User-ID: Agent vs. Agentless - A Deep Dive
What is User-ID?
User-ID is a cornerstone feature of Palo Alto Networks Next-Generation Firewalls (NGFWs). Its primary function is to map IP addresses to usernames . This seemingly simple capability unlocks powerful, granular visibility and control over network traffic based on user identity rather than just static IP addresses, which can be dynamic or shared.
Imagine trying to understand network activity or enforce security policies when all you see are IP addresses. It's like trying to manage building access by only knowing room numbers without knowing who occupies them. User-ID provides the "who" behind the IP address.
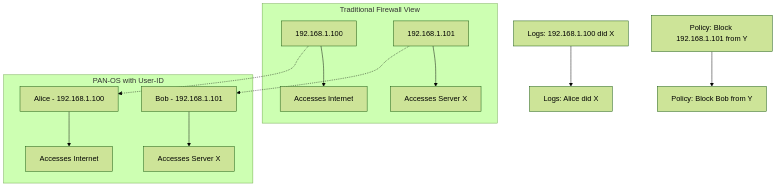
User-ID transforms anonymous IP-based logging and policies into user-centric ones.
PAN-OS offers two main architectural approaches for collecting these IP-to-user mappings:
- Windows-based Usfer-ID Agent: A dedicated piece of software installed on a Windows server.
- Agentless User-ID (PAN-OS Integrated User-ID Agent): Functionality built directly into the firewall's operating system (PAN-OS).
This article will delve into both options, comparing their mechanisms, capabilities, and deployment considerations.
Why User-ID Matters
Implementing User-ID is fundamental for modern network security and provides several key benefits:
-
User-Based Visibility:
Transforms logs (Traffic, Threat, URL Filtering, Data Filtering, WildFire) and reports (Application Command Center - ACC) from IP-centric to user-centric. Instead of seeing
10.1.1.5 accessed facebook.com, you seeDOMAIN\jsmith accessed facebook.com. This dramatically improves the ability to understand network usage patterns. - Granular Policy Control: Enables the creation of Security, QoS, Decryption, Authentication, and PBF policies based on users and Active Directory (AD) or LDAP groups. For example, you can allow the "Engineering" group access to specific development servers while denying the "Sales" group, or apply stricter URL filtering to "Interns".
- Enhanced Incident Response: When a threat is detected from an IP address, User-ID allows security teams to quickly identify the associated user, streamlining investigation and remediation. This is crucial for understanding the scope and impact of a security incident.
- Accurate Reporting and Auditing: Provides user-centric audit trails necessary for compliance with various regulations (e.g., PCI DSS, HIPAA, SOX) which often require tracking user activity.
- Application Function Control: Allows granular control over specific functions within applications based on user identity (e.g., allowing "Managers" to post on social media but "Employees" only to read).
General User-ID Mapping Sources
Both the dedicated User-ID Agent and Agentless User-ID can leverage a variety of sources to build and maintain the IP-address-to-username mapping table. The firewall or agent will attempt to gather mappings from these configured sources, prioritizing them based on configuration.
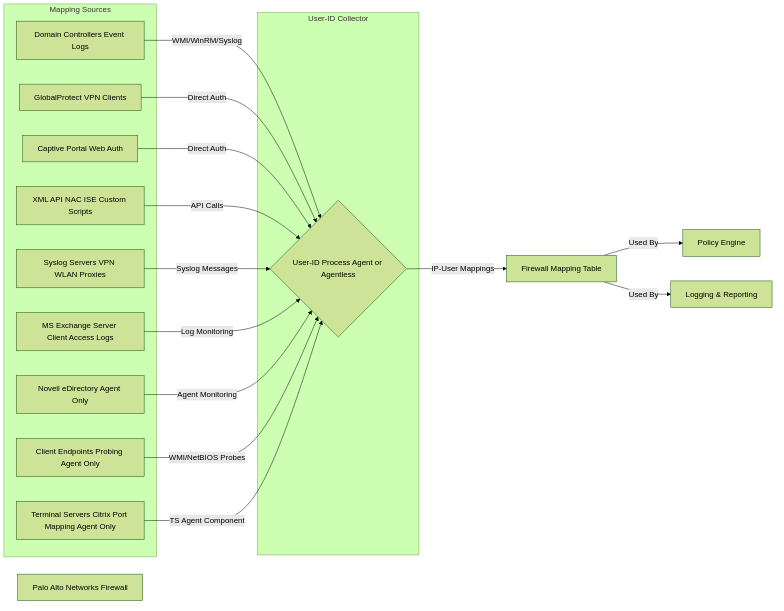
Overview of common User-ID mapping sources feeding into the User-ID collection process.
