Comprehensive Guide to Palo Alto Networks Zone Protection Profiles
Palo Alto Networks Next-Generation Firewalls (NGFWs) provide multiple layers of security. One crucial layer, operating at the network ingress point before session establishment or policy lookup for certain attacks, is managed through Zone Protection Profiles . These profiles are designed to safeguard the firewall itself and the network segments behind it from common flood attacks, reconnaissance activities, and other packet-level threats that aim to overwhelm resources or gather intelligence.
This article provides an in-depth explanation of Zone Protection Profiles, covering their purpose, different protection types, detailed configuration options, relevant PCNSE exam topics, and illustrative diagrams based on Palo Alto Networks documentation and common knowledge.
Understanding how Zone Protection Profiles work and how to configure them effectively is essential for any network security professional managing Palo Alto Networks firewalls, and it's a key topic for the PCNSE certification.
Core Concepts of Zone Protection
Before diving into the specifics, let's clarify some fundamental concepts:
- Ingress Zone Protection: Zone Protection Profiles are applied to network zones (e.g., Untrust, DMZ, Trust) and scrutinize traffic entering the firewall through interfaces belonging to that zone. They do not inspect traffic leaving a zone. [1]
- Pre-Session / Early Packet Inspection: Many Zone Protection checks, particularly for floods and packet-based attacks, occur very early in the packet processing flow, before a full session is established and often before Security Policy lookup. This allows the firewall to discard malicious traffic efficiently without consuming significant resources. [1] Reconnaissance protection typically monitors connection patterns over time.
- Resource Protection: A primary goal is to protect the firewall's control plane and data plane resources from being exhausted by DoS (Denial of Service) attacks like SYN floods. [1]
- Zone Types: Zone Protection Profiles can be applied to Layer 3, Layer 2, Virtual Wire, and Tap zones. Tunnel zones do not support Zone Protection Profiles directly; protection should be applied to the zone where the tunnel terminates. [1]
- Stateful Nature (Implicit): While some checks are purely packet-based, flood and reconnaissance protection mechanisms inherently track connection rates and patterns over time, implying stateful monitoring at the zone level.
- No Subscription Required: Zone Protection Profile functionality is part of the base PAN-OS software and does not require a separate subscription license. [1]
Zone Protection Profiles offer three main categories of defense: Flood Protection, Reconnaissance Protection, and Packet-Based Attack Protection.
Protection Type: Flood Protection
Flood protection defends against attacks that attempt to overwhelm network resources by sending a high volume of specific types of packets. Zone Protection Profiles monitor the rate of incoming connections or packets per second (CPS/PPS) for various protocols. [1, 2]
Common Flood Protection Settings
For each flood type (SYN, UDP, ICMP, Other IP), you configure thresholds:
- Alarm Rate (Optional): The CPS/PPS rate at which the firewall generates a system log alert indicating a potential flood, but takes no mitigation action yet. [2]
- Activate Rate: The CPS/PPS rate at which the firewall starts taking defensive action (SYN Cookies or Random Early Drop). [2]
- Maximum Rate: The maximum CPS/PPS rate the firewall will allow for this protocol into the zone. Packets exceeding this rate are dropped. [2]
Flood Types and Actions
-
TCP SYN Flood:
Protects against attackers sending numerous SYN packets without completing the TCP handshake, exhausting server resources. [2]
-
Action:
- SYN Cookies (Recommended): When the Activate Rate is exceeded, the firewall acts as a proxy. It responds to the client SYN with a SYN-ACK containing a cryptographic "cookie". It doesn't create a session or forward the SYN to the server yet. Only when the client responds with a valid ACK (containing the cookie) does the firewall verify the cookie, establish the session, and forward the connection to the real server. This validates the client source is legitimate without consuming state table entries during the flood. [2, 4]
