Mastering User-ID Group Mapping in PAN-OS
Introduction to Group Mapping
While User-ID is the mechanism that maps an IP address to an individual username (e.g.,
192.168.1.100
is
DOMAIN\jsmith
),
Group Mapping
is the feature that allows Palo Alto Networks firewalls to understand the
group memberships
of these identified users. This is a critical second step in building truly effective identity-based security policies.
Instead of creating policies for hundreds or thousands of individual users, administrators can define policies based on logical groupings of users, such as "Sales," "Engineering," "IT_Admins," or "Contractors." When a user's group membership changes in the central directory (e.g., Active Directory), their access permissions, as defined by group-based firewall policies, update automatically without requiring manual changes to the firewall configuration.
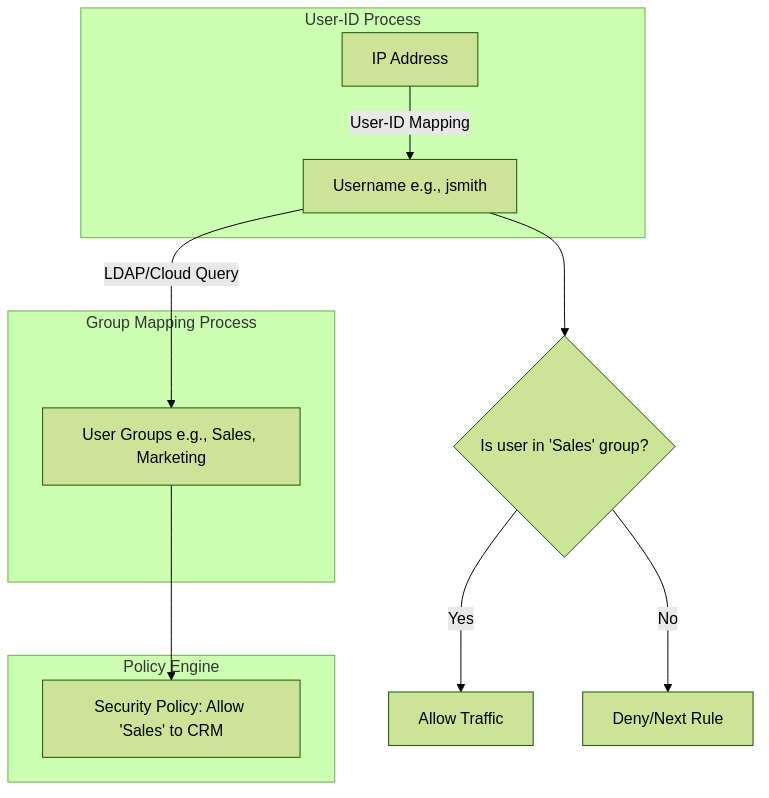 User-ID provides the 'who', Group Mapping provides their 'affiliations', enabling group-based policy decisions.
User-ID provides the 'who', Group Mapping provides their 'affiliations', enabling group-based policy decisions.
Group Mapping essentially allows the firewall to query an external directory service or identity provider to retrieve a list of groups a specific user belongs to. This information is then cached on the firewall and used in policy enforcement.
Importance of Group Mapping in Identity-Based Policy
Group Mapping is not just a convenience; it's fundamental to scalable and maintainable identity-based security. Here's why it's so important:
-
Simplified Policy Management:
Managing policies for a few well-defined groups is significantly easier and less error-prone than managing policies for numerous individual users. A single rule like "Allow 'Engineering' group to access Git repositories" covers all current and future members of that group.
Example:
Without Group Mapping: 100 engineers require access to a dev server. You'd need 100 user-based rules or one very broad IP-based rule.
With Group Mapping: 1 rule: "Source User: Engineering_Group, Destination: Dev_Server_Zone, Action: Allow".
- Scalability: As organizations grow and user roles change, managing individual user access in firewall policies becomes unmanageable. Group-based policies scale effortlessly with organizational changes handled in the central directory.
- Dynamic Policy Enforcement: When a user is added to or removed from a group in Active Directory (or another source), their access permissions through the firewall (based on those group policies) are automatically updated after the firewall refreshes its group mapping information. No manual firewall changes are needed for routine user onboarding/offboarding or role changes.
- Role-Based Access Control (RBAC): Group Mapping is the enabler for RBAC on the firewall. You define access based on roles (represented by groups) rather than individual identities.
- Reduced Administrative Overhead: Significantly lowers the time and effort spent by network security administrators on managing user access rules. The responsibility for managing who belongs to which group typically resides with directory administrators or identity management teams.
- Improved Security Posture: By making policies easier to manage and more dynamic, the likelihood of misconfigurations or overly permissive rules (due to the complexity of individual user rules) is reduced. It ensures the principle of least privilege can be more effectively applied.
- Consistency with Enterprise Identity Management: Aligns firewall security policies with the organization's broader identity and access management (IAM) strategy, using the central directory as the source of truth for user affiliations.
