Palo Alto Networks LSVPN: Mastering One-to-One and One-to-Many Topologies for PCNSE
This guide provides an in-depth exploration of Palo Alto Networks' Large Scale VPN (LSVPN) technology, focusing on one-to-one and one-to-many deployment topologies. It is designed to offer comprehensive, practical insights essential for network security professionals and those preparing for the Palo Alto Networks Certified Network Security Engineer (PCNSE) certification.
1. Deep Dive into Palo Alto Networks LSVPN Fundamentals
Palo Alto Networks' Large Scale VPN (LSVPN) is a powerful feature integrated within PAN-OS that simplifies and automates the creation of secure, scalable hub-and-spoke IPSec VPN networks. It leverages components of the GlobalProtect framework – specifically the Portal and Gateways – to manage and establish IPSec tunnels with remote Palo Alto Networks Next-Generation Firewalls (NGFWs) acting as LSVPN Satellites. This architecture is designed to reduce the administrative overhead typically associated with deploying and managing numerous site-to-site VPNs.
1.1 Key Components of Palo Alto Networks LSVPN
Understanding the role of each component is crucial for designing, deploying, and troubleshooting LSVPN environments:
-
GlobalProtect Portal (Hub Firewall):
- Role: Acts as the central management point for LSVPN Satellites. It authenticates Satellites and provides them with their VPN configuration, including information about available GlobalProtect Gateways, IPSec settings, and network routes.
- Implementation: Typically configured on a high-availability pair of Palo Alto Networks NGFWs at the central/hub location.
- Key Functions: Satellite authentication, configuration distribution, Gateway list provision.
-
GlobalProtect Gateway(s) (Hub Firewall(s)):
- Role: These are Palo Alto Networks NGFWs at the hub site(s) that terminate IPSec tunnels from LSVPN Satellites. They enforce security policies on traffic traversing the tunnels.
- Implementation: Can be one or more NGFWs. Multiple Gateways provide redundancy and load distribution.
- Key Functions: IPSec tunnel termination, security policy enforcement for tunneled traffic, routing between remote sites and hub resources.
-
LSVPN Satellite (Remote NGFW):
- Role: A Palo Alto Networks NGFW located at a remote site (e.g., branch office). It initiates a connection to the GlobalProtect Portal to retrieve its configuration and then establishes IPSec tunnels to the designated GlobalProtect Gateway(s).
- Implementation: Any PAN-OS firewall capable of acting as a GlobalProtect Satellite.
- Key Functions: Portal authentication, configuration retrieval, IPSec tunnel initiation to Gateway(s).
-
Panorama (Optional but Recommended for Scale):
- Role: While not a direct LSVPN component, Panorama, Palo Alto Networks' network security management platform, is highly recommended for managing LSVPN deployments, especially at scale. It simplifies the configuration of Portals, Gateways, and Satellites through templates and device groups.
- Key Functions: Centralized configuration, policy management, monitoring, and logging for all firewalls in the LSVPN.
1.2 Core Benefits of LSVPN in the Palo Alto Networks Ecosystem
- Scalability: Easily connect hundreds or thousands of remote sites without manually configuring individual IPSec tunnels on the hub firewall for each remote site.
- Centralized Management: The GlobalProtect Portal acts as a central point for distributing VPN configurations to Satellites. Panorama further enhances this by managing the Portal, Gateway, and Satellite firewall configurations.
- Simplified Deployment: Adding a new remote site (Satellite) is streamlined. The Satellite automatically fetches its configuration, reducing manual intervention.
- Dynamic Tunnel Establishment: Satellites dynamically establish tunnels based on the configuration received from the Portal.
- Redundancy and High Availability: Supports multiple Gateways, allowing Satellites to connect to alternate Gateways if a primary Gateway fails.
- Consistent Security Posture: Security policies, including App-ID, User-ID, and Content-ID, are enforced on traffic passing through the LSVPN tunnels by Palo Alto Networks NGFWs.