Here's a breakdown of common sources:
-
Server Monitoring (Primary for Domain Users):
This is the most common and generally most reliable method for domain-joined Windows clients. The User-ID process (either on the Agent or the firewall itself) monitors security event logs on Microsoft Domain Controllers (DCs).
- It looks for successful user logon events (e.g., Event ID 4624 on modern Windows Servers, 672 on older ones, or Kerberos TGT events).
- The connection to DCs is typically made using WMI (Windows Management Instrumentation) or WinRM (Windows Remote Management) .
- Alternatively, DCs can be configured to forward relevant event logs via Syslog to the User-ID Agent or firewall.
- Network Access Control (NAC) solutions (e.g., Aruba ClearPass, Cisco ISE).
- Custom scripts or third-party authentication systems.
- Wireless LAN Controllers (WLCs) that can identify users.
- VPN concentrators from other vendors.
- Wireless controllers.
- Proxy servers.
- Other authentication systems.
- This method is generally less recommended due to potential performance impact on client machines and the agent server.
- It requires firewall exceptions on client endpoints.
- It can be unreliable if clients are offline or block probes.
- This component assigns a unique range of source ports to each user session.
- It then sends this user-to-IP-and-port-range mapping to the main User-ID Agent, which relays it to the firewall.
- The firewall can then differentiate users on the same terminal server IP based on their source port range.
Key Takeaway: The firewall builds a table of IP-to-user mappings from these various sources. When traffic arrives, the firewall consults this table to identify the user associated with the source IP address of the packet.
Dedicated Windows User-ID Agent
Architecture and Function
The Windows User-ID Agent is a software application provided by Palo Alto Networks that is installed on a Windows Server machine within your environment. This server can be a member server or, less ideally, a Domain Controller (a member server is generally preferred to reduce load on DCs and for security separation).
Key architectural points:
- Centralized Collector: The Agent server acts as a central point for collecting IP-to-user mapping information from the various sources you configure (DCs, Exchange, Syslog, etc.).
- Processing Offload: It offloads the task of querying sources and processing mapping information from the firewall's management plane.
- Redistribution: Once the Agent has gathered mappings, it securely redistributes this information to one or more Palo Alto Networks firewalls or to Panorama (which can then redistribute to managed firewalls). Communication between the Agent and firewalls typically occurs over TCP port 5007.
- Software Installation: Requires downloading and installing the User-ID Agent software package from the Palo Alto Networks support portal.
- Service Account: The Agent runs under a service account that requires specific permissions to access event logs and other information from monitored servers.
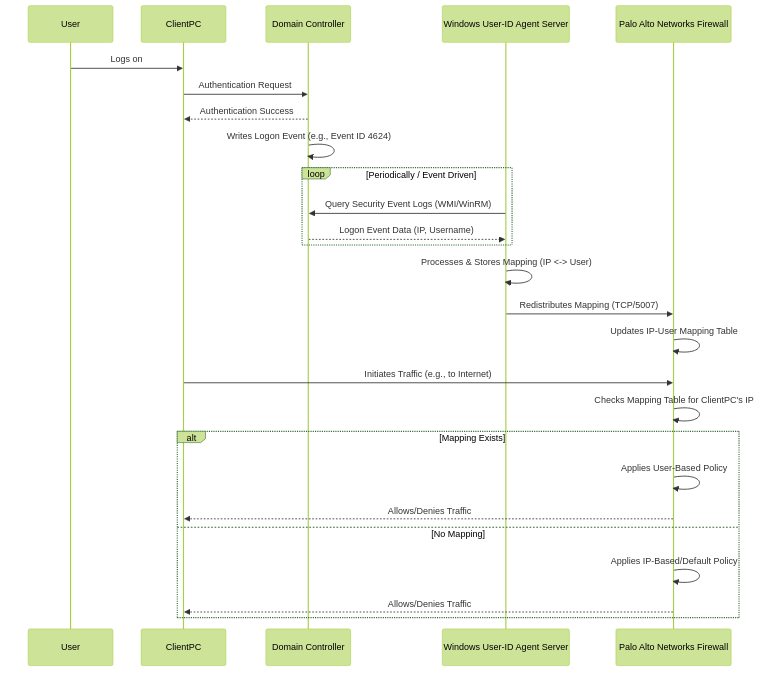
High-level sequence of mapping collection and usage with a dedicated Windows User-ID Agent.
Agent Mapping Methods
The Windows User-ID Agent supports a comprehensive set of methods for discovering IP-to-user mappings:
-
Server Monitoring (Primary):
- Connects to Domain Controllers (DCs) using a service account via WMI or WinRM to remotely read Security Event Logs for logon events.
