Understanding User-ID and its Importance
User-ID is a Palo Alto Networks PAN-OS feature that enables you to identify users on your network and enforce security policies based on user identity rather than just IP addresses. In dynamic network environments where IP addresses can change frequently (e.g., DHCP, BYOD), relying solely on IP-based policies is insufficient and can lead to security gaps or overly permissive rules.
Why is User-ID Crucial?
- Visibility: Gain insight into who is accessing which applications and data, regardless of their device or location. This is fundamental for security monitoring and incident response.
- Granular Policy Control: Create security policies based on users and groups defined in your directory services (e.g., Active Directory, LDAP). This allows for more precise and effective access control. For example, you can allow the "Engineering" group access to development servers while denying access to the "Sales" group.
- Threat Correlation: Correlate network threats with specific users, enabling faster identification of compromised accounts or malicious insider activity.
- Logging and Reporting: Generate detailed logs and reports that include user information, providing a clear audit trail of user activity for compliance and forensics.
- Zero Trust Enablement: User identity is a core pillar of a Zero Trust security model, which assumes no implicit trust and verifies every access attempt.
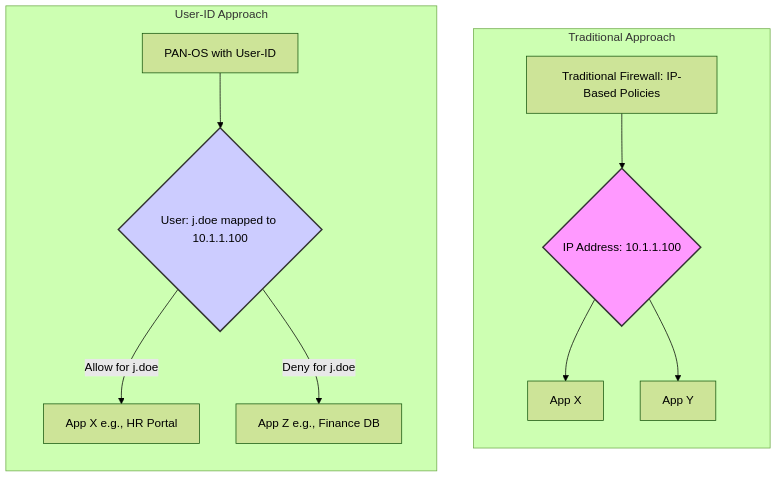
Comparison: Traditional IP-based vs. User-ID based policy enforcement.
Essentially, User-ID translates IP addresses into meaningful user identities, allowing the firewall to understand the "who" behind network traffic, not just the "what" and "where".
Why Use GlobalProtect for User-ID Mapping?
GlobalProtect is a powerful solution for extending enterprise security to all users, regardless of their location. Beyond its primary role in providing secure remote access (VPN) and consistent security policy enforcement, GlobalProtect is an excellent and often preferred source for User-ID information for several reasons:
- Direct Authentication: When users connect via GlobalProtect (either to an external or internal gateway), they typically authenticate directly against the corporate directory (LDAP, SAML, Kerberos, RADIUS). This authentication event provides a highly reliable way for the firewall to create a User-to-IP address mapping.
- Ubiquitous Coverage: For organizations that mandate GlobalProtect for both remote and on-premise users (via internal gateways), it can provide comprehensive User-ID coverage across the entire user base.
- HIP Integration: GlobalProtect's Host Information Profile (HIP) checks can assess the security posture of the connecting endpoint. This information, combined with User-ID, allows for even more granular context-aware policies (e.g., allowing access only if the user is "j.doe" AND their device is compliant).
- Real-time Mappings: Mappings are typically created as soon as the user connects and authenticates, providing up-to-date identity information.
- Reduced Reliance on Probing/Logs: Using GlobalProtect as a User-ID source can reduce the need for other methods like AD Security Log monitoring or WMI probing, which can sometimes be complex to configure or have performance implications.
- Zero Trust Alignment: Forcing internal users to connect via an Internal GlobalProtect Gateway aligns perfectly with Zero Trust principles by verifying the user and device *before* granting access, even within the corporate network. The User-ID mapping is a natural outcome of this verification.
When a GlobalProtect client connects and authenticates to a GlobalProtect Gateway (internal or external) configured on a Palo Alto Networks firewall, the firewall automatically learns the user's identity and their assigned IP address (either physical IP or IP from the GlobalProtect IP pool). This mapping is then populated into the firewall's User-ID mapping table.
GlobalProtect External Gateways & User-ID
This section leverages content from the original "PAN-OS: GlobalProtect Internal vs. External Gateways" article.
External Gateways
Purpose
- Provide secure, encrypted VPN tunnels for remote users connecting from untrusted external networks.
- Authenticate remote users (This is key for User-ID).
- Enforce security policy (App-ID, Threat Prevention, URL Filtering, etc.) on traffic entering the corporate network from remote users.
- Provide access to internal resources based on user identity and potentially device posture (HIP).
When a user authenticates to an External Gateway, the firewall automatically creates a User-ID to IP mapping. The IP address in this mapping is the one assigned to the client from the Gateway's IP Pool.
Typical Configuration
- Listening Interface: Configured on an external-facing firewall interface (e.g., in the
Untrustzone). - Tunnel Interface: Terminates tunnels on a logical Tunnel Interface assigned to a specific VPN zone (e.g.,
GP-External-VPN). - Authentication: Uses configured Authentication Profiles (LDAP, SAML, RADIUS, etc.) suitable for remote users. The successful authentication event is crucial for User-ID.
- Client IP Pool: Assigns IP addresses to remote clients from a dedicated pool. This IP is what gets mapped to the authenticated user.
- Split/Full Tunnel: Configured via Access Routes in the Agent Client Settings to control routing for remote users.
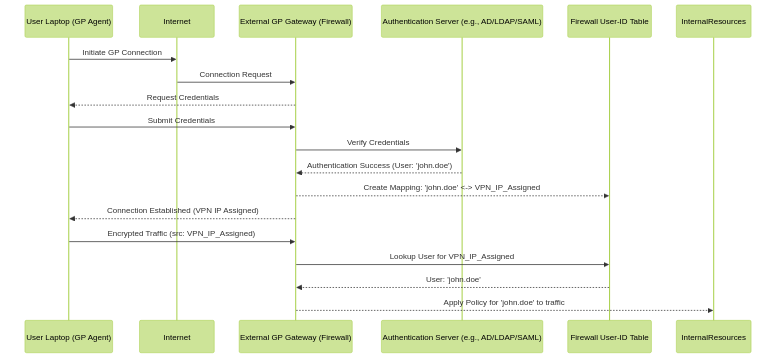 User-ID mapping process with External GlobalProtect Gateway.
