Understanding Palo Alto Networks Threat Prevention vs. Advanced Threat Prevention
Palo Alto Networks Next-Generation Firewalls (NGFWs) provide robust security capabilities through various subscription services. Two fundamental subscriptions focused on stopping malicious content and activities are Threat Prevention (TP) and Advanced Threat Prevention (ATP) . While both aim to protect your network, they differ significantly in their approach, scope, and the types of threats they are designed to counter most effectively.
Based on information gathered from Palo Alto Networks documentation and related web resources, this article provides a comprehensive comparison, focusing on aspects relevant to the PCNSE (Palo Alto Networks Certified Network Security Engineer) certification.
Understanding the nuances between these two subscriptions is crucial for designing, deploying, and managing effective security postures using Palo Alto Networks firewalls.
Threat Prevention (TP): The Foundation
The Threat Prevention subscription is the cornerstone of PAN-OS security services for protecting against known threats traversing the network. It combines multiple security engines that inspect traffic identified by App-ID for malicious patterns and content.
Core features typically included in the standard Threat Prevention subscription are:
- Antivirus: Detects and blocks known viruses, worms, trojans, and other malware in file transfers (e.g., HTTP, SMTP, FTP, SMB) and web browsing. It primarily relies on signature-based detection.
- Anti-Spyware: Identifies and blocks spyware downloads and Command-and-Control (C2) traffic originating from compromised hosts attempting to communicate with external malicious servers. This also includes features like DNS Sinkholing.
- Vulnerability Protection: Protects against known software vulnerabilities being exploited by attackers. It scans traffic for patterns matching known exploit techniques targeting client and server applications.
- WildFire Integration (Basic): TP leverages verdicts from the WildFire cloud-based threat analysis service. If WildFire has previously analyzed a file or URL and determined it to be malicious, TP can block it based on this verdict delivered via signature updates.
Threat Prevention relies heavily on regularly updated Content Updates which contain the latest signatures for malware, spyware C2, and vulnerabilities.
Threat Prevention: Detailed Feature Explanations
Let's delve deeper into the core components of the standard Threat Prevention subscription:
Antivirus Profiles
- Detection Mechanism: Primarily uses a stream-based engine to scan traffic for known malware signatures as files are transferred.
- WildFire Integration: Leverages WildFire signatures. When WildFire identifies a new piece of malware, a signature is generated and distributed via Content Updates, allowing TP Antivirus profiles to block it.
- Protocol Decoders: Uses specific decoders (e.g., for HTTP, SMTP, IMAP, POP3, FTP, SMB) to reassemble files and scan them.
- Actions: Configurable actions per decoder and verdict (e.g., `alert`, `block`, `reset-client`, `reset-server`, `reset-both`). The `block` action prevents the malicious file transfer.
- File Blocking: While technically part of File Blocking profiles, Antivirus profiles often work in conjunction, focusing on *malicious* files vs. just blocking specific file *types*.
Anti-Spyware Profiles
- Detection Mechanism: Uses signatures to detect known spyware downloads and malicious Command-and-Control (C2) traffic patterns (e.g., beaconing, specific URLs/IPs used by botnets).
- Threat Categories: Signatures are categorized (e.g., critical, high, medium, low severity). Actions can be set per category.
- DNS Sinkholing: A crucial feature. Allows the firewall to intercept DNS queries for known malicious domains and redirect the client to a Palo Alto Networks Sinkhole IP or an internal IP address. This prevents compromised hosts from reaching their C2 servers and helps identify infected machines.
- Actions: Similar to Antivirus (`alert`, `block`, `reset-client`, etc.). `block` stops the C2 communication or spyware download. Sinkholing is a specific action configured within the profile.
Vulnerability Protection Profiles
- Detection Mechanism: Scans traffic (client-to-server and server-to-client) for patterns matching known vulnerability exploits. This protects unpatched systems from being compromised.
- Signatures: Based on known CVEs (Common Vulnerabilities and Exposures) and other identified exploits.
- Actions: Configurable actions per signature or severity (`alert`, `block`, `reset-client`, etc.). `block` prevents the exploit attempt from reaching its target.