- Can be configured to automatically discover DCs in the domain.
- Can also receive Syslog messages from DCs if they are configured to forward event logs.
- Connects to Microsoft Exchange Servers (typically Client Access Servers) to monitor logs for user activity associated with IP addresses (e.g., OWA, ActiveSync).
- Specifically supports monitoring Novell eDirectory environments for user login events.
- Can be configured to actively probe client workstations using NetBIOS or WMI to determine the logged-on user.
- This is generally less preferred due to potential performance overhead and reliability issues but can be a fallback or used for non-domain machines if other methods are unavailable.
- Requires appropriate firewall exceptions on client endpoints.
- Requires a separate component (Terminal Server Agent or TS Agent) installed directly on Microsoft RDS (Remote Desktop Services) hosts or Citrix XenApp/XenDesktop servers.
- This component identifies users on shared-IP terminal servers by allocating a unique range of source TCP/UDP ports to each user session.
- The TS Agent then sends (IP, Port Range, Username) mappings to the main User-ID Agent.
- The Agent can act as a syslog server, listening for syslog messages from various network devices (VPNs, WLAN controllers, proxies, etc.).
- Requires configuring Syslog Parse Profiles on the Agent to extract IP and username information from these messages.
- The Agent can receive IP-to-user mappings via XML API calls from external systems like NAC solutions (Cisco ISE, Aruba ClearPass), custom scripts, or other identity management platforms.
-
The Agent can parse
X-Forwarded-ForHTTP headers from an upstream proxy server. If the proxy authenticates users and includes their username (typically inDOMAIN\usernameformat) in this header, the Agent can create a mapping.
Information Captured by User-ID Agent
Regardless of the source, the primary goal is to establish a mapping between an IP address and a user. The core information captured and stored by the User-ID Agent, which is then sent to the firewall, includes:
- IP Address: The IPv4 or IPv6 address of the user's device.
-
Username:
The identified user, typically in
DOMAIN\username(SAMAccountName) format oruser@domain.com(User Principal Name - UPN) format. - Domain Name: The domain to which the user belongs (if applicable).
- Timestamp of Mapping Creation: When the mapping was learned by the agent. This is used for aging out stale mappings.
- Source of Mapping: An indicator of how the mapping was learned (e.g., "SM" for Server Monitor, "GP" for GlobalProtect, "API" for XML API, "TS" for Terminal Server Agent).
Additionally, depending on the specific mapping method, more contextual information might be involved:
- For Server Monitoring: The name of the Domain Controller that reported the logon event and the specific Event ID might be logged by the agent for troubleshooting.
- For Terminal Server (TS) Agent: Crucially, the source port range allocated to the user on the terminal server is captured along with the IP and username. The firewall uses this port range to distinguish between different users on the same terminal server IP.
- For Syslog or API: The data parsed or received will depend on what the source system sends, but must resolve to an IP and a username for User-ID to use it effectively.
It's important to note that user group membership information is NOT directly part of the IP-to-user mapping itself . Group memberships are retrieved by the firewall through a separate Group Mapping process (typically by querying an LDAP server like Active Directory). The firewall then correlates the username from the IP-to-user map with its known group memberships to apply group-based policies.
Pros & Cons (Windows User-ID Agent)
Pros:
- Scalability: Generally better suited for very large environments with a high number of Domain Controllers, users, and logon events. The dedicated server resources can handle higher processing loads.
- Dedicated Resources: Runs on its own server, offloading CPU and memory consumption from the firewall's management plane. This can be critical for firewall performance in busy networks.
-
Broader Source Compatibility:
Historically, and still for some specific sources, the Agent offers more comprehensive support. Key examples include:
- Novell eDirectory monitoring.
- Client Probing (WMI/NetBIOS to endpoints).
- Terminal Server Agent for detailed port-based mapping in RDS/Citrix environments.
- Centralized Collection Point: Can act as a single point of collection from numerous, diverse sources and then redistribute these mappings to multiple firewalls or Panorama. This simplifies management in distributed environments.
- Advanced Filtering and Debugging: The Agent software provides its own GUI and logging, which can offer more granular control over source configuration, filtering of events, and dedicated troubleshooting tools.
- High Availability (HA): Multiple User-ID Agent instances can be deployed for redundancy. Firewalls can be configured to connect to primary and secondary agents.
Cons:
-
Requires Dedicated Windows Server(s):
This introduces additional infrastructure overhead:
- Windows Server OS license costs.
- Server hardware or virtual machine resources.
- Ongoing server maintenance, patching, and security hardening.
