-
[... Session Info options ...]
Advanced WildFire™ provides detection and prevention of zero-day malware using a combination of dynamic / static analysis and Intelligent Run-time Memory Analysis to detect highly evasive threats and create protections to block malware.
Why it's important for PCNSE: Understand that WildFire's core function is analyzing *unknown* threats using sandboxing and other techniques beyond simple signatures.
The Advanced WildFire Analysis Environment identifies previously unknown malware and generates signatures that Palo Alto Networks NGFWs can use to then detect and block the malware. When a Palo Alto Networks firewall detects an unknown sample, the firewall automatically forwards all supported file types from any application to the WildFire public-cloud service for Advanced WildFire analysis. Based on the properties, behaviors, and activities the sample displays when analyzed and executed in the sandbox, Advanced WildFire determines the sample to be benign, grayware, phishing, or malicious , and then generates signatures to recognize the newly-discovered malware, and makes the latest signatures globally available for retrieval in real-time. All Palo Alto Networks firewalls can then compare incoming samples against these signatures to automatically block the malware first detected by a single firewall.
Why it's important for PCNSE: Know the four possible WildFire verdicts and the overall flow: forward -> analyze -> verdict -> signature -> protect.
This diagram illustrates the basic interaction:
sequenceDiagram
participant UserPC as User PC
participant NGFW as Palo Alto NGFW
participant WFCloud as WildFire Cloud
UserPC->>NGFW: Requests/Downloads File
NGFW->>NGFW: Check local cache/known signatures
alt File is Unknown
NGFW->>WFCloud: Forward Sample for Analysis
activate WFCloud
WFCloud->>WFCloud: Dynamic/Static/ML Analysis
WFCloud-->>NGFW: Analysis Verdict (e.g., Malicious)
deactivate WFCloud
NGFW->>NGFW: Log Submission & Verdict
Note over WFCloud: Generate Signature
WFCloud-->>NGFW: Distribute Signature
NGFW->>NGFW: Install Signature
NGFW-->>UserPC: Block/Allow based on policy + verdict
else File is Known Malicious
NGFW->>NGFW: Apply Security Policy Action (Block)
NGFW-->>UserPC: Block File
else File is Known Benign
NGFW-->>UserPC: Allow File
end
To learn more about Advanced WildFire, or to get started, see the following topics:
The basic WildFire service is included as part of the Palo Alto Networks next generation firewall and does not require an Advanced WildFire or WildFire subscription . With the basic WildFire service, the firewall can forward portable executable (PE) files for analysis, and can retrieve Advanced WildFire signatures only with antivirus and/or Threat Prevention updates which are made available every 24-48 hours.
Why it's important for PCNSE: Know the limitations of the *free* basic service: only PE files forwarded, slow signature updates via Antivirus content. This contrasts with the paid license benefits.
Palo Alto Networks offers several subscription options:
Why it's important for PCNSE: Recognize that the *Advanced* license adds more sophisticated cloud analysis techniques (like runtime memory analysis) for evasive threats and requires PAN-OS 10.0+.
Why it's important for PCNSE: This option is crucial for organizations wanting to integrate WildFire analysis into custom tools or workflows without needing a Palo Alto Networks firewall for forwarding.
Comparing key features based on subscription:
graph TD
A[Subscription Level] --> B(Basic - No License)
A --> C(WildFire License)
A --> D(Advanced WildFire License)
B --> B1[File Types: PE Only]
B --> B2[Updates: Slow - 24-48hr via AV]
B --> B3[Inline ML: No]
B --> B4[API Access: No]
B --> B5[Adv. Cloud Analysis: No]
C --> C1[File Types: Multiple - PE, Office, PDF, etc.]
C --> C2[Updates: Fast - Real-time/5min]
C --> C3[Inline ML: Yes]
C --> C4[API Access: Yes - Limited]
C --> C5[Adv. Cloud Analysis: No]
D --> D1[File Types: Multiple]
D --> D2[Updates: Fast - Real-time/5min]
D --> D3[Inline ML: Yes]
D --> D4[API Access: Yes - Limited]
D --> D5[Adv. Cloud Analysis: Yes - Runtime Mem, etc.]
style B fill:#f9f,stroke:#333,stroke-width:2px
style C fill:#ccf,stroke:#333,stroke-width:2px
style D fill:#9cf,stroke:#333,stroke-width:2px
The standard WildFire subscription unlocks the following features:
Why it's important for PCNSE: Real-time updates drastically reduce the window of exposure to new threats compared to the basic service or older update methods. This is a key benefit of the subscription and a best practice.
Select Device > Dynamic Updates and enable the firewall to get the latest Advanced WildFire signatures in real-time.
This sequence diagram shows how real-time updates work:
sequenceDiagram
participant WFCloud as WildFire Cloud
participant NGFW as Palo Alto NGFW
WFCloud->>WFCloud: Generate New Signature
Note right of WFCloud: Signature available
NGFW->>WFCloud: Check for Updates (Real-time)
WFCloud-->>NGFW: Provide New Signature
NGFW->>NGFW: Install Signature Locally
NGFW->>NGFW: Apply Signature for Future Traffic
If you are running PAN-OS 10.0 or later, it is a best practice to use real-time Advanced WildFire updates instead of scheduling recurring updates.
Select Device > Dynamic Updates to enable the firewall to get the latest Advanced WildFire signatures. Depending on your Advanced WildFire deployment, you can set up one or both of the following signature package updates:
Why it's important for PCNSE: Understand Inline ML provides on-box, real-time ML detection for specific file types (PE, ELF, PS1, etc.), requires a license, PAN-OS 10+, and is configured in the *Antivirus Profile*.
Here's a flowchart for how Inline ML integrates:
flowchart TD
A[File Traffic Seen] --> B{Supported Type?};
B -- No --> F[Process via Standard AV/Sig Checks];
B -- Yes --> C{Inline ML Enabled in AV Profile?};
C -- No --> F;
C -- Yes --> D[Run Inline ML Model on NGFW];
D --> E{Malicious Prediction?};
E -- Yes --> G[Block/Action per AV Profile];
E -- No --> F;
F --> H[Check Known Signatures];
H --> I{Unknown?};
I -- Yes --> J[Forward to WildFire Cloud];
I -- No --> K[Apply Sig Action];
J --> L[Cloud Analysis...];
G --> M[End];
K --> M;
L --> M;
Why it's important for PCNSE: The basic service only handles PE files; the subscription greatly expands the range of potentially malicious files that can be analyzed.
