Converting Port/Protocol Rules to App-ID Rules
This article provides comprehensive information on transitioning Palo Alto Networks firewall security rules from traditional port and protocol-based enforcement to leveraging App-ID.
The Need for Migration
Migrating from legacy security rules based solely on ports and protocols (Layer 4) to rules leveraging App-ID (Layer 7) is a critical step in realizing the full security potential of a Palo Alto Networks firewall. Port-based rules are inherently insecure in modern networks because:
- Applications often use non-standard ports or hop between ports.
- Multiple applications can run over standard ports like TCP/80 (HTTP) and TCP/443 (SSL/TLS).
- Malicious actors deliberately disguise traffic by using well-known ports for C2 communication or data exfiltration.
Converting to App-ID rules provides true visibility and control over the actual applications traversing the network, significantly reducing the attack surface and enabling effective threat prevention.
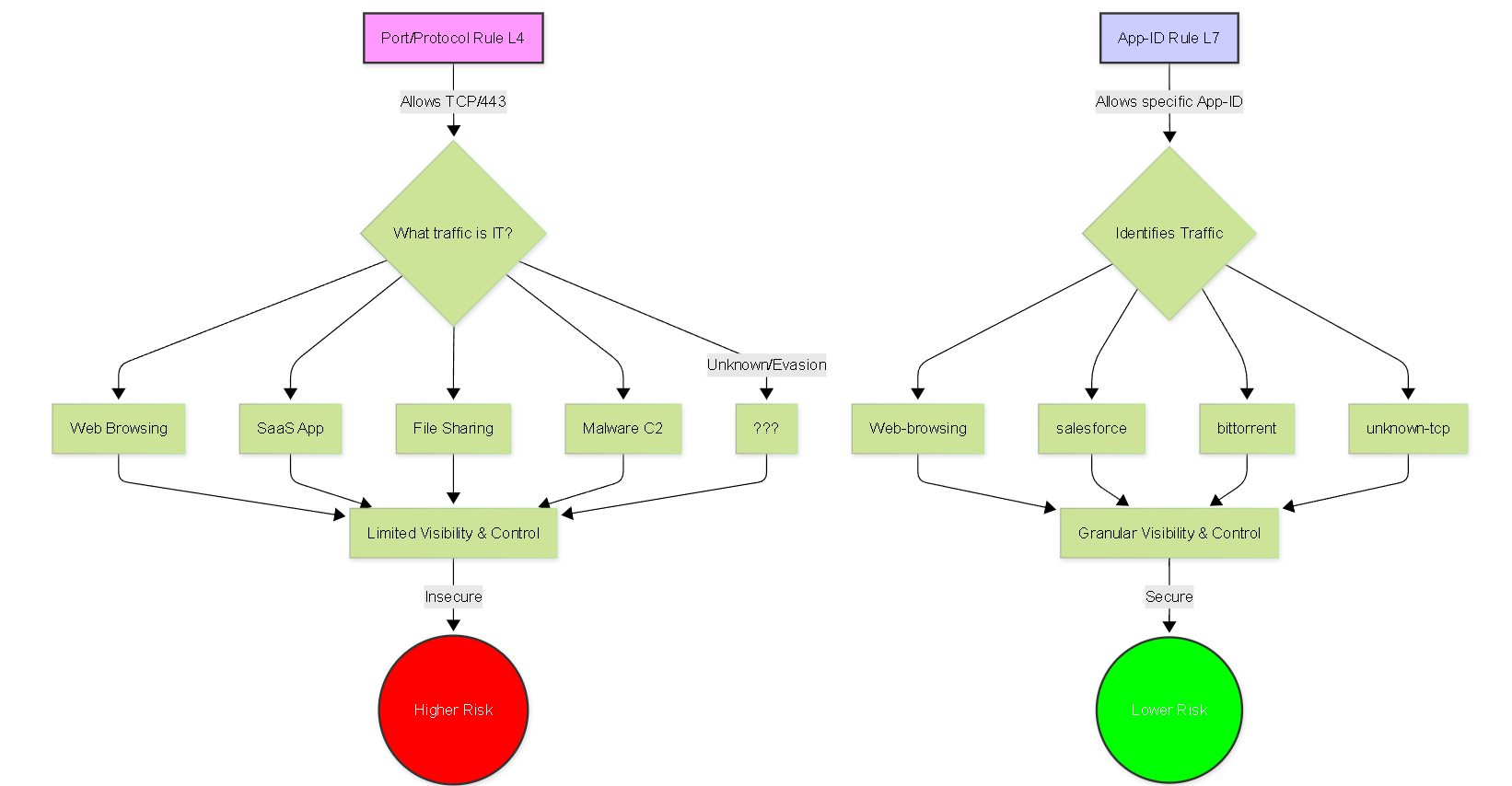
App-ID (L7) provides granular visibility and control over specific applications, unlike traditional Port/Protocol (L4) rules which allow any traffic using the permitted port, increasing risk.