Overall Group Mapping Workflow
The process of how the firewall learns and uses group information involves several steps:
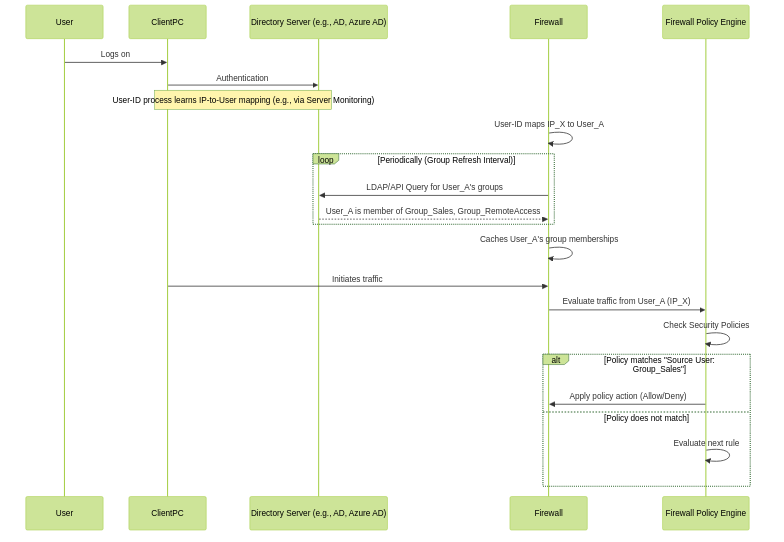
Simplified workflow showing User-ID mapping followed by Group Mapping and policy evaluation.
-
User Identification:
First, the User-ID feature (Agent or Agentless) identifies the user associated with an IP address (e.g.,
jsmithis at10.1.1.50). -
Group Mapping Configuration:
The administrator configures Group Mapping settings on the firewall. This involves:
- Creating Server Profiles (e.g., LDAP Server Profile for Active Directory, or configuring Cloud Identity Engine for cloud IDPs).
- Defining how often the firewall should poll the directory server for updates (Update Interval).
- Specifying which groups to include or exclude (Group Include List / Custom Filters).
- Firewall Queries Directory: Periodically (based on the configured update interval), the firewall connects to the configured directory service (e.g., an Active Directory Domain Controller via LDAP).
-
Retrieval of Group Information:
The firewall queries the directory for:
- A list of all available groups (within the specified scope/filter).
-
The members of those groups.
For an already identified user (e.g.,
jsmith), it can specifically query for all groups thatjsmithbelongs to.
- Caching: The firewall caches this user-to-group membership information locally. This cache is crucial for fast policy lookups.
-
Policy Enforcement:
When traffic from an identified user (
jsmithat10.1.1.50) hits the firewall:-
The firewall looks up
jsmithin its cached group information. - It then evaluates Security Policies that use group names in the "Source User" field.
-
If
jsmithis a member of a group specified in a matching policy rule, that rule's action is applied.
-
The firewall looks up
- Periodic Refresh: The firewall continues to poll the directory service at the configured interval to update its cache with any changes in group memberships.
Group Mapping Sources & Configuration
1. LDAP (e.g., On-Premises Active Directory)
This is the most traditional and widely used method for Group Mapping, especially for organizations with on-premises Microsoft Active Directory.
Mechanism:
The firewall acts as an LDAP client and queries the AD Domain Controllers (which act as LDAP servers) to retrieve user and group information. It typically binds (authenticates) to the LDAP server using a service account.
Prerequisites:
- LDAP Server(s): Accessible Active Directory Domain Controller(s).
- Network Connectivity: Firewall must be able to reach DCs on LDAP (TCP 389) or LDAPS (TCP 636) ports.
- Service Account: An AD user account with at least read permissions to the necessary user and group attributes in AD. Domain User is usually sufficient, but verify specific attribute read access. Do not use a Domain Admin account.
-
Directory Structure Knowledge:
-
Base DN (Distinguished Name):
The starting point in the AD tree from where the firewall will search for users and groups (e.g.,
DC=example,DC=com). -
Bind DN:
The full distinguished name of the service account used for LDAP bind (e.g.,
CN=svc_paloalto,OU=ServiceAccounts,DC=example,DC=com). - User and Group attributes (see configuration).
-
Base DN (Distinguished Name):
The starting point in the AD tree from where the firewall will search for users and groups (e.g.,
Configuration Steps:
-
Create an LDAP Server Profile:
-
Navigate to
Device > Server Profiles > LDAP. ClickAdd. -
Profile Name:
A descriptive name (e.g.,
AD_LDAP_Profile). -
Server List:
Click
Addto add LDAP servers.-
Name:
Name for this server entry (e.g.,
DC01). - LDAP Server: IP address or FQDN of the Domain Controller.
-
Port:
389for LDAP,636for LDAPS (recommended). If using LDAPS, ensure the firewall trusts the DC's certificate or import the CA certificate.
You can add up to 10 servers in PAN-OS 10.0+ (previously 4) for redundancy. The firewall tries them in order. -
Name:
Name for this server entry (e.g.,
-
Type:
Select
active-directory. -
Base DN:
The Base DN for your domain (e.g.,
DC=company,DC=local). -
Bind DN:
The full DN of your service account (e.g.,
CN=svc_ldap,OU=Service Accounts,DC=company,DC=local). - Password: Password for the Bind DN service account.
