Palo Alto Networks SSL Forward Proxy Explained
Introduction
This article provides a comprehensive explanation of Palo Alto Networks SSL Forward Proxy, a critical feature for securing modern networks where SSL/TLS encryption is pervasive. We will cover its purpose, mechanism, configuration elements, and important considerations, including exemptions and exam-relevant points.
What is SSL Forward Proxy?
SSL Forward Proxy, also known as Outbound Decryption, is a Palo Alto Networks firewall feature designed to decrypt and inspect SSL/TLS encrypted traffic originating from internal clients destined for external servers (like websites, SaaS applications, etc.). With over 95% of internet traffic now encrypted, visibility into this traffic is essential for effective security.
Without SSL Forward Proxy, the firewall sees only an encrypted stream, typically identified as App-ID
ssl
or
tls
. This severely limits the effectiveness of various security features:
-
Accurate App-ID:
Cannot identify the true application within the tunnel (e.g., differentiating
facebook-postingfromgoogle-drive-upload). - Threat Prevention: Cannot scan encrypted content for malware, exploits, or command-and-control traffic.
- Granular URL Filtering: Restricted to filtering based only on the domain name (SNI), not the full URL path or parameters within HTTPS.
- File and Data Filtering: Cannot inspect encrypted files or data streams for sensitive information (DLP).
- Application-Based Policies: Cannot enforce granular policies based on the specific application running within the encrypted session.
By decrypting outbound traffic, the firewall regains the ability to apply full security inspection, significantly enhancing the network's security posture.
Core Concepts: How SSL Forward Proxy Works & Certificates
How SSL Forward Proxy Works: The MITM Mechanism
SSL Forward Proxy operates as a Man-in-the-Middle (MITM) between the internal client and the external server. Unlike Inbound Inspection, which requires the server's private key, Forward Proxy uses a certificate-based approach.
Here's the process:
-
Client Initiates Connection:
An internal client attempts to connect to an external HTTPS site (e.g.,
https://example.com). - Firewall Intercepts: A Decryption Policy rule configured for SSL Forward Proxy matches the session.
-
Firewall Connects to Server:
The firewall initiates its
own separate SSL/TLS connection
to the actual external server (
example.com). It validates the server's real certificate. - Firewall Generates Certificate: The firewall dynamically creates a new SSL certificate that mimics the identity of the original server's certificate (copying attributes like Common Name, Subject Alternative Names).
- Firewall Signs Certificate: The firewall signs this newly generated certificate using the private key of a special Certificate Authority (CA) certificate stored on the firewall and designated as the Forward Trust CA .
- Firewall Presents Certificate to Client: The firewall presents this firewall-signed certificate to the internal client instead of the real server's certificate.
- Client Verification: The client's browser/OS checks if the CA that signed the presented certificate (the firewall's Forward Trust CA) is trusted.
- If Trusted: The client accepts the certificate, and the SSL/TLS handshake completes successfully between the client and the firewall . Decryption proceeds.
- If Not Trusted: The client's browser will display a prominent certificate warning/error, potentially blocking the connection. This underscores the critical need to deploy the Forward Trust CA to client trust stores.
- Decryption and Inspection: With two separate SSL sessions established (Client<->Firewall and Firewall<->Server), the firewall decrypts client traffic, inspects it using its security engines, re-encrypts it using the session key from the connection to the real server, and forwards it. Return traffic follows the reverse path.
