Tuning and Adding Exceptions to Palo Alto Networks Security Profiles
Overview
Palo Alto Networks Security Profiles (including Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, and Data Filtering) are powerful tools for inspecting traffic and enforcing security policy. However, default profiles or strict settings might sometimes generate false positives (blocking legitimate traffic) or excessive alerts for benign events in a specific environment.
Tuning these profiles involves adjusting their settings and creating exceptions to achieve a balance between robust security and operational usability. This process helps:
- Reduce false positives, ensuring business-critical applications remain available.
- Minimize alert fatigue for security operations teams.
- Optimize firewall performance by avoiding unnecessary inspection cycles where appropriate.
- Tailor security posture to the organization's specific risk tolerance and traffic patterns.
Creating Exceptions: General Process
Adding an exception allows you to modify the firewall's response to a specific threat signature, overriding the default action or the action defined by the profile's rules.
Implementation Steps
-
Identify the Signature / Threat ID
The first step is to pinpoint the exact signature causing the false positive or requiring a modified action. Use the firewall's logs for this:
- Navigate to Monitor > Logs > Threat .
- Locate the log entry corresponding to the event you want to address.
- Note the Threat ID (a numerical identifier) and the Threat Name associated with the signature.
Accurate identification of the Threat ID is crucial for creating the correct exception. -
Modify the Security Profile
Navigate to the specific Security Profile type where the exception is needed:
- Antivirus: Objects > Security Profiles > Antivirus
- Anti-Spyware: Objects > Security Profiles > Anti-Spyware
- Vulnerability Protection: Objects > Security Profiles > Vulnerability Protection
Note that exceptions are configured within these specific profile types. URL Filtering, File Blocking, and Data Filtering profiles are tuned differently (e.g., custom categories, file type rules, data patterns).Select and edit the profile applied to the Security Policy rule governing the traffic where the exception is needed.
-
Add the Exception
- Within the selected profile, navigate to the Exceptions tab.
- Check the box Show all signatures (or similar wording depending on PAN-OS version) to make the search/add function available.
- Click Add (or use the search function) and enter the Threat ID you identified in Step 1.
- The signature details (Name, Severity, etc.) should populate.
- Check the Enable box next to the signature ID.
-
Select the desired
Action
for this specific signature from the dropdown. Available actions typically include:
-
default: Use the action defined by Palo Alto Networks for the signature or the profile rule it matches. -
allow: Permit the traffic without logging a threat event for this signature. (Use with extreme caution). -
alert: Generate a Threat log entry but allow the traffic. (Good for monitoring). -
drop: Drop the packets associated with the threat (no TCP reset sent). -
reset-client: Send a TCP reset to the client-side connection. -
reset-server: Send a TCP reset to the server-side connection. -
reset-both: Send TCP resets to both client and server. -
block: (Often synonymous with drop for non-TCP, or reset for TCP, depending on profile type/version - primarily used in AS/VP). Blocks the threat activity.
-
- (Optional, see next section) Configure IP Address Exemptions if needed.
- Click OK .
Know the different exception actions and their impact (allow vs alert vs drop/reset/block). `Allow` completely bypasses detection for that signature, while `Alert` provides visibility without blocking. -
Commit the Changes
After configuring the exception(s), Commit the changes to the firewall for them to take effect.
