-
License Activation (VM-Series, PA-1400, PA-3400):
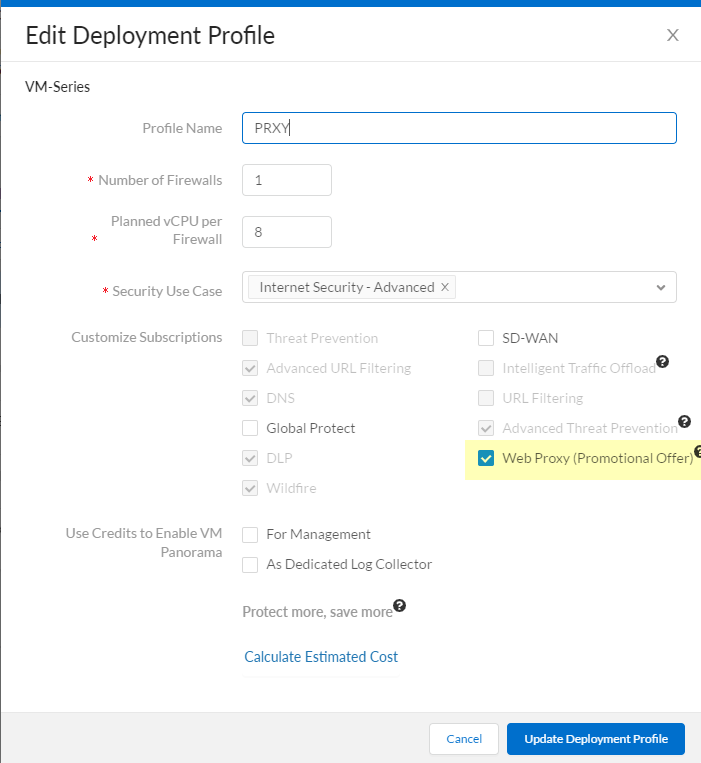
For specific models like VM-Series, PA-1400, and PA-3400, the web proxy feature requires license activation.
- VM-Series: Log in to the Customer Support Portal (CSP), edit the relevant deployment profile, select Web Proxy (Promotional Offer) or the appropriate license, and click Update Deployment Profile .
-
On the firewall, retrieve the license keys from the server (
Device > Licenses > Retrieve license keys from license server). Restart if retrieval fails initially. - PA-1400/PA-3400: Follow standard subscription license activation steps ( Activate Subscription Licenses ).
-
Set Up Interfaces and Zones:
Configure the necessary interfaces. Best practice is to use Layer 3 interfaces, each in its own zone within the same virtual router.
-
Client Interface:
Interface facing the clients whose traffic will be proxied (e.g.,
ethernet1/1in zoneTrust). -
Internet Interface:
Interface facing the internet/external network (e.g.,
ethernet1/2in zoneUntrust). -
Proxy Loopback Interface:
Configure a dedicated Loopback interface (e.g.,
loopback.1). Assign it an IP address (e.g.,192.168.254.254/32) and place it in its own zone (e.g.,Proxy-Zone) within the same virtual router as the client and internet interfaces. This loopback IP is where client traffic will be redirected via NAT. Note down this IP address.
-
Client Interface:
Interface facing the clients whose traffic will be proxied (e.g.,
-
Set Up DNS Proxy:
Configure DNS Proxy to handle DNS requests intercepted by the proxy function.
-
Configure a
DNS Proxy Object
(
Network > DNS Proxy). Enable it on the interface facing the clients (e.g.,ethernet1/1). -
Configure a
DNS Server Profile
(
Device > Server Profiles > DNS) specifying Primary and Secondary DNS servers. - (Note: While the text mentions specifying the loopback interface for the proxy connection in DNS setup, typically DNS Proxy is enabled on the client-facing interface, and the firewall uses its standard routing/Service Routes to reach external DNS servers).
Ensure reliable DNS resolution is available for the firewall.