If you have purchased a Advanced WildFire subscription, you must activate the license before you can take advantage of the subscription-only WildFire features.
The Advanced WildFire subscription unlocks the following feature:
Intelligent Run-time Memory Analysis relies on the existing WildFire analysis profile settings and does not require any additional configuration; however, you must have an active Advanced WildFire license . Samples that display or otherwise indicate evasive and/or advanced malware qualities are automatically forwarded to the appropriate analysis environments.
Why it's important for PCNSE: This advanced analysis capability specifically requires the *Advanced* WildFire license.
Samples are all file types and email links submitted for Advanced WildFire analysis from the firewall and the public API. See File Analysis and Email Link Analysis for details on the file types and links that a firewall can submit for Advanced WildFire analysis.
The firewall forwards unknown samples, as well as blocked files that match antivirus signatures,
Why it's important for PCNSE: Know the primary location for configuring *what* gets forwarded to WildFire, and that App-ID enables inspection beyond just web/email.
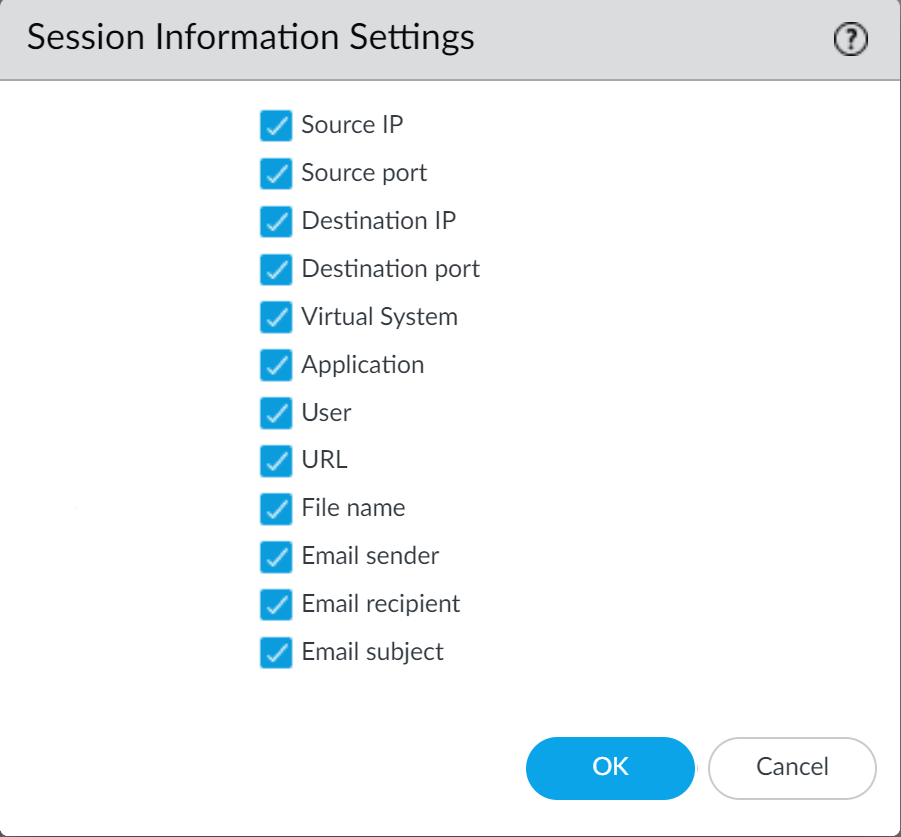
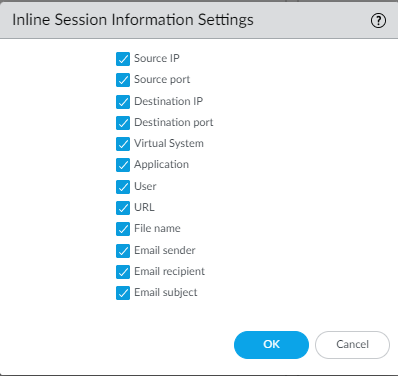
By default, the firewall also forwards information about the session in which an unknown sample was detected. To manage the session information that the firewall forwards, select Device > Setup > WildFire and edit Session Information Settings.
In addition to forwarding unknown and blocked samples for analysis, the firewall also forwards information about the network session for a sample. Palo Alto Networks uses session information to learn more about the context of the suspicious network event, indicators of compromise related to the malware, affected hosts and clients, and applications used to deliver the malware.
Forward of session information is enabled by default; however, you can adjust the default settings and choose what type of session information is forwarded to one of the WildFire cloud options.
Why it's important for PCNSE: Understand that session information forwarding is configurable for privacy/compliance reasons, adjustable under Device > Setup > WildFire.

Advanced WildFire reproduces a variety of analysis environments, including the operating system, to identify malicious behaviors within samples. Depending on the characteristics and features of the sample, multiple analysis environments may be used to determine the nature of the file. Advanced WildFire uses static analysis with machine learning to initially determine if known and variants of known samples are malicious. Based on the initial verdict of the submission, Advanced WildFire sends the unknown samples to analysis environment(s) to inspect the file in greater detail by extracting additional information and indicators from dynamic analysis. If the file has been obfuscated using custom or open source methods, the Advanced WildFire cloud decompresses and decrypts the file in-memory within the dynamic analysis environment before analyzing it using static analysis. During dynamic analysis, Advanced WildFire observes the file as it would behave when executed within client systems and looks for various signs of malicious activities, such as changes to browser security settings, injection of code into other processes, modification of files in operating system folders, or attempts by the sample to access malicious domains. Additionally, PCAPs generated during dynamic analysis in the Advanced WildFire cloud undergo deep inspection and are used to create network activity profiles. Network traffic profiles can detect known malware and previously unknown malware using a one-to-many profile match.
Advanced WildFire can analyze files using the following methods, based on sample characteristics:
Advanced WildFire operates analysis environments that replicate the following operating systems:
The Advanced WildFire public cloud also analyzes files using multiple versions of software to accurately identify malware that target specific versions of client applications. The WildFire private cloud does not support multi-version analysis , and does not analyze application-specific files across multiple versions.
