-
Prerequisites:
- Ensure Explicit Proxy itself is configured (see Configure Explicit Proxy ).
- Ensure standard Authentication for Explicit Web Proxy is configured (this is what you are exempting from).
-
Define Exemption Criteria Objects:
Create objects representing the traffic you want to exempt. You can exempt based on source, destination, or both:
-
Source Exemption:
Create an
Address Object
or Address Group (
Objects > Addresses/Objects > Address Groups) containing the source IP addresses of the trusted devices (printers, servers, IoT devices) that should bypass authentication. -
Destination Exemption:
Create a
Custom URL Category
(
Objects > Custom Objects > URL Category) containing the destination domains or specific URLs these devices need to access without authentication (e.g., update servers, specific internal web services accessed via proxy). Review guidelines for URL category exceptions .
-
Source Exemption:
Create an
Address Object
or Address Group (
-
Enable Authentication Portal (Required):
Even though you are creating bypass rules, the Authentication Portal feature must be generally enabled for Authentication Policy rules to be processed. Configure it under
Device > Setup > Management > Authentication Settings > Authentication Portal(refer to Configure Captive Portal/Authentication Portal documentation if needed, though the portal itself might not be actively used if all traffic is exempt or uses other auth methods). -
Configure Authentication Policy Rule for Exemption:
-
Navigate to
Policies > Authentication. -
Click
