PAN-OS: User-ID Data Redistribution
What is User-ID Data Redistribution?
User-ID Data Redistribution refers to the mechanisms within PAN-OS for sharing IP address-to-username mappings learned by one component (like a User-ID Agent or Panorama) with other PAN-OS devices (firewalls or other agents). The goal is to ensure that multiple enforcement points have consistent and up-to-date User-ID information without requiring each device to independently query all the original mapping sources.
This is essential in environments with multiple firewalls, geographically distributed locations, or centralized management scenarios, where user identity is critical for enforcing user-based security policies .
Why Use User-ID Redistribution?
- Scalability: Prevents numerous firewalls from individually querying Domain Controllers or other sources, reducing load on those systems.
- Consistency: Ensures all participating firewalls have the same view of IP-to-user mappings, leading to consistent policy enforcement regardless of which firewall a user's traffic traverses.
- Centralized Management: Allows Panorama to act as a central broker, collecting mappings from various agents/sources and distributing a consolidated view to managed firewalls.
- Network Segmentation: Enables firewalls in isolated network segments (that cannot reach identity sources directly) to receive mappings from an Agent, Panorama, or Cloud Identity Engine that *can* reach the sources.
- HA and DR: Facilitates mapping availability in High Availability clusters (often automatic) and Disaster Recovery scenarios.
- Efficiency: Reduces the need to configure complex Server Monitoring or source connections on every single firewall, simplifying deployment and ongoing management.
Basic User-ID Flow (Without Redistribution)
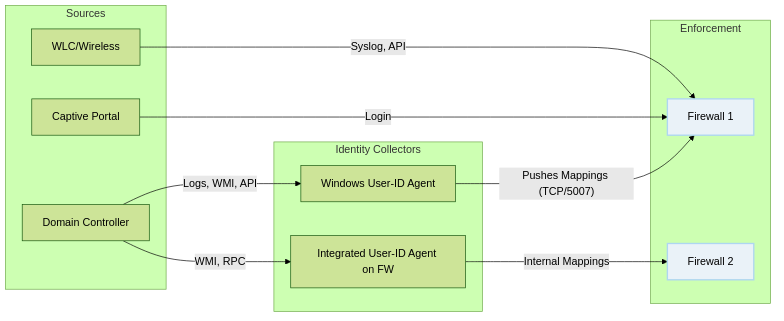
Each firewall independently collects mappings.
Redistribution Mechanism: Panorama Distribution
How Panorama Acts as a Redistributor
Using Panorama as the central User-ID redistributor is the most common and recommended best practice for environments managed by Panorama. It provides a single point for collecting, consolidating, and distributing user-mapping information.
In this model, Panorama is configured to gather IP-to-user mappings from various sources such as:
- Windows User-ID Agents
- PAN-OS Integrated User-ID Agents (configured to forward to Panorama)
- Server Monitoring (if Panorama has direct network access to DCs)
- XML API (from third-party systems)
- Cloud Identity Engine (CIE)
Panorama consolidates all this information into its central mapping table. Managed firewalls are then configured to receive their User-ID mappings directly from Panorama , rather than connecting to the original sources (like agents or DCs) themselves.
In-depth Explanation: Panorama Workflow
- Mapping Collection: Panorama's Collector Groups (or Panorama acting as an agent) connect to configured identity sources (Agents, DCs via Server Monitoring, CIE, etc.) and pull/receive mapping updates (IP-User, IP-User-Group).
- Consolidation: Panorama maintains a comprehensive and up-to-date mapping table based on data received from all its configured sources. It handles potential conflicts or overlapping data.
- Redistribution: Via the Panorama management connection, the consolidated mapping table is pushed down to the managed firewalls. The firewalls are configured to accept these mappings from Panorama.
- Policy Enforcement: Managed firewalls use the mapping table received from Panorama to identify users by their IP addresses and apply user-based security policies.
Configuration Steps (Conceptual)
While exact steps vary slightly by version, the general flow is:
-
On Panorama:
- Configure Collector Groups under Panorama > Collector Groups .