- Agent Installation & Maintenance: The User-ID Agent software itself needs to be installed, configured, and periodically updated to newer versions.
-
Network Connectivity & Firewall Rules:
Requires careful planning of network connectivity and firewall rules:
- Agent server to Domain Controllers (WMI/WinRM, LDAP, etc.).
- Agent server to Exchange servers.
- Agent server to firewalls/Panorama (typically TCP/5007).
- Potentially Agent server to clients (for client probing).
Agentless User-ID (PAN-OS Integrated Agent)
Architecture and Function
Agentless User-ID refers to the capability of the Palo Alto Networks firewall (or Panorama) to perform IP-to-user mapping collection directly using its own PAN-OS software . The User-ID logic, in this case, runs as a process on the firewall's management plane . This is often referred to as the "PAN-OS Integrated User-ID Agent."
Key architectural points:
- No Separate Server: No dedicated Windows server or external software installation is required for the core collection tasks.
- Direct Connection to Sources: The firewall's management interface (or a service-routed interface) connects directly to sources like Domain Controllers (using WMI/WinRM) or syslog servers.
- Configuration within PAN-OS: All User-ID source configurations (Server Monitoring, Syslog Parse Profiles, etc.) are done directly within the firewall's GUI or CLI, or centrally via Panorama.
- Resource Consumption on Firewall: The collection and processing of mappings consume CPU and memory resources on the firewall's management plane.
 User-ID.png)
High-level sequence of mapping collection and usage with Agentless (PAN-OS Integrated) User-ID.
This approach simplifies deployment, especially for smaller to medium-sized environments or when minimizing the number of managed servers is a priority.
Agentless Mapping Methods
The PAN-OS Integrated User-ID Agent (Agentless User-ID) supports several common methods for gathering IP-to-user mappings directly from the firewall:
-
Server Monitoring (Primary):
- The firewall directly connects to Domain Controllers (DCs) using a configured service account.
- It uses WMI (Windows Management Instrumentation) or WinRM (Windows Remote Management) to query Security Event Logs for user logon events.
- This requires the firewall's management interface (or an interface specified via a service route) to have network reachability and the necessary permissions to the DCs.
- The firewall can connect directly to Microsoft Exchange Servers to monitor logs for user activity, similar to how the dedicated agent does.
- The firewall itself can act as a syslog listener.
- Syslog Parse Profiles are configured on the firewall to extract IP and username information from incoming syslog messages from various sources (e.g., VPNs, wireless controllers, proxies).
- The firewall's XML API can directly receive IP-to-user mappings pushed by external systems (NAC, custom scripts, etc.). The firewall acts as the API endpoint.
- The firewall directly handles user authentication via web-based Captive Portal (Active or Passive) and creates mappings upon successful login.
- The firewall directly manages GlobalProtect Portal and Gateway authentications, creating mappings for successfully connected VPN users.
Important Limitations of Agentless User-ID:
Agentless User-ID does NOT natively support:- Client Probing (NetBIOS or WMI probes to client endpoints).
- Novell eDirectory Monitoring .
- Terminal Server (TS) Agent functionality for port-based mapping in RDS/Citrix environments. If you need these specific capabilities, you must use the Windows User-ID Agent.
Information Captured by Agentless User-ID
When using Agentless User-ID, the core information captured and stored directly by the firewall in its IP-to-user mapping table is essentially the same as with the dedicated agent for the *common supported sources*:
- IP Address: The IPv4 or IPv6 address of the user's device.
-
Username:
The identified user, typically in
DOMAIN\usernameoruser@domain.comformat. - Domain Name: The domain of the user (if applicable).
- Timestamp of Mapping Creation: When the firewall learned the mapping.
- Source of Mapping: How the mapping was learned (e.g., "SM" for Server Monitor direct from firewall, "GP" for GlobalProtect, "CP" for Captive Portal, "API", "SL" for Syslog).
Key points regarding information capture with Agentless User-ID:
- Shared Sources Consistency: For sources like Server Monitoring (DCs) or Exchange Monitoring, the *event log data itself* is the same. The difference is that the firewall's management plane is doing the querying and parsing directly. So, the fundamental user and IP information extracted will be consistent with what the agent would get from those same logs.
- No TS Agent Port Data: Since Agentless User-ID does not support the Terminal Server Agent component, it cannot capture the specific source port range information used to differentiate users on a shared terminal server IP. If you have such an environment and need granular user identification, the dedicated Windows User-ID Agent with the TS Agent component is required.
- No eDirectory Specifics: Similarly, no eDirectory-specific attributes are captured as this source is not supported by agentless.
- No Client Probing Data: No information is gathered via direct client probing.
