Redistribute HIP Information with Prisma Access
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To ensure consistent Host Information Profile (HIP) policy enforcement and to simplify policy management , you can redistribute HIP information received from mobile users and users at remote networks that use the GlobalProtect app from Prisma Access to other gateways, firewalls, and Panorama appliances in your enterprise, including the Panorama that manages Prisma Access .
PCNSE/PCNSA Note: Understanding HIP redistribution is key for centralized policy management and consistent security posture across your network, including remote users.
The following section (Use Cases) describes some common Prisma Access deployments where HIP redistribution is useful for consistent policy enforcement and HIP report viewing.
Common HIP Redistribution Use Cases
The following scenarios illustrate the value of HIP redistribution with Prisma Access :
HIP redistribution from Prisma Access to a next-generation firewall
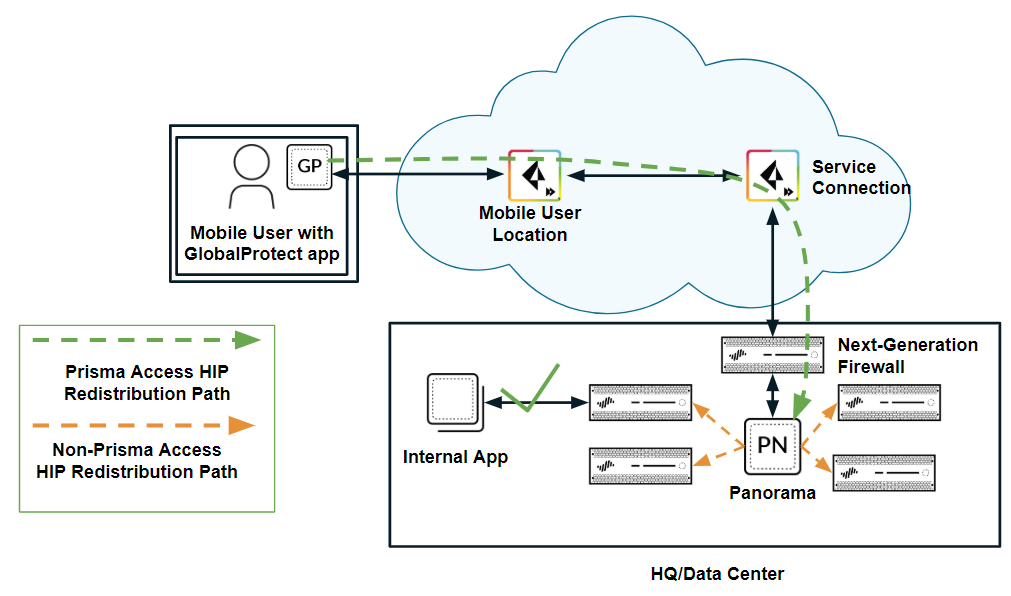
If you have a next-generation firewall in your organization’s data center or headquarters location, and have configured that firewall with HIP-based security policies , you cannot enforce those policies for Prisma Access mobile users until you redistribute HIP redistribution from Prisma Access to the firewall.
The following figure shows a mobile user whose endpoint is protected with the GlobalProtect app. The user attempts to access an internal app at an HQ/data center whose access is controlled by a next-generation firewall with HIP-based security policies. When the user logs in to the GlobalProtect app, the app collects HIP information and sends it to Prisma Access ; however, Prisma Access does not redistribute this information to the on-premises firewall. Since the firewall does not have the user’s HIP information, it blocks the user’s access to the app.
