Understanding Application Override in Palo Alto Networks Firewalls
Palo Alto Networks firewalls are designed to identify applications traversing the network regardless of port, protocol, or evasive tactics, using their signature-based App-ID technology. This granular visibility is the foundation for modern security policies.
However, there are specific scenarios where the firewall's standard application identification process might need to be bypassed or altered for particular traffic flows. This is where the Application Override feature becomes necessary.
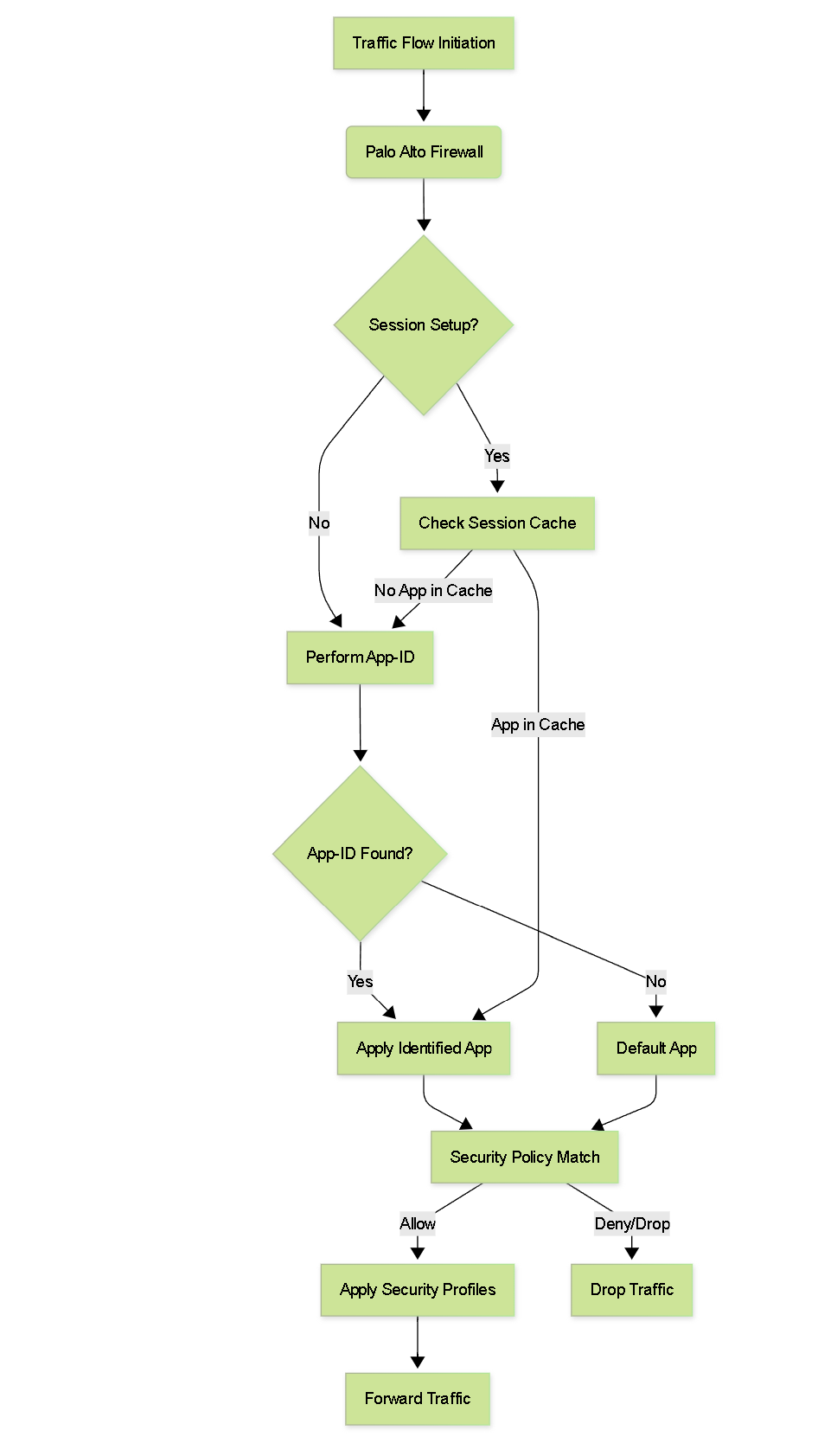
Simplified Traffic Flow without Application Override.
