Palo Alto Networks: Layer 3 & Layer 4 Header Inspection
Palo Alto Networks firewalls offer advanced security capabilities that extend beyond basic stateful inspection. One such capability is Layer 3 (Network Layer) and Layer 4 (Transport Layer) Header Inspection . This feature allows the firewall to analyze packet headers for anomalies, malformed structures, and specific attributes associated with threats or vulnerabilities, often before a session is fully established.
Introduced formally as a configurable feature within Zone Protection profiles in PAN-OS 11.0, L3/L4 header inspection provides a proactive defense mechanism, enabling administrators to detect and mitigate potential attacks at a very early stage of packet processing. This capability enhances the firewall's ability to protect itself and downstream network segments.
This article provides a comprehensive overview of L3/L4 Header Inspection, its integration with other firewall features, configuration details, best practices, and key points relevant for the PCNSE exam.
Core Concepts of L3/L4 Header Inspection
- Early Stage Inspection: This inspection occurs very early in the firewall's packet processing pipeline, often before session lookup or Security Policy evaluation for certain threat types. This allows the firewall to drop malicious or non-compliant packets efficiently.
- Focus on Headers: As the name implies, the inspection focuses solely on the information contained within the Layer 3 (e.g., IP flags, version, TTL, options) and Layer 4 (e.g., TCP flags, ports, sequence numbers, UDP checksum) headers. It does not inspect the payload at this stage (payload inspection is handled by Threat Prevention, Anti-Spyware, etc.).
- Protocol Anomaly Detection: It can identify packets that violate protocol standards (e.g., malformed headers, invalid flag combinations like TCP SYN+FIN, SYN packets with data, zero ports).
- Custom Signature Matching: A powerful aspect is the ability to create custom vulnerability signatures that match specific patterns or values within L3/L4 headers. This is particularly useful for protecting against exploits targeting vulnerabilities in legacy or non-standard TCP/IP stacks often found in IoT or embedded devices.
- Supported Protocols: Inspection and custom signatures are supported for IP/IPv6, ICMP/ICMPv6, TCP, and UDP.
- Primary Configuration Point: While enabled globally, the rules and actions for L3/L4 Header Inspection are primarily configured within Zone Protection Profiles.
Integration with Zone Protection Profiles
The primary way to leverage L3/L4 header inspection is through Zone Protection Profiles. Starting in PAN-OS 11.0, Zone Protection Profiles gained a dedicated section for configuring L3/L4 inspection rules.
Integrating with Zone Protection allows the firewall to:
- Apply header inspection rules to all traffic entering a specific zone.
- Detect malformed packets and protocol anomalies defined in the profile.
- Match traffic against custom L3/L4 vulnerability signatures based on header attributes.
-
Enforce actions like
alert,drop, orresetconnection upon detecting threats defined by these custom rules. - Stop potentially harmful traffic before it consumes further firewall resources or reaches protected network segments.
Configuration Steps within Zone Protection:
-
Global Enablement (Requires Reboot):
First, L3/L4 Header Inspection must be enabled globally under
Device > Setup > Session. This requires a firewall reboot . -
Create/Edit Zone Protection Profile:
Navigate to
Network > Network Profiles > Zone Protectionand select or create a profile. - Enable L3 & L4 Header Inspection Tab: Within the profile, go to the "L3 & L4 Header Inspection" tab to define custom rules.
- Define Custom Rules: Add rules specifying conditions (matching specific header fields/values) and actions (alert, drop, reset, allow). Each rule requires a unique Threat ID within specific ranges.
-
Apply Profile to Zone:
Navigate to
Network > Zones, select the target ingress zone, and assign the configured Zone Protection Profile. -
Enable Zone Inspection:
Within the Zone configuration (
Network > Zones), ensure "Enable Net Inspection" (or similar wording depending on PAN-OS version) is checked for the zone to activate the L3/L4 header inspection rules defined in the applied profile. - Commit the changes.