- Random Early Drop (RED): A simpler method where the firewall starts randomly dropping incoming SYN packets once the Activate Rate is hit. Less sophisticated than SYN Cookies. [2]
- Block Duration: How long (in seconds) the SYN Cookie or RED mechanism remains active after the flood starts. Default is often 0 (active as long as rate exceeds threshold). [2]
SYN Cookies is a very important PCNSE topic. Understand how it works: Firewall intercepts SYN, sends SYN-ACK cookie, waits for ACK, verifies cookie, then forwards to server. This protects the firewall and server session tables during a flood. -
Action:
-
UDP Flood:
Protects against high volumes of UDP packets targeting specific services or causing general network saturation. [2]
- Action: Random Early Drop (RED). Drops UDP packets exceeding the Maximum Rate. [2]
-
ICMP Flood:
Protects against high volumes of ICMP packets (e.g., Ping floods). [2]
- Action: Random Early Drop (RED). Drops ICMP packets exceeding the Maximum Rate. [2]
-
Other IP Flood:
Protects against high volumes of non-TCP/UDP/ICMP IP packets (based on IP protocol number). [2]
- Action: Random Early Drop (RED). Drops packets exceeding the Maximum Rate. [2]
Protection Type: Reconnaissance Protection
Reconnaissance protection detects and blocks attempts by attackers to scan the network to identify active hosts, open ports, and running services. These scans are often precursors to targeted attacks. [1, 3]
Reconnaissance Types and Settings
-
TCP Port Scan:
Detects attempts to scan multiple TCP ports on one or more destination hosts from a single source IP address within a specified time interval. [3]
- Configuration: Define the Interval (seconds) and Threshold (number of destination ports scanned from one source). Action (`alert` or `block`) is triggered if the threshold is exceeded within the interval.
-
UDP Port Scan:
Detects attempts to scan multiple UDP ports on one or more destination hosts from a single source IP address within a specified time interval. [3]
- Configuration: Similar to TCP Port Scan: Define Interval and Threshold . Action (`alert` or `block`).
-
Host Sweep:
Detects attempts by a single source IP to probe multiple destination IP addresses within the zone using ICMP Echo Requests (pings) or TCP/UDP probes to discover live hosts. [3]
- Configuration: Define Interval and Threshold (number of destination IPs probed from one source). Action (`alert` or `block`).
Common Settings for Reconnaissance
- Interval (seconds): The time window over which the firewall counts scan events from a single source. [3]
- Threshold (events): The number of unique destination ports (for port scans) or destination hosts (for host sweeps) probed from a single source within the Interval to trigger an action. [3]
-
Action:
- `alert`: Log the detected reconnaissance activity but allow the traffic.
- `block`: Log the activity AND block subsequent traffic from the source IP address for a specified duration. [3]
- Block Duration (seconds): If the action is set to `block`, this specifies how long traffic from the offending source IP address will be blocked. (Default can vary, e.g., 3600 seconds). [3]
Protection Type: Packet-Based Attack Protection
This category provides defense against various attacks that involve malformed or non-standard IP, TCP, ICMP, or UDP packets. These are often designed to bypass security devices, cause instability, or exploit specific protocol handling weaknesses. These checks are typically performed very early, before session creation. [1, 5]
IP Drop Options
- Spoofed IP address: Drops packets where the source IP address matches the destination IP address (Land Attack). [5]
- Packet with Bad Inner/Outer IP Checksum: Drops packets with invalid IP header checksums.
- Source address is IP broadcast address: Drops packets originating from a broadcast address.
- Source address is IP multicast address: Drops packets originating from a multicast address.
- Destination address is IP broadcast address: Drops packets sent to a broadcast address (unless explicitly allowed, e.g., for DHCP).
- Strict IP Address Check: Drops packets if the source IP is invalid (e.g., 0.0.0.0, loopback, multicast, broadcast). [5]
- Malformed IP header: Drops packets with incorrectly formatted IP headers.