Why it's important for PCNSE: Know this limitation of the private appliance (WF-500) compared to the public cloud.
The Advanced WildFire cloud operates a series of inline cloud ML-based detection engines to analyze PE (portable executable) samples traversing through your network to detect and prevent unknown malware in real-time. This allows the Advanced WildFire cloud service to detect never-before seen malware (that does not have an existing WildFire signature or is detectable through the local Advanced WildFire inline cloud ML detectors) and block it from infecting the client. This includes scenarios where certain types of malware that have been previously unseen in the wild, and are not intercepted by Advanced WildFire Inline ML, can proceed unhindered because the file was not seen recently enough for its signature to be present on the firewall due to signature age-out or signature database capacity limits. Newly defined malicious files will be blocked in subsequent encounters by the firewall as the signature has become part of the current set, however, that occurs after a malicious file is analyzed by the WildFire cloud.
The Advanced WildFire Inline Cloud can hold files from downloading (and potentially spreading within your network) while analyzing these suspicious files for malware in the cloud, in a real-time exchange. As with other malicious content that is analyzed by WildFire, any threat detected by Advanced WildFire Inline Cloud generates a threat signature that is disseminated by Palo Alto Networks to customers through a signature update package to provide a future defense for all Palo Alto Networks customers.
Why it's important for PCNSE: Recognize this feature provides real-time cloud analysis with file holding, offering faster protection than traditional asynchronous forwarding.
Advanced WildFire Inline Cloud operates using a lightweight forwarding mechanism on the firewall to minimize any local performance impact; and to keep up with the latest changes in the threat landscape, cloud inline ML detection models are added and updated seamlessly in the cloud, without requiring content updates or feature release support.
Advanced WildFire Inline Cloud Analysis is enabled and configured through the WildFire Analysis profile and requires PAN-OS 11.1 or later with an active Advanced WildFire license .
Why it's important for PCNSE: Know the license (Advanced WF), minimum OS (11.1+), and configuration location (WF Analysis Profile) for this feature.
The Advanced WildFire inline ML option present in the Antivirus profile enables the firewall dataplane to apply machine learning on PE (portable executable), ELF (executable and linked format), MS Office files, OOXML, Mach-O, and PowerShell and shell scripts in real-time. This layer of antivirus protection complements the Advanced WildFire-based signatures to provide extended coverage for files of which signatures do not already exist. Each inline ML model dynamically detects malicious files of a specific type by evaluating file details, including decoder fields and patterns, to formulate a high probability classification of a file. This protection extends to currently unknown as well as future variants of threats that match characteristics that Palo Alto Networks has identified as malicious. To keep up with the latest changes in the threat landscape, inline ML models are added or updated via content releases. Before you can enable Advanced WildFire inline ML, you must possess an active Advanced WildFire or standard WildFire subscription.
Why it's important for PCNSE: Understand Inline ML provides on-box, real-time analysis for specific file types, is configured in the *Antivirus Profile*, requires a license, and complements cloud analysis.
Inline ML-based protection can also be enabled to detect malicious URLs in real-time as part of your URL Filtering configuration.
Why it's important for PCNSE: Recognize Inline ML extends beyond files to URL analysis within the URL Filtering profile.
When Advanced WildFire analyzes a previously unknown sample in one of the Palo Alto Networks-hosted Advanced WildFire public clouds or a locally-hosted WildFire private cloud, a verdict is produced to identify samples as malicious, unwanted (grayware is considered obtrusive but not malicious), phishing, or benign :
Why it's important for PCNSE: Be able to list and differentiate the four WildFire verdict types. Note the private appliance limitation regarding the 'phishing' verdict.
This flowchart shows the verdict/signature process:
graph TD
A[Sample Received by Cloud] --> B{Analyze Sample};
B --> C{Verdict?};
C -- Malicious --> D[Generate Signature];
C -- Phishing --> E[Generate URL Category Update];
C -- Grayware --> F[Log Optional];
C -- Benign --> G[Log Optional];
D --> H[Distribute Signature];
E --> I[Distribute URL Update];
F --> J[End Analysis];
G --> J;
H --> K[NGFW Downloads/Installs];
I --> K;
K --> L[Future Protection Enabled];
L --> J;
Each Advanced WildFire cloud—global (U.S.) and regional, and the WildFire private cloud—analyzes samples and generates WildFire verdicts independently of the other WildFire cloud options. With the exception of WildFire private cloud verdicts, verdicts are shared globally, enabling Advanced WildFire users to access a worldwide database of threat data.
A Palo Alto Networks firewall configured with a WildFire analysis profile forwards samples for Advanced WildFire analysis based on file type (including email links). Additionally, the firewall decodes files that have been encoded or compressed up to four times (such as files in ZIP format); if the decoded file matches Advanced WildFire Analysis profile criteria, the firewall forwards the decoded file for analysis.
The Advanced WildFire analysis capabilities can also be enabled on the firewall to provide inline antivirus protection. The Advanced WildFire inline ML option present in the Antivirus profiles enables the firewall dataplane to apply machine learning analysis on PE and ELF files as well as PowerShell scripts in real-time. Each inline ML model dynamically detects malicious files of a specific type by evaluating file details, including decoder fields and patterns, to formulate a high probability classification of a file. This protection extends to currently unknown as well as future variants of threats that match characteristics that Palo Alto Networks has identified as malicious. To keep up with the latest changes in the threat landscape, inline ML models are added or updated via content releases. See Advanced WildFire Inline ML for more information.
The Advanced WildFire cloud is also capable of analyzing certain file types which are used as secondary payloads as part of multi-stage PE, APK, and ELF malware packages. Analysis of secondary payloads can provide additional coverage to disrupt sophisticated attacks by advanced threats. These advanced threats operate by executing code which activate additional malicious payloads, including those designed to assist in the circumvention of security measures as well as facilitate proliferation of the primary payload. Advanced WildFire analyzes the multi-stage threats by processing them in static and dynamic analysis environments. Files referenced by multi-stage malware are treated independently during analysis; as a result, verdicts and protections are delivered as soon as they finish for each file. The overall verdict for the multi-stage file is determined based on a threat assessment of malicious content found in all analyzed stages of the attack. Any malicious content discovered during analysis of the multi-stage file immediately marks the file as malicious.