Integration with Packet Buffer Protection
Packet Buffer Protection is designed to prevent the firewall's packet buffers from being exhausted, typically by high volumes of legitimate or attack traffic. While distinct, L3/L4 header inspection complements Packet Buffer Protection.
How L3/L4 Header Inspection helps:
- Early Packet Filtering: By inspecting headers and dropping malformed or anomalous packets based on L3/L4 rules (either built-in Zone Protection packet-based rules or custom L3/L4 signatures), the firewall prevents these invalid packets from ever reaching or consuming space in the packet buffers.
- Reducing Buffer Load: Filtering out unwanted traffic at the header level reduces the overall load on the packet buffers, making them less susceptible to exhaustion during high traffic or attack scenarios.
- Improving Traffic Quality: By ensuring only valid packets (from a header perspective) proceed further, it enhances the quality of traffic being processed by later stages, including the buffer management system.
Integration with DoS Protection Profiles/Policies
DoS Protection profiles and policies focus on mitigating denial-of-service attacks, primarily floods, by enforcing rate limits and other protections based on traffic volume and characteristics.
L3/L4 header inspection integrates with and enhances DoS protection in several ways:
- Protocol Anomaly Detection: DoS attacks often exploit protocol weaknesses or use malformed packets. L3/L4 header inspection (via Zone Protection's packet-based rules or custom L3/L4 signatures) can detect and drop these anomalous packets before they contribute to overwhelming DoS protection thresholds.
- Granular Control Foundation: While DoS Protection profiles themselves define rate limits (CPS/PPS) and actions (protect, syncookie, allow, deny), the underlying ability of the firewall to parse and understand L3/L4 headers is fundamental. Header inspection provides the granular visibility needed for DoS protection to classify traffic (e.g., SYN packets, UDP packets) and apply specific thresholds.
- Complementary Protection: Zone Protection (including L3/L4 header inspection rules and standard flood/recon/packet protections) and DoS Protection Profiles/Policies work together. Zone Protection provides broad, zone-level defense, while DoS Protection allows for more targeted protection of specific destination IPs or classified traffic types.
Configuration Context:
-
DoS Protection profiles are configured under
Objects > Security Profiles > DoS Protection. -
DoS Protection policies, which apply these profiles to specific traffic matching source/destination zones, addresses, and services, are configured under
Policies > DoS Protection.
Custom L3/L4 Vulnerability Signatures: Overview & Purpose
A powerful feature enabled by L3/L4 Header Inspection is the ability to create Custom Layer 3 & Layer 4 Vulnerability Signatures . These allow administrators to define specific threat patterns based purely on header fields.
Purpose:
- Targeting Specific Vulnerabilities: Create signatures for known vulnerabilities that can be identified solely by L3/L4 header characteristics (e.g., specific IP options, TCP flag combinations, unusual lengths, specific port usage anomalies).
- Protecting Legacy/IoT Devices: Provide targeted protection for devices using old, deprecated, or non-standard TCP/IP stacks that might be vulnerable to exploits detectable via header analysis, especially when standard Threat Prevention signatures might not exist.
- Policy Enforcement: Block or alert on specific types of traffic based on header attributes that might not align with standard protocols but are known to be used for specific unwanted applications or tunnels within the organization.
- Proactive Defense: Implement defenses against newly discovered header-based attack vectors before official signatures are released.
These signatures are configured as rules within the "L3 & L4 Header Inspection" tab of a Zone Protection Profile.
Custom L3/L4 Vulnerability Signatures: Configuration Details
Creating a custom L3/L4 signature involves defining matching conditions within the header and specifying the action to take. This is done when adding or editing a rule in the "L3 & L4 Header Inspection" tab of a Zone Protection Profile.
Key Configuration Fields (Rule > Configuration Tab):
- Rule Name: A descriptive name for the custom rule.