Addor edit an existing rule that applies to your explicit proxy traffic. Place this exemption rule ABOVE your standard authentication enforcement rule(s) for the proxy. - Source Tab: If exempting by source, select the Address Object/Group created in Step 2 for the Source Address . Otherwise, leave as needed.
- Destination Tab: If exempting by destination, select the Custom URL Category created in Step 2 for the URL Category . Otherwise, leave as needed.
- Service/URL Category Tab: Ensure Service matches your explicit proxy service (likely HTTP/HTTPS or Any if proxy handles various protocols).
-
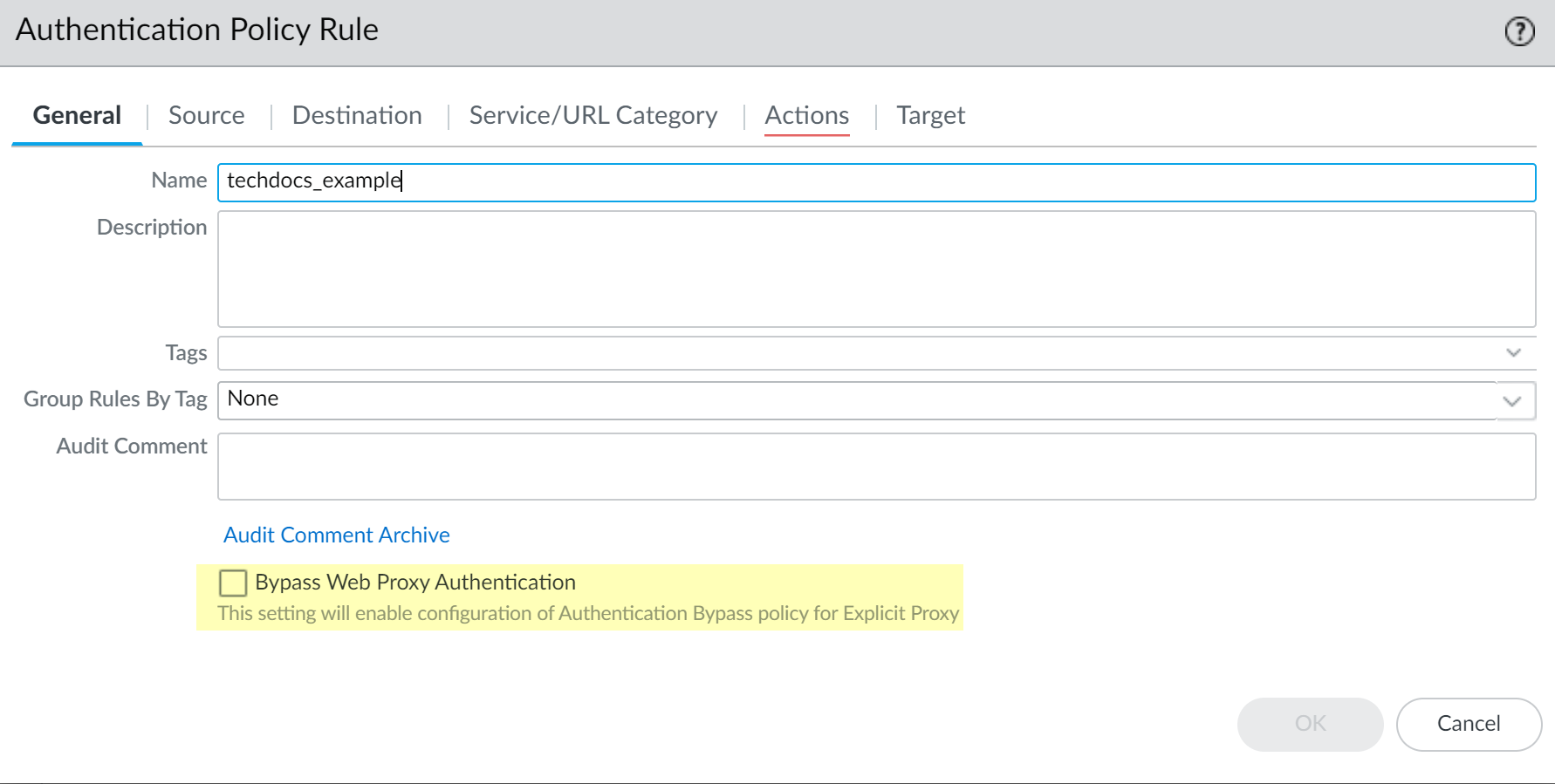
Action Tab (CRITICAL):
- Check the box: Bypass Web Proxy Authentication .
- Note: When this box is checked, the Authentication Enforcement field automatically becomes `None` and cannot be changed for this rule.
-
Navigate to
-
Commit and Verify:
- Commit your changes.
-
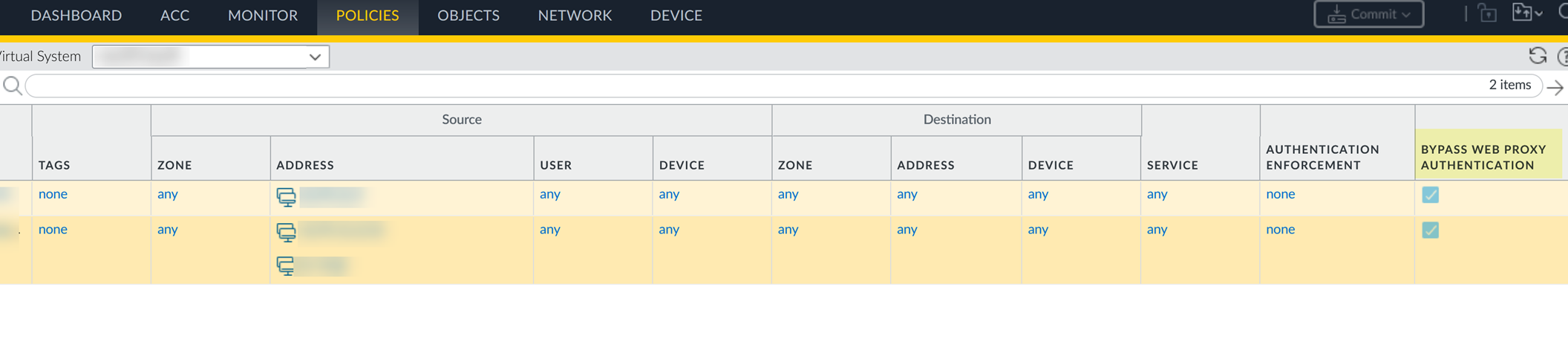
Verify Policy View:
Go to
Policies > Authenticationand confirm a checkmark appears in the Bypass Web Proxy Authentication column for your exemption rule. -
Verify via CLI (Optional):
Use counter commands depending on the primary authentication method being bypassed:
-
For SAML bypass:
show counter global name ctd_eproxy_skip_auth_url_match -
For Kerberos bypass:
show counter global name flow_swg_ep_kerberos_skip_auth - These commands show hit counts for traffic matching exemption rules.
-
For SAML bypass:
- Test Functionality: Ensure devices matching the exemption criteria can access required resources via the proxy without authentication prompts, while other devices are still prompted for authentication as expected.