Organizations with safe-handling procedures for malicious content can manually submit password-protected samples using the RAR format through the API or WildFire portal. When the Advanced WildFire cloud receives a sample that has been encrypted using the password infected or virus , the Advanced WildFire cloud decrypts and analyzes the archive file. You can view the verdict and analysis results for the file in the format that it was received, in this case, an archive.
While the firewall can forward all the file types listed below, Advanced WildFire analysis support can vary depending on the Advanced WildFire cloud to which you are submitted samples. Review Advanced WildFire File Type Support to learn more.
A Palo Alto Networks firewall can extract HTTP/HTTPS links contained in SMTP and POP3 email messages and forward the links for WildFire analysis. The firewall only extracts links and associated session information (sender, recipient, and subject) from email messages; it does not receive, store, forward, or view the email message.
WildFire visits submitted links to determine if the corresponding web page hosts any exploits or displays phishing activity. A link that WildFire finds to be malicious or phishing is:
Why it's important for PCNSE: Understand the active nature of email link analysis – WildFire doesn't just check a reputation DB, it visits the site.
Why it's important for PCNSE: Know that malicious/phishing links found by WildFire feed into the PAN-DB URL Filtering categories.
The firewall forwards email links in batches of 100 email links or every two minutes (depending on which limit is hit first). Each batch upload to WildFire counts as one upload toward the upload per-minute capacity for the given firewall Firewall File-Forwarding Capacity by Model. If a link included in an email corresponds to a file download instead of a URL, the firewall forwards the file only if the corresponding file type is enabled for WildFire analysis.
This diagram shows the email link process:
sequenceDiagram
participant MailServer
participant NGFW
participant WFCloud as WildFire Cloud
participant PANDB as PAN-DB
MailServer->>NGFW: Email with Link
NGFW->>NGFW: Policy allows SMTP/POP3
NGFW->>NGFW: Extract HTTP/HTTPS Link
NGFW->>WFCloud: Forward Link for Analysis
activate WFCloud
WFCloud->>WFCloud: Visit Link URL
WFCloud->>WFCloud: Analyze Web Page Content/Behavior
WFCloud-->>NGFW: Verdict (e.g., Phishing)
deactivate WFCloud
alt Verdict is Malicious/Phishing
WFCloud->>PANDB: Update URL Category
NGFW->>NGFW: Log WildFire Submission (with Email Headers if enabled)
else Verdict is Benign/Grayware
NGFW->>NGFW: No Submission Log for Link (by default)
end
To enable the firewall to forward links included in emails for WildFire analysis, see Forward Files for Advanced WildFire Analysis. With a Advanced URL Filtering license, you can also block user access to malicious and phishing sites.
The Advanced WildFire global cloud (U.S.) and regional clouds can analyze URLs, and by extension, email links, to provide standardized verdicts and reports through the WildFire API. By aggregating threat analysis details from all Palo Alto Networks services, including PAN-DB, Advanced WildFire is able to generate a more accurate verdict and provide consistent URL analysis data.
The URL analyzers operating in the Advanced WildFire global cloud processes URL feeds, correlated URL sources (such as email links), NRD (newly registered domain) lists, PAN-DB content, and manually uploaded URLs, to provide all Advanced WildFire clouds with the improved capabilities, without affecting GDPR compliance. After a URL has been processed, you can retrieve the URL analysis report, which includes the verdict, detection reasons with evidence, screenshots, and analysis data generated for the web request. You can also retrieve web page artifacts (downloaded files and screenshots) seen during URL analysis to further investigate anomalous activity.
No additional configuration is necessary to take advantage of this feature, however, if you want to automatically submit email links for analysis (which are now analyzed through this service), you must Forward Files for Advanced WildFire Analysis.
Verdicts that you suspect are either false positives or false negatives can be submitted to the Palo Alto Networks threat team for additional analysis.
By default, the firewall decodes files that have been encoded or compressed up to four times, including files that have been compressed using the ZIP format. The firewall then inspects and enforces policy on the decoded file; if the file is unknown, the firewall forwards the decoded file for WildFire analysis. While the firewall cannot forward complete ZIP archive files for Advanced WildFire analysis, you can submit files directly to the Advanced WildFire public cloud using the WildFire portal or the WildFire API.
Advanced WildFire can discover zero-day malware in web traffic (HTTP/HTTPS), email protocols (SMTP, IMAP, and POP), and FTP traffic and can quickly generate signatures to identify and protect against future infections from the malware it discovers. Advanced WildFire automatically generates a signature based on the malware payload of the sample and tests it for accuracy and safety.
Each Advanced WildFire cloud analyzes samples and generates malware signatures independently of the other Advanced WildFire clouds. With the exception of WildFire private cloud signatures, Advanced WildFire signatures are shared globally, enabling users worldwide to benefit from malware coverage regardless of the location in which the malware was first detected. Because malware evolves rapidly, the signatures that Advanced WildFire generates address multiple variants of the malware.
Why it's important for PCNSE: Understand the global benefit of the public cloud - one detection protects all subscribers quickly. Private cloud signatures remain local unless forwarded.
Firewalls with an active Advanced WildFire license can retrieve the latest Advanced WildFire signatures in real-time, as soon as they become available. If you do not have an Advanced WildFire subscription, signatures are made available within 24-48 hours as part of the antivirus update for firewalls with an active Threat Prevention license.
Why it's important for PCNSE: This directly contrasts the update speed difference between licensed (real-time/fast) and unlicensed (slow via AV updates) WildFire signature delivery.
As soon as the firewall downloads and installs the new signature, the firewall can block the files that contain that malware (or a variant of the malware). Malware signatures do not detect malicious and phishing links; to enforce these links, you must have a PAN-DB URL Filtering license. You can then block user access to malicious and phishing sites.
Why it's important for PCNSE: Clarifies that WildFire *signatures* block files, while blocking malicious *links/URLs* identified by WildFire requires the separate URL Filtering license and profile.