- Require SSL/TLS secured connection: Check if using LDAPS (port 636). Recommended.
-
Verify Server Certificate (for SSL/TLS):
If checked, the firewall must trust the DC's certificate. You might need to import your internal CA cert into
Device > Certificate Management > Certificatesand assign it to an SSL/TLS Service Profile used here. - (Optional) Bind Timeout / Timelimit / Retry Interval: Adjust if needed for slow LDAP servers.
-
Click
OK.
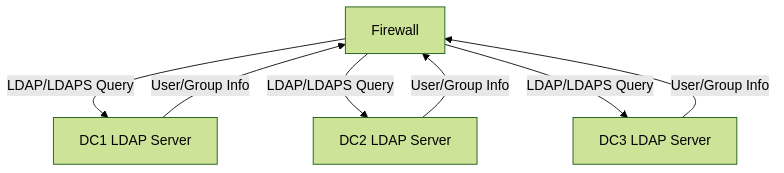
Firewall querying multiple DCs in an LDAP Server Profile for redundancy.
-
Navigate to
-
Configure Group Mapping Settings:
-
Navigate to
Device > User Identification > Group Mapping Settingstab. ClickAdd. -
Name:
A descriptive name (e.g.,
AD_Group_Mapping). - Server Profile: Select the LDAP Server Profile created above.
- Enabled: Check this box.
-
User Domain:
(Optional) If users log in with just their username (e.g.,
jsmithinstead ofCOMPANY\jsmith), you can specify the domain here. Otherwise, the firewall often derives it. - Update Interval: How often the firewall re-queries LDAP for group memberships. Default is 3600 seconds (1 hour). Adjust based on how frequently group memberships change in your AD. Too frequent can load DCs; too infrequent means delays in policy updates.
-
User and Group Objects / Attributes:
-
Primary Username:
Typically
sAMAccountNamefor AD. Can also beuserPrincipalName. - Alternate Username 1/2/3: (Optional) If users might be identified by other attributes.
-
User Object Class:
Default
useris usually correct for AD. -
Group Object Class:
Default
groupis usually correct for AD. -
Group Name Attribute:
Default
cn(Common Name) ornameis often used. Could also besAMAccountNamefor groups. -
Group Member Attribute:
Default
memberis usually correct for AD. - Nested Groups: Select "Enabled" if you want the firewall to resolve nested group memberships (e.g., User A is in Group B, Group B is in Group C; with nesting, User A is considered part of Group C). This can increase LDAP query load.
-
Primary Username:
Typically
-
Navigate to
-
Group Include List:
This is crucial for performance and manageability.
-
Click
Addto specify which AD groups the firewall should import and make available for policy. - You can specify groups by their DN or common name.
- Best Practice: Only include groups that you will actually use in firewall policies. Importing all groups from a large AD can consume significant firewall resources and clutter the policy creation interface.
-
Click
-
(Optional)
Custom Group Settings / LDAP Filters:
- Instead of, or in addition to, the Group Include List, you can define custom groups based on LDAP filters that match specific user attributes. This is more advanced.
-
Click
OK. - Commit Changes: Commit the configuration to the firewall.
2. Azure Active Directory (via Cloud Identity Engine)
For organizations using Azure AD as their primary identity provider, Palo Alto Networks offers the Cloud Identity Engine (CIE) to facilitate group mapping.
Mechanism:
The firewall doesn't directly query Azure AD via LDAP (as Azure AD's LDAP support is limited for this purpose). Instead:
- You subscribe to the Cloud Identity Engine app (available on the Palo Alto Networks hub).
-
Configure the CIE to connect to your Azure AD tenant using appropriate permissions (typically via an App Registration with Microsoft Graph API permissions like
Group.Read.AllandUser.Read.All). - The CIE periodically polls Azure AD for user and group information.
- The firewall (or Panorama) is configured to connect to the CIE instance associated with your support account.
- The firewall retrieves user-to-group mappings from the CIE.
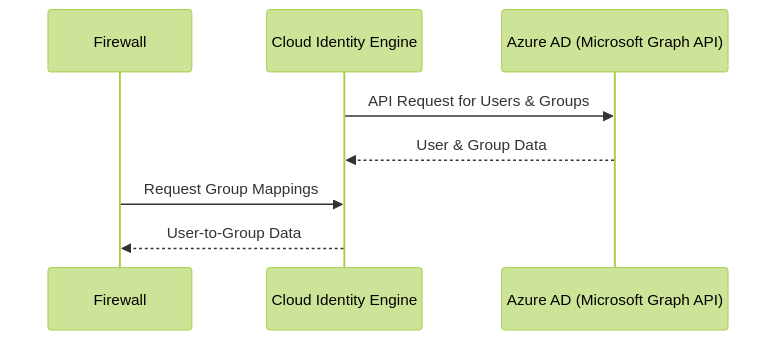
Firewall retrieves group information from Azure AD via the Cloud Identity Engine.
Prerequisites:
- Azure AD tenant.
-
Permissions in Azure AD to create an App Registration and grant it necessary Microsoft Graph API permissions (e.g.,
Group.Read.All,User.Read.All,Directory.Read.All). - A Palo Alto Networks support account to activate and configure the Cloud Identity Engine app.