-
Configure a
DNS Proxy Object
(
-
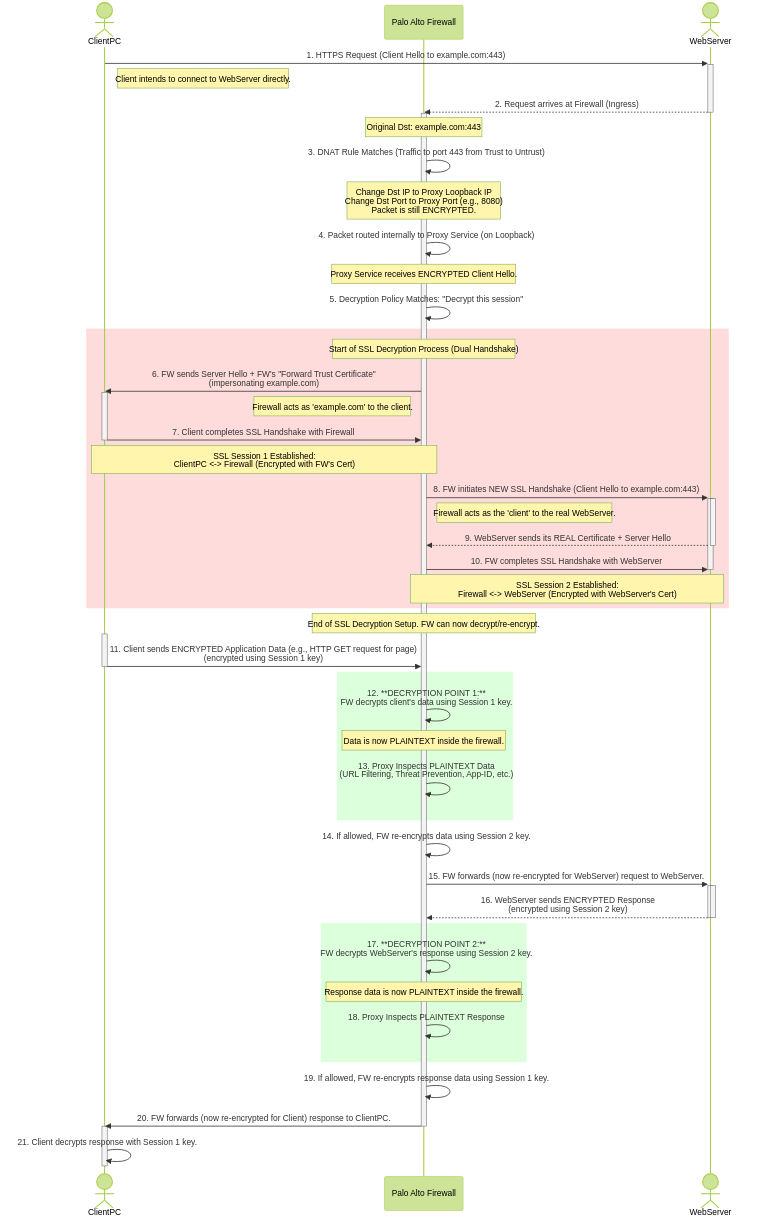
(Optional) Certificate Setup for Decryption:
If you intend to decrypt HTTPS traffic intercepted by the transparent proxy (which is essential for full visibility), configure SSL Forward Proxy. This involves generating/importing a Forward Trust CA certificate and deploying it to clients. Refer to SSL Forward Proxy documentation for details.
(See Create a Self-Signed Root CA Certificate or use an Enterprise CA).
-
Enable Transparent Proxy Mode:
-
Navigate to
Network > Proxy. -
Click
Editfor Proxy Enablement . - Select Transparent Proxy as the Proxy Type .
-
Click
OK.
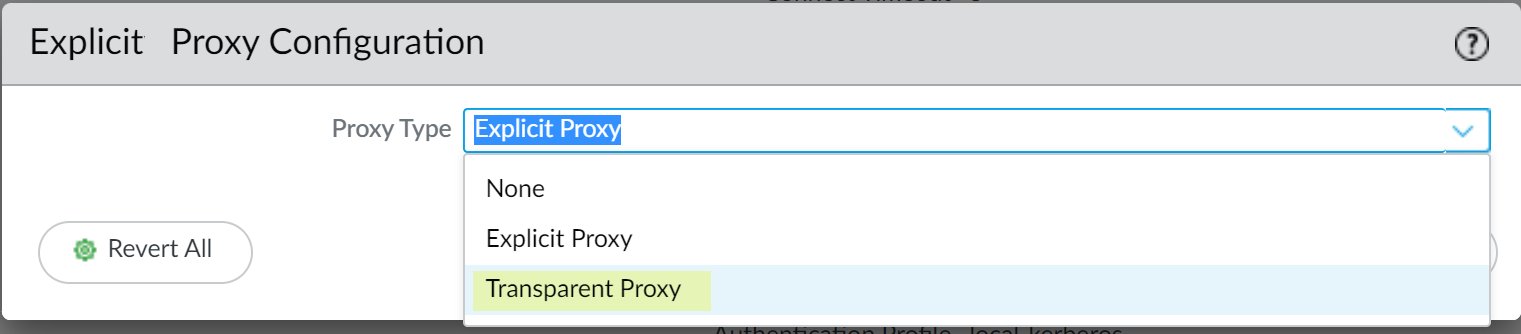
If 'Transparent Proxy' is not an option, verify the license activation (Step 1).
