PAN-OS: User-ID Mapping Methods
Introduction: Identifying the User
The User-ID feature is a cornerstone of the Palo Alto Networks platform, enabling visibility and control based on user identity rather than just IP addresses. To achieve this, the firewall needs reliable methods to learn which user is associated with which IP address at any given time. PAN-OS supports a variety of methods, often used in combination, to gather this critical IP-address-to-username mapping information.
Understanding these different methods, their use cases, requirements, and limitations is essential for successfully deploying and troubleshooting User-ID. Comprehensive user visibility is critical for effective policy enforcement, reporting, and incident response.
Overview of User-ID Mapping Methods
The firewall (either directly via the PAN-OS Integrated User-ID Agent or indirectly via the Windows User-ID Agent ) can leverage numerous sources to obtain IP-to-user mappings:
- Server Monitoring: Monitoring authentication event logs on directory servers (e.g., Active Directory Domain Controllers).
- Port Mapping (Terminal Services Agent): Mapping users on multi-user systems (RDS/Citrix) based on source port ranges (Requires Windows Agent).
- Client Probing: Actively probing client workstations (Requires Windows Agent).
- GlobalProtect: Using authentication logs from GlobalProtect Portal/Gateway connections.
- Captive Portal: Using authentication logs from Captive Portal sessions.
- Syslog Integration: Parsing username and IP information from syslog messages sent by other network devices (VPNs, WLAN controllers, proxies, etc.).
- XML API / REST API: Receiving mappings pushed from external systems (NAC, ClearPass, ISE, custom scripts) via the API.
- Exchange Monitoring: Monitoring Microsoft Exchange server logs.
- eDirectory Monitoring: Monitoring Novell eDirectory environments (Requires Windows Agent).
Often, multiple methods are deployed concurrently to achieve comprehensive coverage across different user types and access methods. The optimal combination depends heavily on the specific network environment and authentication infrastructure.
Core User-ID Mapping Methods
1. Server Monitoring (Event Log Scraping)
This is typically the primary method for environments with Microsoft Active Directory.
- How it works: The User-ID component (either the Windows Agent or the PAN-OS Integrated Agent) monitors security event logs on domain controllers (DCs) for successful user logon events (e.g., Event ID 4624 - Account successfully logged on). These events provide the username and the source IP address of the client machine. Logoff events (e.g., Event ID 4634) are also monitored to remove stale mappings.
- Mechanism: Uses Windows Management Instrumentation (WMI) or Windows Remote Management (WinRM) to query DCs remotely. Requires a dedicated service account with sufficient permissions ( Event Log Readers group recommended). Can also process logs forwarded via Syslog.
- Use Case: Primary method for identifying users on domain-joined Windows clients in traditional enterprise networks. Provides accurate mapping for standard domain logons.
- Pros: Highly reliable for its primary use case, captures standard domain logon/logoff events, passive (doesn't require client-side configuration).
- Cons: Requires service account setup and permissions, network connectivity between the collector and DCs, sensitive to DC log rollover speed (requires tuning), doesn't typically capture non-domain logons or logons to systems not writing standard AD security logs .
- Agent/Agentless: Supported by both the Windows Agent and the Agentless PAN-OS Integrated Agent.
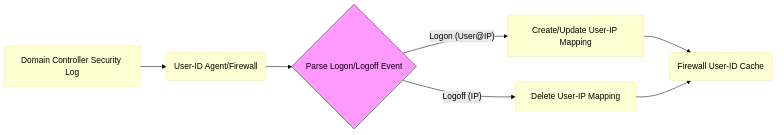
Simplified flow of Server Monitoring (Event Log Scraping).
Core User-ID Mapping Methods
2. GlobalProtect Authentication
Ideal for remote and mobile users connecting via VPN.
- How it works: When users successfully authenticate to a GlobalProtect Portal or Gateway (using methods like LDAP, SAML, RADIUS, Kerberos, Local DB), the firewall component hosting the service automatically creates a secure IP-to-user mapping. This mapping uses the authenticated username and the internal IP address assigned to the client from the VPN IP pool.
- Mechanism: Integrated directly into the GlobalProtect connection process. Authentication happens at the firewall, which directly creates the mapping entry.
