Comprehensive Guide to Palo Alto Networks Zero Touch Provisioning (ZTP)
Zero Touch Provisioning (ZTP) is a powerful feature offered by Palo Alto Networks that streamlines the deployment of new firewalls, particularly in large-scale or remote environments. It allows a brand new, unconfigured firewall shipped directly to its destination site to automatically connect to the network, download its configuration, update its software, and register itself with a central management system (Panorama) with minimal to no manual intervention required at the remote site.
This automated onboarding process significantly reduces deployment time, minimizes the potential for human error during initial setup, ensures configuration consistency, and lowers operational costs by eliminating the need for skilled technicians to be physically present at every location.
This article delves into the details of the ZTP workflow, requirements, implementation steps with Panorama, operational commands, troubleshooting tips, best practices, and key concepts relevant for the PCNSE certification.
Benefits of Using ZTP
Implementing ZTP offers several significant advantages, especially for organizations managing numerous firewalls across distributed locations:
- Automated Deployment: The primary benefit is the automation of the initial setup process. Devices arrive at the site, are powered on and connected to the network, and configure themselves automatically.
- Reduced Manual Intervention & Cost: Eliminates the need for specialized network engineers to travel to each remote site for initial configuration, saving time and travel expenses. Less technical staff at the remote site only need to handle physical racking and cabling.
- Consistency & Reduced Errors: Centralized configuration templates pushed via Panorama ensure that all ZTP-deployed devices receive a standardized, pre-approved configuration, drastically reducing inconsistencies and errors associated with manual setup.
- Scalability & Speed: ZTP greatly accelerates the rollout of new firewalls, making it feasible to deploy dozens or hundreds of devices rapidly across multiple branches or locations.
- Simplified Logistics: Firewalls can be shipped directly from the manufacturer or warehouse to the final deployment location without needing pre-staging or configuration at a central IT office.
- Enhanced Security Posture from Day One: Devices can be configured to immediately connect to Panorama, download the latest software/content updates, and apply security policies upon boot-up, ensuring they are secure from the moment they join the network.
How ZTP Works: Workflow Overview
The ZTP process involves a coordinated sequence of steps between the new firewall, the local network infrastructure (DHCP), the Palo Alto Networks cloud services (ZTP Service and Customer Support Portal), and optionally, Panorama.
Here's a breakdown of the typical workflow for Panorama-managed ZTP:
- Device Registration (Pre-Step): Before deployment, the firewall's serial number must be registered in the Palo Alto Networks Customer Support Portal (CSP). This associates the device with the customer's account.
- Panorama Pre-Provisioning (Pre-Step): The administrator adds the firewall's serial number to Panorama and assigns it to the desired Device Group and Template Stack. This prepares Panorama to manage the device once it connects.
- Power On & Boot Up: The unconfigured firewall is physically installed at the remote site, connected to the network (typically via its management port or a designated ZTP interface), and powered on.
- DHCP Request: The firewall, in its factory default state, sends a DHCP request on its management (or designated ZTP) interface to obtain an IP address, default gateway, DNS server information, and potentially ZTP-specific options.
-
Contact ZTP Service:
Using the obtained network settings (especially DNS), the firewall attempts to resolve and connect to the regional Palo Alto Networks ZTP cloud service (e.g.,
ztp.paloaltonetworks.com). - Authentication: The firewall presents its serial number to the ZTP service. The ZTP service verifies the serial number against the CSP registration to authenticate the device and confirm it's eligible for ZTP.
- Retrieve Panorama Info: Once authenticated, the ZTP service, having looked up the device in the CSP, provides the firewall with the IP address or FQDN of the Panorama server designated to manage it (as configured during pre-provisioning).
- Connect to Panorama: The firewall initiates a secure connection (HTTPS) to the specified Panorama server.
- Configuration/Software Download: Panorama recognizes the connecting firewall (based on its serial number added earlier). It pushes the appropriate PAN-OS software version (if an upgrade/downgrade is needed based on the template) and the configuration associated with the assigned Device Group and Template Stack down to the firewall.
- Apply Configuration & Reboot (If Needed): The firewall installs the software update (if applicable, requiring a reboot) and applies the received configuration.
- Connect & Managed State: After applying the configuration (and potentially rebooting), the firewall establishes a persistent connection to Panorama and enters a managed state, ready for operation and ongoing administration via Panorama.