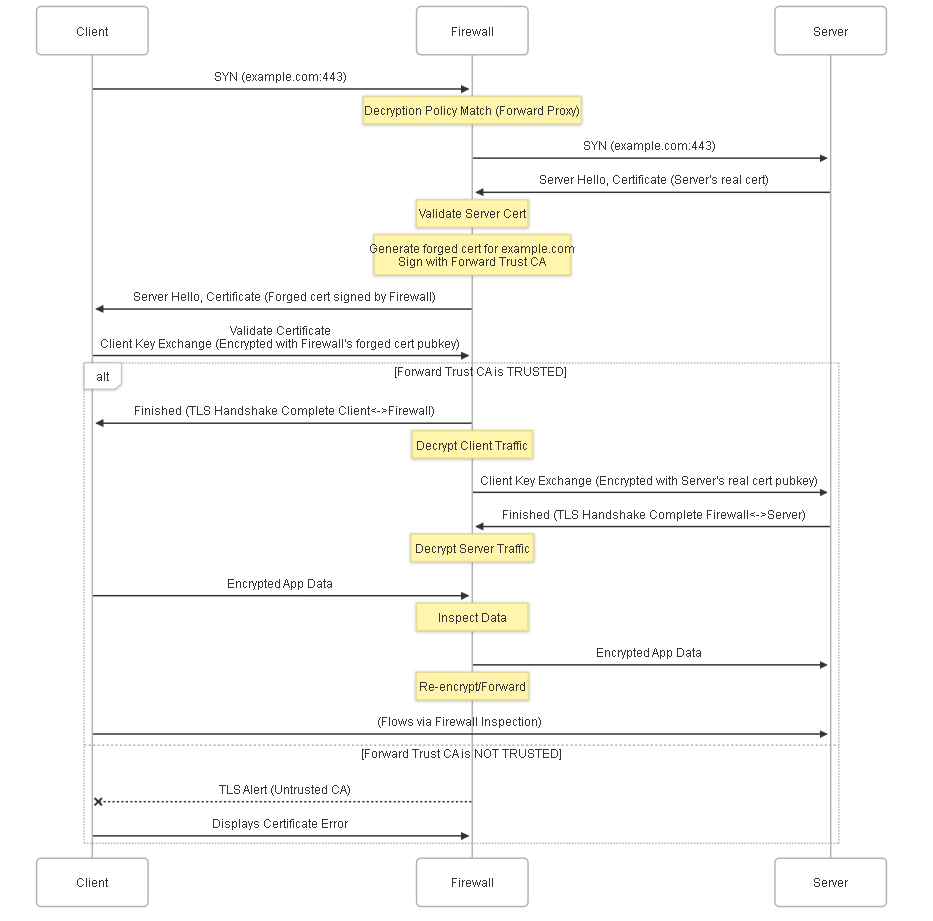
Simplified sequence diagram showing the SSL Forward Proxy (MITM) process.
Certificates Needed for SSL Forward Proxy
Implementing SSL Forward Proxy requires specific certificates:
-
Forward Trust Certificate Authority (CA):
- This is a private CA certificate generated on the firewall itself (or imported if using an internal PKI).
- Its private key is used by the firewall to sign the dynamically generated certificates for external websites.
- This CA certificate MUST be deployed to the trusted root certificate stores of all internal clients whose traffic you wish to decrypt. If it's not trusted by the client, the MITM process fails with a certificate error.
-
Forward Untrust Certificate Authority (CA):
- This is also typically a private CA certificate generated on the firewall.
- It is used by the firewall to sign substitute certificates for sessions that FAIL certificate validation against the client's trust store (e.g., invalid certificate, expired certificate, unknown CA).
- Clients should NOT trust this CA . When a client receives a certificate signed by the Forward Untrust CA, its browser/OS should trigger a severe certificate error (e.g., "This connection is not private"). This is the desired behavior to alert the user to a potentially malicious or misconfigured site that would otherwise go unnoticed if just blocked.
- This CA certificate does NOT need to be deployed to clients . The client's default lack of trust is the intended behavior.
-
Default/Intermediate Certificates (Optional but Recommended):
- PAN-OS comes with a default certificates.
- You can generate or import separate certificates for the Forward Trust and Forward Untrust roles for better management.
- Using intermediate CAs can be part of a larger PKI strategy.
