Aggregate vs. Classified DoS Protection Profiles
Overview
Palo Alto Networks firewalls provide robust Denial-of-Service (DoS) protection capabilities configured via DoS Protection Profiles applied to DoS Protection Policy rules ( Policies > DoS Protection ). A fundamental choice when creating a DoS Protection Profile ( Objects > Security Profiles > DoS Protection ) is selecting the profile type: Aggregate or Classified .
Choosing the correct profile type is crucial because it determines the scope and granularity of protection, impacting both security effectiveness and firewall resource consumption.
- Aggregate Profiles: Monitor the total traffic volume or connection rate for *all* traffic matching the DoS policy rule criteria combined.
- Classified Profiles: Monitor traffic volume or connection rates on a more granular basis, tracking statistics *per source IP*, *per destination IP*, or *per source-destination IP pair* within the traffic matching the DoS policy rule.
Aggregate DoS Protection Profiles
An Aggregate DoS Protection profile applies its configured thresholds (Alarm, Activate, Maximum Rates for metrics like CPS - Connections Per Second) to the total combined traffic that matches the associated DoS Protection Policy rule.
How it Works:
- The firewall maintains a single set of counters for the chosen metric (e.g., SYN CPS, UDP CPS, Total Concurrent Sessions) for all sessions matching the policy rule.
- When the total rate or count exceeds the configured Activate Rate threshold, the firewall initiates the configured mitigation action (e.g., SYN Cookies, rate limiting via Random Early Drop - RED) against all new incoming sessions that match the policy rule.
- It does not differentiate between individual source or destination IPs contributing to the threshold breach; the action is applied collectively.
Use Cases:
- Protecting a group of servers (e.g., a web farm behind a load balancer) where the primary concern is the total load hitting the service or the firewall resources handling that load, rather than identifying individual malicious sources.
- Simpler scenarios where granular per-IP tracking is not required or desired.
- Environments where firewall resource consumption for state tracking needs to be minimized.
Configuration:
- Create a DoS Protection Profile ( Objects > Security Profiles > DoS Protection ).
- Select Type: Aggregate .
- Configure thresholds (Alarm, Activate, Max) for relevant Flood Protection types (e.g., TCP SYN, UDP, ICMP). These thresholds represent the total rate for all matching traffic.
- Apply this profile to a DoS Protection Policy rule ( Policies > DoS Protection ) targeting the destination resource(s).
Classified DoS Protection Profiles
A Classified DoS Protection profile provides more granular protection by monitoring traffic and applying thresholds independently for specific entities within the overall traffic flow matching the DoS policy rule.
How it Works:
- The firewall maintains separate counters and state information based on the chosen classification criteria.
-
When configuring the profile (
Objects > Security Profiles > DoS Protection
), you select the
Classified Address
type:
-
destination-ip-only: Tracks connection rates/counts per unique destination IP address matching the policy. -
source-ip-only: Tracks connection rates/counts per unique source IP address matching the policy. -
source-and-destination-ip(orsrc-dest-ip-both): Tracks connection rates/counts per unique source-destination IP address pair matching the policy.
-
- Each classified entity (e.g., each source IP if classified by source) has its own set of thresholds (Alarm, Activate, Max).
- When a *specific* classified entity (e.g., a single attacking source IP) exceeds its individual threshold, the mitigation action (e.g., SYN Cookies, RED) is applied only to new sessions involving that specific offending entity . Legitimate traffic from other sources/to other destinations (within the same policy rule) remains unaffected unless they also exceed their thresholds independently.
Use Cases:
-
Protecting multiple critical servers individually when they reside within the same subnet targeted by a single DoS policy rule (using
destination-ip-only). -
Identifying and mitigating attacks originating from specific abusive source IPs while allowing legitimate traffic from other sources (using
source-ip-onlyorsource-and-destination-ip). - Scenarios requiring fine-grained control over DoS mitigation actions.
Configuration:
- Create a DoS Protection Profile ( Objects > Security Profiles > DoS Protection ).
- Select Type: Classified .