As with the agent-based method, user group membership information is obtained separately via Group Mapping configured on the firewall, not as part of the direct IP-to-user mapping event.
Pros & Cons (Agentless User-ID)
Pros:
- Simplified Deployment: Significantly easier initial setup as there's no need to provision, install, or maintain separate agent software on a Windows server. Configuration is done directly on the firewall or Panorama.
- Reduced Infrastructure Footprint: Fewer components to manage, patch, and license (no extra Windows Server OS or User-ID Agent software). This can lower total cost of ownership (TCO).
- Direct Integration: User-ID configuration is tightly integrated into PAN-OS. Monitoring and troubleshooting (for the supported sources) can often be done directly from the firewall's CLI and GUI.
- Good for Smaller/Medium Environments: Often a suitable choice for organizations where the scale of Domain Controllers and user logon events is manageable for the firewall's resources, or where simplicity is a key driver.
Cons:
-
Management Plane Load:
The primary drawback. All mapping collection (polling DCs, parsing syslog, etc.) and processing consumes CPU and memory resources on the
firewall's management plane
.
- In very large environments with many DCs to monitor or high logon/logoff rates, this can potentially impact management plane responsiveness or even stability.
- The data plane (traffic processing) is generally unaffected, but a slow management plane can hinder configuration changes, logging, and reporting.
- This might require complex firewall rules or network designs, especially if DCs are in restricted segments.
- The service account credentials used by the firewall must have the necessary permissions on the DCs.
- Client Probing.
- Novell eDirectory monitoring.
- Terminal Server Agent functionality for port-based mapping in RDS/Citrix.
Deployment & Strategy
Comparison: User-ID Agent vs. Agentless User-ID
Choosing between the Windows User-ID Agent and Agentless User-ID depends on your environment's scale, complexity, existing infrastructure, and specific feature requirements.
| Feature / Aspect | Windows User-ID Agent | Agentless User-ID (PAN-OS Integrated) |
|---|---|---|
| Deployment Model | Software installed on a separate Windows Server. | Functionality runs directly on the Firewall/Panorama Management Plane. |
| Infrastructure Required | Dedicated Windows Server(s) (OS license, maintenance). | None beyond the firewall itself. |
| Management & Configuration | Managed via Agent software GUI & server OS; Firewall configured to connect to Agent. | Managed entirely within PAN-OS (Firewall/Panorama GUI/CLI). |
| Resource Impact | Uses dedicated server CPU/memory; minimal direct load on firewall for collection. | Consumes Firewall Management Plane CPU/Memory for collection. |
| Scalability (High Volume Environments) | Generally higher scalability for many DCs and high mapping rates. Can use multiple agents. | Scalability limited by firewall management plane capacity. Check PAN-OS release notes for recommended limits. |
| DC/Source Connectivity | Agent server needs network connectivity to DCs/sources. Firewall needs connectivity to Agent server. | Firewall's management interface (or service-routed interface) needs direct network connectivity to DCs/sources. |
| Primary AD Event Log Source | Server Monitoring (Agent connects to DCs via WMI/WinRM, or receives Syslog from DCs). | Server Monitoring (Firewall connects directly to DCs via WMI/WinRM). |
| Client Probing Support | Yes (WMI/NetBIOS to endpoints). | No . |
| eDirectory Monitoring Support | Yes . | No . |
| Terminal Server (RDS/Citrix) Agent Support | Yes (requires TS Agent component on terminal servers). Provides port-based mapping. | No native port-based mapping for TS. Users on TS will share the TS IP unless other methods like Captive Portal on TS are used. |
| Syslog Collection | Agent can act as syslog listener with advanced parsing. | Firewall can act as syslog listener. |
| XML API Recipient | Agent can receive API calls. | Firewall can receive API calls directly. |
| High Availability (HA) for Collection | Achieved by deploying multiple User-ID Agent servers. | Relies on firewall HA. Panorama can act as a central agentless collector for multiple firewalls. |
| Typical Use Case | Larger, complex deployments; specific source needs (eDirectory, TS Agent, Client Probing); desire to offload firewall management plane; centralized collection for many firewalls. | Smaller to medium deployments; simpler infrastructure desired; direct firewall-to-DC access is feasible; management plane load is acceptable. |
Scenario-Based Decision Making:
- Small office, single DC, few users, simple needs: Agentless User-ID is likely sufficient and simpler.
- Large enterprise, dozens of DCs, thousands of users, Citrix farm: Windows User-ID Agent (likely multiple instances for HA) with TS Agent component is a better fit for scalability and specific feature needs.
- Environment with Novell eDirectory: Windows User-ID Agent is required.