How ZTP Works: Prerequisites
For ZTP to function correctly, several prerequisites must be met both in the central management environment and at the remote deployment site:
Central / Pre-Deployment Requirements:
- Panorama Instance: A functioning Panorama instance (Physical, Virtual, or Cloud-based) is required to act as the configuration source and central manager.
- Device Registration in CSP: The serial number of the firewall(s) intended for ZTP must be registered under the correct account in the Palo Alto Networks Customer Support Portal (CSP).
-
Panorama Device Pre-Provisioning:
The firewall serial number(s) must be added to Panorama (
Panorama > Managed Devicesor ZTP configuration section) and associated with the target Device Group and Template Stack. - Panorama Connectivity: Panorama must be reachable from the internet (or the remote site's network) by the ZTP firewall during the onboarding process. Ensure necessary firewall rules allow inbound HTTPS (typically TCP/443 and potentially others for management) from the ZTP firewall's expected source IP range to Panorama.
- Licensing: Ensure appropriate Panorama licenses are available for managing the new devices.
- PAN-OS Version Compatibility: Ensure the target PAN-OS version defined in the Panorama template is compatible with the firewall hardware model being deployed.
Remote Site Requirements:
-
DHCP Server:
A DHCP server must be available on the network segment where the firewall's management (or ZTP-designated) interface will be connected. This server must provide at minimum:
- IP Address
- Subnet Mask
- Default Gateway
- DNS Server Address(es) (crucial for resolving ZTP service and Panorama FQDNs)
-
Internet Connectivity:
The firewall needs internet access upon receiving its DHCP lease to reach:
-
Palo Alto Networks ZTP Service (
ztp.paloaltonetworks.comor regional equivalent) - Palo Alto Networks Update Servers (for potential PAN-OS downloads if directed by Panorama)
- The managing Panorama instance (IP or FQDN)
-
Palo Alto Networks ZTP Service (
-
Physical Connection:
The firewall's management interface (usually
MGT) or a designated ZTP interface must be connected to the network segment served by the DHCP server. - Factory Default State: The firewall should ideally be in its factory default configuration state for ZTP to initiate correctly. (Though mechanisms exist to re-trigger ZTP).
Implementation: Panorama Setup for ZTP
Setting up Panorama to support ZTP involves registering the devices and ensuring Panorama is prepared to manage them once they connect.
- Register Devices in CSP: Log in to the Palo Alto Networks Customer Support Portal (CSP). Navigate to Assets > Device Registration (or similar path). Register the firewall's serial number if it's not already associated with your account. This step links the physical hardware to your organization.
-
Add Firewall Serial Number to Panorama:
- Log in to the Panorama Web UI.
-
Navigate to
Panorama > Managed Devices > Summary. - Click Add .
- Enter the firewall's Serial Number accurately.
- (Optional but recommended for ZTP) Check the box indicating the device will connect via ZTP or select the ZTP device type if applicable in your Panorama version.
- Click OK .
-
Assign to Device Group & Template Stack:
- After adding the serial number, it will appear in the device list, likely in an unassigned or default group initially.
-
Navigate to
Panorama > Device Groups, select the target Device Group where the ZTP firewall should reside, go to the Devices tab, and add the newly added serial number. -
Navigate to
Panorama > Templates, select the target Template Stack containing the base configuration and PAN-OS version settings for the ZTP firewall, go to the Devices tab, and add the newly added serial number. - Ensure the assigned Template Stack specifies the desired target PAN-OS version and includes essential network settings (like Panorama connectivity details if not using defaults) and base policies.
- Commit and Push (Optional Pre-Push): While not strictly required before the device connects, committing changes to Panorama (especially template/device group assignments) ensures Panorama is ready. A push isn't needed until the device actually connects and registers.
- Verify Panorama Reachability: Ensure the Panorama management IP address or FQDN is resolvable via public DNS (if firewalls are connecting over the internet) and that firewall rules allow the ZTP firewall to connect back to Panorama on the necessary ports (typically HTTPS/TCP 443).
Implementation: Device Onboarding Process
Once the prerequisites and Panorama setup are complete, the physical onboarding of the device at the remote site is straightforward:
- Unpack and Rack: Physically install the firewall at the remote location.