-
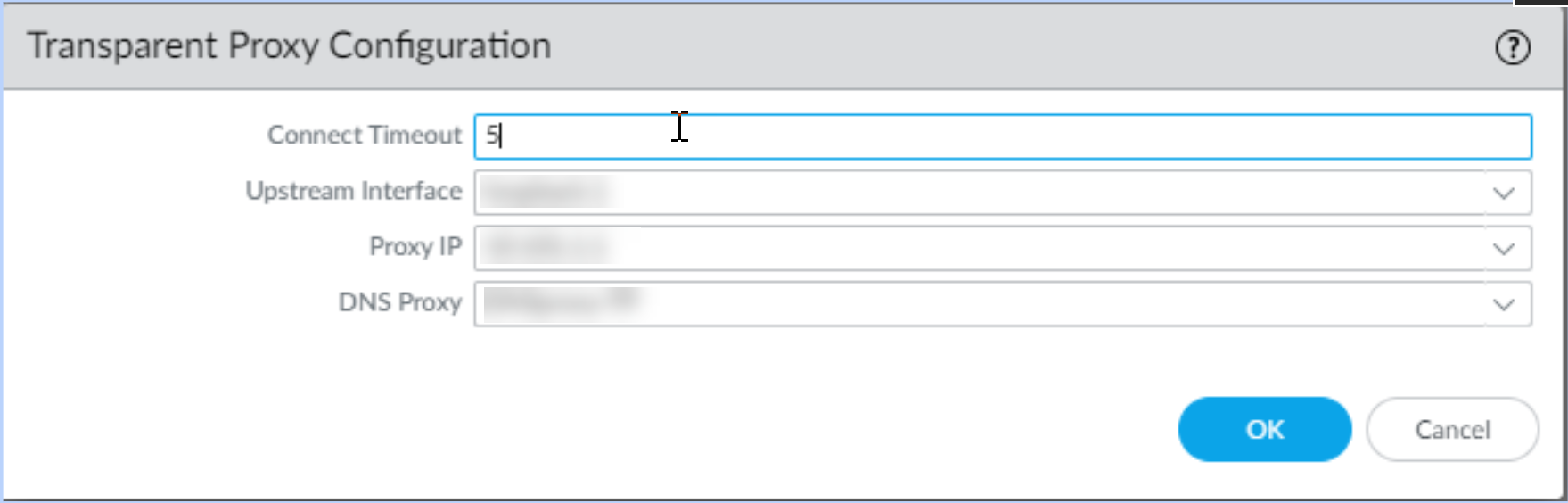
Click
Editfor Transparent Proxy Configuration . - Specify the Connect Timeout (seconds the proxy waits for server response, default usually fine).
-
Select the
Upstream Interface
: Choose the dedicated
Loopback interface
created in Step 2 (e.g.,
loopback.1). - Enter the IP address of the loopback interface as the Proxy IP .
- Select the DNS Proxy object created in Step 3.
-
Click
OK.
