Introduction: Beyond Static Groups
Traditional User-ID implementation relies heavily on mapping users to static groups retrieved from directory services like Active Directory or LDAP. While essential for role-based access control, static groups represent relatively fixed organizational structures.
Dynamic User Groups (DUGs) offer a powerful enhancement by allowing group membership to be determined automatically and dynamically based on criteria associated with a user's session or device state at a given time. This mechanism relies on tags being associated with User-ID mappings.
Instead of defining policy solely based on "who" a user is (their static group), DUGs enable policies based on "what" a user's context is right now (e.g., device compliance, location, threat exposure).
Core Mechanism: Tags and Sources
The foundation of Dynamic User Groups lies in tags .
- Tags: Metadata labels (simple strings) that can be associated with an IP-to-User mapping on the firewall.
-
Tag Sources:
Tags can be assigned to mappings via several methods:
-
GlobalProtect HIP Checks:
The firewall can automatically tag user sessions based on whether their device matches (or doesn't match) specific Host Information Profiles (HIP) (e.g., tag
Compliant-DeviceorNon-Compliant-AV). This is a very common and powerful source for endpoint posture-based policies. -
User-ID XML API / REST API:
External systems (like Network Access Control (NAC), Security Orchestration, Automation, and Response (SOAR), Threat Intelligence Platforms (TIPs), or custom scripts) can push tags along with IP/User mappings programmatically via the API. This enables integrating real-time threat or status information (e.g., tag
Quarantined-Device,High-Risk-User,Guest-Wifi). - VM Information Sources (Panorama): In virtualized environments, tags can be derived from VM attributes provided by sources like VMware vCenter.
- (Future integrations may add more sources).
-
GlobalProtect HIP Checks:
The firewall can automatically tag user sessions based on whether their device matches (or doesn't match) specific Host Information Profiles (HIP) (e.g., tag
-
DUG Definition:
A Dynamic User Group (configured under
Objects > Dynamic User Groups) is defined by one or more specified tags that a user's mapping must possess to be a member. You can use AND/OR logic when defining multiple tag criteria. - Policy Usage: The DUG name is then used just like a static group name in the 'Source User' field of Security, QoS, Decryption, or Authentication policies.
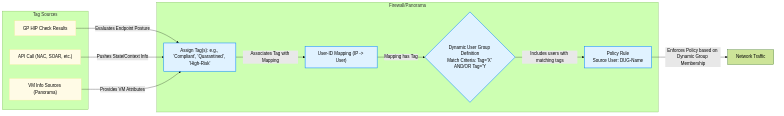
Simplified DUG Tagging and Policy Flow.
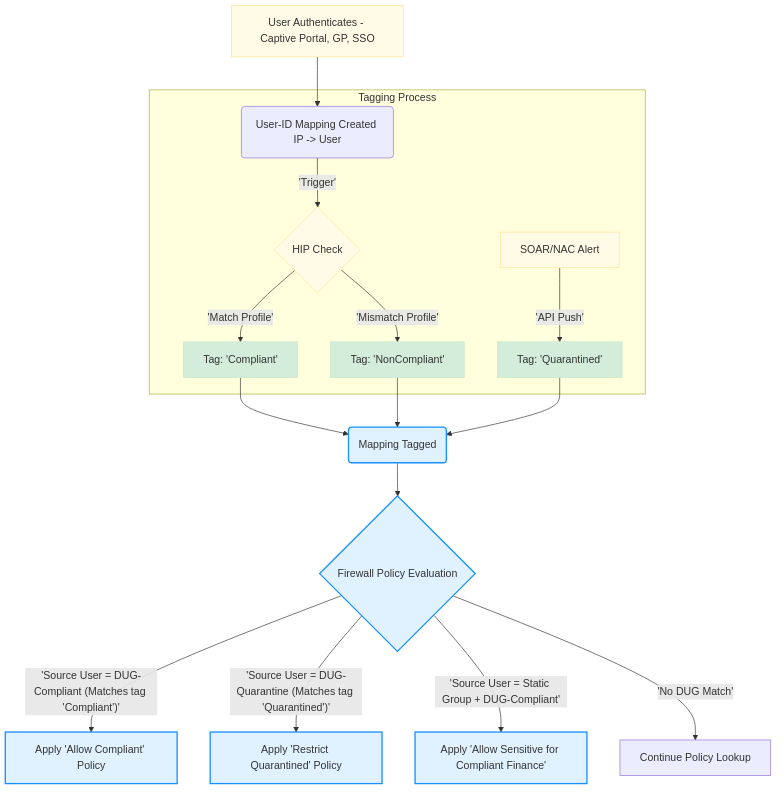
Detailed flow illustrating how different tag sources influence DUG membership and policy evaluation.
