zones, etc.
- Example filter: `( ( nat_rule eq 'Specific-DNAT-Rule' ) and ( destination_address eq 203.0.113.50 ) )`
-
Interpret Log Entries:
- Each log entry representing a session that matched a NAT rule will populate the "NAT Rule," "NAT Source IP/Port," and "NAT Destination IP/Port" fields accordingly.
- If these fields are blank for a session, it means no NAT rule was applied to that specific session.
Process for leveraging PAN-OS Traffic Logs to identify NAT rules applied to past sessions and their translation details.
Understanding Different NAT Types and Their Impact on Session Identification
The type of NAT rule configured influences what you'll see in session details and logs.
Source NAT (SNAT)
Primarily changes the source IP address (and often port) of traffic, typically from internal networks to external networks.
-
Dynamic IP and Port (DIPP):
- Session Identification: You'll see the original internal source IP and the translated public source IP (often the firewall's egress interface IP) and a translated source port. The "NAT Rule" field will show the DIPP NAT rule name.
-
Example:
Internal client 192.168.1.100 accessing an internet server.
- Original Source: 192.168.1.100:50000
- NAT Source IP: 203.0.113.10 (Firewall Egress IP)
- NAT Source Port: 34567 (Dynamically assigned port)
-
Dynamic IP (DIP):
- Session Identification: Similar to DIPP, but the NAT Source IP will be one of the IPs from the configured DIP pool. Port translation may or may not occur depending on the "Port Translation" setting in the DIP configuration.
-
Example:
Internal client 10.1.1.20 accessing internet, using a DIP pool (203.0.113.20 - 203.0.113.30).
- Original Source: 10.1.1.20:51000
- NAT Source IP: 203.0.113.25 (An IP from the pool)
- NAT Source Port: 51000 (if no port translation) or a translated port (if port translation enabled for DIP).
-
Static IP (for Source NAT):
- Session Identification: A specific original source IP is mapped to a specific translated source IP. The "NAT Rule" field will show the static NAT rule name.
-
Example:
Internal server 192.168.10.5 needs to source outbound traffic from a dedicated public IP 203.0.113.5.
- Original Source: 192.168.10.5
- NAT Source IP: 203.0.113.5
Destination NAT (DNAT)
Primarily changes the destination IP address (and often port) of traffic, typically from external networks to internal services.
-
Static IP (for Destination NAT):
- Session Identification: The original public destination IP and port are translated to an internal private IP and potentially a different port. The "NAT Rule" field shows the DNAT rule name.
-
Example:
External user accessing public IP 203.0.113.50:443, which is DNATted to internal web server 10.0.0.80:443.
- Original Destination: 203.0.113.50:443
- NAT Destination IP: 10.0.0.80
- NAT Destination Port: 443 (or a translated port if configured)
No-NAT
When a No-NAT rule is matched, the session details and logs will show:
- NAT Rule: The name of the No-NAT rule.
- NAT Source IP/Port: Same as Original Source IP/Port.
- NAT Destination IP/Port: Same as Original Destination IP/Port.
No translation occurs, but the rule match itself is logged.
U-Turn NAT
This is a more complex scenario where an internal client tries to access an internal server using the server's public IP address.
-
Session Identification:
This requires careful examination.
- The client (e.g., 192.168.1.100) initiates a connection to the server's public IP (e.g., 203.0.113.50).
- A DNAT rule translates 203.0.113.50 to the server's internal IP (e.g., 10.1.1.20).
- To ensure the server's reply goes back through the firewall and is correctly NATted back to the internal client, an SNAT rule is often needed. This SNAT rule might translate the internal client's source IP (192.168.1.100) to the firewall's internal interface IP (for the segment the server is on).
-
In session details:
- Original Source: 192.168.1.100
- Original Destination: 203.0.113.50
- Post-NAT Source: Might be 192.168.1.100 or the firewall's internal interface IP (e.g., 192.168.1.1 or 10.1.1.1 depending on the SNAT config for U-Turn).
- Post-NAT Destination: 10.1.1.20
- You will see both a DNAT rule and an SNAT rule (or a combined U-Turn NAT rule, if configured that way) hit. The session details will show the specific NAT rule(s) applied.