-
Threat ID:
A unique numeric identifier for the custom threat. Must be within specific reserved ranges:
41000-45000or6800001-6900000. This ID appears in the Threat logs. - Comment: Optional description of the rule's purpose.
-
Packet Capture:
Options like
disable,single-packet, orextended-captureto capture packets matching the rule for analysis. - Send ICMP Unreachable: Option to send an ICMP unreachable message back to the source if the packet is dropped by this rule.
- Exempt IP: Define source or destination IP addresses/subnets that should be excluded from this specific rule (useful for preventing blocks on legitimate scanners or management tools).
- Log Severity: Set the severity level (Informational to Critical) for the corresponding Threat log entry.
- Log Interval: Define the interval for logging events triggered by this rule.
-
Action:
The action to take when the signature matches:
-
alert: Log the event but allow the packet. -
drop: Silently discard the packet and log the event. -
reset-client: Send TCP RST to the client. -
reset-server: Send TCP RST to the server. -
reset-both: Send TCP RST to both client and server. -
allow: Explicitly permit the packet (can be used for exceptions before broader block rules).
-
Key Configuration Fields (Rule > Signature Tab):
This tab defines the actual conditions that must match within the packet headers.
- Add Condition (Logical AND): Multiple conditions can be added; all must match for the rule to trigger.
- Add Or-Condition (Logical OR): Create groups of conditions where any one condition within the "OR" group needs to match.
- Attribute: Select the specific L3 or L4 header field to inspect (e.g., `ip.flags.df`, `ip.proto`, `tcp.flags.syn`, `tcp.dstport`, `udp.len`, `icmp.type`).
- Operator: Choose the comparison operator (e.g., `greater-than`, `less-than`, `equal-to`, `not-equal-to`, `pattern-match`, `range`). The available operators depend on the selected attribute.
- Value/Qualifier/Context: Specify the value, pattern (using PCRE syntax for pattern-match), range, or context for the condition based on the attribute and operator selected.
Configuration Summary
Enabling and using L3/L4 Header Inspection involves these steps:
- Global Enablement (Device > Setup > Session): Check the box for "L3 & L4 Header Inspection". Requires Firewall Reboot .
-
Define Zone Protection Profile (Network > Network Profiles > Zone Protection):
- Create or edit a profile.
- Navigate to the "L3 & L4 Header Inspection" tab.
- Click "Add" to create a new custom rule.
- In the Configuration tab: Define Rule Name, Threat ID (e.g., 41001), Action (drop, alert, reset), Severity, Exempt IPs, Packet Capture, etc.
- In the Signature tab: Define the header matching conditions using Attributes, Operators, and Values. Add multiple AND/OR conditions as needed.
- Click OK to save the rule, and OK again to save the profile.
-
Apply Profile and Enable on Zone (Network > Zones):
- Select the ingress zone to protect.
- Assign the created Zone Protection Profile.
- Check the box "Enable Net Inspection" (or similar wording) to activate the L3/L4 rules within the assigned profile for this specific zone.
- Click OK.
- Commit the configuration changes.
Best Practices for L3/L4 Header Inspection
Follow these best practices when implementing L3/L4 Header Inspection:
- Enable Judiciously: Activate L3/L4 header inspection only on security zones where necessary, particularly internet-facing or untrusted zones. There's a limit to the number of zones that can have this feature enabled simultaneously, though specific numbers aren't always documented and may vary by platform. Apply it where the risk of protocol anomalies or header-based attacks is highest.
- Start with Alerting: When deploying new custom L3/L4 rules, initially set the action to `alert` rather than `drop` or `reset`. Monitor the Threat logs to ensure the rule matches the intended traffic and doesn't cause false positives by blocking legitimate flows.
- Define Specific Custom Signatures: Leverage custom L3/L4 signatures for targeted threats or vulnerabilities relevant to your environment, especially for non-standard or legacy systems. Avoid overly broad rules that might impact performance or block valid traffic.