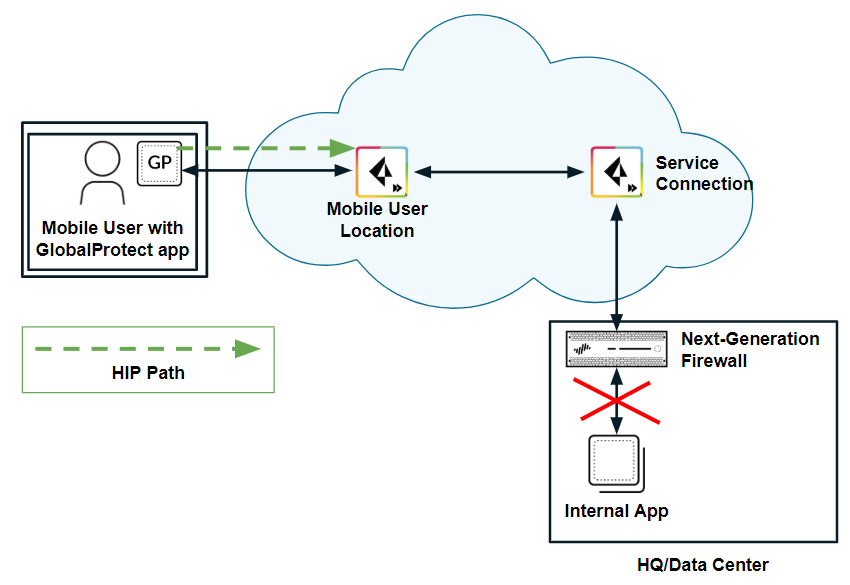
Scenario 1: Access Blocked Without HIP Redistribution
HIP redistribution allows you to distribute the mobile users’ HIP information to the on-premises firewall . The firewall can then check the user’s HIP information against its configured security policies and grant the user access to the app.
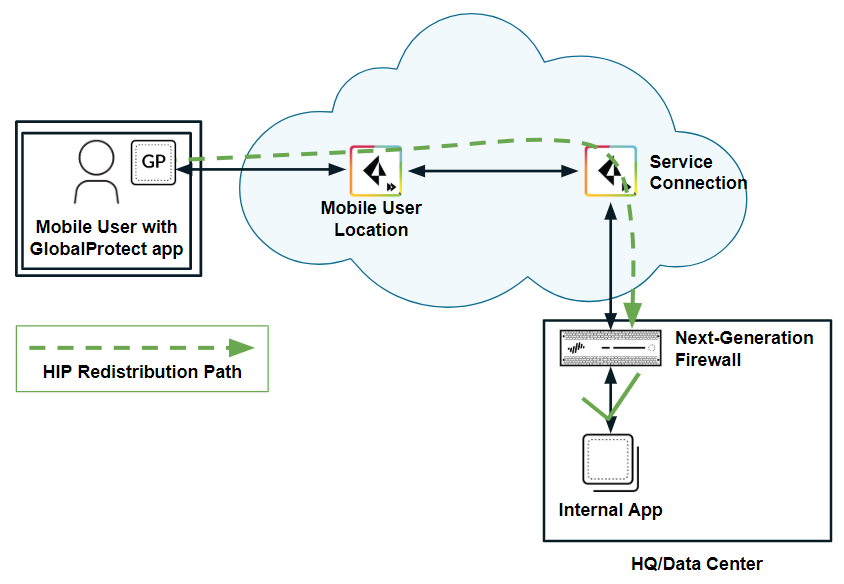
Scenario 1: Access Granted With HIP Redistribution
To redistribute HIP information from Prisma Access to the firewall, you allow Prisma Access to redistribute HIP information, then Add a User-ID Agent (Panorama > User Identification > User-ID Agents for 9.1. x Panorama appliances or Panorama > Data Redistribution for Panorama 10. x appliances) on the firewall, and specify the Prisma Access User-ID Agent Address (Panorama > Cloud Services > Status > Network Details > Service Connection > User-ID Agent Address) as the Host (e.g., 10.1.1.1) and 5007 as the Port .