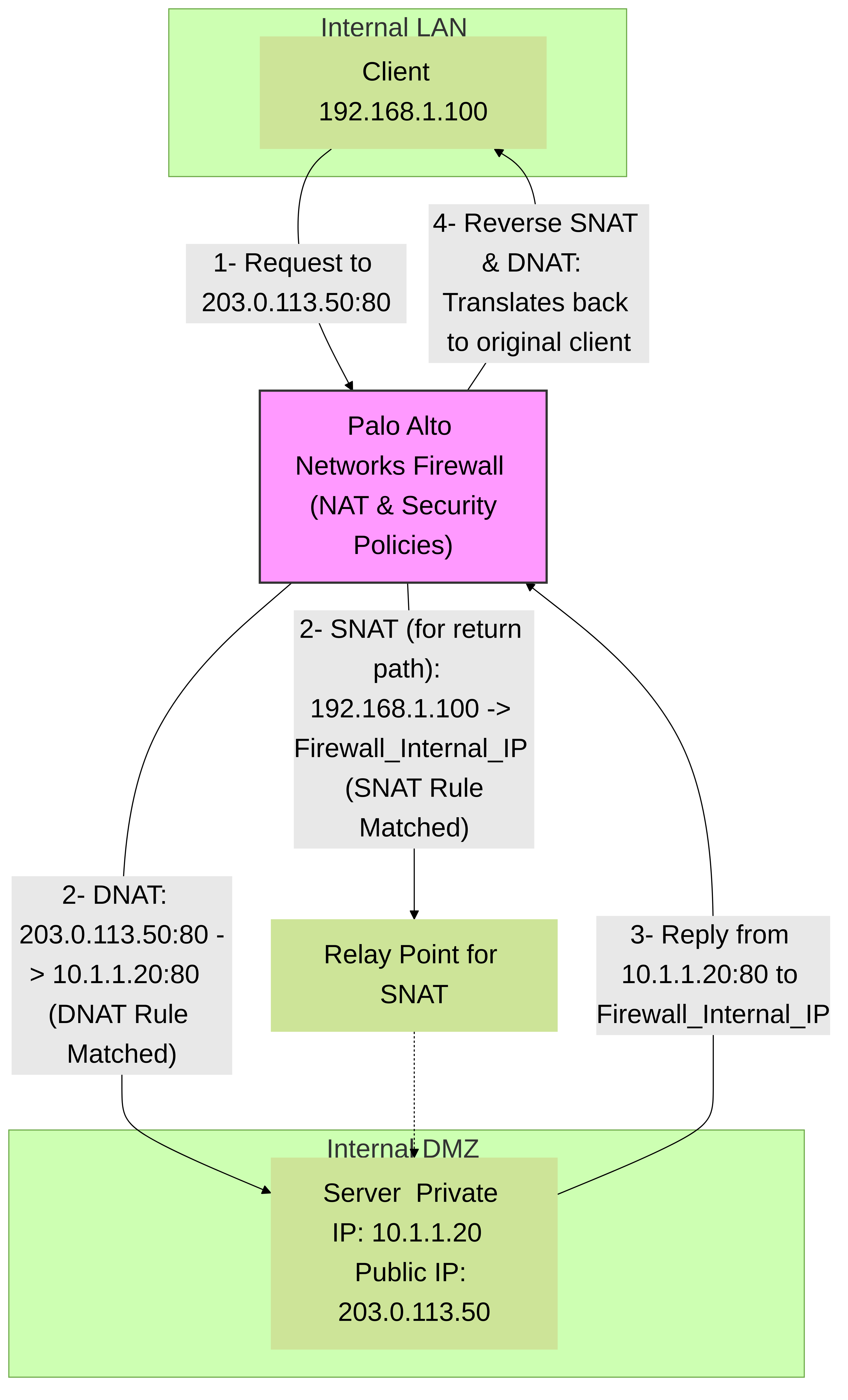
Simplified U-Turn NAT traffic flow. An internal client accesses an internal server via its public IP. The firewall applies DNAT to reach the server and SNAT to ensure the return traffic routes correctly back through the firewall to the client. Session details will reflect these translations and the specific NAT rules matched.
Advanced Considerations and Troubleshooting
NAT Rule Order and Policy Lookup
NAT policies in PAN-OS are evaluated from top to bottom, just like Security policies. The first rule that matches the traffic criteria is applied.