Why Application Override Might Be Needed
While App-ID is powerful, there are legitimate reasons to use Application Override:
-
Custom or Proprietary Applications: Traffic for internally developed or highly specific vendor applications might not have a pre-defined App-ID signature. Without an override, this traffic could be identified as 'incomplete', 'unknown-tcp', or simply by its port/protocol, preventing granular policy enforcement based on the actual (known) purpose of the traffic.
-
Performance-Sensitive Applications: The App-ID engine inspects traffic to identify applications. For certain high-throughput, low-latency applications (like Voice over IP, specific video streams, or large file transfers over known ports), bypassing L7 inspection can potentially improve performance or reduce latency, though this should be carefully evaluated.
-
Protocol Mismatches or Non-Standard Ports: Sometimes, an application might run on a non-standard port (e.g., HTTP traffic on port 8080, or an application using a standard port like 443 but is *not* SSL/TLS). While App-ID can often identify applications on non-standard ports, an override guarantees a specific identification for policy matching.
-
Troubleshooting: In troubleshooting scenarios, overriding traffic to a specific known application can help isolate whether identification issues are contributing to a problem.
-
Interfacing with Legacy Systems: Older or less-standardized systems might use protocols or traffic patterns that confuse App-ID, making override necessary for reliable policy enforcement.
Essentially, override is used when you know exactly what the traffic is or *should be*, and you want to enforce policy based on that known identity, bypassing the firewall's dynamic App-ID process for that specific flow.
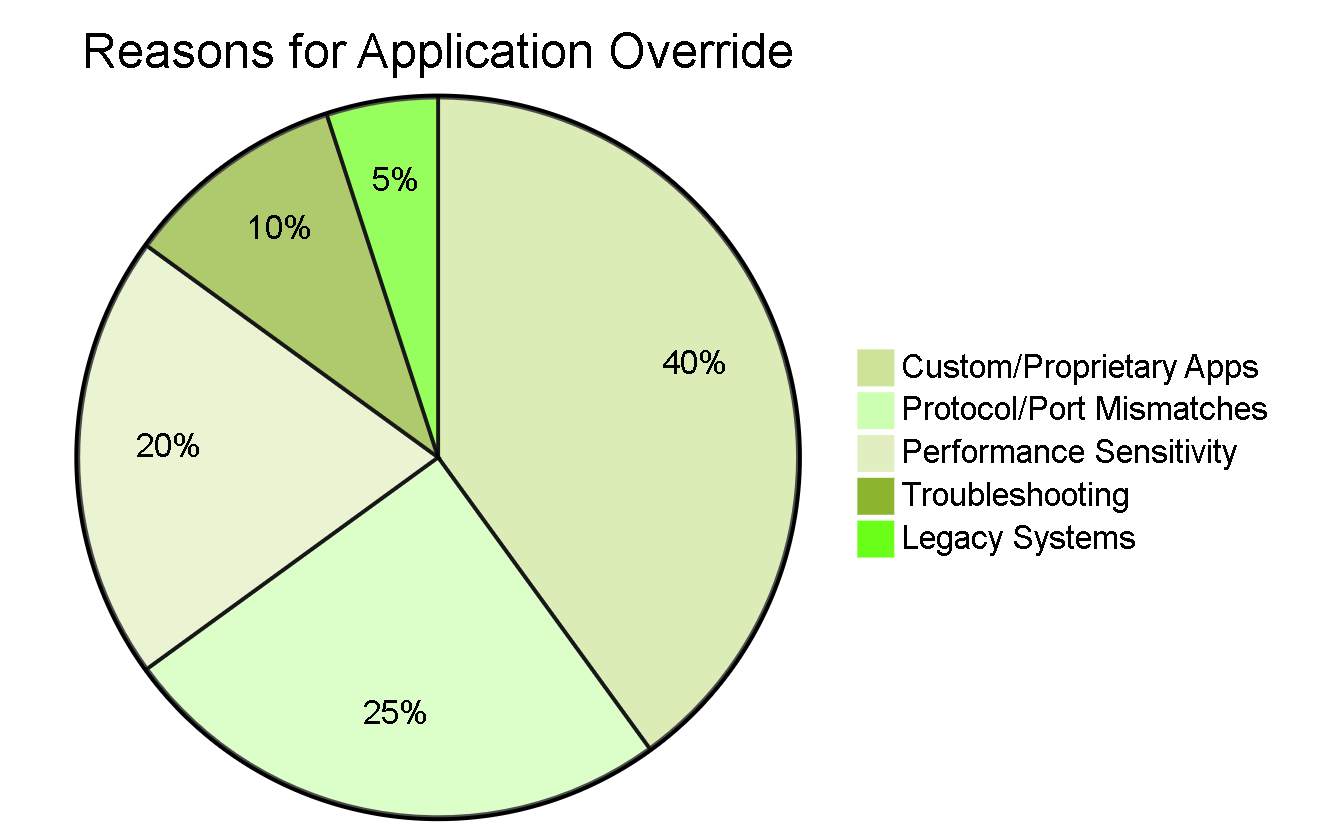
Typical reasons administrators use Application Override.
Specific Use Cases for Application Override
Building on the "Why Needed" section, here are some concrete examples:
-
Internal Database Connections: Your custom ERP system talks to a SQL database on port 1433, but App-ID identifies it generically or as 'incomplete'. You can create an override to classify this traffic as a specific custom application (e.g., 'erp-sql-connection') to apply granular security policies (User-ID, specific zones) just to this traffic, rather than all SQL traffic.