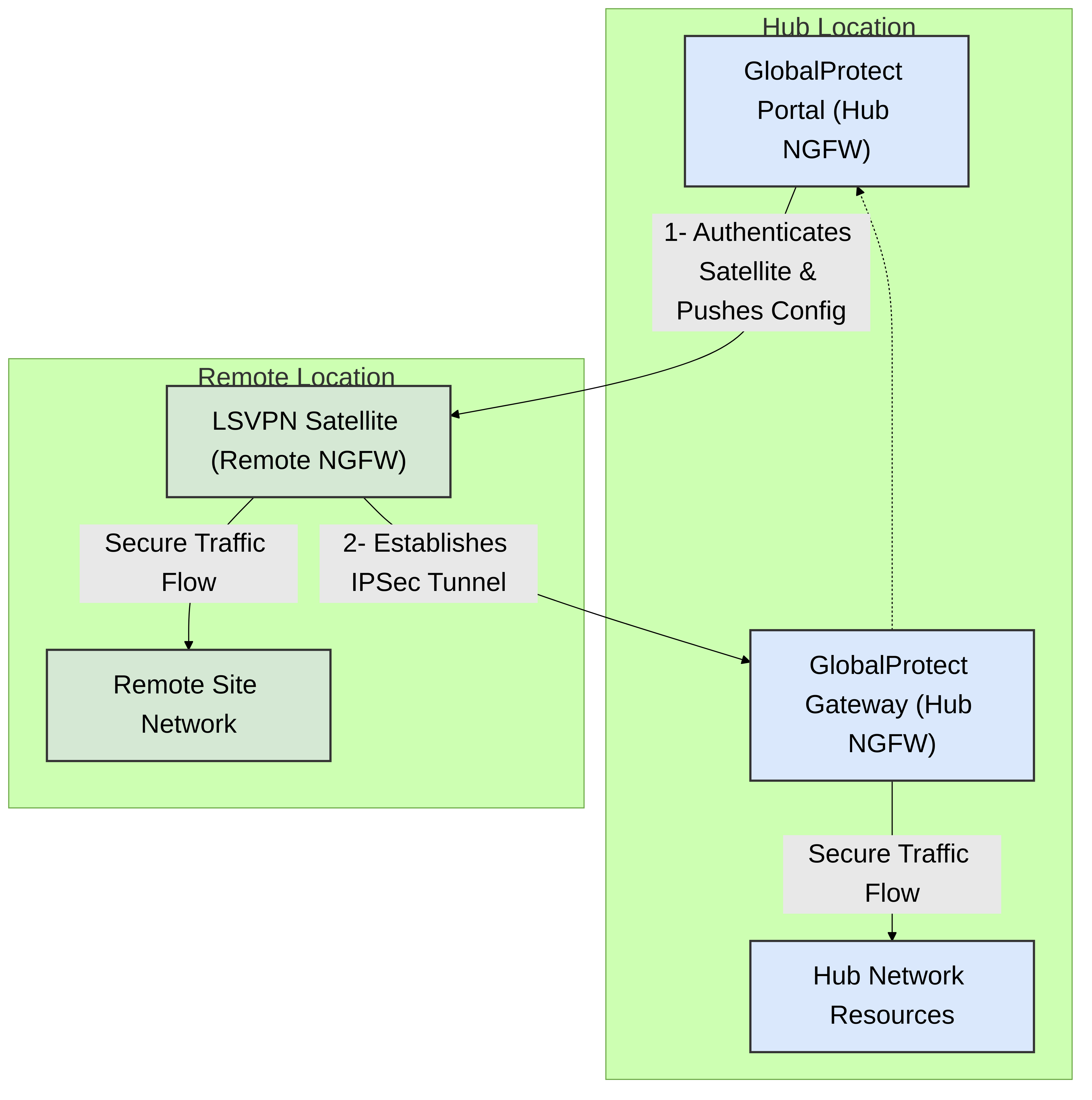
Figure 1: Basic Palo Alto Networks LSVPN Architecture illustrating the interaction between Portal, Satellite, and Gateway.
2. One-to-One LSVPN Topology
In a one-to-one LSVPN topology, a single LSVPN Satellite (remote Palo Alto Networks NGFW) connects to a single GlobalProtect Gateway (hub Palo Alto Networks NGFW). The Satellite still retrieves its configuration from a GlobalProtect Portal, which could be on the same NGFW as the Gateway or a separate one.
2.1 Characteristics and Use Cases
- Simplicity: This is the most straightforward LSVPN deployment.
- Direct Connection: The Satellite establishes an IPSec tunnel directly to its assigned Gateway.
-
Palo Alto Networks Use Cases:
- Connecting a small branch office or retail store with a single Palo Alto Networks NGFW to a central data center.
- Specific site-to-site connections where LSVPN's dynamic configuration benefits are desired over traditional IPSec tunnels, even for a single connection.
- Proof-of-concept LSVPN deployments before scaling out.
2.2 Configuration Highlights (Palo Alto Networks Perspective)
- Portal Configuration: The Portal is configured with the Satellite's information (e.g., serial number or certificate for authentication) and the details of the single Gateway it should connect to.
- Gateway Configuration: The Gateway is configured to accept connections from authorized Satellites.
- Satellite Configuration: The Satellite NGFW is configured with the Portal's address. Upon connecting, it receives the Gateway information and tunnel parameters.
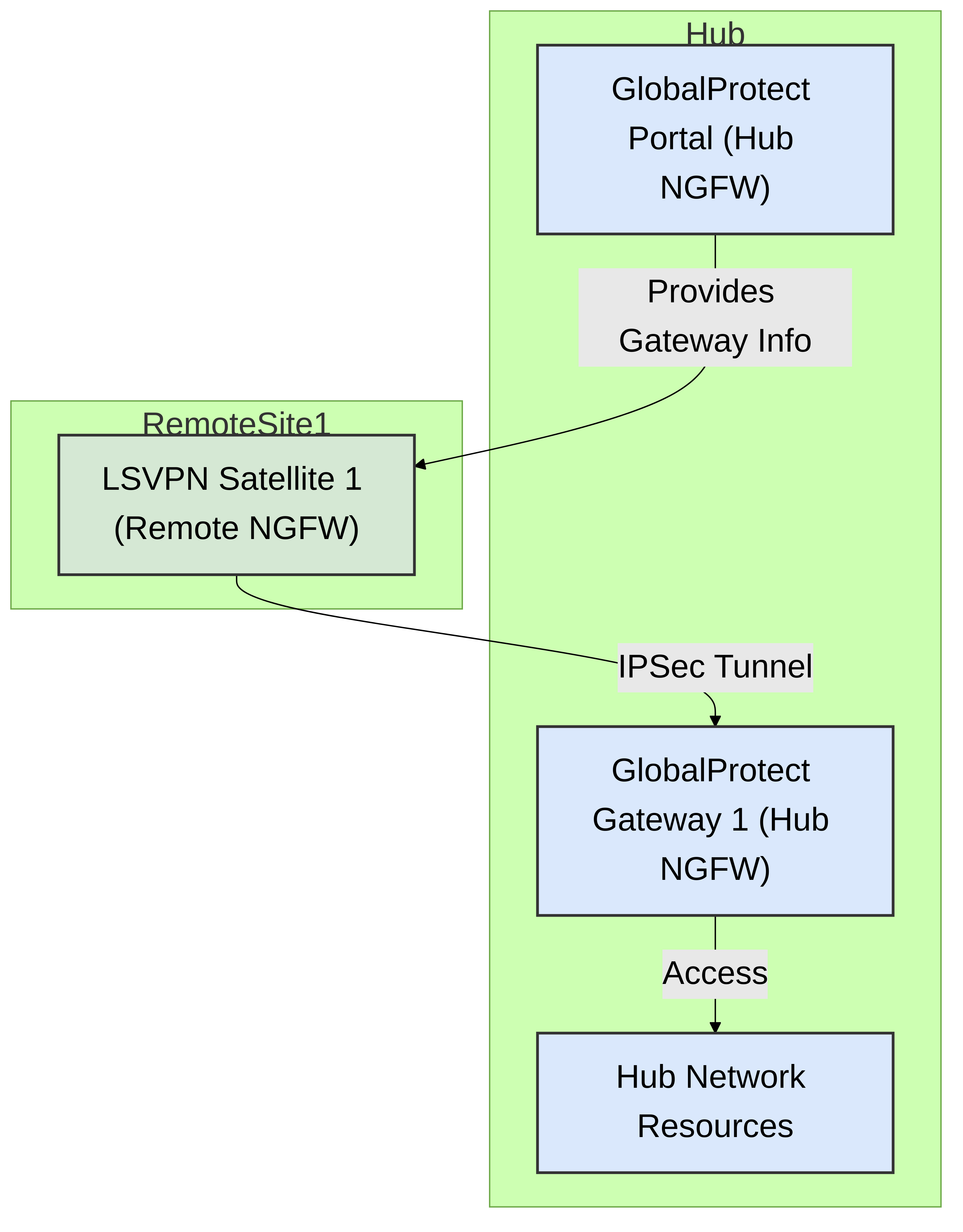
Figure 2: Palo Alto Networks One-to-One LSVPN Topology. A single Satellite connects to a single Gateway after configuration retrieval from the Portal.
3. One-to-Many LSVPN Topology
A one-to-many LSVPN topology involves a single LSVPN Satellite connecting to multiple GlobalProtect Gateways. This model is designed to provide enhanced redundancy and potentially load distribution for critical remote sites.