The Challenge: Discovering Real Application Usage
The main challenge in conversion is accurately determining which applications are actually using the ports allowed by the legacy rules. A rule allowing TCP/443 might be intended for web browsing, but could also be carrying:
- Specific SaaS applications (Salesforce, Office 365)
- Social Media
- File Sharing applications tunneling over SSL
- Collaboration tools
- Potentially malicious C2 traffic
Simply replacing
service-https
with App-ID
ssl
or
web-browsing
in a rule is often insufficient and doesn't achieve the desired granularity or security improvement. A methodical approach involving discovery is required.
Methodology for Conversion
A phased approach is recommended for converting port-based rules to App-ID rules:
Phase 1: Discovery and Analysis
Goal: Identify the specific applications currently traversing the network using the ports allowed by legacy rules.
Methods:
-
Analyze Traffic Logs:
Filter logs based on the legacy port-based rule(s) and examine the
Applicationcolumn. This shows what App-ID has identified even on port-based rules. - Use ACC (Application Command Center): Visualize application traffic passing through specific rules or using specific ports/services. Look for unexpected applications on standard ports.
- Run Reports: Generate custom reports focusing on traffic hitting specific port-based rules, showing application distribution.
- Leverage Policy Optimizer: Use the built-in tool designed for this purpose (see details below).
-
Temporary Monitoring Rules (Optional):
Clone the port-based rule, set the Application to
any, Service to the original port(s), Action toAllow, and enable logging. Place it below the original rule (or temporarily disable the original) to capture and log all applications trying to use that port. Analyze these logs carefully.
Phase 2: Create App-ID Based Rules
Goal: Build new Security Policy rules that explicitly allow the identified, required applications discovered in Phase 1.
Best Practices:
- Create new rules using specific App-IDs, Application Groups, or Filters based on your analysis.
-
Set the Service to
application-defaultwhenever possible. Only use specific ports if absolutely required for custom/non-standard applications. - Place these new App-ID rules above the legacy port-based rule they are intended to replace.
- Handle application dependencies appropriately (often implicit, sometimes needs explicit rules).
-
Consider rules for unidentified traffic (App-ID
unknown-tcp,unknown-udp). Decide whether to allow (with caution/inspection) or block it.
Phase 3: Validation, Refinement, and Cleanup
Goal: Ensure the new App-ID rules work as intended and safely remove the legacy rules.
Methods:
- Monitor Hit Counts: After committing the new App-ID rules (placed above the legacy rule), monitor their hit counts. Traffic should start hitting the new rules.
- Monitor Legacy Rule Hit Count: The hit count on the legacy port-based rule (now below the App-ID rules) should decrease significantly or drop to zero.
- Analyze Logs: Check logs for the new App-ID rules to confirm expected traffic. Also check logs for denied traffic to see if any required applications were missed.
