GlobalProtect Clientless VPN Overview
GlobalProtect Clientless VPN provides secure remote access to common enterprise web applications. Users have the advantage of secure access from SSL-enabled web browsers without installing the GlobalProtect software. This is useful when you need to enable partner or contractor access to applications, and safely enable unmanaged assets, including personal endpoints. You can configure the GlobalProtect portal landing page to provide access to web applications based on users and user groups and also allow single-sign on to SAML-enabled applications.
Clientless VPN functions as a reverse proxy that modifies the web pages returned by published web applications. It presents a rewritten version of these pages to remote users. When users access these URLs, their requests are routed through the GlobalProtect portal. This leads to the following:
- The protection typically provided by the Same Origin Policy does not apply to pages accessed via Clientless VPN, as the browser treats all pages as if they come from the same origin, regardless of their actual origin.
- The page rewriting process may cause JavaScript to behave differently than intended.
Consequently, if a user visits a compromised website or clicks on a phishing link, a remote attacker could potentially obtain VPN session tokens and read or modify content (including cookies, scripts, or HTML) from any site accessed through the Clientless SSL VPN. This effectively bypasses Same Origin Policy restrictions in all browsers.
Therefore, the Clientless VPN feature only ensures secure remote access to a single trusted application. Since the Same Origin Policy is not enforced, we strongly recommend configuring access to only a trusted page through Clientless VPN. Clientless VPN should never be used to access multiple different websites on the internet or the intranet. If you need to access untrusted websites, use Prisma Access Browser instead.
It is strongly recommended that you access only trusted pages through Clientless VPN. For more information, see GlobalProtect Clientless VPN (within this guide).
When you configure GlobalProtect Clientless VPN, remote users can log in to the GlobalProtect portal using a web browser and launch the web applications you publish for the users. Based on users or user groups, you can allow users to access a set of applications that you make available to them or allow them to access additional corporate applications by entering a custom application URL.
Clientless VPN is not supported on firewalls with multiple virtual systems if the Clientless VPN traffic must traverse multiple virtual systems.
After logging in to the portal, users see a published applications page with the list of web applications that they can launch. You can use the default applications landing page on the GlobalProtect portal or create a custom landing page for your enterprise.

Because this page replaces the default portal landing page, it includes a link to the GlobalProtect app download page. If configured, users can also select Application URL and enter URLs to launch additional unpublished corporate web applications.
When you configure only one web application (and disable access to unpublished applications), instead of taking the user to the published applications page, the application will launch automatically as soon as the user logs in. If you do not configure GlobalProtect Clientless VPN, users will see the app software download page when they log in to the portal.
When you configure GlobalProtect Clientless VPN, you need security policies to allow traffic from GlobalProtect endpoints to the security zone associated with the GlobalProtect portal that hosts the published applications landing page and security policies to allow user-based traffic from the GlobalProtect portal zone to the security zone where the published application servers are hosted. The security policies you define control which users have permission to use each published application.
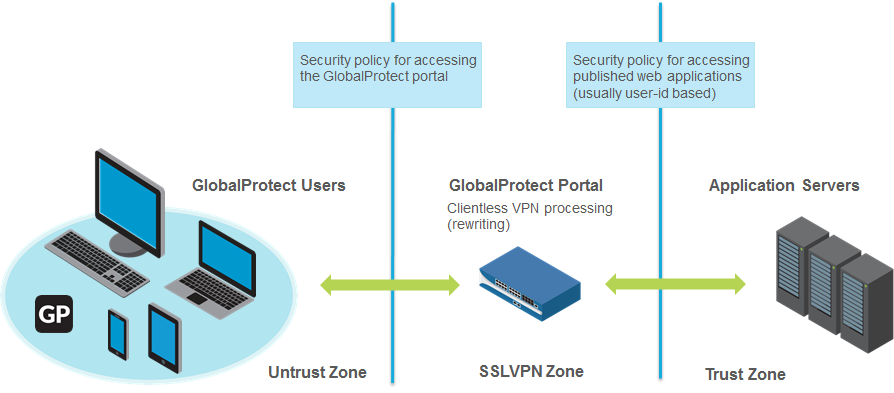
Diagram Explanation: This diagram illustrates the traffic flow and required security zones for GlobalProtect Clientless VPN. User traffic arrives at the GlobalProtect Portal Zone. A security policy is needed to allow this traffic towards the firewall itself (where the portal is hosted). Then, traffic from the Portal Zone needs security policies with User-ID enabled to allow access to the internal Application Zone where the web servers reside.