-
Choose the
Classified Address
criteria (
destination-ip-only,source-ip-only,source-and-destination-ip). - Configure thresholds (Alarm, Activate, Max). These thresholds apply *per classified entity*.
- Apply this profile to a DoS Protection Policy rule ( Policies > DoS Protection ).
source-ip-only
or
source-and-destination-ip
classification in DoS policies applied to internet-facing zones (like Untrust) is generally
not recommended
. The potentially vast number of unique external source IPs can overwhelm the firewall's resources dedicated to tracking these classified states. Use
destination-ip-only
for protecting specific internal servers from external attacks.
Comparison Table: Aggregate vs. Classified
| Feature | Classified Profile | Aggregate Profile |
|---|---|---|
| Scope of Protection | Applies thresholds individually based on classification (Source IP, Destination IP, or Source-Destination Pair). | Applies thresholds to the total combined traffic matching the policy rule. |
| Threshold Application | Each classified entity has its own independent set of counters and thresholds. | All matching traffic contributes to a single, shared set of counters and thresholds. |
| Mitigation Action Scope | Action (e.g., RED, SYN Cookies) applies only to new sessions involving the specific entity that exceeded its threshold. | Action applies to all new sessions matching the policy rule once the aggregate threshold is exceeded. |
| Primary Use Case | Protecting specific critical hosts individually; identifying/mitigating specific abusive sources. | Protecting groups of resources collectively; situations where overall load is the main concern. |
| Firewall Resource Consumption | Higher (due to tracking state per classified entity). Can be very high if using source-based classification on internet traffic. | Lower (only tracks aggregate state). |
| Configuration Complexity | Slightly more complex due to classification choice. | Simpler. |
| Recommended Internet-Facing Classification |
destination-ip-only
(to protect specific internal servers).
|
N/A (applies to aggregate). |
| Configuration Location |
Objects > Security Profiles > DoS Protection
(Profile definition)
Policies > DoS Protection (Policy Rule application) |
|
Best Practices for DoS Protection
- Understand Your Goal: Determine if you need to protect specific critical servers individually (favor Classified - destination-ip-only) or protect a group of resources from collective overload (favor Aggregate).
- Baseline Traffic: Before enabling blocking actions, monitor normal connection rates (CPS) and concurrent session counts for the resources you intend to protect. Set thresholds based on these baselines plus a reasonable buffer.
- Start with Alert/Monitor: Initially configure DoS profiles with high thresholds or set the DoS Policy rule action to 'Allow' but ensure logging is enabled (or use 'Protect' with high thresholds) to monitor logs for legitimate peaks versus actual attacks.
- Tune Thresholds Gradually: Lower thresholds cautiously based on observed traffic and log analysis. Avoid setting thresholds too low, which could block legitimate users during normal peak times.
-
Use
destination-ip-onlyfor Internet-Facing Classified: As highlighted before, avoidsource-ip-onlyorsource-and-destination-ipclassification in Classified profiles applied to rules matching internet traffic to prevent excessive resource consumption on the firewall. - Combine Profiles (Advanced): A single DoS Protection Policy rule can reference *both* an Aggregate profile and a Classified profile. This allows for layered protection: the Aggregate profile protects against massive overall floods, while the Classified profile can target specific abusive sources or protect individual destinations within the group once the overall traffic level is acceptable.
- Leverage SYN Cookies: For protecting TCP-based services (like web servers) against SYN floods, ensure SYN Flood protection is enabled in the DoS Profile and use the 'SYN Cookies' action in the DoS Policy rule.
- Regularly Review Logs: Monitor the Threat logs for DoS protection events to understand attack patterns and refine thresholds.
- Consider Zone Protection First: Implement Zone Protection Profiles on ingress zones as a first line of defense against broad floods and reconnaissance before relying solely on DoS policies for specific resource protection.
