-
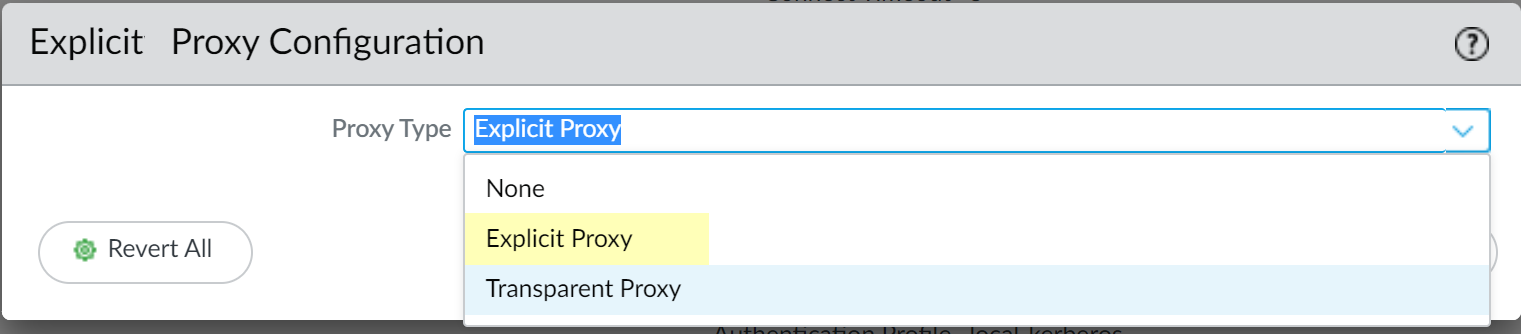
License Activation (Specific Models):
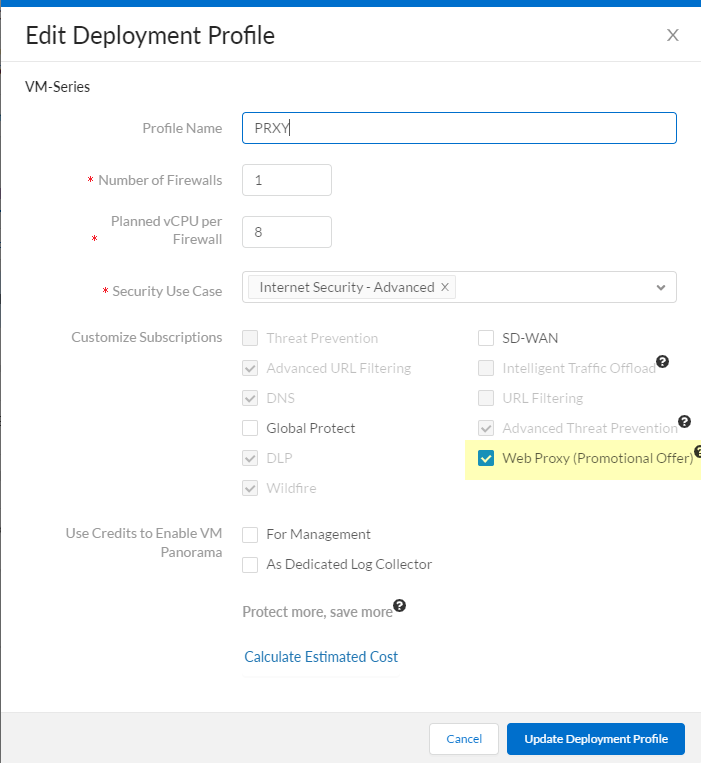
Web proxy functionality requires license activation on PA-1400 Series, PA-3400 Series, and VM-Series firewalls.
- VM-Series Example: Log in to CSP, edit the deployment profile, select Web Proxy (Promotional Offer) or the appropriate license, and update.
-
On the firewall, retrieve license keys (
Device > Licenses). Restart if needed. - PA-1400/PA-3400: Follow standard subscription license activation steps .