Supported Technologies
You can configure the GlobalProtect portal to provide secure remote access to common enterprise web applications. For best results, make sure you thoroughly test your Clientless VPN applications in a controlled environment before deploying them or making them available to a large number of users.
The following Web application technologies are not supported :
- Non-Web applications such as SSH, FTP, SMTP, Remote desktop protocol (RDP), and so forth (unless accessed via HTML5-based VDI/VM environments or third-party middleware).
- HTTP 2.0
- Non-UTF-8 encodings
- IPv6 deployment
- Multiple transactions in HTTP such as NT LAN Manager (NTLM) authentication
- Javascript ES6 (Only ES5 or earlier supported)
- Files are not rewritten other than HTML, Javascript, and CSS (for example, Flash, Java Applet, Microsoft Silverlight, PDF, XML, and so forth)
- Other technologies (for example, Microsoft Silverlight or XML/XSLT)
- Any content encodings (for example, Accept-Encoding: defalte, br )
The following table details supported technologies:
| Technology | Supported Version |
|---|---|
| Web application technologies |
UTF-16 encoded files are not supported.
|
| Operating systems |
|
| Supported browsers |
|
| Supported authentication methods |
|
Configure Clientless VPN
It is strongly recommended that you access only trusted pages through Clientless VPN. For more information, see GlobalProtect Clientless VPN (Overview section).
To configure GlobalProtect Clientless VPN:
-
Before you begin:
- Install a GlobalProtect subscription on the firewall that hosts the Clientless VPN from the GlobalProtect portal. Refer to Active Licenses and Subscriptions .
- Install the latest GlobalProtect Clientless VPN dynamic update (see Install Content and Software Updates ) and set a schedule for installing new dynamic content updates. As a best practice, it is recommended to always install the latest content updates for GlobalProtect Clientless VPN.
-
Configure the applications that are available using GlobalProtect Clientless VPN. The GlobalProtect portal displays these applications on the landing page that users see when they log in (the applications landing page).
-
Select
Network > GlobalProtect > Clientless Apps
and
Add
one or more applications. For each application, specify the following:
- Name —A descriptive name for the application (up to 31 characters). The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
- Location (for a firewall that is in multiple virtual system mode)—the virtual system (vsys) where the Clientless VPN applications are available. For a firewall that is not in multi-vsys mode, the Location field does not display.
- Application Home URL —The URL where the web application is located (up to 4,095 characters).
- Application Description ( Optional )—A brief description of the application (up to 255 characters).
- Application Icon ( Optional )—An icon to identify the application on the published application page. You can browse to upload the icon.
- Click OK .
-
Select
Network > GlobalProtect > Clientless Apps
and
Add
one or more applications. For each application, specify the following:
- ( Optional ) Create groups to manage sets of web applications.
-
Configure the GlobalProtect portal to provide the Clientless VPN service.
- Select Network > GlobalProtect > Portal and select an existing portal configuration or Add a new one. Refer to Set Up Access to the GlobalProtect Portal .
-
In the
Authentication
tab, you can:
- ( Optional ) Create a new client authentication specifically for Clientless VPN. In this case, choose Browser as the OS for Client Authentication .
- Use an existing client authentication.