User-ID mapping process with External GlobalProtect Gateway.
GlobalProtect Internal Gateways & User-ID
This section leverages content from the original "PAN-OS: GlobalProtect Internal vs. External Gateways" article and expands on User-ID aspects.
Internal Gateways
Purpose
- Enforce Consistent Security Policy: Ensure users *already inside* the network are subject to the same rigorous security inspection.
- Apply HIP Checks Internally: Verify device posture for internal connections.
- Implement Zero Trust Principles Internally.
- Segment Internal Access.
- Visibility & User-ID: Gain user-based visibility (User-ID logging) for traffic originating internally, even if not tunneled. The authentication to the internal gateway is a primary source for User-ID.
Internal Gateways are a powerful source for User-ID mappings for on-premise users. The connection and authentication event itself allows the firewall to map the user to their physical IP address (if not using an IP pool or if configured for "no-tunnel" mode primarily for User-ID).
Typical Configuration
- Listening Interface: Configured on an internal-facing firewall interface (e.g., in the
Trustor a specific internal zone). - Tunnel Interface: May or may not be used extensively depending on whether tunnel mode is enforced. Even in "no-tunnel" or "User-ID only" mode, a tunnel interface is usually configured.
- Authentication: Often configured for seamless authentication (e.g., using Kerberos, or relying on cookies from Portal authentication). Standard Authentication Profiles are used. The success of this authentication is what generates the User-ID mapping.
- Client IP Pool: Optional for internal gateways. If not used, the user's physical IP is mapped. If used (e.g., in tunnel mode), the pool IP is mapped.
- Split/Full Tunnel (Access Routes): Crucial for defining what traffic, if any, is tunneled. For User-ID collection without full tunneling, specific configurations apply.
- Requires Internal Host Detection (IHD) to be configured so the agent knows it's inside and should connect to this gateway.
The subsequent sections will delve deeper into non-tunnel and tunnel modes for Internal Gateways with respect to User-ID collection and policy enforcement.
Internal Host Detection (IHD) - The Key Differentiator
This section leverages content from the original "PAN-OS: GlobalProtect Internal vs. External Gateways" article.
For the GlobalProtect agent to automatically choose between External and Internal Gateways, Internal Host Detection (IHD) must be configured within the Portal's Agent configuration. This mechanism is crucial for directing internal users to an Internal Gateway, which can then be used as a source for User-ID.
- Location:
Network > GlobalProtect > Portals > [Portal Name] > Agent > [Agent Config] > Internaltab. - Mechanism: The agent attempts to connect to specific IP addresses or resolve specific DNS names that should *only* be reachable when the client is *inside* the corporate network.
- Configuration:
- Specify one or more Internal Host IP addresses or FQDNs.
- Define the connection attempt method (e.g., HTTPS probe on port 443, ICMP ping).
- If the agent successfully connects/resolves, it determines it is internal and connects to an Internal Gateway. This connection event is a source for User-ID mapping.
- If the agent fails, it determines it is external and connects to an External Gateway.
- Reliability: Choose IHD targets that are highly available and uniquely reachable only from the internal network. Using multiple targets improves reliability.
If IHD fails for an internal user (e.g., IHD host is down), they may connect to an External Gateway, potentially getting an IP from the VPN pool, which is still a valid User-ID mapping but might not be the desired behavior for an on-premise user.
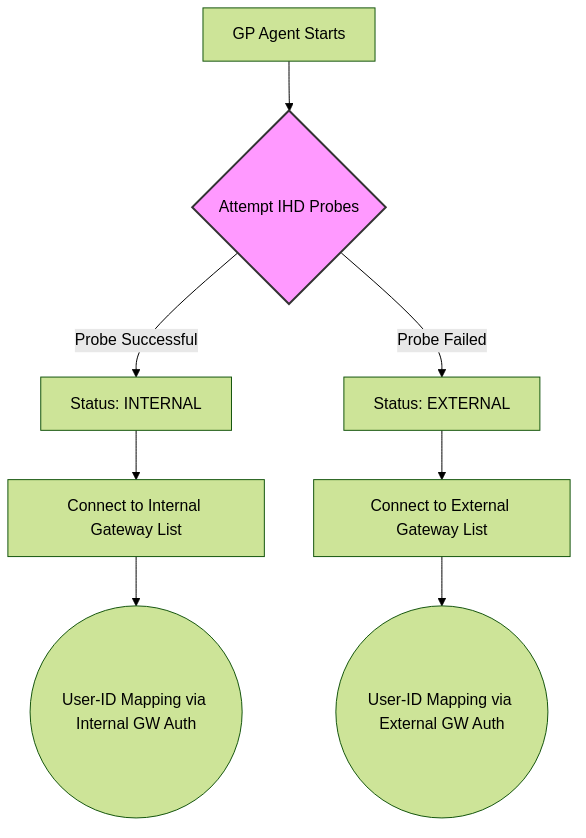
IHD process and its impact on gateway selection and subsequent User-ID mapping.
Internal Gateway: Non-Tunnel Mode for User-ID
A common use case for GlobalProtect Internal Gateways is to collect User-ID to IP mappings for on-premise users without forcing all their traffic through a VPN tunnel. This is often referred to as "User-ID only" mode or "on-demand tunnel" where the primary connection is for identification and HIP checks.
How it Works for User-ID Collection:
- IHD Success: The GlobalProtect agent, through successful Internal Host Detection (IHD), identifies itself as being on the internal network.
- Connect to Internal Gateway: The agent connects to a configured Internal Gateway.
- Authentication: The user is authenticated (often seamlessly via Kerberos or using existing portal cookies). This authentication event is critical.
- User-ID Mapping Created: Upon successful authentication, the firewall creates a User-ID mapping, associating the authenticated username with the user's actual source IP address (their physical LAN/WLAN IP).
- No Tunnel (or On-Demand): In this mode, the "tunnel" established might be very lightweight or primarily for control messages. Traffic routing is configured such that:
- General internet/local traffic continues to use the existing network path, not necessarily tunneled through the firewall via the GP tunnel interface.
- Access Routes in the GP Agent client settings for the Internal Gateway are configured with "no-access" or very specific routes for "tunnel" if any traffic is to be forced.
- The primary goal is achieved: the firewall knows `UserA` is at `IP_Address_X`.
- HIP Submission (Optional but Recommended): Even without full tunneling, the agent can submit HIP reports to the Internal Gateway. This allows policies to leverage user identity AND device posture.