Key Benefits of Using DUGs in Policy
DUGs provide significant advantages over relying solely on static group mapping:
- Context-Aware Security Policies: Policies adapt based on real-time context (device health, threat exposure, location) rather than just static identity. This is fundamental to Zero Trust Network Architecture (ZTNA). You can enforce policies like "Allow access to the critical server only if the user is in the 'Admins' static group AND their device is tagged as 'Compliant-Endpoint'".
- Automation and Dynamic Response: Automatically adjust user permissions or apply different security controls based on changing conditions without manual intervention. For example, automatically move a user to a "Quarantined" DUG if their device fails a HIP check or if a SOAR platform tags them due to detected malware. This automates incident response at the network access level.
- Enhanced Granularity: Create policies targeting very specific conditions (e.g., "Allow access only for Finance users AND connecting on a Compliant device tagged 'Corporate-Asset'"). Combining static groups with dynamic context via DUGs allows for highly specific policy rules.
- Reduced Administrative Overhead: Avoids constantly creating/updating static groups in Active Directory for temporary or state-based conditions (like device compliance, temporary contractor access, or quarantine status). Tags handle the dynamic state changes, which are automatically reflected in DUG membership.
- Improved Zero Trust Implementation: Directly supports the "Verify Explicitly" and "Assume Breach" principles by continuously checking context (via tags from sources like HIP) and adjusting access accordingly, regardless of static identity or network location. Policies can be based on verified device health (via HIP tags) alongside user identity and least privilege principles.
- Integration with Security Ecosystem: Enables powerful integrations where external tools (NAC, EDR, SOAR, TIPs) can influence firewall policy in near real-time by pushing tags via the API. This allows for centralized security intelligence to directly impact network access control.
-
Simplified Policy Logic (Potentially):
Instead of complex policy rules with multiple, potentially disparate conditions (e.g., IF Group=X AND Source_Zone=Y AND HIP_Profile=Z), a single DUG matching specific tags (e.g., Tag=
CompliantFinanceUser-VPN) can represent that combined state, making the policy rule cleaner and easier to read and manage.
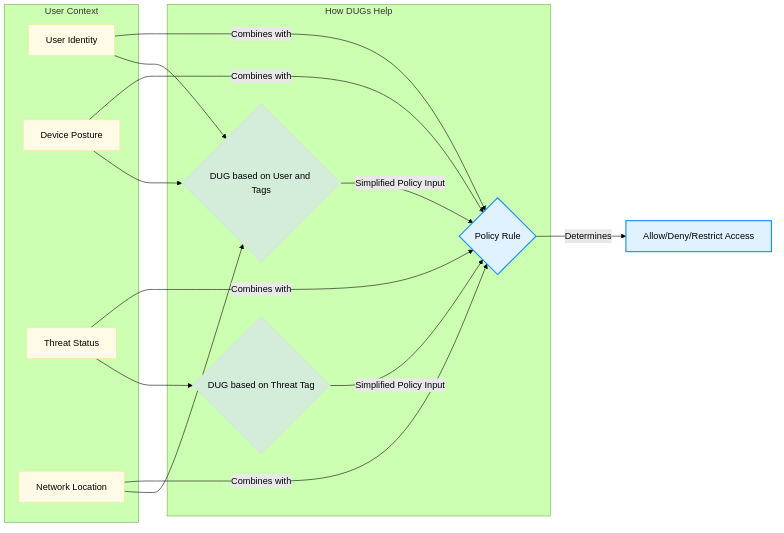
DUGs help consolidate various context attributes into a single 'Source User' object for simplified policy creation.
DUGs vs. Static Group Mapping
It's crucial to understand that DUGs are a different mechanism than static group mapping, though they are often used together.