Configuration: Decryption Policy
Decryption Policy and Rules
The Decryption Policy determines which sessions are subjected to SSL inspection. It functions much like the Security Policy, using criteria to match traffic and then applying a decryption action.
Flowchart showing how Decryption Policy interacts with Security Policy.
Decryption Policy rules have a top-down matching order, similar to Security Policy. The first rule that matches a session's criteria determines the decryption action.
Decryption Policy Parameters
A Decryption Policy rule is defined by several components:
- Name: A descriptive name for the rule.
-
Type:
- SSL Forward Proxy: Used for decrypting outbound client-to-server traffic. This is the focus of this article.
- SSL Inbound Inspection: Used for decrypting inbound client-to-server traffic where the firewall has the server's private key.
- SSL Protocol Settings: Applies settings based on protocol versions/cipher suites, often used for control or blocking without full decryption.
-
Source:
- Source Zone: Typically the internal zone(s) where clients reside.
- Source Address: Specific client IP addresses, ranges, or address groups.
- Source User: Users or user groups (requires User-ID).
-
Destination:
- Destination Zone: Typically the external (Untrust/WAN) zone.
- Destination Address: Specific server IP addresses, ranges, or address groups (less common for general outbound decryption, but useful for specific sites).
- Destination URL Category: Matches based on URL categories (e.g., match 'Business and Economy', exclude 'Financial Services'). This is a very common and powerful way to define decryption scope.
-
Service:
-
Service:
Typically
service-https(TCP/443). Can include other custom services if SSL/TLS runs on non-standard ports.
-
Service:
Typically
-
Action:
- Decrypt: Enable decryption for matching traffic. When selecting this for SSL Forward Proxy, you must also select a Decryption Profile .
- No Decrypt: Explicitly skip decryption for matching traffic. This is used for sites that break decryption, contain sensitive information, or for compliance reasons (e.g., banking sites).
- Block: Block the session immediately. No further processing occurs for this session. Useful for blocking known malicious or unwanted encrypted connections entirely.
- For exam purposes, understand the difference between No Decrypt (allow encrypted) and Block (prevent connection).
- Decryption Profile: (Required when Action is Decrypt) Specifies how decryption is performed and what errors are tolerated. (Covered in the next section).
- Security Profiles: (Optional, applies *before* decryption) You can apply specific security profiles (like Vulnerability Protection or DoS Protection) to the initial handshake if needed, though most inspection happens post-decryption via the Security Policy.
Configuration: Decryption Profile
Decryption Profile and Control
While the Decryption Policy determines *which* sessions are decrypted (or not), the Decryption Profile determines *how* the decryption process behaves , specifically regarding handling TLS protocol settings and certificate validation errors.
A Decryption Profile is a collection of settings applied to sessions matched by a Decryption Policy rule with the Action set to 'Decrypt'. It provides granular control over the decryption session based on potential issues encountered during the TLS handshake or certificate validation.