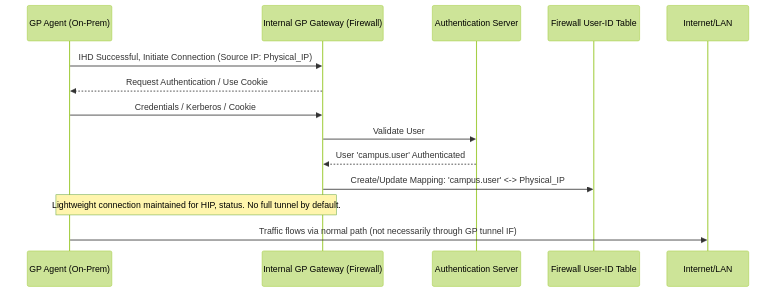
User-ID Mapping via Internal Gateway (Non-Tunnel Mode Focus).
Advantages for User-ID:
- Accurate On-Premise User-ID: Provides reliable mappings for users on the internal network using their real source IPs.
- Minimal Network Disruption: User traffic flow is largely unaffected as it doesn't need to be hair-pinned through the firewall's tunnel interface for all destinations.
- HIP Checks: Still allows for device posture assessment for internal users.
- Scalability: Less resource-intensive on the firewall compared to full tunneling for all internal users if the primary goal is just User-ID and HIP.
Internal Gateway: Tunnel Mode for Accurate Policy Enforcement
While non-tunnel mode is excellent for User-ID and HIP collection with minimal network overhead, using an Internal Gateway in Tunnel Mode offers distinct advantages for consistent and accurate security policy enforcement, aligning with Zero Trust principles for internal users.
How it Works with Tunneling:
- IHD, Connection, Authentication: Same as non-tunnel mode, resulting in a User-ID mapping (user to their physical IP or an IP from a pool if configured for the internal gateway).
- Traffic Tunneling: The key difference is that specific (or all) network traffic from the user's endpoint is encapsulated and sent through the GlobalProtect tunnel to the Internal Gateway's tunnel interface on the firewall. This is controlled by:
- Access Routes: Defined in the Agent Client Settings for the Internal Gateway. You specify which destination subnets should be tunneled.
- Exclude Routes: Define traffic that should explicitly NOT be tunneled (e.g., local LAN resources like printers).
- Policy Enforcement on Tunnel Interface: All tunneled traffic ingresses the firewall on the designated GlobalProtect tunnel interface (e.g., `tunnel.10`). Security policies are then applied based on the source zone of this tunnel interface (e.g., `GP-Internal-Users` zone).
Advantages of Tunnel Mode for Policy Enforcement:
- Consistent Policy Application: Internal users are subjected to the same security inspection (App-ID, Threat Prevention, URL Filtering, File Blocking, WildFire) as remote users if their traffic is tunneled. This ensures consistent policy regardless of user location.
- Accurate Source Zone Identification: Traffic from internal GP users arrives in a dedicated zone (e.g., `GP-Internal-Users`), making policy creation more precise and easier to manage compared to policies based on broad `Trust` zones.
- Segmentation: Facilitates microsegmentation by forcing traffic between different internal segments through the firewall for inspection.
- Enhanced HIP Enforcement: Policies can be more strictly tied to HIP compliance for tunneled traffic (e.g., "Allow access from `GP-Internal-Users` zone to `Sensitive-Data` zone ONLY IF HIP profile `Compliant-Device` matches").
- Simplified Auditing: All relevant traffic is logged and attributed to the user, passing through a central inspection point.
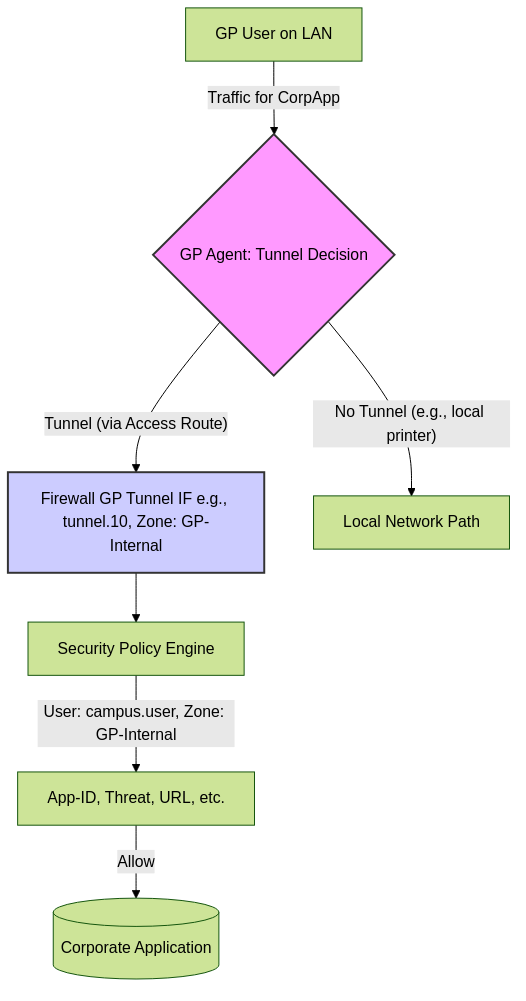
Traffic flow and policy decision with Internal Gateway in Tunnel Mode.
Considerations:
- Performance: Tunneling all internal user traffic can increase the load on the firewall. Careful capacity planning is needed.
- Complexity: Configuring Access Routes and Exclude Routes requires careful planning to ensure correct traffic flow and avoid breaking access to local resources.
- User Experience: May introduce slight latency for tunneled traffic compared to direct local routing.
The choice between non-tunnel and tunnel mode for Internal Gateways depends on the organization's security goals. If the primary aim is User-ID and basic HIP for on-premise users, non-tunnel might suffice. If consistent, Zero Trust-aligned policy enforcement for internal users is paramount, tunnel mode is superior.
GlobalProtect Gateway Selection and Configuration Workflow
This section explains how GlobalProtect agents select the appropriate gateway and the general configuration steps involved, leveraging and adapting content from the original article.
- Portal Configuration: (
Network > GlobalProtect > Portals > ... > Agent > External/Internal)- Define BOTH External and Internal Gateways in the agent configuration distributed by the Portal.
- Specify FQDNs (recommended) or IP addresses for each gateway.
- Set priorities for gateways within each list (External list, Internal list).
- Internal Host Detection (IHD) Config:
- Within the same Portal Agent configuration (
... > Agent > [Agent Config] > Internaltab), configure IHD criteria (IPs/FQDNs, probe method). This is what allows the agent to distinguish its location.
- Within the same Portal Agent configuration (
- Gateway Configuration: Create separate Gateway objects (
Network > GlobalProtect > Gateways):- One (or more) for External Gateways listening on external interfaces (e.g., Untrust zone).
- These Gateways will have Client Settings (IP Pools, Access Routes) tailored for remote users.
- One (or more) for Internal Gateways listening on internal interfaces (e.g., Trust or a dedicated internal zone).