-
VoIP Traffic: You have a specific VoIP system using known ports (like UDP 5060, RTP ports) but App-ID sometimes identifies other traffic on those ports or the VoIP application itself isn't perfectly identified in all scenarios. Overriding the known VoIP traffic on its specific ports can ensure correct identification for QoS and security policies.
-
Legacy Client-Server Applications: An old application uses a fixed port and protocol (e.g., TCP 5000) but its internal traffic isn't standard HTTP or another recognizable protocol. Overriding this to a custom app like 'legacy-app-tcp5000' allows you to manage its policy rules accurately.
-
Non-Standard Web Servers: An internal web server serves specific content on a non-standard port (e.g., TCP 8080). If App-ID identifies this as 'web-browsing' but you want to treat it differently from standard internet browsing, an override to a custom app like 'internal-webapp-8080' is useful.
Example Scenario: Internal ERP System
Your internal ERP application uses a proprietary client that connects to a server on TCP port 7000. Standard App-ID might see this as 'unknown-tcp'. You need to allow this traffic between the user VLAN and the server VLAN, but you also want to ensure no *other* unknown-tcp traffic is allowed between these zones on this port. An Application Override policy targeting TCP 7000 between these specific zones/addresses, assigning it a custom application like 'erp-proprietary', allows you to create a precise security policy rule for 'erp-proprietary', thereby limiting the scope of the 'unknown-tcp' allowance.
Step-by-Step: Creating an Application Override Policy
Application Override policies are configured under Policies > Application Override .
Here are the typical steps:
-
Navigate: Go to
Policies > Application Override. -
Add Policy: Click
Addto create a new policy rule. -
Name: Give the policy a descriptive name (e.g.,
override-internal-erp-tcp7000). -
Traffic Matching Criteria: Define the specific traffic you want to override. This is based on Layer 4 information:
- Source Zone: The zone(s) where the traffic originates.
- Source Address: The IP address(es) of the source.