- Connect Management Interface: Connect the firewall's dedicated Management (MGT) port (or the interface designated for ZTP if using a data port, which requires specific bootstrap configurations typically not covered by standard ZTP) to the local network switch segment where the DHCP server is active.
- Power On: Connect the power cable(s) and turn on the firewall.
-
Automatic Process Initiation:
The firewall boots up in its factory default state. Finding no configuration, it automatically attempts to:
- Initiate DHCP client on the MGT interface.
- Obtain IP configuration (IP, Mask, Gateway, DNS) from DHCP.
- Resolve and contact the Palo Alto Networks ZTP service using DNS.
- Authenticate using its serial number.
- Receive Panorama details from the ZTP service.
- Connect securely to Panorama.
- Download software (if needed) and configuration from Panorama.
- Apply configuration and reboot (if necessary).
- Establish persistent management connection to Panorama.
-
Verification (Panorama):
Monitor Panorama (
Panorama > Managed Devices > SummaryandCommit > Task Manager) to see the device connect, register, receive its configuration push, and show up as 'Connected'. - Verification (Device CLI - Optional): Once basic IP connectivity is established via ZTP/DHCP, you could potentially SSH to the management IP (if allowed by initial config/template) and use CLI commands to check status (see Operations section).
Operations: Relevant CLI Commands
While ZTP aims for minimal touch, CLI commands can be useful for verification, troubleshooting, or disabling ZTP post-onboarding.
-
Check ZTP Status:
show ztp statusDisplays the current state of the ZTP process, including whether it's enabled, the current stage, any errors encountered, and the Panorama server it's trying to reach. This is the primary command for checking ZTP progress on the device itself.
-
Show System Info (Serial Number):
show system info | match serialUseful to quickly verify the serial number of the device you are working on, ensuring it matches what's registered in CSP and Panorama.
-
Show DHCP Client Lease Info:
show dhcp client state managementVerifies if the management interface successfully obtained an IP address, gateway, and DNS servers via DHCP.
-
Test Connectivity:
ping host <ip_or_fqdn>ping source <mgt_ip> host <ip_or_fqdn>Test basic network reachability from the firewall's management interface to the DNS server, default gateway, ZTP service FQDN, or Panorama IP/FQDN.
-
Test DNS Resolution:
test dns-proxy dns-resolve fqdn <fqdn> dns-server <dns_server_ip>Verify if the firewall can resolve critical FQDNs (like
ztp.paloaltonetworks.comor the Panorama FQDN) using the DNS server obtained via DHCP. -
Disable ZTP:
request ztp disableThis command is used after successful onboarding to permanently disable the ZTP feature on the firewall. This is necessary before configuring features like High Availability (HA).
-
Force ZTP Retry (Advanced):
debug ztp restart(Use with caution, primarily for troubleshooting specific stalled states under guidance)Restarts the ZTP agent process on the firewall.
-
View ZTP Logs (Advanced):
less mp-log ztp.logProvides detailed logging of the ZTP agent's activities and encountered errors (requires familiarity with PAN-OS logging).
Operations: Monitoring ZTP
Monitoring the ZTP process involves checking both Panorama and potentially the firewall CLI.
Panorama Monitoring:
-
Managed Devices Summary:
Navigate to
Panorama > Managed Devices > Summary. Look for the device serial number. Its status should transition from 'Waiting for device' to 'Connecting', and finally 'Connected'. The 'Management' column should show 'Panorama'. -
ZTP Devices Tab (If available):
Newer Panorama versions may have a dedicated
Panorama > Zero Touch Provisioningsection showing ZTP-specific status and logs. -
Commit Task Manager:
Check
Commit > Tasks(or Task Manager icon) for commit/push jobs targeting the new firewall's Device Group/Template Stack. Look for successful completion messages once the device connects and receives its configuration. -
System Logs:
Check
Monitor > Logs > Systemon Panorama, filtering for the device's serial number, to see registration and connection events.
Firewall CLI Monitoring:
-
show ztp status: As mentioned, this is the primary command on the firewall itself to see the current stage and any errors. -
System Logs:
Use
show log system direction equal backwardto view recent system events on the firewall CLI, which might include ZTP progress or failure messages.
Successful ZTP results in the firewall appearing as 'Connected' in Panorama's managed devices list and receiving its configuration.