-
In
Clientless > General
, select
Clientless VPN
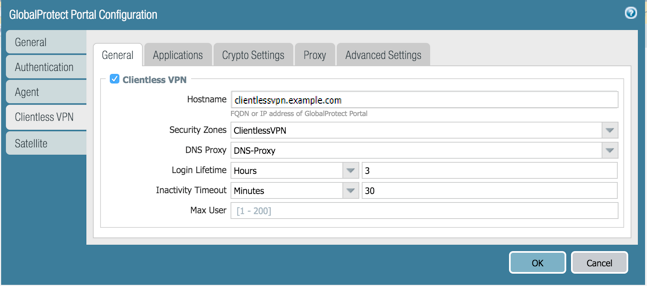
to enable the portal service and configure the following:
- Specify a Hostname (IP address or FQDN) for the GlobalProtect portal that hosts the applications landing page. This hostname is used for rewriting application URLs.
If you use Network Address Translation (NAT) to provide access to the GlobalProtect portal, the IP address or FQDN you enter must match (or resolve to) the NAT IP address for the GlobalProtect portal (the public IP address). Because users cannot access the GlobalProtect portal on a custom port, the pre-NAT port must also be TCP port 443 .
- Specify a Security Zone . This zone is used as a source zone for the traffic between the firewall and the applications. Security rules defined from this zone to the application zone determine which applications users can access.
- Select a DNS Proxy server or configure a New DNS Proxy . GlobalProtect will use this proxy to resolve application names. Refer to DNS Proxy Object .
- Login Lifetime —Specify the maximum length of time (in hours or minutes) that a Clientless VPN session is valid. The typical session time is 3 hours. The range for hours is 1 to 24; the range for minutes is 60 to 1,440. After the session expires, users must re-authenticate and start a new Clientless VPN session.
- Inactivity Timeout —Specify the length of time (in hours or minutes) that a Clientless VPN session can remain idle. The typical inactivity timeout is 30 minutes. The range for hours is 1 to 24; the range for minutes is 5 to 1,440. If there is no user activity during the specified length of time, users must re-authenticate and start a new Clientless VPN session.
- Max User —Specify the maximum number of users who can be logged in to the portal at the same time. If no value is specified, then endpoint capacity is assumed. If the endpoint capacity is unknown, then a capacity of 50 users is assumed. When the maximum number of users is reached, additional Clientless VPN users cannot log in to the portal.
- Map users and user groups to applications.
This mapping controls which applications users or user groups can launch from a GlobalProtect Clientless VPN session.
The GlobalProtect portal uses the user/user group settings that you specify to determine which configuration to deliver to the GlobalProtect Clientless VPN user that connects. If you have multiple configurations, make sure they are ordered correctly and map to all of the required applications; the portal looks for a configuration match starting from the top of the list. As soon as the portal finds a match, it delivers the associated configuration to the GlobalProtect Clientless VPN user.
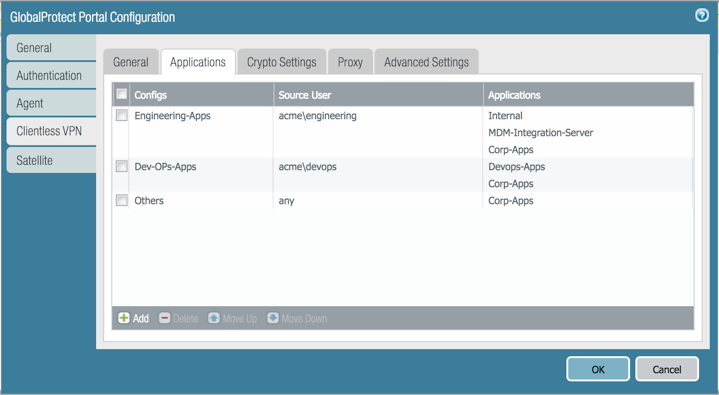
Publishing an application to a user/user group or allowing them to launch unpublished applications does not imply that they can access those applications. You use security policies to control access to applications (published or not).
You must configure group mapping ( Device > User Identification > Group Mapping Settings ) before you can select the groups.