3.1 Characteristics and Use Cases
-
High Availability:
If the primary Gateway becomes unavailable, the Satellite can establish a tunnel to a secondary (or tertiary, etc.) Gateway.
- PAN-OS allows configuration of Gateway priority. The Satellite will attempt to connect to Gateways in the order of priority specified in the configuration received from the Portal.
- Load Balancing/Distribution (Manual): While LSVPN itself doesn't perform dynamic per-packet load balancing across multiple active tunnels to different gateways for a single satellite, you can influence traffic paths using routing. For instance, different subnets at the remote site could be preferentially routed over tunnels to different gateways. However, true dynamic load balancing is more a feature of Palo Alto Networks SD-WAN.
-
Palo Alto Networks Use Cases:
- Critical branch offices requiring resilient connectivity to hub resources.
- Sites connecting to geographically distributed data centers, each with its own Gateway. The Satellite can connect to the "closest" or "primary" Gateway, with others as backup.
- Phased migrations or temporary connections to multiple hub locations.
3.2 Configuration Highlights (Palo Alto Networks Perspective)
-
Portal Configuration:
- The Portal configuration for the Satellite will list multiple Gateways.
- Gateway priority can be set (e.g., Gateway A - Priority 1, Gateway B - Priority 2). The Satellite will try to connect to Gateway A first. If it fails, it will try Gateway B.
- Preemptive behavior can be configured. If preemption is enabled, and a higher-priority gateway becomes available after the satellite has failed over to a lower-priority gateway, the satellite will attempt to switch back to the higher-priority gateway.
- Gateway Configuration: Each Gateway NGFW is configured to accept connections from authorized Satellites.
- Satellite Behavior: The Satellite receives the list of Gateways and their priorities. It attempts to establish an IPSec tunnel to the highest-priority available Gateway.
