Introduction: The Power of App-ID
One of the core strengths of Palo Alto Networks firewalls is App-ID, the technology used for application identification. Unlike traditional firewalls that rely solely on port and protocol (Layer 4) information, App-ID uses multiple identification techniques (including signatures, heuristics, protocol decoding, and decryption) to identify applications at Layer 7, regardless of the port they use, whether they hop ports, use non-standard ports, or are hidden within SSL/TLS encryption (requires decryption).
Leveraging App-ID within Security Policy rules is fundamental to implementing a true Next-Generation Firewall strategy, enabling granular control, reducing the attack surface, and allowing other security features like Threat Prevention and QoS to function effectively based on the actual application.
This guide focuses specifically on how to configure and use App-ID as a matching criterion within Security Policy rules (PCNSE Objective 3.1.1).
App-ID Basics: How Applications Are Identified
Palo Alto Networks firewalls employ a systematic process to identify applications:
- Signature Matching: The firewall first tries to identify the application based on known patterns in the traffic flow, similar to how intrusion prevention systems work. This is often the quickest and most accurate method for well-known applications.
- Protocol Decoding: The firewall decodes the application-layer protocol (e.g., HTTP, FTP, DNS, SMB). This identifies the base protocol, which can then provide context for further analysis or identify simple applications.
- Heuristics: For evasive or custom applications, heuristics are used. These are behavioral analysis techniques that look at traffic patterns, transaction characteristics, or other clues within the session to determine the application.
- Decryption: If the traffic is encrypted (SSL/TLS), the firewall can decrypt it (if configured to do so) to reveal the cleartext application traffic within. Once decrypted, steps 1-3 can be applied to the inner traffic. The outer encrypted traffic is initially identified as 'ssl'.
This multi-pass approach ensures that applications are identified accurately, even if they try to evade traditional port-based detection.
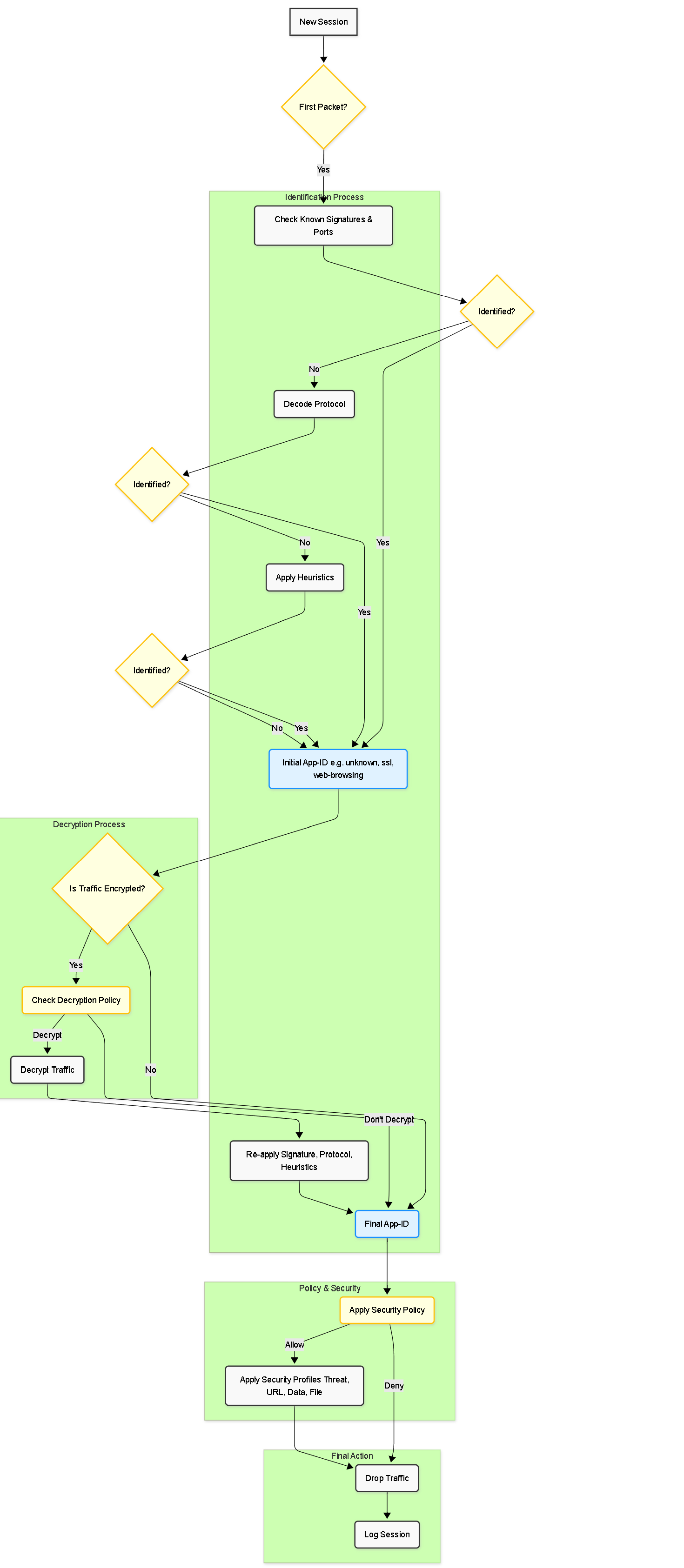
Simplified App-ID Identification Flow
App-ID Basics: Why Use App-ID in Security Rules?
Using App-ID instead of or in conjunction with traditional port/protocol matching offers significant advantages:
- Accurate Identification: Ensures policy decisions are based on the actual application, not just the port (which can be easily spoofed or misused).
-
Reduced Attack Surface:
By explicitly allowing only sanctioned applications on their standard ports (using
application-default), you block potentially malicious or unwanted traffic trying to use common ports like 80 or 443. -
Granular Control:
Allows you to create policies for specific applications (e.g., allow
facebook-basebut blockfacebook-appsorfacebook-chat). - Enable Threat Prevention: Accurate App-ID is often a prerequisite for effective threat signatures (Antivirus, Anti-Spyware, Vulnerability Protection) which are application-specific.
- Enable QoS by Application: Allows bandwidth management based on the identified application.
- Improved Logging and Visibility: Logs show the actual application, providing much better insights into network activity than port-based logs.
Policy Configuration: Methods for Selecting Applications
App-ID is configured within the Security Policy rule definition (Policies > Security). You have several ways to specify applications in a rule:
-
Specific Applications:
You can browse or search for and add individual App-IDs.
Examples:
ssl,web-browsing,dns,microsoft-teams-base,youtube-base,bitorrent.Use Case: For explicitly allowing or blocking known, specific applications.
Example Rule Segment (Conceptual)
Rule Name: Allow_Teams_Core
Source Zone: Trust
Destination Zone: Untrust
Application: [ Add:microsoft-teams-base,microsoft-teams-audio-video]
Service:application-default
Action: Allow -
Application Groups:
These are custom objects (Objects > Application Groups) where you manually group multiple related App-IDs together.
Example: Create a group called "Approved-Web-Tools" containing App-IDs for
salesforce,workday,office366-web.Use Case: Simplifies policy creation and management by allowing you to reference a logical group instead of numerous individual App-IDs. Makes policies easier to read and update.
Example Rule Segment (Conceptual)
Rule Name: Allow_Approved_Web_Tools
Source Zone: Trust
Destination Zone: Untrust
Application: [ Add: Approved-Web-Tools ] # Reference the custom group
Service:application-default
Action: Allow -
Application Filters:
These are dynamic groups based on application characteristics defined by Palo Alto Networks (Objects > Application Filters).