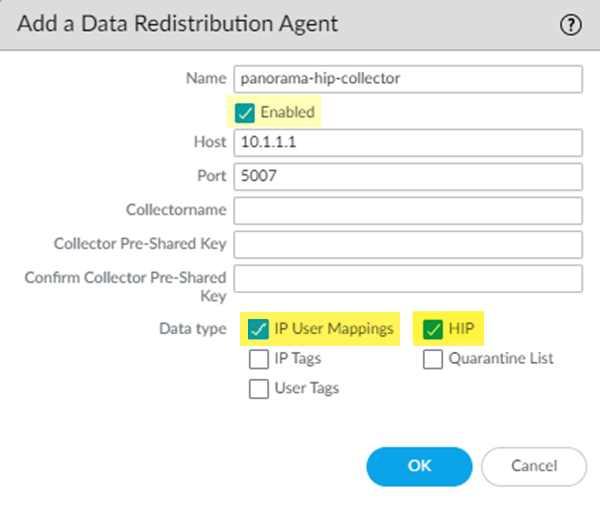
User-ID Agent Configuration (Host and Port)
HIP redistribution from Prisma Access to Panorama
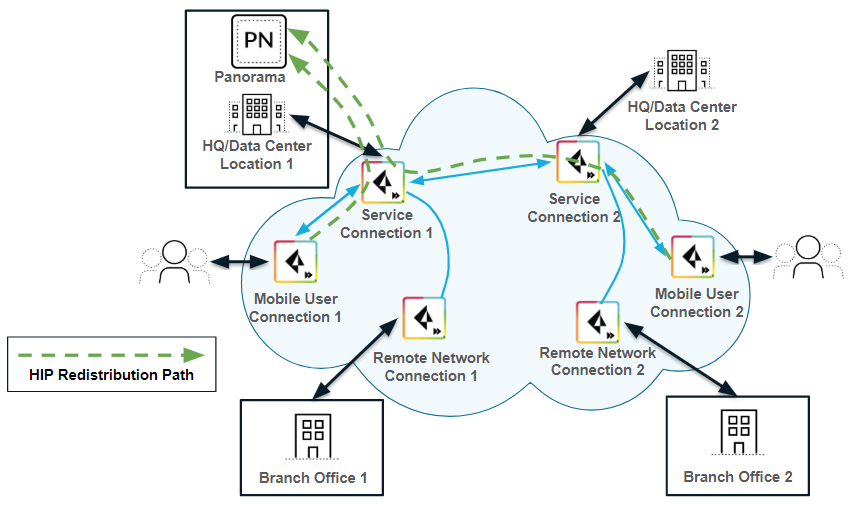
If you have multiple firewalls or gateways in your organization with HIP-based security policies, you can redistribute the HIP information from Prisma Access to the Panorama that manages Prisma Access by creating a User-ID agent in Panorama and specifying the Prisma Access User-ID Agent Address as the User-ID Host . You can then redistribute HIP reports from that Panorama appliance to the other managed Panorama appliances, gateways, firewalls, and virtual systems in your enterprise, using the same workflow that you use to redistribute User-ID information to managed firewalls and enforce consistent policy for internal apps and resources, as shown in the following figure.
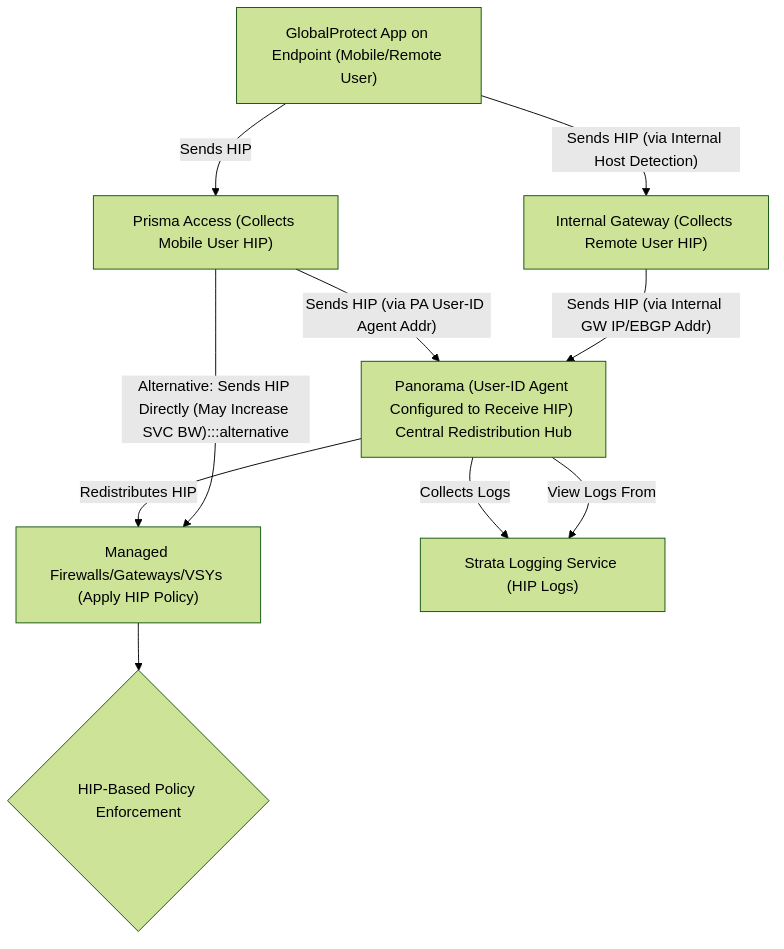
Scenario 2: Prisma Access redistributing HIP to Panorama, then Panorama redistributing
Alternatively, you can configure each internal firewall or gateway in your enterprise to directly collect HIP information from Prisma Access , without using Panorama as a central location, by creating a User-ID Agent in each device. Note, however, that Prisma Access uses service connections to send HIP information, and service connection bandwidth consumption might increase if Prisma Access sends a large number of HIP reports.