- Firewall (PAN-OS 9.1 or later typically recommended for full CIE features) or Panorama with internet access to reach the CIE.
Configuration Steps (High-Level):
-
In Azure Portal:
- Create an App Registration for the Cloud Identity Engine.
- Grant the required Microsoft Graph API permissions (Application permissions).
- Create a client secret for the App Registration and note the Application (client) ID, Directory (tenant) ID, and client secret value.
-
In Palo Alto Networks Hub (Cortex Apps):
- Activate and launch the "Cloud Identity Engine" application.
-
Add a new Azure AD Directory Sync:
- Provide a name.
- Enter the Application (client) ID, Directory (tenant) ID, and client secret obtained from Azure.
- Test the connection.
- Select which Azure AD groups to sync to the CIE (similar to a Group Include List).
- Allow time for the initial sync to complete.
-
On the Firewall/Panorama:
-
Navigate to
Device > User Identification > Group Mapping Settings. ClickAdd. -
Name:
A descriptive name (e.g.,
AzureAD_CIE_Groups). -
Server Profile:
Select
"Cloud Identity Engine"
from the dropdown.
No separate LDAP server profile is needed for this method.
- Enabled: Check this box.
- User Domain: (Optional) Specify if needed.
- Update Interval: How often the firewall polls the CIE for updates.
-
Primary Username:
Typically
userPrincipalNamefor Azure AD. - Group Include List: This will be populated based on the groups you configured to sync from Azure AD to the CIE. You can further refine which of those synced groups are made available for policy on this specific firewall.
-
Click
OK.
-
Navigate to
- Commit Changes: Commit the configuration to the firewall.
The Cloud Identity Engine simplifies integration with cloud-based identity providers by abstracting the direct API interactions.
3. Other Cloud IDPs (GCP, Okta via Cloud Identity Engine)
Similar to Azure AD, the Cloud Identity Engine (CIE) is also the mechanism for integrating with other popular cloud identity providers like Google Cloud Platform (GCP) Identity / Google Workspace and Okta.
Mechanism:
The process mirrors the Azure AD integration via CIE:
- The CIE is configured with credentials/API keys to connect to your GCP or Okta environment.
- CIE polls these IDPs for user and group information.
- The firewall queries the CIE for the consolidated identity data.
Prerequisites:
- Your specific cloud IDP account (GCP with Directory Sync enabled, or Okta).
- Administrative access to your IDP to configure API access for CIE (e.g., service account keys for GCP, API token for Okta).
- Palo Alto Networks support account for CIE.
- Firewall/Panorama with internet access to CIE.
Configuration Steps (High-Level):
-
In your IDP (GCP or Okta):
- GCP: Create a service account, grant it appropriate roles (e.g., Group Member Viewer, User Viewer), and generate a JSON key.
- Okta: Create an API token with read-only administrator privileges (or more granular permissions if possible).
-
In Palo Alto Networks Hub (Cloud Identity Engine App):
- Add a new Directory Sync for GCP or Okta.
- Provide the necessary credentials (e.g., GCP service account JSON key, Okta domain and API token).
- Test connection and select groups to sync.
-
On the Firewall/Panorama:
-
Configuration under
Device > User Identification > Group Mapping Settingsis identical to the Azure AD via CIE method:- Select "Cloud Identity Engine" as the Server Profile type.
- The Group Include List will reflect groups synced from GCP/Okta to CIE.
-
Configuration under
- Commit Changes.
4. Panorama (Master Device Groups)
In environments managed by Panorama, you can define Master Device Groups directly on Panorama. These are essentially locally defined groups on Panorama that can then be pushed down to managed firewalls and used in policies.
Mechanism:
This method does not involve querying an external directory for dynamic group memberships. Instead, administrators manually define these groups on Panorama.
-
Groups are created on Panorama (e.g., under
Panorama > Objects > Custom Objects > User Groupsor as part of a Device Group configuration). - These groups are then referenced in policies pushed from Panorama to managed firewalls.
- When User-ID identifies a user on a managed firewall, and if that user's username matches an entry in a Master Device Group that's used in a policy, the policy applies.
This method is less about dynamic "mapping" of external groups and more about using locally defined, centrally managed user group objects.
Use Cases:
- For defining very static groups of users where external directory integration is not available or desired for those specific groups.
- To complement other dynamic group mapping methods with some locally defined, centrally managed groups.
- For simplified scenarios where user lists are small and manually managed.
Prerequisites:
- Panorama managing the firewalls.
- User-ID configured on firewalls to identify individual users.
Configuration Steps (High-Level):
-
On Panorama:
-
Navigate to
Panorama > Objects > Custom Objects > User Groups(or similar path depending on PAN-OS version for creating user group objects). -
Create new user group objects and manually add usernames to them (e.g.,
DOMAIN\user1,user2@example.com). Alternatively, these can sometimes be configured within Device Group hierarchies if users are to be part of specific device group contexts.
-
Navigate to
-
Policy Creation on Panorama:
- When creating Security Policies (or other policies like QoS, Decryption) on Panorama within a Device Group, select these locally defined Panorama user groups in the "Source User" field.