-
Navigate to
-
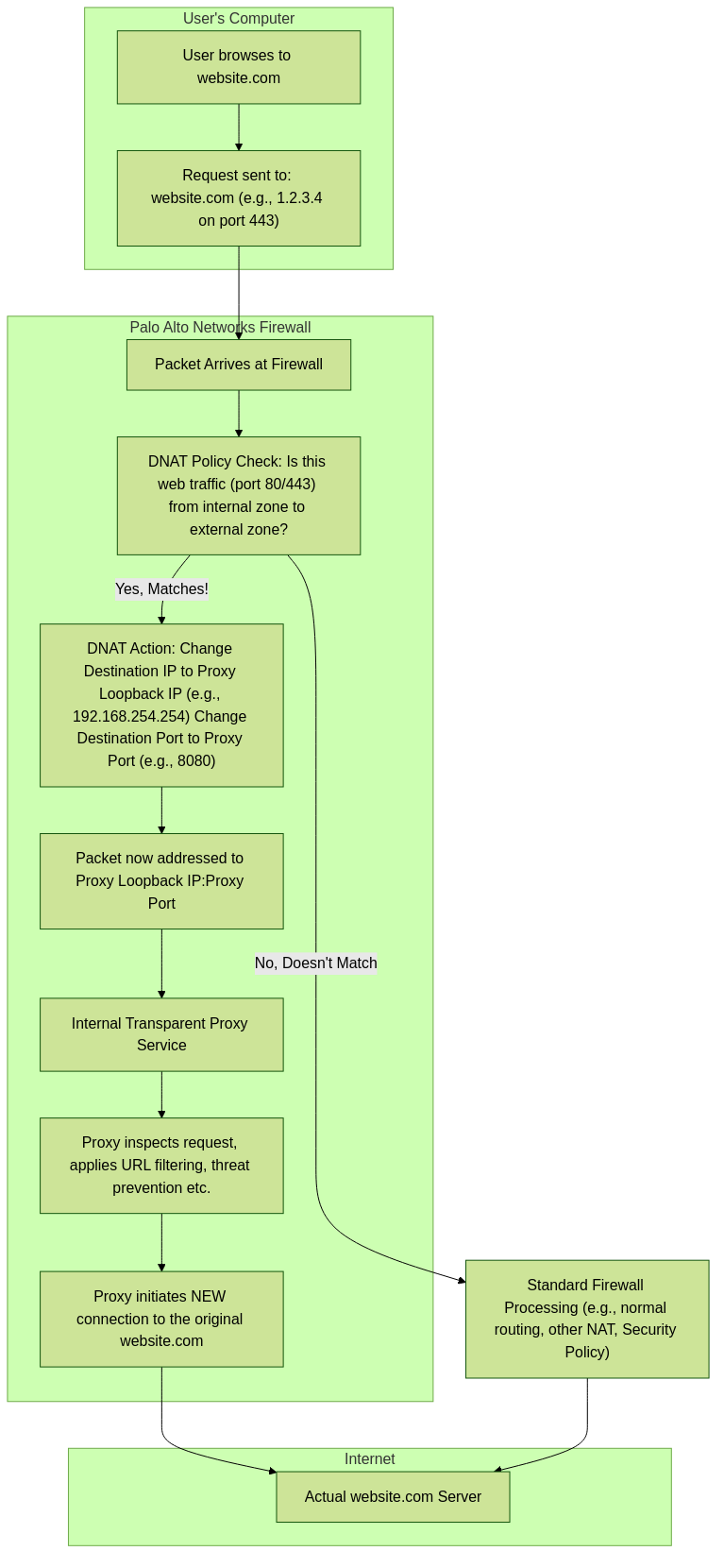
Configure Destination NAT (DNAT) Policy (CRITICAL):
This rule redirects the client's original web request (port 80/443) to the proxy loopback interface.
-
Navigate to
Policies > NATandAdda NAT rule. - Place this rule before any general outbound Source NAT (SNAT) rules.