Operations: Troubleshooting ZTP Issues
If a firewall fails to complete the ZTP process, follow these troubleshooting steps:
-
Verify Prerequisites (Remote Site):
- Physical Connection: Is the correct interface (usually MGT) plugged into the correct network segment? Check link lights.
- DHCP Server: Is the DHCP server online and functioning? Can other devices on the same segment get a lease?
-
DHCP Lease Details:
Console into the firewall (if possible) or check DHCP server logs. Did the firewall receive an IP, mask, gateway, AND valid DNS server addresses? Use
show dhcp client state managementon the firewall CLI. -
DNS Resolution:
Can the firewall resolve
ztp.paloaltonetworks.comand the Panorama FQDN using the provided DNS servers? Usetest dns-proxy...CLI command. -
Internet/Panorama Reachability:
Can the firewall ping its default gateway? Can it ping public IPs? Use
pingcommand. Are there any upstream firewalls blocking outbound TCP/443 or other necessary ports to the ZTP service or Panorama?
-
Verify Prerequisites (Central / Panorama):
- CSP Registration: Double-check the serial number is correctly registered in the CSP under the correct account.
-
Panorama Pre-Provisioning:
Verify the serial number is added correctly in Panorama (
Panorama > Managed Devices) and assigned to the correct Device Group and Template Stack. - Panorama Reachability: Confirm Panorama's management interface IP/FQDN is correct and reachable from the internet/remote site. Check firewall rules allowing inbound connections to Panorama.
- Template/Software Compatibility: Ensure the PAN-OS version specified in the assigned Template Stack is compatible with the firewall hardware model.
-
Check Firewall ZTP Status:
- Connect to the firewall console port.
- Log in using default credentials (admin/admin initially).
-
Run
show ztp status. Note the current stage and any specific error messages displayed. This often points directly to the problem (e.g., "Failed to resolve ZTP server", "Failed to connect to Panorama").
-
Check Panorama Logs:
-
Review System logs on Panorama (
Monitor > Logs > System) filtering for the device serial number. Look for connection attempts or registration errors. -
Check the ZTP logs under
Panorama > Zero Touch Provisioningif available.
-
Review System logs on Panorama (
-
Review ZTP Logs on Firewall (Advanced):
-
Use
less mp-log ztp.logfor detailed agent logs if basic checks fail.
-
Use
- Factory Reset & Retry: If the device seems stuck or partially configured, consider performing a factory reset and allowing the ZTP process to restart from scratch. Use the CLI command `request system private-data-reset`.
ZTP Best Practices
To ensure smooth and secure ZTP deployments, consider these best practices:
- Use for Scale: ZTP provides the most significant benefits for large-scale deployments with numerous remote sites.
- Robust DHCP/DNS: Ensure reliable DHCP and DNS services at remote locations. Consider DHCP reservations for management IPs if static assignment post-ZTP is desired (though ZTP itself uses dynamic).
- Accurate Registration: Triple-check serial number registration in CSP and addition to Panorama. Typos are a common source of failure.
- Standardized Templates: Develop well-tested, standardized Panorama Templates and Template Stacks for different site types or roles. Include essential base configuration (management access, Panorama settings, basic security rules, content updates schedules).
- Secure Panorama Access: Ensure Panorama is appropriately secured and only accessible from expected source IP ranges if possible. Use FQDNs for Panorama addresses where feasible.
- Test ZTP Process: Before a large rollout, test the entire ZTP process with one or two devices to validate prerequisites, Panorama configuration, and the pushed template.
- Post-Onboarding Verification: Have a process to verify successful onboarding, either via Panorama status checks or remote site confirmation.
-
Disable ZTP After Onboarding:
For security hardening and before configuring HA, disable ZTP on the firewall using
request ztp disableonce it's successfully managed by Panorama. - Plan for Exceptions: Have a fallback plan (e.g., USB provisioning, manual config) for sites where ZTP might not be feasible due to network limitations.
- Documentation: Document the ZTP process, prerequisites, Panorama configuration standards, and troubleshooting steps for your organization.