- Threat Exceptions: Allows administrators to create exceptions for specific signatures if they cause false positives or interfere with legitimate applications (use with caution!).
- Host Information Profile (HIP) Integration: Can leverage HIP data (if using GlobalProtect) to apply targeted vulnerability protection based on the host's patch level.
While effective against known threats, the standard Threat Prevention subscription's main limitation is its reliance on pre-existing signatures or WildFire verdicts, which inherently means there's a delay between the discovery of a new threat and the availability of protection.
Advanced Threat Prevention (ATP): Next-Generation Protection
Advanced Threat Prevention is a separate, premium subscription service that represents a significant evolution beyond the standard Threat Prevention capabilities. Its primary goal is to provide real-time protection against unknown, zero-day, and highly evasive threats directly within the firewall's data plane processing.
Key Enhancements Introduced by ATP:
- Inline Machine Learning (ML) / Deep Learning: ATP leverages sophisticated ML models, executed directly on the firewall (or via cloud query), to analyze traffic patterns and file characteristics in real-time. This allows it to detect and block never-before-seen malware and phishing attacks *without* relying on signatures.
- Zero-Day Exploit Prevention: Goes beyond basic signature matching for vulnerabilities. ATP engines analyze traffic for exploit *techniques* and anomalies indicative of an attempt to exploit unknown vulnerabilities, providing inline protection.
- Advanced Command-and-Control (C2) Detection: Utilizes ML and behavioral analysis to detect sophisticated C2 communication patterns (e.g., tunneling, unusual beaconing) that may evade traditional signature-based detection.
- Rapid Response via Cloud: ATP leverages Palo Alto Networks' cloud infrastructure for continuous updates to ML models and threat intelligence, enabling faster adaptation to emerging threats compared to traditional content update cycles.
ATP aims to drastically reduce the time-to-detection and time-to-prevention for sophisticated attacks that bypass traditional security measures.
Advanced Threat Prevention: Key ATP-Specific Features
The power of ATP lies in its advanced detection engines that operate inline:
Inline Deep Learning / Machine Learning for Malware Prevention
- Mechanism: Analyzes file characteristics (e.g., structure, code snippets, metadata) and network traffic patterns using ML models trained on vast datasets.
- Focus: Detects zero-day malware (especially PE files like EXEs, DLLs initially, but expanding) and malicious scripts embedded in web traffic (e.g., JavaScript, VBScript) or files (e.g., Office macros). Can also detect malicious URLs and phishing attempts based on content and structure analysis.
- Benefit: Can block unknown threats instantly ( sub-second prevention ) without needing prior signatures or sandbox analysis. This significantly shrinks the window of exposure.
- Operation: Happens inline as part of the firewall's single-pass architecture when ATP is licensed and configured in relevant Security Profiles (often appearing as enhanced options within Antivirus or new profile types).
Inline Zero-Day Exploit Prevention
- Mechanism: Enhanced capabilities within (or alongside) the Vulnerability Protection engine. Instead of just matching known CVE signatures, it looks for common exploit *techniques* (e.g., buffer overflows, heap sprays, ROP chains) used by attackers.
- Focus: Detects attempts to exploit unknown (zero-day) vulnerabilities in applications and operating systems.
- Benefit: Provides protection against exploits for which no signature exists yet.
Advanced Command-and-Control (C2) Detection
- Mechanism: Uses ML and behavioral analysis on network traffic (often leveraging DNS traffic analysis, potentially integrating features previously part of DNS Security) to identify patterns indicative of C2 communication.
- Focus: Detects stealthy C2 channels like DNS tunneling, domain generation algorithms (DGAs), unusual beaconing intervals, and connections to newly registered domains often used by malware.
- Benefit: Catches C2 traffic missed by signature-based Anti-Spyware profiles.
Cloud-Delivered Security Services
- Mechanism: ATP relies heavily on the cloud for updates to its ML models, real-time threat intelligence feeds (e.g., malicious domain lists), and potentially for cloud-assisted analysis for certain detections.
- Benefit: Ensures the firewall has the latest protections against rapidly evolving threats, often updated much faster than traditional content releases.