-
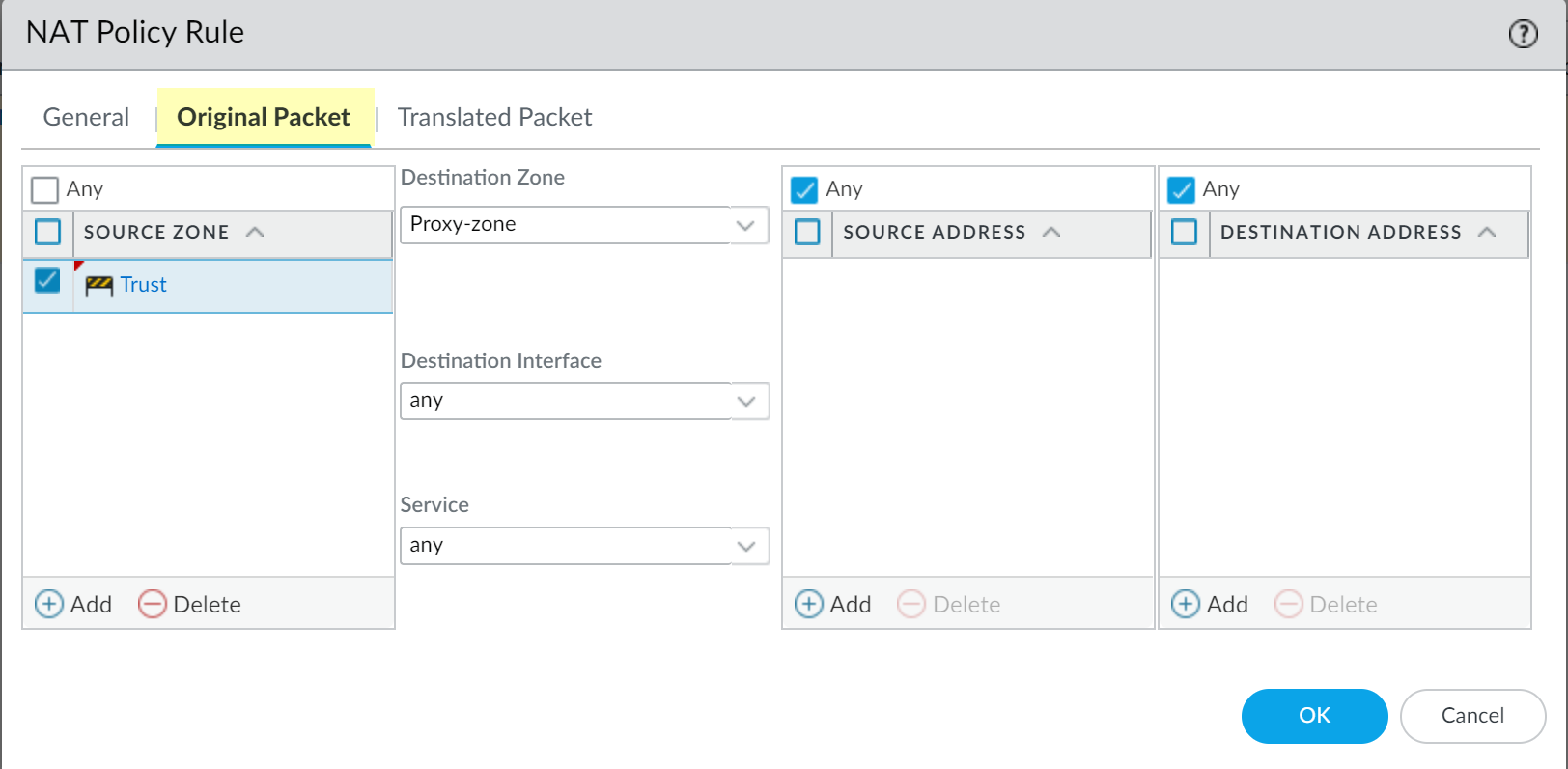
Original Packet Tab:
-
Source Zone: Zone containing clients (e.g.,
Trust). -
Destination Zone: Zone facing the internet (e.g.,
Untrust). - Destination Interface: Any (or specific external interface).
-
Service: Typically
service-httpandservice-https(or a service group containing TCP/80, TCP/443). - Destination Address: Any (or specific external destinations if limiting scope).