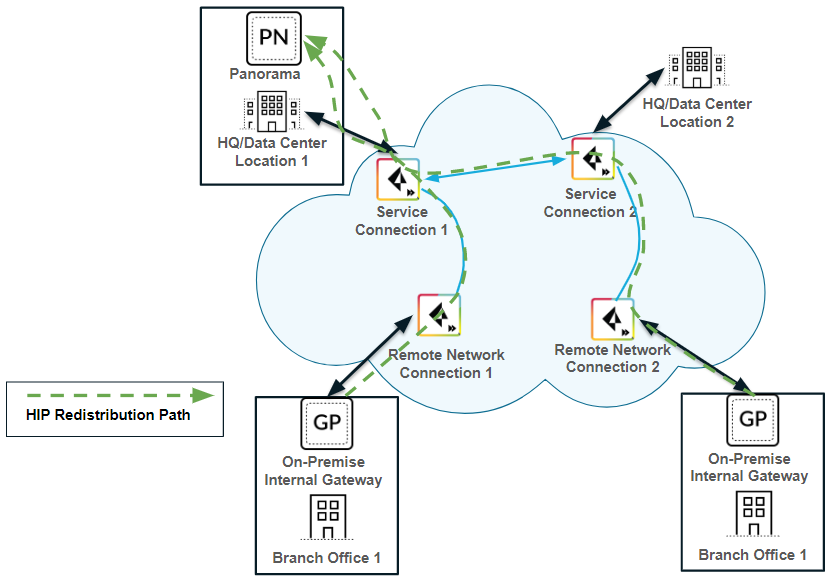
HIP redistribution from a user at a remote network to Prisma Access
The previous use cases showed Prisma Access collecting HIP information from mobile users. If you want to apply HIP-based policies in Prisma Access for a user at a remote network location, you need a way to distribute the HIP information from the remote network user’s GlobalProtect app to Prisma Access .
The following example shows a user at a remote network location whose internet access is located on the remote network connection. In Prisma Access , you control the user’s internet access at the remote network location with security policies created in the Remote_Network_Device_Group or in a shared device group. To properly enforce the policies at the remote network location for the user, you need to configure Prisma Access to retrieve the user’s HIP information from the internal gateway.
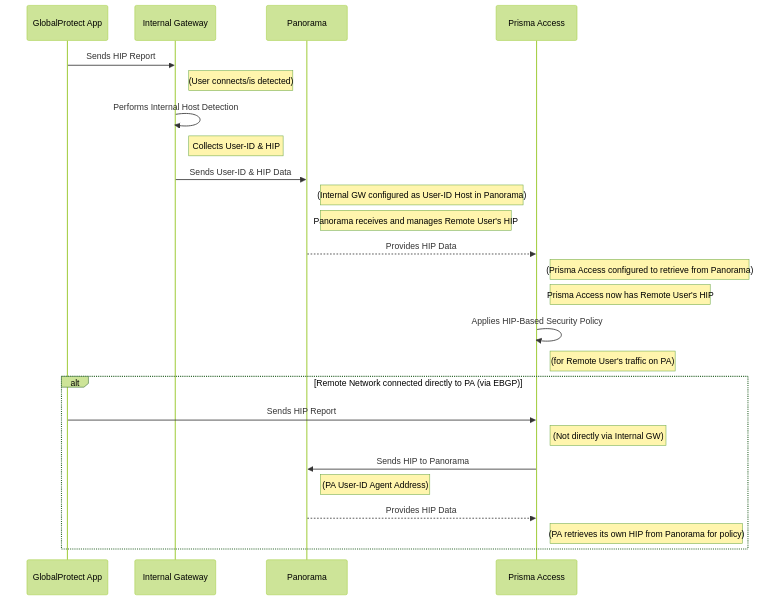
In this example, the GlobalProtect gateway at the HQ/data center that is configured as an internal gateway using internal host detection checks the user’s HIP information from the user’s GlobalProtect app. The internal gateway detects that the user is inside the remote network location and collects both User-ID and HIP information from the user.