- Use Case: Identifying remote users connecting via GlobalProtect VPN. Highly reliable as it's tied directly to the successful authentication event at the firewall itself.
- Pros: Very reliable, automatic upon successful GP authentication, requires no separate collector/agent setup, works for users regardless of location or device domain status.
- Cons: Only provides mappings for active GlobalProtect users. Does not map users connecting to the internal network via other means.
- Agent/Agentless: Managed directly by the firewall component (Portal or Gateway). Works independently of the Windows User-ID Agent.
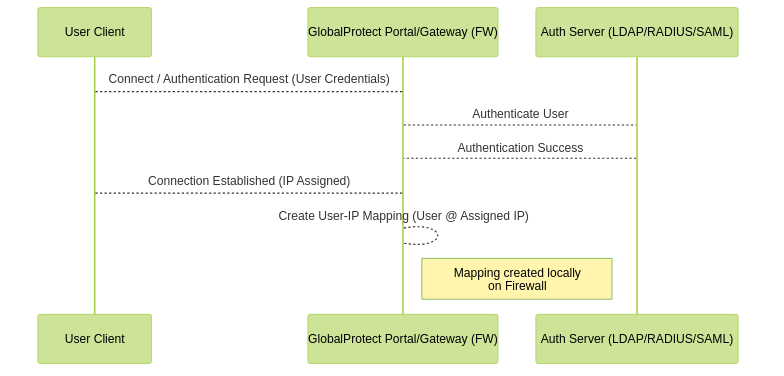
Sequence of GlobalProtect Authentication leading to a User-ID mapping.
Core User-ID Mapping Methods
3. Captive Portal Authentication
Useful for identifying users on guest networks, BYOD devices, or unmanaged clients.
- How it works: The firewall detects traffic from an unmapped IP address destined for resources requiring authentication. It intercepts and redirects the user's web browser to a login page (Captive Portal) hosted by the firewall. The user authenticates (e.g., against AD/LDAP, RADIUS, SAML, Local DB). Upon successful authentication, the firewall creates an IP-to-user mapping for the user's source IP address and a configurable timeout.
-
Modes:
- Transparent (Redirect): Intercepts specific protocols (HTTP/HTTPS by default) and redirects the browser. Least disruptive, common for internet access.
- Redirect (Passive): User is redirected upon attempting *any* connection matching a policy that requires authentication. Can be used for broader coverage but is more disruptive.
- NTLM Authentication: Can attempt transparent Windows authentication for domain-joined clients using NTLM challenges (less common now, browser support varies).
- Use Case: Identifying guest users, users on BYOD devices, non-domain-joined machines, or as a fallback method when Server Monitoring isn't possible or fails. Can also enforce Acceptable Use Policies (AUP) display.
- Pros: Maps users regardless of device/domain status (if they can use a browser), forces authentication, useful for compliance/AUP.
- Cons: Can be disruptive to user experience (especially redirect modes), relies on browser interaction (doesn't work for headless devices or non-web traffic initially), requires users to re-authenticate after session timeout. Potential security risks if not deployed securely (e.g., not using SSL for the portal).
- Agent/Agentless: Managed directly by the firewall. Works independently of the Windows User-ID Agent.
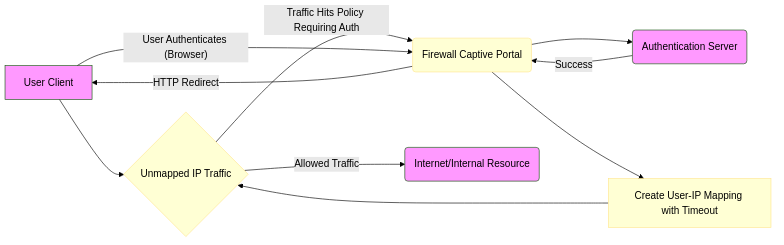
Simplified flow of Captive Portal authentication and mapping.
Core User-ID Mapping Methods
4. XML API / REST API
Provides flexible integration with external identity sources.
- How it works: The firewall (or Windows User-ID Agent) exposes an XML API endpoint (and increasingly, a REST API) specifically for receiving User-ID mappings. External systems that know the IP-to-user relationship (like Network Access Control solutions, wireless controllers, custom applications) can send API calls containing the IP address, username, and optional mapping timeout value. The firewall/agent processes these calls to create or update the mappings.