-
On the
Applications
tab,
Add
an
Applications to User Mapping
to match users with published applications.
- Name —Enter a name for the mapping (up to 31 characters). The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
- Display application URL address bar —Select this option to display an application URL address bar from which users can launch applications that are not published on the applications landing page. When enabled, users can select the Application URL .
When this option is disabled, Application URL will not appear in the Clientless VPN landing page.
-
Specify the
Source Users
. You can
Add
individual users or user groups to which the current application configuration applies. These users have permission to launch the configured applications using a GlobalProtect Clientless VPN. In addition to users and groups, you can specify when these settings apply to the users or groups:
- any —The application configuration applies to all users (no need to Add users or user groups).
- select —The application configuration applies only to users and user groups you Add to this list.
- Add individual applications or application groups to the mapping. The Source Users you included in the configuration can use GlobalProtect Clientless VPN to link to the applications you add.
-
Specify the security settings for a Clientless VPN session.
-
On the
Crypto Settings
tab, specify the authentication and encryption algorithms for the SSL sessions between the firewall and the published applications.
- Protocol Versions —Select the required minimum and maximum TLS/SSL versions. The higher the TLS version, the more secure the connection. Choices include SSLv3 , TLSv1.0 , TLSv1.1 , or TLSv1.2 .
-
On the
Crypto Settings
tab, specify the authentication and encryption algorithms for the SSL sessions between the firewall and the published applications.
The Max Version of TLS supported for Clientless VPN is TLSv1.2. TLSv1.3 is currently not supported for Clientless VPN connections.
- Key Exchange Algorithms —Select the supported algorithm types for key exchange. Choices are: RSA , Diffie-Hellman ( DHE ), or Elliptic Curve Ephemeral Diffie-Hellman ( ECDHE ).
- Encryption Algorithms —Select the supported encryption algorithms. We recommend AES128 or higher.
- Authentication Algorithms —Select the supported authentication algorithms. Choices are: MD5 , SHA1 , SHA256 , or SHA384 . We recommend SHA256 or higher.
-
Select the action to take when the following issues occur with a server certificate presented by an application:
- Block sessions with expired certificate —If the server certificate has expired, block access to the application.
- Block sessions with untrusted issuers —If the server certificate is issued from an untrusted certificate authority, block access to the application.
- Block sessions with unknown certificate status —If the OCSP or CRL service returns a certificate revocation status of unknown , block access to the application.
- Block sessions on certificate status check timeout —If the certificate status check times out before receiving a response from any certificate status service, block access to the application.
- ( Optional ) Specify one or more proxy server configurations to access the applications.
Only basic authentication to the proxy is supported (username and password).
If users need to reach the applications through a proxy server, specify a Proxy Server . You can add multiple proxy server configurations, one for each set of domains.
- Name —A label (up to 31 characters) to identify the proxy server configuration. The name is case-sensitive and must be unique. Use only letters, numbers, spaces, hyphens, and underscores.
- Domains —Add the domains served by the proxy server. You can use a wild card character (*) at the beginning of the domain name to indicate multiple domains.
- Use Proxy —Select to assign a proxy server to provide access to the domains.
- Server —Specify the IP address or hostname of the proxy server.
- Port —Specify a port for communication with the proxy server.
- User and Password —Specify the User and Password credentials needed to log in to the proxy server. Specify the password again for verification.
- ( Optional ) Specify any special treatment for application domains.
The Clientless VPN acts as a reverse proxy and modifies web pages returned by the published web applications. It rewrites all URLs and presents a rewritten page to remote users such that when they access any of those URLs, the requests go through the GlobalProtect portal.
In some cases, the application may have pages that do not need to be accessed through the portal (for example, the application may include a stock ticker from yahoo.finance.com). You can exclude these pages.
On the Advanced Settings tab, Add domain names, hostnames, or IP addresses to the Rewrite Exclude Domain List . These domains are excluded from rewrite rules and cannot be rewritten.