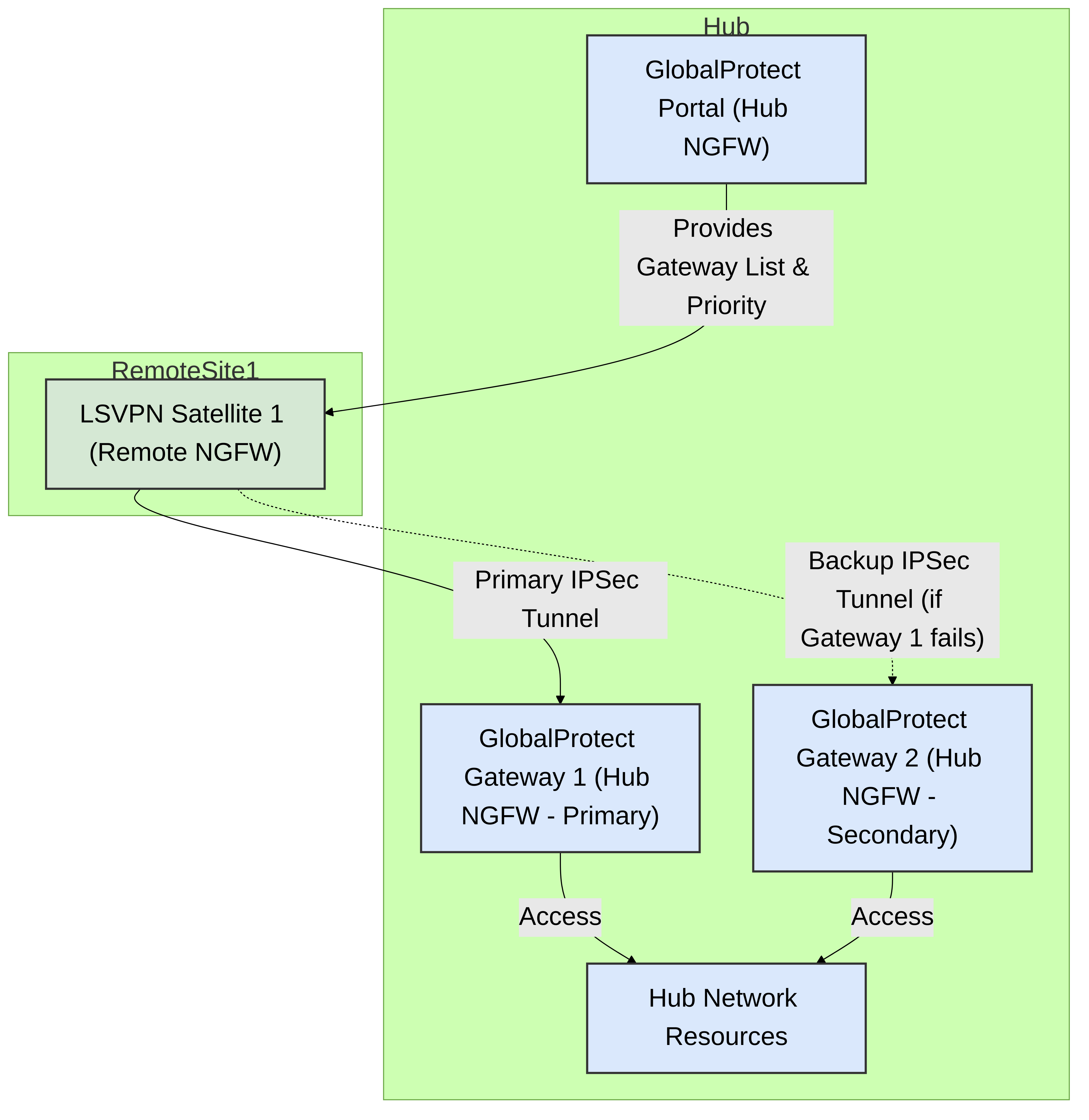
Figure 3: Palo Alto Networks One-to-Many LSVPN Topology. A single Satellite can connect to multiple Gateways, typically based on priority for redundancy.
4. In-Depth LSVPN Configuration on Palo Alto Networks NGFWs
Configuring LSVPN involves several key steps on the Palo Alto Networks NGFWs acting as Portal, Gateway(s), and Satellites. Panorama is highly recommended for managing these configurations, especially in larger deployments, using Templates and Template Stacks.
4.1 Prerequisites
- Palo Alto Networks NGFWs: At hub and remote locations, running compatible PAN-OS versions.
- Licensing: GlobalProtect subscription is required on the Portal and Gateways for LSVPN functionality. Satellites do not require a specific LSVPN license beyond their base NGFW license.
-
Certificates:
A robust Public Key Infrastructure (PKI) is essential.
- CA Certificate: The CA certificate that issues certificates to the Portal, Gateways, and Satellites must be trusted by all devices.
- Device Certificates: Portal, Gateways, and Satellites should have device certificates signed by the trusted CA. These are used for mutual authentication.
- Network Connectivity: IP reachability between Satellites and Portal, and Satellites and Gateways (on management and tunnel interfaces).
- NTP Synchronization: Ensure all firewalls have synchronized time for certificate validation and logging.
4.2 GlobalProtect Portal Configuration (Hub NGFW)
Navigate to Network > GlobalProtect > Portals > [Add/Edit Portal Configuration] :
-
General Tab:
- Specify the Network Interface that the Portal will listen on.
- Assign an IP address.
-
Authentication Tab:
- Create an SSL/TLS Service Profile that references the Portal's device certificate and the CA certificate(s) used to validate Satellite certificates.
- Configure a Client Authentication profile. For LSVPN, this typically uses certificate authentication. Specify a Certificate Profile that references the CA used to sign Satellite certificates and set a Username Field (e.g., Common Name).
-
Agent Tab (LSVPN Satellite Configuration):
-
Go to the
Satellite Configuration
tab within the Agent configuration.
Device GUI Path: Network > GlobalProtect > Portals > [Portal Name] > Agent > [Agent Config Name] > Satellite Configuration - Enable LSVPN: Check the "Enable Large Scale VPN (LSVPN)" box.
- Publish FQDN or IP: Provide the FQDN or IP address that Satellites will use to connect to this Portal.
- Manual Satellite Configuration (Optional): You can manually add Satellites by serial number for pre-approved devices. More commonly, dynamic registration is used where any Satellite with a valid certificate from the trusted CA can register.
-
Gateway Information:
- Add GlobalProtect Gateways that Satellites can connect to.
- Specify Gateway FQDN/IP, priority, and tunnel settings (e.g., IKE Crypto Profile, IPSec Crypto Profile, Tunnel Interface on Gateway).