- These Gateways will have Client Settings tailored for internal users. This includes Access Routes that determine if/what traffic is tunneled (for "tunnel mode") or configured for User-ID/HIP only (for "non-tunnel mode").
- One (or more) for External Gateways listening on external interfaces (e.g., Untrust zone).
- Agent Connection Logic:
- Agent starts and performs Internal Host Detection (IHD) based on Portal config.
- If IHD Succeeds:
- Agent status becomes "Internal".
- It attempts to connect to the highest priority Internal Gateway from its list.
- Upon successful authentication, a User-ID mapping is created (user to physical IP or internal pool IP).
- If IHD Fails:
- Agent status becomes "External".
- It attempts to connect to the highest priority External Gateway from its list.
- Upon successful authentication, a User-ID mapping is created (user to VPN pool IP).
- Policy Enforcement:
- Security Policy rules are applied based on the user identified via User-ID and the source zone.
- For External Gateways, the source zone is typically the one associated with the External Gateway's tunnel interface (e.g., `GP-External-VPN`).
- For Internal Gateways in Tunnel Mode, the source zone is the one associated with the Internal Gateway's tunnel interface (e.g., `GP-Internal-VPN`).
- For Internal Gateways in Non-Tunnel Mode (User-ID/HIP only), policies apply based on the user's actual source zone on the LAN/WLAN (e.g., `Trust`, `Wireless`), but now enriched with User-ID.
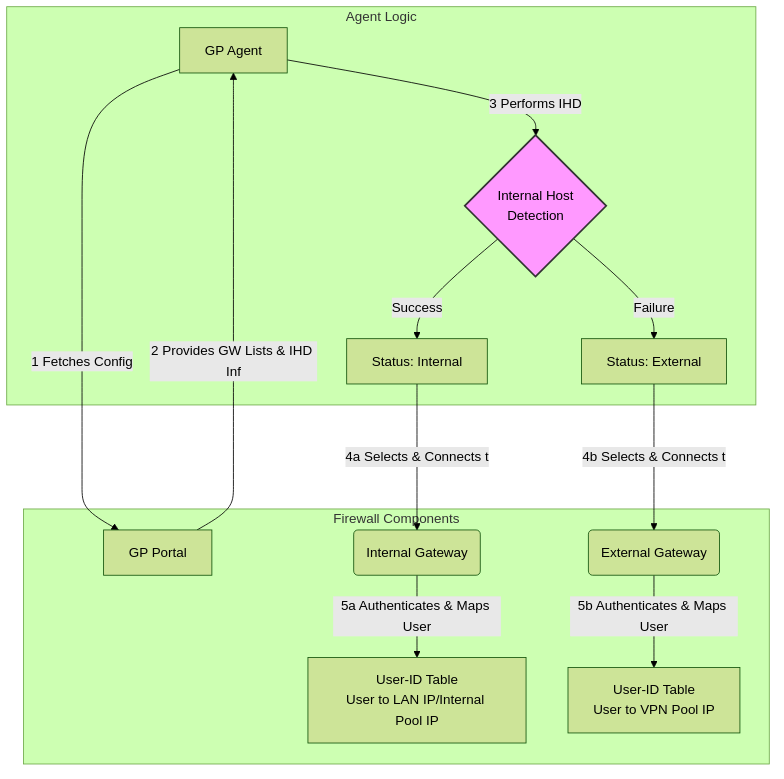
High-level GlobalProtect agent gateway selection and User-ID mapping workflow.
User-ID Agent Deep Dive
While GlobalProtect is an excellent source for User-ID, the Palo Alto Networks User-ID Agent provides other methods to collect user-to-IP mappings, especially in environments where GP might not be deployed on every endpoint or for server-initiated traffic.
The User-ID Agent can be installed on a Windows server or, for some functions, the firewall itself can act as an agent (PAN-OS integrated User-ID features).
Key Methods Used by the User-ID Agent:
-
Server Monitoring (Windows AD):
- The User-ID agent monitors security event logs on Microsoft Domain Controllers (DCs) for user login events (e.g., Event ID 4768, 4769 for Kerberos, 4624 for successful logon).
- When a user logs into a Windows domain, the DC records this event. The User-ID agent reads these logs, extracts the username and IP address of the workstation, and sends this mapping to the firewall.
- Requires appropriate service account permissions for the User-ID agent to read event logs from DCs.
- Can also monitor Exchange Server logs for Outlook Web Access (OWA) or ActiveSync logins.
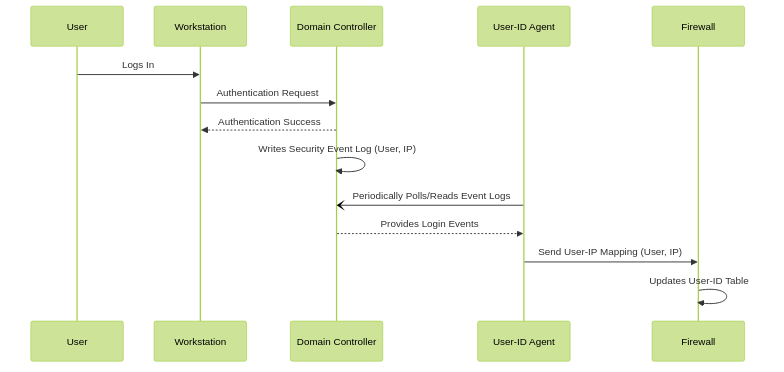
User-ID Agent Server Monitoring (AD Event Logs).
-
Syslog Monitoring:
- The User-ID agent (or the firewall directly) can be configured as a syslog listener.
- Various network devices and applications (e.g., RADIUS servers, 802.1x authenticators, NAC solutions, wireless controllers, VPN concentrators, proxy servers) can send syslog messages containing user login information upon successful authentication.
- The agent/firewall parses these syslog messages using configurable Syslog Parse Profiles to extract usernames and IP addresses.
- This is a very flexible method for integrating with third-party authentication systems.
-
Port Mapping (Terminal Services / Citrix):
- For multi-user environments like Microsoft Remote Desktop Services (RDS) or Citrix XenApp, where multiple users share the same server IP, standard IP-to-user mapping is insufficient.
- The User-ID agent (with specific configuration or a dedicated Terminal Server agent) can map users to source port ranges on the terminal server, allowing the firewall to differentiate between users on the same server IP.
- Requires careful configuration and is a more specialized use case.
-
Client Probing (Less Common for User Workstations):
- The User-ID agent can attempt to probe Windows clients using WMI or NetBIOS to determine the logged-in user for a given IP.
- Generally less reliable and more intrusive than server monitoring or GlobalProtect, often disabled or used as a last resort.