Paths are not supported in hostnames and domain names. The wildcard character (*) for hostnames and domain names can appear only at the beginning of the name (for example, *.etrade.com).
-
Save the portal configuration.
- Click OK twice.
- Commit your changes.
- Configure a Security policy rule to enable users to access the published applications.
You need security policies for the following:
- Make the GlobalProtect portal that hosts Clientless VPN reachable from the internet. This is traffic from the Untrust or Internet Zone to the zone where you host the Clientless VPN portal.
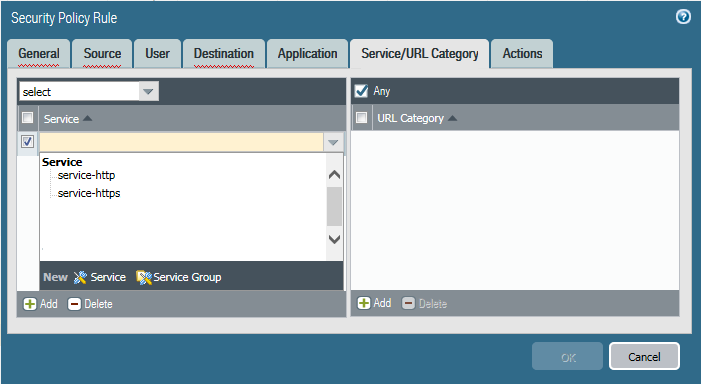
- Allow Clientless VPN users to reach corporate resources. This is traffic from the Clientless VPN zone to the Trust or Corp Zone. The security policies you define control which users have permission to use each published application. For the security zone where the published application servers are hosted, make sure to Enable User Identification .
By default, Service/URL in Security Policy Rule is set to application-default . Clientless VPN will not work for HTTPS sites with this default setting. Change Service/URL to include both service-http and service-https .
- Configure a policy to explicitly block all traffic sourced from the Clientless VPN zone that isn’t explicitly allowed by policy. This will ensure that traffic is not inadvertently allowed by other policies (e.g. intrazone-default). Clientless VPN is not a secure method for browsing multiple internet or intranet sites (see our PAN-SA-2025-0005 advisory for additional details).
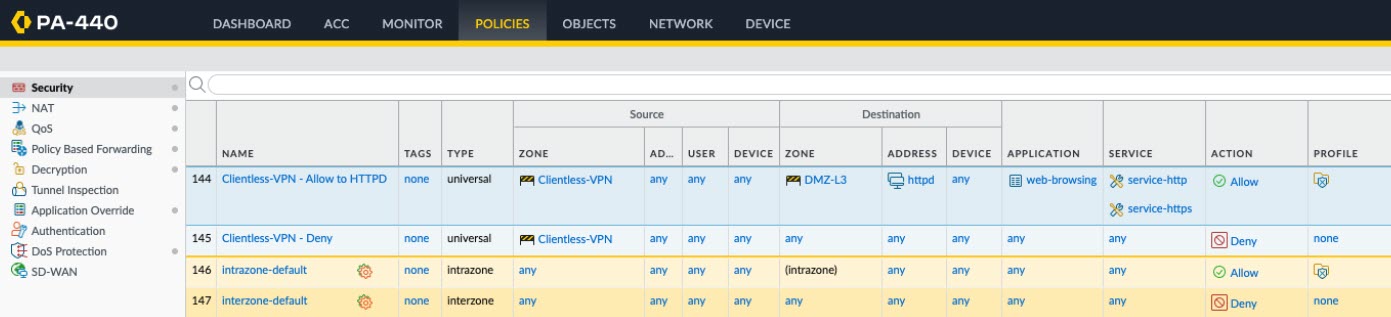
- When you configure a proxy server to access Clientless VPN applications, make sure you include the proxy IP address and port in the security policy definition. When applications are accessed through a proxy server, only Security policies defined for the proxy IP address and port are applied.