- User: (Optional) Specific users or groups.
- Host Information Profile (HIP): (Optional) Match based on endpoint posture.
- Destination Zone: The zone(s) where the traffic is going.
- Destination Address: The IP address(es) of the destination.
-
Service:
This is crucial. You define the port and protocol (e.g.,
service-tcp-7000,service-udp-5060). You can use existing service objects or create new ones. This is where you specify the Layer 4 definition.
-
Application: Under the "Application" tab (or equivalent section in newer PAN-OS versions), specify the application you want this traffic to be identified as. This can be a custom application you have already created or a predefined application.
-
You often need to
create a Custom Application
first if it doesn't exist. Go to
Objects > Applicationsand add a new application. Give it a name and select the appropriate attributes (e.g., Category, Subcategory, Technology - though these are less critical for simple overrides).
-
You often need to
create a Custom Application
first if it doesn't exist. Go to
-
Actions: The primary action is assigning the specified application. There isn't an "allow" or "deny" action here; the override policy's purpose is solely identification.
-
Commit: Commit the configuration changes to the firewall.
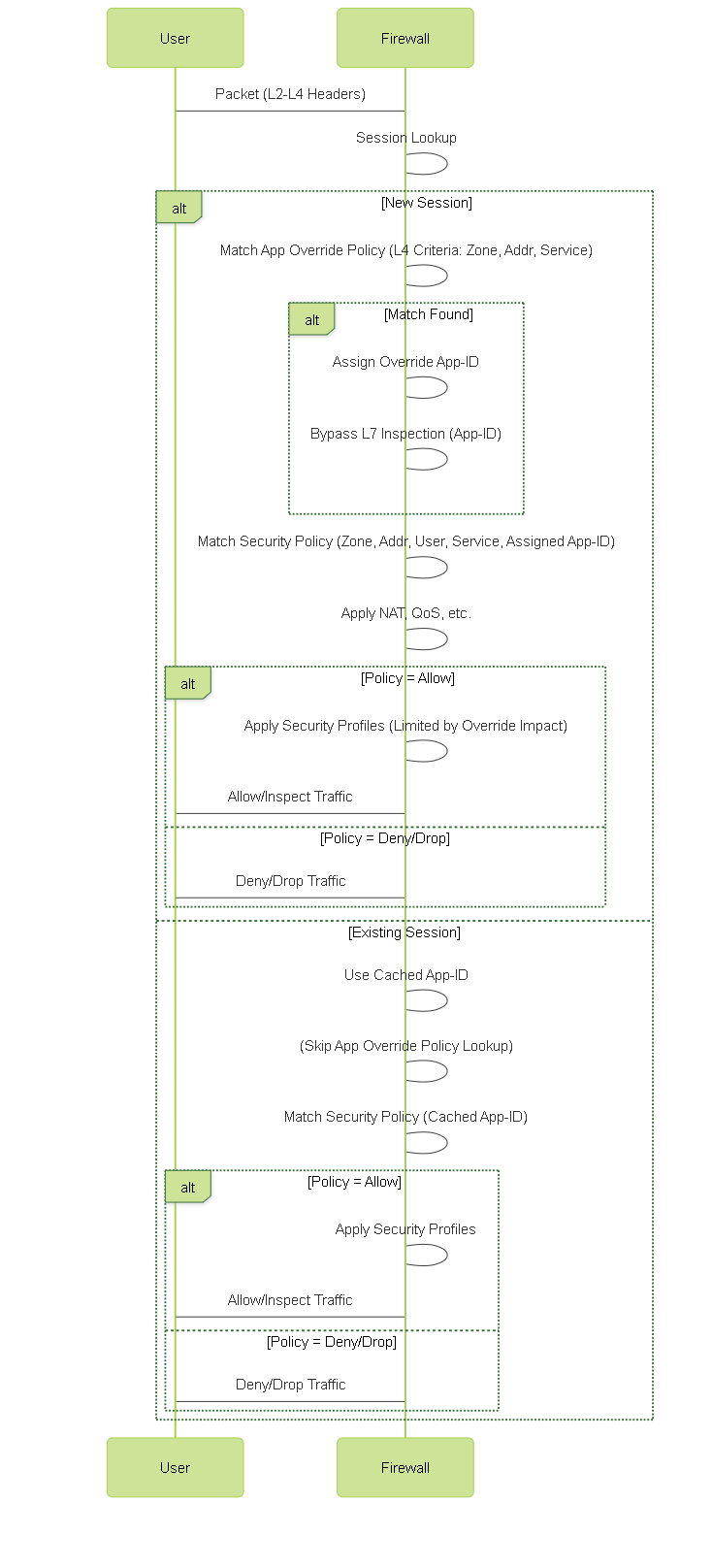
Simplified Sequence Diagram: Traffic Flow with and without Application Override.
