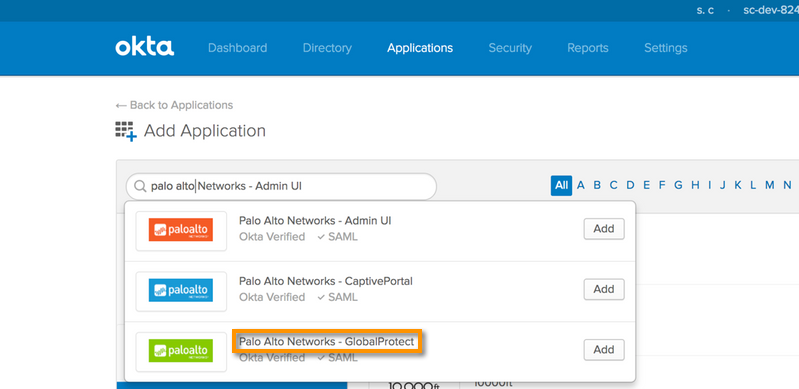
Applications configurations: (Admin > Applications > Add Application )
Search for the Palo Alto Networks GlobalProtect Application > Add
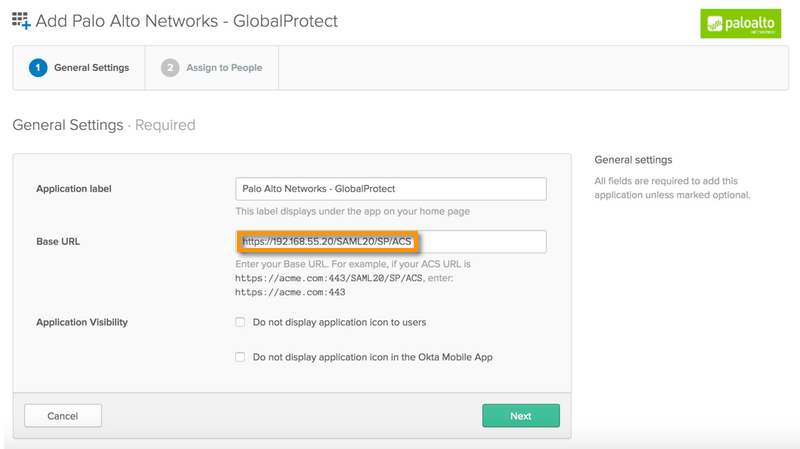
Base URL:
https://GlobalProtectPortalAddress/SAML20/SP/ACS
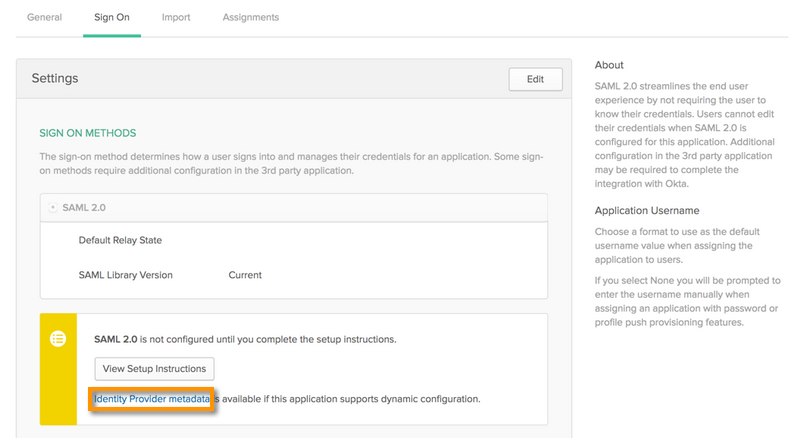
Applications configurations: (Admin > Applications > Palo Alto Networks - GlobalProtect > Sign On)
Download metadata to desktop
Palo Alto Networks Firewall
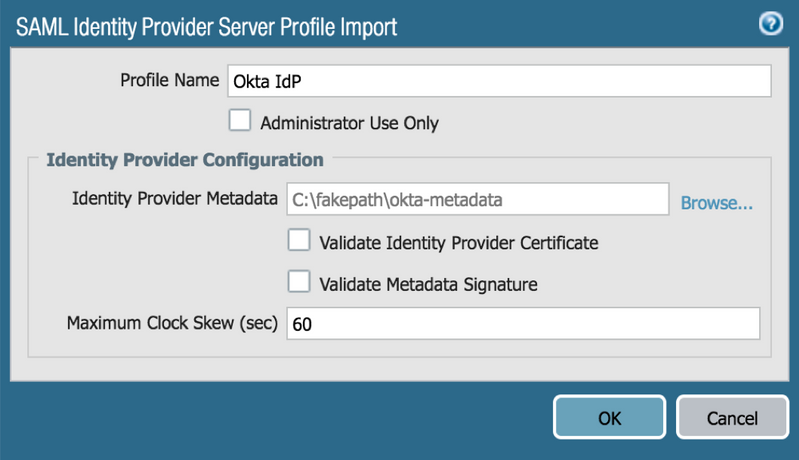