Criteria: You can filter based on Category (e.g.,
collaboration,social-networking), Subcategory, Technology (browser-based,client-server), Risk (1to5), Characteristics (evasive,prone-to-misuse).Use Case: Creating broader policies without needing to list every single application. For example, block all applications with Risk 5 or allow all applications in the 'business-systems' category.
Dynamic Nature: As Palo Alto Networks adds or updates App-IDs, applications matching the filter criteria are automatically included or excluded.
Example Rule Segment (Conceptual)
Rule Name: Block_High_Risk_Apps
Source Zone: Any
Destination Zone: Any
Application: [ Add: High-Risk-App-Filter ] # Reference custom filter based on Risk=4,5
Service:any
Action: Deny
You can combine these methods within a single rule (e.g., allow a specific Application Group but also add one extra specific App-ID).
Policy Configuration: Application-Default vs Service Specified
When configuring Security Policy rules, you must specify the
Service
. The two main options are
application-default
and a specific port/protocol definition (e.g.,
service-http
,
service-https
, or a custom TCP/UDP port).
This setting controls whether the firewall allows the identified application ONLY on its standard, default ports, or if it allows the application on the ports specified in the Service field, regardless of App-ID's default ports.
Comparison:
| Feature | Application-Default | Service Specified (e.g., tcp/80, tcp/443) |
|---|---|---|
| Port Matching | Traffic must match the application's identified App-ID AND the standard default ports defined for that App-ID. | Traffic must match the application's identified App-ID. The port is matched against the specified Service object, NOT the application's default ports. |
| Security/Attack Surface | Advantage: Tighter security. Blocks attempts to run applications on non-standard or commonly misused ports (e.g., running BitTorrent on TCP/443). Significant reduction of attack surface. Recommended for most policies. |
Disadvantage:
Less secure. Allows the application on ANY port defined in the Service object. If the Service is
any
, it allows the application on any port it's found on. Can increase the attack surface by allowing legitimate applications on non-standard ports.
|
| Flexibility | Disadvantage: Less flexible for applications that legitimately use non-standard ports, require a custom service object for exceptions. |
Advantage:
More flexible. Necessary if an application truly runs on non-standard or multiple custom ports not covered by its application-default definition. Can use
any
for maximum flexibility (least security).
|
| Configuration |
Simple - select
application-default
from the Service dropdown.
|
Requires creating or selecting a specific Service object (standard or custom). |
| Best Practice |
Use
application-default
whenever possible for least privilege and reduced attack surface.
|
Only use a specific Service when absolutely necessary for an application running on non-standard ports. Avoid
any
unless truly unavoidable and risk is assessed.
|
Example Scenario: Allowing Web Browsing
Rule 1: Allow Web Browsing (Recommended)
Source: Trust Zone
Destination: Untrust Zone
Application:
web-browsing
Service:
application-default
Action: Allow
Result:
Allows HTTP (tcp/80) and HTTPS (tcp/443) traffic *only* when it is identified as
web-browsing
.
Rule 2: Allow Web Browsing (Less Secure)
Source: Trust Zone
Destination: Untrust Zone
Application:
web-browsing
Service:
service-any
(or
any
)
Action: Allow
Result:
Allows HTTP and HTTPS traffic identified as
web-browsing
, even if it runs on non-standard ports (e.g., tcp/8080, tcp/8443). Also allows
web-browsing
traffic on *any* other port it might potentially be identified on.
Rule 3: Traditional Port-Based Rule (Insecure)
Source: Trust Zone
Destination: Untrust Zone
Application:
any
Service:
service-http
(tcp/80) OR
service-https
(tcp/443)
Action: Allow
Result: Allows *ANY* application traffic as long as it uses TCP/80 or TCP/443. BitTorrent, malware C2, etc., could potentially traverse this rule if they use these ports. This defeats the purpose of App-ID.
application-default
, the port must match the *App-ID's* defined default ports. If App-ID is
any
, only Service matters (traditional firewall). If Service is
any
, only App-ID matters for matching (up to that point).