- IP options in header: Drops packets containing IP options (often used for reconnaissance or exploits).
- Strict Source Routing / Loose Source Routing: Drops packets using deprecated source routing options. [5]
- Unknown IP Protocol: Drops packets with an unrecognized IP protocol number in the header.
- IP fragment: Drops all fragmented IP packets. Use with caution, as fragmentation can be legitimate. [5]
- Non-Syn-TCP Allow TCP Timestamp: (Related to TCP timestamp handling with non-SYN packets, more nuanced).
TCP Drop Options
- TCP SYN with data: Drops SYN packets that contain data payload (non-standard). [5]
- TCP SYNACK with data: Drops SYN-ACK packets containing data (non-standard).
- TCP Header length check: Drops packets where the TCP header length field is invalid.
- TCP port is zero: Drops packets with source or destination TCP port 0.
- TCP SYN FIN: Drops packets with both SYN and FIN flags set (invalid combination).
- TCP FIN with data: Drops FIN packets containing data (non-standard).
- TCP fragment - deny session: Drops TCP fragments.
- Remove TCP Timestamp: Strips the TCP timestamp option from packets.
ICMP Drop Options
- ICMP fragment: Drops fragmented ICMP packets. [5]
- ICMP with large packet size: Drops ICMP packets exceeding a certain size (e.g., >1024 bytes) to prevent Ping of Death variants.
- ICMP Ping ID is zero: Drops ICMP Echo Requests with an ID of 0 (sometimes used in older scan tools). [5]
- ICMP Need Fragmentation with invalid MTU size: Drops ICMP "Destination Unreachable - Fragmentation Needed" messages with an invalid MTU value.
UDP Drop Options
- UDP port is zero: Drops UDP packets with source or destination port 0.
- UDP checksum is zero: Drops UDP packets with a checksum value of zero (often indicates error or manipulation, though technically allowed by RFC under specific conditions for IPv4).
Each of these packet-based checks can be enabled individually within the Zone Protection Profile to tailor the defense against specific perceived threats.
Configuration Steps
Configuring Zone Protection involves two main steps:
-
Create the Zone Protection Profile:
- Navigate to Network > Network Profiles > Zone Protection .
- Click Add to create a new profile.
- Give the profile a descriptive name (e.g., `zp_untrust`, `zp_dmz`).
- Configure the desired settings under the Flood Protection , Reconnaissance Protection , and Packet Based Attack Protection tabs. Select the specific flood types, recon methods, or packet anomalies you want to protect against and define their thresholds and actions. [1]
- Click OK to save the profile.
-
Apply the Profile to an Ingress Zone:
- Navigate to Network > Zones .
- Select the zone you want to protect (e.g., the `untrust` zone where external traffic arrives).
- In the zone configuration window, select the Zone Protection Profile you created from the Zone Protection Profile dropdown list. [1]
- Ensure the zone Type (L3, L2, VWire, Tap) is compatible.
- Click OK to apply the profile to the zone.
- Commit the changes to the firewall.
Careful planning is needed to determine appropriate thresholds and which protections are necessary for each zone based on its exposure and the resources within it.