To distribute this HIP information from the internal gateway to Prisma Access, create a User-ID agent in Panorama and specify the IP address of the internal gateway as the host.
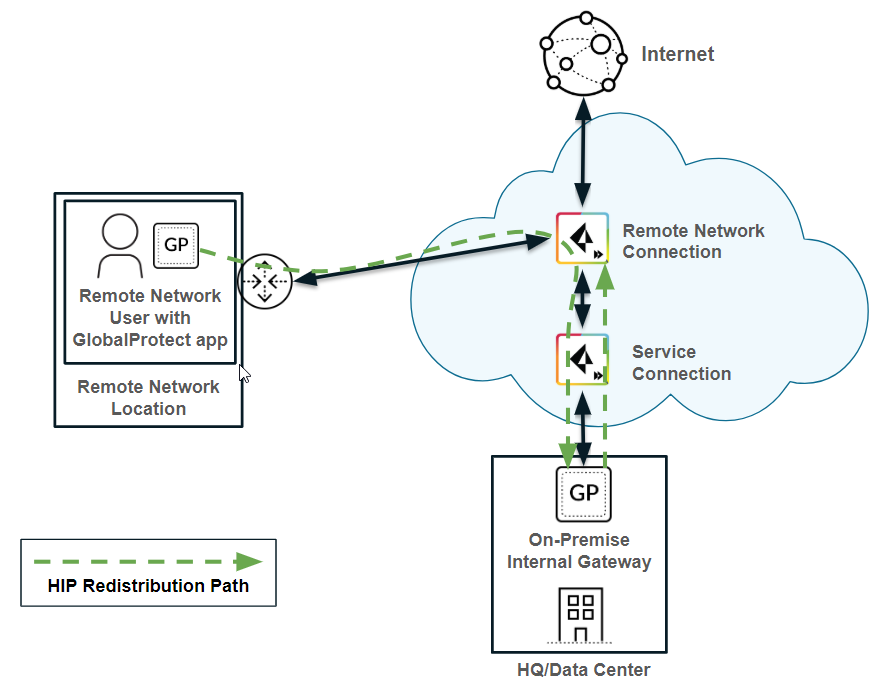
Scenario 3: Remote Network User HIP distributed via Internal Gateway and Panorama to Prisma Access
View detailed HIP logs from Panorama
When mobile users log in using the GlobalProtect app, the app sends the HIP information to Prisma Access . Panorama retrieves the log results from Strata Logging Service to view the results of the HIP Match logs (Monitor > Logs > HIP Match); however, you cannot view detailed HIP reports until you configure Panorama to redistribute HIP report details from Prisma Access to Panorama.
HIP Match Logs in Panorama (Summary View)
To redistribute detailed HIP information from mobile users to Panorama, create a User-ID agent in Panorama and specify the User-ID Agent Address (Panorama > Cloud Services > Status > Network Details > Service Connection > User-ID Agent Address) as the User-ID host.
If you have configured an on-premises gateway as an internal gateway at a remote user location, you can also send the HIP information for users at remote networks to Panorama by creating a User-ID agent in Panorama and specifying the remote network EBGP Router address (Panorama > Cloud Services > Status > Network Details > Remote Networks > EBGP Router) as the User-ID host.
Location of EBGP Router Address in Panorama
PCNSE/PCNSA Note: Recognize the different sources of HIP information (mobile users, remote networks via internal gateway/EBGP) and how they are configured for redistribution via User-ID agents in Panorama.
Gotcha: GlobalProtect internal and external gateways don't support bi-directional HIP redistribution directly. The best practice is to use Panorama as the central redistribution point.
Configuration: Strata Cloud Manager
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
HIP report redistribution is enabled by default in Strata Cloud Manager. To view the redistribution details or to disable redistribution, follow the steps below.
- In Strata Cloud Manager , select Manage > Configuration > NGFW and Prisma Access > Identify Services > Identify Redistribution .
The Prisma Access Identity Redistribution Diagram displays the default HIP report redistribution settings between mobile users and service connections as well as between remote networks and service connections.
