PAN-OS: Configuring Decryption Logging
Importance of Decryption Logging
When you implement SSL/TLS Decryption (either Forward Proxy or Inbound Inspection), enabling appropriate logging is crucial for visibility, troubleshooting, and compliance. Decryption logs provide insights into:
-
Which sessions were successfully or unsuccessfully decrypted.
-
Reasons for decryption failures (e.g., untrusted issuer, unsupported cipher).
-
Certificates involved in the sessions.
-
Errors encountered during the decryption process.
This information helps administrators verify that decryption policies are working as intended, identify applications or sites causing issues with decryption, and investigate potential security incidents related to encrypted traffic.
Configuration Steps
Step 1: Enable Logging in Decryption Policy Rules
-
Configure the decryption traffic you want to log in a
decryption policy rule
(
Policies > Decryption
).
By default, the NGFW logs only unsuccessful TLS handshakes:
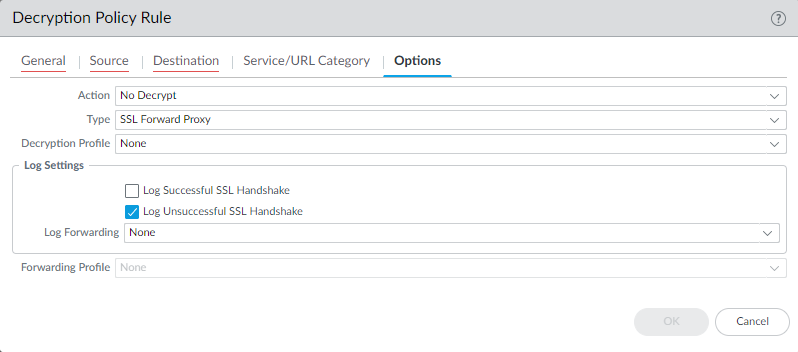
Log successful handshakes as well as unsuccessful handshakes to gain visibility into as much decrypted traffic as your device’s available
resources
permit.
Best Practice:
Log successful handshakes for decryption rules to gain visibility, but be prepared to manage the increased log volume (see Step 3). Follow
decryption best practices
and decrypt as much traffic as is feasible and appropriate.
Step 2: Configure Log Forwarding (Optional but Recommended)
-
Create a
Log Forwarding profile
to forward decryption logs to log collectors, other storage devices, or specific administrators, and then specify the profile in the
Log Forwarding
field of the decryption policy rule
Options
tab.
To forward decryption logs, you must configure a Log Forwarding profile (
Objects > Log Forwarding
) to specify the decryption
Log Type
and method of
forwarding the logs
.
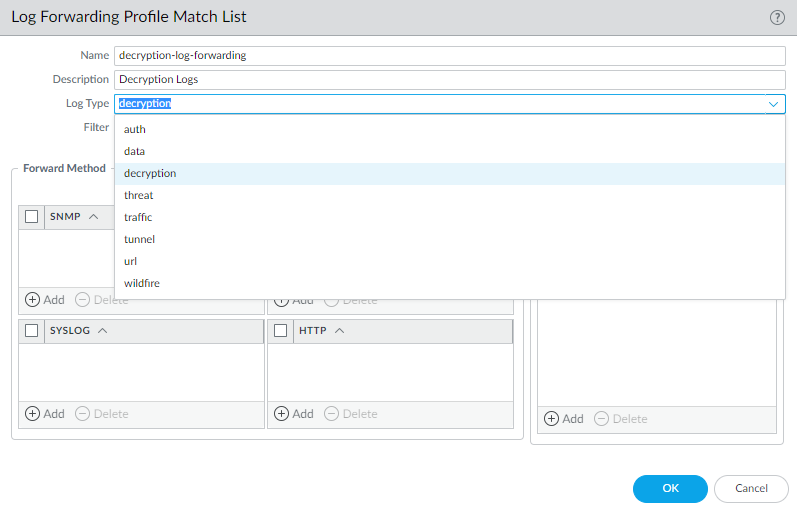
Store forwarded decryption logs securely because they contain sensitive information.