Implications of Implementing Application Override
Implementing Application Override has significant impacts on various firewall functions, primarily because it bypasses the standard App-ID process.
Implication on Layer 7 (App-ID) Inspection
When an Application Override policy is matched, the firewall explicitly bypasses the Layer 7 signature-based App-ID inspection for that specific session. The session is assigned the application defined in the override rule based purely on its Layer 4 characteristics (Source/Destination Zones, Addresses, and Service/Port/Protocol).
This means the firewall will not look into the payload of the traffic to identify the *true* application. It simply trusts that the traffic on the specified port/protocol, between the defined zones/addresses, is the application you've assigned via the override.
Does App Override Cause Layer 4 Inspection?
This question is slightly misleading. The Palo Alto Networks firewall *always* inspects traffic at Layer 4 to build sessions and match policy rules (which include L4 criteria like Service/Port). What App Override *does* is cause the firewall to use the Layer 4 criteria specified in the *override rule* to assign an application identity, *instead of* performing the usual Layer 7 inspection to dynamically identify the application.
So, yes, the override policy itself matches based on L4 parameters, and it dictates the application identity without needing L7 inspection for that session.
Implications on Security Policy Matching
This is a key implication. Security policies match based on Zone, Address, User, Service, AND Application. When a session is overridden, the application used for security policy matching is the one specified in the override rule, NOT the one App-ID might have dynamically identified (or failed to identify) without the override.
This allows you to create security policy rules that are specific to your custom or overridden application, providing granular control even for traffic App-ID wouldn't normally recognize by name.
Implications on Threat Prevention (Anti-Spyware, Vulnerability Protection), URL Filtering, and File Blocking
When a session is overridden, the effectiveness of Security Profiles (Threat Prevention, URL Filtering, File Blocking, WildFire) can be significantly impacted or negated.
-
Threat Prevention: Many threat signatures rely on identifying specific protocol patterns or application behaviors at L7. By bypassing L7 inspection via override, the firewall may not be able to apply these signatures effectively. It can still apply signatures that look for patterns anywhere in the payload, but context-aware protection tied to specific application protocols is lost.
-
URL Filtering: URL filtering typically operates on HTTP/HTTPS traffic identified by App-ID. If you override HTTP/HTTPS traffic (e.g., HTTP on port 8080 overridden to a custom app), URL filtering will likely NOT be applied to that traffic, as it's no longer seen as the standard 'web-browsing' or 'ssl' application by the security policy processing.
-
File Blocking: Similar to Threat Prevention and URL Filtering, File Blocking profiles often rely on application context (e.g., block executables over HTTP). Bypassing App-ID can interfere with the proper application of File Blocking profiles.
-
For PCNSE/PCNSA, understand that Threat Prevention, URL Filtering, and File Blocking profiles are less effective or may not be applied at all to sessions matched by an Application Override rule, because the L7 inspection needed for these features is bypassed.
Implications on QoS
QoS policies can be based on applications. If you override traffic to a specific custom application, you can create QoS policy rules that match this custom application. This allows you to prioritize or shape traffic for your overridden applications based on the assigned custom App-ID, which can be very useful for performance-sensitive internal apps like VoIP or database connections.
