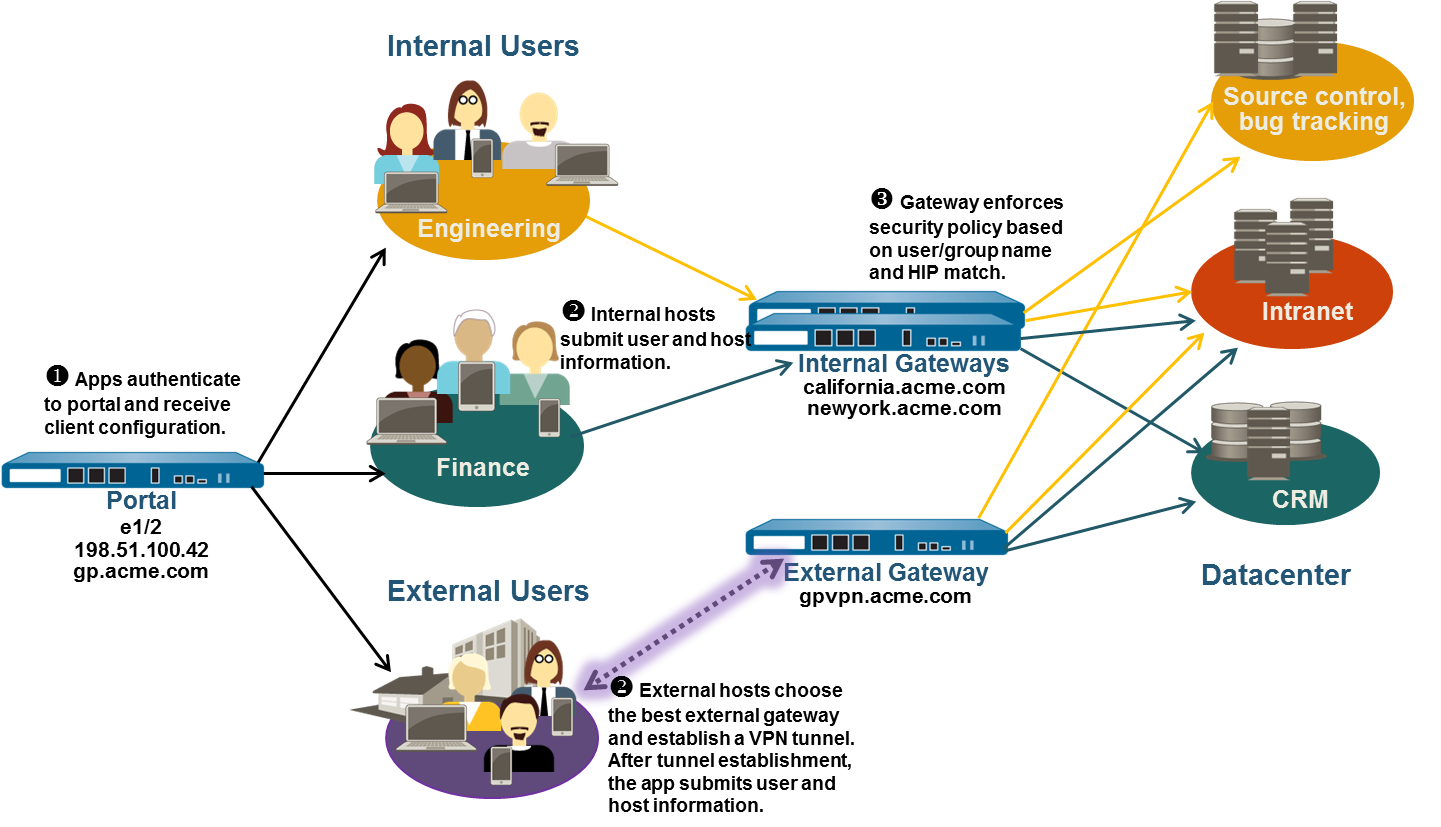
Configuring a mixed gateway deployment involves several steps across the participating firewalls:
-
Ensure appropriate Layer 3 interfaces, Tunnel interfaces, and Security Zones are configured on each firewall acting as a Portal or Gateway.
-
Portal Firewall (Example: gp.acme.com):
-
External Interface (e.g.,
ethernet1/2
, IP
198.51.100.42
) in
l3-untrust
zone. (DNS A record points
gp.acme.com
here).