You can set up a Palo Alto Networks firewall to submit unknown samples to one of the Palo Alto Networks-hosted Advanced WildFire public clouds, the U.S. Government cloud, a locally-hosted WildFire private cloud, or enable the firewall to forward certain samples to one of the Advanced WildFire public cloud options and certain samples to a WildFire private cloud:
A Palo Alto Networks firewall can forward unknown files and email links to the Advanced WildFire global cloud (U.S.) or to the Advanced WildFire regional clouds that Palo Alto Networks owns and maintains. Choose the Advanced WildFire public cloud to which you want to submit samples for analysis based on your location and your organization’s needs:
[... List of Public Cloud URLs ...]Each Advanced WildFire cloud—global (U.S.) and regional—analyzes samples and generates malware signatures and verdicts independently of the other WildFire clouds. Advanced WildFire signatures and verdicts are then shared globally, enabling all WildFire users worldwide to benefit from malware coverage regardless of the location in which the malware was first detected. Review Advanced WildFire File Type Support to learn more about the file types that each cloud analyzes.
Why it's important for PCNSE: Key characteristic of public cloud deployments - global intelligence sharing (except for session data specific to the submission).
If you have a WildFire appliance, you can enable a WildFire Hybrid Cloud deployment, where the firewall can forward certain files to a WildFire public cloud, and other files to a WildFire private cloud for local analysis. The WildFire appliance can also be configured to quickly gather verdicts for known samples by querying the public cloud before performing analysis. This allows the WildFire appliance to dedicate analysis resources to samples that are unknown to both your private network and the global WildFire community.
In a Palo Alto Networks private cloud deployment, Palo Alto Networks firewalls forward files to a WildFire appliance on your corporate network that is being used to host a private cloud analysis location.
Why it's important for PCNSE: Understand that the Private Cloud requires a dedicated on-premise WF-500 appliance.
For more information about hybrid cloud forwarding, refer to the WildFire Appliance Administrator’s Guide.
A firewall in a WildFire hybrid cloud deployment can forward certain samples to one of the Palo Alto Networks-hosted WildFire public clouds and other samples to a WildFire private cloud hosted by a WildFire appliance .
Why it's important for PCNSE: Define Hybrid Cloud - selectively forwarding files to either public or private clouds based on policy/profiles.
For more information about hybrid cloud forwarding, refer to the WildFire Appliance Administrator’s Guide.
In addition to the WildFire Global cloud, private cloud, and hybrid cloud deployment options, Palo Alto Networks also provides access to several high-security, FedRAMP-authorized cloud environments for organizations that need to comply with secure cloud operational standards. FedRAMP-authorized clouds are available in two impact levels: High and moderate, with moderate being available in two cloud configurations. The Advanced WildFire Government Cloud complies to the FedRAMP high certification standard, while the Advanced WildFire Government Cloud and WildFire U.S. Government Cloud complies to the FedRAMP moderate certification standard.
The WildFire U.S. Government Cloud (which complies to FedRAMP moderate certification standards) is planned for decommissioning. For all new customers, Palo Alto Networks recommends using the Advanced WildFire Public Sector cloud, which has an enhanced feature set and support for the Advanced WildFire Cloud.
Why it's important for PCNSE: Awareness of the decommissioning status of the older FedRAMP offering.
The FedRAMP moderate clouds (Advanced WildFire Government Cloud and WildFire U.S. Government Cloud) are generally available to Palo Alto Networks customers, however, the Advanced WildFire Government Cloud, which complies to FedRAMP high certification standards, is only available to Federal, Department of Defense, or Approved Defense Industrial Base (DIB) customers.
Due to the sensitive nature of these services, FedRAMP clouds have a specific onboarding process that differs from that of other services. For more information, refer to the specific FedRAMP cloud type:
[... FedRAMP links ...]The FedRAMP clouds listed above cannot be mixed and matched on the same device, nor can they be used concurrently with the Advanced WildFire global or regional clouds. However, any FedRAMP cloud can be used in cooperation with other cloud-based security services (eg. Advanced Threat Prevention, DLP, etc). If you need to incorporate multiple FedRAMP security levels on a single device, you must use separate account IDs. After onboarding is complete, you can reference the FedRAMP cloud URL in your Antivirus security profile and APIs in the same manner as any other Advanced WildFire cloud.
Palo Alto Networks offers Federal, Department of Defense, or Approved Defense Industrial Base (DIB) customers, the Advanced WildFire Government Cloud, a high-security malware analysis platform that conforms to FedRAMP (Federal Risk and Authorization Management Program) High certification standards.
The Advanced WildFire Public Sector Cloud operates as a separate and distinct entity from Commercial or Government Cloud regions — Any privacy information that might be present in samples sent for analysis, such as email addresses, IP addresses, and passive DNS, will not be shared with any other WildFire cloud instance. However, it is still able to leverage threat data generated by the Advanced WildFire public clouds to maximize coverage capability as well as protections and antivirus signatures produced through file analysis.
Why it's important for PCNSE: Key feature of FedRAMP clouds is data isolation – PII/session data stays within that cloud, though threat intelligence is still leveraged globally.
[... Rest of Government Cloud section ...]Palo Alto Networks offers customers the Advanced WildFire Public Sector Cloud, a high-security malware analysis platform that conforms to FedRAMP (Federal Risk and Authorization Management Program) moderate certification standards. The Advanced WildFire Public Sector Cloud replaces the WildFire U.S. Government Cloud.
The Advanced WildFire Public Sector Cloud operates as a separate and distinct entity from Commercial or Government Cloud regions — Any privacy information that might be present in samples sent for analysis, such as email addresses, IP addresses, and passive DNS, will not be shared with any other WildFire cloud instance. However, it is still able to leverage threat data generated by the Advanced WildFire public clouds to maximize coverage capability as well as protections and antivirus signatures produced through file analysis.
Why it's important for PCNSE: Same as above - confirms data isolation for this specific FedRAMP cloud.
[... Rest of Public Sector Cloud section ...]As of July 15, 2024, the Palo Alto Networks WildFire U.S. Government Cloud has been superseded by the Advanced WildFire Government Cloud and Advanced WildFire Public Sector Cloud , which provides access to high-security Advanced WildFire Cloud environments operating a newer codebase with an enhanced feature set. As a result, Palo Alto Networks no longer onboards new customers to the WildFire U.S. Government Cloud . Existing customers can continue to access the WildFire U.S. Government Cloud until the decommission date of November 30, 2024 , at which point, the existing URI will be redirected to the Advanced WildFire Public Sector Cloud.