- Mechanism: The external system makes HTTP/HTTPS requests to the API endpoint, sending data in XML or JSON format. Requires an API key generated on the firewall for authentication.
- Use Case: Integrating User-ID with third-party systems that manage user authentication or IP assignment, such as NAC solutions (Cisco ISE, Aruba ClearPass), certain wireless controllers, VPN concentrators other than GlobalProtect, or custom identity systems. Ideal for complex environments or when standard methods don't capture all users.
- Pros: Highly flexible and extensible , can integrate with almost any system capable of making API calls, enables near real-time mapping updates from authoritative sources, can include group membership information.
- Cons: Requires configuration and potentially development/scripting effort on the external system sending the mappings. Relies entirely on the accuracy and timeliness of the external system. Requires secure API key management and network connectivity.
- Agent/Agentless: Mappings can be sent directly to the firewall (Agentless) or to the Windows User-ID Agent (which then forwards them).
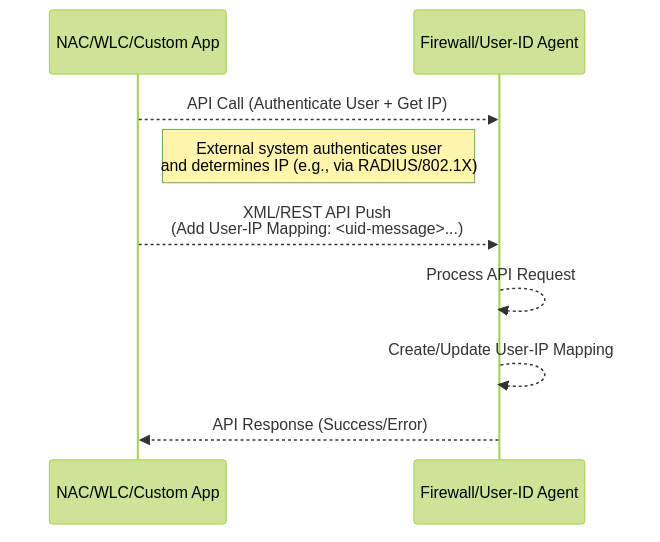
Sequence of User-ID mapping via XML/REST API.
Core User-ID Mapping Methods
5. Syslog Integration
A flexible option for devices that can send logs but don't support API integration.
- How it works: The User-ID component (either the Windows Agent or the PAN-OS Integrated Agent) is configured to listen for Syslog messages from other network devices (e.g., certain wireless controllers, older VPN concentrators, proxy servers, DHCP servers). The firewall/agent uses predefined or custom-configured Syslog Parse Profiles . These profiles contain regular expressions (regex) designed to extract the username and the associated IP address from specific patterns within the syslog messages.
- Mechanism: Requires configuring the source device to send relevant syslog messages to the IP address of the User-ID Agent or Firewall. On the PAN-OS side, a Syslog Listener and appropriate Parse Profiles must be configured and enabled.
- Use Case: Gathering User-ID mappings from third-party devices that log authentication or IP assignment information but lack direct API integration. Useful for environments with diverse network infrastructure components.
- Pros: Leverages existing logging infrastructure, potentially compatible with a wide range of devices.
- Cons: Highly dependent on consistent and predictable log formats from the source device. Requires creating and testing potentially complex regular expressions for parsing. Can be fragile if log formats change (e.g., after a firmware update on the source device). Processing volume can be high.
- Agent/Agentless: Supported by both the Windows Agent and the Agentless PAN-OS Integrated Agent.
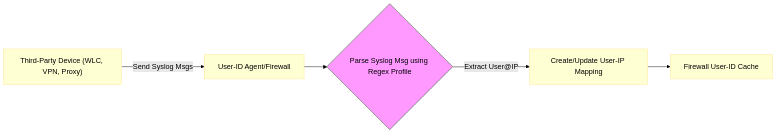
Simplified Syslog Integration mapping process.
Specialized & Agent User-ID Methods
6. Port Mapping (Terminal Services / TS Agent)
Essential for accurate user identification in shared desktop environments.