-
Network Services (Access Routes):
Define which networks are accessible through the LSVPN tunnels. These routes are pushed to the Satellites.
- This is critical for routing traffic from remote sites to the hub and potentially to other remote sites (if hub-to-spoke-to-spoke communication is enabled and routed via the hub).
-
Go to the
Satellite Configuration
tab within the Agent configuration.
4.3 GlobalProtect Gateway Configuration (Hub NGFW)
Navigate to Network > GlobalProtect > Gateways > [Add/Edit Gateway Configuration] :
-
General Tab:
- Specify the Network Interface that the Gateway will listen on for tunnel connections.
- Assign an IP address.
-
Authentication Tab:
- Create an SSL/TLS Service Profile that references the Gateway's device certificate. (While LSVPN primarily uses IKEv2/IPSec, this profile is part of the GP Gateway config).
- Client Authentication is generally not needed here for LSVPN tunnel termination itself, as IKE handles authentication.
-
Agent Tab (Tunnel Settings):
-
Go to the
Tunnel Settings
tab.
Device GUI Path: Network > GlobalProtect > Gateways > [Gateway Name] > Agent > Tunnel Settings - Enable Tunnel Mode: Ensure tunnel mode is enabled.
- Tunnel Interface: Select or create the tunnel interface that will terminate the IPSec connections from Satellites. This tunnel interface must be in a Security Zone and have an IP address.
- IPSec Crypto Profile: Assign an IPSec Crypto profile defining encryption and authentication algorithms for the data plane.
- IKE Gateway: Reference an IKE Gateway configuration (see below).
- Enable LSVPN: Ensure this is implicitly handled by the IKE Gateway configuration being part of the LSVPN setup.
-
Go to the
Tunnel Settings
tab.
-
Network Configuration (IKE Gateway & IPSec Tunnel):
-
IKE Gateway (Network > Network Profiles > IKE Gateways):
- Version: IKEv2 preferred or IKEv2 only.
- Authentication: Certificate. Reference the Gateway's device certificate and a Certificate Profile for validating Satellite certificates.
- Local and Peer Identification: Use appropriate types (e.g., FQDN, DN).
- IKE Crypto Profile: Define IKE Phase 1 parameters.
-
IPSec Tunnel (Network > IPSec Tunnels):
- Associate with the IKE Gateway created above.
- Assign the IPSec Crypto Profile.
- The actual IPSec tunnels for LSVPN are dynamically created based on Satellite connections, but the Gateway needs the profiles and IKE Gateway settings to handle these. The "Tunnel Monitor" feature is generally not used for LSVPN satellite connections as the Portal manages availability.
-
IKE Gateway (Network > Network Profiles > IKE Gateways):
-
Virtual Router Configuration:
- Add the Gateway's tunnel interface to a Virtual Router.
- Configure static routes or dynamic routing (e.g., BGP) to route traffic from the tunnel interface to internal hub networks.
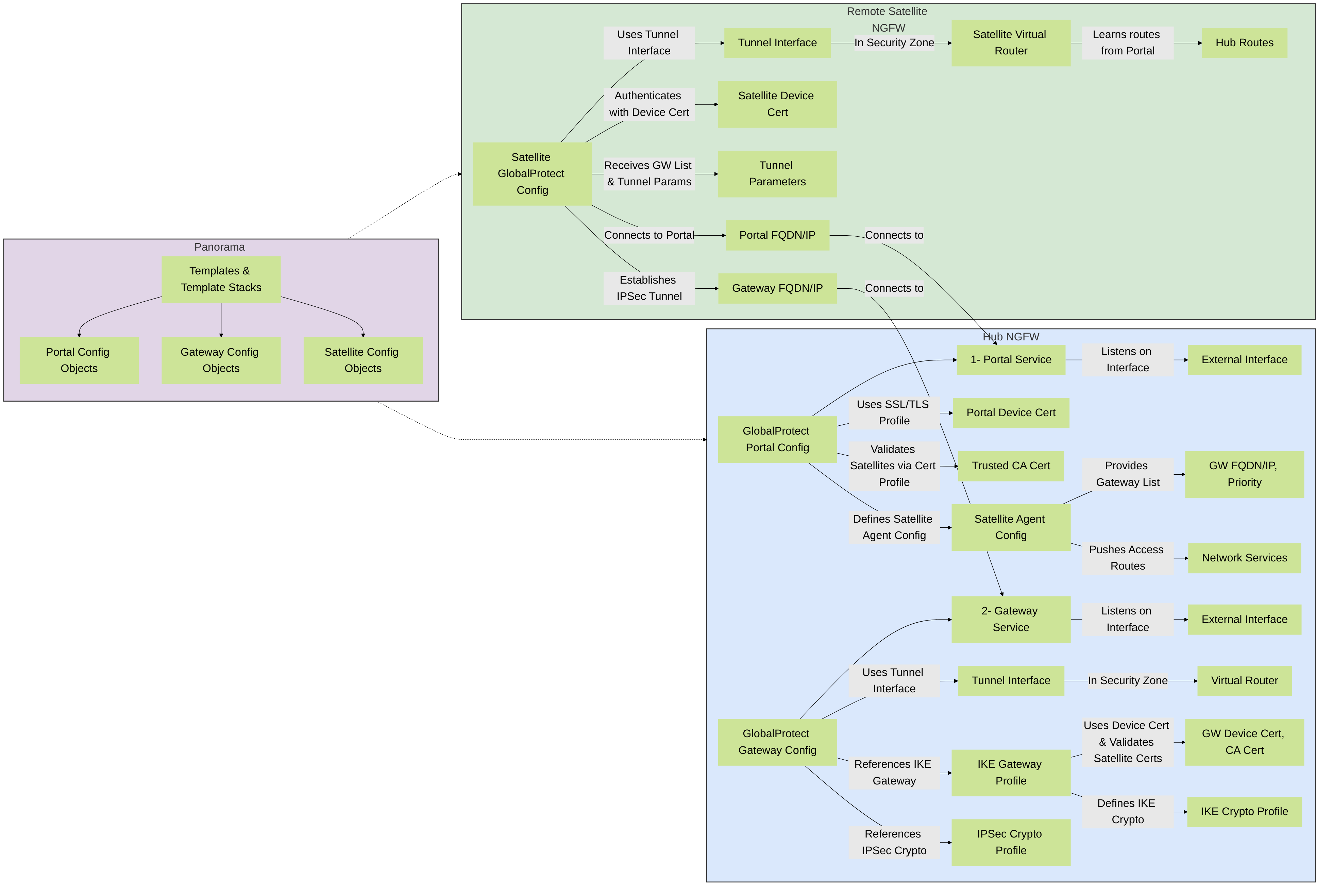
Figure 4: Palo Alto Networks LSVPN Configuration Workflow highlighting key elements on Portal, Gateway, and Satellite, and the role of Panorama.
