URL Filtering and Credential Theft Prevention: A Palo Alto Networks Deep Dive
Credential theft, often facilitated by phishing attacks, remains a primary vector for cyber breaches, granting attackers unauthorized access to sensitive corporate resources. Palo Alto Networks Next-Generation Firewalls (NGFWs) offer a robust, layered defense strategy employing several integrated features. Two cornerstones of this strategy are URL Filtering and Credential Phishing Prevention (CPP) , also known as User Credential Submission detection.
Understanding how these two capabilities function independently and, more importantly, how they synergize is crucial for effective security policy implementation. This article provides an in-depth look at Palo Alto Networks' URL Filtering and Credential Phishing Prevention, leveraging current information to explain their mechanisms, dependencies, configuration context, and their combined role in protecting your organization from credential compromise.
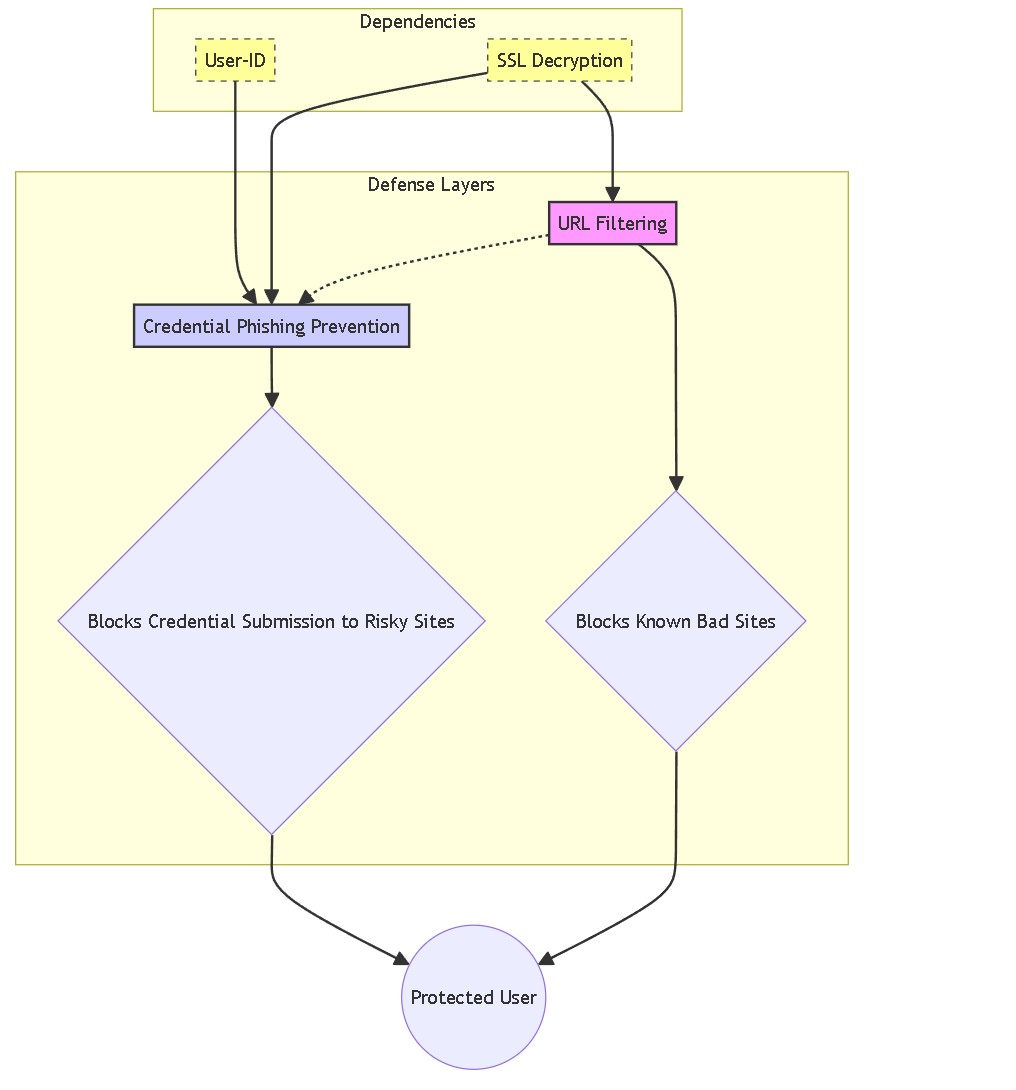
High-level relationship between URL Filtering, CPP, and key dependencies.
Understanding Threats: What is Credential Theft?
Credential theft is the unauthorized acquisition of user login information (usernames, passwords, access tokens). Attackers seek these credentials to impersonate legitimate users, bypass security measures, and gain illicit access to networks, applications, and sensitive data.
Successful credential theft can lead to severe consequences:
- Unauthorized access to sensitive corporate or customer data.
- Financial losses via fraudulent activities or ransomware deployment.
- Lateral movement within the network, escalating the breach impact.
- Reputational damage and loss of customer trust.
- Disruption of essential business operations.
Understanding Threats: Common Methods: Phishing Focus
While various methods exist (malware, brute force, etc.), **phishing** remains a highly prevalent and effective technique targeted by Palo Alto Networks' URL Filtering and Credential Phishing Prevention features.