Diagrams: DoS Protection Concepts
Sequence Diagram: DoS Policy Processing
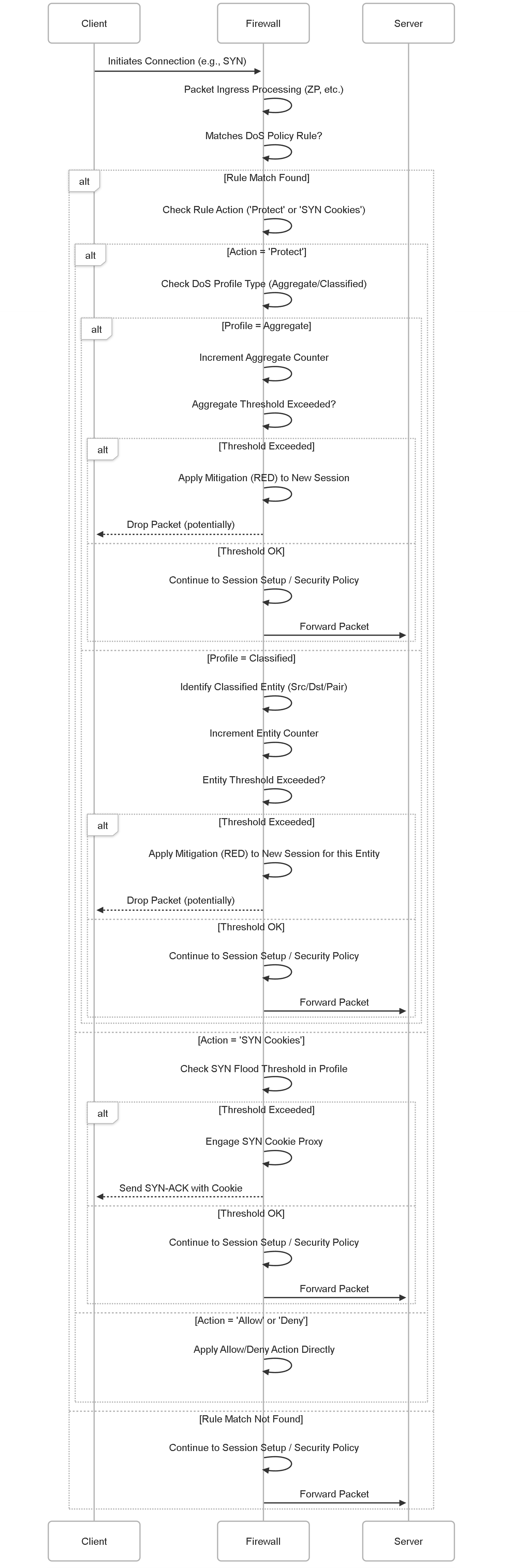
Sequence diagram illustrating how Aggregate and Classified DoS profiles are checked within a DoS Policy rule.
Flowchart: Aggregate vs. Classified Logic
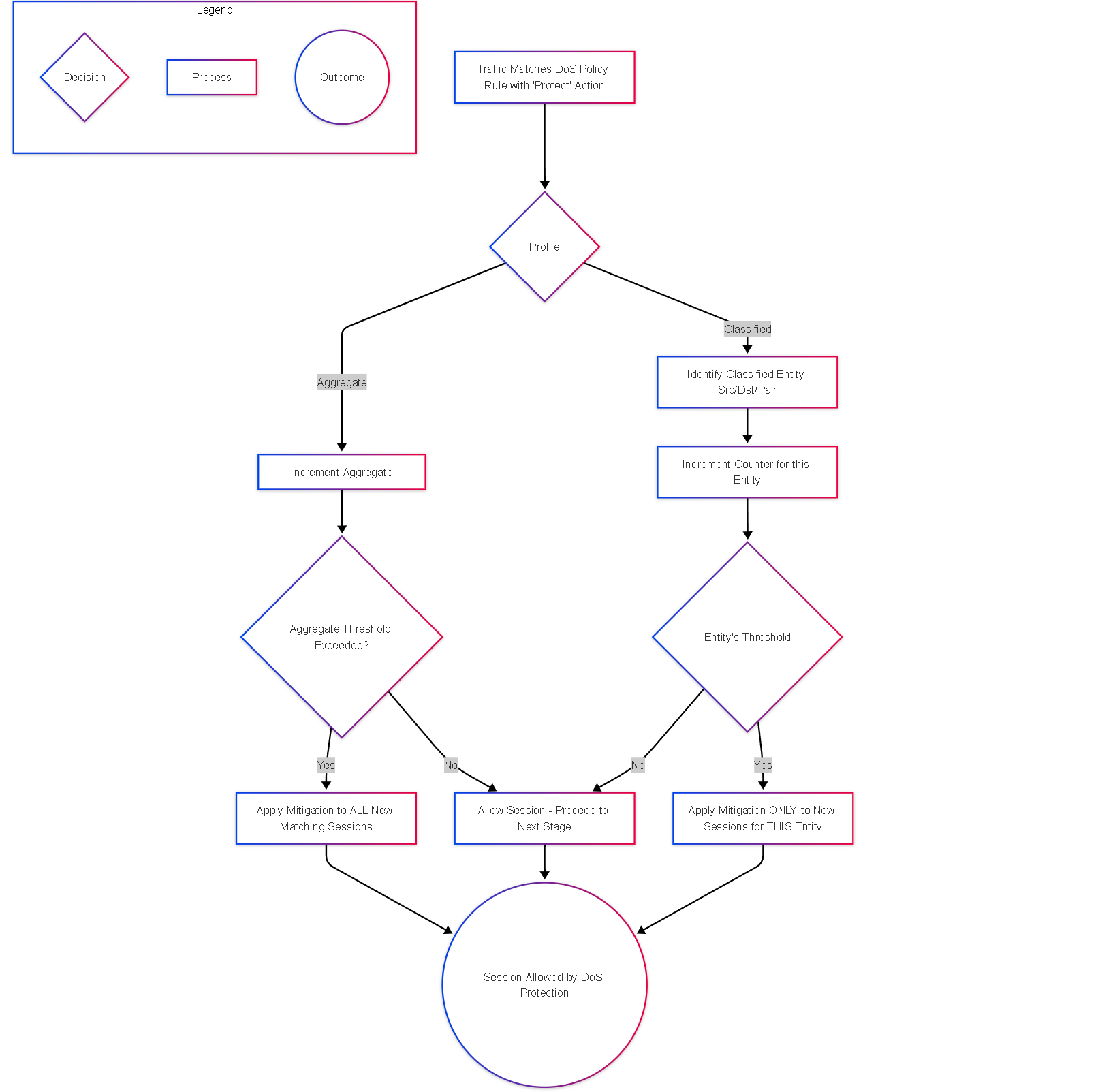
Flowchart comparing the logic flow for Aggregate vs. Classified DoS protection.
Graph: Relationship between Components
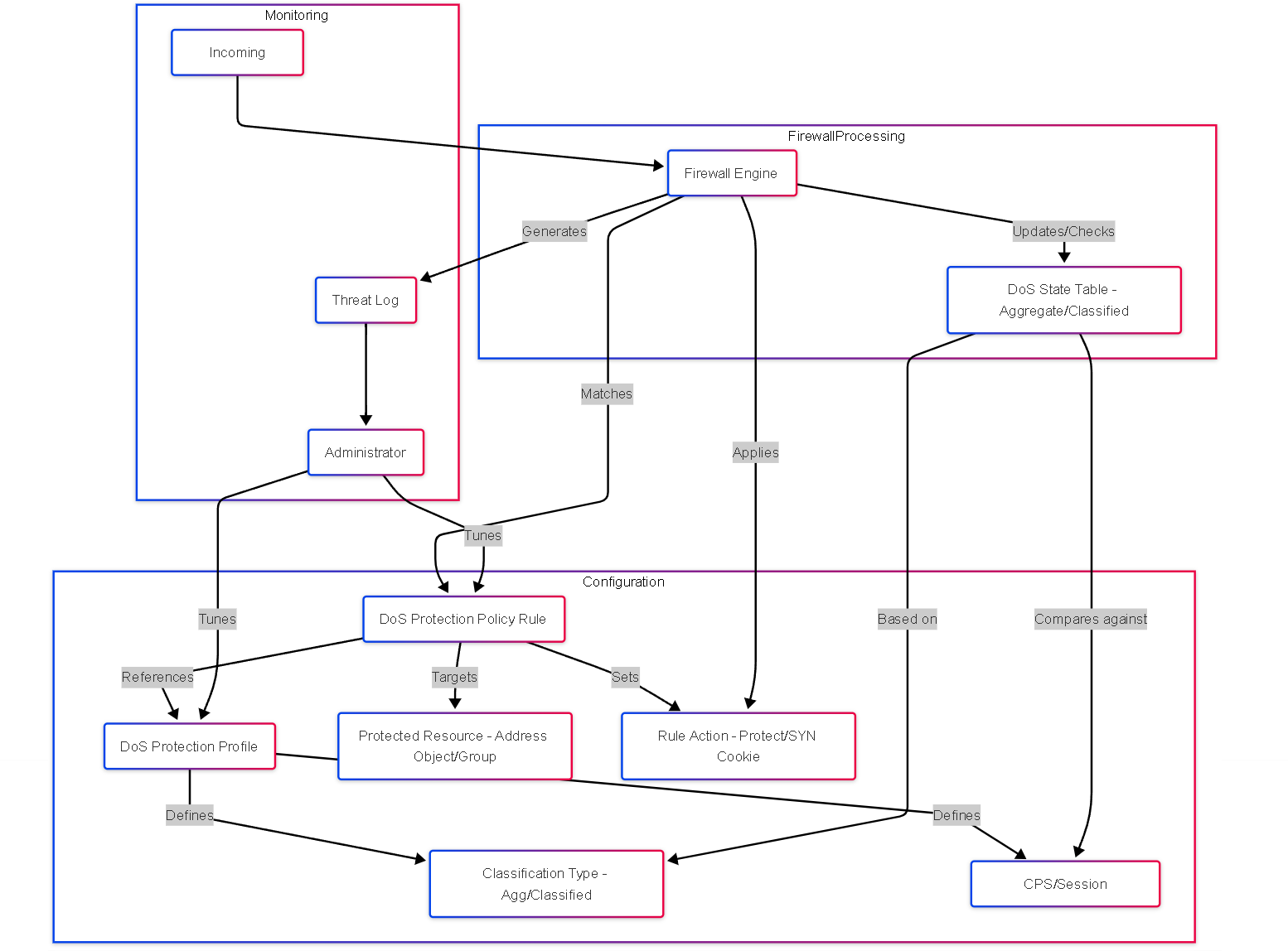
Graph showing the relationships between DoS Policy Rules, DoS Profiles, thresholds, traffic, and logging.
State Diagram: DoS Protection State (Simplified CPS Threshold)
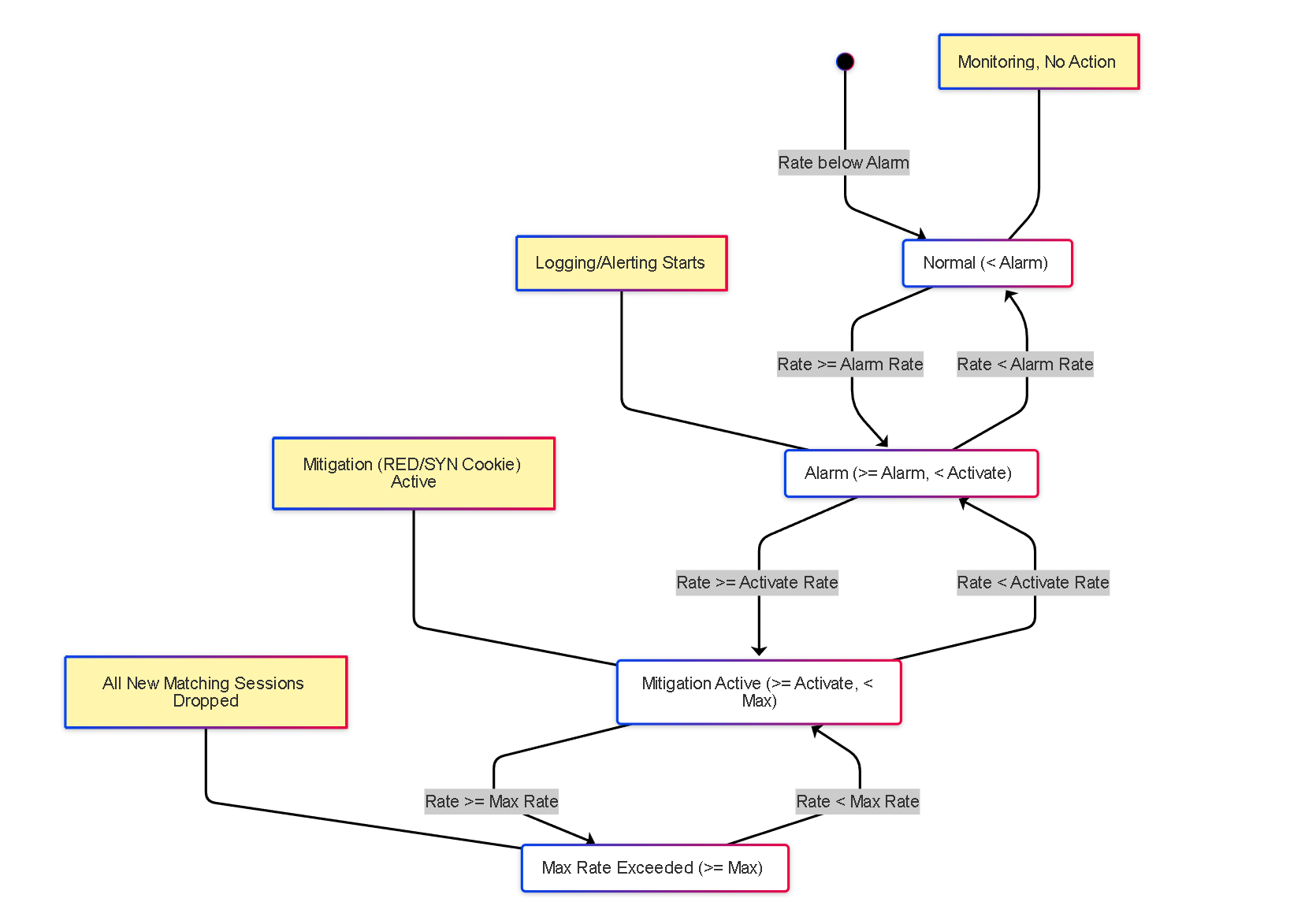