-
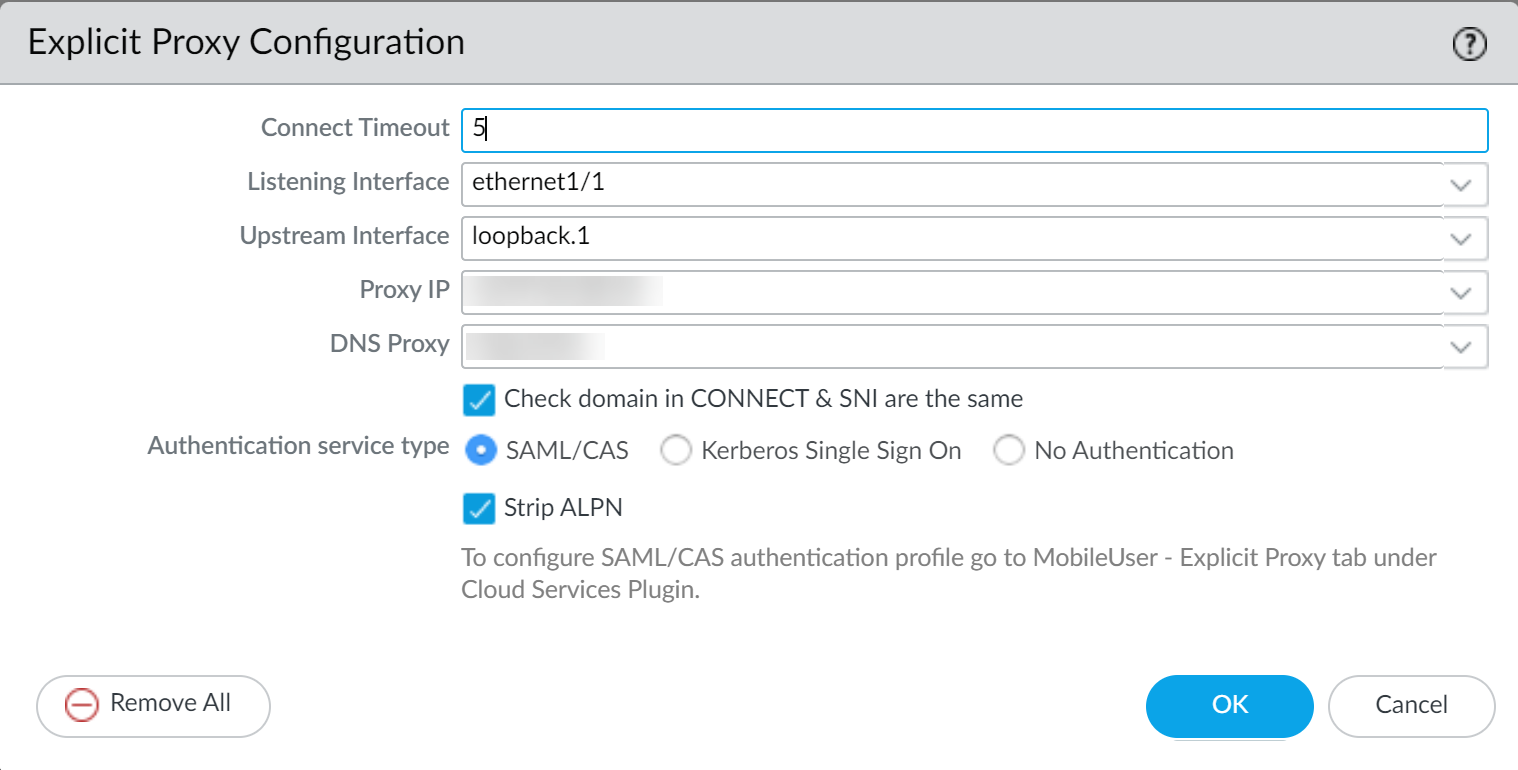
Interfaces and Zones Setup:
Configure necessary interfaces (Layer 3 recommended) and assign them to distinct zones within the same virtual router.
