Protecting Firewall Resources: Zone, Packet Buffer, and DoS Protection
Goal and Use Case
While Security Profiles (like Antivirus, Anti-Spyware, Vulnerability Protection) focus on inspecting the content of allowed traffic for threats, another class of attacks targets the firewall itself or specific protected resources behind it. These attacks aim to exhaust resources like CPU, memory, session tables, or packet buffers, leading to a denial-of-service (DoS) condition where the firewall becomes unresponsive or unable to process legitimate traffic.
Palo Alto Networks firewalls provide several mechanisms, primarily configured under Network > Network Profiles , to mitigate these resource exhaustion and reconnaissance attacks:
- Zone Protection Profiles: Protect network segments (zones) from common flood attacks and reconnaissance scans directed at the firewall interfaces within that zone.
- Packet Buffer Protection: A global defense mechanism against overwhelming the firewall's shared hardware packet buffers.
- DoS Protection Profiles & Policies: Protect specific destination IP addresses (servers, critical hosts) behind the firewall from denial-of-service attacks.
Zone Protection Profiles
Zone Protection profiles are applied directly to ingress zones ( Network > Zones > [Select Zone] > Zone Protection Profile ) and defend against attacks targeting the firewall interfaces within that zone or attempting to map the network via reconnaissance.
Flood Protection
This defends against common volumetric flood attacks designed to overwhelm the firewall's session table or CPU.
-
Types of Floods Covered:
- SYN Flood: Detects excessive SYN packets (indicating the start of TCP sessions) without corresponding ACKs. Action can be RED (Random Early Drop) or SYN Cookies .
- UDP Flood: Detects high rates of UDP packets targeting the zone. Action is RED.
- ICMP Flood: Detects high rates of ICMP packets. Action is RED.
- Other IP Flood: Detects high rates of non-TCP/UDP/ICMP IP packets. Action is RED.
-
Thresholds (per flood type):
- Alarm Rate: Threshold (packets per second - pps) at which logs/alerts are generated. No packets dropped yet.
- Activate Rate: Threshold (pps) at which the firewall starts taking the configured mitigation action (SYN Cookies or RED). (Must be >= Alarm Rate)
- Maximum Rate: Absolute ceiling (pps) above which all matching flood packets are dropped. (Must be >= Activate Rate)
-
Actions:
- SYN Cookies (SYN Flood only): The firewall acts as a proxy for the TCP handshake. It responds to the client SYN with a SYN-ACK containing a cryptographic cookie. Only upon receiving a valid ACK back from the client (validating the source IP) does the firewall establish the connection to the actual server. This prevents the server/firewall session table from being filled by spoofed SYN packets.
- Random Early Drop (RED): As the packet rate approaches the Activate/Maximum thresholds, the firewall starts randomly dropping incoming packets of the flood type. The drop probability increases as the rate increases.
- Block Duration: How long (in seconds) an attacking IP address is blocked after exceeding thresholds (applies to Reconnaissance Protection).
Reconnaissance Protection
This detects and optionally blocks attempts to scan the network for open ports or active hosts.
-
Types Covered:
- TCP Port Scan: Detects when a single source IP scans multiple destination ports on one or more hosts within the zone.
- UDP Port Scan: Detects when a single source IP scans multiple UDP ports.
- Host Sweep: Detects when a single source IP sends packets (e.g., ICMP Echo, TCP SYN) to multiple destination IP addresses within the zone to identify live hosts.
- Action: Can be set to Alert (log only) or Block (log and block the source IP for the configured Block Duration).
- Thresholds: Configured within the profile, defining the number of scanned ports/hosts within a specific time interval that triggers the action.
Predefined Profiles
PAN-OS often includes predefined Zone Protection profiles like `default`, `strict`, and `lenient` with varying threshold levels, which can be used as starting points for tuning.
Packet Buffer Protection
Packet Buffer Protection is a global safeguard against exhaustion of the firewall's hardware packet buffers, which are a finite shared resource used for processing all traffic transiting the device.