Phishing Attacks:
- Attackers create deceptive emails, messages, or websites that mimic legitimate services (e.g., corporate login portals, popular SaaS applications, financial institutions).
- These lures trick users into clicking malicious links or opening attachments.
- Users are often directed to fake login pages where they unwittingly enter their corporate usernames and passwords.
- Even a single successful attempt can compromise network security.
- Attackers constantly create new phishing domains and use evasive techniques to bypass traditional database lookups.
Palo Alto Networks' defenses aim to both block access to known phishing sites and prevent the *act* of submitting credentials to suspicious or untrusted sites, directly combating this threat.
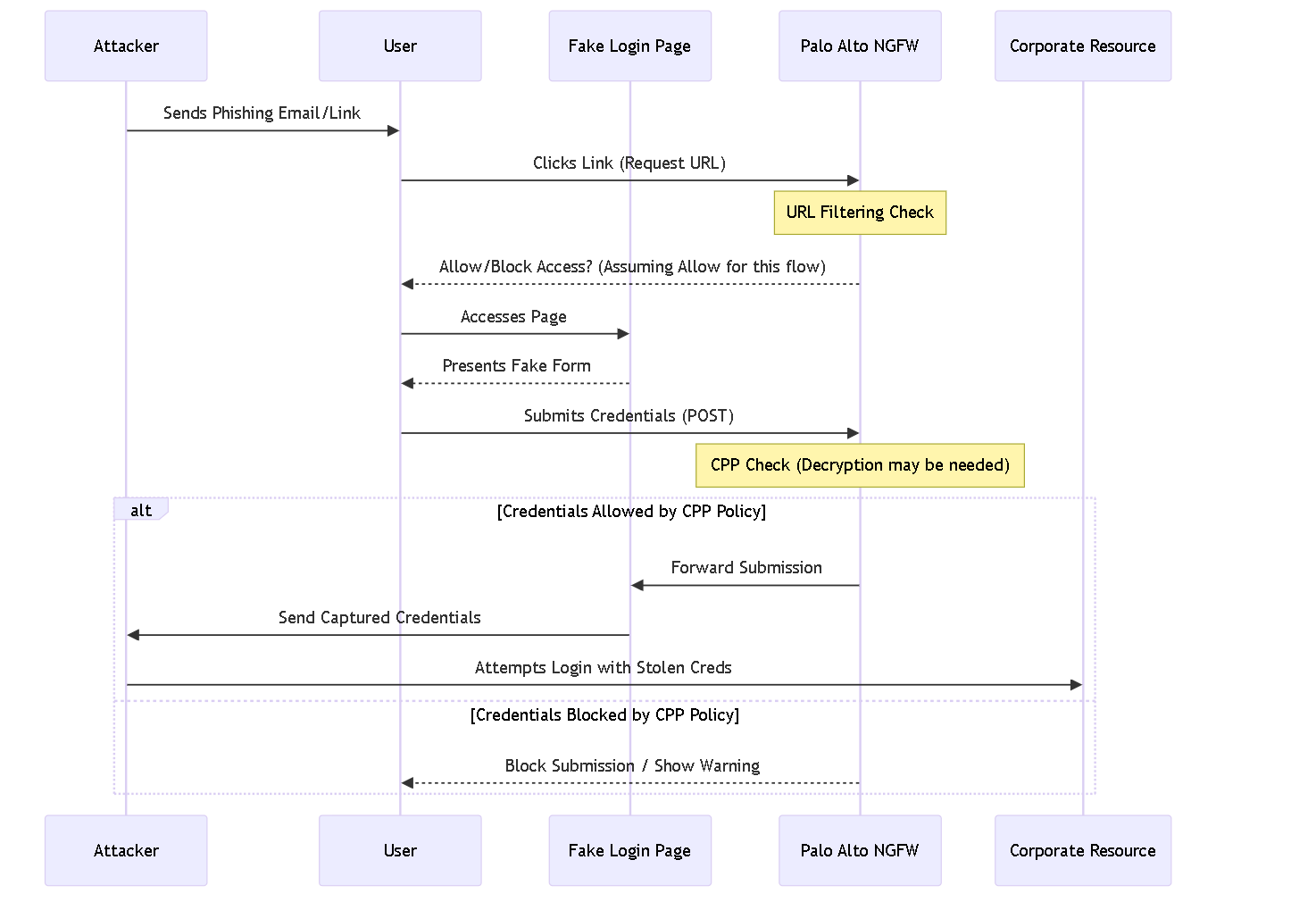
Sequence diagram illustrating a phishing attack and potential NGFW intervention points (URL Filtering access check & CPP submission check).
URL Filtering: Core Concepts
URL Filtering on Palo Alto Networks NGFWs controls web access based on website categorization, serving as a foundational layer of web security. It compares web requests against a comprehensive database to determine the nature and risk associated with the destination site.
Key Components and Mechanisms:
- PAN-DB: A cloud-based database containing millions of URLs categorized based on content, function, and risk (e.g., 'phishing', 'malware', 'social-networking', 'high-risk'). PAN-DB is continuously updated.
- URL Categories: Websites are grouped into numerous categories. These categories form the basis for policy decisions.
- Database Lookups: The firewall utilizes local caches for frequently accessed URLs to minimize latency and queries the PAN-DB cloud service for unknown or less common URLs.