Implications on Logging and Reporting
Sessions matched by an Application Override policy will be logged with the overridden application name , not the name App-ID might have eventually assigned (or 'unknown'). This is beneficial for reporting and visibility if the override name is meaningful (e.g., 'internal-voip', 'erp-db-access'). However, logs will reflect the bypassed L7 inspection, and the lack of detailed application-specific threat logs for that session will be noticeable.
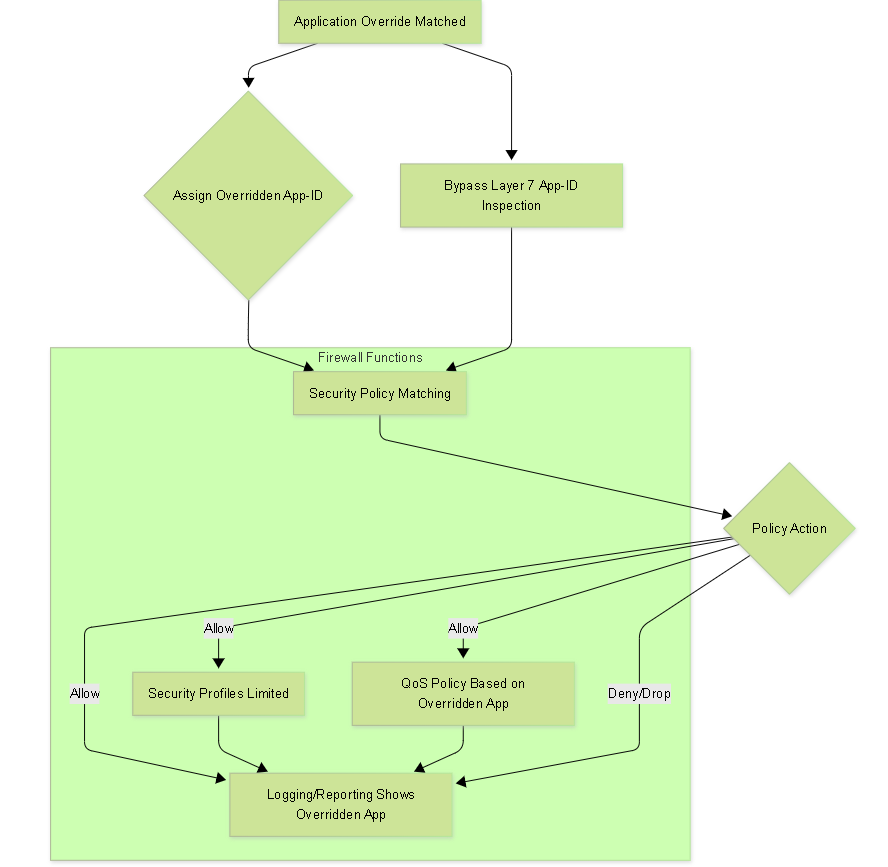
Impact of Application Override on Firewall Functions.
Caveats and Gotchas When Implementing Application Override
While useful, Application Override comes with pitfalls if not used correctly:
-
Loss of Security Visibility: The biggest gotcha is the bypass of L7 inspection. You lose the ability for App-ID to truly validate the traffic. If malicious actors send different traffic (e.g., exploit attempts, malware) over a port/protocol you've overridden for a legitimate internal app, the firewall won't identify it as malicious activity within that application context. It will simply see it as the overridden app.
-
Impact on Security Profiles: As discussed, Threat Prevention, URL Filtering, and File Blocking effectiveness is heavily reduced or negated for overridden traffic. This exposes the overridden traffic to risks that standard App-ID would help mitigate.
-
Broad Overrides Hide Problems: Overriding a common port like TCP 80 or 443 globally is almost always a mistake. This would prevent the firewall from identifying potentially malicious web traffic, command-and-control, or tunneling attempts running on those standard ports. Be very specific with Source/Destination zones and addresses.