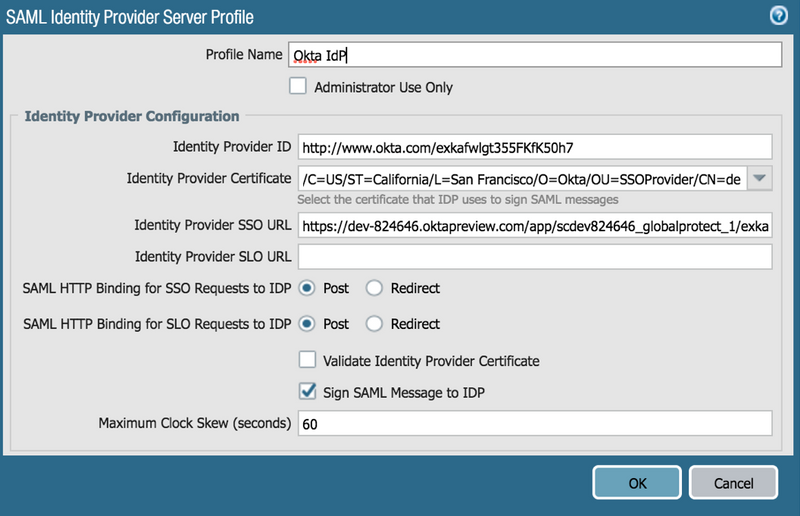
Server configurations: (Device tab > Server Profiles > SAML Identity Provider )
Import Okta metadata
(Note: When you have self signed Certificate from IDP, you won't be able to enable Validate Identity Provider Certificate. Please make sure that you are on PAN-OS
8.1.15, 9.0.9, 9.1.3 or later to mitigate exposure to
https://security.paloaltonetworks.com/CVE-2020-2021
).
Authentication configurations: (Device tab > Authentication Profile )