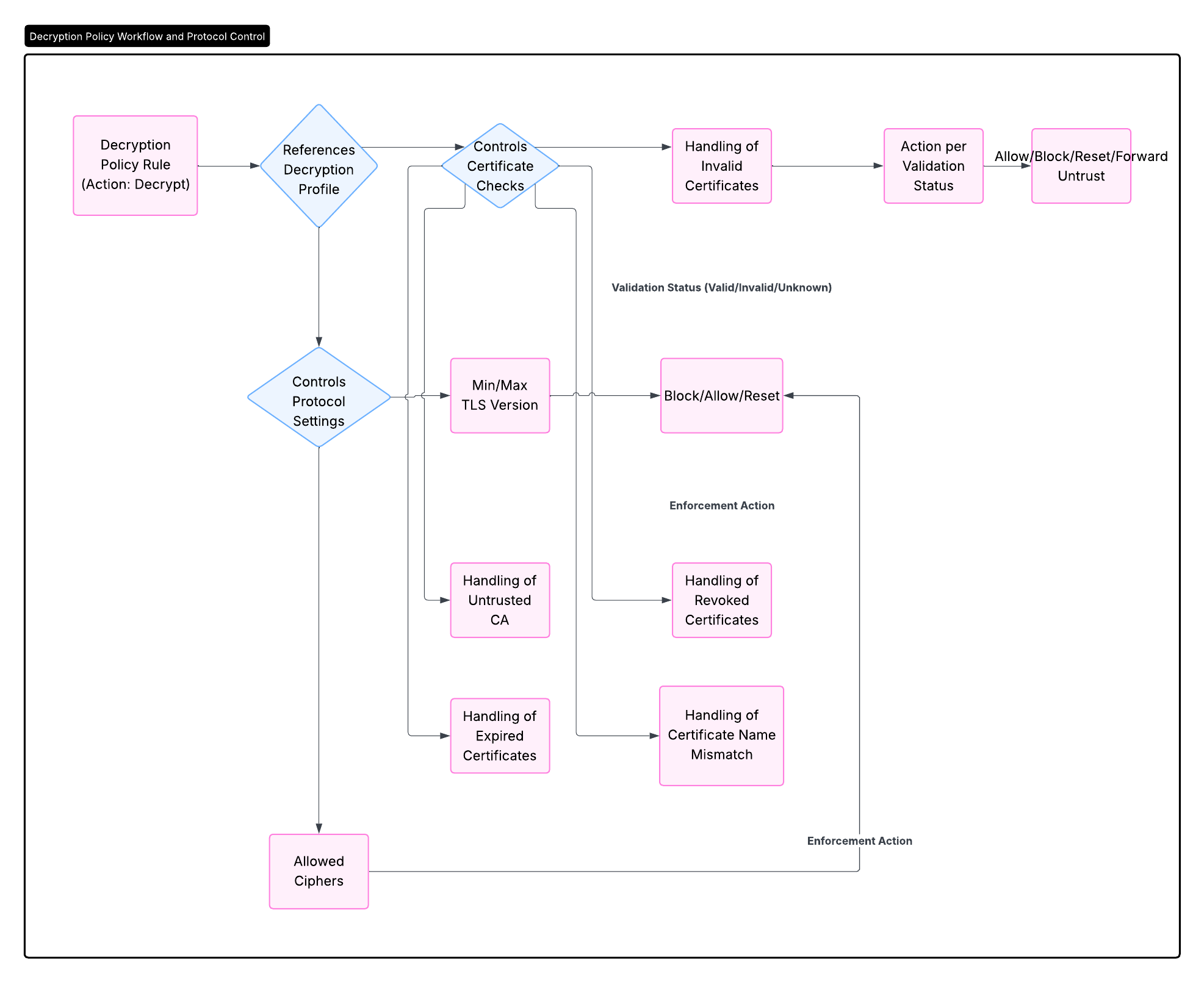 Flowchart illustrating the role and controls within a Decryption Profile.
Flowchart illustrating the role and controls within a Decryption Profile.
Decryption Profile Parameters
A Decryption Profile allows configuration of actions for various certificate and protocol status outcomes. Key sections typically include:
SSL Protocol Settings
-
TLS Versions:
Define the minimum and maximum TLS versions allowed (
SSLv3,TLSv1.0,TLSv1.1,TLSv1.2,TLSv1.3). Older versions like SSLv3, TLSv1.0, and TLSv1.1 are insecure and should typically be blocked or alerted.Focus on knowing insecure protocols (SSLv3, TLSv1.0, TLSv1.1) and the recommended actions (Block or Reset). - Cipher Suites: Control which encryption cipher suites are permitted. Often, you'll block weak or null ciphers.
- Action for Unsupported Version/Cipher: What happens if the client/server tries to negotiate a blocked protocol version or cipher suite (usually Block or Reset).
