How to Configure a Decrypt Mirror Port
Overview
PAN-OS 6.0 introduced a feature to create a copy of decrypted traffic and send it to a mirror port, which enables raw packet captures of the decrypted traffic for archiving and analysis.
To enable Decryption Mirroring, you must obtain and install a Decryption Port Mirror license.
The license is free of charge and can be activated through the support portal as described in the following procedure.
After you install the Decryption Port Mirror license and reboot the firewall, you can enable decryption port mirroring.
Steps
-
Activate the "Decryption Port Mirror" license. Go to Device > Licenses:
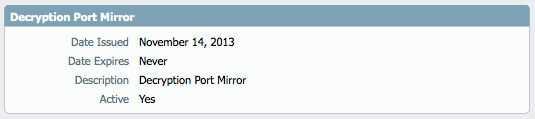
-
Reboot the device.
-
After the reboot completes, choose a free interface. Go to Network > Interfaces to use as port mirror interface:
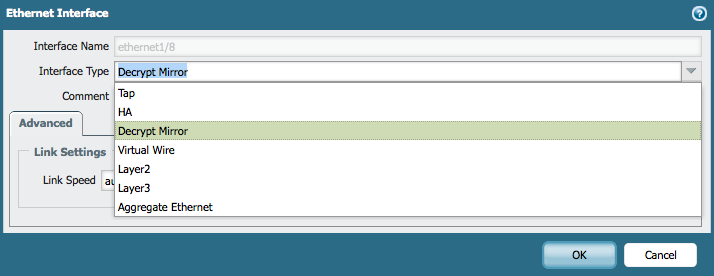
-
Create a Decryption Profile. Go to Objects > Decryption Profile. In this profile, specify which interface the decrypted traffic needs to send.
When configuring the Decryption profile on Panorama, the shared checkbox cannot be ticked.
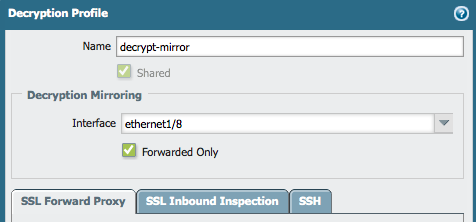
-
Apply the decryption profile to the SSL Decryption Policy or Policies:
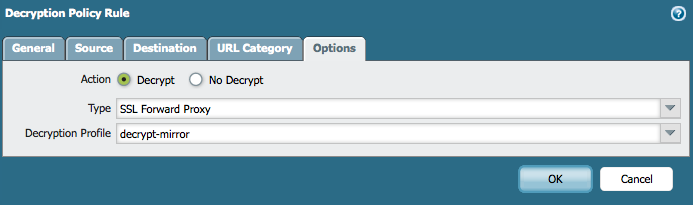
-
Allow forwarding of Decrypted Content. Go to Device > Setup > Content-ID:
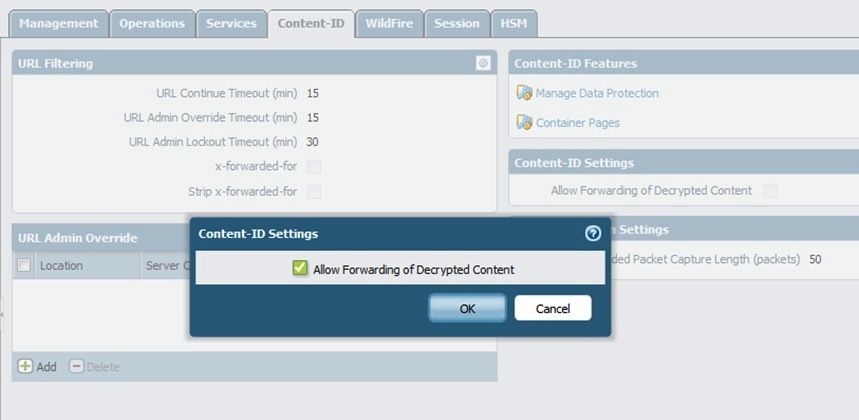
-
Commit the configuration.