- How it works: Requires installing a specific component called the Terminal Services (TS) Agent , which is part of the Windows User-ID Agent package, directly onto Microsoft RDS (formerly Terminal Services) or Citrix XenApp servers. This agent monitors user logons and logoffs *on that specific server*. For each active user session, the TS Agent allocates a unique, dynamic range of source ports. It then sends a mapping of the user-to-source-port-range along with the server's IP address to the main User-ID Agent or directly to the firewall (if configured). The firewall uses the combination of the server's IP address and the source port of the traffic to identify the individual user.
- Mechanism: The TS Agent intercepts or hooks into the Windows login/session process on the multi-user server. It communicates the mappings via a proprietary protocol.
- Use Case: Accurately identifying individual users connecting through multi-user systems like RDS or Citrix servers , where multiple users share the same source IP address. Without the TS Agent, all traffic from the server IP would be mapped to the first user logged on or no user at all.
- Pros: Provides accurate user mapping in shared IP scenarios , which is impossible with other methods alone.
- Cons: Requires agent installation on each Terminal Server/Citrix server. Only applies to traffic originating from those specific servers. Adds complexity to the environment. Requires careful planning of port ranges if custom applications are used. Mappings are NOT shared between firewalls/agents via the User-ID Redistributor feature.
- Agent/Agentless: Requires the TS Agent component (part of the Windows Agent package). This agent can send mappings to the Windows User-ID Agent or directly to the firewall.
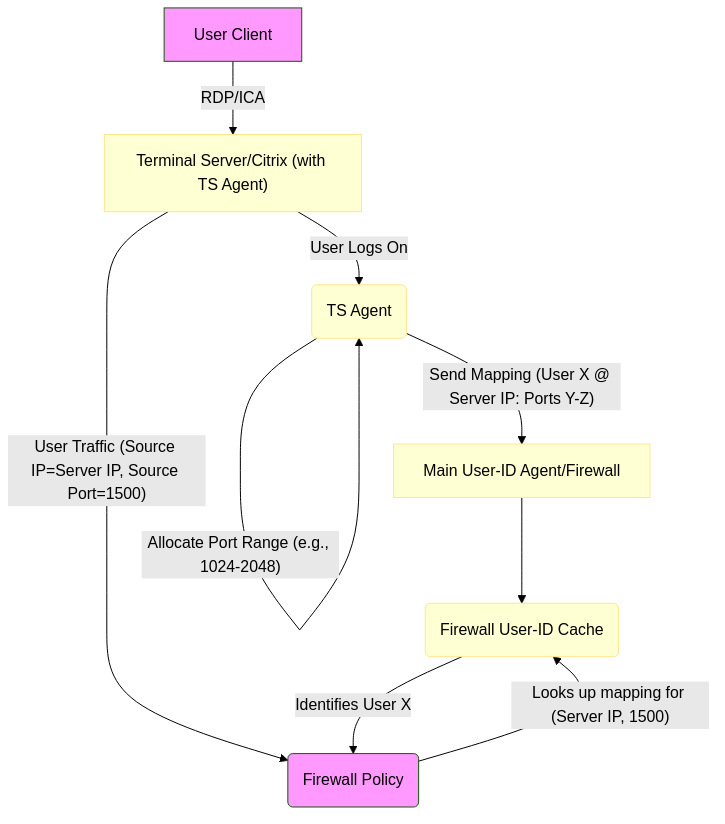
How Port Mapping works with a Terminal Server (TS) Agent.
Specialized & Agent User-ID Methods
7. Client Probing (Windows Agent Only)
An older, less recommended method for directly querying client machines.
- How it works: The Windows User-ID Agent actively attempts to connect to client workstations (using protocols like NetBIOS or WMI/WinRM) within configured subnets or specified IP addresses. It queries the endpoint to determine the currently logged-on user via standard Windows methods (like querying the session ID).
- Mechanism: The Windows Agent initiates outbound connections to client IPs. Requires administrative credentials on the target clients (or permissions allowing the service account to query sessions).
- Use Case: Historically used as a supplemental method to verify mappings or identify users on workstations where server monitoring might miss events. Generally discouraged in modern deployments.
- Pros: Can potentially identify users missed by passive methods.