Unlike Zone or DoS Protection which target specific types of traffic or destinations, Packet Buffer Protection acts as a safety net for the entire system's packet handling capacity.
How it Works
- Applied globally under Device > Setup > Session > Session Settings > Packet Buffer Protection .
- Monitors the overall utilization of the packet buffer pool.
- When buffer utilization exceeds a configured threshold (percentage), the firewall enters a "Red Zone" state.
- While in the Red Zone, the firewall starts applying Random Early Drop (RED) to *all* new incoming connections, regardless of source, destination, zone, or policy. This aims to alleviate buffer pressure by shedding load non-discriminately.
- An alert is typically generated in the System Log when Packet Buffer Protection activates.
Packet Buffer Protection Logging
Environment
- PAN-OS 8.x and later (Note: While the original text specified 8.x, PBP exists in later versions too)
- Packet Buffer Protection (PBP) Enabled
Log Generation
When Packet Buffer Protection is activated due to buffer congestion, the firewall generates specific log entries to record the event and subsequent actions.
System Logs
-
Location:
Monitor > Logs > System - Event Type: Typically general
- Severity: Informational (Note: Can vary, but activation is often informational, indicating a condition)
- Description Example: Indicates the buffer usage percentage exceeded the alert threshold (e.g., "Packet buffer congestion is 14272/17203 (82%)(alert threshold is 40%).").
Example System Log Entry:
Domain Receive Time Serial # Type Threat/Content Type Config Version Generate Time Virtual System Event ID Object fmt id module Severity Description
1 10/11/2019 12:01 xxxxxxx SYSTEM general 1 10/11/2019 12:01 general 0 0 general informational Packet buffer congestion is 14272/17203 (82%)(alert threshold is 40%).Threat Logs
Specific Threat IDs are generated when PBP takes action:
-
Location:
Monitor > Logs > Threat -
Common PBP Threat IDs:
-
Threat ID: 8507
- Type: Flood
- Name: PBP Packet Drop
- Severity: High
- Description: Packet buffer protection enforcing RED packet drop.
-
Threat ID: 8508
- Type: Flood
- Name: PBP Session Discarded
- Severity: High
- Description: Packet buffer protection enforcing session discard.
-
Threat ID: 8509
- Type: Flood
- Name: PBP IP Blocked
- Severity: High
- Description: Packet buffer protection enforcing source IP block. (Note: IP blocking might be less common directly from PBP compared to session/packet actions).
-
Threat ID: 8507
Example Threat Log Entries:
Domain Receive Time Serial # Type Threat/Content Type Config Version Generate Time Source address Destination address NAT Source IP NAT Destination IP Rule Source User Destination User Application Virtual System Source Zone Destination Zone Inbound Interface Outbound Interface Log Action Time Logged Session ID Repeat Count Source Port Destination Port NAT Source Port NAT Destination Port Flags IP Protocol Action URL/Filename Threat/Content Name Category Severity
1 10/11/2019 12:02 xxxxxxx THREAT flood 1 10/11/2019 12:02 10.10.10.10 192.168.10.10 not-applicable vsys1 vwire 10/11/2019 12:02 33555666 1 20033 20033 0 0 0x102000 hopopt block PBP Session Discarded(8508) any high
1 10/11/2019 12:02 xxxxxxx THREAT flood 1 10/11/2019 12:02 10.10.10.10 192.168.10.10 not-applicable vsys1 vwire 10/11/2019 12:02 33555666 1 20033 20033 0 0 0x102000 hopopt drop PBP Packet Drop(8507) any highGlobal Counters
Packet drops due to Packet Buffer Protection will also increment specific global counters, which can be viewed via the CLI:
show counter global | match flow_dos_pbp_drop
-
Counter Name:
flow_dos_pbp_drop - Description: Packets dropped: Dropped by packet buffer protect
Packet Buffer Protection Threat IDs
When Packet Buffer Protection takes specific actions to mitigate buffer exhaustion, corresponding events are logged in the Threat Log with the following Threat IDs:
-
Threat ID:
8507-
Threat Name:
PBP Packet Drop(or similar wording like "PBP IP enforcing RED packet drop" as noted in source) - Threat Type: Flood
- Severity: High
- Description: Indicates that Packet Buffer Protection is actively dropping packets using Random Early Drop (RED) due to buffer congestion.