- Security Policy Integration: URL Filtering profiles, which define actions per category, are attached to Security policy rules to enforce web access controls.
- Content Updates: Regular updates (Applications and Threats content updates) deliver the latest URL categorizations and threat intelligence to the firewall, ensuring the PAN-DB information is current.
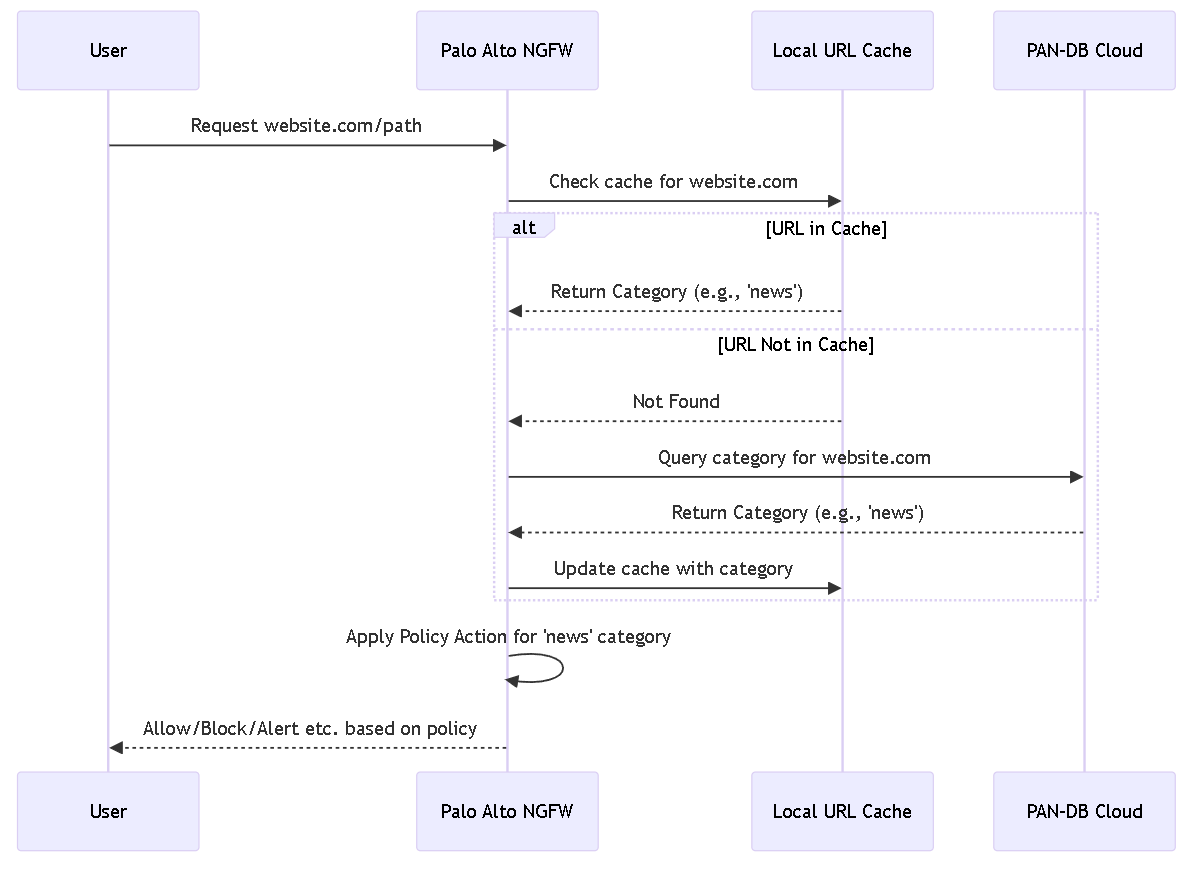
Sequence diagram showing the standard URL lookup process involving local cache and PAN-DB.
URL Filtering: Policy Actions & States
Within a URL Filtering profile, administrators define specific actions to be taken when a user attempts to access a site belonging to a particular URL category. These actions provide granular control over web access:
-
allow: Permits access to the website. This is the default action for many categories. -
alert: Permits access but generates a log entry in the URL Filtering logs each time a site in this category is accessed. Useful for monitoring potentially risky categories without outright blocking. -
block: Denies access to the website and typically presents a block page to the user. This is recommended for high-risk categories like 'phishing', 'malware', 'command-and-control'. -
continue: Presents a response page warning the user about the site category but allows them to click 'Continue' to proceed. This can serve as user education but carries risk. -
override: Blocks access initially but presents a response page where a user with the correct password (configured by the administrator) can override the block and proceed.