- Cons: Highly intrusive , generates significant network overhead (especially at scale), often blocked by endpoint firewalls or security software , requires opening Windows firewall ports (e.g., 135, 445, 5985, 5986) on clients, security concerns regarding administrative credentials used for probing, performance impact on the Agent and clients. Less reliable and less scalable than Server Monitoring.
- Agent/Agentless: Available ONLY with the Windows User-ID Agent. Not supported by the PAN-OS Integrated Agent.
Specialized & Agent User-ID Methods
8. Exchange Monitoring
A method for environments with on-premises Microsoft Exchange.
- How it works: The User-ID agent—either the Windows-based agent or the PAN-OS integrated agent—can monitor logs on Microsoft Exchange Servers (specifically IIS logs on Client Access Servers). This allows correlating user email activity (like Outlook Web Access logins) with the client IP addresses accessing the service.
- Mechanism: Requires configuration on the Exchange server to enable necessary logging and permissions for the User-ID component to read those logs (similar to DC monitoring but targeting IIS logs).
- Use Case: Can supplement Domain Controller monitoring, especially for identifying users connecting from non-Windows clients (like macOS using native mail clients or mobile devices) or in scenarios where DC logs might miss certain types of authentication events related to Exchange access. Useful in environments with significant non-Windows client populations accessing on-premises Exchange.
- Requirements: Service account with permissions to read IIS logs on relevant Exchange servers, network connectivity between the User-ID agent and the Exchange servers. Specific IIS logging settings may need to be enabled on the Exchange servers.
- Pros: Provides mappings for certain types of clients/access missed by DC monitoring alone.
- Cons: Less common now with the shift to cloud-based email (Office 365). Only captures users actively interacting with the monitored Exchange components, requires specific Exchange server access/permissions.
- Agent/Agentless: Supported by both the Windows-based User-ID agent and the PAN-OS integrated User-ID agent.
Specialized & Agent User-ID Methods
9. eDirectory Monitoring (Windows Agent Only)
For legacy Novell eDirectory environments.
- How it works: The Windows User-ID Agent can be configured to monitor Novell eDirectory servers for user authentication and session information.
- Mechanism: Uses Novell-specific protocols or interfaces to query the eDirectory server for active user sessions and their associated IP addresses.
- Use Case: For organizations still using Novell eDirectory as their primary directory service instead of Active Directory.
- Cons: Requires the Windows User-ID Agent. Less common in modern networks compared to Active Directory integration.
- Agent/Agentless: Available ONLY with the Windows User-ID Agent. Not supported by the PAN-OS Integrated Agent.
Specialized & Agent User-ID Methods
Agent vs. Agentless User-ID Architectures
Palo Alto Networks offers two main architectures for User-ID collection:
- Windows User-ID Agent: Software installed on one or more dedicated Windows servers. It collects mappings from various sources (DCs, Exchange, Syslog, API, Client Probing, eDirectory, TS Agents) and then distributes them to one or more Palo Alto Networks firewalls.
- PAN-OS Integrated User-ID Agent (Agentless): User-ID functionality built directly into the PAN-OS software running on the firewall itself. The firewall performs collection tasks (Server Monitoring, Syslog, API, GP, Captive Portal) without needing a separate Windows server.
Method Support Comparison
| Method | Windows Agent | PAN-OS Integrated (Agentless) |
|---|---|---|
| Server Monitoring (AD Event Logs) | ✔ (Primary collector/distributor) | ✔ (Firewall connects directly to DCs) |
| Port Mapping (TS Agent) | ✔ (Requires TS Agent on server, reports to main agent) | ✔ (Requires TS Agent on server, reports directly to FW) |
| Client Probing | ✔ (Only with Windows Agent) | ✖ |
| GlobalProtect Authentication | N/A (FW handles directly) | ✔ (FW handles directly) |
| Captive Portal | N/A (FW handles directly) | ✔ (FW handles directly) |
| Syslog Integration | ✔ (Agent listens for Syslog) | ✔ (Firewall listens for Syslog) |
| XML API / REST API | ✔ (Agent listens for API pushes) | ✔ (Firewall listens for API pushes) |
| Exchange Monitoring | ✔ | ✔ |
| eDirectory Monitoring | ✔ (Only with Windows Agent) | ✖ |
Considerations for Choosing
- Scale & Redundancy: The Windows Agent is often preferred for larger environments with multiple DCs and firewalls. A single agent can collect from many DCs and distribute to many firewalls. Multiple agents can be deployed for redundancy.