- Push Configuration: Commit and push the configuration from Panorama to the managed firewalls.
The firewall will then have these group definitions and can use them in policy matching against the identified username from the User-ID process.
5. Custom Groups (via LDAP Filters)
Within an LDAP-based Group Mapping configuration (typically for Active Directory), you can define Custom Groups . These are not actual group objects in AD but are dynamically populated by the firewall based on an LDAP filter that matches user attributes.
Mechanism:
- You define a custom group name on the firewall.
- You associate an LDAP filter with this custom group. This filter specifies criteria based on user object attributes in AD.
- When the firewall queries AD, it evaluates this filter against user objects.
- Any user whose attributes match the filter is considered a member of this custom group by the firewall.
Example Use Cases:
-
Create a group of all users in a specific department: Filter might be
(department=Sales). -
Create a group of all users whose accounts are enabled: Filter might be
(!(userAccountControl:1.2.840.113556.1.4.803:=2))(bitmask for account disabled). -
Create a group of users with a specific job title: Filter might be
(title=Manager).
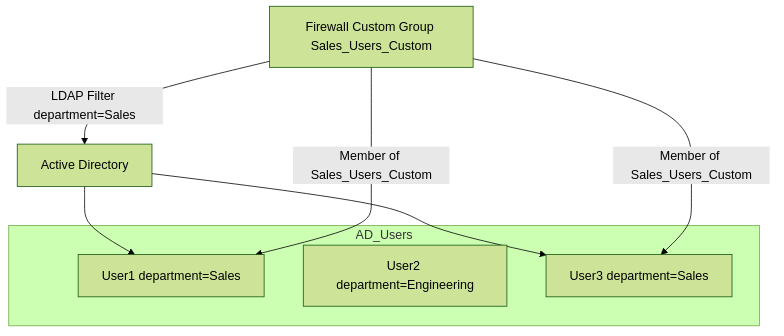
Firewall uses an LDAP filter to dynamically populate a custom group.
Prerequisites:
- A working LDAP Server Profile and basic Group Mapping configuration for AD.
- Knowledge of AD user attributes and LDAP filter syntax.
Configuration Steps:
-
Navigate to
Device > User Identification > Group Mapping Settings. Edit your existing AD group mapping configuration. - Go to the "Custom Groups" or "Group Include List / Custom Groups" tab (exact naming varies slightly by PAN-OS version).
-
Click
Addunder the Custom Groups section. -
Name:
Enter the name you want to use for this custom group in firewall policies (e.g.,
Department_Sales_Custom). This name does not need to exist as an actual group in AD. -
LDAP Filter:
Enter the LDAP filter that defines membership.
-
Example for users in the "Sales" department:
(department=Sales) -
Example for users whose "description" attribute contains "Contractor":
(description=*Contractor*)
-
Example for users in the "Sales" department:
-
Click
OKto save the custom group. -
Click
OKto save the Group Mapping settings. - Commit Changes.
The firewall will then use these custom group definitions when matching users to policies. Users matching the LDAP filter will be considered members of the custom group you defined.
Deployment Planning for Group Mapping
Effective Group Mapping requires careful planning to ensure it aligns with your organization's structure, security requirements, and operational capabilities.
-
Identify Directory Services and Identity Providers (IdPs):
- Determine all sources of user identity: On-premises Active Directory, Azure AD, Okta, GCP Identity, other LDAP v3 compliant directories.
- Understand if you have a hybrid environment (e.g., on-prem AD synced to Azure AD).
-
Assess Directory Topology:
-
For On-Prem AD:
- Number of domains and forests? Are there trusts between them?
- Location and number of Domain Controllers (DCs)? Aim to query DCs local to the firewall or User-ID agent to minimize latency.
- Are Global Catalog servers relevant/necessary for your queries? (Usually for multi-domain searches if Base DN is high in the tree).
-
For On-Prem AD:
- For Cloud IdPs: Understand the subscription model, API limits, and data sync mechanisms (e.g., via Cloud Identity Engine).
-
Analyze Existing Group Structures:
- Review how users are currently organized into groups within your directory service(s).
- Are existing groups suitable for firewall policy, or do new groups need to be created?
- Consider using Universal Groups in AD for multi-domain forests if groups need to be recognized across domains. Global groups are generally sufficient within a single domain. Domain Local groups are typically for resource permissions within a domain and less ideal for cross-domain firewall policy.
-
Define Groups for Firewall Policy:
- Work with stakeholders (application owners, business units) to identify logical groupings of users that require similar network access.
- Principle of Least Privilege: Design groups that grant only necessary access.
- Aim for a manageable number of groups to use in firewall policies. Too many groups can make policy management complex again.
-
Consider using a naming convention for groups intended for firewall policy (e.g.,
FW_Sales_Access,FW_Developers_VPN).
-
Plan for Redundancy (LDAP Server Profiles):
- In your LDAP Server Profile on the firewall, configure multiple Domain Controllers (up to 10 in recent PAN-OS versions).
- The firewall will try them in order if the primary one is unavailable.
- Place DCs from different sites/availability zones if possible.