-
Authentication Policy / Captive Portal:
- While often configured directly on the firewall (see Agentless User-ID), the User-ID agent can also play a role in environments where Captive Portal authentication needs to be relayed or managed centrally.
Common User-ID Agent Gotchas:
- Service Account Permissions: Insufficient permissions for the User-ID agent service account on Domain Controllers is a very common issue. It needs rights to read security event logs and potentially other permissions depending on the monitoring method.
- Firewall Rules: Ensure firewalls (Windows Firewall on DCs/servers, network firewalls) allow communication between the User-ID agent and the DCs/servers it monitors, and between the User-ID agent and the Palo Alto Networks firewall.
- Event Log Overwriting: If DC security event logs are too small or overwrite too quickly, the User-ID agent might miss login events.
- Accurate Time Sync: Time synchronization between DCs, the User-ID agent server, and the firewall is crucial for correct log correlation.
Agentless User-ID Methods
In addition to GlobalProtect and the dedicated User-ID Agent, PAN-OS offers several "agentless" methods to gather User-ID mappings. These methods often leverage capabilities built directly into the firewall or integrate with cloud services.
-
PAN-OS Integrated User-ID:
- Captive Portal:
- When a user tries to access a resource (e.g., the internet) and no User-ID mapping exists for their IP, the firewall can redirect them to a web portal (Captive Portal).
- The user authenticates via the portal (against LDAP, Kerberos, SAML, etc.). Upon success, the firewall creates a User-ID mapping.
- Useful for guest networks, BYOD, or unmanaged devices. Three modes: Transparent, Redirect, NTLM.
- Authentication Policy:
- Similar to Captive Portal, but can be more granular. Authentication Policy rules in Security Policy can trigger authentication challenges for specific traffic, leading to User-ID mappings.
- VM Monitoring (VMware, AWS, Azure, GCP):
- The firewall can query virtualization platforms or cloud providers to get information about virtual machines, including tags that might contain user or owner information. This can be used to map IPs of VMs to "users" (often service accounts or VM owners).
- Direct Syslog Listener on Firewall:
- The firewall itself can act as a syslog listener, parsing messages from authentication sources (like RADIUS) using Syslog Parse Profiles to create User-ID mappings, without needing a separate User-ID agent.
- XFF Headers:
- The firewall can extract usernames from X-Forwarded-For (XFF) headers inserted by upstream proxy servers. Requires trusting the proxy.
- Captive Portal:
-
XML API / PAN-OS API:
- Third-party systems (e.g., NAC solutions like Cisco ISE, Aruba ClearPass, custom scripts) can programmatically send User-ID mappings to the firewall via its XML API or PAN-OS API.
- This is a powerful integration method for heterogeneous environments. The external system authenticates the user and then informs the firewall about the user-IP association.
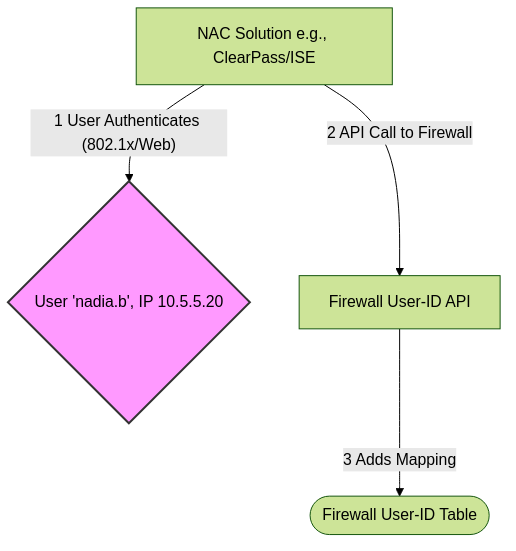
Agentless User-ID via API Integration with NAC.
-
Cloud Identity Engine (CIE):
- A Palo Alto Networks cloud service that centralizes identity information from various sources (Azure AD, Okta, G Suite, etc.).
- Firewalls subscribe to CIE to get User-ID mappings and group information.
- Modern approach, simplifies User-ID in cloud-centric environments and for remote users.
- Reduces the need for on-premise User-ID agents for cloud identity sources.
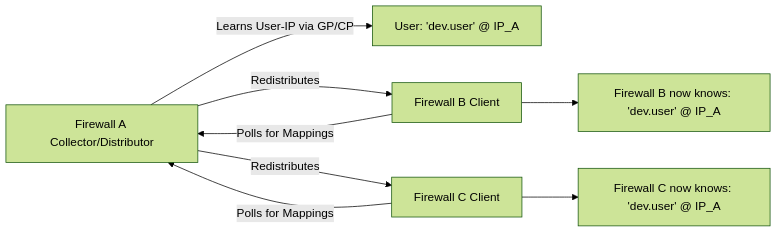
User-ID Redistribution and Data Sharing
In larger environments with multiple Palo Alto Networks firewalls or a dedicated User-ID agent infrastructure, it's often necessary to share or redistribute User-ID mapping information. This ensures that all firewalls enforcing policies have consistent and up-to-date user-to-IP mappings.
Mechanisms for Redistribution:
-
User-ID Agent as a Hub:
- A Windows User-ID Agent can collect mappings from various sources (Domain Controllers, Syslog, etc.).
- Multiple firewalls can then be configured to connect to this single User-ID agent (or a pair for redundancy) to retrieve mappings.
- This centralizes the collection and simplifies firewall configuration, as each firewall doesn't need to independently monitor all sources.
-
Firewall-to-Firewall Redistribution (PAN-OS User-ID Agent):
- A firewall can act as a "distributor" of User-ID information to other firewalls.
- One firewall (often a central or data center firewall) collects User-ID mappings (e.g., via GlobalProtect, Captive Portal, or by acting as a syslog listener).
- Other firewalls ("clients") can then retrieve these mappings from the distributing firewall. This is configured under
Device > User Identification > User-ID Agents, where you add the distributing firewall as an "agent". - This is useful for sharing mappings learned directly by one firewall with others in the network.
Firewall-to-Firewall User-ID Redistribution.
-
Panorama User-ID Redistribution:
- Panorama can act as a central hub for User-ID information.
- Firewalls (and User-ID agents) can send their mappings to Panorama.
- Panorama can then redistribute these consolidated mappings to other managed firewalls.
- This is highly scalable for large deployments managed by Panorama. Mappings are shared via User-ID Redistribution Groups in Panorama.
-
Cloud Identity Engine (CIE):
- As mentioned earlier, CIE acts as a cloud-based hub. Firewalls subscribe to CIE, effectively getting redistributed identity information from various cloud sources.
Considerations for Redistribution:
- Network Latency: Ensure low latency between firewalls and User-ID agents/distributors for timely updates.