Illustrations: ZTP Workflow Flowchart
This flowchart outlines the high-level ZTP process:
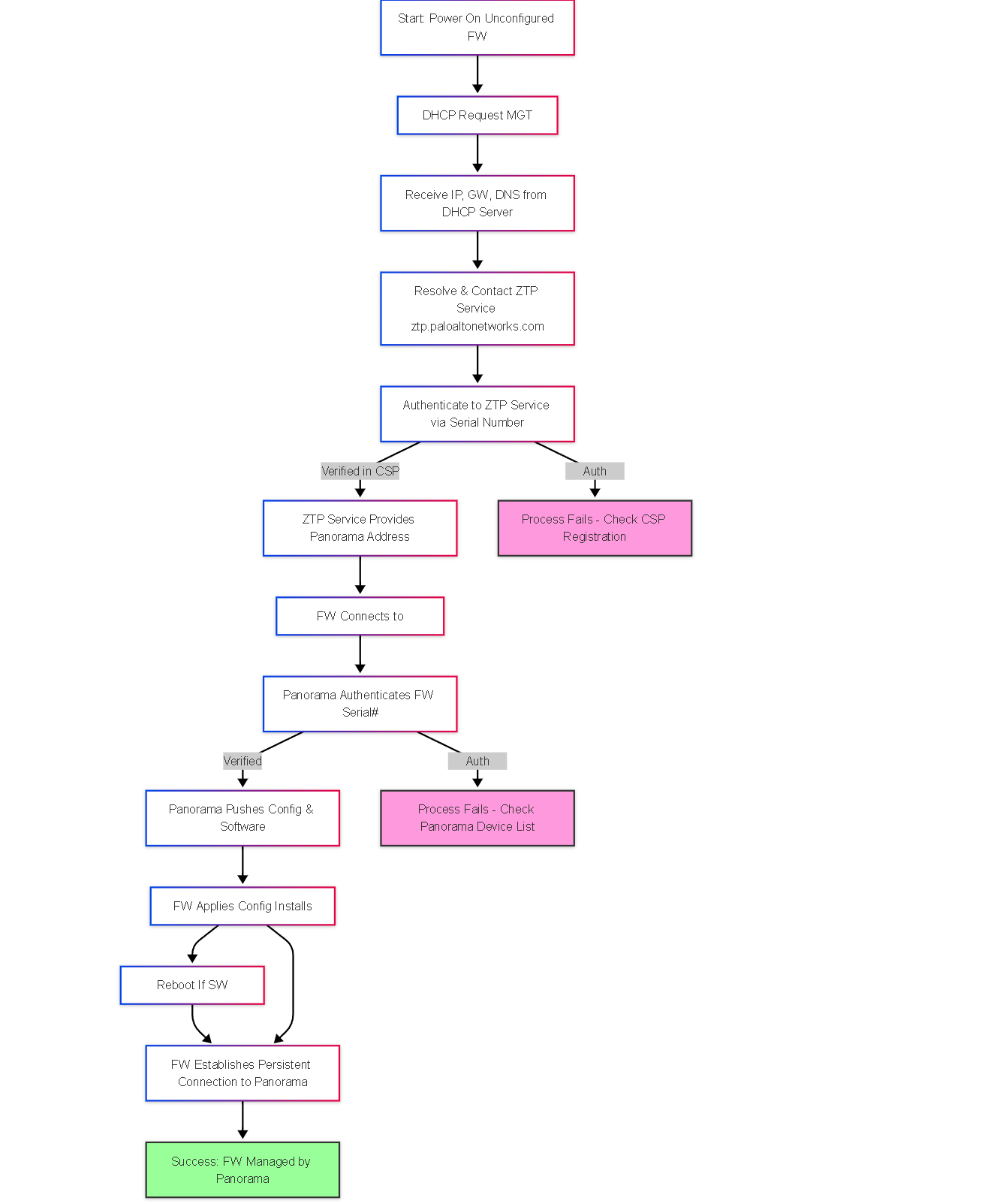
High-level flowchart of the Zero Touch Provisioning process using Panorama.