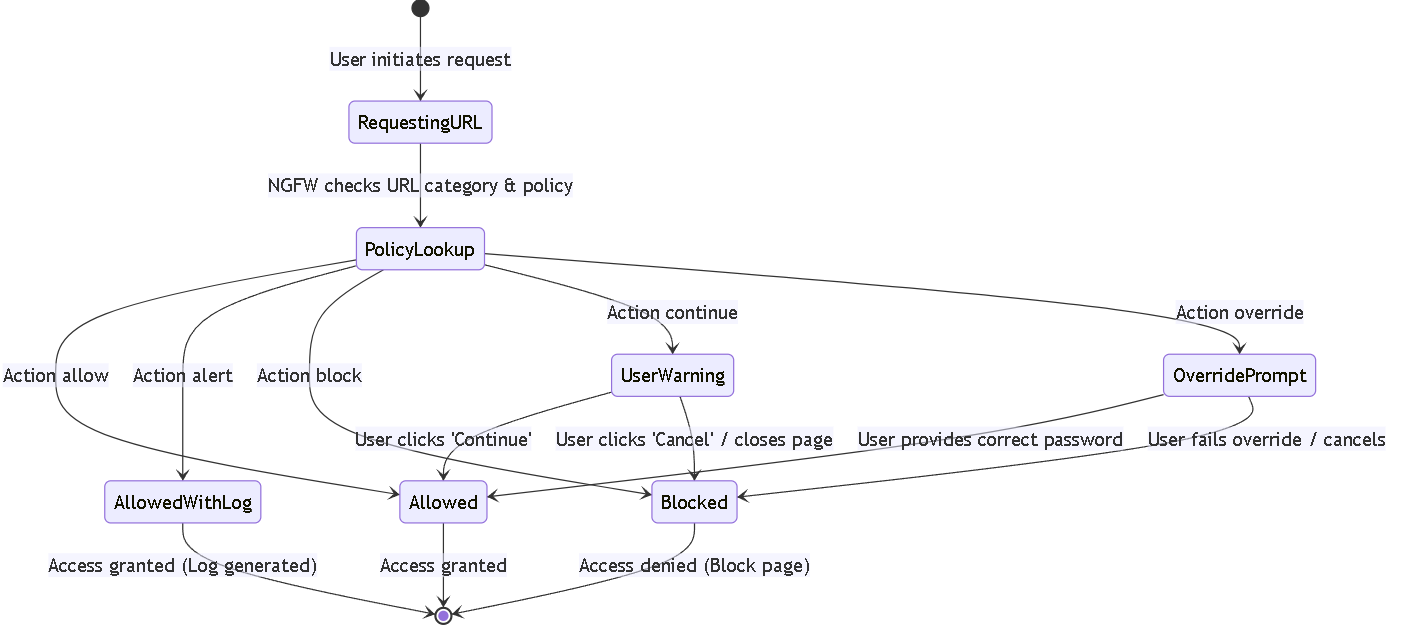
State diagram illustrating potential outcomes based on URL Filtering site access actions.
These actions are configured per URL category within the URL Filtering profile applied to a Security Policy rule.
URL Filtering: Advanced URL Filtering (AURLF)
Advanced URL Filtering is a licensed subscription service that significantly enhances the standard URL Filtering capabilities, particularly against modern, evasive threats.
Key Enhancements:
- Real-time Inline Analysis: Utilizes cloud-based machine learning (ML) and AI (Precision AI™) to analyze unknown or uncategorized URLs and web content *in real time* as the user accesses them, rather than relying solely on pre-existing database entries.
- Improved Phishing Detection: Employs ML models and techniques like phishing image detection to identify and block new and zero-day phishing sites much faster than traditional databases, reportedly preventing significantly more threats.
- Enhanced Credential Theft Prevention: Directly contributes to preventing credential theft by blocking malicious sites in real-time, even before they are widely known or categorized in PAN-DB.
- Evasion Prevention: Better equipped to detect threats hidden using techniques like cloaking or CAPTCHAs designed to fool offline scanners.
- Integration: Works natively with the NGFW platform and leverages threat intelligence from other services like WildFire.
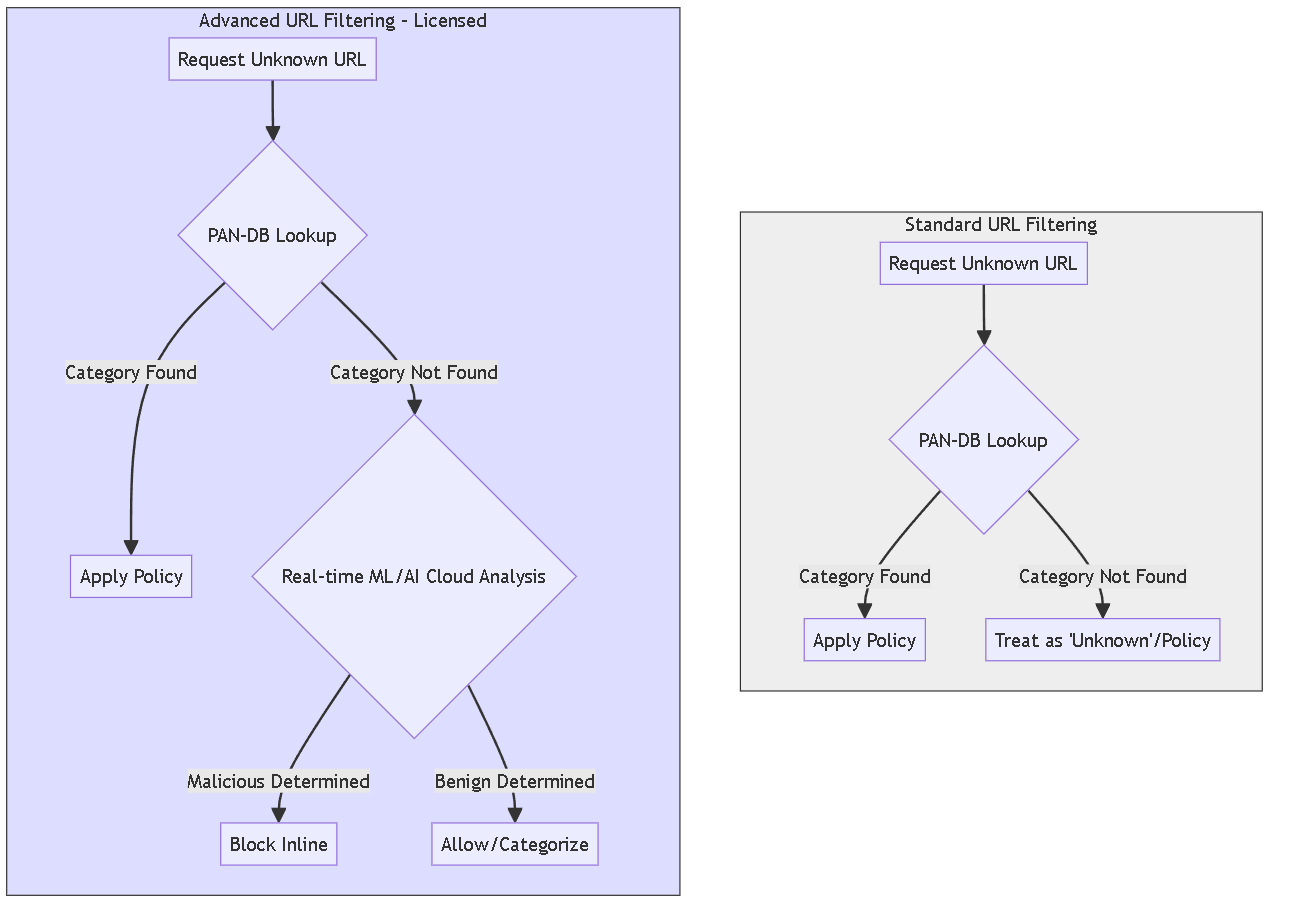
Flowchart comparing Standard URL Filtering's handling of unknown URLs vs. Advanced URL Filtering's real-time inline analysis.
While standard URL Filtering blocks known threats, AURLF proactively identifies and blocks *unknown* web-based threats inline.
Credential Prevention: Core Concepts (CPP)
Credential Phishing Prevention (CPP), also referred to as User Credential Submission detection, is a specialized feature designed to prevent users from submitting valid corporate credentials to websites based on the site's URL category.