- Add Agents ( Agent tab) or Server Monitoring ( Server Monitoring tab) to the Collector Group.
- Configure Group Mapping on Panorama if needed ( Panorama > User Identification > Group Mapping Settings ).
- Ensure redistribution is enabled (often under Panorama > User Identification > Setup or within Collector Group settings).
-
On Managed Firewalls:
- Configure User-ID setup under Device > User Identification > Setup .
- Crucially, configure the firewall to Retrieve User Mapping from Panorama . This is typically a checkbox or option.
- Remove/Disable any direct connections configured under Device > User Identification > User-ID Agents if those agents are already being monitored by Panorama.
- Commit changes on Panorama and Push configuration to the managed firewalls.
Panorama Redistribution Flow
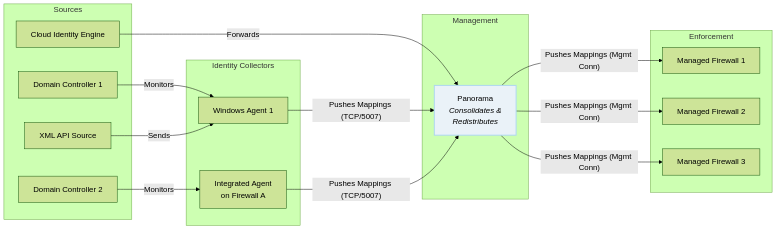
Panorama collects from multiple sources and pushes consolidated mappings to managed firewalls.
Redistribution Mechanism: User-ID Agent Push
How Agents Push Mappings Directly
In environments where Panorama is not used, or for specific network segments, a Windows User-ID Agent or a firewall running the PAN-OS Integrated User-ID Agent can be configured to directly push mappings to one or more specified firewalls . This allows a single agent collecting data to feed multiple enforcement points.
This differs from the Panorama model where the firewall primarily receives mappings from Panorama. Here, the firewalls are configured to explicitly trust and receive mappings from the Agent's IP address.
Configuration Steps (Conceptual)
-
On the User-ID Agent (Windows software or Integrated Agent configuration on a firewall):
- Configure the agent to collect mappings from identity sources (DCs, etc.).
- Define the list of destination firewalls (by management IP address) that this agent should send mappings to. This is typically done within the Agent's configuration interface.
-
On the receiving Firewalls:
- Configure User-ID setup under Device > User Identification > Setup .
-
Under
Device > User Identification > User-ID Agents
, add the IP address(es) of the User-ID Agent(s) that will be pushing mappings to this firewall.
Firewalls listen on TCP/5007 by default to receive pushes from Agents. Ensure a security rule or service route allows this traffic to the firewall's management interface or a dedicated data interface configured for User-ID.
- Commit changes on the firewall(s).
Agent Push Redistribution Flow
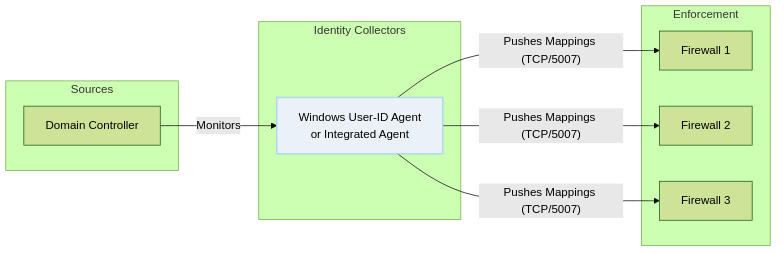
A single User-ID Agent pushes mappings directly to multiple firewalls.
Redistribution Mechanism: High Availability (HA) Synchronization
Automatic Sync in HA Pairs
Within a High Availability (HA) pair of Palo Alto Networks firewalls (Active/Passive or Active/Active), User-ID mappings, along with session state, configuration, and other runtime information, are automatically synchronized between the peers over the dedicated HA links.