- Refine Rules: Adjust App-ID rules based on monitoring (e.g., add a missed application, correct a dependency).
- Disable Legacy Rule: Once confident, disable (don't delete yet!) the legacy port-based rule. Monitor for any issues or user complaints.
- Delete Legacy Rule: After a suitable observation period with the legacy rule disabled, delete it.
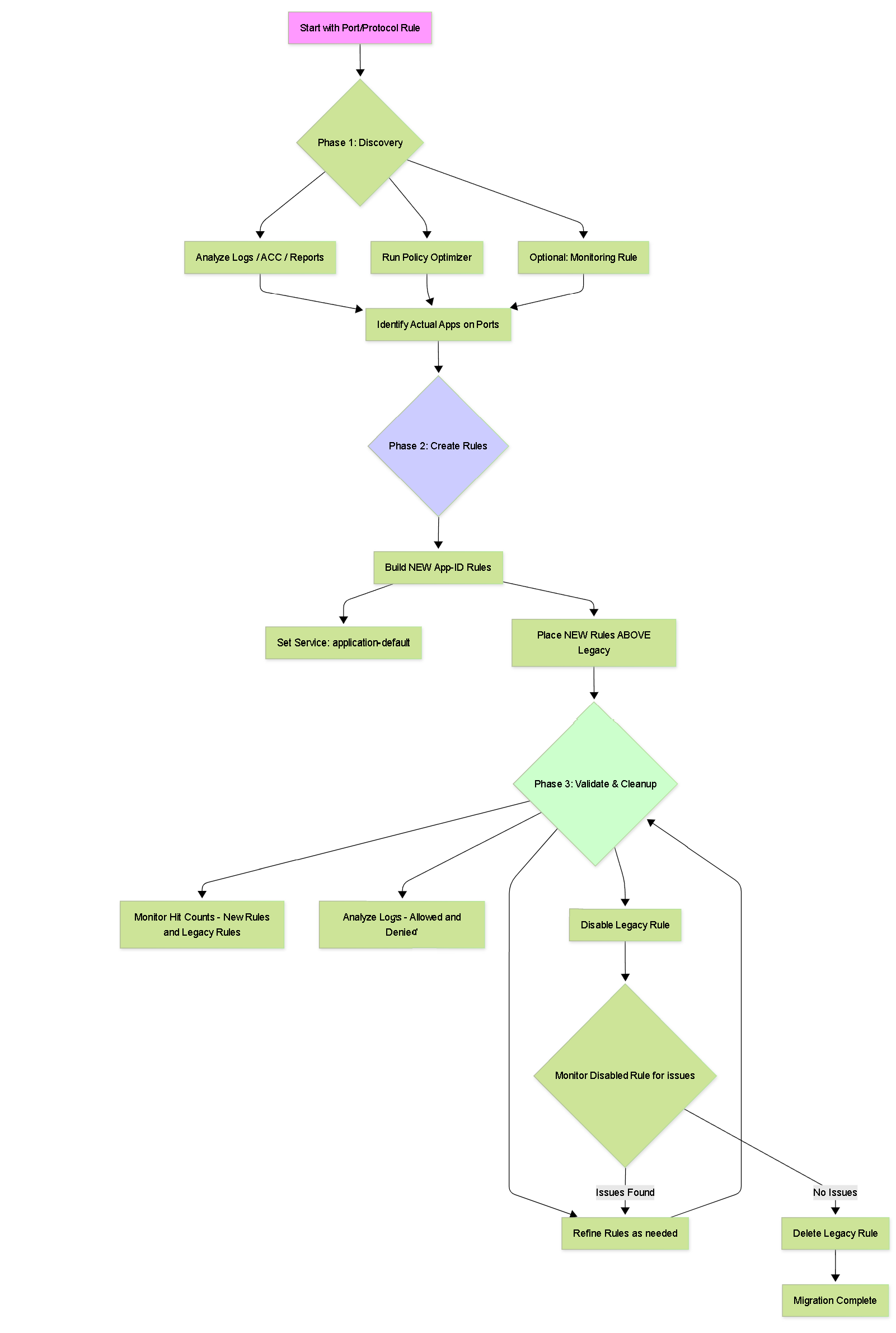
Recommended phased migration methodology from Port/Protocol to App-ID.