Process Diagram
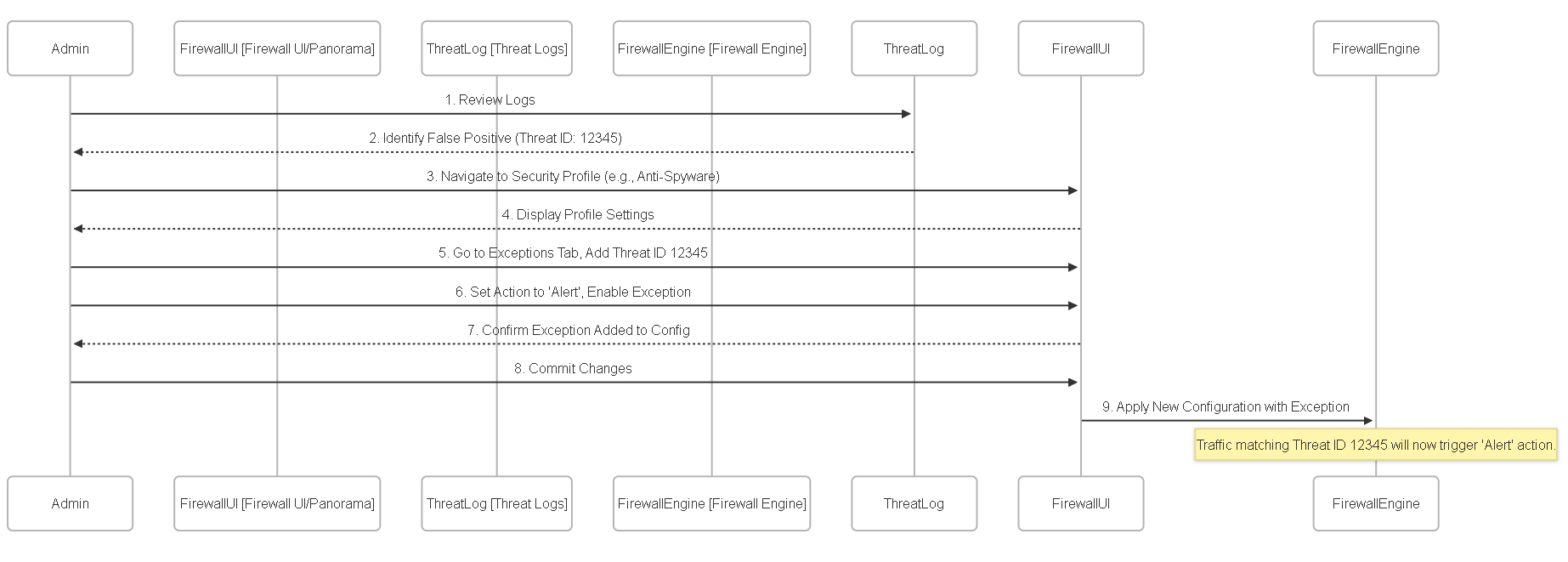
Sequence diagram illustrating the process of adding a general threat exception.
Creating Exceptions: IP-Based Exemptions
For more granular control, Palo Alto Networks allows you to create exceptions in Vulnerability Protection and Anti-Spyware profiles that apply only when specific source or destination IP addresses are involved in the session.
This is useful when a signature correctly identifies a threat in general, but triggers a false positive only when communicating with a specific trusted internal server or originating from a particular test machine.
Key Points
- Scope Limitation: The modified exception action (e.g., `allow`, `alert`) applies only to traffic matching the signature AND involving one of the specified IP addresses (as source OR destination).
- Default Action Applies Otherwise: Traffic matching the signature but NOT involving the exempted IPs will still be subject to the profile's default action (or the action defined by profile rules).
- IP Address Limit: You can add up to 100 IP addresses (or network objects/ranges) per signature exception.
- IP-Based Only: Exceptions cannot be based on user identity (User-ID); they are strictly IP address-based.
Implementation Steps
The process starts the same as adding a general exception:
- Identify the Threat Signature: Find the Threat ID in Monitor > Logs > Threat .
- Modify the Security Profile: Go to Objects > Security Profiles > Vulnerability Protection or Anti-Spyware , select the profile, and go to the Exceptions tab.
- Locate and Enable Signature: Find the signature via Threat ID, check Enable , and set the desired exception Action (e.g., `alert`).
-
Add IP Address Exemptions:
- In the same row for the enabled signature exception, find the column labeled IP Address Exemptions .
- Click Add (or the link within the column).
- Enter the specific IP addresses (IPv4 or IPv6), address objects, or address groups that should be exempted. You are essentially defining "apply this exception action *only if* the source OR destination IP matches one of these".
- Click OK to add the IPs to the exemption list for that signature.
(Conceptual Placeholder: Image showing the 'IP Address Exemptions' column in the profile exceptions tab where IPs are added)Adding specific IP addresses to the exemption list for a threat signature exception. - Commit the Changes: Commit the configuration.