- Use Packet Capture for Analysis: Enable packet capture (`single-packet` or `extended-capture`) on custom rules during testing and troubleshooting phases. This provides invaluable data for verifying signature logic and analyzing the triggering packets.
- Specify Exempt IPs Carefully: Use the "Exempt IP" feature to exclude trusted sources (like vulnerability scanners, network monitoring systems, or specific management stations) from triggering certain rules, preventing accidental blocks.
- Set Appropriate Log Severity: Assign meaningful log severity levels (e.g., Critical, High) to custom rules that detect definite threats, allowing for easier filtering and prioritization during incident response. Use lower severities (e.g., Informational, Medium) for rules designed for monitoring or less critical anomalies.
- Regularly Review and Update Rules: Periodically review the performance and logs related to your custom L3/L4 rules. Update or remove rules that are no longer relevant, trigger excessive false positives, or are superseded by updated standard protections.
- Understand Logging Behavior: Be aware that `reset` actions might log as `alert` in Threat logs. Correlate logs with expected behavior based on configured actions.
- Document Custom Rules: Clearly document the purpose, Threat ID, conditions, and expected behavior of each custom L3/L4 rule created.
Illustrations: L3/L4 Inspection Packet Flow
This flowchart shows where L3/L4 header inspection fits in the early packet processing stages:
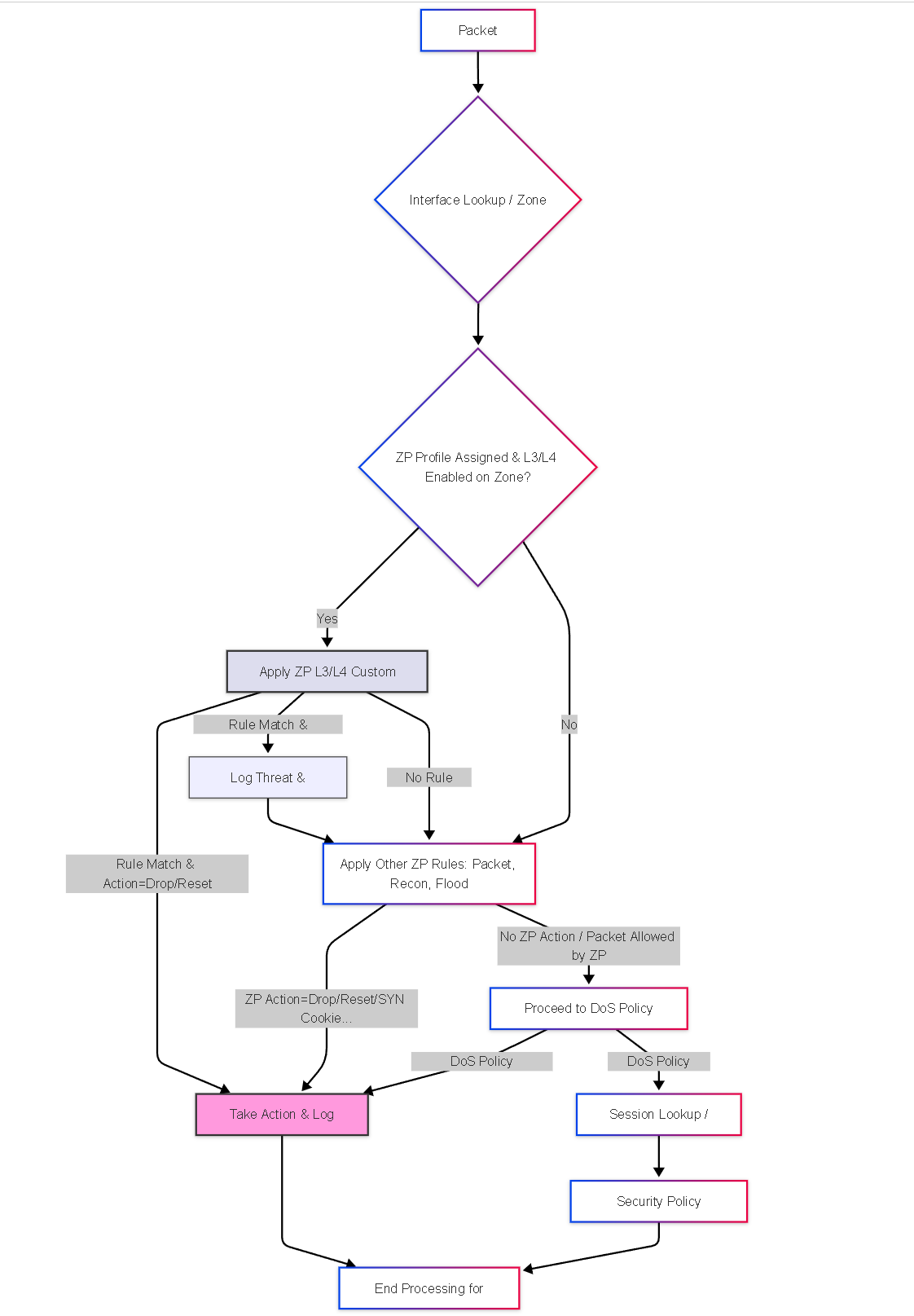
Simplified flow showing L3/L4 custom rule checks occurring within the Zone Protection phase, potentially dropping packets before DoS or Security Policy evaluation.
Illustrations: L3/L4 Inspection Configuration Relationship
This graph illustrates how the configuration elements relate to each other:
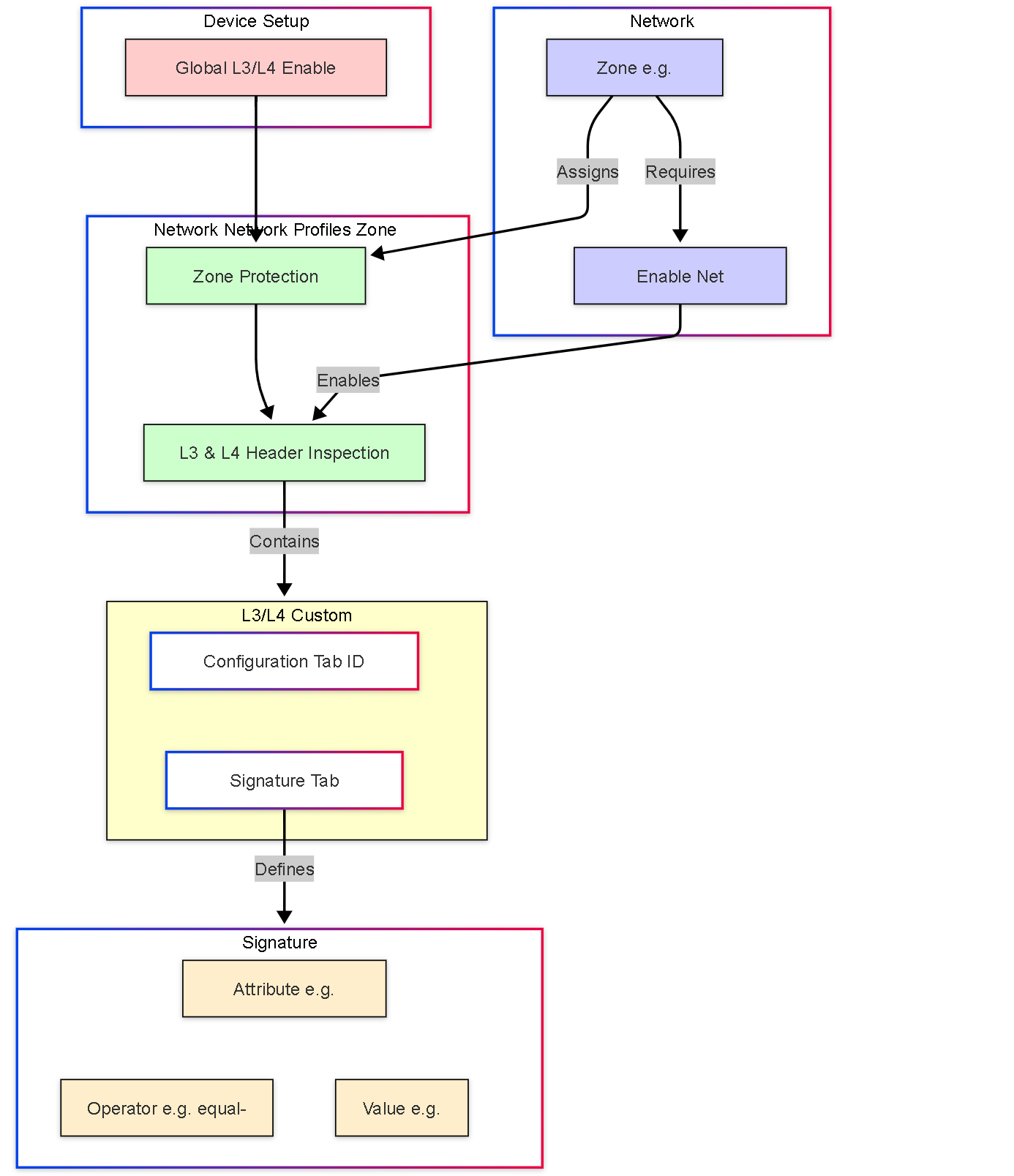
Relationship graph showing the dependencies: Global setting enables the feature, Zone Protection Profile contains the rules (Configuration + Signature), and the Zone applies the profile and activates the inspection.
Illustrations: Packet Processing Sequence with L3/L4 Inspection
This sequence diagram shows a packet being evaluated by a custom L3/L4 rule:
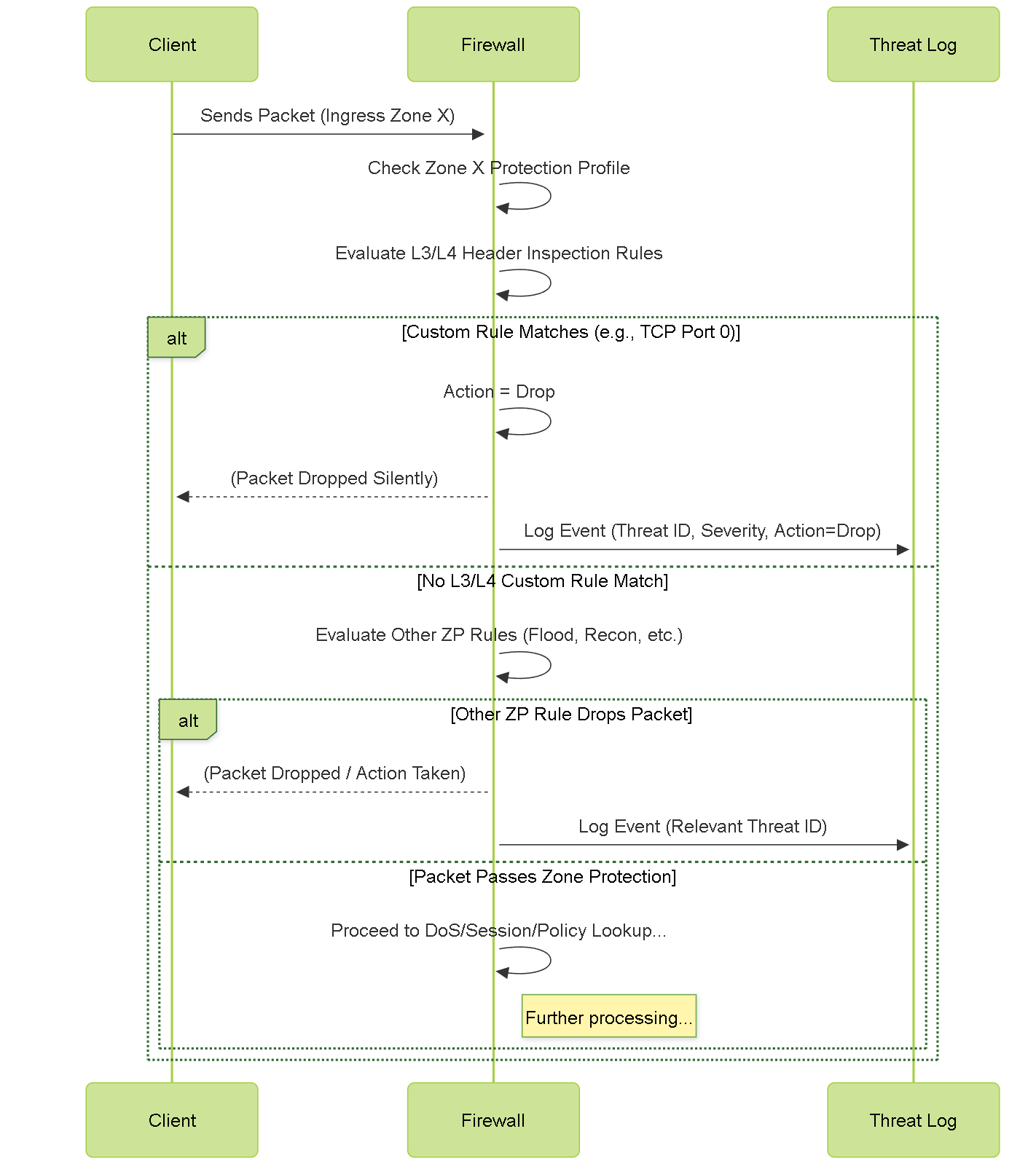
Sequence illustrating how a packet matching a custom L3/L4 rule with a 'drop' action is discarded early and logged, potentially bypassing further firewall processing stages.
Illustrations: Packet State during L3/L4 Inspection
This state diagram shows the possible states of a packet undergoing L3/L4 inspection:
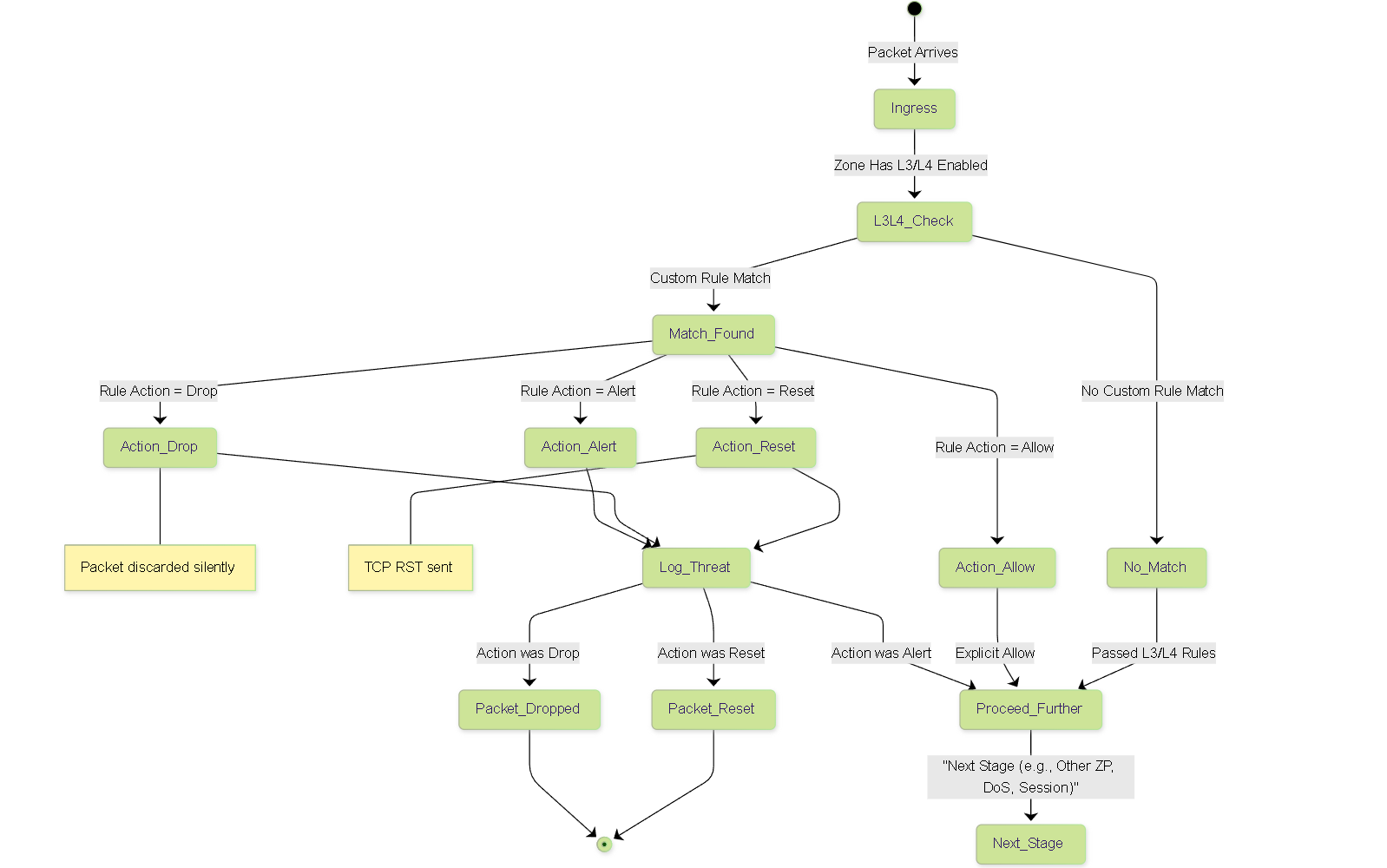
State diagram showing a packet's progression through L3/L4 custom rule evaluation, resulting in actions like Drop, Reset, Alert (log & proceed), or Allow, before moving to subsequent processing stages.