How it Works:
- Submission Scanning: The firewall inspects outbound web traffic (typically HTTP POST requests used in login forms) for patterns resembling username and password submissions.
- Credential Comparison: It compares the submitted data against known corporate credential information (methods vary, see next section).
- URL Category Context: The firewall checks the PAN-DB URL category of the website where the submission is occurring.
- Policy Enforcement: Based on the credential match and the destination URL category, a configured action (`allow`, `alert`, `block`, `continue`) is enforced.
This allows administrators to permit credential submissions to sanctioned corporate sites while blocking or warning against submissions to untrusted, risky, or explicitly disallowed categories like 'phishing', 'social-networking', or even 'unknown'.
Configuration for CPP is done within the URL Filtering profile applied to Security policy rules.
Credential Prevention: Detection Methods & User-ID Dependency
Credential Phishing Prevention relies on User-ID integration to accurately identify corporate credential submissions. There are three primary methods for detecting these submissions, each with specific User-ID configuration requirements:
- Group Mapping: Checks if submitted username belongs to specific configured groups. Requires User-ID Group Mapping (LDAP).
- IP User Mapping: Checks if submitted username matches the user currently mapped to the source IP. Requires User-ID IP-to-User Mapping.
- Domain Credential Filter: Checks username and password hash against secure representation (bloom filter) from RODC. Requires User-ID Agent on RODC + Credential Service Add-on + IP-to-User Mapping.
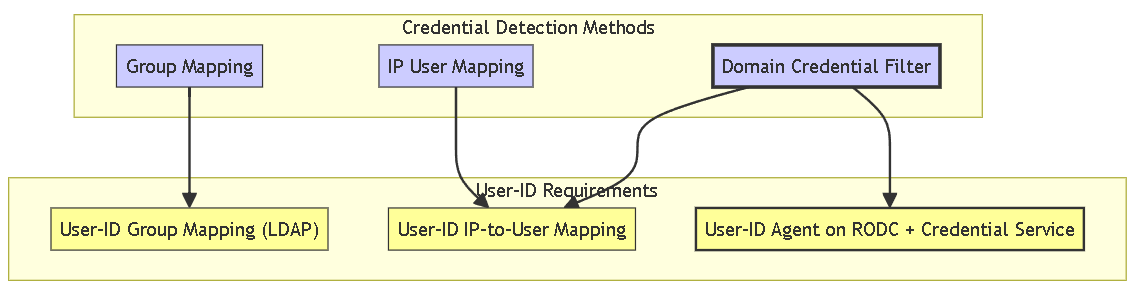
Graph showing the dependency of each Credential Phishing Prevention detection method on specific User-ID capabilities. Note Domain Credential Filter's dual dependency.