In essence, ATP shifts the paradigm from primarily reactive (blocking known bad) to proactive and predictive (identifying and blocking unknown threats based on malicious characteristics and behaviors).
Feature Comparison: Threat Prevention vs. Advanced Threat Prevention
This table summarizes the key capabilities and differences:
| Feature / Aspect | Threat Prevention (TP) | Advanced Threat Prevention (ATP) |
|---|---|---|
| Core Subscription | Foundation Subscription | Premium Subscription (Includes all TP features) |
| Primary Focus | Known Threats (Malware, Spyware C2, Exploits) | Known Threats + Unknown/Zero-Day Threats (Malware, Exploits, C2) |
| Antivirus (Known Malware) | Yes (Signature-based, WildFire Signatures) | Yes (Signature-based, WildFire Signatures) |
| Anti-Spyware (Known C2/Spyware) | Yes (Signature-based, DNS Sinkholing) | Yes (Signature-based, DNS Sinkholing) |
| Vulnerability Protection (Known Exploits) | Yes (Signature-based - CVEs) | Yes (Signature-based - CVEs) |
| Inline ML/DL (Zero-Day Malware/Phishing) | No | Yes (Key differentiator - Real-time inline detection) |
| Inline Zero-Day Exploit Prevention | Limited / No (Relies on known signatures) | Yes (Analyzes exploit techniques inline) |
| Advanced C2 Detection (ML-Based) | Limited / No (Relies on known signatures) | Yes (Detects DGAs, tunneling, behavioral anomalies - often integrates DNS Security features) |
| Detection Method for Unknown Threats | Relies primarily on WildFire (Offline Sandbox Analysis -> Signature) | Inline ML/Behavioral Analysis + WildFire |
| Speed of Protection (Zero-Day) | Delayed (Requires WildFire analysis + signature creation/distribution) | Near Real-time / Instant (For threats detected by inline engines) |
| Licensing | Standard Subscription | Premium Subscription (Separate license required) |
Key Differences & PCNSE Focus
Boiling down the comparison, the most critical distinctions relevant for PCNSE understanding are:
-
Scope: Known vs. Unknown Threats:
- TP: Excellent baseline protection against threats that are already known and have signatures or WildFire verdicts.
- ATP: Extends protection significantly into the realm of unknown, zero-day, and evasive threats by adding inline analysis capabilities that don't solely rely on prior knowledge.
-
Detection Mechanism for New Threats:
- TP: Primarily reactive. Relies on Content Updates (signatures) derived from sources like WildFire analysis. There's an inherent delay.
- ATP: Proactive and predictive. Uses inline ML and behavioral analysis to identify malicious characteristics *as traffic flows*, enabling immediate blocking without waiting for signatures.
-
Speed of Prevention for Zero-Days:
- TP (+ WildFire): Prevention occurs *after* WildFire analysis and signature distribution (minutes to hours).
- ATP: Prevention can occur *instantly* (sub-second) if the inline engines detect the threat. This dramatically reduces risk.
-
Licensing and Configuration:
- TP: A standard license. Features configured in Antivirus, Anti-Spyware, Vulnerability Protection profiles.
- ATP: A premium, separate license. It *enables* advanced engines and options within the existing Security Profiles (or potentially new ATP-specific profiles/settings depending on PAN-OS version). You still configure these profiles and attach them to Security Policy rules.
You don't need to buy *both* TP and ATP. ATP includes all TP functionality. If you purchase ATP, you gain the advanced inline features on top of the standard signature-based protections. -
Integration with Other Services (e.g., DNS Security):
- TP: Basic DNS Sinkholing via Anti-Spyware profiles.
- ATP: Often incorporates the advanced detection capabilities of the DNS Security subscription (ML-based DGA detection, tunneling detection, etc.), potentially simplifying licensing needs. Always verify current bundles and features.
PCNSE Scenario Example
Scenario: An organization wants the fastest possible protection against ransomware delivered via executable files downloaded from the web, even if the specific ransomware variant has never been seen before.
Solution Focus: This scenario screams for Advanced Threat Prevention . While standard TP with WildFire would eventually detect and block the ransomware after analysis, ATP's inline machine learning engine has the potential to analyze the downloaded executable file in real-time and block it immediately based on malicious characteristics, preventing infection *before* a signature is available.