- Client Traffic Interface ("Listening Interface"): The interface where the firewall listens for proxy connections from clients. Note its IP address (this is the Proxy IP clients configure).
- Internet Traffic Interface ("Upstream Interface"): The interface the firewall uses to send proxied traffic out to the internet.
- Proxy Loopback Interface (Optional but common): Often used as the logical "Upstream Interface" configured in the proxy settings to route traffic internally before it exits via the physical internet interface.
-
DNS Proxy Setup:
The explicit proxy often needs to perform DNS lookups.
-
Configure a
DNS Proxy Object
(
Network > DNS Proxy). -
Configure a
DNS Server Profile
(
Device > Server Profiles > DNS) with reliable Primary and Secondary DNS servers. - Associate the DNS Proxy object with the appropriate interface (often the client-facing listening interface or potentially a loopback, depending on design).
Reliable DNS resolution for the firewall is required.
-
Configure a
DNS Proxy Object
(
-
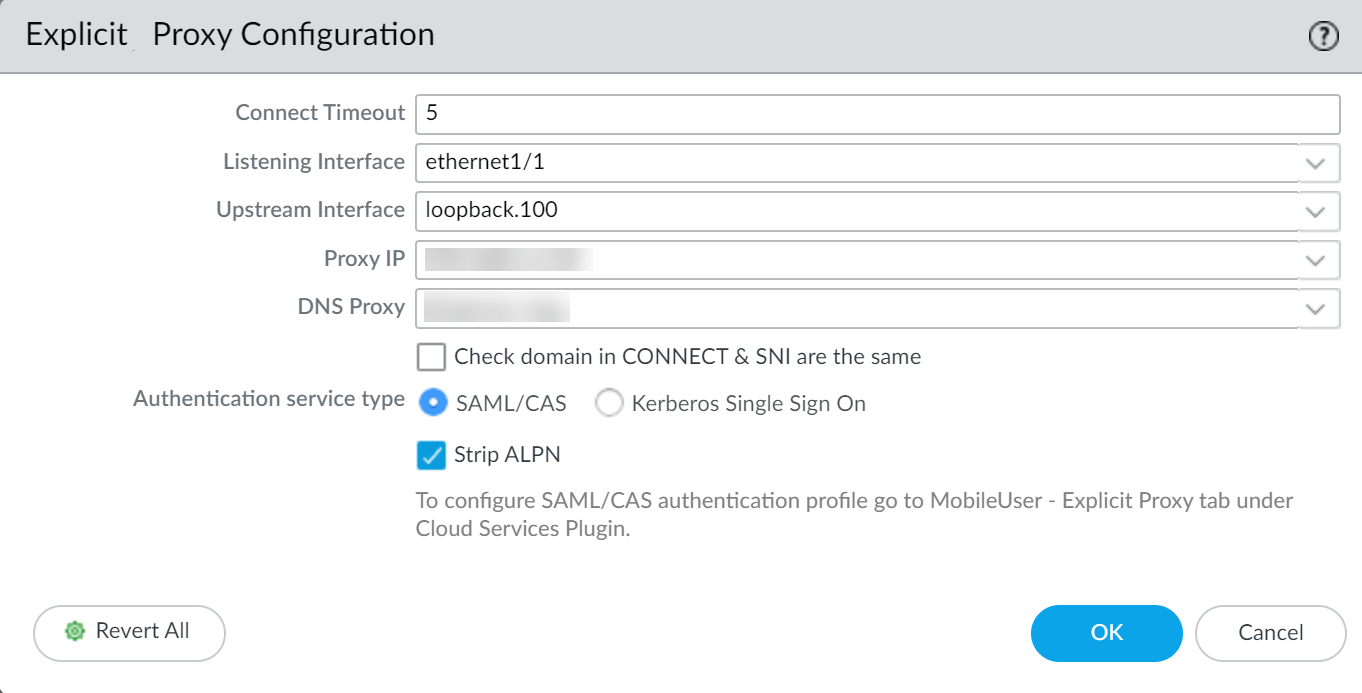
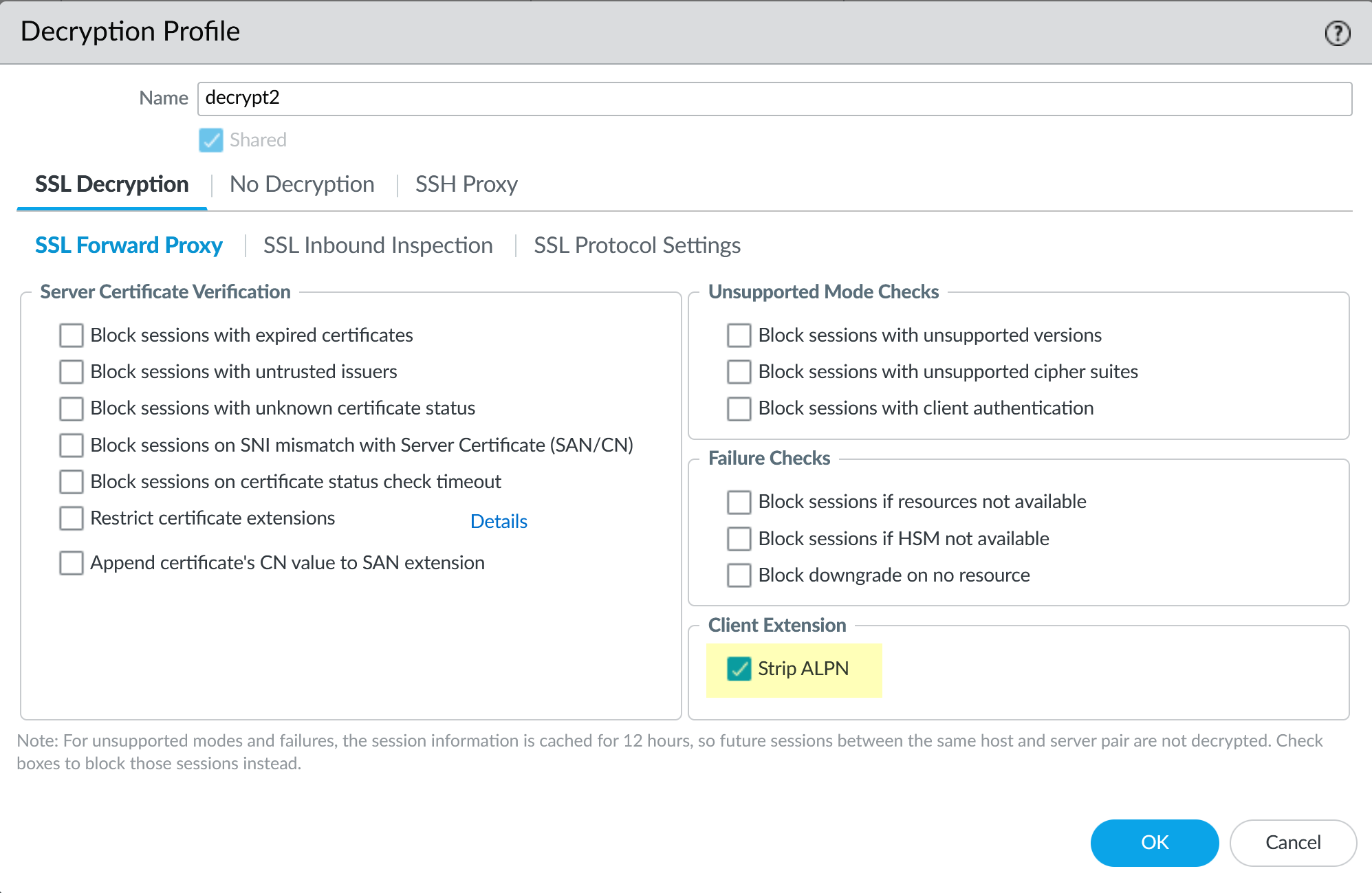
Certificate Setup (for Decryption):
If you plan to decrypt SSL/TLS traffic passing through the proxy (highly recommended for security), configure SSL Forward Proxy. This involves setting up a Forward Trust CA (self-signed or enterprise subordinate) and deploying its public certificate to clients.