Why it's important for PCNSE: Extremely critical lifecycle information about this specific service being phased out, including dates and redirection plans.
[... Rest of U.S. Government Cloud section ...]The following table lists the file types that are supported for analysis in the WildFire cloud environments.
For a comprehensive list of specific file types supported by WildFire, refer to Supported File Types (Complete List).
* Static analysis of DMG, PKG, and ZBundle files is only available in the Advanced WildFire Global (U.S.) and Europe Cloud regions, however, static analysis for other Mac OS X files (fat and macho) is supported across all regional clouds. Dynamic analysis for all Mac OS X files is only supported in the Advanced WildFire Global (U.S.) and Europe Cloud regions.
** ZIP files are not directly forwarded to the Advanced Wildfire cloud for analysis. Instead, they are first decoded by the firewall, and files that match the WildFire Analysis profile criteria are separately forwarded for analysis.
Looking for more?
The following table lists the file types supported by WildFire analysis. For files marked Yes in the Forwarding Support column, this includes files that are MIME encoded in web traffic (HTTP/HTTPS) and email protocols (SMTP, IMAP, POP).
The following steps provide a quick workflow to get started with Advanced WildFire™ on the firewall. If you’d like to learn more about Advanced WildFire before getting started, take a look at the Advanced WildFire Overview and review the Advanced WildFire Best Practices.
For information about using the WildFire private cloud or hybrid cloud, refer to the WildFire Appliance administration.
If you are using Advanced WildFire on Prisma Access, familiarize yourself with the product before configuring your WildFire Analysis Security Profile to Forward Files for Advanced WildFire Analysis.
If you are deploying a WildFire private or hybrid cloud, refer to the WildFire Appliance administration.
If the WildFire License is not displayed, select one of the License Management options to activate the license.
Why it's important for PCNSE: Essential first step - many WildFire features depend on an active, appropriate license. Know where to check this (Device > Licenses).
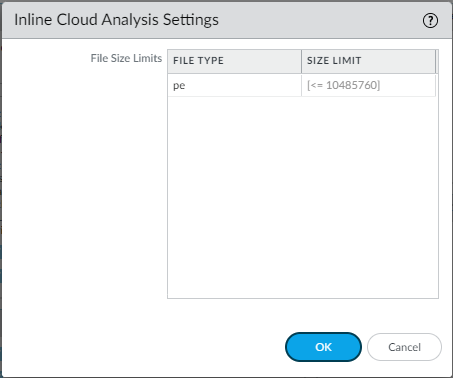
It is a Advanced WildFire Best Practices to set the File Size for PEs to the maximum size limit of 10 MB, and to leave the File Size for all other file types set to the default value.
Why it's important for PCNSE: Know the location (Device > Setup > WildFire) for core settings like selecting the cloud server and file size limits.
This is a recommended Advanced WildFire best practice.
Why it's important for PCNSE: Critical configuration step found under Device > Setup > Content-ID. WildFire cannot analyze threats in encrypted traffic without this.
Why it's important for PCNSE: Know where WildFire Analysis profiles are created/modified.
As a best practice, use the WildFire Analysis default profile to ensure complete coverage for traffic the firewall allows. If you still decide to create a custom WildFire Analysis profile, set the profile to forward Any file type—this enables the firewall to automatically start forwarding newly-supported file types for analysis.
Why it's important for PCNSE: WildFire forwarding only happens if the profile is applied to a Security Policy rule that allows the traffic.
New Advanced WildFire signatures are retrieved in real-time to detect and identify malware. If you are operating PAN-OS 9.1 or earlier, you can receive new signatures every five minutes.
Why it's important for PCNSE: Know where to configure signature update frequency (Device > Dynamic Updates) and that 'Real-time' is the best practice for licensed PAN-OS 10.0+.
Attach the default Antivirus profile to a security policy rule to scan traffic the rules allows based on WildFire antivirus signatures (select Policies > Security and add or a modify the defined Actions for a rule).
Why it's important for PCNSE: Blocking based on WildFire *signatures* requires an Antivirus profile applied to the Security Policy rule.
This option requires a PAN-DB URL Filtering license . Learn more about URL Filtering and how it enables you to control web site access and corporate credential submissions (to prevent phishing attempts) based on URL category.
Why it's important for PCNSE: Blocking malicious *URLs* identified by WildFire requires the separate URL Filtering license and profile applied to the policy.
[... URL Filtering config steps ...]Why it's important for PCNSE: Know where to check if files are actually being submitted (Monitor > Logs > WildFire Submissions) and how enabling benign logging helps verification.
Review and implement Advanced WildFire Best Practices.
The following topics describe deployments and configurations that Palo Alto Networks recommends when you are using WildFire ® hardware or services as part of your network threat detection and prevention solution.
Prisma Access users—Refer to the Prisma Access for product-specific information about the user-interface.
Why it's important for PCNSE: Explicitly calls out real-time updates as a best practice for optimal protection speed.
Why it's important for PCNSE: Critical best practice. Without decrypting and forwarding, threats in SSL/TLS are missed by WildFire. Know the config location.
Why it's important for PCNSE: Recommends using the 'default' profile or setting file types to 'any' in custom profiles for maximum coverage and reducing the chance of missing threats due to misconfiguration.
The following topics describe how to enable Advanced WildFire™ analysis in your network deployment. You can set up Palo Alto Networks firewalls to automatically forward unknown files to the Advanced WildFire public cloud or a WildFire private cloud, and you can also manually submit files for analysis using the Advanced WildFire portal. Samples submitted for analysis receive a verdict of benign, grayware, malicious, or phishing, and a detailed analysis report is generated for each sample.
Configure Palo Alto Networks firewalls to forward unknown files or email links and blocked files that match existing antivirus signatures for analysis. Use the WildFire Analysis profile to define files to forward to one of the Advanced WildFire public cloud options and then attach the profile to a security rule to trigger inspection for zero-day malware.
Why it's important for PCNSE: Reiterates that the profile must be applied to a Security Policy Rule to take effect.