- Heavily utilized firewall management plane: Consider Windows User-ID Agent to offload User-ID processing.
Common Prerequisites & Configuration for User-ID
Regardless of whether you choose the User-ID Agent or Agentless User-ID, several common configuration elements and prerequisites must be in place:
1. Service Account
An Active Directory service account is crucial for Server Monitoring (the primary method for domain users). This account needs specific, minimum-required permissions.
Typical permissions include:
-
Membership in
Domain Users. -
Membership in the local
Event Log Readersgroup on each Domain Controller being monitored. -
Membership in the local
Distributed COM Usersgroup on each Domain Controller (often needed for WMI). -
Permissions for WMI or WinRM:
-
For WMI:
- Enable Remote Administration in Windows Firewall on DCs.
-
Grant "Enable Account" and "Remote Enable" permissions for the service account on the
Root\CIMV2WMI namespace on DCs. This can be done viawmimgmt.msc-> WMI Control (Local) -> Properties -> Security tab.
-
For WinRM:
-
Ensure WinRM service is running and configured on DCs (
winrm quickconfigcan help). - The service account needs read access to the security event log via WinRM. This is often covered by Event Log Readers, but specific Security Descriptors (SDDL) for the WinRM listener or event log might need adjustment in complex setups.
- Windows Firewall rules for WinRM (TCP 5985 for HTTP, 5986 for HTTPS).
-
Ensure WinRM service is running and configured on DCs (
-
For WMI:
2. Server Monitoring Configuration
-
With User-ID Agent:
- Install the User-ID Agent software on a Windows server.
- Configure the Agent to monitor specific Domain Controllers (or auto-discover them).
- Specify the service account credentials within the Agent configuration.
- Define which event logs/types to monitor.
-
On the firewall (or Panorama), navigate to
Device > User Identification > User Mapping > Server Monitoring. - Add Server Monitor entries for each Domain Controller.
- Specify the FQDN or IP address of the DC.
- Select the connection method (WMI or WinRM).
- Provide the service account credentials.
3. Network Connectivity & Firewall Rules
Ensure necessary network paths and firewall rules allow communication:
| Source | Destination | Protocol/Port(s) | Purpose | Notes |
|---|---|---|---|---|
| User-ID Agent Server | Domain Controllers | TCP 135 (RPC Endpoint Mapper), TCP Dynamic High Ports (WMI), TCP 5985 (WinRM HTTP), TCP 5986 (WinRM HTTPS), UDP 389 (LDAP for DC discovery), TCP 389 (LDAP) | Server Monitoring, DC Discovery | WMI uses dynamic ports after initial connection on 135. WinRM is preferred for predictability. |
| User-ID Agent Server | Firewall/Panorama | TCP 5007 (Default User-ID Agent to Firewall) | Agent sends mappings to Firewall | Can be changed; SSL can be enabled. |
| Firewall (Agentless) Mgmt/Service Route Interface | Domain Controllers | TCP 135 (RPC), TCP Dynamic High Ports (WMI), TCP 5985 (WinRM HTTP), TCP 5986 (WinRM HTTPS) | Agentless Server Monitoring | |
| Firewall | LDAP Server (e.g., DC) | TCP 389 (LDAP), TCP 636 (LDAPS) | Group Mapping | |
| External Syslog Sources | User-ID Agent / Firewall | UDP 514 (Default Syslog) or custom | Syslog-based mapping | |
| External API Clients (NAC, etc.) | User-ID Agent / Firewall | TCP/UDP (depends on API, often HTTPS/443 for Firewall XML API) | XML API based mapping | Firewall API uses HTTPS. |
4. User-ID Agent Configuration (Firewall Side - for Agent method only)
-
Navigate to
Device > User Identification > User-ID Agents. - Add an entry for each Windows User-ID Agent server.
- Specify the Agent's IP address and the port (default 5007).
- Configure SSL if the Agent is set up for secure communication.
5. Group Mapping
-
Navigate to
Device > User Identification > Group Mapping Settings. - Configure connections to your directory servers (e.g., Active Directory via LDAP or LDAPS).
- This allows the firewall to retrieve group membership information for users identified by User-ID, enabling group-based policies.
- Specify search filters and attributes to fetch groups.
User-ID provides the user, Group Mapping provides the groups, and Policy Engine uses both.
6. User-ID Enabled Zones
-
Navigate to
Network > Zones. - For each zone where user traffic originates (typically internal/trusted zones like "LAN", "Users", "WiFi"), edit the zone and check the "Enable User Identification" box.
- This tells the firewall to consider User-ID mappings for traffic traversing these zones.