Illustrations: ZTP Sequence Diagram
This sequence diagram shows the interactions between components:
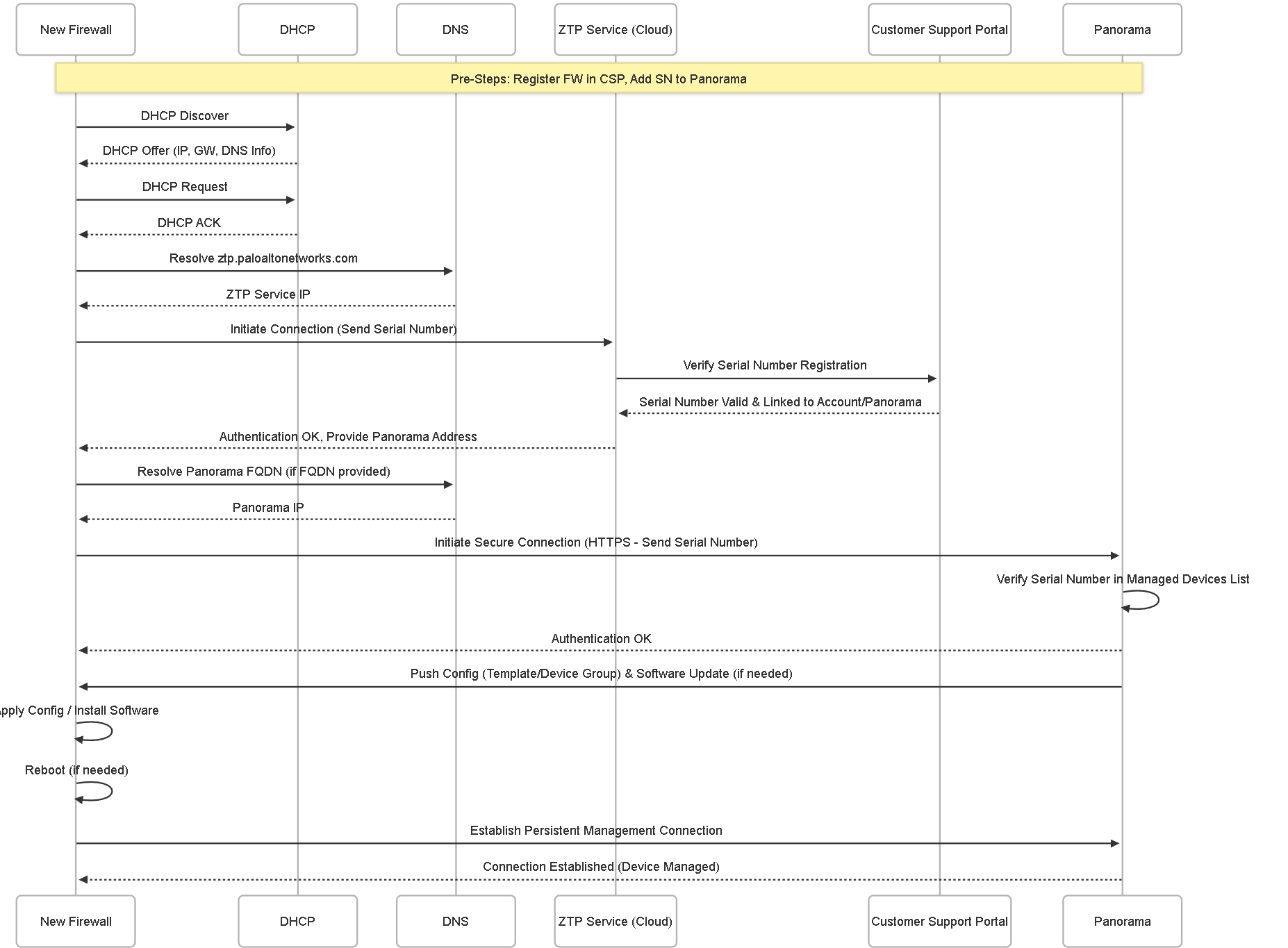
Sequence of interactions during the ZTP onboarding process.