-
Note: Portal itself doesn't typically require a tunnel interface unless it also acts as a gateway.
-
External Gateway Firewall (Example: gpvpn.acme.com):
-
External Interface (e.g.,
ethernet1/5
, IP
192.0.2.4
) in
l3-untrust
zone. (DNS A record points
gpvpn.acme.com
here).
-
Tunnel Interface (e.g.,
tunnel.3
) in a dedicated VPN zone (e.g.,
corp-vpn
). Enable User-ID on this zone.
-
Internal Gateway Firewall (Example: Serving california.acme.com & newyork.acme.com):
-
Internal Interface(s) (e.g.,
ethernet1/1
, IP
10.1.1.1
) in
l3-trust
zone. (DNS A records point FQDNs here).
-
Tunnel Interface (e.g.,
tunnel.10
) in a dedicated internal VPN zone (e.g.,
GP-Internal-VPN
). Enable User-ID on the *internal user source zones* (like
l3-trust
).
Follow
Administrative Access Best Practices
. Do not enable management services (HTTP/S, SSH) on external-facing interfaces used for GlobalProtect.
-
Obtain GlobalProtect Licenses
Ensure each firewall hosting a
Gateway
(both internal and external) has a valid GlobalProtect subscription activated (
Device > Licenses
). This is required for agent connections and HIP features.
See
About GlobalProtect Licenses
for details.
-
Obtain/Generate and Deploy Certificates
SSL/TLS Server Certificates are required for the Portal and all Gateways to secure communications.
-
Clients must trust the CA that issued the Portal certificate for the initial connection.
-
Using certificates from a trusted Public CA or a well-managed Internal Enterprise CA is recommended over self-signed certificates for production.
-
If using self-signed certificates generated on the firewall (e.g., using the firewall as a Root CA), the Root CA's public certificate must be deployed to clients for gateway connections (often via the Portal Agent config).
-
Consult the documentation for detailed steps on
Enabling SSL Between GlobalProtect Components
.
-
Configure Authentication
Define Authentication Profiles (
Device > Authentication Profile
) and potentially Certificate Profiles (
Device > Certificate Management > Certificate Profile
) for authenticating users to the Portal and Gateways. Different profiles can be used for Portal vs. Gateway, or Internal vs. External Gateways.
-
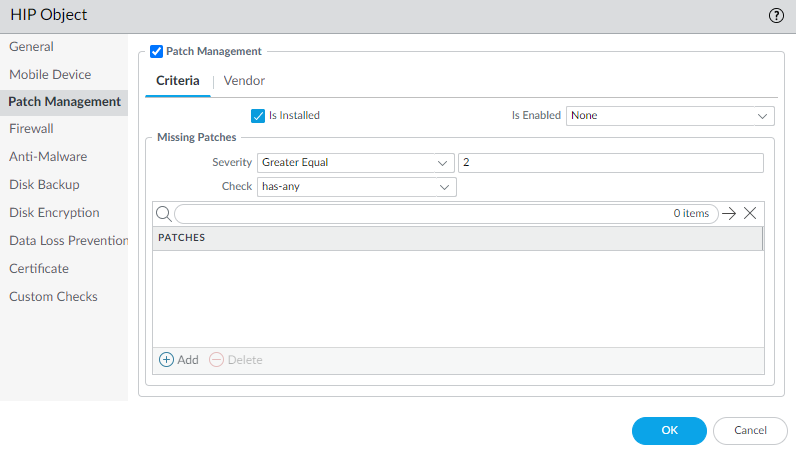
Configure HIP Objects and Profiles (If Using HIP)
If leveraging device posture checks:
-
Define HIP Objects (
Objects > GlobalProtect > HIP Objects
) specifying attributes to check (OS, AV, Patch Mgmt, etc.).