PCNSE Focus Points
Key areas related to L3/L4 Header Inspection for the PCNSE exam:
- Purpose and Placement: Understand that L3/L4 inspection occurs early, within Zone Protection Profiles applied to ingress zones, to detect anomalies and apply custom header-based signatures before full session processing.
- Configuration Steps: Know the multi-step process: Global enable (Device > Setup > Session, needs reboot), Profile creation (Network > Network Profiles > Zone Protection > L3&L4 Tab), Zone application (Network > Zones), and Enabling inspection on the zone itself.
- Custom Signatures: Recognize the ability to create custom vulnerability signatures based on L3/L4 header fields, their purpose (especially for IoT/legacy stacks), and the key configuration elements (Threat ID ranges, attributes, operators, actions).
- Supported Protocols: Be aware of the supported protocols: IP/IPv6, ICMP/ICMPv6, TCP, UDP.
- Integration: Understand how L3/L4 inspection complements Zone Protection (packet-based, flood, recon), Packet Buffer Protection (early filtering), and DoS Protection (detecting anomalous packets contributing to DoS).
- Logging: Know that events triggered by L3/L4 inspection rules are typically logged in the Threat Log . Be aware of the potential discrepancy where 'reset' actions might log as 'alert'.
- Limitations: Be aware that there is a limit on the number of zones where L3/L4 inspection can be simultaneously enabled.
- Use Cases: Identify scenarios where L3/L4 inspection is particularly useful, such as blocking specific protocol anomalies, protecting non-standard stacks, or enforcing policies based on header attributes.
PCNSE Prep Quiz: L3/L4 Header Inspection
Test your knowledge of Layer 3 and Layer 4 Header Inspection.