PCNSE Focus & Key Considerations
For the PCNSE exam and practical application, keep these points in mind:
- Ingress Zone Application: Zone protection is always applied to the zone where traffic *enters* the firewall. Understand how traffic flows between zones to determine which profile applies. [1]
- Order of Operations: Packet-based checks and flood mitigation actions (like dropping packets or sending SYN Cookies) happen very early, often *before* Security Policy evaluation for the affected packets. Reconnaissance blocking also affects future traffic from the source before policy lookup. This is crucial for troubleshooting why traffic might be dropped without hitting a Security Policy rule. [1]
- SYN Cookies: Understand the mechanism and its benefit – validating clients during a SYN flood without consuming firewall/server session resources. Know it's the default action for TCP SYN Flood protection. [2, 4]
- Threshold Tuning: Recognize the importance of setting appropriate Activate and Maximum thresholds based on network baselines to avoid blocking legitimate traffic or rendering protection useless. Defaults exist but may need adjustment. [2]
- Reconnaissance Blocking: Know the `block` action includes a configurable block duration for the source IP. Understand the difference between port scans and host sweeps. [3]
- Packet-Based Protections: Be familiar with key options like Spoofed IP, Strict IP check, IP options, Fragments, and TCP SYN with data, as these relate to common attack or evasion techniques. [5]
-
Logging and Monitoring:
Know where to look for evidence of Zone Protection actions:
- Flood/Packet/Recon Drops/Alerts: Often found in the Threat Logs with Threat IDs related to network attacks (e.g., Flood, Scan subtypes). [7]
- Threshold Exceeded Alarms: Check the System Logs .
- Counters: Use CLI commands like `show counter global filter aspect zone` or `show counter global filter packet-filter yes delta yes` to view statistics related to zone protection drops and actions. [7]
- Licensing: Zone Protection is a core feature; no specific subscription license is required. [1]