- Management Simplicity: Agentless may be simpler for smaller environments with fewer DCs and firewalls, as it reduces the number of components to manage.
- Required Features: If Client Probing or eDirectory monitoring is required, the Windows Agent is mandatory. Port Mapping (TS Agent) is often used with the Windows Agent for consistency, but TS Agents can report directly to Agentless firewalls.
- Resource Allocation: The Windows Agent dedicates server resources to collection and processing, freeing up firewall resources. Agentless utilizes firewall resources for collection.
Best Practices & PCNSE Focus
Choosing the Right User-ID Methods
Selecting the appropriate User-ID methods depends on your specific network environment, authentication infrastructure, and user types.
Common Scenario Example
An enterprise network with:
- Domain-joined Windows PCs (internal network)
- Remote users connecting via GlobalProtect VPN
- Guest wireless network
- Citrix servers for application access
- Non-domain macOS clients accessing internal resources
Recommended method combination:
- Server Monitoring: Primary method for Windows PCs on the internal network.
- GlobalProtect: Automatically maps VPN users.
- Captive Portal or XML API: For Guest Wi-Fi. Captive Portal forces authentication. API integration with a WLC or NAC provides mappings upon wireless authentication.
- Port Mapping (TS Agent): Required on Citrix servers for accurate user identification.
- XML API or Syslog Integration: To capture non-domain clients if they authenticate to other systems (e.g., 802.1X on Wi-Fi reported via RADIUS/NAC/Syslog).
General Best Practices
- Use Multiple Sources: Relying on a single method is rarely sufficient for full coverage. Combine methods to map users across different access methods (internal, VPN, wireless, shared desktop, etc.).
- Prioritize Passive Methods: Server Monitoring, GlobalProtect, Captive Portal (Transparent), API, and Syslog are generally preferred as they are less intrusive than Client Probing.
- Address Non-Domain Users: Plan explicitly how to identify users on non-Windows platforms, BYOD, or guest networks (GlobalProtect, Captive Portal, API/Syslog from WLC/NAC).
- Handle Shared IPs: Implement the Terminal Server (TS) Agent with Port Mapping for accurate identification in RDS/Citrix environments.
- Avoid Client Probing (If Possible): Due to its intrusiveness, overhead, and unreliability, avoid Client Probing unless absolutely necessary and other methods fail.
- Validation and Monitoring: Regularly verify mappings using CLI commands ( show user ip-user-mapping all , show user user-ip-mapping all ) and monitor the health of collection methods (Server Monitoring state, agent connectivity, API logs) and the User-ID cache ( show user user-id-agent state ).
Best Practices & PCNSE Focus
Method Accuracy
The "most accurate" method can depend on the context, but generally, methods tied directly to a successful authentication event are considered highly reliable for that specific session:
- Server Monitoring (AD): Highly accurate for domain-joined Windows clients because it directly processes authoritative logon events from the directory server. Mappings are automatically removed on logoff.
- GlobalProtect: Very accurate for VPN users, as the mapping is created directly by the firewall upon successful authentication and session establishment.
- XML API / REST API: Accuracy depends on the source system (e.g., NAC). If the external system is an authoritative source for authentication (like 802.1X via ISE/ClearPass), the mappings pushed via API are typically very accurate and timely.
- Port Mapping (TS Agent): Highly accurate for identifying individual users *within* a shared Terminal Server session, specifically for traffic originating from that server's IP and within the assigned port range.
- Captive Portal: Accurate at the moment of authentication. Reliability over time depends on the session timeout configuration and user re-authentication behavior. Mappings can become stale if the user remains active but doesn't re-authenticate after timeout.
- Syslog Integration: Accuracy is highly variable and depends on the source device's logging, the consistency of the log format, and the correctness of the regex parse profile. More prone to errors or missing events if log formats change.
- Client Probing: Generally considered the least accurate and least reliable method. It's an active query that can fail due to firewalls, permissions, or timing issues, potentially leading to incorrect or missed mappings.
Conclusion on Accuracy: For typical domain environments, Server Monitoring provides the most comprehensive and accurate mapping for domain-joined PCs. However, GlobalProtect and API integrations are equally, if not more, accurate for their specific use cases (VPN and NAC-authenticated users, respectively). A robust User-ID deployment often uses multiple reliable methods together.