Tools for Discovery and Conversion
Palo Alto Networks firewalls provide several tools to assist with the conversion process.
1. Traffic Logs, ACC, and Reports
What they do: Provide raw data and visualizations of actual network traffic.
How to use for conversion:
-
Filter Traffic logs on a specific port-based Security Rule name or policy ID (
(rule eq 'Legacy-Web-Allow')). Examine the 'Application' column for traffic hitting that rule. -
Use the ACC tab, filtering by Rule or Service (e.g.,
service-https), and view the Applications widget to see the distribution of App-IDs using that port. - Create custom Reports (Monitor > Manage Custom Reports) to aggregate application usage data over time for specific rules or services.
Pros: Uses built-in tools, provides direct visibility into actual traffic.
Cons: Can be time-consuming to analyze manually, requires effective filtering and interpretation.
2. Policy Optimizer (Built-in Tool)
What it does: Specifically designed to aid in migrating port-based rules to App-ID rules and identifying unused rules.
Location: Policies > Policy Optimizer
Key Features for Conversion:
-
No App Specified / Port-Based Rules:
Identifies rules where the Application field is set to
anybut the Service is specific (port-based). - Apps Seen: Shows the actual applications (App-IDs) that have matched a specific port-based rule based on traffic logs over a configurable time period (e.g., last 30 days).
- Suggested Apps: Recommends which App-IDs could be added to the rule based on the observed traffic.
- Rule Conversion: Provides options to directly add suggested App-IDs to the existing rule or clone the rule with the new App-IDs.
Pros: Highly effective, integrated, directly analyzes rule usage vs. logs, simplifies identification, provides direct modification options.
Cons: Relies on historical log data; if an application hasn't run recently, it won't be seen. Still requires administrator review and validation before converting rules.
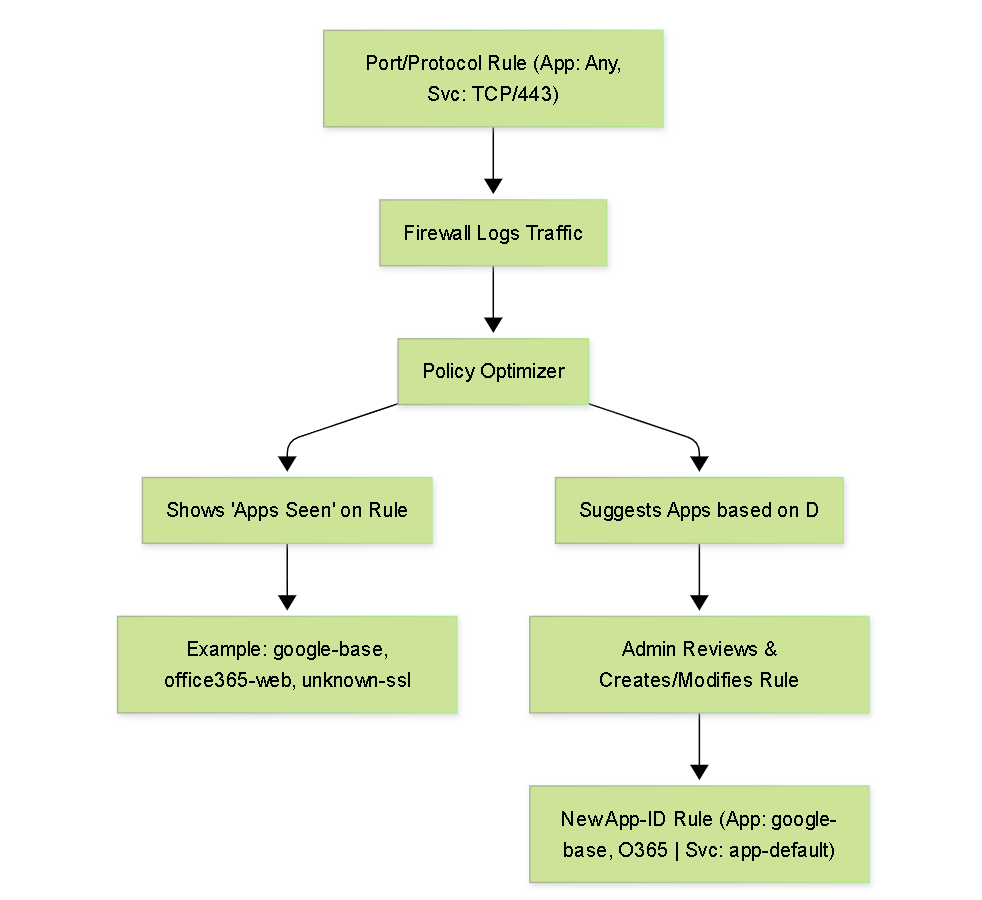
Simplified Policy Optimizer workflow for converting port-based rules.
3. Expedition Migration Tool
What it is: A free, powerful, standalone tool provided by Palo Alto Networks (runs as a VM or container) designed for complex configuration analysis, migration, and best practice implementation.
How to use for conversion:
- Import firewall configurations (PAN-OS or other vendors).
- Analyze existing rulebases for port-based rules.