-
Ensure Unique Usernames (Especially in Multi-Domain/Forest Scenarios):
-
If integrating multiple directories where usernames might not be globally unique (e.g.,
jsmithin domain A andjsmithin domain B), User-ID needs a way to distinguish them. -
Using User Principal Names (UPNs -
user@domain.com) as the primary username attribute is often better in these scenarios. - The "User Domain" setting in Group Mapping can help if users log in with unqualified names.
-
If integrating multiple directories where usernames might not be globally unique (e.g.,
-
Determine Update Intervals:
- How frequently do group memberships change in your organization?
- Balance the need for up-to-date information with the load on directory servers and the firewall.
- Default is 1 hour (3600 seconds). For very dynamic environments, you might reduce it, but monitor performance. For static environments, you could increase it.
-
Service Account Strategy:
- Create a dedicated, least-privilege service account for Group Mapping (and User-ID Server Monitoring).
- Document its permissions and manage its password securely.
-
Security for LDAP/API Connections:
- Prefer LDAPS (TCP 636) over LDAP (TCP 389) for encrypted communication with AD.
- If using Cloud Identity Engine, ensure secure API key/secret management.
-
Group Include List Strategy:
- Crucial: Always use the Group Include List (or custom group filters) to limit the number of groups the firewall imports. Importing all groups from a large AD can severely impact firewall performance and make policy management cumbersome. Only include groups you intend to use in policies.
For detailed planning guidelines, the official Palo Alto Networks documentation like the User-ID Best Practices for Group Mapping is an excellent resource.
Prerequisites for Group Mapping
Before configuring Group Mapping, ensure the following prerequisites are met:
-
Functional User-ID:
- Group Mapping relies on User-ID to first identify the individual user associated with an IP address. Ensure your User-ID collection methods (Server Monitoring, GlobalProtect, Captive Portal, etc.) are working correctly and the firewall has an up-to-date IP-to-user mapping table.
-
Directory Service / Identity Provider Access:
-
For LDAP (e.g., Active Directory):
- Accessible Domain Controller(s) acting as LDAP servers.
-
A dedicated
service account
with at least read permissions to user and group objects and their relevant attributes (e.g.,
sAMAccountName,memberOf,member,departmentif using for custom groups). - Knowledge of your AD structure: Base DN, Bind DN of the service account, service account password.
-
For LDAP (e.g., Active Directory):
-
For Cloud Identity Engine (Azure AD, GCP, Okta):
- Subscription to and configuration of the Palo Alto Networks Cloud Identity Engine app.
- Administrative credentials or API keys/secrets for your cloud IdP to allow CIE to sync data (e.g., Azure App Registration with Graph API permissions, GCP service account key, Okta API token).
-
Network Connectivity:
- The firewall's management interface (or a specified service route source interface) must have network reachability to the directory servers or the Cloud Identity Engine.
-
Necessary ports must be open through any intermediary firewalls:
- LDAP: TCP 389
- LDAPS: TCP 636 (Recommended for security)
- Cloud Identity Engine: HTTPS (TCP 443) to Palo Alto Networks cloud services.
-
SSL/TLS Certificates (for LDAPS or secure CIE):
-
If using LDAPS, the firewall must trust the certificate presented by the Domain Controller. This usually means importing the CA certificate (or the DC's certificate itself if self-signed, not recommended for production) into the firewall's certificate store (
Device > Certificate Management > Certificates) and potentially creating/assigning an SSL/TLS Service Profile. - Communication with CIE is typically over HTTPS and requires the firewall to trust standard public CAs.
-
If using LDAPS, the firewall must trust the certificate presented by the Domain Controller. This usually means importing the CA certificate (or the DC's certificate itself if self-signed, not recommended for production) into the firewall's certificate store (
-
PAN-OS Version:
- Ensure your PAN-OS version supports the specific Group Mapping features you intend to use (e.g., Cloud Identity Engine integration might have minimum PAN-OS requirements). Refer to release notes.
-
User and Group Attribute Knowledge:
-
Know the names of the attributes in your directory that store the primary username (e.g.,
sAMAccountName,userPrincipalName), group names (e.g.,cn,name), and group membership (e.g.,member,memberOf). Defaults are usually fine for AD, but can be customized.
-
Know the names of the attributes in your directory that store the primary username (e.g.,
-
(Optional) Panorama:
- If managing firewalls via Panorama, Group Mapping configurations can (and generally should) be done on Panorama within templates or template stacks for consistent deployment.
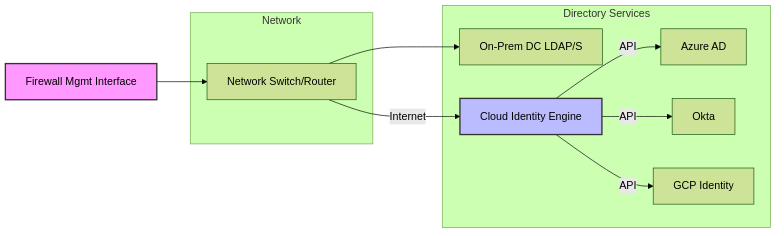
Network connectivity paths for Group Mapping sources.