This synchronization ensures that if a failover occurs, the new active firewall already has the vast majority of the necessary user-mapping information to continue enforcing policies for existing and new sessions without significant interruption or the need to re-collect all mappings.
How it Works (Conceptual)
- Mappings learned by the active device (either directly or via Panorama/Agent redistribution) are replicated to the passive device in near real-time over the HA data link (HSCI - High Speed Cluster Interface).
- Configuration settings related to User-ID sources are synchronized over the HA control link (HSCI or dedicated HA1 ports).
- No specific "redistribution" configuration is needed between the HA peers themselves; it's an inherent function of the HA synchronization process.
HA Synchronization Flow (User-ID Mappings)

User-ID mappings are automatically synced between HA peers.
Redistribution Mechanism: Cloud Identity Engine (CIE)
Role of CIE in User-ID Redistribution
The Palo Alto Networks Cloud Identity Engine (CIE) is a modern, cloud-based service designed to centralize identity information from various sources, especially SaaS applications and cloud directories like Azure AD and Okta. CIE significantly enhances User-ID capabilities, particularly in cloud-centric and hybrid environments.
CIE can act as a primary source for user and group information, including IP-to-user mappings. It integrates with your identity providers and provides a consolidated view that PAN-OS devices (Panorama and firewalls) can consume.
How CIE Integrates with User-ID
There are typically two main ways PAN-OS devices leverage CIE for User-ID:
- CIE as a Source for Panorama: Panorama can be configured to connect to CIE to retrieve user and group information. Panorama then includes this information in the consolidated mapping table it redistributes to its managed firewalls. This is the most common approach in Panorama-managed environments.
- CIE as a Direct Source for Firewalls: Firewalls (especially those not managed by Panorama or in specific deployments) can potentially connect directly to CIE to obtain identity information.
CIE provides APIs that firewalls and Panorama use to query or subscribe to identity updates.
Benefits of Using CIE for Redistribution
- Modern Identity Sources: Easily integrates with cloud-based identity providers that traditional Windows Agents might not support natively.
- Centralization: Provides a single point for collecting identity data from diverse sources (Active Directory, Azure AD, Okta, Google Workspace, etc.).
- Simplified Management: Reduces the need for multiple on-premises agents or complex configurations for different identity sources.
- Rich User Attributes: Can provide richer context beyond just IP-to-user mappings, including device posture, location, and group memberships directly from the identity provider.
CIE Integration Flow
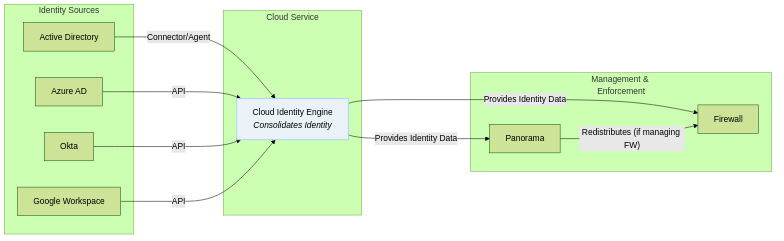
CIE integrates various sources and provides identity data to Panorama/Firewalls.
Configuration & Practice: Panorama Configuration Recap
Recap: Configuring Panorama as the Central Source
As highlighted earlier, configuring Panorama to collect and redistribute User-ID mappings is the recommended approach for managed devices.
Key configuration areas on Panorama include:
-
Collector Groups:
Containers for logically grouping User-ID sources (Agents, Server Monitors) and configuring settings like logging, exception lists, etc.
Located under Panorama > Collector Groups .
-
Agents:
Defining connections to Windows User-ID Agents or firewalls acting as Integrated User-ID Agents.
Configured within a Collector Group under the Agent tab.
-
Server Monitoring:
Configuring Panorama itself to monitor Domain Controllers or Exchange servers directly. Requires Panorama's management interface to reach these servers.
Configured within a Collector Group under the Server Monitoring tab.
-
Cloud Identity Engine (CIE):
Configuring Panorama to connect to your CIE instance for identity data.