IP Exemption Logic Diagram
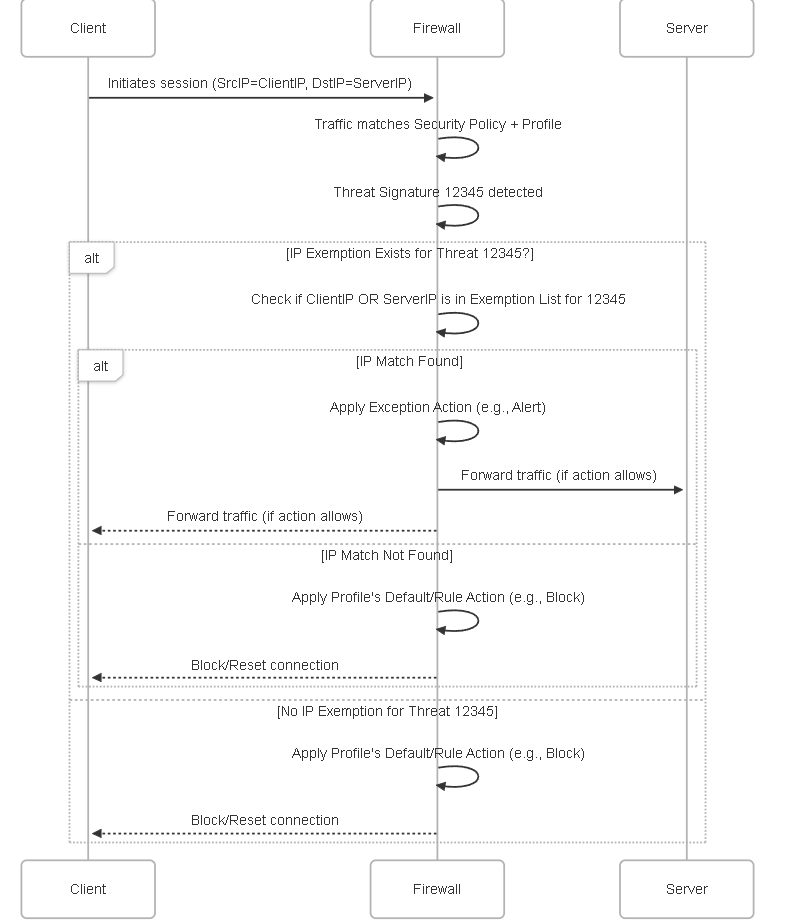
Sequence diagram showing how IP address exemptions affect the action taken for a detected threat.
Creating Exceptions: Considerations
Before adding exceptions, consider the following:
- False Positive Verification: Thoroughly investigate why a signature is triggering. Is it truly a false positive, or is it detecting potentially unwanted but legitimate application behavior, or even actual malicious activity? Use packet captures (PCAPs) enabled via profile actions and Threat Vault details to understand the signature context.
- Risk Assessment: If the traffic is legitimate but triggers a signature, assess the risk of allowing it. Can the application be reconfigured? Is there an updated version? Allowing traffic that matches a valid threat signature, even if benign in context, carries inherent risk.
- Scope: Use IP address exemptions whenever possible to limit the scope of an exception rather than applying it globally.
- Action Choice: Prefer `alert` over `allow` initially when creating an exception. Monitor the alerts to confirm the exception behaves as expected and only affects the intended traffic before considering `allow` (if absolutely necessary and the risk is accepted).
- Documentation: Document every exception added. Include the Threat ID, the reason for the exception, the date it was added, the associated application/hosts, and the responsible administrator.
- Regular Review: Periodically review all configured exceptions (e.g., quarterly or semi-annually). Signatures get updated, applications change, and environments evolve. An exception valid today might become a security risk tomorrow. Remove exceptions that are no longer necessary.
- Content Updates: Keep Threat content versions up-to-date. Sometimes, a false positive might be fixed in a newer content release, eliminating the need for an exception.
Tuning Best Practices
Effective Security Profile tuning goes beyond just adding exceptions. It involves a strategic approach to applying and refining profiles over time.
- Start with Best Practices: Leverage Palo Alto Networks' recommended best practice profiles (often available as predefined options like "strict" or documented guidelines) as a starting point. These profiles typically block known critical/high/medium threats.
- Use "Alert-Then-Block": For new deployments or when applying stricter profiles to sensitive segments, initially set the action for medium or potentially problematic signatures/categories to `alert` instead of `block` or `drop`. Monitor the Threat logs closely.
- Analyze Alerts: Investigate the alerts generated. Use Threat Vault, packet captures, and application/server owner input to determine if they are false positives or legitimate threats.
- Gradual Blocking: Once confident that an alerted signature represents a real threat or unwanted traffic, change the action in the profile to `block`, `drop`, or `reset`.
- Phased Rollout: Apply stricter profiles or changes to less critical network segments first. Use Security Profile Groups applied to specific policies targeting test groups or zones before applying changes broadly.