Key Differences
| Feature | Static Group Mapping | Dynamic User Groups (DUGs) |
|---|---|---|
| Membership Source | Directory Service (AD, LDAP) | Tags associated with User-ID Mappings |
| Membership Basis | Organizational structure, user roles (defined in directory) | Real-time attributes, device state, security context (defined by tags) |
| Update Mechanism | Periodic polling of directory server (Group Mapping Refresh) | Near real-time based on tag assignment/removal (from HIP, API, etc.) |
| Nature | Static (changes require directory modification) | Dynamic (membership changes as tags change) |
| Primary Use | Role-Based Access Control (RBAC) | Context-Aware Access Control , Dynamic Response, Automation |
| Configuration | LDAP Server Profile, Group Mapping Settings, User-ID Agent (optional) | Tag sources (HIP Profiles, API integration, VM Info), DUG Objects (matching tags) |
Important: DUGs do not replace static group mapping. They complement it. Often, the most effective policies use a combination – for example, matching a static group (e.g., 'Sales-Users') AND a dynamic tag/DUG (e.g., 'Compliant-Device'). This implements a more granular "who AND what" policy.
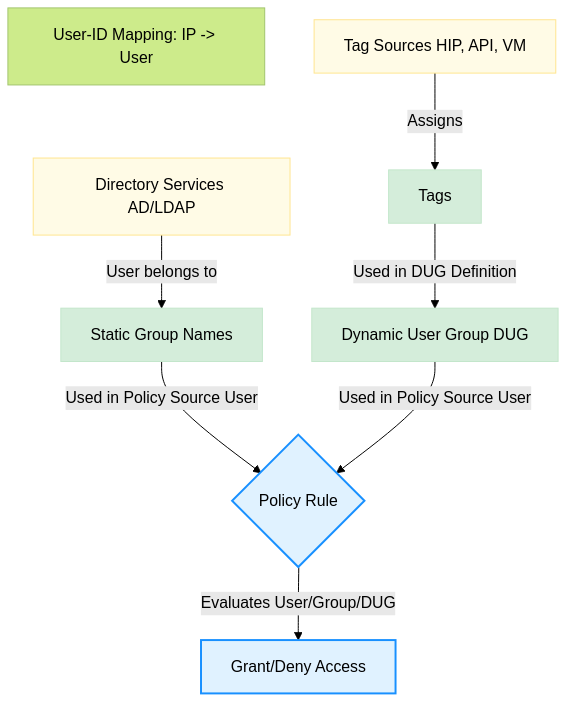
DUGs and Static Groups are distinct inputs that both feed into policy evaluation.
Example Use Cases for DUGs
Here are some practical scenarios where Dynamic User Groups significantly improve security posture and operational efficiency:
-
Device Compliance Enforcement:
- Configure HIP Profiles to check for endpoint security posture (AV status, patches, disk encryption, running processes, etc.).
- HIP Profile `Compliant-Windows` matches devices meeting standards and automatically tags the user's mapping with `win-compliant`.
- HIP Profile `NonCompliant-AV` matches devices with out-of-date AV and tags users with `av-noncompliant`.
- Create a DUG `DUG-Compliant-Endpoints` that matches the tag `win-compliant`.
- Create a DUG `DUG-Quarantine` that matches the tag `av-noncompliant`.
-
Policy Example:
-
Security Policy 1: Source User =
DUG-Compliant-Endpoints, Destination Zone = Trust, Application = business-critical-apps -> Action: Allow. -
Security Policy 2: Source User =
DUG-Quarantine, Destination Zone = Untrust, Application = web-browsing (limited), URL Category = High-Risk -> Action: Deny. Source User =DUG-Quarantine, Destination Zone = Trust, Application = remediation-tools -> Action: Allow.
-
Security Policy 1: Source User =
-
Threat Response / SOAR Integration:
- A SOAR platform, EDR, or other security tool detects suspicious activity associated with a user account or endpoint IP address (e.g., malware execution, unusual login location).
- The external platform uses the PAN-OS API to register a specific tag (e.g., `compromised-host`, `high-risk-user`) for the relevant IP-to-User mapping in near real-time.
- Create a DUG `DUG-Compromised-Users` matching tags `compromised-host` OR `high-risk-user`.
-
Policy Example:
Security Policy (high in rule order): Source User =
DUG-Compromised-Users, Destination = Any -> Action: Deny, Log at Session End. This immediately isolates the potentially compromised user/device.