Step 3: Configure Log Storage Quotas (If Logging Locally)
-
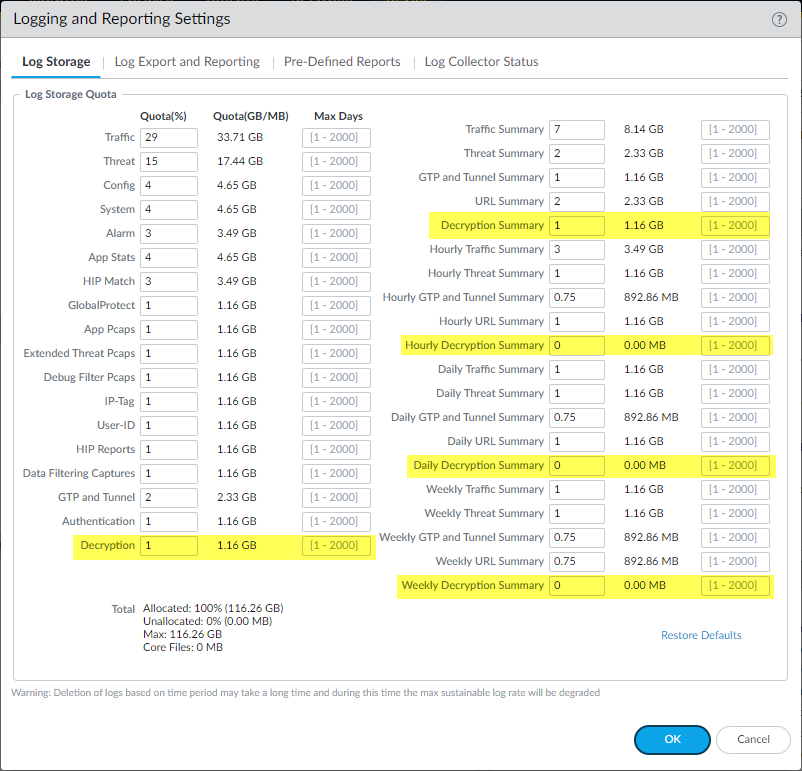
If you log successful TLS handshakes in addition to unsuccessful TLS handshakes, configure a larger log storage space quota (
Device > Setup > Management > Logging and Reporting Settings > Log Storage
) for decryption logs.
The default quota (allocation) is one percent of the device’s log storage capacity for decryption logs and one percent for the general decryption summary. There is no default allocation for hourly, daily, or weekly decryption summaries.
Many factors determine the amount of storage you might need for decryption logs and they depend on your deployment. For example, take these factors into account:
-
The amount of TLS traffic that passes through the NGFW.
-
The amount of TLS traffic that you decrypt.
-
Your usage of other logs (evaluate from which logs you should take capacity to allocate to decryption logs).
-
If you log both successful and unsuccessful TLS handshakes, you probably need more capacity than you need to only log unsuccessful TLS handshakes. Depending on the amount of traffic you decrypt, decryption logs could consume as much capacity as Traffic logs or Threat logs and may require a tradeoff among them if the device’s capacity is fully subscribed.
The total combined allocation of log quotas cannot exceed 100% of the available NGFW log resources.
You may need to experiment to find the right quota for each log category in your particular deployment. If you only log unsuccessful handshakes, you could start with the default or increase the allocation to two or three percent. If you log both successful and unsuccessful handshakes, you could start by allocating about half of the space to decryption logs that you allocate to Traffic logs. The logs from which you take the space to allocate to decryption logs depends on your traffic, your business, and your monitoring requirements.
PCNSE Exam Focus
For the PCNSE exam, understand:
-
Where to enable logging for decrypted sessions: within the
Actions tab of Decryption Policy rules
.
-
The difference between logging successful vs. unsuccessful TLS handshakes and the visibility implications.
-
The
default logging behavior
(only unsuccessful handshakes).
-
That Log Forwarding requires creating a
Log Forwarding Profile
(selecting Log Type `Decryption`) and applying it to the Decryption Policy rule.
-
Where local log storage quotas are configured:
Device > Setup > Management > Logging and Reporting Settings
.
-
The necessity of
increasing the default Decryption log quota
if logging successful handshakes.
-
The factors that influence required log storage space.