Best Practices for Group Mapping
- Use a Dedicated Service Account with Least Privilege: Never use a domain admin account. Create a specific service account for LDAP queries with only the necessary read permissions for user and group attributes. Securely manage its credentials.
- Prefer LDAPS over LDAP: Use LDAP over SSL/TLS (LDAPS, TCP port 636) for encrypted communication between the firewall and your Active Directory Domain Controllers. This protects bind credentials and directory data in transit.
-
Utilize the Group Include List Aggressively:
This is paramount for performance and manageability.
Only include groups in your Group Mapping configuration that you will actually use in firewall Security, QoS, Decryption, or Authentication policies. Importing all groups from a large directory can:
- Consume excessive firewall management plane memory and CPU.
- Slow down commit times.
- Clutter the GUI when selecting groups for policies.
- Increase LDAP query load on your Domain Controllers.
-
Optimize Update Intervals:
The default Group Mapping update interval (e.g., 3600 seconds / 1 hour) is a good starting point.
- If group memberships change very frequently and timely policy updates are critical, you might reduce this interval.
- If group memberships are relatively static, you could increase it to reduce load.
- Monitor firewall and DC performance when adjusting this.
sAMAccountName
or
userPrincipalName
) matches the username format being learned by your User-ID methods. Consistency is key for successful correlation.
show user group-mapping state all
,
show user group list
) and Panorama/firewall GUI to check the status, last update time, and number of groups/users mapped. Investigate any errors promptly.
- Consider using Global Catalog servers in your LDAP Server Profile if you need to search across multiple domains in a forest with a single Base DN.
- Ensure usernames are unique or use UPNs.
- You might need separate Group Mapping configurations for different forests if there's no trust or common schema.
- Follow Palo Alto Networks' best practices for CIE setup and Azure AD/Okta/GCP app registration permissions.
- Monitor sync status in the CIE dashboard.
- Ensure the firewall has reliable internet connectivity to reach the CIE.
Verification & Troubleshooting Group Mapping
Verifying that Group Mapping is working correctly and knowing how to troubleshoot issues is crucial.
Verification Steps:
-
Check Group Mapping State:
-
CLI:
show user group-mapping state all - This command shows the status of each configured group mapping (e.g., "success", "error"), the last update time, the number of groups, and users found.
- Look for "success" and a recent update time.
-
CLI:
-
List Available Groups:
-
CLI:
show user group list - This displays all the groups the firewall has successfully retrieved and cached from the directory service(s) based on your Group Include List or custom filters. Verify that the groups you expect to use in policies are present.
-
CLI:
-
Check Specific Group Membership:
-
CLI:
show user group name "<group_name_in_quotes_if_spaces>" -
Example:
show user group name "Domain Admins" - This command lists the users that the firewall believes are members of the specified group. Compare this with the actual membership in your directory service.
-
CLI:
-
Verify User-to-IP Mapping:
-
CLI:
show user ip-user-mapping ip <user_ip_address> - First, ensure the user is correctly identified by User-ID.
-
CLI:
-
Test Policy Matching:
- Create a test security policy using one of the mapped groups in the "Source User" field.
- Generate traffic from a user who *is* and a user who *is not* in that group.
-
Check the traffic logs (
Monitor > Logs > Traffic) to see if the policy is being matched correctly and if the username and groups are populated in the log details.
-
Check Panorama/Firewall System Logs:
-
Filter for logs related to User-ID or LDAP (
Monitor > Logs > System). Look for any errors or warnings.
-
Filter for logs related to User-ID or LDAP (
Common Troubleshooting Scenarios & Tips:
-
Issue: No groups are listed or "Error" state in
show user group-mapping state all.- Cause: LDAP server unreachable, incorrect Bind DN/password, incorrect Base DN, SSL/TLS certificate issues (for LDAPS), firewall rules blocking LDAP/LDAPS.
-
Troubleshooting:
- Verify LDAP Server Profile: Correct IP/FQDN, port, service account credentials, Base DN.
-
Test connectivity from firewall to LDAP server on port 389/636 (e.g.,
test routing fib-lookup virtual-router <vr_name> ip <ldap_server_ip>, then tryping host <ldap_server_ip>andshow arp entry | match <ldap_server_ip>if on same L2, or test with a client on same segment as firewall mgmt). - Check firewall traffic logs for denied LDAP/LDAPS traffic from firewall's management IP.
-
If using LDAPS, verify the firewall trusts the DC's certificate. Check
Device > Certificate Management > SSL/TLS Service Profileused by LDAP profile. - Examine system logs on firewall for LDAP errors.
-
Run LDAP query from another machine using the same service account and Base DN to confirm they work outside the firewall (e.g., using
ldp.exeon Windows orldapsearchon Linux).
show user group list
.
- Cause: Group Include List is too restrictive or incorrect; group is outside the search scope (Base DN); service account lacks permission to read the group or its members.
-
Troubleshooting:
- Verify the Group Include List in Group Mapping settings. Ensure correct group names/DNs.
- Ensure the Base DN in the LDAP Server Profile is broad enough to include the missing groups.
- Check permissions for the service account on the specific group objects in AD.