- Stateful Inspection Bypass: Because some ZP actions occur before session setup, they can protect against attacks targeting the session table itself.
PCNSE Scenario Example
Scenario: A firewall administrator observes high CPU utilization and slow response times for servers in the DMZ during certain periods. Threat logs show numerous entries for "TCP SYN Flood" originating from various external IPs, associated with the 'Untrust' zone profile. However, no Security Policy rules seem to be explicitly blocking this traffic.
Analysis: This points directly to the Zone Protection Profile applied to the 'Untrust' (ingress) zone triggering its TCP SYN Flood protection. If SYN Cookies are enabled (default), the firewall is handling the flood by intercepting SYNs, which protects the DMZ servers' session tables but still consumes firewall resources (hence the high CPU). If only RED was enabled or thresholds were extremely high, the servers might still be overwhelmed.
Troubleshooting/Solution: 1. Verify the Zone Protection Profile settings applied to the 'Untrust' zone, specifically the TCP SYN Flood thresholds (Activate, Maximum) and action (confirm SYN Cookies is active). 2. Check Threat Logs for details on the flood events. 3. Monitor `show counter global filter aspect zone` or similar CLI commands to see the rate of SYN Cookies being issued or packets dropped by the flood protection mechanism. 4. Consider adjusting thresholds if they are too sensitive or too high. Ensure the action is SYN Cookies for optimal server protection during a flood. Investigate upstream mitigation possibilities if floods are persistent and overwhelming.
Illustrations: Zone Protection Processing Flowchart
This simplified flowchart shows the decision process when a packet enters a protected zone:
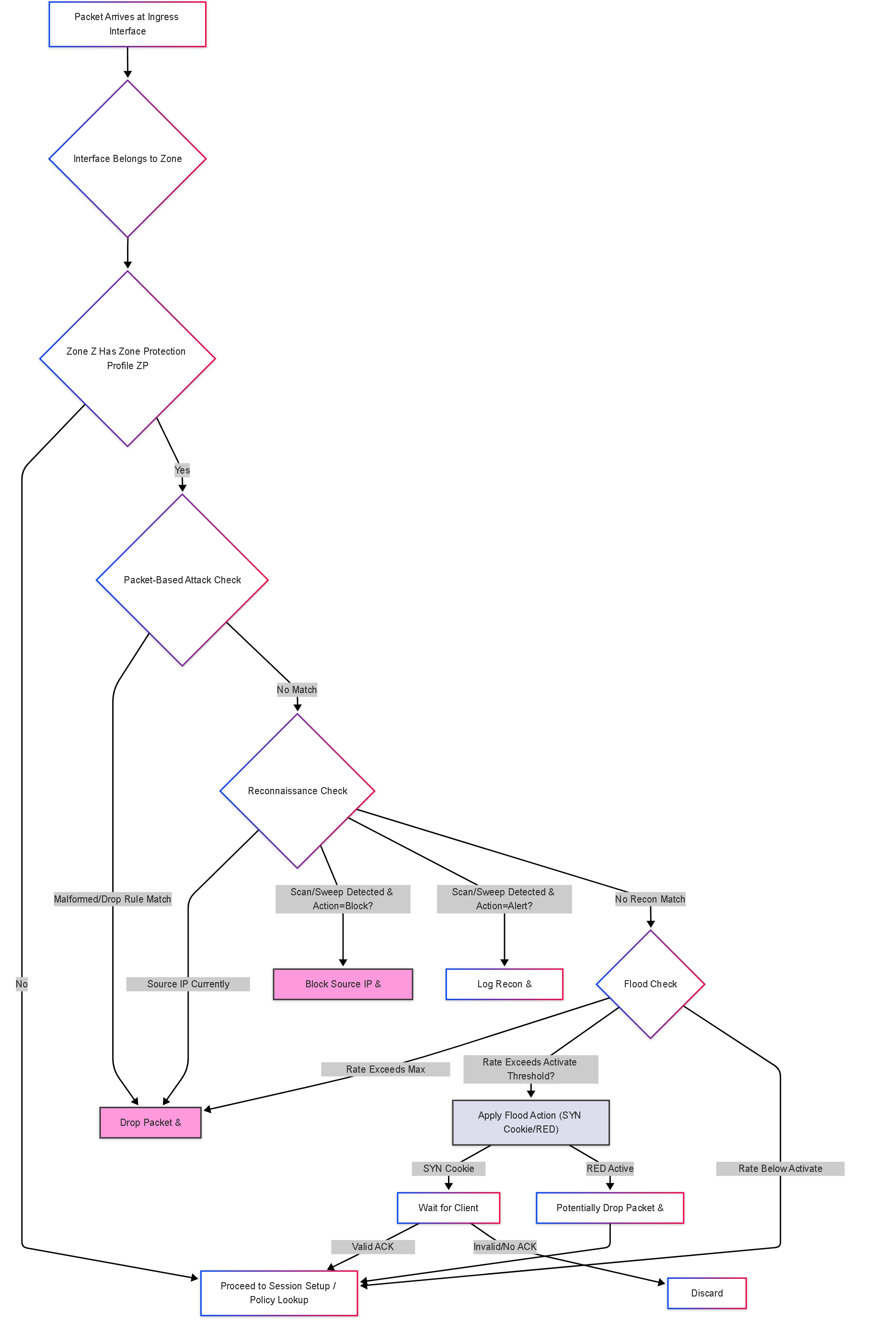
Simplified Zone Protection decision flow. Checks happen sequentially (Packet -> Recon -> Flood), and actions like drops or SYN Cookies can prevent the packet from reaching session setup.