-
Order of Operations: App Override policies are evaluated before Security policies. If a session matches an override, it will *never* be processed by the standard App-ID engine for that session, even if the traffic is later correctly identified by App-ID signatures on a different session.
-
Debugging Difficulty: If traffic doesn't behave as expected after implementing an override, troubleshooting can be harder because you've removed App-ID from the equation for that flow. Packet captures and session info (`show session all filter`) are crucial.
-
Maintaining Custom Apps: If you create many custom applications for overrides, managing them over time can become complex.
Gotcha: An Application Override policy matches based on L4 (Zone, Address, Service). It does NOT match on App-ID, as its purpose is to set the App-ID. The security policy *then* matches using the App-ID set by the override.
Best Practices for Using Application Override
To mitigate the risks and leverage the feature effectively:
-
Use Sparingly and Judiciously: Only use Application Override when strictly necessary – typically for custom, proprietary, or highly performance-sensitive internal applications running on known ports.
-
Be Specific with Matching Criteria: Never use 'any' for Source/Destination zones, addresses, or services if possible. Define the override rule with the narrowest possible scope (specific zones, subnets, individual IPs, exact ports, and protocols).
-
Create Meaningful Custom Applications: When overriding, create custom applications with descriptive names that clearly indicate the actual traffic (e.g., `internal-voip-signaling`, `corp-db-access-sql`). This improves logging, reporting, and policy readability.
-
Document Your Overrides: Keep clear documentation explaining why each override rule was created and what traffic it is intended to match.
-
Monitor Overridden Traffic: Regularly review logs for overridden traffic. While you lose detailed L7 security logs, session logs can confirm the override is matching the intended traffic and highlight unexpected volume or patterns.
-
Consider Security Policies Carefully: Understand that the security policy rule allowing the overridden application will have limited security profile effectiveness. Assess the risk of the overridden traffic and potentially implement alternative security controls if needed.
-
Review Regularly: Periodically review your Application Override policies to ensure they are still necessary and correctly configured. Applications or network needs may change.
-
Test Thoroughly: Always test overrides in a controlled environment before deploying to production, especially regarding impact on application function and performance.
Application Override and PCNSE/PCNSA Exam Relevance
Application Override is a moderately important topic for the PCNSE and PCNSA exams. It tests your understanding of how the firewall processes traffic, specifically the relationship between Layer 4 matching, App-ID, policy evaluation order, and the impact on security features.
Key concepts frequently tested:
-
Policy Evaluation Order: Understanding that Application Override policies are matched *before* Security policies and bypass standard App-ID.
-
Matching Criteria: Knowing that Application Override policies match on Layer 4 attributes (Zone, Address, User, Service) and *assign* an App-ID, they do not match on App-ID itself.
-
Impact on L7 Inspection: Recognizing that L7 App-ID inspection is bypassed for overridden traffic.
-
Impact on Security Profiles: Knowing that Threat Prevention, URL Filtering, and File Blocking are less effective or disabled for overridden traffic.
-
Use Cases: Identifying appropriate scenarios for using Application Override (custom apps, performance). Identifying inappropriate scenarios (overriding standard internet traffic).
-
Configuration Steps: Basic knowledge of where to configure Application Override rules and what parameters are required.
-
Custom Applications: Understanding that you often need to create a custom application object first.
Exam questions often present a scenario involving a specific application or traffic type and ask how to handle it, or ask about the consequences of using an override on security features.
Be prepared for questions that:
- Ask which policy rule type is evaluated first.
- Ask what traffic attributes an App Override rule matches.
- Present a list of security profiles and ask which ones are *least* effective when an override is used.
- Describe a custom application scenario and ask the recommended Palo Alto Networks approach (often involving a custom application and potentially an override).
- Ask how overridden traffic appears in logs.
Interactive Quiz: Application Override & App-ID
Test your knowledge on Palo Alto Networks Application Override and its interaction with App-ID and other features.