Decryption & App-ID: Impact on Identification and Policy Order
Encrypted traffic (SSL/TLS) poses a challenge to Layer 7 identification. Before decryption, the firewall can typically only identify this traffic as the generic
ssl
application, potentially with some limited information gleaned from the SSL/TLS handshake (like SNI - Server Name Indication).
For full, granular App-ID of the traffic *within* the encrypted tunnel (e.g., identifying
facebook-base
or
gmail
inside HTTPS), the firewall must decrypt the traffic. This requires a separate Decryption Policy.
How Decryption Affects App-ID:
-
Initial Identification:
Traffic arrives and is often first identified as
ssl(for TLS/SSL) orweb-browsing(for plain HTTP). -
Decryption Policy Check:
The firewall checks the Decryption Policy based on the initial session parameters (source, destination, zone, service - usually
service-https, application - usuallyssl). -
Decryption Action:
- If a Decryption rule matches and the action is 'Decrypt', the firewall performs SSL Forward Proxy or SSL Inbound Inspection.
- If a Decryption rule matches and the action is 'No Decrypt', the traffic remains encrypted.
- If no Decryption rule matches, the default action applies (usually 'No Decrypt').
-
Post-Decryption App-ID:
If decrypted, the firewall re-evaluates the traffic using the full App-ID process (signatures, protocol decoding, heuristics) on the now visible cleartext payload. The session's App-ID is updated to the specific application (e.g.,
facebook-base,youtube,exchange-web-mail). - Security Policy Re-Evaluation: The security policy lookup happens AFTER App-ID is determined or updated.
Policy Order: Security vs. Decryption
Decryption policies are evaluated before Security policies. However, the Security policy that allows/denies the traffic after decryption must appear *after* the decryption rule has decided to decrypt the traffic.
-
A Security rule matching
sslallows encrypted traffic to pass through to the Decryption policy engine. -
Security rules matching specific applications like
web-browsing,facebook-base, etc., are typically placed below the relevant Decryption policy rules. This ensures that once traffic is decrypted, the specific application can be identified and controlled by the appropriate Security rule. -