-
Threat Name:
-
Threat ID:
8508-
Threat Name:
PBP Session Discarded - Threat Type: Flood
- Severity: High
- Description: Indicates that Packet Buffer Protection is discarding entire sessions to alleviate buffer pressure.
-
Threat Name:
-
Threat ID:
8509-
Threat Name:
PBP IP Blocked - Threat Type: Flood
- Severity: High
- Description: Indicates that Packet Buffer Protection is blocking traffic from specific source IP addresses identified as contributing excessively to buffer congestion (Note: This action might be less common than packet/session drops directly from PBP).
-
Threat Name:
DoS Protection Profiles & Policies
DoS Protection profiles, unlike Zone Protection, are used within DoS Protection Policy Rules ( Policies > DoS Protection ) to safeguard specific destination IP addresses or subnets (e.g., critical servers, entire server segments) from denial-of-service attacks.
It focuses on protecting resources *behind* the firewall, whereas Zone Protection primarily defends the firewall interfaces/zones themselves.
DoS Protection Profile Settings
Configured under Objects > Security Profiles > DoS Protection .
-
Protection Type:
- Aggregate: Monitors the total number of concurrent sessions or connection rate (CPS) for *all* traffic matching the DoS rule. If the total exceeds thresholds, protection actions apply broadly to new matching sessions. Useful for protecting a group of servers sharing a common resource pool.
- Classified: Tracks sessions or CPS *per source IP*, *per destination IP*, or *per source-destination pair*. Allows more granular protection, applying actions only to specific offending sources or overwhelmed destinations within the matched traffic.
-
Thresholds (based on CPS - Connections Per Second):
Defines rates for different actions (can vary slightly based on Aggregate vs. Classified and action type).
- Alarm Rate: Generates logs/alerts when CPS threshold is crossed.
- Activate Rate: Rate at which mitigation actions begin.
- Maximum Rate: Rate above which all new matching connections are dropped.
DoS Protection Policy Rules
Configured under Policies > DoS Protection . These rules determine *which* traffic the DoS Protection profile applies to.
- Matching Criteria: Rules match based on Source/Destination Zone, Source/Destination Address (crucially, protecting specific destination IPs/subnets), Service, etc.
- Profile Application: A configured DoS Protection Profile is attached to the rule.
-
Action:
The primary actions defined within the rule are:
- Protect: Enforces the thresholds and actions defined within the attached DoS Protection Profile (Aggregate or Classified).
- Allow: Bypasses DoS protection for matching traffic.
- Deny: Blocks matching traffic outright.
- SYN Cookies (TCP only): Activates SYN Cookie protection when the SYN Flood thresholds (defined in the *profile*) are exceeded for traffic matching this rule. Mitigates SYN floods targeting the protected destination(s).
Tuning Best Practices for Zone/DoS/Packet Buffer Protection
Effectively tuning these protection mechanisms requires careful consideration and monitoring.
- Establish Baselines: Before enabling blocking actions , understand your normal traffic patterns. Monitor connection rates (CPS), packet rates (pps), and buffer utilization during peak hours. Use tools like SNMP, NetFlow, or firewall reporting to establish baselines.
- Start with 'Alert' or High Thresholds: When first configuring Zone Protection or DoS Protection profiles/policies, set actions to `Alert` or configure relatively high `Activate` and `Maximum` thresholds based on your baseline + buffer room.
-
Monitor Logs:
- Check Monitor > Logs > Threat frequently for Zone Protection and DoS Protection alerts. Investigate the source and nature of triggering traffic.
- Check Monitor > Logs > System for Packet Buffer Protection alerts. These indicate severe load.