- Cause: Stale cache, incorrect "Primary Username" attribute, issues with nested group resolution, user account issues in AD.
-
Troubleshooting:
-
Force a refresh:
debug user-id refresh group-mapping all(or specific mapping name). Wait for completion and recheck. -
Ensure "Primary Username" in Group Mapping (e.g.,
sAMAccountName) matches the username format learned by User-ID. - If using nested groups, try disabling it temporarily to see if the user appears in a direct parent group. Deeply nested or circular group structures can cause issues.
- Verify the user account is active and correctly configured in AD.
-
Force a refresh:
- Cause: Long Update Interval, overloaded DCs, network latency, firewall management plane load (less common for just group mapping).
-
Troubleshooting:
- Review and potentially shorten the "Update Interval" in Group Mapping Settings (balance with DC load).
- Ensure DCs are responsive and not overloaded.
- Check network performance between firewall and DCs.
- Cause: Incorrect API credentials/permissions in Azure AD/Okta/GCP, CIE app configuration error, firewall can't reach CIE.
-
Troubleshooting:
- Verify API permissions and credentials in both CIE and the cloud IdP.
- Check sync status and logs in the CIE dashboard.
- Ensure firewall has internet connectivity to Palo Alto Networks cloud services.
- Verify group selection in CIE for syncing.
The command
less mp-log authd.log
and
less mp-log userid.log
on the firewall can also provide detailed logs related to LDAP authentication and User-ID processes, which can be invaluable for deep troubleshooting.
PCNSE Focus for Group Mapping
For the PCNSE exam, a solid understanding of Group Mapping is essential as it directly relates to identity-based policy, a core tenant of Palo Alto Networks firewalls.
- Purpose of Group Mapping: Understand that it's to retrieve user group memberships from a directory service to enable group-based policies. It complements User-ID (which maps IP to username).
-
Primary Source - LDAP/Active Directory:
- Know how to configure an LDAP Server Profile (DCs, port, Base DN, Bind DN, credentials, SSL/TLS).
- Understand the settings within Group Mapping Settings (Server Profile selection, User Domain, Update Interval, User/Group attributes, Group Include List).
- Group Include List: Its importance for performance and manageability.
-
Username attributes:
sAMAccountNamevs.userPrincipalName. - Nested groups: What it means and potential impact.
- Understand its role as an intermediary for cloud IdPs like Azure AD, Okta, GCP Identity .
- Know that the firewall connects to CIE, and CIE connects to the cloud IdP via APIs.
- In Group Mapping settings on the firewall, you select "Cloud Identity Engine" as the server profile type.
Device > User Identification > Group Mapping Settings
. LDAP Server Profiles are under
Device > Server Profiles > LDAP
.
-
show user group-mapping state all -
show user group list -
show user group name <group_name> -
debug user-id refresh group-mapping all
Common Exam Gotchas for Group Mapping
Be aware of these common misunderstandings or tricky areas that might appear on the PCNSE exam:
- Group Include List is MANDATORY for Practical Use: While technically you *could* try to import all groups, the exam will lean towards the best practice, which is always use the Group Include List to only bring in necessary groups. Questions might imply what happens if it's not used (performance issues, too many groups).
- Service Account Permissions: Questions might test your knowledge of *minimum* required permissions (read access to user/group attributes) vs. overkill (Domain Admin).
- LDAP vs. LDAPS: Know that LDAPS (TCP 636) is secure, LDAP (TCP 389) is not. The exam favors secure configurations.
-
Username Attribute Mismatch:
If User-ID learns usernames in
DOMAIN\userformat (sAMAccountName) but Group Mapping is configured to primarily useuser@domain.com(userPrincipalName) without proper fallbacks or consistent directory attributes, the correlation might fail. - Nested Groups Impact: Understand that enabling nested group resolution can be resource-intensive. A question might ask about optimizing performance, and disabling unnecessary nesting could be an answer.
- Update Interval Trade-offs: A very short interval means more up-to-date info but more load. A very long interval means less load but potential delays in policy application for users whose group memberships just changed.
- Cloud Identity Engine (CIE) - Firewall Connects to CIE, NOT Directly to Azure AD via LDAP for Groups: A common point of confusion. For Azure AD group mapping, the firewall talks to CIE, and CIE talks to Azure AD (Graph API). The firewall does *not* use its LDAP Server Profile to query Azure AD for group memberships.
-
Troubleshooting Command Output Interpretation:
You might be shown output of
show user group-mapping state allorshow user group listand asked to identify a problem or next step. - Distinction from User-ID Redistribution by Panorama: Panorama can collect User-ID (IP-to-user) mappings and redistribute them. This is different from Panorama itself being a source for group definitions, although it can manage User-ID and Group Mapping configurations for firewalls. Master Device Groups on Panorama are locally defined groups.
- Base DN Scope: If the Base DN is too narrow, expected groups might not be found. If too broad without good indexing on DCs, queries might be slow.
- "User Domain" Field Purpose: This field in Group Mapping Settings helps the firewall correctly associate a simple username (e.g., "jsmith") with the correct domain if User-ID is providing unqualified usernames.
User-ID Group Mapping Quiz
Test your knowledge of User-ID Group Mapping concepts.