- Redundancy: Implement redundant User-ID agents or distributor firewalls to avoid a single point of failure.
- Data Volume: In very large environments, the volume of User-ID mappings can be significant. Ensure agents and firewalls are appropriately sized.
Palo Alto Networks firewalls have limits on the number of User-ID mappings they can store. Check datasheets for specific platform capabilities.
- Trust: Ensure that only trusted sources are allowed to provide User-ID information to firewalls.
Effective User-ID redistribution is key to maintaining consistent security policy enforcement across a distributed network environment.
Choosing the Right User-ID Methods
Palo Alto Networks offers a diverse set of User-ID methods. The best approach often involves using a combination of methods to achieve comprehensive and reliable user identification across different scenarios and user types.
Factors to Consider:
- User Population:
- On-Premise Domain Users: GlobalProtect Internal Gateway (non-tunnel or tunnel), User-ID Agent monitoring Domain Controllers.
- Remote VPN Users: GlobalProtect External Gateway is the primary and most reliable source.
- Guest Users / BYOD: Captive Portal, API integration with NAC.
- Non-Domain Joined Machines / Servers: Syslog from authentication servers, API integration, VM Monitoring, manual static mappings for servers.
- Cloud Identity Users (Azure AD, Okta): Cloud Identity Engine (CIE), SAML authentication with GlobalProtect/Captive Portal.
- Existing Infrastructure:
- RADIUS / 802.1x / NAC: Syslog monitoring or API integration.
- Proxy Servers: XFF header processing or syslog from proxy.
- Virtualization / Cloud Platforms: VM Monitoring.
- Security Posture Requirements:
- Need for HIP Checks: GlobalProtect (Internal or External) is essential.
- Zero Trust for Internal Users: GlobalProtect Internal Gateway in tunnel mode.
- Scalability and Management:
- Large Distributed Networks: Panorama for redistribution, consider CIE.
- Complexity Tolerance: GlobalProtect and CIE can be simpler to manage than a sprawling User-ID agent deployment if they fit the use case.
General Recommendations (Order of Preference/Reliability):
While specific needs vary, a general hierarchy of preference for reliability and ease of management often is:
- GlobalProtect (External & Internal Gateways): Direct authentication, HIP, excellent for managed endpoints.
- Cloud Identity Engine (CIE): For cloud-based identities (Azure AD, Okta, etc.).
- User-ID Agent Server Monitoring (AD Event Logs): Good for on-premise domain users if GP isn't ubiquitous.
- API Integration (NAC, etc.): Powerful for integrating with existing auth systems.
- Syslog Monitoring (from RADIUS, etc.): Flexible for various auth sources.
- Captive Portal / Authentication Policy: Good for guests, BYOD, unmanaged devices, or as a fallback.
- VM Monitoring: For identifying server owners/services.
- XFF Headers: If a trusted proxy is in place.
- Client Probing: Generally a last resort due to potential reliability and intrusiveness issues.
| User Type / Scenario | Primary Recommended Method(s) | Secondary/Alternative Method(s) |
|---|---|---|
| Remote Employees (Managed Devices) | GlobalProtect External Gateway | CIE (if cloud identity) |
| On-Premise Employees (Managed Devices, Domain-Joined) | GlobalProtect Internal Gateway, User-ID Agent (Server Mon.) | CIE (if cloud identity), Captive Portal (fallback) |
| Guest Users / BYOD | Captive Portal | API with NAC, Syslog from Wireless Auth |
| Servers / Service Accounts | Static Mapping, VM Monitoring, API/Syslog from app auth | - |
| Multi-User Systems (RDS/Citrix) | User-ID Agent with Terminal Server Agent / Port Mapping | - |
| Users Authenticating via 802.1x/NAC | API Integration with NAC, Syslog from RADIUS/NAC | - |
A multi-layered approach ensures the highest possible User-ID coverage and accuracy.
PCNSE Key Concepts: User-ID & GlobalProtect
For the PCNSE exam, a thorough understanding of User-ID and its integration with GlobalProtect is critical. Here are key areas to focus on:
GlobalProtect as a User-ID Source:
- External vs. Internal Gateways: Know their distinct purposes and how each contributes to User-ID. External for remote users (VPN IP mapping), Internal for on-premise users (physical IP or internal pool IP mapping).
- Internal Host Detection (IHD): Understand its role in gateway selection and how misconfiguration impacts User-ID for internal users.
- What happens if IHD fails for an internal user? (They might connect to an external GW).
- Authentication: The authentication event at the Portal and Gateway is fundamental for creating User-ID mappings. Know supported auth methods (LDAP, SAML, Kerberos, RADIUS, cookies).
- Client IP Pools: How IPs are assigned and mapped to users.
- "No Tunnel" / "User-ID Only" Internal Gateway: How it collects User-ID and HIP without full tunneling. Understand Access Route configuration.
- Tunnel Mode Internal Gateway: Advantages for consistent policy enforcement.
User-ID Agent:
- Sources: Server Monitoring (AD Event Logs - know common event IDs like 4768, 4769, 4624), Syslog (RADIUS, 802.1x), Exchange Monitoring.
- Understand the role of the User-ID service account and required permissions.
- Syslog Parse Profiles: How they are used to extract user/IP from syslog messages.
- Terminal Server Agent: Purpose for multi-user environments (RDS/Citrix).
- Configuration: Connecting firewalls to the User-ID agent. Agent redundancy.
Agentless User-ID:
- Captive Portal: Modes (Transparent, Redirect, NTLM), use cases (guest, BYOD), and how it generates mappings. Authentication Policy as a related concept.
- XML API / PAN-OS API: Integration with third-party systems (NACs like ClearPass, ISE).
- VM Monitoring: How it identifies users/owners of VMs.
- Cloud Identity Engine (CIE): Its role as a cloud-based User-ID aggregator and provider.
- Firewall as Syslog Listener: Direct syslog parsing on the firewall.
General User-ID Concepts:
- User-ID Mapping Table: How it's populated, mapping limits per platform.
- User-ID Timeouts: Idle timeout, session timeout – how they affect mapping freshness. Configured under
Device > User Identification > User Mapping. - Group Mapping: How the firewall retrieves user group memberships from LDAP/AD/CIE to use in policies. This is separate from User-ID to IP mapping but relies on it.
- User-ID Redistribution: Methods (Agent as hub, Firewall-to-Firewall, Panorama, CIE).
- Order of Precedence: How the firewall prioritizes mappings from different sources for the same IP.
- Troubleshooting Commands:
show user ip-user-mapping all(or specific IP/user)show user user-id-agent state allshow user group list/show user group name <group_name>debug user-id dump [option](e.g.,hip-report-map,user-map)test user-id-agent [options]- Checking system, userid, globalprotect logs.