Credential Prevention: Policy Actions
Within the URL Filtering profile, under the "User Credential Submission" settings for each URL category, administrators specify the action to take when a corporate credential submission is detected targeting a site in that category:
-
allow: (Default) Permits the credential submission without logging or warning. Use this for sanctioned corporate applications or known legitimate login pages (often managed via custom URL categories). -
alert: Permits the submission but generates a URL Filtering log (or Data Filtering log depending on version/context) indicating a corporate credential was submitted to this category. Useful for monitoring submissions to potentially sensitive or less-trusted categories. -
block: Prevents the user from submitting the credentials and displays a customizable block response page. This is the most secure action and recommended for high-risk categories like 'phishing', 'malware', 'unknown', and potentially others like 'social-networking' or 'web-based-email' depending on policy. -
continue: Presents a customizable warning page to the user, informing them about the risk of submitting credentials to this type of site. The user must click 'Continue' to proceed with the submission. This acts as a deterrent and educational tool but doesn't strictly prevent submission.
The choice of action per category allows organizations to tailor credential protection based on the perceived risk of the destination site type.
Credential Prevention: Trusted Site Exemption
An important nuance in Credential Phishing Prevention is the concept of "trusted sites." Palo Alto Networks maintains an internal list of domains considered highly trustworthy, where malicious activity or phishing is generally not observed.
- Performance Optimization: To optimize performance, the firewall typically *does not* perform credential submission checks on sites categorized as trusted, even if the URL category they belong to is configured for blocking or alerting credential submissions in the URL Filtering profile.
- Dynamic Updates: This list of trusted sites (often related to specific App-IDs) is updated via Application and Threat content updates.
- Potential Configuration Challenge: This exemption means that simply setting a 'block' action for credential submissions on a broad category (like 'business-and-economy') might not prevent submissions to a specific, highly trusted site within that category (e.g., a major SaaS provider). This behavior has sometimes caused confusion during testing or implementation.
Synergy: How They Work Together
URL Filtering and Credential Phishing Prevention (CPP) are designed to function as a layered defense:
- URL Filtering (First Line): Checks site category, applies site access action (Block/Allow/Warn).
- Credential Phishing Prevention (Second Line - if access allowed): Inspects submission, checks against User-ID data, checks URL category again against *submission* policy, applies submission action (Block/Allow/Warn).
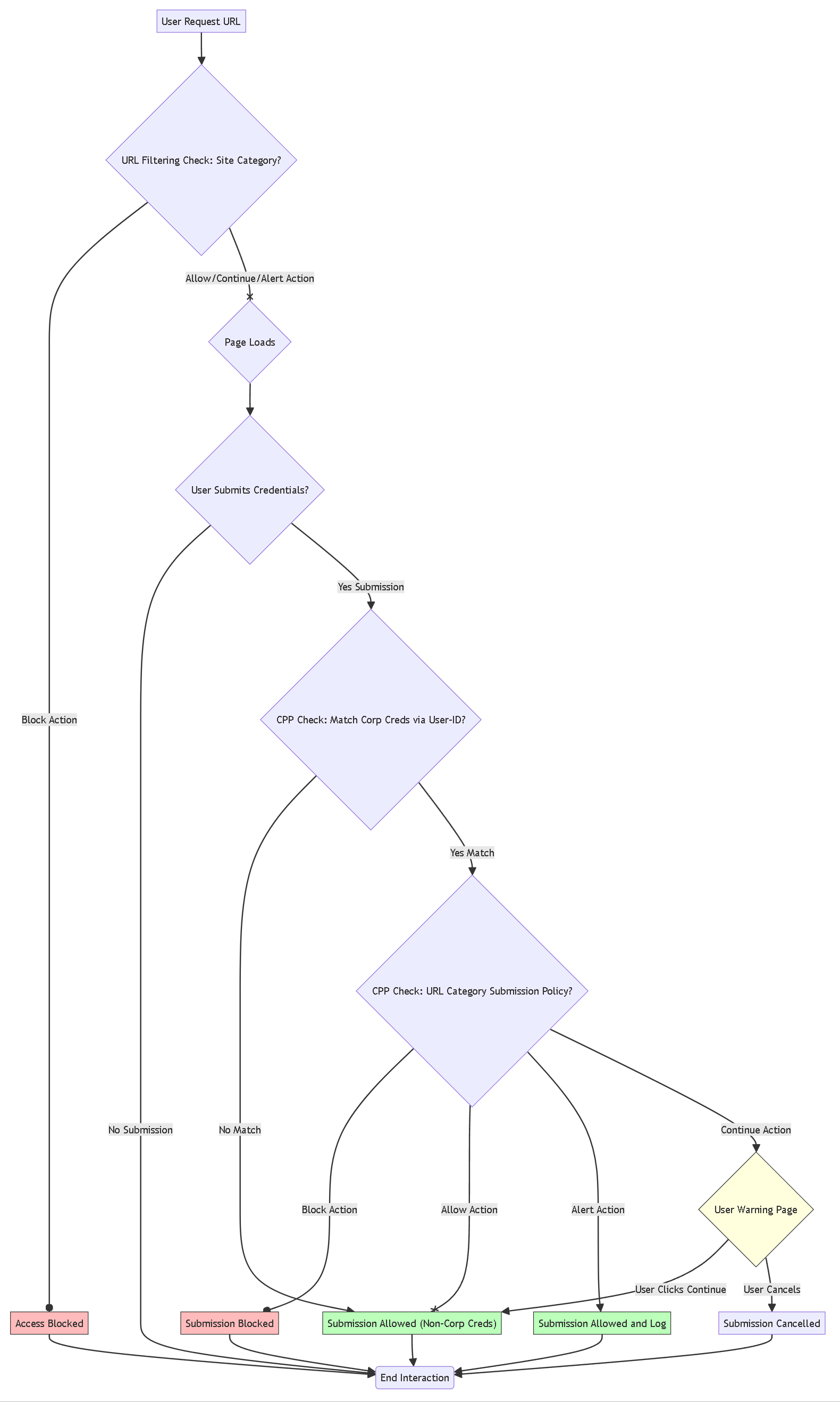
Detailed flowchart showing the combined logic of URL Filtering (site access) and Credential Phishing Prevention (submission control).