- Leverage SSL Decryption: A significant portion of modern traffic is encrypted. Implement SSL Decryption where possible and appropriate (considering privacy and regulations) to allow Security Profiles (URL Filtering, VP, AS, File Blocking, Data Filtering) to inspect encrypted payloads.
-
Tune URL Filtering:
- Block high-risk categories like malware, phishing, command-and-control, questionable, proxy-avoidance.
- Consider blocking the `unknown` URL category after an initial monitoring period to identify and re-categorize legitimate business sites. Unknown sites often host new threats.
- Create custom URL categories for specific allow/block requirements.
-
Tune File Blocking:
- Start with the 'strict' profile, which blocks many high-risk file types (.exe, .dll, script files, etc.).
- Identify necessary exceptions based on business needs (e.g., allowing specific types for updates or specific applications) but apply them narrowly using dedicated rules if possible.
- Use the 'Direction' setting to control uploads vs. downloads.
-
Tune Data Filtering:
- Use predefined patterns (Credit Card, SSN) and custom patterns carefully.
- Expect false positives initially; work closely with users to refine patterns and thresholds (Alert Threshold vs. Block Threshold).
- Implement a clear process for users to report false positive blocks.
- Zone Protection & DoS Profiles: While not Security Profiles in the same sense, tune Zone Protection and DoS profiles based on baseline traffic analysis (e.g., connections/packets per second) to protect the firewall and specific resources from volumetric attacks. Use 'alert' first.
- Regular Log Review: Continuously monitor Threat, URL Filtering, Data Filtering, and WildFire logs to identify emerging threats, policy gaps, and potential new false positives needing tuning.
- Documentation & Review Cycle: Maintain clear documentation for all profile settings and exceptions. Schedule regular reviews (e.g., quarterly) to reassess tuning decisions and remove unnecessary exceptions.
Diagrams: Tuning Concepts
Flowchart: Threat Signature Exception Handling
Flowchart showing the logic for applying threat exceptions, including IP-based exemptions.
State Diagram: Signature Action State
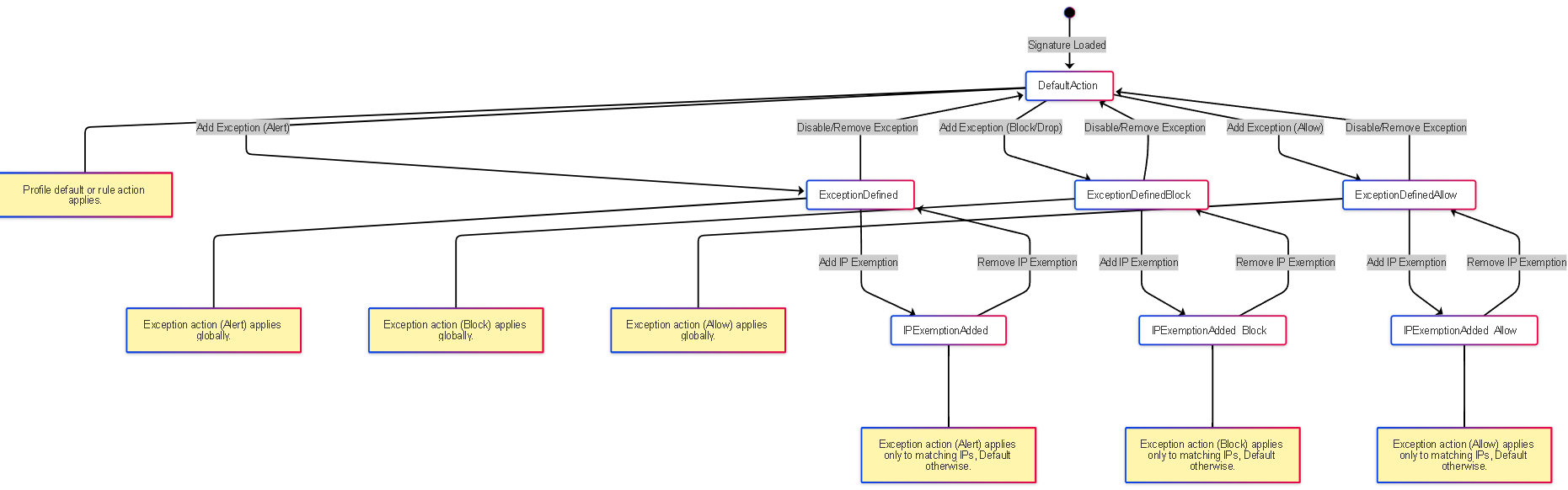
State diagram illustrating how adding exceptions and IP exemptions changes the action state for a specific signature.