4.4 LSVPN Satellite Configuration (Remote NGFW)
Navigate to Network > GlobalProtect > Satellites > [Add/Edit Satellite Configuration] (or configure via Portal push if using older PAN-OS method where satellite config is minimal and most is pushed):
The primary configuration on the Satellite itself is to point it to the GlobalProtect Portal. Most of the detailed VPN configuration is then dynamically pushed from the Portal.
-
General Tab:
- Portal Address: Enter the FQDN or IP address of the GlobalProtect Portal.
- Client Certificate: Select the Satellite's device certificate used to authenticate to the Portal.
- Tunnel Interface: Select or create a tunnel interface on the Satellite. This interface will be used for the IPSec tunnel to the Gateway. Ensure it's in a Security Zone and Virtual Router.
-
Enable the GlobalProtect Satellite service:
Device GUI Path: Device > Setup > Management > GlobalProtect Satellite Enable GlobalProtect Satellite: Checked
-
Virtual Router Configuration:
- Add the Satellite's tunnel interface to a Virtual Router.
- Routes to hub networks are typically learned dynamically from the Portal (as part of "Network Services" or via BGP if configured).
- Configure static routes for local networks to be advertised or ensure they are part of a dynamic routing protocol.
4.5 Security Policies and NAT
- Security Policies: On both Hub (Gateway) and Satellite firewalls, create Security Policies to permit (or deny) traffic between the respective Security Zones (e.g., zone for local LAN and zone for the tunnel interface). Apply appropriate Security Profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, File Blocking, WildFire) for full threat prevention.
- NAT Policies: If NAT is required for traffic traversing the LSVPN (e.g., Satellites using overlapping IP spaces, or specific source NAT requirements), configure NAT policies accordingly. Typically, for corporate VPNs, you want to avoid NAT to maintain end-to-end IP visibility, unless necessary.
4.6 Dynamic Routing with BGP (Optional but Recommended for Scale)
For larger LSVPN deployments, using BGP is highly recommended for dynamic route exchange between the hub and satellites over the LSVPN tunnels.
-
Hub (Gateway):
- Configure BGP on the Virtual Router containing the tunnel interfaces.
- Establish BGP peerings with Satellites over their tunnel IP addresses (often assigned from an IP pool configured on the Portal/Gateway).
- Redistribute routes from internal networks into BGP to advertise to Satellites.
-
Satellite:
- Configure BGP on the Virtual Router containing its tunnel interface.
- Establish BGP peering with the Hub Gateway(s).
- Advertise local Satellite networks into BGP.
BGP simplifies route management, especially when dealing with many Satellites or complex network topologies, and provides faster convergence than relying solely on Portal-pushed static routes for changes.
4.7 Verification CLI Commands (PAN-OS)
On the Portal :
> show global-protect-portal lsvpn-satellite detail all > show global-protect-portal lsvpn-gateway detail all > show log global-protect
On the Gateway :
> show vpn ike-sa detail yes gateway <IKE-gateway-name> > show vpn ipsec-sa tunnel <tunnel-interface-name> > show vpn flow > show log vpn > show routing route
On the Satellite :
> show global-protect-satellite status > show global-protect-satellite gateway > show global-protect-satellite lsvpn-config > show vpn ike-sa > show vpn ipsec-sa > show log global-protect > show log vpn > show routing route
5. Advanced Considerations and Palo Alto Networks Best Practices
-
PAN-OS Version Compatibility:
- Ensure all Palo Alto Networks firewalls (Portal, Gateways, Satellites) are running compatible PAN-OS versions. Refer to the Palo Alto Networks compatibility matrix for specific version interoperability. Mismatched versions can lead to unexpected behavior or connection failures.
-
Certificate Management:
- Use a dedicated, secure internal CA or a trusted third-party CA for issuing device certificates.
- Implement certificate revocation checking (CRL or OCSP) to ensure compromised certificates cannot be used. This is configured in the Certificate Profile.
- Monitor certificate expiry dates and have a renewal plan in place. Panorama can help with certificate management.