All traffic that matches the SSL Decryption Policy will be decrypted and forwarded to the mirror port, which is ethernet 1/8 in the above example.
Multi-VSYS Configuration
When creating a new VSYS, select the option "Allow Forwarding of Decrypted Content," which is shown below. The rest of the configuration is the same as for a single VSYS environment.
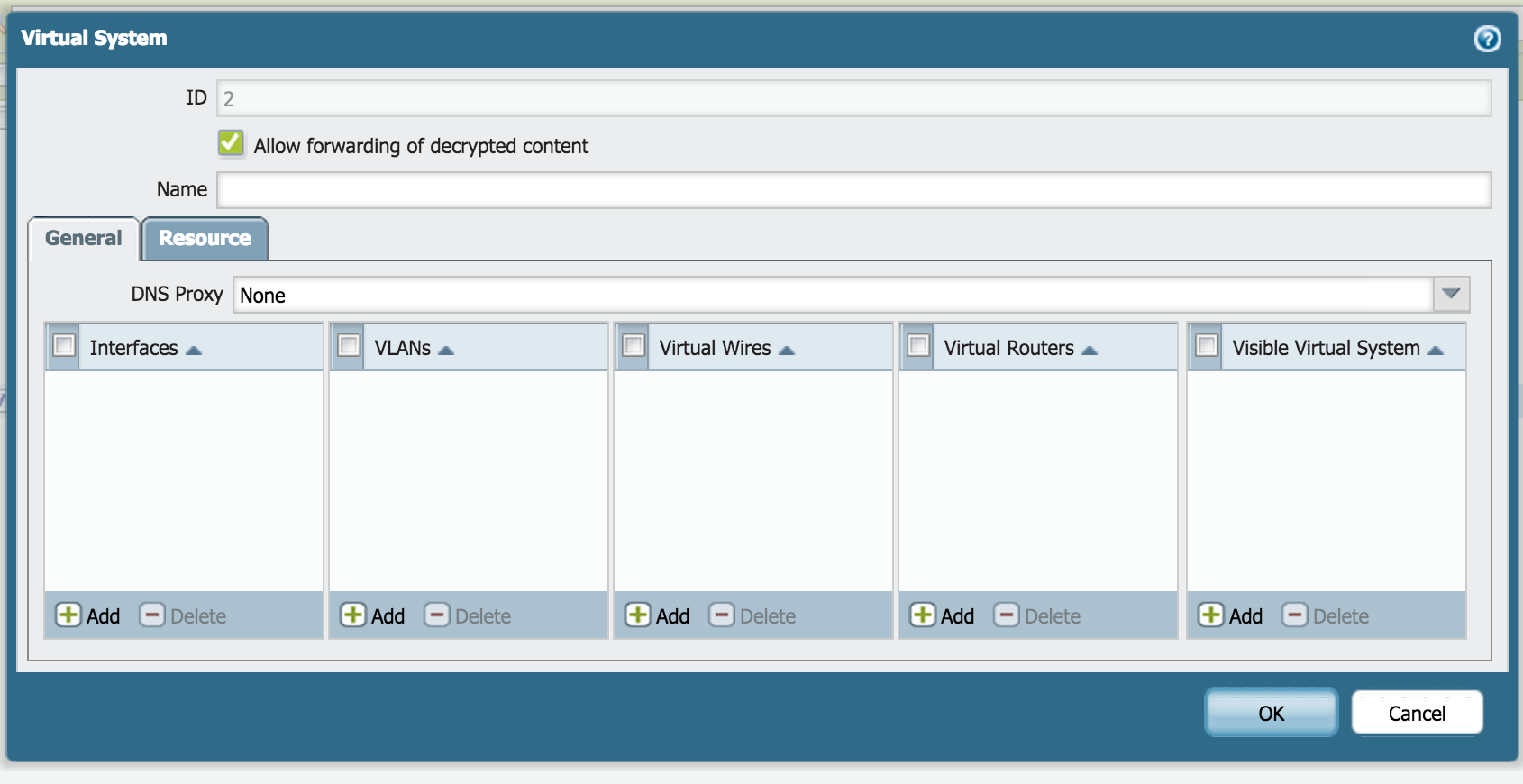
Verification
After the setup is complete, the sessions that are marked for decryption will be forwarded to the designated port.