-
Source Zone: Zone containing clients (e.g.,
-
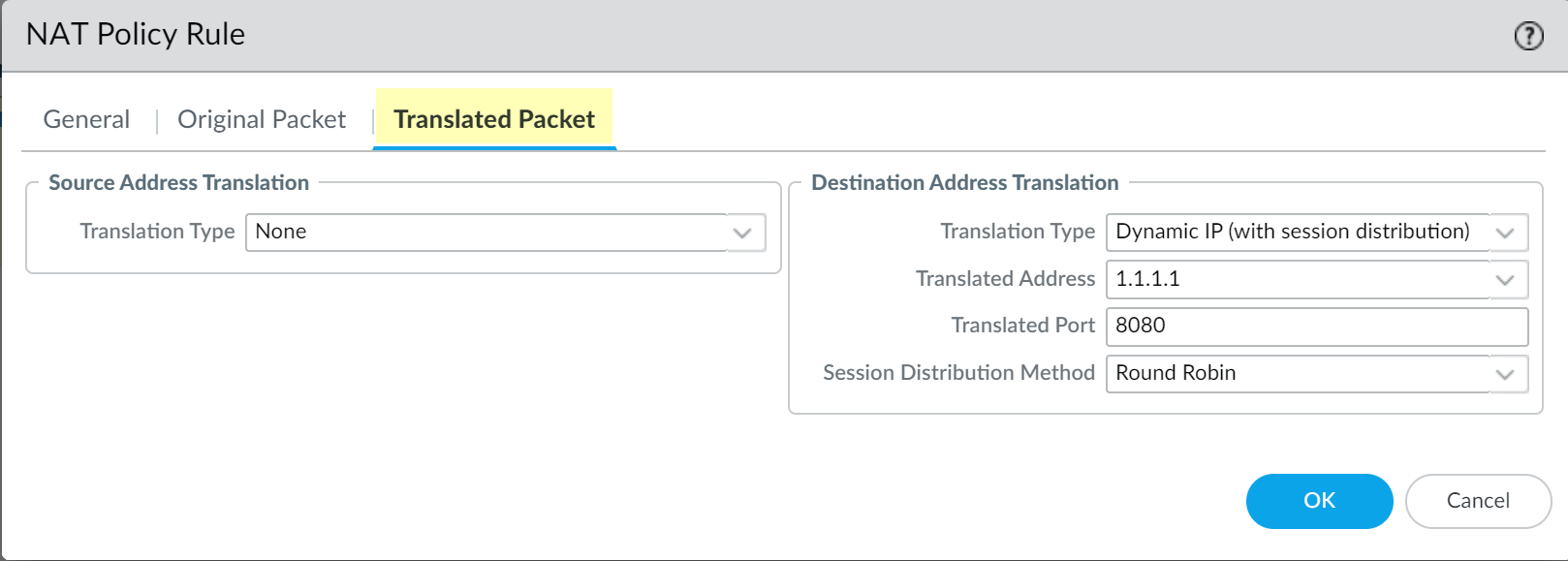
Translated Packet Tab:
-
Source Address Translation: Set Type to
None(No SNAT in this rule). -
Destination Address Translation:
-
Set Translation Type to
Dynamic IP (with session distribution)(or Static IP if preferred, DIPP generally suitable here). -
Set
Translated Address
to the IP address of the
Proxy Loopback interface
(e.g.,
192.168.254.254). -
Set
Translated Port
to the port the transparent proxy listener expects (typically
8080). -
Session Distribution: Can usually be left as default (e.g.,
Round Robin- not strictly applicable here but required field).
-
Set Translation Type to
-
Source Address Translation: Set Type to
-
Click
OK.
-
Navigate to
-
Configure Supporting Security Policies:
Multiple rules are needed to allow the complete flow:
- Client to Proxy Zone: Allow traffic from the client zone (e.g., `Trust`) to the Proxy Loopback zone (`Proxy-Zone`) for destination port 8080 (or the configured proxy port). Apply relevant Security Profiles here for initial inspection before traffic leaves the firewall.
- Proxy Zone to Internet: Allow traffic originating from the Proxy Loopback zone (`Proxy-Zone`) to the internet zone (`Untrust`). Apply necessary Security Profiles (URL Filtering, Threat Prevention, etc.) here for outbound inspection.
- DNS Access: Ensure both clients (via DNS Proxy) and the firewall itself (potentially via the Proxy Loopback interface or another Service Route) can reach necessary DNS servers.
-
Configure Source NAT (SNAT) Policy:
- Create a standard outbound SNAT rule (placed *after* the DNAT rule) to translate traffic originating from the Proxy Loopback zone going to the internet (`Untrust` zone) to use an appropriate external IP address (e.g., the firewall's external interface IP).
-
(Optional) Configure Decryption Policy:
- If inspecting HTTPS, create Decryption Policy rules (as described in SSL Forward Proxy documentation) matching traffic from the client zone (`Trust`) to the internet zone (`Untrust`) for Service `service-https`.