Illustrations: Conceptual Relationship Graph
This graph shows the relationship between zones, profiles, and protection types:
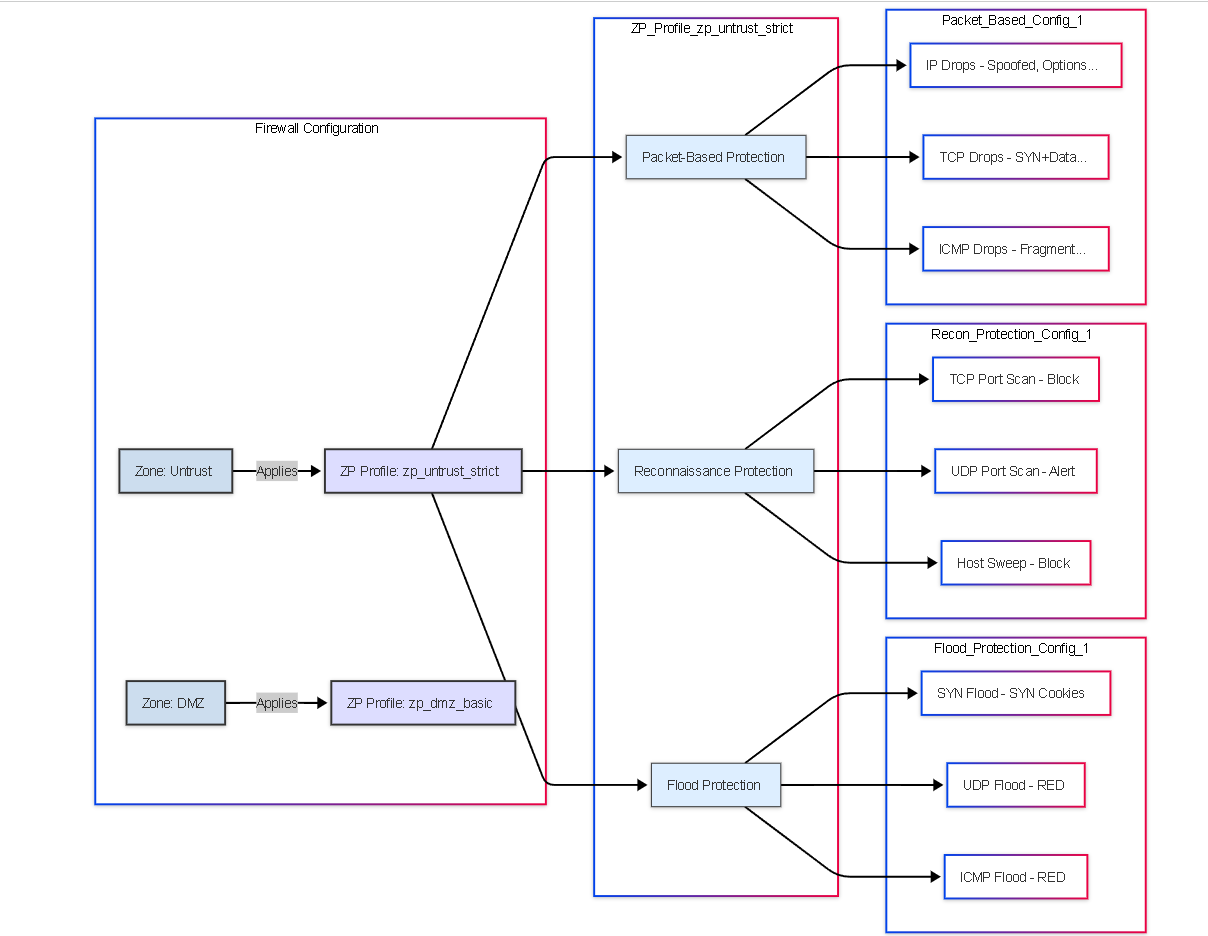
Conceptual graph showing Zones linked to Zone Protection Profiles, which contain configurations for Flood, Reconnaissance, and Packet-Based protection types.