Synergy: Role of SSL Decryption
A critical enabler for both effective URL Filtering (beyond just domain name) and especially Credential Phishing Prevention is SSL/TLS Decryption .
- Visibility Limitation: Most web traffic, including phishing sites, uses HTTPS. Without decryption, the firewall lacks visibility into the encrypted payload.
- URL Filtering Impact: Reduced effectiveness for full path/content analysis.
- Credential Prevention Impact: CPP *cannot* inspect usernames/passwords inside encrypted HTTPS POST requests without decryption.
- Configuration: Requires Decryption policies, profiles, and certificate management.
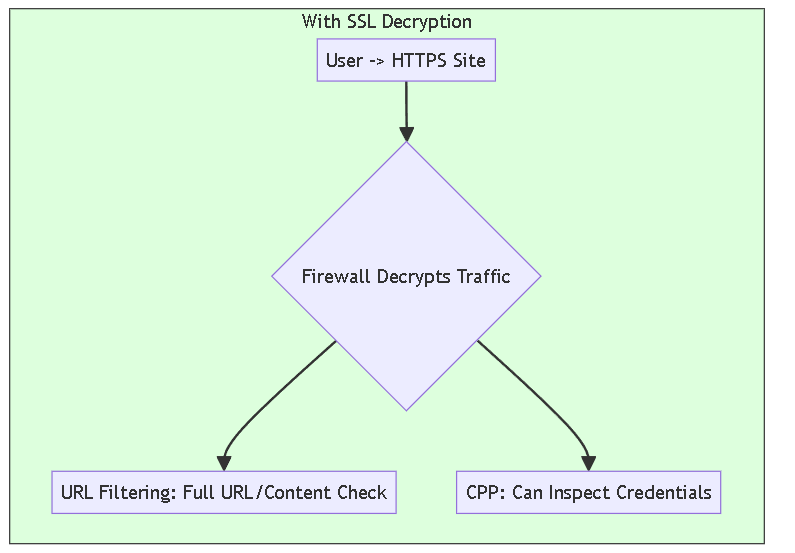
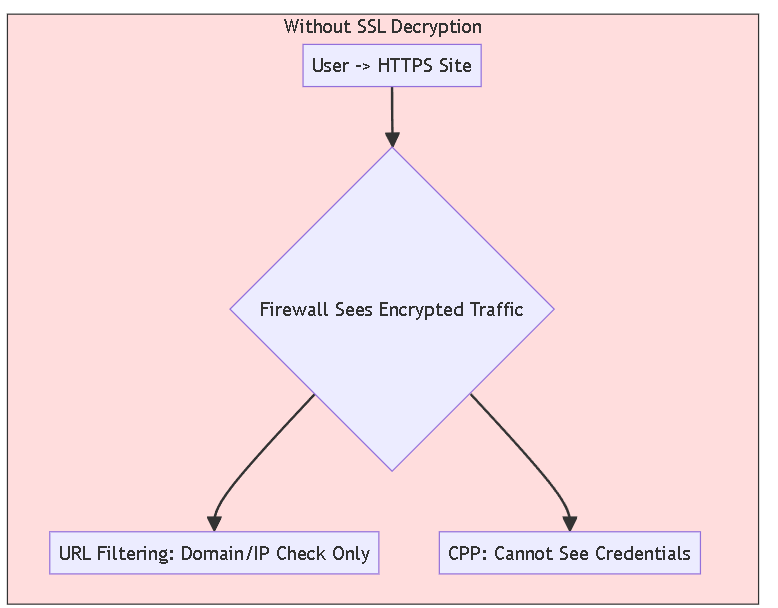
Flowchart comparing visibility and feature effectiveness with and without SSL Decryption for HTTPS traffic.
Targeted decryption policies can be created, for example, decrypting traffic destined for 'high-risk' or 'unknown' URL categories while potentially excluding sensitive categories like 'financial-services' or 'health-and-medicine'.
Synergy: Configuration Summary
Configuring URL Filtering and Credential Phishing Prevention involves several interconnected steps within the PAN-OS interface (or Panorama):
- User-ID Configuration: Map IPs/Users/Groups. For Domain Credential Filter: RODC + Agent + Service.
- SSL Decryption Policy: Decrypt relevant traffic categories.
- URL Filtering Profile: Configure Site Access actions AND User Credential Submission actions per category. Select CPP Detection Method.
- Security Policy Rule: Apply URL Filtering Profile and relevant Decryption Policy.
- Commit Changes.