-
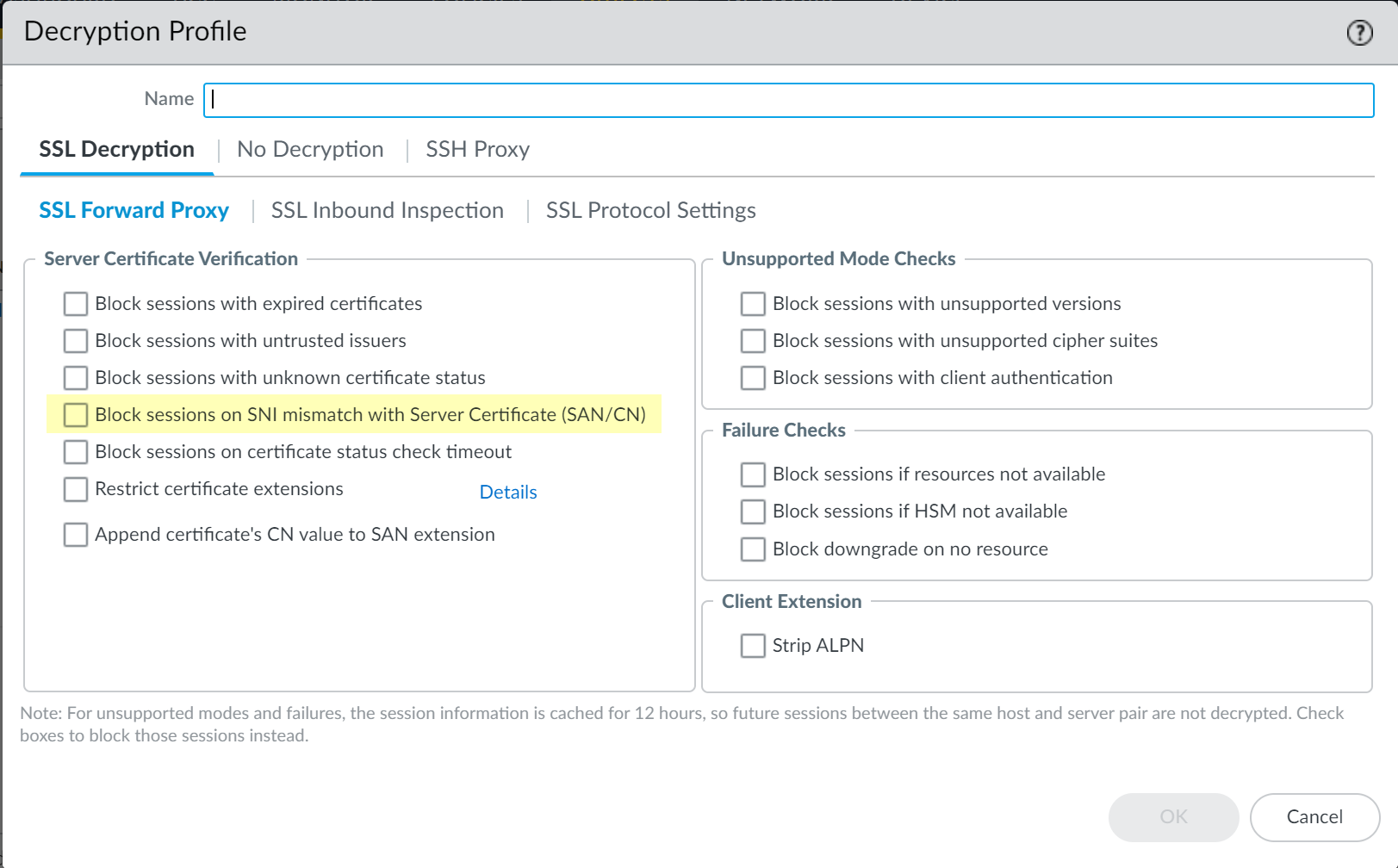
(Optional but recommended) In the Decryption Profile (
Objects > Decryption Profile > SSL Decryption > SSL Forward Proxy), check Block sessions on SNI mismatch with Server Certificate (SAN/CN) for added security.
-
Commit Changes:
Commit the configuration. The documentation suggests making a minor change in DNS Proxy and Interface settings and committing again if this is the initial setup to ensure all settings populate correctly (this might be less necessary in modern versions but worth noting).