Configured under Panorama > Cloud Services > Cloud Identity Engine .
-
Group Mapping Settings:
Configuring Panorama to query directory services (LDAP) to resolve user-to-group memberships. This is essential for user group-based policies.
Located under Panorama > User Identification > Group Mapping Settings .
-
User-ID Setup:
Enabling and configuring general User-ID settings and options, including potentially enabling redistribution settings (though specific redistribution push settings for managed devices are often implicit when configured under Templates/Template Stacks).
Located under Panorama > User Identification > Setup .
Once configured on Panorama, these settings, including the collected mapping tables, are pushed down to the managed firewalls via Device Group and Template/Template Stack configurations. The firewalls receive the complete mapping table from Panorama and use it locally.
Configuration & Practice: General Best Practices
Implementing User-ID data redistribution effectively requires following several best practices:
- Centralize with Panorama: For large-scale deployments managed by Panorama, use Panorama as the single point for User-ID collection and redistribution. This simplifies firewall configuration and ensures consistency.
- Consolidate Sources: Minimize the number of direct connections from individual firewalls or agents to identity sources like Domain Controllers. Have Panorama or a limited set of redundant Agents/CIE connectors collect data and distribute it.
-
Avoid Conflicting Sources:
Never
configure a firewall to receive mappings directly from an Agent or monitor DCs *and* also receive mappings from Panorama if Panorama is collecting from those same sources. This can lead to mapping conflicts, flapping entries, and unpredictable policy enforcement. Choose one primary source for the firewall (either direct Agent/Agentless or Panorama).
This is a common misconfiguration and a frequent source of issues.
- Secure Communication: Whenever possible, configure User-ID agents and firewalls to use SSL/TLS for communication (default is often unencrypted). This protects sensitive identity data during transit. Check the Agent and firewall configuration settings for SSL options.
-
Ensure Network Connectivity:
Verify that the necessary ports are open between User-ID components:
- Agent/Integrated Agent to Firewall/Panorama: TCP/5007 (default, potentially SSL on a different port)
- Firewall/Panorama to Domain Controllers (for Agentless or Group Mapping): TCP/135 (RPC), TCP/445 (SMB), UDP/137 (NetBIOS), UDP/389 (LDAP), TCP/389 (LDAP), TCP/636 (LDAPS), Global Catalog ports (3268, 3269) . Ensure relevant firewall rules or service routes are configured.
- Panorama/Firewall to CIE: Typically HTTPS (TCP/443) or other defined API ports.
- Monitor Status and Logs: Regularly check the User-ID status on firewalls ( show user user-id-agent state , show user ip-user-mapping all ) and Panorama logs ( show user log read ) to ensure mappings are being received and are current.
- Utilize Group Mapping: Configure Group Mapping on Panorama or the collecting firewall/agent to resolve user memberships. This allows you to use user groups in security policies, simplifying rules and adapting automatically as users are added/removed from groups in AD/LDAP/CIE.
- Redundant Sources: Configure multiple Windows Agents or Integrated Agents, and/or connect to multiple DCs for Server Monitoring, to ensure User-ID data is available even if one source fails. Panorama's Collector Groups help manage this redundancy centrally.
Configuration & Practice: Caveats and Gotchas
While powerful, User-ID redistribution has potential pitfalls:
- Network Latency/Disruption: Delays or outages between identity sources, collectors (Agents/Panorama), and the final firewall can cause stale or missing mappings, leading to policy bypasses or incorrect enforcement.
- Configuration Conflicts: As mentioned in best practices, configuring redundant or conflicting mapping sources on a firewall is a major issue. Example: Firewall configured for Agentless *and* connected to a Windows Agent *and* managed by Panorama getting mappings from that same agent.
- DNS Resolution: Proper DNS resolution is crucial for User-ID to resolve server names and user principals. Ensure firewalls and agents can correctly resolve names.