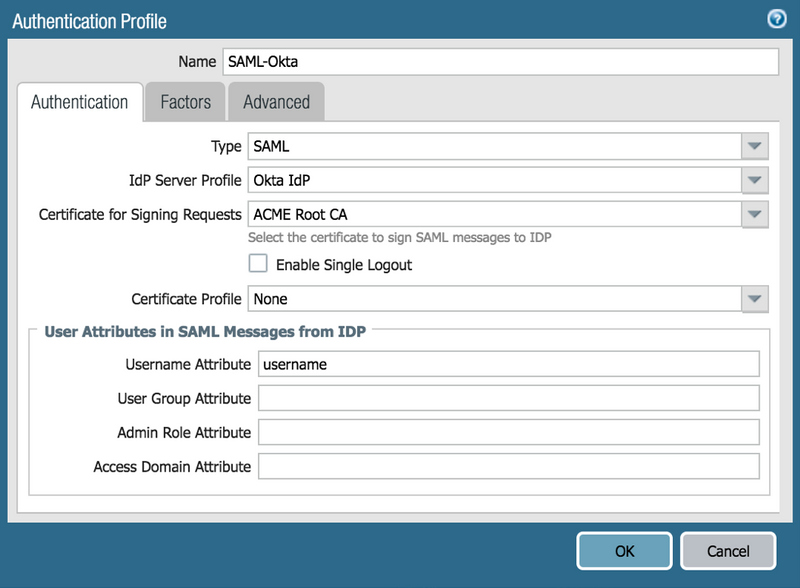
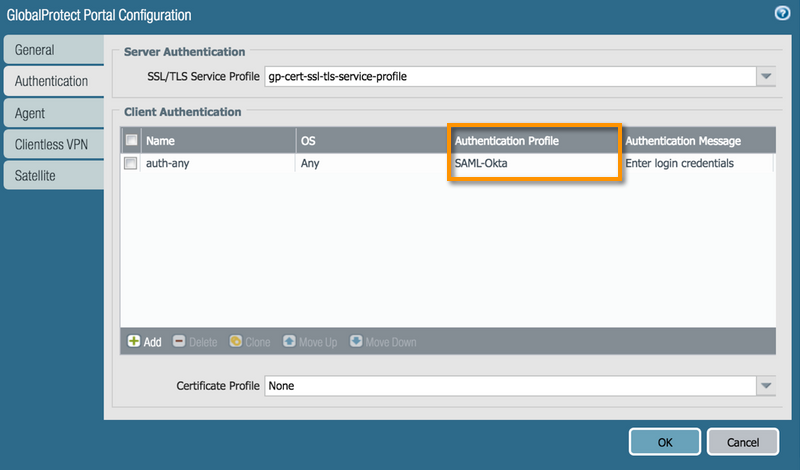
GlobalProtect Portal configurations: (Network tab > GlobalProtect > Portals
GlobalProtect Portal Authentication = SAML
GlobalProtect Clientless VPN Configuration
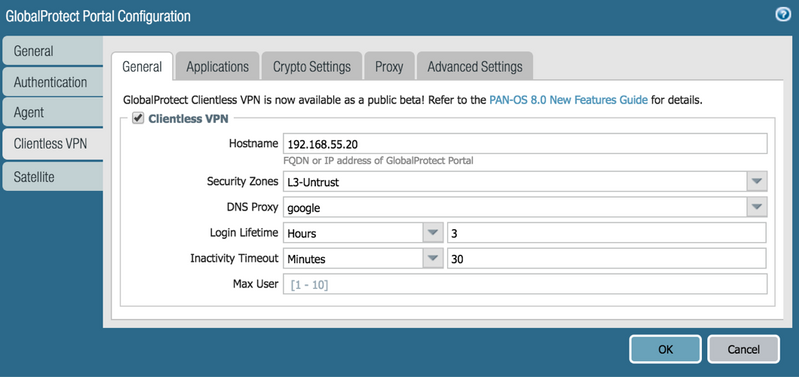
Goto GlobalProtect Clientless VPN
https://192.168.55.20
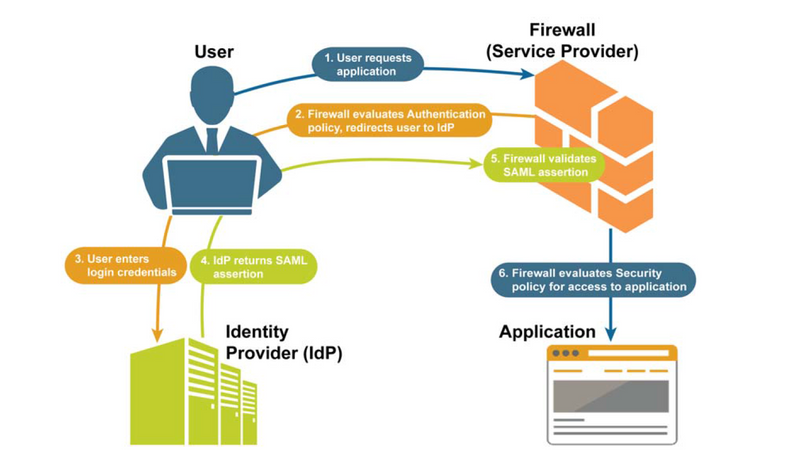
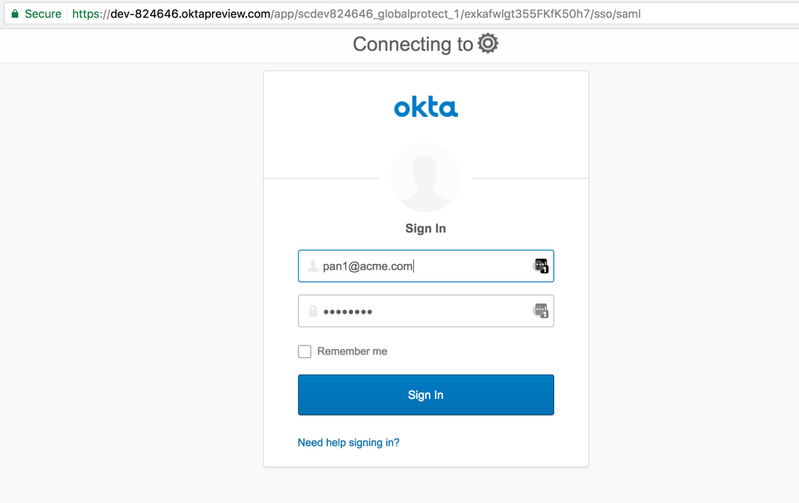
Redirects to Okta to authenticate. Okta sends SAML assertion to firewall.