- Gradual Tightening: Based on log analysis and baseline data, gradually lower the `Activate` and `Maximum` thresholds towards values slightly above your observed legitimate peaks. Switch actions from `Alert` to mitigation actions (`SYN Cookies`, `RED`, `Protect`, `Block`) cautiously, one rule or profile at a time.
- Understand Scope: Remember Zone Protection applies broadly to zone ingress, while DoS Protection applies specifically via policy to protected destinations. Don't rely solely on Zone Protection to safeguard critical servers; use DoS policies.
- Use SYN Cookies Wisely: SYN Cookies are effective against SYN floods but add some processing overhead. Use the `SYN Cookies` action in Zone or DoS Protection specifically when SYN floods are a concern and observed.
- Classified vs. Aggregate DoS: Use Classified DoS profiles for more granular protection of multiple servers behind a single policy, applying actions only to offending sources/destinations. Use Aggregate if protecting a single resource or if the combined load is the primary concern.
- Packet Buffer Monitoring: Treat Packet Buffer Protection alerts as critical indicators of potential undersizing or massive attacks bypassing other layers. Investigate the cause immediately; tuning the threshold itself is usually less important than addressing the root cause.
- Documentation: Document baseline values, configured thresholds, and reasons for specific settings.
Diagrams: Resource Protection Concepts
Packet Flow Order
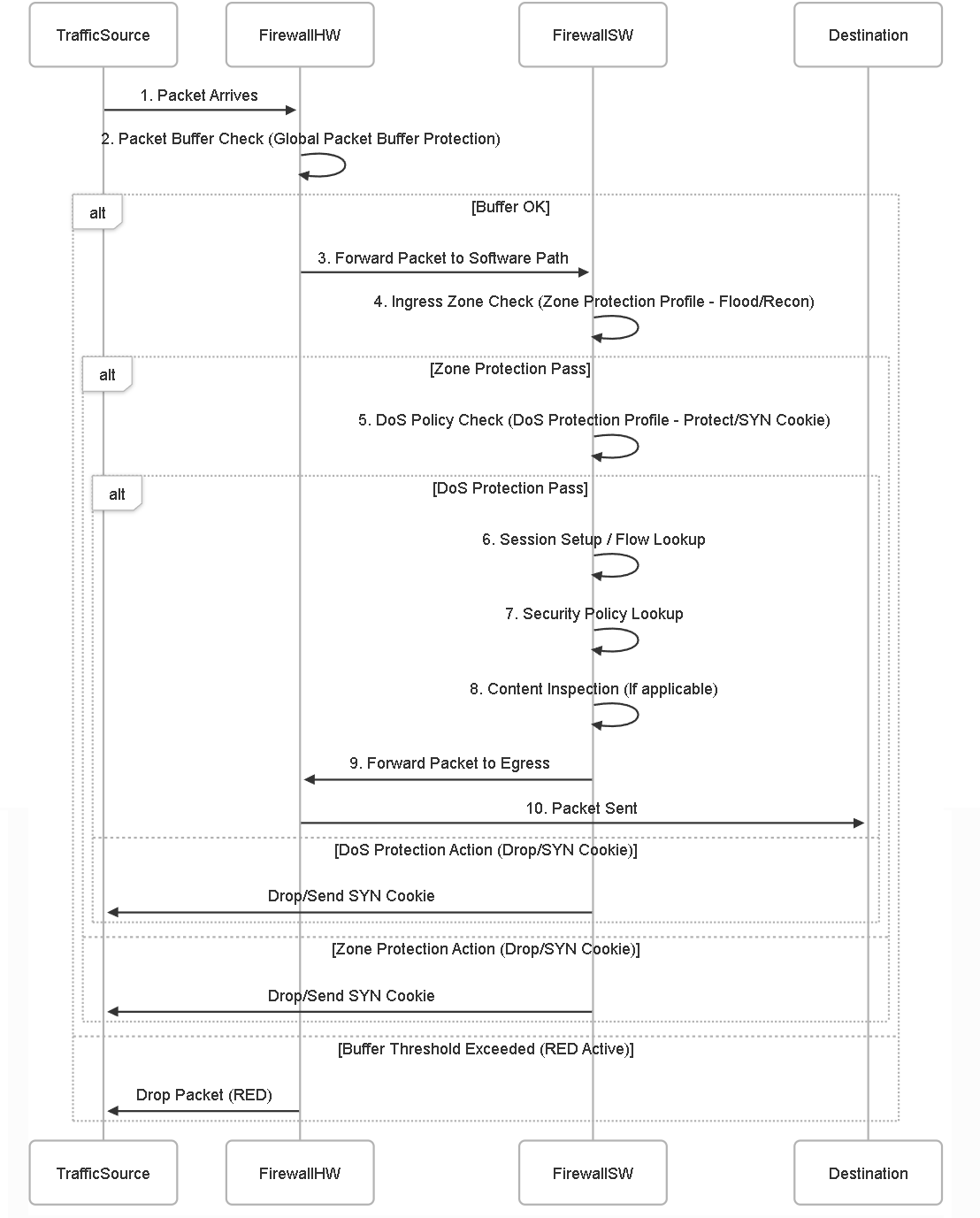
Simplified sequence showing the order of checks: Packet Buffer -> Zone Protection -> DoS Protection -> Security Policy/Content Inspection.
Zone Protection Flowchart
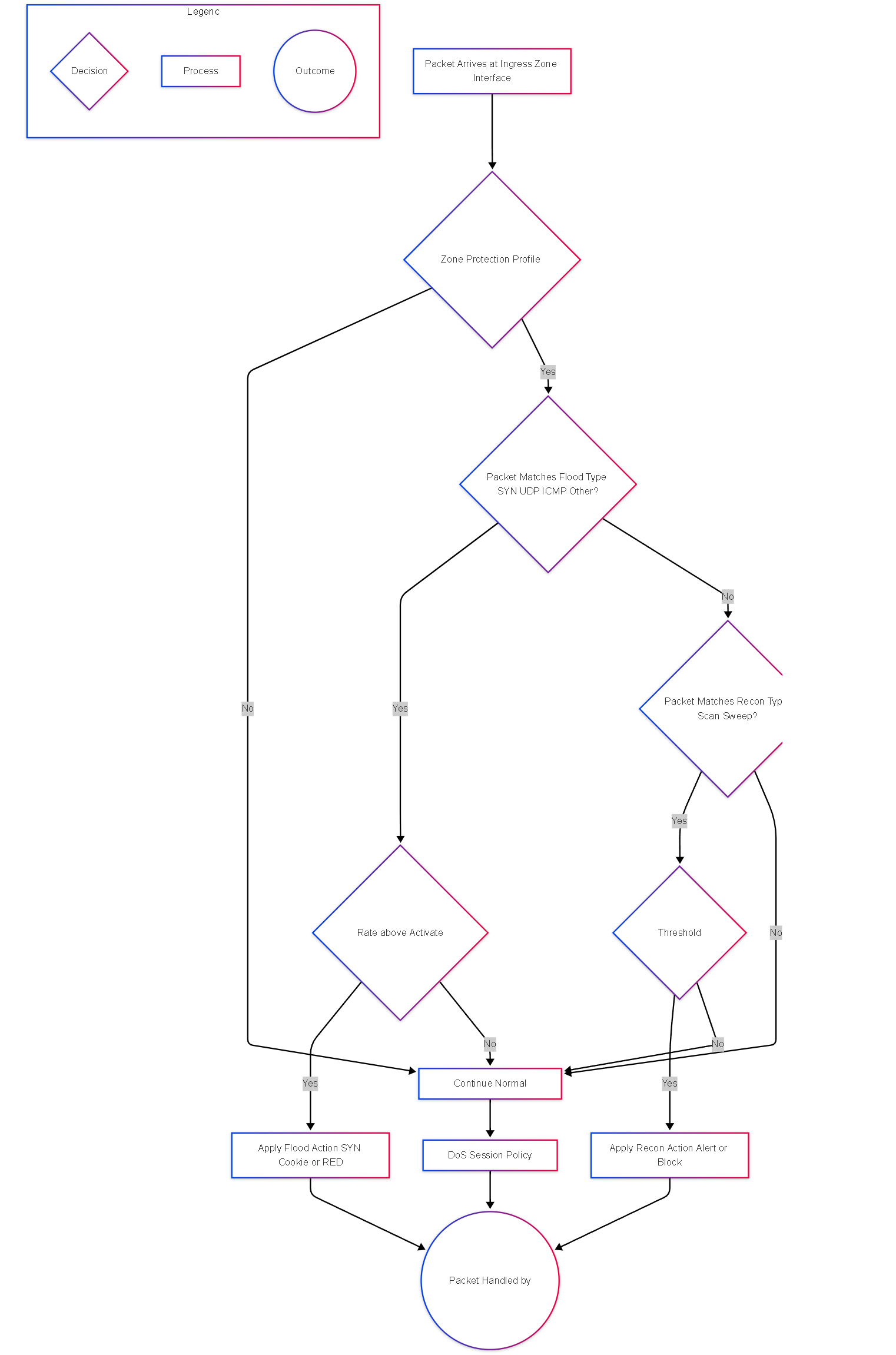
Decision flowchart for Zone Protection Profile processing.
DoS Protection State Diagram (Classified Example)
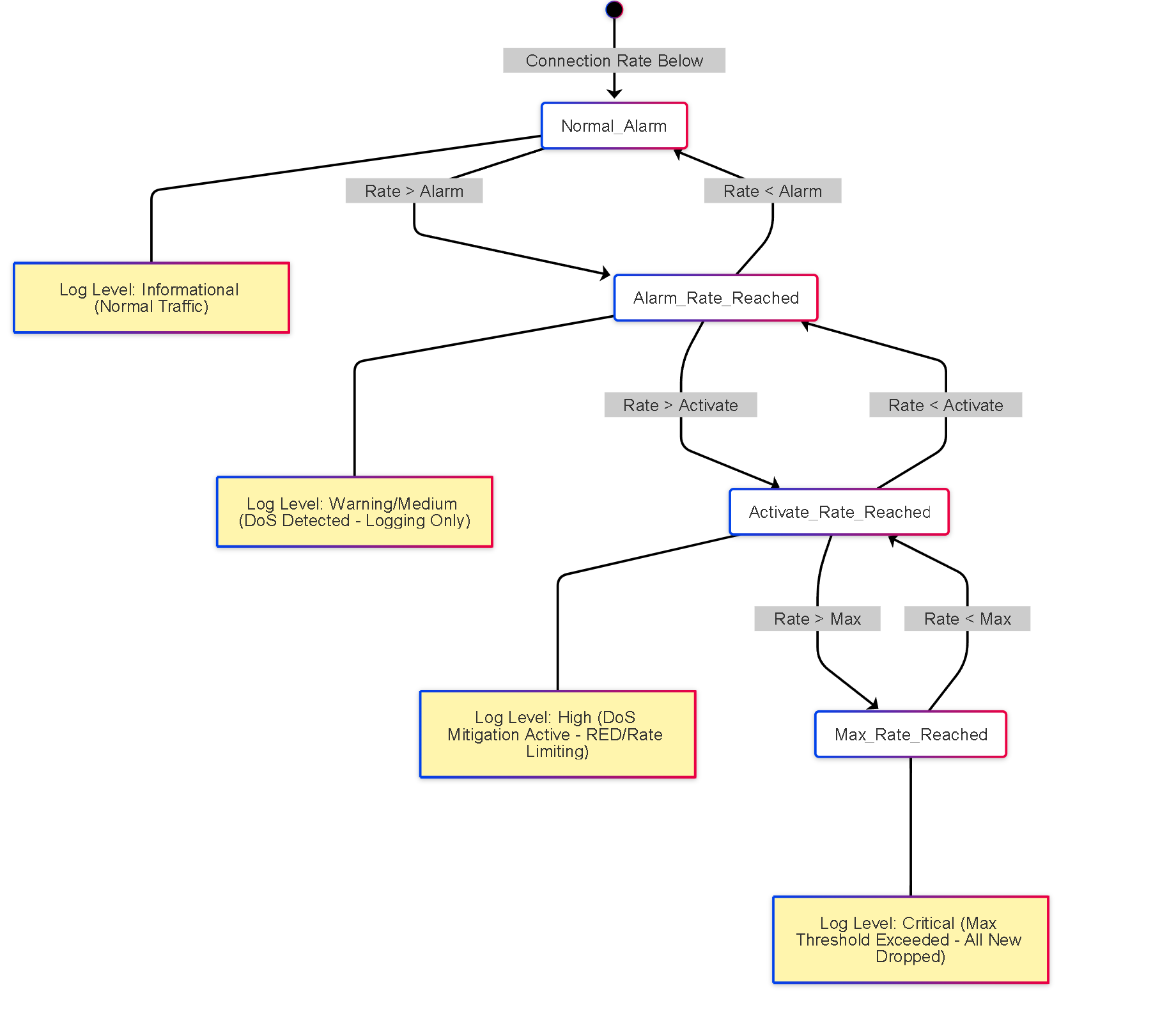
State transitions for a specific source/destination pair under Classified DoS Protection based on Connection Rate (CPS).
PCNSE Exam Focus Points
Key concepts related to Zone Protection, Packet Buffer Protection, and DoS Protection for the PCNSE exam:
- Core Purpose: Understand these features primarily protect the firewall resources (CPU, memory, buffers, sessions) and specific downstream servers, operating *before* content inspection security profiles.
-
Zone Protection vs. DoS Protection:
This is a critical distinction.
- Zone Protection: Applied directly to network Zones . Protects the firewall interfaces within the zone from ingress floods (SYN, UDP, ICMP, Other IP) and reconnaissance (scans, sweeps).
- DoS Protection: Applied via DoS Protection Policies . Protects specific destination IP addresses/subnets behind the firewall from DoS attacks based on connection rates (CPS).
- Packet Buffer Protection: Know it's a global setting ( Device > Setup > Session ) protecting shared hardware buffers via RED when utilization exceeds the threshold. Logged in System Logs .
-
Configuration Locations:
- Zone Protection Profiles: Network > Network Profiles > Zone Protection , applied under Network > Zones .
- DoS Protection Profiles: Objects > Security Profiles > DoS Protection , applied via Policies > DoS Protection .
- Packet Buffer Protection: Device > Setup > Session .
-
Zone Protection Details:
- Flood types: SYN, UDP, ICMP, Other IP.
- Thresholds: Alarm Rate, Activate Rate, Maximum Rate (all in pps).
- Actions: SYN Cookies (for SYN flood), Random Early Drop (RED).
- Recon types: TCP/UDP Port Scan, Host Sweep. Actions: Alert, Block (+ Block Duration).
-
DoS Protection Details:
- Policy-based, targets destination IPs.
- Profile Types: Aggregate vs. Classified. Know the difference in monitoring scope.
- Thresholds: Typically based on Connections Per Second (CPS) - Alarm, Activate, Max.
- Rule Actions: Protect (uses profile thresholds), SYN Cookies (uses profile SYN flood settings), Allow, Deny.
-
Logging:
- Zone Protection events: Threat Log .
- DoS Protection events: Threat Log .
- Packet Buffer Protection activation: System Log .
- Tuning Approach: Understand the importance of baselining, starting with alert/high thresholds, and gradual implementation.
Resource Protection Knowledge Check (PCNSE Style)
Test your understanding of Zone Protection, Packet Buffer Protection, and DoS Protection.