Configuration: Ensure the ATP license is active, configure an Antivirus profile with relevant actions and ensure the inline ML features within it (or related ATP settings) are enabled, and apply this profile to the Security Policy rule governing web browsing traffic.
Understanding these differences is crucial for recommending, implementing, and troubleshooting the appropriate level of threat protection based on organizational risk tolerance and security requirements.
Illustrations: Simplified Processing Flow
This diagram illustrates conceptually where Threat Prevention and Advanced Threat Prevention fit into the firewall's packet processing flow (highly simplified):
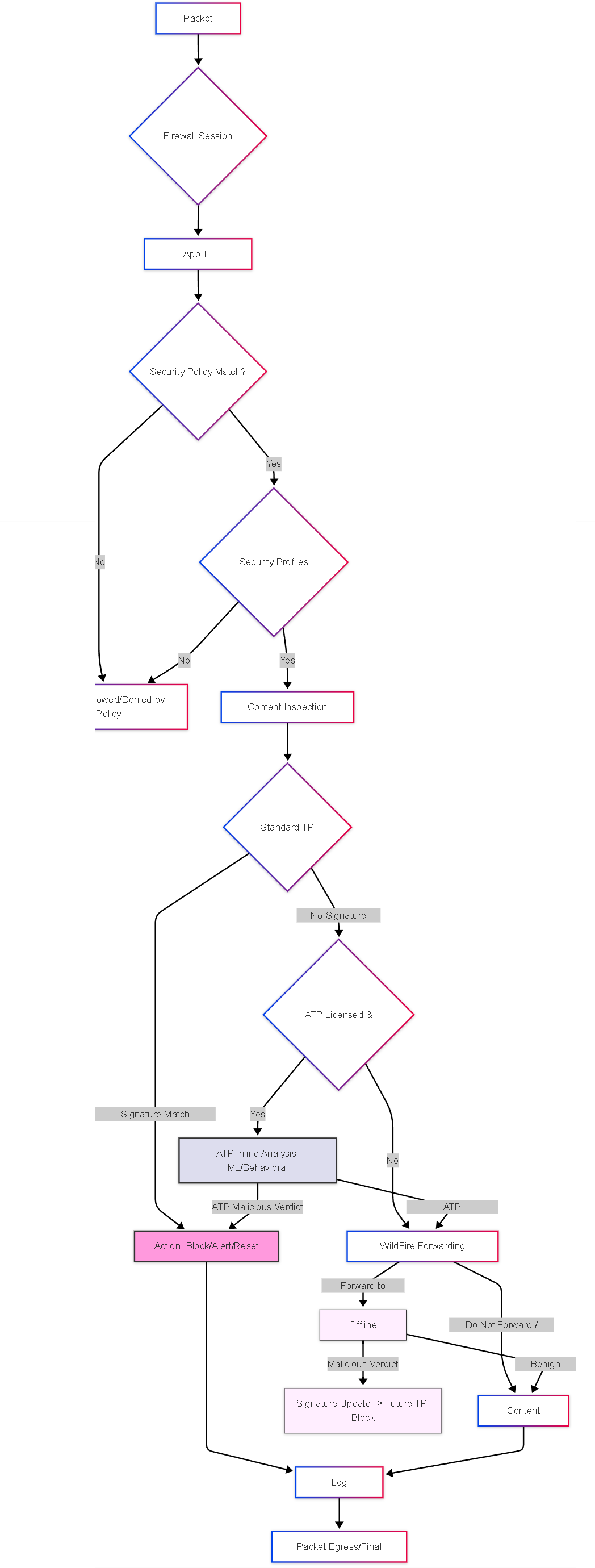
Simplified flow showing standard TP checks followed by ATP inline analysis if licensed. WildFire remains a crucial component for broader analysis.