Specify traffic to be forwarded for analysis based on the application in use, the file type detected, links contained in email messages, or the transmission direction of the sample (upload, download, or both). For example, you can set up the firewall to forward Portable Executables (PEs) or any files that users attempt to download during a web-browsing session. In addition to unknown samples, the firewall forwards blocked files that match existing antivirus signatures. This provides Palo Alto Networks a valuable source of threat intelligence based on malware variants that signatures successfully prevented but has not been seen before.
If you are using a WildFire appliance to host a WildFire private cloud, you can extend WildFire analysis resources to a WildFire hybrid cloud, by configuring the firewall to continue to forward sensitive files to your WildFire private cloud for local analysis, and forward less sensitive or unsupported file types to the WildFire public cloud. For more information about using and configuring the WildFire appliance, refer to the WildFire Appliance Administration.
Before you begin:
Select Device > Setup > WildFire and edit the General Settings based on your WildFire cloud deployment (public, government, private, or hybrid).
[... Cloud URL configuration ...]Continue editing General Settings ( Device > Setup >WildFire ).
local-PDF-analysis
.
Why it's important for PCNSE: Understand the components of a WildFire Analysis profile rule: Application, File Type, and Direction are key criteria for deciding what to forward.
Traffic allowed by the security policy rule is evaluated against the attached WildFire analysis profile; the firewalls forwards traffic matched to the profile for WildFire analysis.
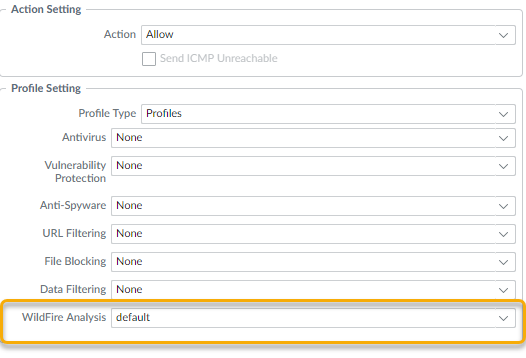
Why it's important for PCNSE: Know exactly where in the Security Policy rule (Actions tab -> Profile Setting) the WildFire Analysis profile is applied.
This is a recommended best practice.
Enable the firewall to forward decrypted SSL traffic for Advanced WildFire analysis. Traffic that the firewall decrypts is evaluated against security policy rules; if it matches the WildFire analysis profile attached to the security rule, the decrypted traffic is forwarded for analysis before the firewall re-encrypts it. Only a super user can enable this option.
Why it's important for PCNSE: Notes the administrative privilege required for this setting.
Forwarding decrypted SSL traffic for analysis is a Advanced WildFire Best Practices.
Why it's important for PCNSE: Know the exact GUI path (Device > Setup > Content-ID) to enable forwarding of decrypted content.
Why it's important for PCNSE: Know the configuration path differs slightly when using virtual systems.
Palo Alto Networks Advanced WildFire operates a series of cloud-based ML detection engines that provide inline analysis of PE (portable executable) files traversing your network to detect and prevent advanced malware in real-time. As with other malicious content that WildFire detects, threats detected by Advanced WildFire Inline Cloud Analysis generate a signature that is then disseminated to customers through an update package, providing a future defense for all Palo Alto Networks customers.
The cloud-based engines enable the detection of never-before-seen malware (e.g., a Palo Alto Networks zero-day - malware previously unseen in the wild or by Palo Alto Networks) and block it from entering your environment. Advanced WildFire Inline Cloud Analysis uses a lightweight forwarding mechanism on the firewall to minimize performance impact. The cloud-based ML models are updated seamlessly, to address the ever-changing threat landscape without requiring content updates or feature release support.
Advanced WildFire Inline Cloud Analysis is enabled and configured through the WildFire Analysis profile and requires PAN-OS 11.1 or later with an active Advanced WildFire license.
Why it's important for PCNSE: Know the OS version (11.1+), license (Advanced WF), and configuration profile (WildFire Analysis) for this feature.
This step is not necessary if you already installed the current version of the device certificate on your firewall.
To verify subscriptions for which you have currently-active licenses, select Device > Licenses and verify that the appropriate licenses are available and have not expired.
If your current WildFire license has expired and you are installing an Advanced WildFire license, you must first remove the WildFire license from the NGFW before installing the Advanced WildFire license.
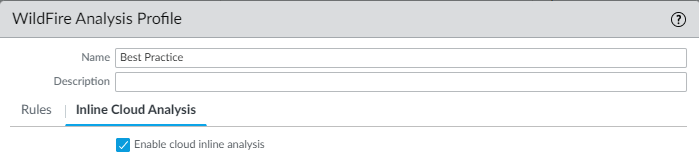
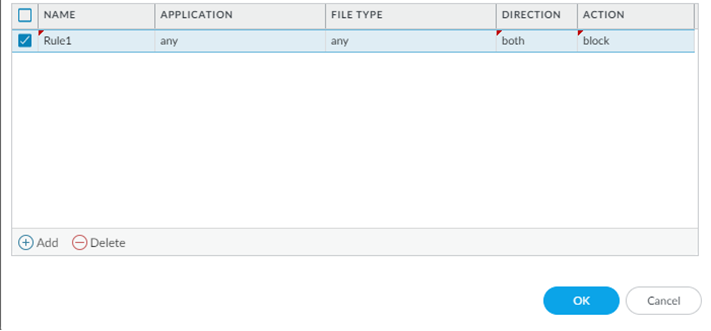
Why it's important for PCNSE: Note the current file type limitation (PE only) for Inline Cloud Analysis.
Palo Alto Networks recommends setting the action to block for optimal security.
Advanced WildFire Inline Cloud Analysis provides a fast WildFire verdict, however, a full report for a malicious sample is only available after the sample undergoes full dynamic analysis, which can take up to 30 minutes.
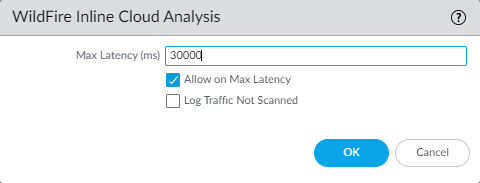
Allow HTTP partial response is a global setting and affects HTTP-based data transfers which use the RANGE header, which may cause service anomalies for certain applications. After you disable Allow HTTP partial response , validate the operation of your business-critical applications.