Certificate Validation Checks
For each of the following checks, you can typically configure different actions (Allow, Block, Reset) based on the validation status:
-
Invalid Certificate:
The certificate is structurally invalid or malformed.
- Recommended Action: Block or Reset. Never allow.
-
Untrusted CA:
The server's certificate is signed by a CA not present or not trusted in the firewall's trust store.
- Recommended Action: Block or Reset. The firewall *validates the server's real certificate*. If it's signed by an untrusted CA, it's suspicious. This is different from the client trusting the *firewall's* Forward Trust CA.
-
Expired Certificate:
The server's certificate has passed its validity period.
- Recommended Action: Block or Reset. Expired certificates indicate poor maintenance or potential malicious activity.
-
Certificate Revoked:
The server's certificate has been revoked (checked via CRL or OCSP).
- Recommended Action: Block or Reset.
-
Certificate Status Unknown:
The firewall could not determine the revocation status (e.g., cannot reach CRL/OCSP server).
- Exam Relevance: You need to know the implications of allowing or blocking unknown status. Allowing might miss revoked certs. Blocking might block legitimate sites if OCSP/CRL infrastructure is down.
-
Certificate Name Mismatch:
The hostname the client requested (SNI or common name in older TLS) does not match the Common Name or Subject Alternative Names in the server's certificate.
- Recommended Action: Block or Reset. A mismatch is often a sign of a misconfigured server or, more importantly, a phishing or malicious site attempting to use a certificate for a different domain.
Other Settings
- Forward Untrust Certificate: This setting within the profile specifies which specific certificate (typically the firewall's Forward Untrust CA certificate) is used to sign the substitute certificate presented to the client when any of the above certificate validation checks fail and the profile action is configured to use the Forward Untrust certificate.
- Passthrough (Fail Open): In some older PAN-OS versions or specific configurations, there might be an option to "pass through" traffic if decryption fails for certain reasons. This is generally NOT recommended as it bypasses security inspection. The modern approach is to Block or Reset on failure.
Exemptions & Updates
Exemption Mechanisms for SSL Decryption
While the goal is to decrypt as much traffic as possible, certain types of SSL-encrypted communication must be exempted from decryption for functional, security, or privacy reasons.
Common reasons and mechanisms for exemption include:
-
"No Decrypt" Policy Rule:
- This is the primary administrative method. You create Decryption Policy rules above your 'Decrypt' rules.
- Match criteria (Source, Destination, User, URL Category, Service) are used to identify traffic that should NOT be decrypted.
-
Action is set to
No Decrypt. The session is allowed to proceed encrypted. - Commonly used for financial sites, healthcare sites, sensitive internal resources (if traffic hairpinning through the firewall), or applications known to break decryption.
-
Predefined Decryption Exclusions List:
- Palo Alto Networks maintains a built-in list of critical applications and services that are exempted from decryption by default and cannot be decrypted even if a policy rule matches .
- This list includes services where decryption is known to break functionality (e.g., certain update services, collaboration tools with embedded crypto), applications that use client-certificate authentication (which conflicts with MITM), or services for which decryption would be highly controversial or illegal (e.g., certificate revocation checks themselves, certain OS updates).
- This list is updated dynamically.
- You cannot remove entries from this predefined list.
-
Client Certificate Authentication:
- Sites that require the client browser to present a certificate for authentication.
- The MITM process breaks this because the firewall cannot obtain the client's private key to present the correct certificate to the server.
- Such sessions are typically identified and exempted automatically by the firewall.
-
Untrusted Server Certificate:
- If the firewall itself, when connecting to the server, determines the server's certificate is invalid (e.g., signed by an untrusted public CA, expired, name mismatch), the session may be handled based on the Decryption Profile settings.
- If the profile action is Block or Reset, the session is prevented.
- If the profile action is configured to use the Forward Untrust certificate, the firewall attempts to present that to the client, resulting in a client-side error if the Forward Untrust CA is not trusted (the desired outcome). In some failure scenarios, the session might be implicitly exempted from full inspection.