- Impact of NAT: How NAT can affect User-ID accuracy if not handled correctly (e.g., if many users are NATted behind a single IP before reaching a resource where User-ID is needed).
Configuration Gotchas & Common Pitfalls
Implementing User-ID effectively requires careful configuration. Here are common gotchas and considerations, incorporating points from the original article's caveats and expanding on them:
GlobalProtect & IHD Related:
- IHD Reliability & Accuracy:
- If IHD targets are down, misconfigured (e.g., wrong IP, port, FQDN), or DNS for IHD FQDNs fails, internal clients might incorrectly connect to an external gateway (getting a VPN pool IP) or fail to connect to any GP gateway.
- Ensure IHD targets are uniquely reachable only from the internal network. Using an internet-resolvable FQDN that points to an internal IP for IHD can be problematic if DNS resolves differently externally.
- User Experience (Internal Gateway): Forcing internal users through an Internal Gateway (especially in tunnel mode) can add slight connection delay or alter their source IP for internal resources if an IP pool is used. Ensure benefits outweigh friction. Communicate changes to users.
- Split Tunnel Complexity (Internal GW): Defining Access Routes and Exclude Routes for internal gateways requires precision. Incorrect configurations can block access to necessary local resources (printers, file shares) or fail to tunnel required traffic.
- Portal vs. Gateway Authentication: Understand how portal authentication (and cookies) can affect gateway authentication. If "Accept Cookie for Authentication" is used on gateways, ensure the cookie lifetime is appropriate.
- Certificate Issues: Ensure GP Portals and Gateways have valid, trusted certificates to avoid connection errors and user warnings.
User-ID Agent & Server Monitoring:
- Service Account Permissions: The User-ID agent's service account needing to read security event logs from Domain Controllers is the #1 point of failure. Ensure it's part of the "Event Log Readers" group on DCs and has necessary network access.
- Windows Firewall / Network Firewalls: Firewalls on DCs or between the User-ID agent and DCs can block communication (RPC, WMI, NetBIOS probes).
- Event Log Configuration: DCs must be configured to log necessary events (e.g., logon success). Log files must be large enough not to overwrite events before the agent reads them.
- Time Synchronization: Kerberos (and accurate log correlation) relies on synchronized time between clients, DCs, User-ID agent server, and the Palo Alto Networks firewall. NTP is crucial.
- Domain Functional Level: Some advanced User-ID features might have dependencies on AD domain/forest functional levels.
- Ignoring "Server Sessions": By default, the User-ID agent might ignore sessions originating from servers. This can be adjusted if server-initiated traffic needs User-ID based on logged-on users (e.g., admins RDP'd to servers).
Syslog & API Based User-ID:
- Syslog Format Mismatch: The format of syslog messages from your source (e.g., RADIUS server) must exactly match what the Syslog Parse Profile on the firewall/agent expects. Any deviation will cause parsing to fail.
- Incomplete Information in Syslog: If syslog messages lack clear username or IP address fields, User-ID mapping will fail.
- API Rate Limiting / Errors: When using the API, ensure your scripts/NAC handle potential API errors, retries, and don't exceed rate limits.
- Trusting API/Syslog Source: Ensure the source providing User-ID information via API or syslog is trusted and secured, as incorrect mappings can lead to policy bypasses.
General User-ID Issues:
- User-ID Timeouts: Setting timeouts too short can cause frequent re-authentication or loss of mapping. Too long can lead to stale mappings if users change IPs without a new login event.
- NAT: If many users are behind a source NAT device before their traffic hits the firewall where User-ID policy is enforced, they will all appear as the same NAT IP, making individual User-ID ineffective for those users *at that firewall*. User-ID should be captured *before* such NAT if possible.
- Multiple Mappings for One IP: In non-persistent VDI or shared workstation scenarios, an IP might get re-assigned quickly. The firewall needs timely updates to reflect the correct current user.
- Group Mapping Delays: Changes in user group memberships in AD might take time to reflect on the firewall due to polling intervals.
- Forgetting to Enable User-ID on Zones: User-ID inspection must be enabled on the relevant source zones where user traffic originates for User-ID based policies to be effective on those zones. (
Network > Zones > [Zone Name] > Enable User Identification).
Troubleshooting User-ID Mappings
When User-ID isn't working as expected, a systematic approach to troubleshooting is essential. Here's a breakdown of common areas and steps:
1. Verify User-ID Mappings on the Firewall:
- CLI Command:
show user ip-user-mapping all(or filter byip <ip_address>,user <domain\username>,type GP,type AD, etc.)- Check if the expected user is mapped to the correct IP.
- Note the "Type" (source of mapping: GP, AD, CP, SYSLOG, API).
- Check "Idle Timeout" and "Max Timeout".
- GUI:
Monitor > User-ID(for mappings) andMonitor > Logs > Traffic(check if User field is populated).
2. Check User-ID Agent Status (if applicable):
- CLI Command (on Firewall):
show user user-id-agent state all- Verify agent connectivity ("Connected"), version, number of mappings.
- Check server monitoring status for each DC (Connected/Disconnected, error messages).
- GUI (on Firewall):
Device > User Identification > User-ID Agents. - On User-ID Agent Server (Windows): Check User-ID agent GUI logs and status. Ensure the service is running.
3. GlobalProtect Issues:
- Agent Logs: Check GlobalProtect agent logs on the client endpoint for connection errors, IHD status, gateway selection.
- Firewall Logs:
Monitor > Logs > GlobalProtect: For Portal/Gateway connection events, authentication, HIP.Monitor > Logs > System: For general system messages related to GP.
- IHD: Manually test IHD target reachability from an internal client.
- Authentication: Test authentication profile used by GP separately (
Device > Authentication Profile > [Profile] > Test).
4. Server Monitoring (AD) Issues:
- Service Account: Verify permissions on DCs (Event Log Readers). Test with a domain admin account temporarily to isolate permission issues.
- DC Event Logs: Manually inspect Security Event Logs on DCs for relevant logon events (4768, 4769, 4624). Are they being generated?
- Connectivity: Ping, WMI, RPC connectivity from User-ID agent server to DCs. Check Windows Firewall on DCs.
- Time Sync: Ensure time is synchronized.
- User-ID Agent Server Logs: Detailed logs here can pinpoint DC communication failures.
5. Syslog Issues:
- Firewall/Agent Logs: Check User-ID agent logs or firewall system logs (if firewall is direct listener) for received syslog messages.
- Packet Capture: On the firewall/agent interface listening for syslog, capture traffic to see if messages are arriving from the source.
- Syslog Parse Profile: This is a common culprit. Ensure the Event Regex, Username Regex, and IP Address Regex correctly match the incoming syslog message format. Use the "Test Syslog Parse Profile" tool on the firewall.