- ( Optional ) To configure the Clientless VPN portal landing page to display the location of the portal to which Clientless VPN users are connected, specify the physical location of the firewall on which you configured the portal.
When Clientless VPN users experience unusual behavior, such as poor network performance, they can provide this location information to their support or Help Desk professionals to assist with troubleshooting. They can also use this location information to determine their proximity to the portal. Based on their proximity, they can evaluate whether they need to switch to a closer portal.
If you do not specify a portal location, the Clientless VPN portal landing page displays an empty location field.
-
In the CLI
—Use the following CLI command to specify the physical location of the firewall on which you configured the portal:
<username@hostname> set deviceconfig setting global-protect location <location>
-
In the XML API
—Use the following XML API to specify the physical location of the firewall on which you configured the portal:
- devices —name of the firewall on which you configured the portal
- location —location of the firewall on which you configured the portal
curl -k -F file=@filename.txt -g 'https://<firewall>/api/?key=<apikey>&type=config&action=set&xpath=/config/devices/entry[@name='<device-name>']/deviceconfig/setting/global-protect&element=<location>location-string</location>'
The source IP address of Clientless VPN traffic (as seen by the application) will be either the IP address of the egress interface through which the portal can reach the application or the translated IP address when source NAT is in use.
Diagram Explanation: Sequence diagram showing the high-level flow for a user accessing a published application via GlobalProtect Clientless VPN, including authentication and URL/content rewriting by the firewall.
Troubleshoot Clientless VPN
Because this feature involves dynamic re-writing of HTML applications, the HTML content for some applications may not re-write correctly and break the application. If issues occur, use the commands in the following table to help you identify the likely cause:
| Action | Command |
|---|---|
| CLI Commands | |
|
List the version of Clientless VPN dynamic content being used You can also view the dynamic update version from the Device > Dynamic Updates > GlobalProtect Clientless VPN . |
show system setting ssl-decrypt memory Example Output: proxy uses shared allocator SSL certificate cache: Current Entries: 1 Allocated 1, Freed 0 Current CRE (61-62) : 3456 KB (Actual 3343 KB) Last CRE (60-47) : 3328 KB (Actual 3283 KB) In this example, the current dynamic update is version 61-62, and the last installed dynamic update is version 60-47. |
| List active (current) users of Clientless VPN |
show global-protect-portal current-user portal GPClientlessPortal filter-user all-users Example Output: GlobalProtect Portal : GPClientlessPortal Vsys-Id : 1 User : paloaltonetworks.com\johndoe Session-id : 1SU2vrPIDfdopGf-7gahMTCiX8PuL0S0 Client-IP : 5.5.5.5 Inactivity Timeout : 1800 Seconds before inactivity timeout : 1750 Login Lifetime : 10800 Seconds before login lifetime : 10748 Total number of user sessions: 1 |
|
Show DNS resolution results This can be useful to determine if there are DNS issues. If there is a DNS issue, you will notice querying against an FQDN that was not resolvable in the CLI output. |
show system setting ssl-decrypt dns-cache Example Output: Total DNS cache entries: 89 Site IP Expire(secs) Interface bugzilla.panw.local 10.0.2.15 querying 0 www.google.com 216.58.216.4 Expired 0 stats.g.doubleclick.net 74.125.199.154 Expired 0 |
| Show all Clientless VPN user sessions and cookies stored |
show system setting ssl-decrypt gp-cookie-cache Example Output: User: johndoe, Session-id: 1SU2vrPIDfdopGf-7gahMTCiX8PuL0S0, Client-ip: 199.167.55.50 |
| Show rewrite-stats |
show system setting ssl-decrypt rewrite-stats Example Output (Partial): Rewrite Statistics initiate_connection : 11938 setup_connection : 11909 ... Return Codes Statistics ABORT : 18 RESET : 30 ... |
| Debug Commands | |
| Enable debug logs on the firewall running Clientless VPN Portal |
debug dataplane packet-diag set log feature ssl all debug dataplane packet-diag set log feature misc all debug dataplane packet-diag set log feature proxy all debug dataplane packet-diag set log feature flow basic debug dataplane packet-diag set log on |