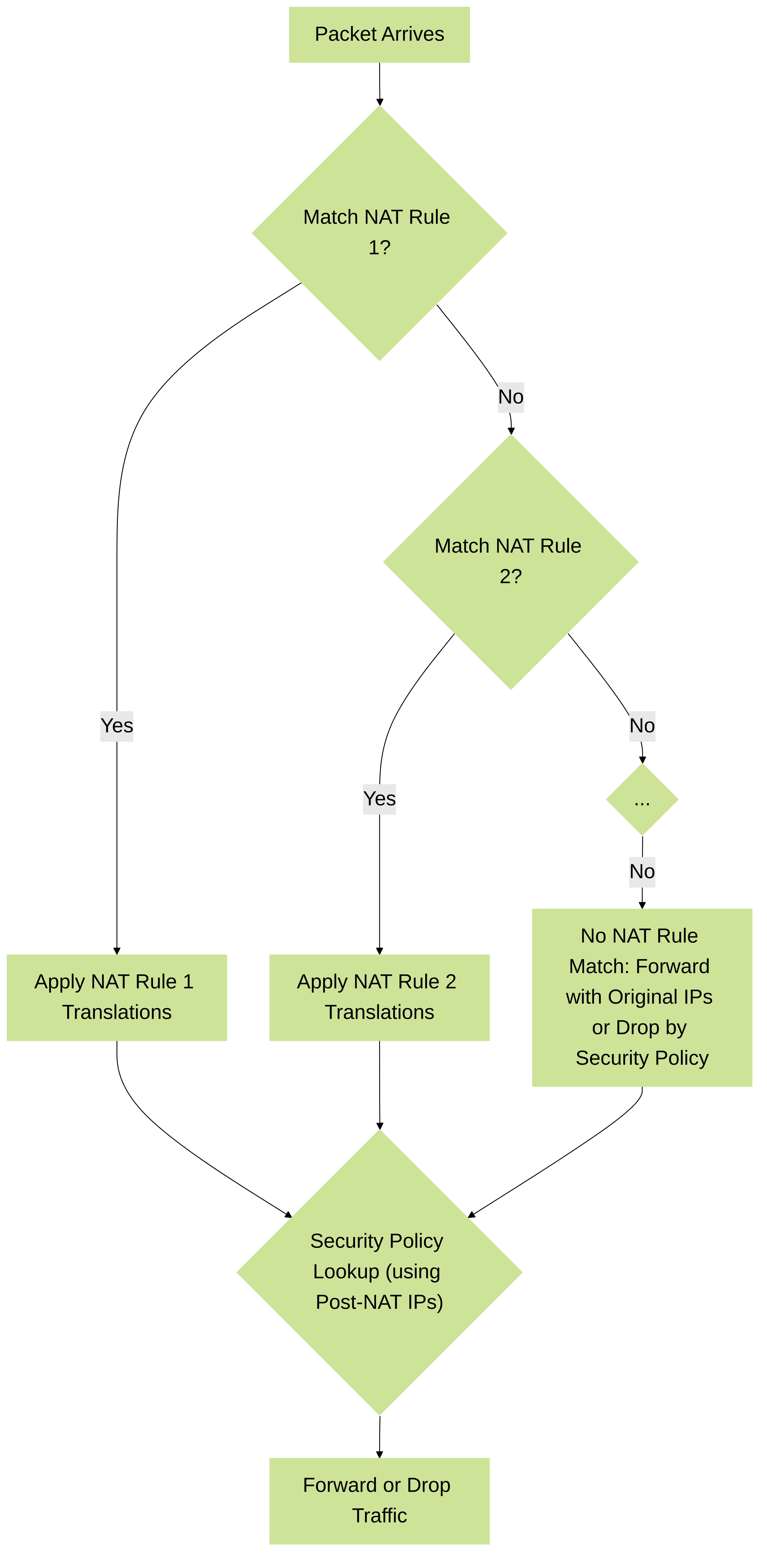
Simplified PAN-OS NAT policy lookup logic. The firewall evaluates NAT rules sequentially. Once a match is found, that NAT rule is applied, and subsequent NAT rules are not evaluated for that session. Security policy lookup then uses the post-NAT addresses.