Illustrations: Zone Protection Sequence Diagram (SYN Flood Example)
This sequence diagram illustrates the SYN Cookie mechanism during a flood:
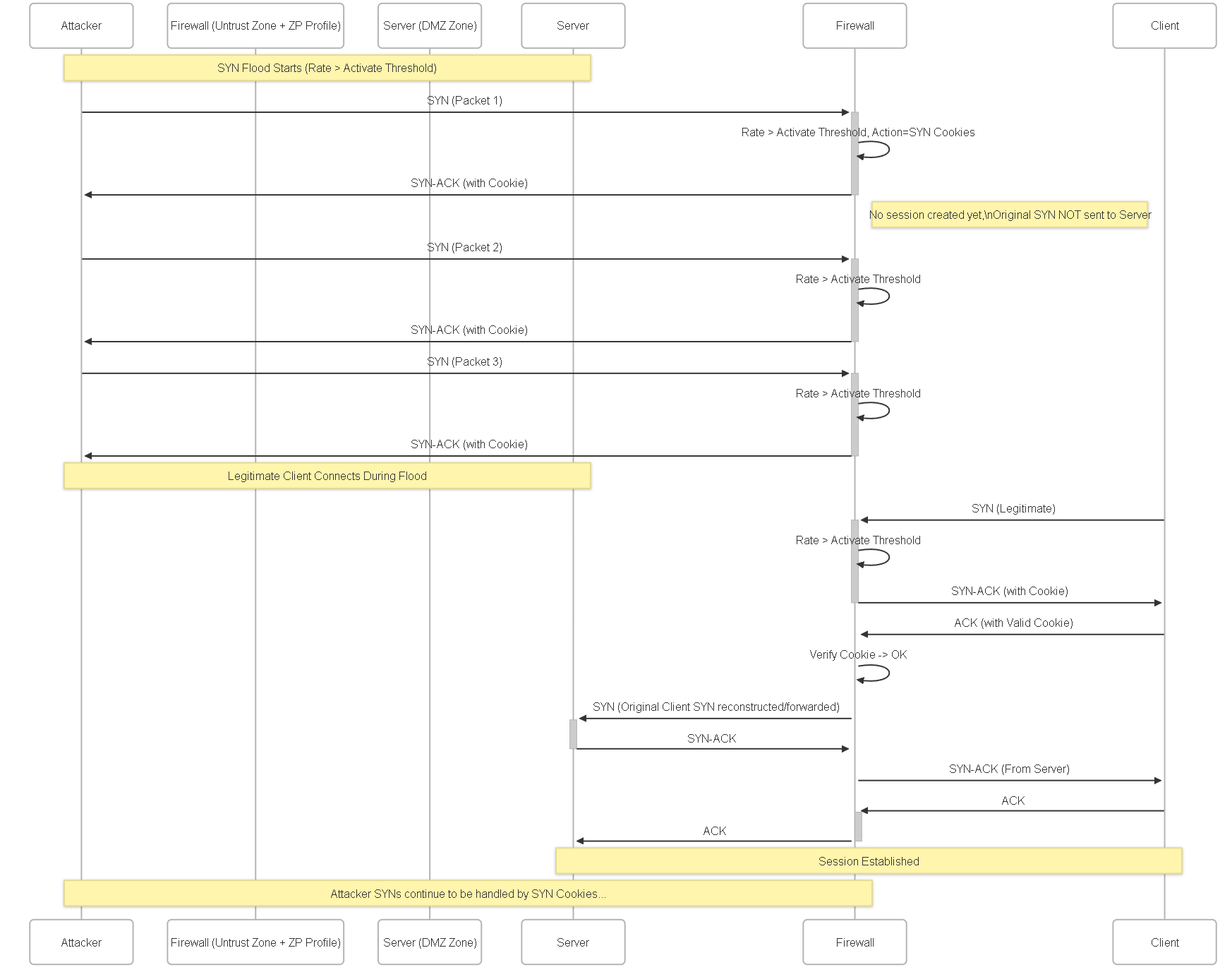
Sequence showing how the firewall intercepts SYNs during a flood, responds with SYN-ACK cookies, and only forwards the connection to the server if a valid ACK with the cookie is received from the client.