|
Enable packet capture on the firewall running the Clientless VPN Portal When you execute packet capture commands, a consent page appears after end users log in to the Clientless VPN portal, informing them that the packets captured during their user session will contain unencrypted (clear-text) data. Users must consent. |
debug dataplane packet-diag set capture username <portal-username> debug dataplane packet-diag set capture stage clientless-vpn-client file <clientless-vpn-client-file> debug dataplane packet-diag set capture stage clientless-vpn-server file <clientless-vpn-server-file> debug dataplane packet-diag set capture stage firewall file <firewall-file> debug dataplane packet-diag set capture stage receive file <receive-file> debug dataplane packet-diag set capture stage transmit file <transmit-file> debug dataplane packet-diag set capture on |
| Show packet capture files |
debug dataplane packet-diag show setting Example Output (Partial): ---------------------------------------------------------- Packet diagnosis setting: ---------------------------------------------------------- Packet capture Enabled: yes Username: test1 Stage clientless-vpn-client: file client.pcap Captured: packets - 3558 bytes - 11366322 Stage clientless-vpn-server: file server.pcap Captured: packets - 1779 bytes - 5651923 ---------------------------------------------------------- |
| Export packet capture files to a Secure Copy (SCP) server |
scp export filter-pcap + remote-port SSH port number on remote host + source-ip Set source address to specified interface address * from from * to Destination (username@host:path) scp export filter-pcap from <source-file> to <scp-server> Destination (username@host:path) |
This table lists common rewrite engine statistics and their meaning:
| Statistic | Description |
|---|---|
| initiate_connection_failure | Connection initiation failed to back-end host |
| setup_connection_failure | Connection setup failed |
| setup_connection_duplicate | Duplicate peer session exists |
| session_notify_mismatch | Mostly invalid session |
| packet_mismatch_session | Failed to find right session for incoming packet |
| peer_queue_update_rcvd_failure | Session was invalid when packet update received by peer |
| peer_queue_update_sent_failure | Failed to send packet updates to peer or failed to send packet queue length updates to peer |
| exceed_pkt_queue_limit | Too many packets queued |
| proxy_connection_failure | Proxy connection failed |
| setup_connection_r | Installing the peer session to the application server. This value should match the values for initiate_connection and setup_connection . |
| setup_connection_duplicate_r | Duplicate sessions already in proxy |
| setup_connection_failure_r | Failed to set up the peer session |
| session_notify_mismatch_r | Peer session not found |
| packet_mismatch_session_r | Peer session not found when trying to get the packet |
| exceed_pkt_queue_limit_r | Too many packets held |
| unknown_dest | Failed to find destination host |
| pkt_no_dest | No destination for this packet |
| cookie_suspend | Suspended session to fetch cookies |
| cookie_resume | Received response from MP with updated cookies. This value generally matches the value of cookie_suspend. |
| decompress_failure | Failed to decompress |
| memory_alloc_failure | Failed to allocate memory |
| wait_for_dns_resolve | Suspended session to resolve DNS requests |
| dns_resolve_reschedule | Rescheduled DNS query due to no response (retry before timeout) |
| dns_resolve_timeout | DNS query timeout |
| setup_site_conn_failure | Failed to setup connection to site (proxy, DNS) |
| site_dns_invalid | DNS resolve failed |
| multiple_multipart | Multi-part content-type processed |
| site_from_referer | Received the back-end host from referrer. This can indicate failed rewrite links from flash or other content which Clientless VPN does not rewrite. |
| received_fin_for_pending_req | Received FIN from server for pending request from client |
| unmatched_http_state | Unexpected HTTP content. This can indicate an issue parsing the http headers or body. |
Clientless VPN Quiz
Test your knowledge on GlobalProtect Clientless VPN concepts.