You might have a "catch-all" Security rule allowing
sslabove decryption for certain traffic that shouldn't be decrypted or needs a temporary pass before specific App-ID rules are refined.
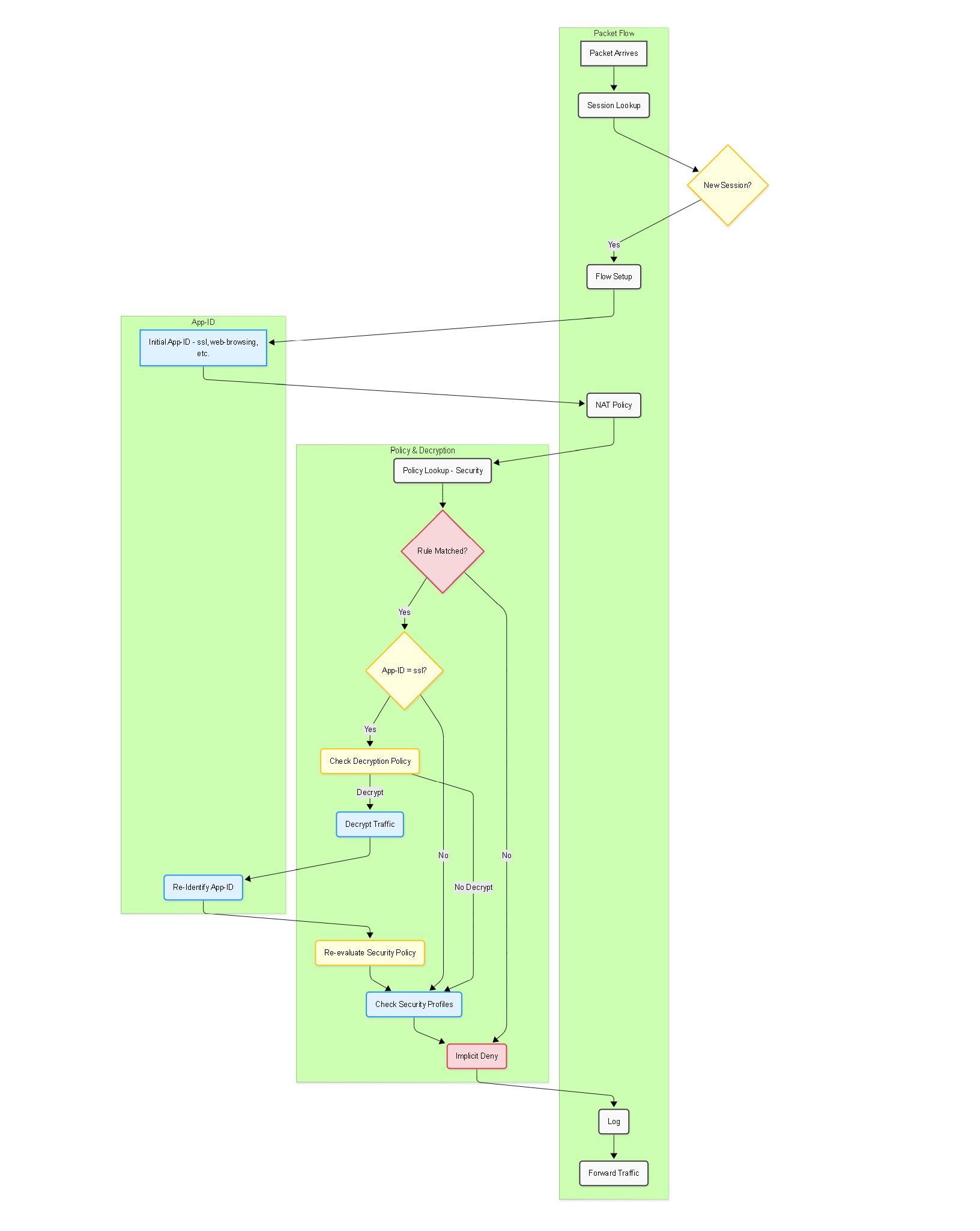
Simplified Packet Flow with App-ID and Decryption
Decryption & App-ID: Decryption Exemption Issues
While decrypting SSL/TLS traffic is essential for full App-ID and threat inspection, there are scenarios where traffic must be exempted from decryption:
- Privacy/Compliance: Traffic to sensitive sites like banking, healthcare, or legal services may be legally or policy-mandated to remain private and not be intercepted/decrypted.
- Technical Compatibility: Some applications use techniques like certificate pinning or expect specific certificate chains that conflict with the firewall's SSL Forward Proxy certificate, causing connection errors. Examples include some mobile apps, update services, or specific internal applications.
- Resource Limitations: Decryption is CPU-intensive. Exempting high-volume, low-risk traffic can conserve firewall resources.
Issues Arising from Exemption:
-
Limited App-ID:
Traffic exempted from decryption is typically identified only as
ssl. The firewall cannot see the actual application or content within the tunnel. - Reduced Security Inspection: Without decryption, Threat Prevention profiles (Antivirus, Anti-Spyware, Vulnerability Protection), URL Filtering, and Data Filtering cannot inspect the content within the SSL/TLS tunnel. Malware, exploits, or sensitive data exfiltration hidden within encrypted traffic will pass through undetected.
-
Policy Blind Spots:
Granular policies based on specific App-IDs (like blocking social media) will not apply if the traffic is exempted and only identified as
ssl. You can only control it based on source, destination, user, service (usually 443), and the genericsslApp-ID.
Decryption exemption is configured in the Decryption Policy. Best practice is to exempt traffic only when necessary, document the exemptions, and understand the associated security risk.
App-ID Interactive Quiz
Test your knowledge of Palo Alto Networks App-ID with these 30 questions covering concepts often found in PCNSE exams.