This can be verified in the session table by filtering all the sessions that are decrypt-mirrored:
> show session all filter decrypt-mirror yes
--------------------------------------------------------------------------------
ID Application State Type Flag Src[Sport]/Zone/Proto (translated IP[Port])
Vsys Dst[Dport]/Zone (translated IP[Port])
--------------------------------------------------------------------------------
33557112 web-browsing ACTIVE FLOW *NS 10.193.91.111[55193]/Untrust/6 (10.193.88.91[28832])
vsys1 216.58.209.224[443]/Untrust (216.58.209.224[443])
33557161 web-browsing ACTIVE FLOW *NS 10.193.91.111[55241]/Untrust/6 (10.193.88.91[6770])
vsys1 216.58.209.238[443]/Untrust (216.58.209.238[443])
33557106 web-browsing ACTIVE FLOW *NS 10.193.91.111[55190]/Untrust/6 (10.193.88.91[1490])
vsys1 216.58.209.230[443]/Untrust (216.58.209.230[443])
33557131 web-browsing ACTIVE FLOW *NS 10.193.91.111[55207]/Untrust/6 (10.193.88.91[44665])
vsys1 74.125.71.94[443]/Untrust (74.125.71.94[443])
33557084 web-browsing ACTIVE FLOW *NS 10.193.91.111[55170]/Untrust/6 (10.193.88.91[34083])
vsys1 204.79.197.203[443]/Untrust (204.79.197.203[443])
33557166 web-browsing ACTIVE FLOW *NS 10.193.91.111[55244]/Untrust/6 (10.193.88.91[50576])
vsys1 216.58.209.226[443]/Untrust (216.58.209.226[443])
33557086 facebook-social-plugin ACTIVE FLOW *NS 10.193.91.111[55172]/Untrust/6 (10.193.88.91[55838])
vsys1 31.13.93.3[443]/Untrust (31.13.93.3[443])
33557135 youtube-base ACTIVE FLOW *NS 10.193.91.111[55210]/Untrust/6 (10.193.88.91[31302])
vsys1 216.58.209.224[443]/Untrust (216.58.209.224[443])
33557118 web-browsing ACTIVE FLOW *NS 10.193.91.111[55195]/Untrust/6 (10.193.88.91[33260])
vsys1 74.125.206.154[443]/Untrust (74.125.206.154[443])
33557141 web-browsing ACTIVE FLOW *NS 10.193.91.111[55215]/Untrust/6 (10.193.88.91[50351])
vsys1 216.58.209.224[443]/Untrust (216.58.209.224[443])
33557116 web-browsing ACTIVE FLOW *NS 10.193.91.111[55194]/Untrust/6 (10.193.88.91[15099])
vsys1 216.58.209.238[443]/Untrust (216.58.209.238[443])
33557127 flash ACTIVE FLOW *NS 10.193.91.111[55202]/Untrust/6 (10.193.88.91[9829])
vsys1 216.58.209.230[443]/Untrust (216.58.209.230[443])
33557091 twitter-base ACTIVE FLOW *NS 10.193.91.111[55179]/Untrust/6 (10.193.88.91[28557])
vsys1 199.16.157.105[443]/Untrust (199.16.157.105[443])
33557143 web-browsing ACTIVE FLOW *NS 10.193.91.111[55216]/Untrust/6 (10.193.88.91[54633])
7316 http-video ACTIVE FLOW *NS 10.193.91.111[55238]/Untrust/6 (10.193.88.91[26068])
vsys1 173.194.129.178[443]/Untrust (173.194.129.178[443])
7238 web-browsing ACTIVE FLOW *NS 10.193.91.111[55184]/Untrust/6 (10.193.88.91[28250])
vsys1 74.125.195.113[443]/Untrust (74.125.195.113[443])
7307 web-browsing ACTIVE FLOW *NS 10.193.91.111[55233]/Untrust/6 (10.193.88.91[44945])
vsys1 74.125.206.154[443]/Untrust (74.125.206.154[443])