- Correlate configuration with imported traffic logs (optional but recommended) to see actual application usage.
- Provides sophisticated rule merging, object cleanup, and best-practice recommendations.
- Can automate the generation of App-ID based rules based on its analysis.
- Outputs configuration changes that can be imported back into Panorama or the firewall.
Pros: Very powerful for large/complex environments, multi-vendor migrations, advanced analysis, automation capabilities.
Cons: Requires separate setup and learning curve, more complex than Policy Optimizer, processing can take time for large configs/logs. Often overkill for simple conversions but invaluable for large migrations.
Best Practices Summary
Follow these best practices for a smooth and secure transition:
- Analyze Before Converting: Don't guess; use logs, ACC, Policy Optimizer, or Expedition to see what's really using the ports.
- Prioritize application-default: Use this service setting whenever possible for enhanced security.
- Start Specific: Create rules for known, required applications first.
-
Handle Unknown/Unidentified:
Decide on a policy for
unknown-tcp/unknown-udptraffic (often deny or allow with strict profiles). - Use New Rules: Create new App-ID rules above the legacy ones; avoid simply modifying the legacy rule initially.
- Decrypt Where Needed: Implement SSL/TLS decryption for visibility into encrypted flows.
- Log Everything: Ensure both the new App-ID rules and potentially denied traffic are logged.
- Test and Validate: Monitor hit counts and logs carefully after changes.
- Cleanup Systematically: Disable, then delete legacy rules only after confirming the new App-ID rules handle the required traffic.
- Leverage Tools: Use Policy Optimizer regularly; consider Expedition for larger projects.
PCNSE Exam Focus
For the PCNSE exam, regarding rule conversion:
- Understand the why (security benefits of App-ID).
- Know the methodology (discovery, creation, validation, cleanup).
- Be familiar with the tools used for discovery, especially Policy Optimizer (its purpose and basic function) and the role of log/ACC analysis. Know that Expedition is a more advanced migration tool.
-
Recognize the importance of
application-default. - Understand the best practice of creating new rules above legacy ones during migration.
- Know that validating hit counts and logs is crucial before removing old rules.
App-ID Conversion Quiz (PCNSE Focus)
Test your knowledge on converting port/protocol rules to App-ID.