Illustrations: Flood Protection State Diagram Example
This state diagram shows possible states for flood protection (e.g., SYN Flood):
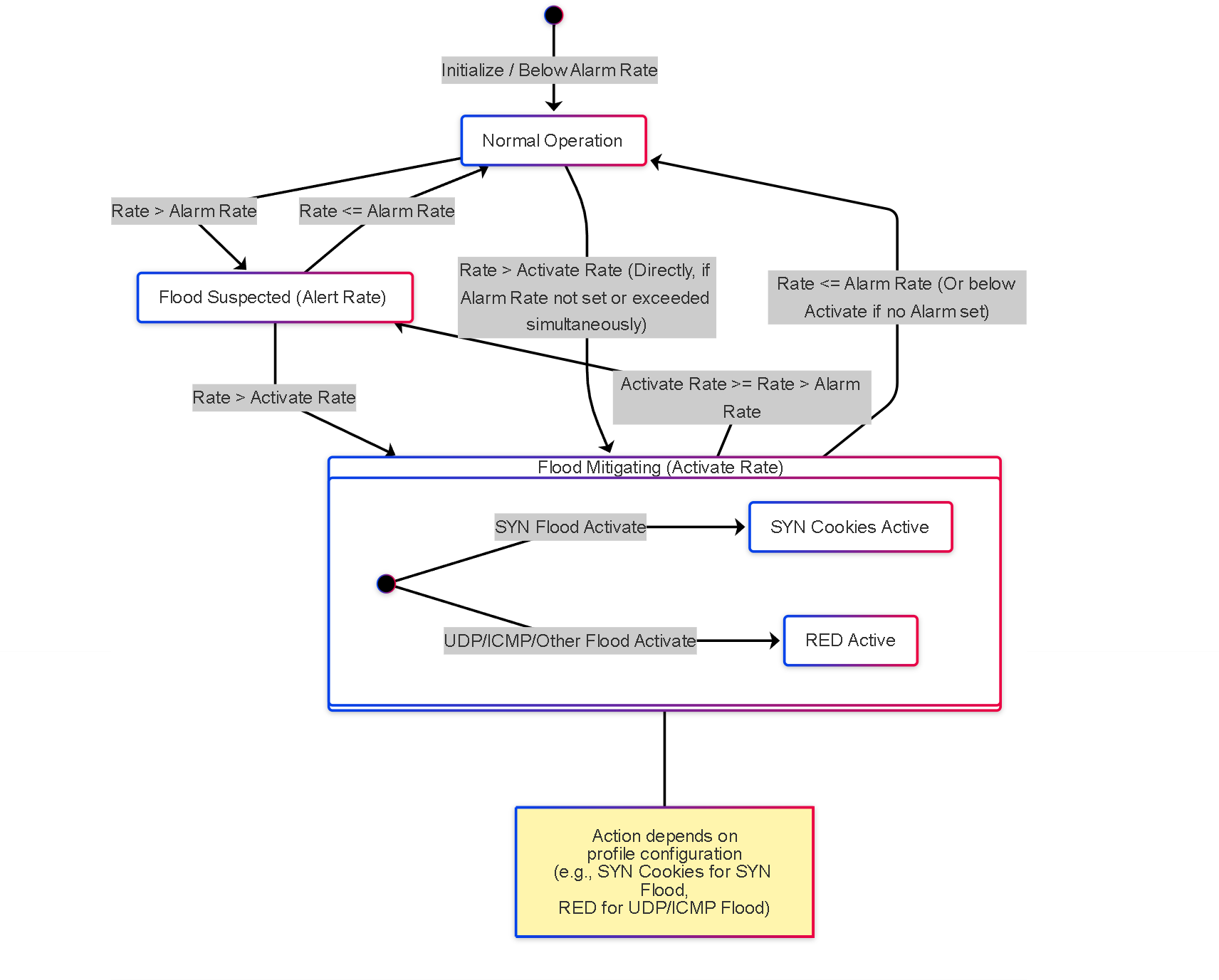 Simplified state transitions for flood protection based on configured rate thresholds (Alarm, Activate). The 'Mitigating' state involves actions like SYN Cookies or RED.
Simplified state transitions for flood protection based on configured rate thresholds (Alarm, Activate). The 'Mitigating' state involves actions like SYN Cookies or RED.
PCNSE Prep Quiz: Zone Protection Profiles
Test your understanding of Palo Alto Networks Zone Protection Profiles.