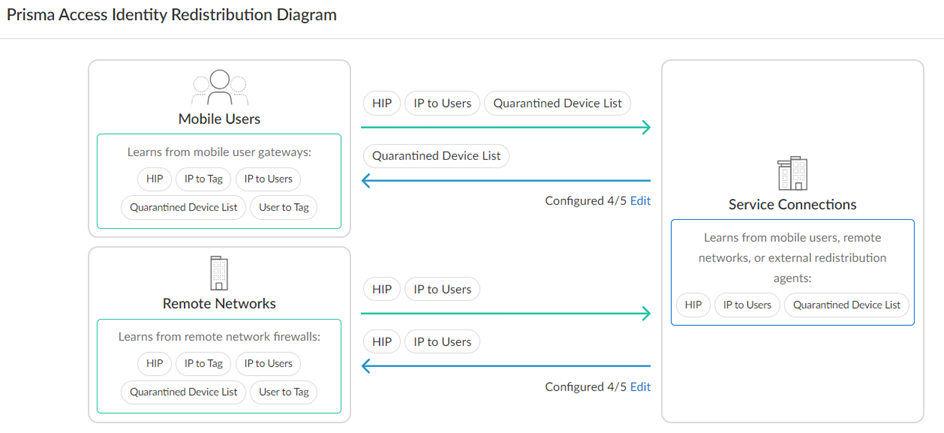
Prisma Access Identity Redistribution Diagram (Strata Cloud Manager)
PCNSE/PCNSA Note: Know that SCM enables HIP redistribution by default, and how to verify/disable it in the UI.
- To disable redistribution between a segment, click Edit and then click Edit next to the relevant source remote network.
- Disable HIP .
Configuration: Panorama
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To allow Prisma Access to collect and redistribute HIP information when managed by Panorama, complete the following task.
-
Allow
Prisma Access
to redistribute HIP information.
- In Panorama, select Panorama > Cloud Services > Configuration > Service Setup .
- Click the gear icon to edit the settings.
- In the Advanced tab, select Enable HIP Redistribution .
Enabling HIP Redistribution enables Prisma Access to redistribute the HIP reports received from the GlobalProtect app to internal firewalls and to Panorama.
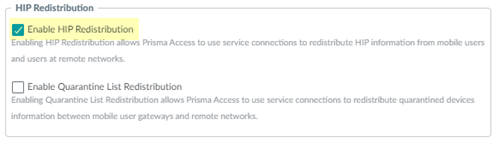
Enabling HIP Redistribution in Panorama Cloud Services
-
Configure Panorama to receive HIP reports from
Prisma Access
.
- Select Panorama > Setup > Interfaces .
- Select the Management interface.
- Select User-ID .
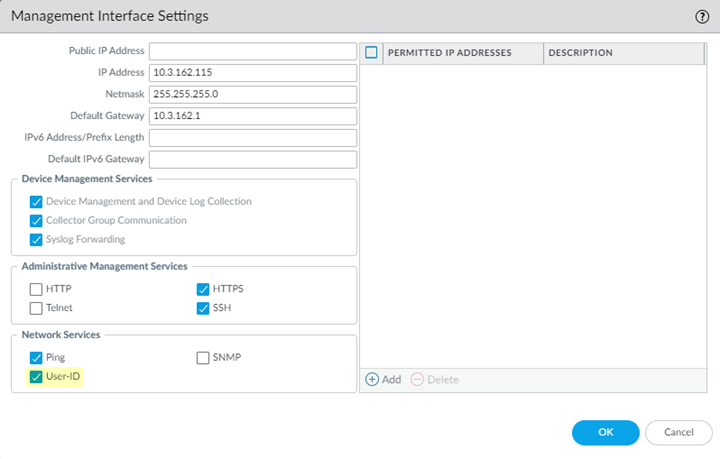
Enabling User-ID on Panorama Management Interface
-
Configure Panorama to collect the User-ID mapping from
Prisma Access
.
- From the Panorama that manages Prisma Access , select Panorama > Data Redistribution > Agents (for Panorama 10. x appliances) or Panorama > User Identification > User-ID Agents (for 9.1. x Panorama appliances).
- Add a User-ID Agent and give it a Name .
-
Enter one of the following values in the
Host
field, depending on the types of HIP information you want to collect.
- To collect HIP information for mobile users, enter the User-ID Agent Address ( Panorama > Cloud Services > Status > Network Details > Service Connection > User-ID Agent Address ).
- To collect HIP information from users at a remote network locations with an internal gateway, enter the IP address of the internal gateway.
- To collect HIP information from users are a remote network connection, enter the EBGP Router address ( Panorama > Cloud Services > Status > Network Details > Remote Networks > EBGP Router ) as the User-ID host.
- Enter 5007 in the port field.