Graph: Tuning Ecosystem Components
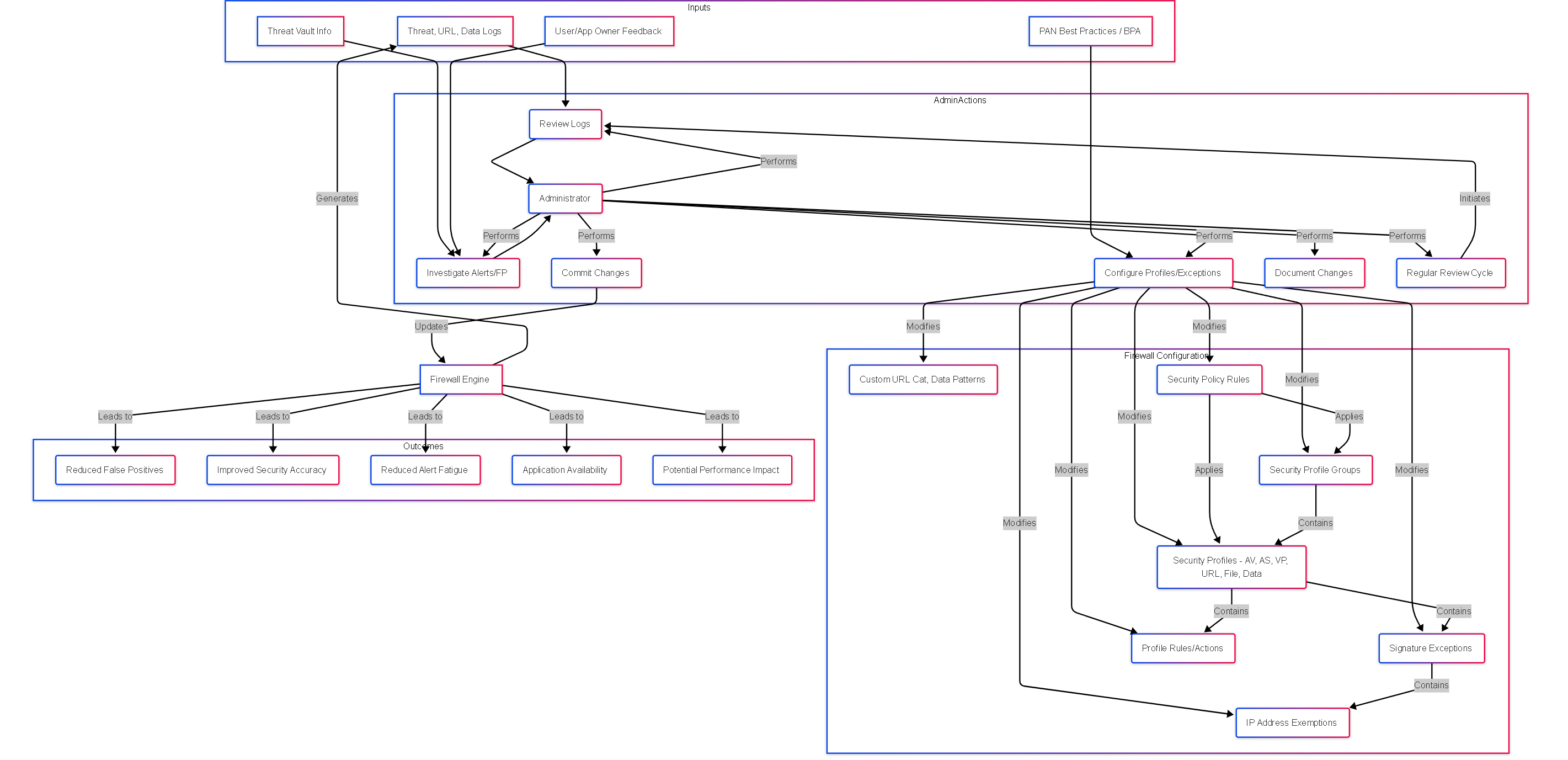
Graph showing the relationship between logs, admin actions, configuration objects, and outcomes in the security profile tuning process.
Security Profile Tuning Knowledge Check
Test your understanding of tuning Palo Alto Networks Security Profiles.