(See Create a Self-Signed Root CA Certificate or relevant Enterprise CA documentation).
-
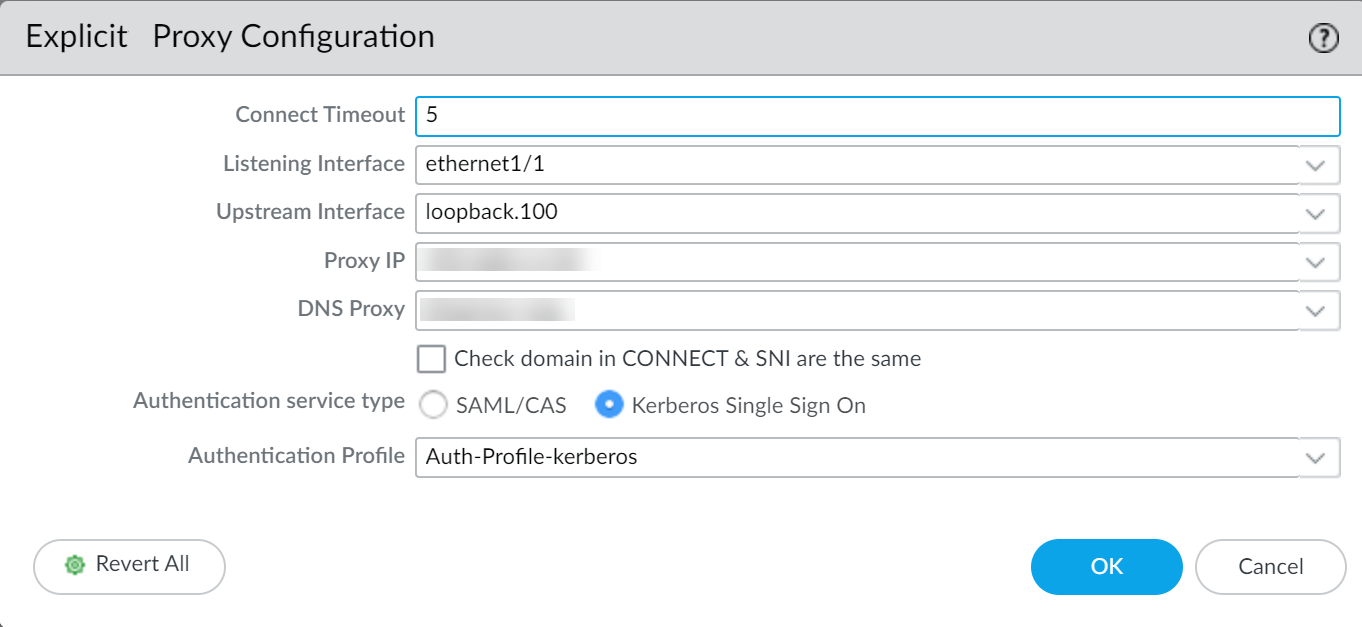
Authentication Method Prerequisites:
Complete the specific setup steps for your chosen authentication method (Kerberos SPN/keytab, SAML IdP integration, CIE setup) before configuring it in the explicit proxy settings.