Critical Point: The User-ID agent uses port 5007 by default to listen for HIP information. Ensure this port is open in your network between Prisma Access and the Panorama/device collecting HIP.
- Select Enabled to enable Panorama to communicate with the User-ID agent.
- Select IP User Mappings and HIP to enable Panorama to receive IP address-to-username mappings and GlobalProtect HIP data from all mobile user locations.
- Click OK .

User-ID Agent Configuration (Full View)
- Repeat Step 3 for each service connection or remote network from which you want to configure HIP report collection.
PCNSE/PCNSA Note: This configuration process (Enabling HIP, Enabling User-ID on interface, Configuring User-ID agent) is a frequently tested topic. Understand the different host addresses used for mobile users vs. remote networks.
View HIP Reports
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
After you configure Prisma Access to collect and redistribute HIP information to Panorama, use the following workflow to view HIP information in Panorama.
- Select Monitor > Logs > HIP Match to view HIP information.
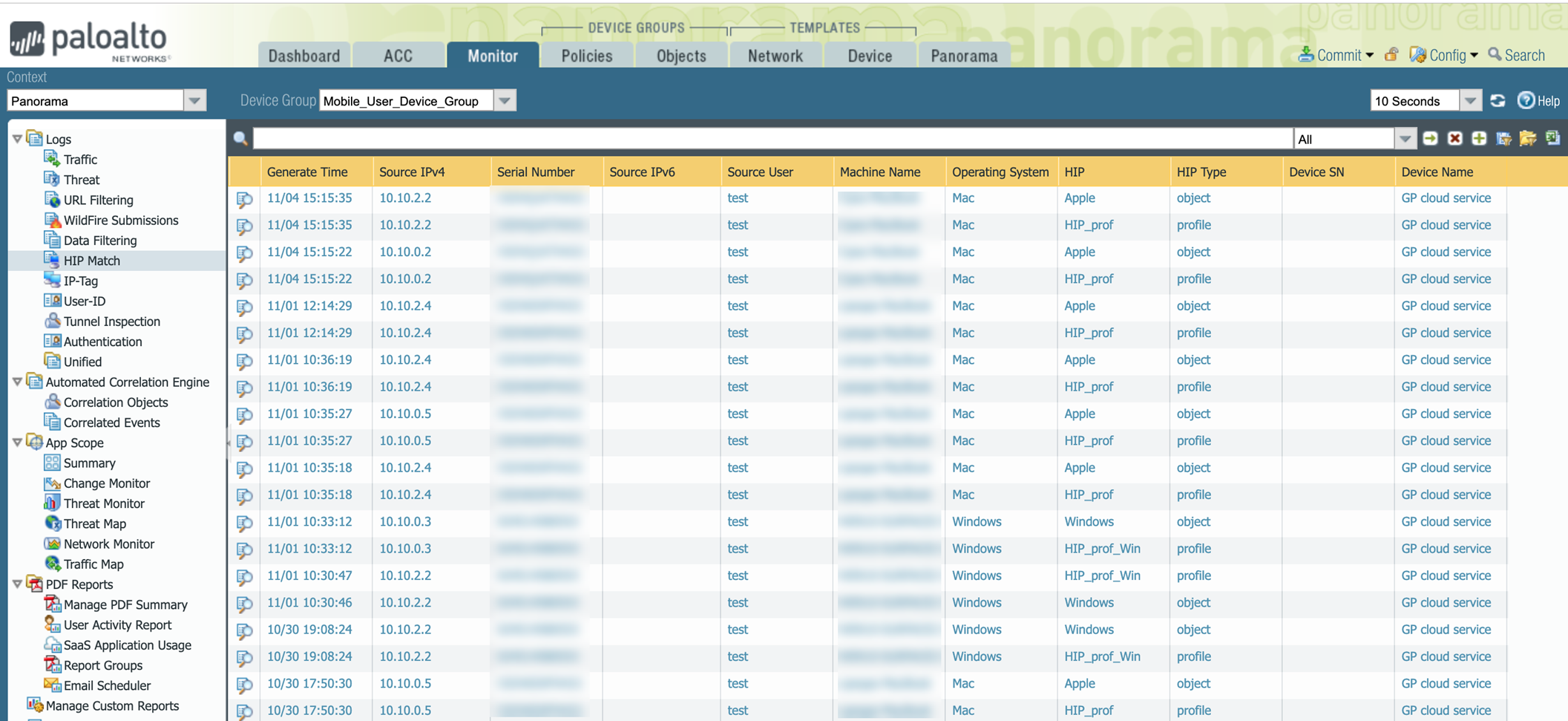
Panorama HIP Match Logs View
- Click the icon to the left of a record to view detailed HIP information.