- Service Routes: If User-ID traffic (TCP/5007, LDAP, WMI, etc.) needs to use a specific data interface instead of the management interface, ensure Service Routes are correctly configured on the firewall/Panorama.
- Resource Limitations: Panorama or a firewall acting as a central collector/redistributor needs sufficient CPU and memory resources, especially in large environments with high mapping churn.
- Overlapping IP Ranges: If different User-ID sources provide mappings for the same IP addresses based on different criteria (e.g., VPN vs. wired), it can cause mapping instability. Careful design is needed.
- Authentication vs. Mapping: User-ID maps IP to User after authentication occurs elsewhere (AD, Okta, etc.). It is not an authentication service itself (though it can trigger Captive Portal). Misunderstanding this can lead to incorrect expectations.
Configuration & Practice: Troubleshooting User-ID
Troubleshooting User-ID issues, especially involving redistribution, requires a systematic approach:
-
Verify Connectivity:
Use ping, traceroute, and telnet/test-port to ensure network paths are open between:
- Identity Source (DC, WLC, etc.) <--> Collector (Agent, Integrated Agent, Panorama, CIE Connector)
- Collector (Agent, Panorama, CIE) <--> Firewall(s) (specifically on TCP/5007 for pushes, or relevant API ports for CIE)
- Firewall <--> DNS Servers
- Firewall/Panorama <--> LDAP Servers (for Group Mapping)
Check Service Routes if non-management interfaces are used for User-ID traffic. -
Check Service/Agent Status:
- Windows Agent: Check the Windows service status and the agent's logs.
- Integrated Agent: Check the User-ID process status on the firewall CLI ( show system process list | match useridd ).
- Panorama: Check Collector Group and Agent status on the Panorama GUI and CLI.
- Firewall: Check User-ID status ( show user user-id-agent state , show user user-id-service status ).
- CIE: Check connection status on Panorama/Firewall and the CIE cloud portal health.
-
Inspect Logs:
- Firewall: User-ID logs ( show user log read ), System logs.
- Panorama: User-ID logs, System logs.
- Windows Agent: Application event logs on the Windows server.
- DCs: Security event logs (4624/4625 for logon/logoff).
-
Verify Mappings:
- Firewall CLI: show user ip-user-mapping all , show user ip-user-mapping state all . Filter by IP or user.
- Panorama CLI: show user panorama ip-user-mapping all (if Panorama is the source).
- Windows Agent GUI: Check the live user list.
Look for missing mappings, stale entries, or flapping mappings for a specific IP. - Check Configuration: Double-check firewall and Panorama User-ID configuration, especially the source of mappings (direct agent vs. Panorama), agent IP addresses, and port settings. Ensure no conflicting mapping sources are configured on the firewall.
- Policy Check: Ensure the security policies are configured to use User/Group objects and that the User-ID feature is enabled in the relevant security zones.
User-Based Automation: Automated Quarantine
How User-ID Enables Automated Quarantine
User-ID mappings are fundamental to implementing automated quarantine policies based on user behavior. Since policies can identify traffic by the user accessing a resource, this allows the firewall to log security events (threats, URL filtering blocks, WildFire verdicts) against that specific user identity.
Automated quarantine leverages these user-associated security logs as triggers to automatically restrict or block traffic for the user responsible for the suspicious activity, regardless of their IP address changing (within the mapping's validity).
Mechanism for Automated Quarantine
Common approaches involve using User-ID in conjunction with Dynamic Address Groups (DAGs) and automation:
- Security Policy & Logging: Configure security policies that use User-ID and apply security profiles (Antivirus, Anti-Spyware, Vulnerability Protection, URL Filtering, WildFire). Ensure logging is enabled for relevant threat/traffic events. Logs will contain the User and Source IP information thanks to User-ID.
- Log Forwarding / SNMP Traps: Forward relevant logs (e.g., Critical Severity Threats, High Severity URL blocks, WildFire Malware verdicts) from the firewall (or Panorama) to an external system or generate SNMP traps.