Illustrations: Firewall ZTP State Diagram
This diagram shows the different states a firewall might be in during ZTP:
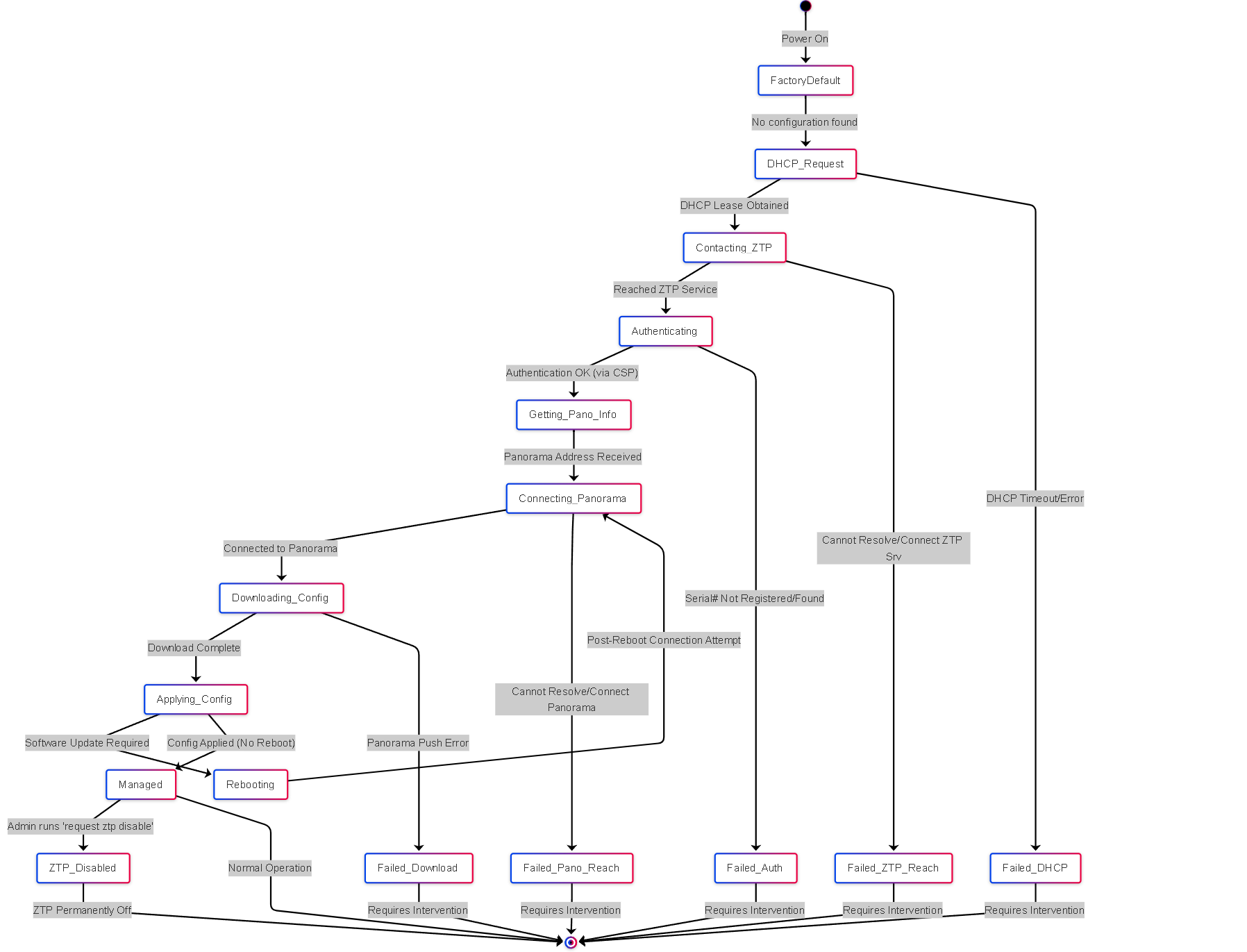
Simplified state transitions for a firewall undergoing the ZTP process, including potential failure states.