7. Mapping Timeouts and Caching
-
Navigate to
Device > User Identification > User Mapping. - Under "Palo Alto Networks User-ID Agent Setup" (even for Agentless, these settings apply), click the gear icon for "User Identification Timeout Settings".
- Timeout (minutes): How long an IP-to-user mapping remains valid if not refreshed. Default is often 45-60 minutes. Adjust based on DHCP lease times and user session behavior. Too short can cause unnecessary re-mapping; too long can lead to stale mappings.
- Unknown User Timeout (minutes): How long the firewall remembers an IP address for which it couldn't find a user mapping.
Best Practices for User-ID Deployment
- Use Dedicated Service Accounts: Always create a specific service account for User-ID with the absolute minimum required privileges. Avoid using domain administrator accounts or highly privileged accounts. Regularly review these permissions.
- Prefer Server Monitoring: Relying on DC Security Event Logs (via WMI/WinRM or Syslog forwarding from DCs) is generally the most reliable, scalable, and least intrusive method for domain-joined clients.
- Avoid Client Probing if Possible: Client probing can be resource-intensive for both the agent and client machines, and less reliable. Use it only as a last resort or for very specific scenarios where other methods fail.
-
Monitor Multiple DCs/Sources:
- Configure Server Monitoring for multiple (ideally all) Domain Controllers in each relevant domain for redundancy and comprehensive coverage.
- Utilize other sources like GlobalProtect, Captive Portal, Syslog, and XML API to capture mappings for non-domain clients, BYOD, and specific application authentications.
- Agentless User-ID: Suitable for smaller to medium environments where the firewall's management plane load is not a concern and direct DC access is feasible. Simpler to deploy and manage.
- Windows User-ID Agent: Preferred for very large, complex environments, when specific Agent-only features (eDirectory, TS Agent, Client Probing) are needed, or when it's critical to offload processing from the firewall management plane.
- If using the Windows User-ID Agent, enable SSL/TLS to encrypt communication between the Agent and Firewalls/Panorama.
- Implement strict firewall rules to control access to Domain Controllers for WMI/WinRM, allowing only the User-ID Agent server IPs or firewall management IP.
- Use LDAPS (LDAP over SSL/TLS) for Group Mapping.
-
On the firewall CLI:
-
show user ip-user-mapping all(to view current mappings) -
show user server-monitor state all(for Agentless DC connectivity status) -
show user user-id-agent state all(for Agent connectivity status) -
show user user-id-agent statistics -
debug user-id dump statisticsand otherdebug user-id dump ...commands for deeper dives.
-
Troubleshooting User-ID & Common Gotchas
User-ID issues are common, often stemming from misconfigurations in permissions, network connectivity, or source systems. Here are key areas to check and common pitfalls:
Common Gotchas:
-
Service Account Permissions:
This is the #1 cause of Server Monitoring failures.
- Not in 'Event Log Readers' on DCs.
- Insufficient WMI permissions (DCOM, WMI namespace `root\cimv2`).
- WinRM not configured or service account lacks remote access rights for WinRM.
- Password expired or account locked out.
-
Firewall Rules Blocking Communication:
- Agent server <-> DCs (WMI/WinRM ports, LDAP).
- Agent server -> Firewalls (TCP 5007 default).
- Firewall (Agentless) -> DCs (WMI/WinRM ports).
-
WMI/WinRM Service Issues on DCs:
- Windows Management Instrumentation service not running or corrupted.
- WinRM service not running, not configured for remote access, or listeners not set up.
-
Incorrect Server Monitoring Configuration:
- Wrong DC IP/FQDN.
- Wrong service account credentials.
- Incorrect protocol selected (WMI vs. WinRM).
- Security Event Log Overwriting: If DC Security Event Logs are too small or roll over too quickly, the Agent/Firewall might miss logon events before they can be polled. Ensure adequate log size and retention.
- Non-Domain / Shared IP Clients: Server Monitoring only works well for domain logons. Users on non-domain machines, BYOD, or behind NAT devices require alternative methods (GlobalProtect, Captive Portal, XML API, TS Agent) for accurate mapping.
- Stale Mappings / Incorrect Timeouts: Default timeouts might not suit your environment. If a user logs off and another user takes the same IP before the mapping times out, policies might be incorrectly applied. Align timeouts with DHCP lease times and user behavior.
- Agentless Performance on Management Plane: In very large environments, direct polling of many DCs by the firewall (Agentless) can strain the management plane CPU, leading to slow GUI/CLI or commit issues.
- Group Mapping Not Configured or Failing: If Group Mapping isn't set up or the LDAP server is unreachable, you can't use AD groups in policies, even if IP-to-user mapping works.