- Troubleshooting: If an unexpected NAT rule is being hit, or no NAT is applied when expected, review the NAT policy order. A more general rule placed higher might be "shadowing" a more specific rule placed lower.
- Use the "NAT Rule" field in session details/logs to confirm which rule is actually being matched.
Bidirectional NAT
When configuring NAT, especially static NAT for servers, you might need to allow traffic in both directions.
- DNAT for Inbound: A Destination NAT rule translates the public IP to the private IP for incoming connections.
- SNAT for Outbound (Optional but common for consistency): If the same server needs to initiate outbound connections using its public IP, a corresponding Source NAT rule (Static IP type) is needed to translate its private IP to its public IP for outbound traffic.
- Palo Alto Networks NAT rules have a "Translation Type" option. For static 1:1 NAT, you can often achieve bidirectional behavior with a single rule by setting the source and destination translation appropriately, or by using two separate rules (one for DNAT, one for SNAT). The "Bi-directional" checkbox on a static NAT rule (available in some contexts or versions) simplifies this by automatically creating the reverse translation logic. Check your PAN-OS version's specific NAT rule options.
Session States and NAT
- NAT is applied at session initiation. The decision of which NAT rule to apply is made when the first packet of a new session arrives.
- Once a session is established and a NAT rule is applied, that session will continue to use the same NAT translation for its duration, even if the NAT policy is changed. New sessions will use the updated NAT policy.
Troubleshooting NAT Rule Misses
If traffic is not being NATted as expected:
- Verify NAT Policy Criteria: Double-check the source/destination zones, source/destination addresses, and service/application defined in your NAT rule. Ensure they accurately match the traffic flow.
- Check Rule Order: As mentioned, ensure a more general rule isn't matching before your intended specific rule.
- Zone Mismatch: Ensure the traffic is actually entering and exiting the zones specified in the NAT rule. Use traffic logs to verify zones.
- No-NAT Rules: Check if an explicit No-NAT rule is matching the traffic and preventing your intended NAT rule from being applied.
- Interface IP for DIPP: If using "Translated Address: Interface Address" in a DIPP rule, ensure the selected interface has an IP address configured and is in the correct state (up).
- DIP Pool Exhaustion: If using DIP, check if the pool of available IP addresses has been exhausted. Monitor `show nat pool dynamic <pool_name>` or related CLI commands.
-
Global Counters:
Use CLI commands like `show counter global filter aspect nat` to see NAT statistics, including potential errors or drops related to NAT.
admin@PA-VM> show counter global filter delta yes aspect nat
This can show counters like `nat_session_no_match`, `nat_pool_failed`, etc., which can indicate problems.
Session Termination for NAT Changes
If you've made a NAT rule change and need existing sessions to use the new rule (or stop using an old NAT rule), you may need to clear the relevant active sessions.
-
Using the CLI:
admin@PA-VM> clear session id <session_id>
To clear all sessions matching certain criteria (use with caution on production firewalls):admin@PA-VM> clear session all filter source <ip> destination <ip>
- Be aware that clearing sessions will interrupt active connections.
Summary for PCNSE Candidates
Mastering NAT session identification on Palo Alto Networks firewalls is a core competency tested on the PCNSE exam. Key areas to focus on include:
- Differentiating NAT Types: Source NAT (DIPP, DIP, Static), Destination NAT (Static), No-NAT, U-Turn NAT.
- GUI Tools: Effectively using the Session Browser and Traffic Logs, including filtering and interpreting NAT-specific columns/fields.
-
CLI Commands:
Proficiency with `show session all filter
` and `show session id `, and understanding their output related to NAT. - NAT Policy Logic: Top-down evaluation, rule shadowing, and the interaction between NAT and Security policies (NAT typically first for outbound, DNAT pre-security policy lookup for inbound).
- Troubleshooting: Common NAT issues like incorrect rule matching, zone mismatches, U-Turn NAT misconfigurations, and how to use firewall tools to diagnose them.
- Log Interpretation: Correlating NAT rule names and translated IPs/ports found in traffic logs with specific sessions.
By thoroughly understanding these concepts and practicing with the PAN-OS interface and CLI, you will be well-prepared to handle NAT-related questions and real-world scenarios.