Illustrations: ZTP Component Relationship Graph
This graph shows how the different components interact:
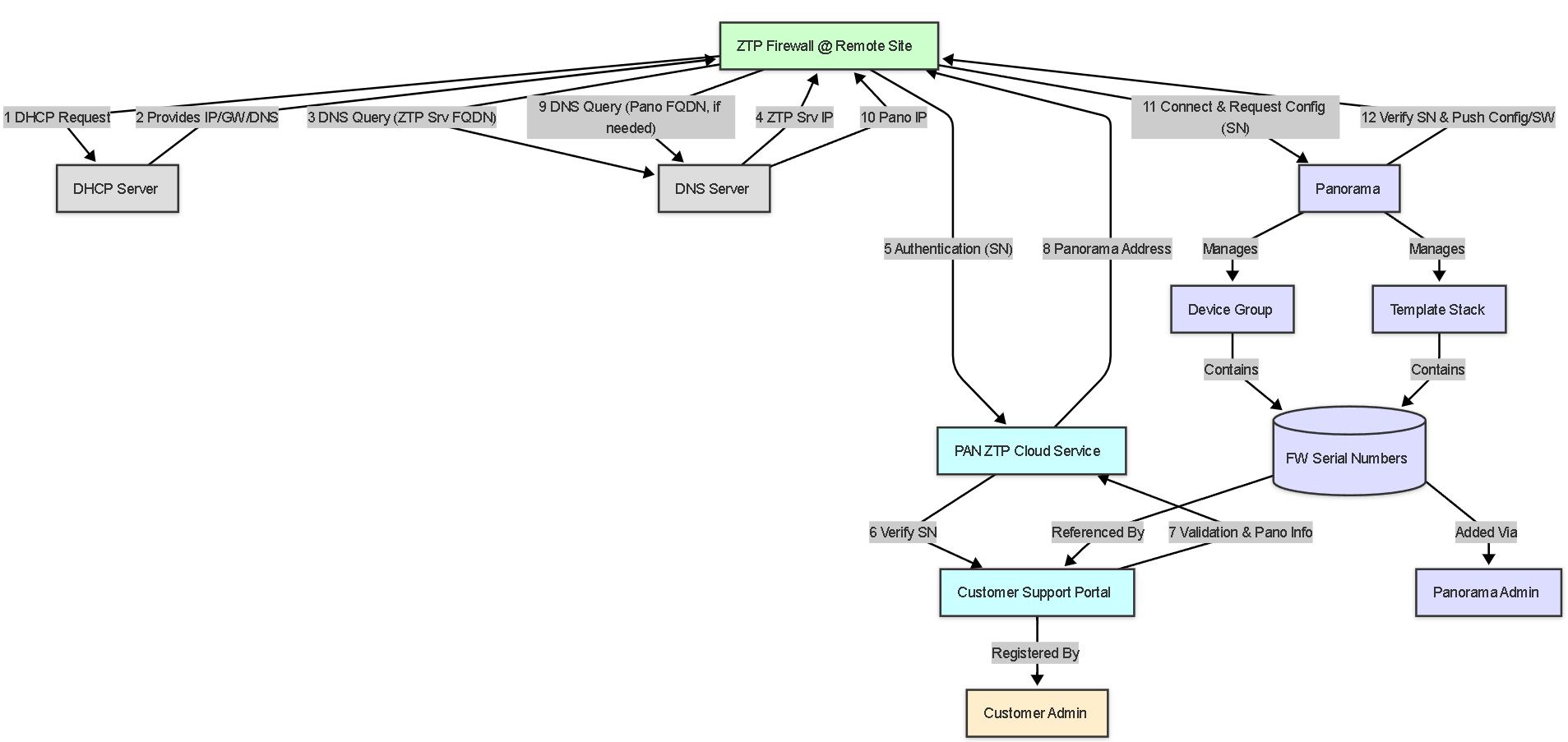
Conceptual graph illustrating the key components involved in ZTP and their interactions.
PCNSE Focus Points
Key ZTP concepts and details relevant for the PCNSE exam:
- Core Purpose: Understand ZTP's goal is automated onboarding of new firewalls, reducing manual effort and ensuring consistency, especially for remote deployments.
- Key Components & Flow: Know the roles of DHCP, DNS, CSP Registration, ZTP Cloud Service, and Panorama in the workflow.
- Prerequisites: Be aware of essential requirements: CSP registration, Panorama pre-provisioning (SN added, assigned DG/TS), DHCP providing DNS at the remote site, and internet/Panorama reachability.
- Initiation: ZTP typically initiates automatically on a factory-default firewall upon boot when connected to a network with DHCP.
- Authentication: Understand that authentication relies on the firewall's serial number being registered in CSP and matching the entry in Panorama.
- Configuration Source: Recognize that Panorama (via assigned Template Stacks and Device Groups) provides the configuration and target PAN-OS version.
- CLI Commands: Know `show ztp status` for checking progress/errors and `request ztp disable` for disabling ZTP post-onboarding.
- HA Limitation: Remember that ZTP must be disabled before configuring High Availability (HA).
- Troubleshooting Basics: Be prepared to identify common failure points like DHCP/DNS issues, incorrect serial number registration/entry in Panorama, or network connectivity blocks.
- Benefits Emphasis: Focus on the operational efficiency, cost savings, consistency, and scalability benefits.
PCNSE Prep Quiz: Zero Touch Provisioning (ZTP)
Test your knowledge of Palo Alto Networks ZTP.