- User-ID Not Enabled on Zone: If "Enable User Identification" is not checked for the source zone of the traffic, mappings won't be applied for that traffic.
- Clock Skew: Significant time differences between DCs, Agent server, and Firewall can sometimes interfere with Kerberos-based event detection or log correlation. Ensure NTP is used consistently.
- User-ID Agent Software Version: Outdated agent software might have bugs or compatibility issues with newer PAN-OS versions or Windows Server OS.
Troubleshooting Steps & Commands:
-
Verify Basic Connectivity:
- Ping from Agent/Firewall to DCs.
- Telnet/Test TCP ports (e.g., to DC on 135 for WMI, 5985 for WinRM; from DC to Agent/Firewall on 5007).
-
Check Service Account:
- Try logging into a DC with the service account credentials.
- Use tools like `wbemtest` (from Agent server to DC) to test WMI connectivity and permissions.
- Use PowerShell `Test-WSMan` (from Agent/Firewall CLI if possible, or test server) to check WinRM.
-
Firewall CLI Commands (Essential):
-
show user ip-user-mapping all: Displays the current IP-to-user mapping table. Check if expected mappings exist. -
show user server-monitor state all: Shows status of Agentless connections to DCs. Look for "connected" state. -
show user user-id-agent state all: Shows status of firewall's connection to Windows User-ID Agents. -
show user group list/show user group name <group_name>: Verify group mapping. -
show counter global filter delta yes aspect useridd: Check User-ID related counters for errors or activity. -
debug user-id dump statistics: View detailed statistics about mapping sources and processing. -
debug user-id dump server-monitor: Detailed server monitor debug. -
debug user-id dump agent- conexión <agent_name>: Detailed agent connection debug. -
less mp-log useridd.log: View the User-ID daemon log on the management plane. -
less dp-log useridd.log: (If applicable, less common for initial mapping issues).
-
- Windows User-ID Agent Logs: If using the agent, check its logs (usually in the installation directory) for errors related to DC connections, event parsing, or firewall communication. The Agent GUI also provides status.
- DC Security Event Logs: Manually inspect Security Event Logs on DCs for relevant logon events (e.g., 4624) to confirm they are being generated for the users in question.
- Packet Captures: If network connectivity is suspected, run packet captures on the firewall, Agent server, or DCs to see if WMI/WinRM/Syslog/Agent traffic is flowing correctly and if there are any resets or errors.
PCNSE Exam Focus for User-ID
Understanding User-ID is critical for the PCNSE exam. Expect questions covering these areas:
- Fundamental Purpose: Know that User-ID maps IP addresses to usernames to enable user-based visibility and policy enforcement.
- Agent vs. Agentless Distinction: Clearly differentiate between the Windows User-ID Agent (separate server, broader capabilities like client probing/eDir/TS Agent) and Agentless User-ID (PAN-OS Integrated Agent on firewall, simpler deployment, potential MP load).
- Primary Mapping Method for Domain Users: Recognize Server Monitoring (reading DC Security Event Logs) as the primary and most common method.
- Technologies for Server Monitoring: Know that WMI and WinRM are used by the Agent/Firewall to query DCs. Syslog from DCs is also an option.
- Other Common Mapping Sources: Be familiar with GlobalProtect, Captive Portal, XML API, Syslog (generic), and Exchange Monitoring as supplementary or alternative sources.
- Service Account Role: Understand the absolute necessity of a Service Account with appropriate permissions (Event Log Readers, WMI/WinRM access) for Server Monitoring.
-
Pros, Cons, and Scalability:
- Agent: More scalable for very large environments, offloads firewall MP, supports more sources. Con: requires dedicated server.
- Agentless: Simpler, no extra server. Con: loads firewall MP, fewer sources supported.
- Where User-ID is Used: Know that User-ID mappings are leveraged in Security Policy (Source User field) , QoS Policy, Decryption Policy, Authentication Policy, as well as for enhanced logging and ACC reporting.
-
Configuration Locations:
-
Server Monitoring (Agentless):
Device > User Identification > User Mapping > Server Monitoring. -
Agent Configuration (Firewall side):
Device > User Identification > User-ID Agents. - User-ID Agent software (Windows Agent): Configuration is within the installed agent application.
-
Server Monitoring (Agentless):
Device > User Identification > Group Mapping Settings
) are configured separately to connect to AD/LDAP and retrieve group memberships. User-ID provides the *user*, Group Mapping provides their *groups*.
Network > Zones
) where user traffic originates.
show user ip-user-mapping all
and
show user server-monitor state all
.
User-ID: Agent vs. Agentless Quiz
Test your understanding of User-ID concepts with this 20-question quiz.