-
Redundancy and Failover:
- For one-to-many Satellite deployments, carefully plan Gateway priorities and preemption settings to achieve desired failover behavior.
- Consider HA (Active/Passive or Active/Active) for Portal and Gateway NGFWs at the hub for maximum uptime.
-
Monitoring, Logging, and Alerting:
- Regularly monitor tunnel statuses using Panorama, the PAN-OS GUI, or CLI commands.
- Forward logs (System, GlobalProtect, VPN, Traffic, Threat) to a SIEM or Panorama for centralized analysis and alerting on critical events like tunnel down, authentication failures, or detected threats.
- Utilize ACC (Application Command Center) on Panorama or the NGFW to gain visibility into traffic patterns across LSVPN.
-
Satellite Authentication (PAN-OS 10.1 and Later):
- In PAN-OS 10.1 and later, for enhanced security, Satellites using certificate authentication might require periodic re-authentication with the Portal (e.g., every 180 days by default for some configurations). This may involve manual intervention if not automated or if the Satellite's initial bootstrap authentication token expires.
- Understand the "authenticate-override" settings on the Portal and how they impact long-term Satellite connectivity without manual re-authentication. Using a unique device certificate per satellite is a best practice.
Gotcha! (Palo Alto Networks): The 180-day re-authentication behavior for LSVPN Satellites introduced in PAN-OS 10.1+ can catch administrators off-guard if not planned for. Ensure your operational procedures account for this, or investigate configuration options to extend or manage this behavior, such as ensuring each Satellite has a unique certificate and is registered in the Portal. -
Scalability and Performance:
- Choose appropriate Palo Alto Networks hardware models for Portal, Gateway, and Satellite roles based on the number of tunnels, throughput requirements, and concurrent sessions.
- Optimize IPSec and IKE crypto profiles. While stronger encryption is better, it also consumes more CPU. Balance security requirements with performance capabilities of the devices. AES-GCM modes often provide good performance.
-
Traffic Segmentation with Zones and VRFs:
- Place tunnel interfaces in dedicated Security Zones to apply granular security policies.
- In complex scenarios, Virtual Routers (VRFs) can be used to segment routing domains over LSVPN. For example, guest traffic from remote sites could be routed differently than corporate traffic.
-
Quality of Service (QoS):
- Implement QoS policies on the Gateway and Satellite firewalls to prioritize critical applications (e.g., VoIP, video conferencing) over the LSVPN tunnels. QoS is applied before traffic enters the tunnel on the way out and after it exits on the way in.
-
LSVPN with Palo Alto Networks SD-WAN:
- Palo Alto Networks SD-WAN can leverage LSVPN for secure underlay connectivity. SD-WAN adds an overlay of intelligent path selection, application-aware routing, and simplified branch orchestration, often using LSVPN tunnels as one of the available paths.
- While LSVPN provides the secure tunnels, SD-WAN provides the intelligence for how to use them along with other WAN links.
6. LSVPN Packet Flow Overview
Understanding the packet flow helps in troubleshooting and conceptualizing LSVPN operations.
6.1 Control Plane (Tunnel Establishment & Management)
-
Satellite to Portal:
- The LSVPN Satellite initiates an HTTPS connection to the configured GlobalProtect Portal address.
- Mutual authentication occurs, typically using device certificates. The Portal validates the Satellite's certificate, and the Satellite validates the Portal's certificate.
- If authentication is successful, the Portal sends the LSVPN configuration to the Satellite. This includes the list of available Gateways, their priorities, IPSec parameters (IKE and IPSec crypto profiles, Perfect Forward Secrecy settings), and access routes (networks reachable via the VPN).
-
Satellite to Gateway (IKE/IPSec Negotiation):
- Based on the received configuration (and Gateway priority), the Satellite initiates IKE (Internet Key Exchange) Phase 1 negotiation with the chosen GlobalProtect Gateway. This involves authentication (again, typically certificate-based) and establishing a secure channel for IKE Phase 2.
- IKE Phase 2 negotiation occurs, establishing the IPSec Security Associations (SAs) that will protect the data traffic. This includes agreeing on encryption and integrity algorithms for the data plane.
- Once IPSec SAs are established, the tunnel is up and ready to pass data.
6.2 Data Plane (Traffic Flow through Tunnel)
- A user/device at the remote site sends traffic destined for a hub network (or another network reachable via the LSVPN).
- The LSVPN Satellite firewall's routing table directs this traffic towards its tunnel interface associated with the LSVPN.
- Before entering the tunnel, the traffic is processed by the Satellite's Security Policies (App-ID, User-ID, Content-ID, threat prevention).
- If permitted, the traffic is encrypted and encapsulated according to the negotiated IPSec SA and sent to the GlobalProtect Gateway.
- The GlobalProtect Gateway receives the encrypted packet, decrypts it, and de-encapsulates it.
- The decrypted traffic is then processed by the Gateway's Security Policies.
- If permitted, the Gateway's routing table forwards the packet to the destination resource in the hub network.
- Return traffic follows the reverse path.