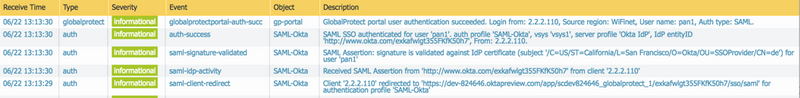
System Logs: (Monitor tab > System )
How-To publish GlobalProtect Clientless VPN app in user Okta Portal with SSO
We don’t support IdP initiated workflow. As a workaround, use the Okta Bookmark App
Applications configurations: (Admin > Applications > Add Application )
Search for the Bookmark App > Add
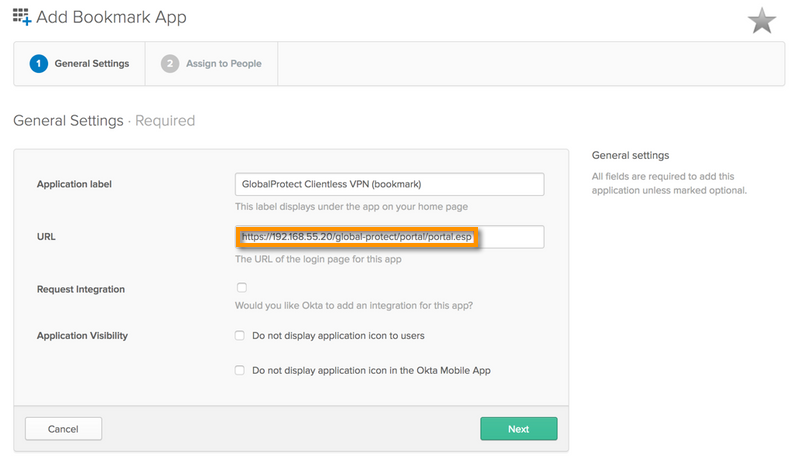
URL:
https://GlobalProtectPortalAddress/global-protect/portal/portal.esp
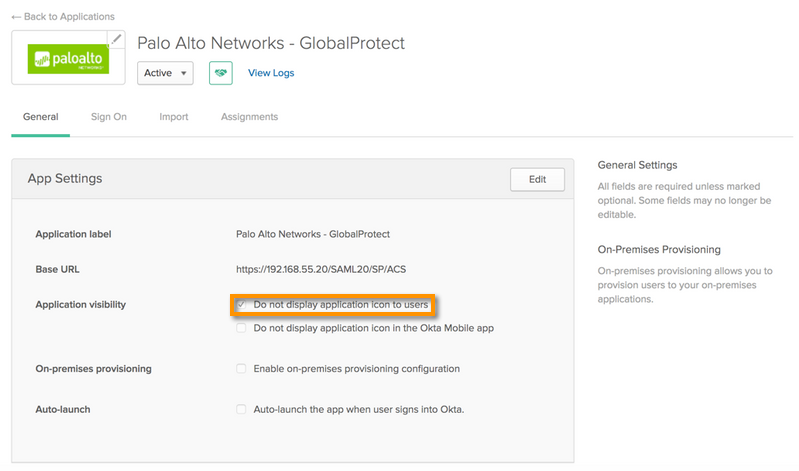
Applications configurations: (Admin > Applications > Palo Alto Networks - GlobalProtect > General )
Hide the Palo Alto Networks - GlobalProtect SAML application to users
Log-in to Okta portal –
https://mycompany.okta.com