-
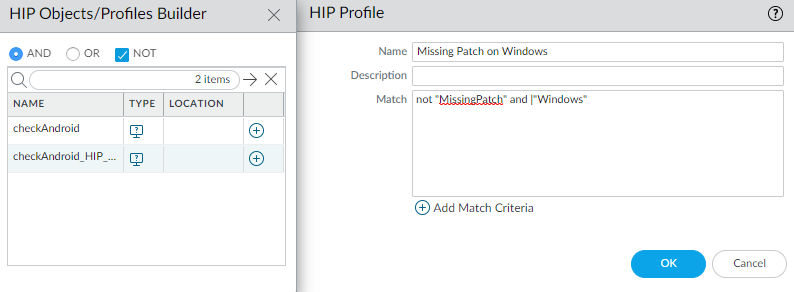
Define HIP Profiles (
Objects > GlobalProtect > HIP Profiles
) referencing the HIP Objects to define compliance states (e.g., `Compliant-Host`, `Missing-Patches`).
See
Host Information
for details.
-
Configure Internal Gateways
On the firewall(s) hosting Internal Gateways (
Network > GlobalProtect > Gateways
):
-
Configure the Gateway object(s), specifying internal listening Interface/IP, Server Certificate (via SSL/TLS Profile), and Authentication Profile(s).
-
Configure Agent settings, particularly Client Settings (IP Pool, DNS) and Split Tunnel rules appropriate for internal users.
-
Enable HIP collection in the Agent settings if required.
See
Configure a GlobalProtect Gateway
.
Client Authentication configuration on the Internal Gateway might rely on cookies (Authentication Modifier) from the Portal authentication or use methods like Kerberos for seamless internal connections, though standard profiles are also possible.
-
Configure External Gateway(s)
On the firewall(s) hosting External Gateways (
Network > GlobalProtect > Gateways
):
-
Configure the Gateway object(s) similarly, but listening on the external Interface/IP.
-
Define Agent Client Settings appropriate for remote users (IP Pool, DNS, Split/Full Tunnel Access Routes).
-
Enable HIP collection if required.
-
Configure the GlobalProtect Portal
On the firewall hosting the Portal (
Network > GlobalProtect > Portals
):
-
Define Portal Access:
Configure listening Interface/IP and the Portal's SSL/TLS Service Profile.
-
Define Portal Authentication:
Configure Client Authentication using appropriate Authentication Profile(s).
-
Configure Agent Configuration(s):
-
Under the `Agent` tab, define one or more configurations.
-
Crucially, under the `External` tab list your External Gateway(s) (FQDNs recommended).
-
Under the `Internal` tab, list your Internal Gateway(s) AND configure Internal Host Detection (IHD) settings
(IPs/FQDNs only reachable internally).
-
Configure Connect Method (e.g., `User-logon (Always On)`), HIP Data Collection, Trusted Root CA distribution (if using self-signed gateway certs), etc.
-
You can create multiple Agent Configurations assigned based on User/Group or OS if different settings are needed for different populations.
See
Configure a GlobalProtect Portal
.
-
Deploy GlobalProtect Agent Software
Make the agent software available to users. Common methods:
-
Host the software directly on the Portal for download (
Device > GlobalProtect Client
).
-
Use enterprise software deployment tools (SCCM, JAMF, Intune).
-
Provide users a download link.
See
Deploy the GlobalProtect App Software
.
-
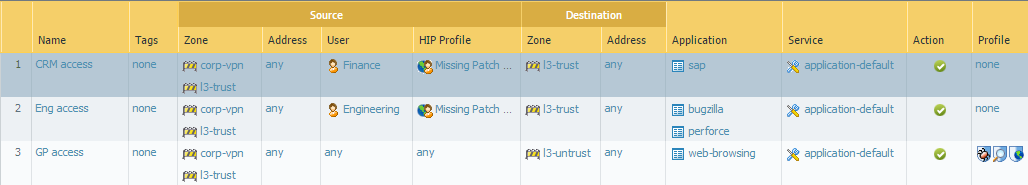
Configure Security Policy Rules
On the gateway firewalls (both internal and external), create Security rules (
Policies > Security
) to control traffic coming from the respective VPN zones:
-
Allow traffic from the
External VPN zone
(e.g., `corp-vpn`) to internal zones (`l3-trust`, etc.) based on User/Group and HIP Profile.
-
Allow traffic from the
Internal VPN zone
(e.g., `GP-Internal-VPN`) to specific sensitive internal zones based on User/Group and HIP Profile.
-
Apply appropriate Security Profiles (Threat Prevention, URL Filtering, etc.) to inspect the traffic.
-
Commit Configuration
Commit the changes on the Portal and all Gateway firewalls.