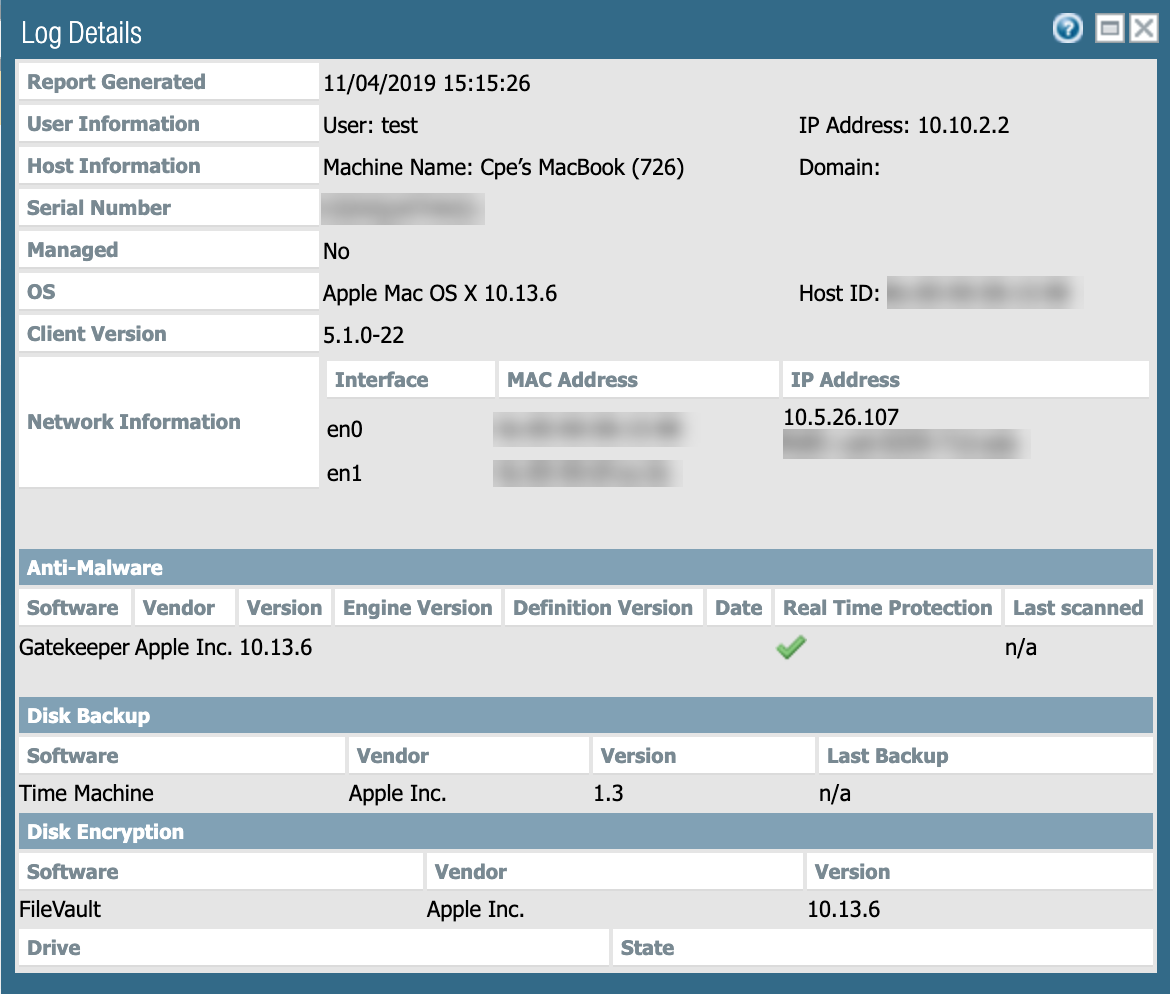
Detailed HIP Report in Panorama
PCNSE/PCNSA Note: Knowing where to find and interpret HIP Match logs and detailed HIP reports is important for verifying policy enforcement and troubleshooting.
Quiz: Test Your Knowledge
Answer the following questions based on the content you've reviewed.