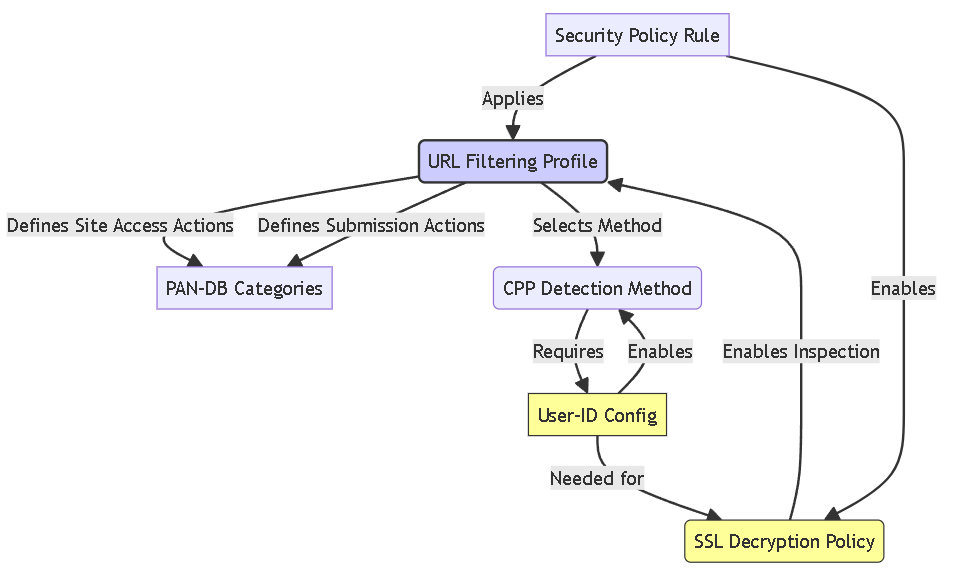
Graph illustrating the relationship between key configuration objects for URL Filtering and CPP.
Best Practices
To maximize the effectiveness of URL Filtering and Credential Phishing Prevention:
- Maintain Content Updates: Ensure the firewall regularly downloads the latest Content-ID (Applications and Threats) updates.
- Implement SSL Decryption: Deploy SSL/TLS Decryption targeting relevant traffic.
- Block High-Risk Categories: Block access to 'phishing', 'malware', 'C2', 'hacking', 'questionable'. Consider blocking/alerting 'unknown', 'newly-registered-domain'.
- Enforce Strict Credential Submission Policy: Use `block` for submissions to untrusted categories. Use `alert`/`allow` sparingly and specifically.
- Leverage User-ID Fully: Implement accurately. Use Domain Credential Filter for password checking.
- Customize Response Pages: Provide clear warnings and education.
- Monitor Logs: Review URL Filtering and Data Filtering logs.
- Use Advanced URL Filtering: Leverage AURLF if licensed.
- User Education: Train users on phishing and password hygiene.
- Test Thoroughly: Validate configuration changes.
Exam Focus: Key Concepts and Sample Questions
Based on the research, here are key areas related to URL Filtering and Credential Phishing Prevention likely to appear on Palo Alto Networks certification exams (like PCNSA/PCNSE), along with sample questions:
Key Concepts for Exams:
- Distinction: URL Filtering (Site Access) vs. CPP (Credential Submission).
- Configuration Location: Both configured in the URL Filtering Profile.
- Dependencies: CPP needs User-ID; HTTPS inspection needs SSL Decryption.
- CPP Detection Methods: Group Mapping (Groups), IP User Mapping (IP->User), Domain Credential Filter (RODC Agent + IP->User, checks passwords).
- Actions: Site access (allow/alert/block/continue/override) vs. Submission (allow/alert/block/continue).
- Advanced URL Filtering: Real-time, ML/AI, unknown threats, licensed.
- Order of Operations: URLF check first, then CPP check on allowed traffic.
Sample Exam-Style Questions (Deduced):
1. An administrator wants to prevent users from submitting their corporate usernames and passwords to websites categorized as 'social-networking', even though site access to this category is allowed. Which feature and configuration step are required?
2. To enable the 'Domain Credential Filter' method for Credential Phishing Prevention, which User-ID component is specifically required?
3. A user attempts to access `https://malicious-phishing.com`. The site is categorized as 'phishing' in PAN-DB, and the URL Filtering profile applied has the 'phishing' category action set to 'block'. SSL Decryption is NOT enabled for this traffic. What is the expected outcome?
4. What is a primary benefit of the Advanced URL Filtering subscription compared to standard URL Filtering?
Conclusion
Palo Alto Networks provides a powerful, integrated defense against credential theft through the synergistic operation of URL Filtering and Credential Phishing Prevention. URL Filtering serves as the essential first line, leveraging PAN-DB and potentially Advanced URL Filtering's real-time analysis to block access to known and emerging malicious websites.
Credential Phishing Prevention acts as a critical second line, scrutinizing credential submissions on allowed websites by leveraging User-ID and targeted policies. It effectively prevents users from handing over corporate credentials to phishing sites, compromised legitimate sites, or simply reusing them inappropriately.
Maximizing this protection requires careful configuration, enabling prerequisites like User-ID and SSL Decryption, keeping content databases updated, and applying granular policies based on risk tolerance. By implementing these features thoughtfully according to best practices, organizations can significantly reduce their attack surface and mitigate the substantial risks associated with credential compromise.
Knowledge Check Quiz
Test your understanding based on the detailed information provided.