Simplified state diagram based on Connections Per Second (CPS) thresholds in a DoS profile (applies conceptually to Aggregate total or individual Classified entity).
PCNSE Exam Focus Points
Key concepts regarding Aggregate vs. Classified DoS Protection for the PCNSE exam:
- Primary Distinction: Understand that Aggregate applies one set of thresholds to the total matching traffic, while Classified applies thresholds independently per source IP, destination IP, or source-destination pair.
-
Use Cases:
- Use Aggregate to protect a group of servers collectively or when overall load is the concern.
- Use Classified (destination-ip-only) to protect specific critical servers individually within a broader policy match.
- Use Classified (source-ip-only / src-dest-ip-both) cautiously, primarily for internal zones, to mitigate specific abusive sources.
-
Configuration Locations:
- Profiles created under: Objects > Security Profiles > DoS Protection .
- Profiles applied via policy rules under: Policies > DoS Protection .
-
Classified Types:
Know the three classification types:
destination-ip-only,source-ip-only,source-and-destination-ip. -
Resource Consumption Warning:
Be aware of the
high resource usage potential
of source-based Classified profiles, especially on internet-facing interfaces, and why
destination-ip-onlyis generally preferred there. -
Policy Actions:
Understand the main DoS Policy rule actions:
Protect(enforces profile settings),SYN Cookies(enforces SYN flood settings from profile),Allow,Deny. - Thresholds: Recognize that thresholds (Alarm, Activate, Max) are typically based on Connections Per Second (CPS) or concurrent sessions.
- Logging: DoS Protection events are logged in the Threat Log .
- Relationship to Zone Protection: Understand that DoS Protection complements Zone Protection by providing targeted defense for specific destination resources, while Zone Protection defends the zone ingress.
Aggregate vs. Classified DoS Quiz (PCNSE Style)
Test your understanding of DoS Protection profile types.