-
Unsupported Protocol/Cipher:
- If the client and server attempt to negotiate an SSL/TLS version or cipher suite that is explicitly blocked by the Decryption Profile.
- The action defined in the profile (typically Block or Reset) is applied, preventing decryption and usually the connection itself.
Dynamic Exemption Updates
The list of applications and services that should be exempted from decryption is not static. Palo Alto Networks continuously researches applications and identifies those that break when decrypted or require exemption for other reasons (security, compliance, functionality).
The Decryption Exemption list is part of the Applications and Threats content update (also known as App-ID and Threat signatures). When you install a new version of this content pack:
- It includes updates to App-ID signatures.
- It includes updates to Threat signatures.
- It also includes updates to the built-in Decryption Exclusions List.
This means that enabling or disabling decryption for specific applications or services might change automatically when you install a content update. The firewall uses the most current list provided by the update.
The type of update is essentially an addition or modification to an internal database on the firewall that flags certain known applications/services as requiring exemption from SSL decryption, overriding even an explicit 'Decrypt' policy rule that might match the traffic.
This dynamic update mechanism ensures that the firewall can decrypt as much traffic as possible while minimizing disruption to applications that are incompatible with decryption or require specific handling.
PCNSE Focus: Key Notes & Gotchas
PCNSE/PCNSA Exam Notes on SSL Forward Proxy
SSL Decryption, particularly Forward Proxy, is a heavily tested topic on Palo Alto Networks certification exams. Here are some key points to focus on:
- Purpose: Why decrypt? What visibility/capabilities does it enable? (App-ID, Threat, URL, DLP). What's the default if not decrypted? (App-ID ssl/tls).
- MITM Mechanism: Understand the basic steps - Firewall intercepts, connects to server, generates certificate, signs with Forward Trust CA, presents to client.
- Certificates: Know the roles of Forward Trust CA and Forward Untrust CA. Critical: Forward Trust CA must be deployed/trusted on clients. Forward Untrust CA should NOT be trusted on clients.
- Decryption Policy: How it works (top-down matching), key parameters (Source, Dest, Service, URL Cat), and Actions (Decrypt, No Decrypt, Block) .
- Policy Order: 'No Decrypt' rules must be higher (more specific) than 'Decrypt' rules.
- Decryption Profile: Controls *how* decryption handles protocol versions, cipher suites, and certificate validation errors.
- Profile Actions: Understand the meaning of Block, Reset, Allow, and using the Forward Untrust certificate for validation failures.
- Key Profile Checks: Focus on Invalid Certificate, Untrusted CA, Expired Certificate, Certificate Name Mismatch, Certificate Status Unknown, and blocking insecure TLS versions (SSLv3, TLSv1.0, TLSv1.1). Name Mismatch is a common exam scenario.
- Exemptions: Distinguish between administrator-configured 'No Decrypt' policy rules and the built-in, non-configurable Decryption Exclusions List .
- Dynamic Updates: Decryption Exclusions are part of the Applications and Threats content update .
- Troubleshooting: Common issues involve clients not trusting the Forward Trust CA (certificate errors in browser), applications breaking due to decryption (requires 'No Decrypt' rule or checking exclusions), or firewall resource limitations (though less common for basic concepts).
Scenario Example for Exam:
A user reports certificate errors when visiting banking sites, but other sites work fine with decryption. What is the most likely cause and solution?
Likely Cause: The banking site is likely matching a general 'Decrypt' rule instead of being explicitly exempted.
Solution: Create a 'No Decrypt' Decryption Policy rule for the banking site's URL category or domain, placed higher than the general 'Decrypt' rule.
PCNSE Focus: Interactive Quiz
Test Your Knowledge on SSL Forward Proxy
Answer the following 20 questions covering common concepts and potential exam topics related to Palo Alto Networks SSL Forward Proxy.