- Source Configuration: Verify the syslog source (e.g., RADIUS server) is configured to send messages to the correct IP/port of the firewall/agent.
6. Captive Portal / Authentication Policy:
- Policy Hits: Ensure the Authentication Policy rule or Security Policy rule triggering Captive Portal is being hit.
- Authentication Profile: Test the Authentication Profile used by CP.
- Browser Issues: Test from different browsers, clear cache/cookies. Check for SSL certificate errors if using HTTPS for CP.
- Redirect Issues: Ensure DNS is working correctly for any redirects.
7. Group Mapping Issues:
- CLI Command:
show user group list(see if groups are populated),show user group name "<DOMAIN\group_name>"(see members). - LDAP Server Profile: Test connectivity to LDAP server (
Device > Server Profiles > LDAP > [Profile] > Test). Verify Base DN, Bind DN, filters. - Group Include List: Ensure the desired groups are in the include list in
Device > User Identification > Group Mapping Settings. - Polling Interval: Check the interval for fetching group updates.
8. Debug CLI Commands (Use with Caution):
// General User-ID debug
debug user-id set traceinfo level high
debug user-id dump user-map ip <ip_address>
debug user-id dump group-map group <group_name>
debug user-id dump hip-report-map ip <ip_address>
less mp-log useridd.log
less mp-log authd.log (for authentication issues)
// To clear debug
debug user-id set traceinfo level none
User-ID & GlobalProtect Best Practices Summary
This section combines best practices from the original article and new User-ID specific recommendations.
GlobalProtect Specific:
- Use Internal Gateways for Zero Trust: Implement Internal Gateways for consistent security policy enforcement and device posture checks for all users, aligning with Zero Trust principles. This also provides an excellent User-ID source.
- Configure Reliable IHD: Use multiple, stable IHD targets (IPs or FQDNs) that are uniquely reachable *only* from inside the network. Test IHD thoroughly.
- Separate Zones for GP Tunnels: Use distinct Security Zones for external gateway tunnels (e.g.,
GP-External) and internal gateway tunnels (e.g.,GP-Internal) for granular policy control. - Consistent Authentication: Aim for consistent or seamless authentication methods (e.g., SAML, Kerberos, cookies) across portals and gateways to improve user experience.
- Tailor Agent Client Settings: Carefully configure IP Pools, DNS, and especially Split Tunnel Access Routes appropriately for internal vs. external client settings within the respective Gateway configurations.
- Use FQDNs for Portals/Gateways: Instead of IP addresses, use FQDNs for easier management and certificate handling.
- Regularly Update GP Agent: Keep GlobalProtect client software updated to benefit from security patches and new features.
User-ID Specific:
- Employ Multiple User-ID Sources: Use a combination of methods (GlobalProtect, User-ID Agent, API, Captive Portal, CIE) for comprehensive coverage.
- Prioritize Reliable Sources: Prefer direct authentication methods like GlobalProtect or API integrations with NACs over probing methods.
- Secure the User-ID Agent: If using the Windows User-ID agent, ensure the server is hardened, the agent software is updated, and communication is secured. Use a dedicated service account with least privilege.
- Optimize User-ID Timeouts: Configure User-ID timeouts (idle and session) appropriately for your environment to balance mapping freshness with performance.
- Enable User-ID on Relevant Zones: Ensure User-ID is enabled on all source zones where you want to enforce identity-based policies.
- Implement User-ID Redistribution: In multi-firewall environments, use Panorama, User-ID agents, or firewall-to-firewall redistribution to ensure consistent mappings.
- Monitor User-ID Mappings: Regularly check the User-ID mapping table and agent status to proactively identify issues. Set up alerts for User-ID agent disconnections.
- Plan for Scale: Be aware of User-ID mapping limits per firewall platform and design your User-ID infrastructure accordingly.
- Thoroughly Test Syslog Parsing: If using syslog as a source, meticulously test your Syslog Parse Profiles.
- Group Mapping Best Practices: Use specific Group Include Lists rather than fetching all groups. Ensure LDAP/AD server profiles are correctly configured and redundant.
By following these best practices, you can build a robust and reliable User-ID infrastructure that significantly enhances your network security posture.
Comprehensive User-ID & GlobalProtect Quiz
1. What is the primary purpose of Internal Host Detection (IHD) in a GlobalProtect deployment?
2. An administrator wants to collect User-ID mappings for on-premise users via an Internal GlobalProtect Gateway without forcing all their traffic through a tunnel. Which configuration aspect is most critical for this?
3. Which User-ID collection method involves the User-ID agent reading security event logs from Domain Controllers?
4. What is a primary advantage of using an Internal GlobalProtect Gateway in TUNNEL mode for on-premise users?
5. A company uses Cisco ISE for 802.1x authentication. How can User-ID mappings from ISE be sent to the Palo Alto Networks firewall?
6. Which Palo Alto Networks component is primarily responsible for distributing the list of available Internal and External GlobalProtect Gateways to the GP agent?
7. What is the primary role of the Palo Alto Networks Cloud Identity Engine (CIE)?
8. A user logs into a Windows domain. The User-ID agent is configured for Server Monitoring. Which Windows Event IDs are commonly monitored for Kerberos authentication to obtain User-ID mappings?
9. What firewall CLI command is used to display the current User-ID to IP address mappings?
show user ip-user-mapping all (or with filters like ip <ip> or user <user>) is used to view the active User-ID mappings on the firewall.10. If multiple sources provide a User-ID mapping for the same IP address, how does the firewall typically decide which mapping to use?
11. Which User-ID method is most suitable for identifying users on a guest wireless network where devices are unmanaged?
12. User-ID redistribution can be facilitated by which of the following? (Select all that apply)
13. What is a common "gotcha" when configuring User-ID Agent server monitoring for Active Directory?
14. Enabling User-ID inspection on a security zone in PAN-OS is necessary for:
15. What is the primary purpose of a Syslog Parse Profile in the context of User-ID?
16. A user is mapped to an IP address. If the "User-ID Timeout" is configured to 60 minutes and the user is continuously active, when will the mapping expire by default?
17. For multi-user environments like Citrix or RDS, which User-ID agent feature is specifically designed to differentiate users sharing the same server IP?
18. Which of these is NOT a direct method for the Palo Alto Networks firewall to learn User-ID to IP mappings?
19. A security policy is written to allow access for the "Engineering" AD group. What component is responsible for providing the firewall with the list of users belonging to the "Engineering" group?
20. If an internal user successfully authenticates via GlobalProtect Internal Gateway configured for "User-ID only" (non-tunnel mode), which IP address is typically mapped to the user in the User-ID table?