- Automation Engine: An external system (e.g., scripts, SOAR platform, logging server with alerting) or built-in firewall automation responds to these specific log events.
- Identify User and IP: The automation extracts the User and the associated IP address from the log event.
-
Update Dynamic Address Group:
The automation engine uses the firewall's/Panorama's XML API to add the user's current IP address to a predefined Dynamic Address Group (DAG).
The DAG is defined on the firewall/Panorama using a matching criterion like type dynamic match "suspect_user_tag" .
- Apply Quarantine Policy: A dedicated security policy is configured higher in the rulebase, matching the User (or Any) and the Quarantine DAG (Destination/Source). This policy is configured to block all traffic, limit bandwidth, or redirect traffic for IPs contained within the DAG.
- Expiration: Configure the DAG entries or the automation logic to automatically remove the IP from the DAG after a set time.
User-ID is the critical component that links the suspicious IP seen in the log to the specific user, allowing the automation to update the DAG effectively and quarantine the user regardless of them potentially getting a new IP address later (as long as User-ID learns the new mapping).
Automated Quarantine Flow
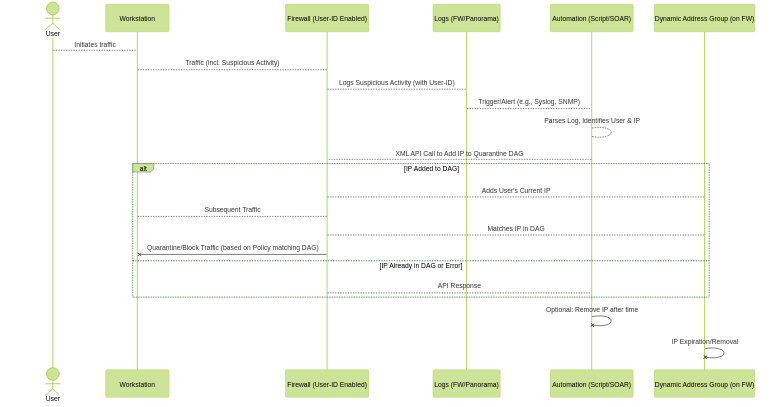
Automated Quarantine workflow leveraging User-ID and DAGs.
Exam & Quiz: PCNSE Exam Focus
For the PCNSE exam (and practical administration), a strong understanding of User-ID redistribution is essential. Key areas to focus on include:
- Purpose: Why is redistribution needed in multi-firewall environments? (Scalability, Consistency, Centralization, Segmentation).
- Main Mechanisms: Know the primary methods - Panorama Distribution (recommended for managed devices) and direct Agent Push (Windows or Integrated). Understand the fundamental difference in configuration (firewall gets from Pano vs. firewall gets from Agent).
- HA Sync: Recognize that synchronization between HA peers is automatic and inherent, not configured via redistribution methods.
- Cloud Identity Engine (CIE): Understand its role as a modern, centralized identity source and how Panorama/Firewalls integrate with it.
- Key Ports: Know the default ports used for Agent-to-Firewall/Panorama communication ( TCP/5007 ) and common ports for identity source monitoring (LDAP, LDAPS, WMI, RPC, SMB).
- Best Practices: Especially centralizing with Panorama and avoiding conflicting sources .
- Configuration Location: Be able to identify where on Panorama ( Collector Groups , Group Mapping , Cloud Services ) and the firewall ( User-ID Agents , Server Monitoring , Setup ) you configure User-ID and its sources/redistribution.
- Troubleshooting: Know the basic CLI commands to check User-ID status, mappings, and logs on both firewalls and Panorama ( show user ... commands). Understand the troubleshooting flow (connectivity, service status, logs, mappings, config).
- User-Based Policy: Understand that the core purpose of User-ID (and redistribution) is to enable user-based security policies.
- Automated Actions: Understand how User-ID facilitates automated actions like quarantine by correlating logs with users and using dynamic address groups.
Exam & Quiz: User-ID Redistribution Quiz
Test your knowledge on User-ID data redistribution and related concepts.