Illustrations: Threat Detection Sequence Example
This sequence diagram shows a potential interaction flow when a user downloads a file, comparing paths with TP only vs. ATP:
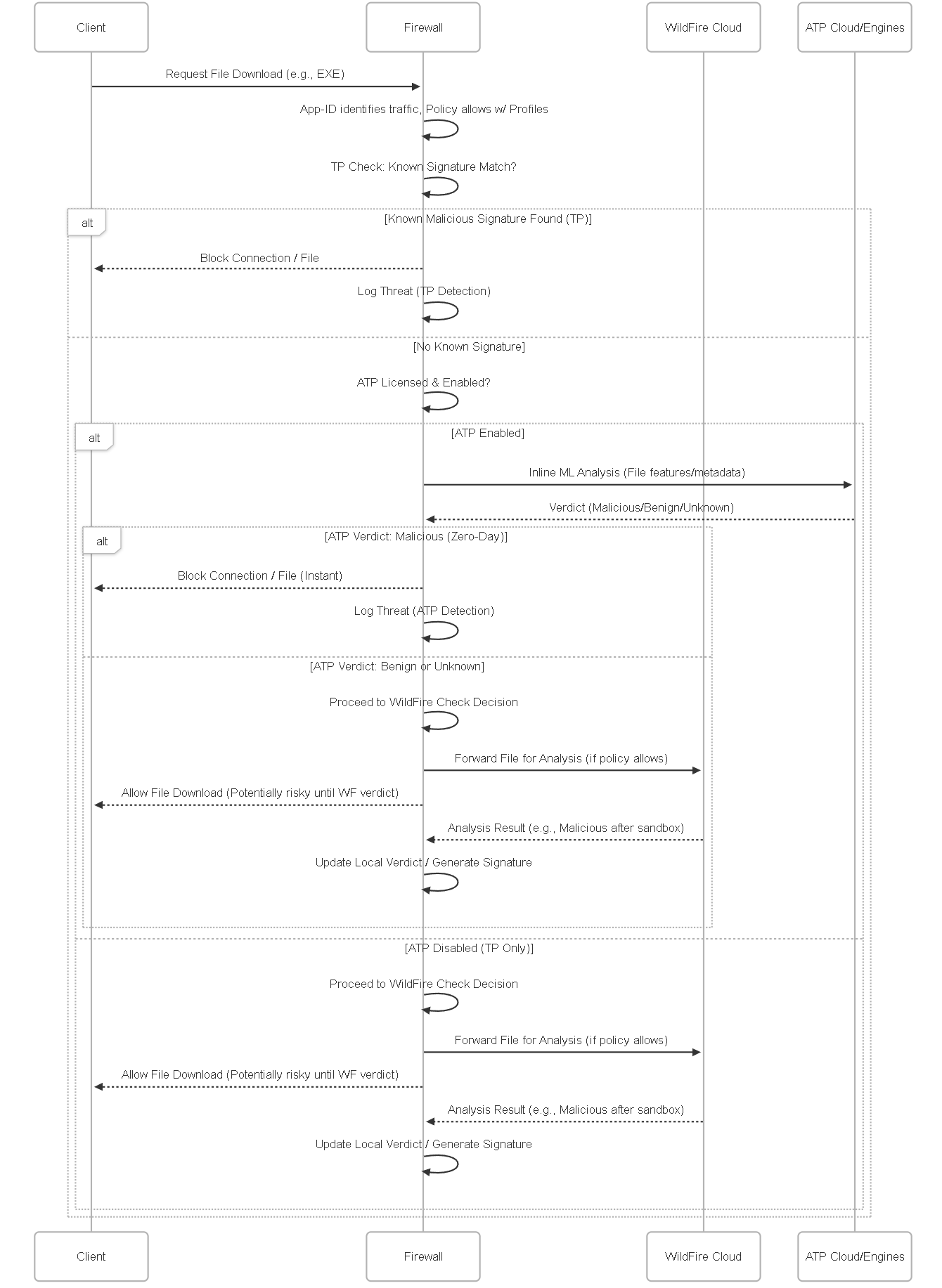
Sequence showing how ATP provides an earlier, inline detection opportunity compared to relying solely on WildFire's offline analysis for unknown threats.