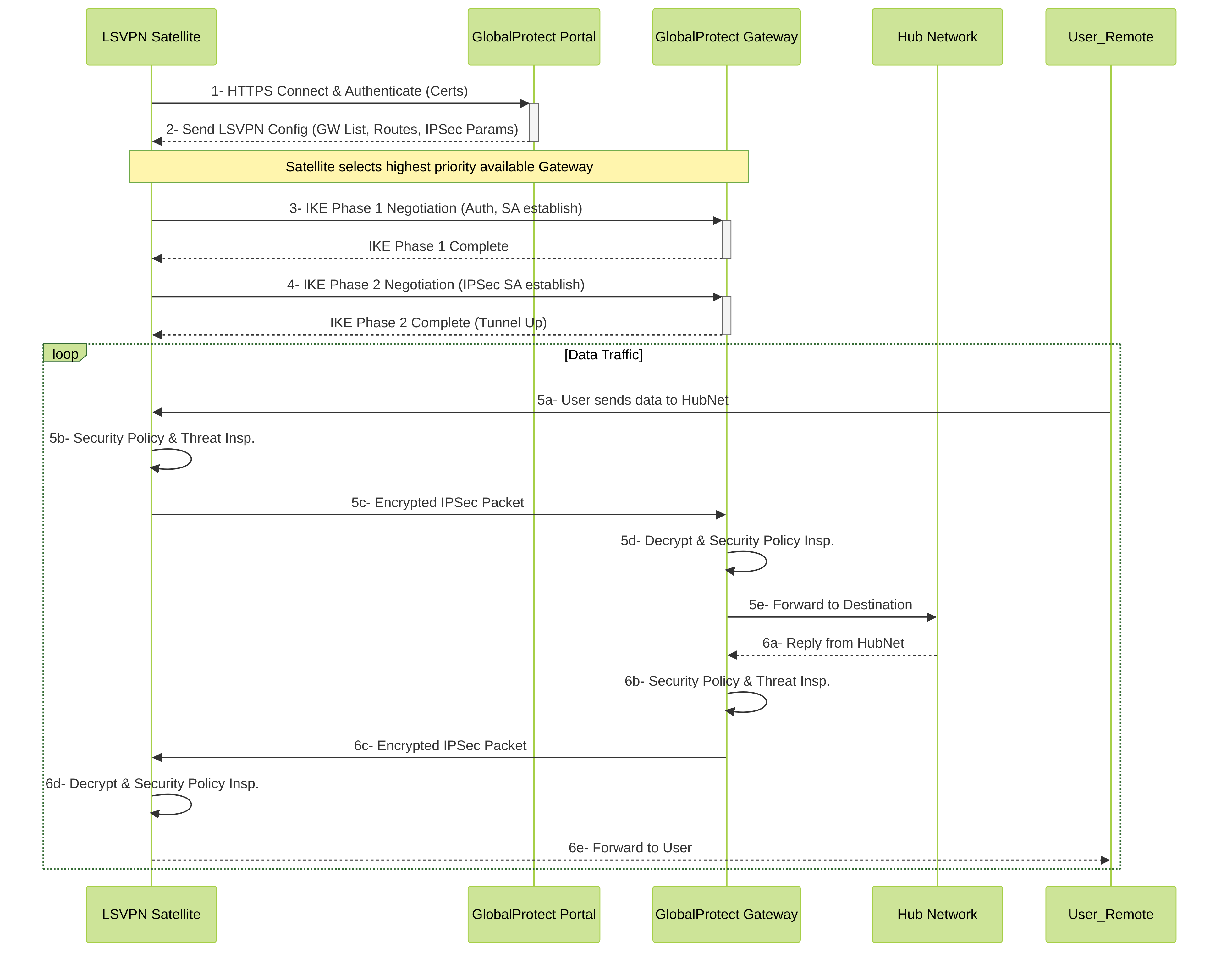
Figure 5: Simplified Palo Alto Networks LSVPN Control Plane and Data Plane sequence, showing Portal interaction, tunnel establishment with Gateway, and data flow.
7. LSVPN vs. Traditional Site-to-Site IPSec VPNs (Palo Alto Networks Context)
While both LSVPN and traditional (manual) site-to-site IPSec VPNs on Palo Alto Networks NGFWs use IPSec to secure data, LSVPN offers distinct advantages, particularly for larger or more dynamic environments:
| Feature | Palo Alto Networks LSVPN | Traditional Palo Alto Networks Site-to-Site IPSec VPN |
|---|---|---|
| Configuration Scalability | Excellent. Hub (Portal/Gateway) configuration is minimal per Satellite. Satellites auto-configure. | Moderate. Each tunnel typically requires manual configuration on both ends. Can become complex with many sites. |
| Management Overhead | Lower. Centralized configuration distribution via Portal. Panorama further simplifies. | Higher. Decentralized configuration. Changes require updates on multiple devices. |
| New Site Deployment | Simplified. Configure Satellite to point to Portal; it pulls down its full VPN config. | Manual. Configure IPSec and IKE settings, tunnel interfaces, routes on both hub and remote firewall. |
| Hub Redundancy | Built-in. Satellites can connect to multiple Gateways with priority. | Possible, but often requires more complex routing, multiple tunnel configurations, or scripting. Tunnel monitoring helps. |
| Dynamic Parameter Updates | Yes. Changes to crypto profiles, routes, etc., on the Portal can be pushed to Satellites. | No. Manual updates required on each firewall. |
| Use Case Focus | Hub-and-spoke topologies, large number of remote sites, dynamic environments. | Any site-to-site connection, including full mesh (if configured individually), simpler point-to-point links. |
| Underlying Technology | IPSec, IKEv1/IKEv2, leveraging GlobalProtect Portal/Gateway framework for orchestration. | IPSec, IKEv1/IKEv2. |
LSVPN is Palo Alto Networks' preferred solution for scalable hub-and-spoke VPN deployments, offering operational efficiencies not easily achievable with traditional manual IPSec configurations when managing many sites.