Best Practices & PCNSE Focus
Common Gotchas & Troubleshooting Areas
Deploying and maintaining User-ID can encounter several common issues. Be aware of these potential "gotchas" :
- Service Account Permissions: Insufficient permissions (e.g., not being in the "Event Log Readers" group or lacking WMI/WinRM access) for the account used by the User-ID collector (Agent or Agentless) to query Domain Controllers. This is a frequent cause of Server Monitoring failures.
- Firewall Rules: Blocking necessary traffic between the User-ID collector (Agent or Firewall) and the source devices (DCs, Exchange, Syslog senders, API clients, client machines for probing). Ensure required ports (RPC, WMI, WinRM, Syslog, HTTP/S) are allowed.
- DC Log Management: Domain Controller security logs filling up and rolling over too quickly. The User-ID collector needs to process events faster than the logs are overwritten. Adjust DC log size/retention or consider Syslog forwarding from DCs for faster processing.
- Syslog Parse Profile Errors: Incorrect regular expressions in Syslog Parse Profiles lead to the firewall/agent failing to extract username and IP from logs. Small format changes in the source device's logs can break parsing.
- Stale Mappings: User sessions ending without a corresponding logoff event (e.g., hard power off, network disconnect). Mappings linger in the cache until the timeout expires. Configure appropriate timeouts. Server Monitoring captures logoffs, which helps.
- Shared IP Environments: Forgetting or incorrectly configuring the TS Agent in RDS/Citrix environments, resulting in all users on the server being mapped to one identity or being unmapped.
- Captive Portal Issues: Users bypassing the portal (e.g., using non-web protocols before authentication), browser incompatibility, issues with SSL certificates for the portal, or users not re-authenticating after timeout.
- Client Probing Problems: Endpoint firewalls blocking probes, lack of administrative credentials, performance issues on clients or the Agent. (This method has many gotchas, hence it's discouraged).
- Time Synchronization: Time differences between DCs, the User-ID collector, and the firewall can cause events to be processed out of order or mappings to expire prematurely/late. Ensure NTP synchronization.
- User-ID Agent Communication: For Windows Agent deployments, ensure firewalls can connect to the Agent and the Agent can connect to configured collectors (DCs, Syslog sources, etc.).
Best Practices & PCNSE Focus
User-ID for the PCNSE Exam
User-ID is a fundamental feature of the Palo Alto Networks platform and is heavily tested on the PCNSE (and PCNSA) exam. Be prepared to demonstrate a solid understanding of:
- Core User-ID Concepts: Why User-ID is needed (user-based policy, visibility), the goal (IP-to-User mapping), and how group mapping integrates.
-
Major Mapping Methods:
Be able to list, describe, and identify the primary use case for:
- Server Monitoring (especially for Active Directory)
- GlobalProtect Authentication
- Captive Portal
- XML API
- Syslog Integration
-
Specialized Methods:
Understand the specific purpose of:
- Port Mapping (Terminal Server Agent) - CRITICAL for shared IP environments .
- Client Probing - Know it exists, but also know it's typically discouraged and requires the Windows Agent.
- Agent vs. Agentless: Differentiate between the Windows User-ID Agent and the PAN-OS Integrated (Agentless) User-ID. Know which methods require the Windows Agent (Client Probing, eDirectory) and which can be done agentless (Server Monitoring, Syslog, API, GP, CP). Understand the high-level pros/cons of each architecture (scalability, management).
- Requirements: Know the basic requirements for key methods, such as the need for a service account with specific permissions for Server Monitoring.
- Configuration Basics: Be familiar with the steps involved in setting up Server Monitoring, Captive Portal, or Syslog integration (though detailed configuration steps are less common than conceptual understanding).
- Troubleshooting: Understand common failure points (permissions, firewall rules, DC log speed) and key verification commands ( show user ip-user-mapping ).
- Combining Methods: Recognize that multiple methods are often used together for complete coverage across different user types and access scenarios.
User-ID Mapping Methods Quiz
Test your knowledge on the different User-ID mapping methods used by Palo Alto Networks firewalls. Select the best answer for each question.