Illustrations: Simplified Threat State Example
This state diagram illustrates the possible states of a potentially malicious file as it's processed:
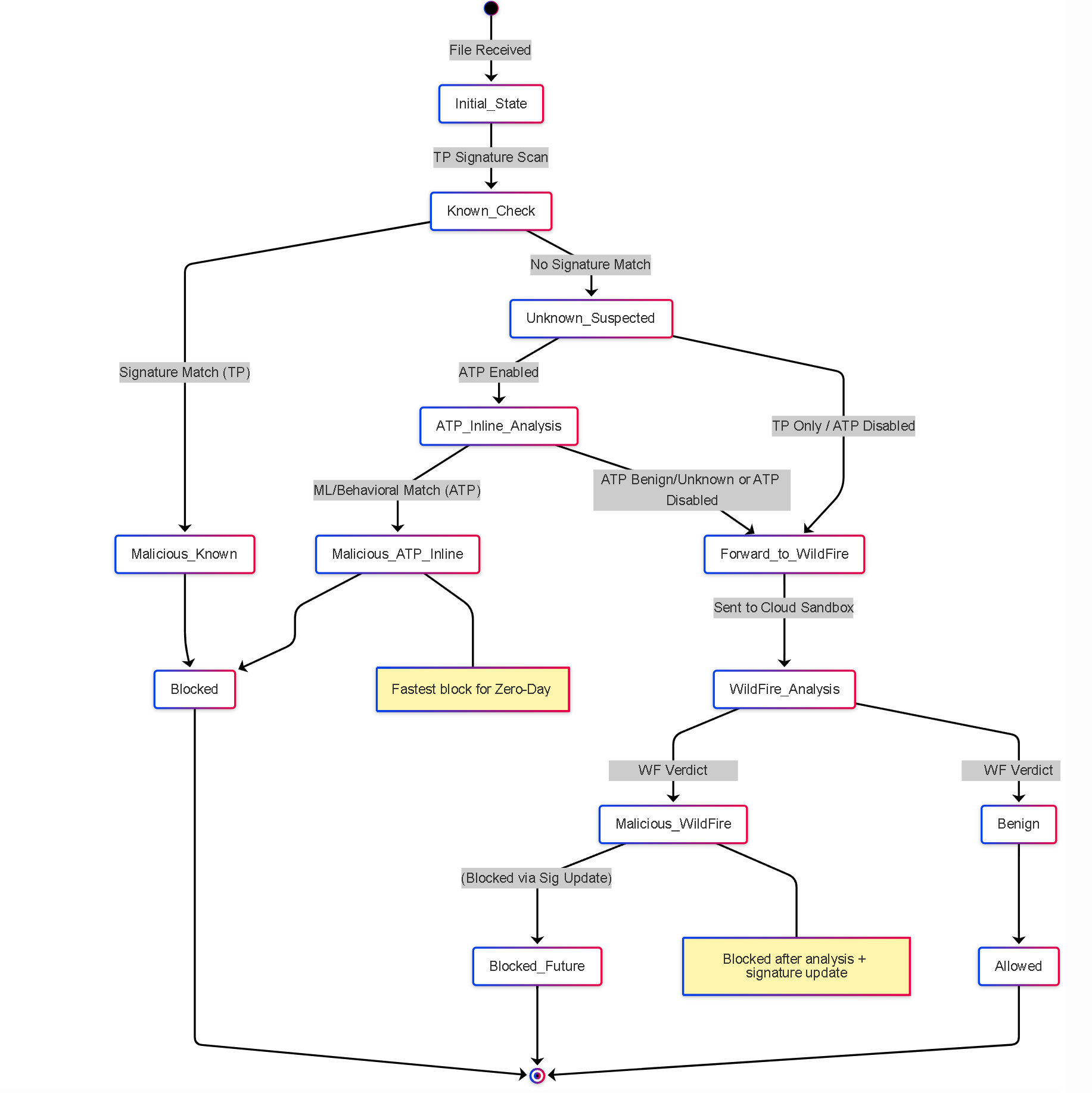
State diagram showing how ATP introduces an "Inline Analysis" state that can lead to faster blocking (`Malicious_ATP_Inline`) compared to the traditional path through WildFire for unknown threats.
PCNSE Prep Quiz: TP vs. ATP
Test your understanding of Palo Alto Networks Threat Prevention and Advanced Threat Prevention with these PCNSE-style questions.