-
BYOD vs. Corporate Asset Differentiation:
- Configure HIP checks to identify characteristics specific to corporate-owned assets (e.g., domain membership, specific software installed, presence of corporate certificates). Tag corporate assets with `corp-asset` and BYOD with `byod`.
- Create DUGs `DUG-Corp-Assets` and `DUG-BYOD` matching the respective tags.
-
Policy Example:
- Policies grant broader access or less strict security profiles to users in `DUG-Corp-Assets`.
- Policies apply more restrictive access or stronger security profiles (e.g., stricter content filtering, heavier decryption) to users in `DUG-BYOD`.
-
Temporary Access Provisioning:
- For temporary contractors, visitors, or specific project teams, use an external system or script to API-tag their IP/User mapping for a limited time (e.g., tag `Project-Alpha-Access`, `Visitor-Kiosk`).
- Create DUGs for these temporary tags.
- Policy Example: Policies allow access to specific resources only for users in the relevant temporary DUG, and access is automatically revoked when the tag expires or is removed.
Caveats and Considerations
While powerful, DUGs come with certain points you need to be aware of:
Gotcha! Pay close attention to these points:
- Tag Source Reliability is Paramount: The effectiveness and accuracy of DUG membership depend entirely on the accuracy and timeliness of the tag assignments from the source systems (HIP, API, etc.). If HIP checks are inaccurate, API pushes fail, or VM info is stale, DUG membership will be incorrect, leading to wrong policy enforcement.
- Tag Management Complexity: As the number of tag sources and specific conditions grows, managing a large number of different tags and ensuring consistent naming conventions across different integration points can become complex. Plan your tagging strategy carefully.
-
Troubleshooting Requires Visibility into Tags:
Diagnosing policy issues involving DUGs is more complex than static groups. You must check not only the policy rule and DUG definition but also
verify the specific tags currently assigned to the user's IP-to-User mapping
.
CLI Command:
This command is critical for seeing which tags are currently active for a user's session.show user ip-user-mapping ip <ip_address> - Dependency on User-ID Mapping: DUGs rely on a valid IP-to-User mapping existing first. If User-ID itself is not working correctly for a user's session, they cannot be tagged, and therefore cannot be members of a DUG.
- Potential for Rapid Changes: Depending on the tag source (especially API-driven tags from SOAR/TIPs), DUG membership can change rapidly (e.g., a user tagged as 'Quarantined' then later tagged as 'Remediated'). This dynamic nature is the power of DUGs, but session handling and user experience during these state transitions need to be considered.
- Policy Order: Just like static groups, DUGs are used in the Source User field. Ensure policies utilizing DUGs are ordered logically to achieve the desired outcome, especially when overlapping with other policies. More specific DUG/static group combinations should generally be higher.
PCNSE Exam Focus
For the PCNSE (and PCNSA) exam, you must have a solid understanding of Dynamic User Groups and how they function alongside User-ID.
Key areas to focus on include:
- Definition and Purpose: Clearly understand what DUGs are (group membership based on dynamic tags) and why they are used (context-aware, dynamic policies, Zero Trust). Differentiate them from static directory groups.
- Core Mechanism: Tags: Know that tags are the fundamental building block and that they are associated with the IP-to-User mapping.
-
Primary Sources for Tags:
Be able to name and describe the main ways tags get applied:
- GlobalProtect HIP Profiles (match/mismatch results).
- User-ID XML/REST API (for integration with external security tools).
- VM Information Sources (less common on PCNSA, more on PCNSE).
-
Configuration:
Understand where DUG objects are defined in the GUI (
Objects > Dynamic User Groups) and how you specify the tags that define membership for a DUG. - Policy Usage: Know that DUGs are referenced in the Source User field of Security, QoS, Decryption, and Authentication policies.
- Benefits: Be able to articulate the key benefits (context-awareness, automation, Zero Trust enablement, reduced admin for dynamic states).
- Relationship to Static Groups: Crucially, understand that DUGs complement , not replace, static groups. Policies often use a combination.
-
Troubleshooting DUGs:
Remember the CLI command
show user ip-user-mapping ip <ip_address>is vital for seeing the tags currently applied to a user's session when troubleshooting DUG-related policy issues.
Dynamic User Groups (DUG) and User-ID Quiz
Test your knowledge on Dynamic User Groups and related User-ID concepts.