You can prevent malicious variants of portable executables and PowerShell scripts from entering your network in real-time using machine learning (ML) based analytics on the firewall dataplane. By utilizing WildFire® Cloud analysis technology on your security platform, Advanced WildFire Inline ML dynamically detects malicious files of a specific type by evaluating various file details, including decoder fields and patterns, to formulate a high probability classification of a file. This protection extends to currently unknown as well as future variants of threats that match characteristics that Palo Alto Networks identified as malicious. Advanced WildFire inline ML complements your existing Antivirus profile protection configuration. Additionally, you can specify file hash exceptions to exclude any false-positives that you encounter, which enables you to create more granular rules in your profiles to support your specific security needs.
To enable Advanced WildFire Inline ML, you must have an active Advanced WildFire or WildFire subscription, create (or modify) an Antivirus (or WildFire and Antivirus for Prisma Access) security profile to configure and enable the service, and then attach the Antivirus profile to a security policy rule .
Why it's important for PCNSE: Clearly states that Inline ML is configured within the *Antivirus Profile* (not WildFire Analysis Profile) and must be applied via a Security Policy Rule.
Advanced WildFire Inline ML is not currently supported on the VM-50 or VM50L virtual appliance.
Why it's important for PCNSE: Platform limitations are common exam topics.
To enable your WildFire inline ML configuration, attach the Antivirus profile configured with the inline ML settings to a security policy rule.
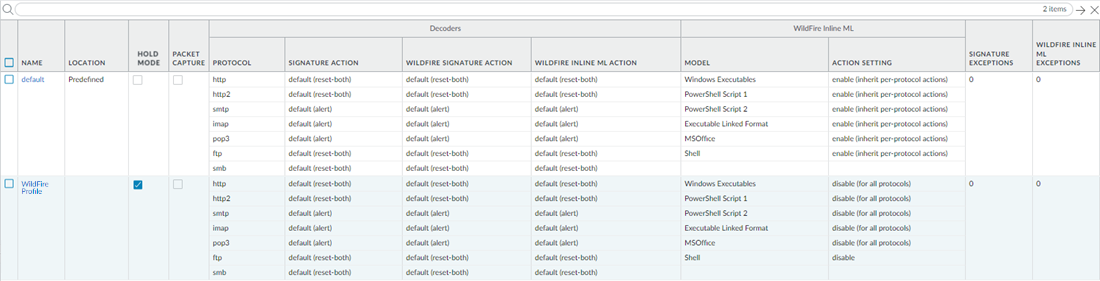
To bypass Advanced WildFire Inline ML, you must set the Action Setting to disable (for all protocols) on a per-model basis or create a WildFire Inline ML file exception using the partial hash. Do not configure your antivirus profile with signature exceptions based off of WildFire Inline ML Threat IDs. This will cause the firewall to block all traffic from your network to the IP address.
WildFire inline ML is not currently supported on the VM-50 or VM50L virtual appliance.
Verify that you have a WildFire subscription. To verify which subscriptions that you currently have licenses for, select Device > Licenses and verify that the appropriate licenses display and have not expired.
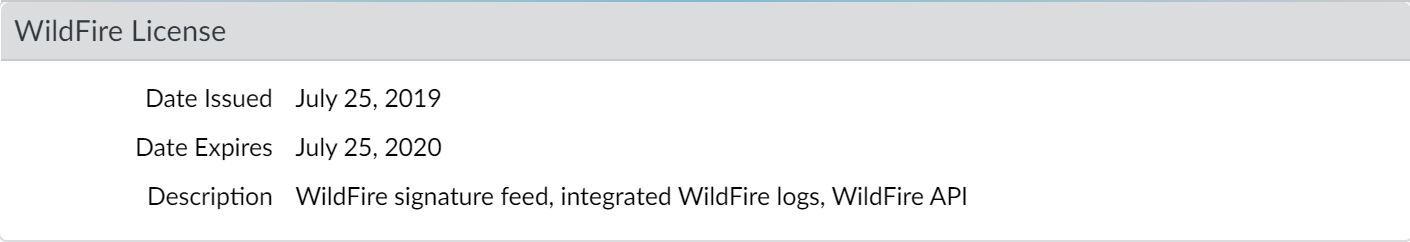
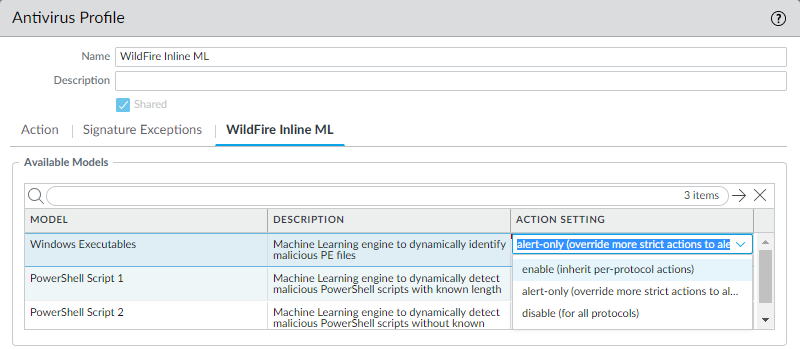
The following action settings are available:
Why it's important for PCNSE: Know the configuration location (Antivirus Profile > WildFire Inline ML tab) and the available actions (enable, alert-only, disable).
If your WildFire Analysis security profile is configured to forward the filetypes analyzed using WildFire inline ML, false-positives are automatically corrected as they are received. If you continue to see ml-virus alerts for files that have been classified as benign by WildFire Analysis, please contact Palo Alto Networks Support.

Why it's important for PCNSE: Know how to handle Inline ML false positives using hash-based exceptions within the Antivirus Profile.
Use the following CLI command on the firewall to view the connection status.
show mlav cloud-status
If you are unable to connect to the Inline ML cloud service, verify that the following domain is not being blocked:
ml.service.paloaltonetworks.com
.
Why it's important for PCNSE: Know the CLI command to verify connectivity specifically for the Inline ML service.
To view information about files that have been detected using WildFire Inline ML, examine the threat logs ( Monitor > Logs > Threat , then select the log type from the list). Files that have been analyzed using WildFire inline ML are labeled with the threat type ml-virus :
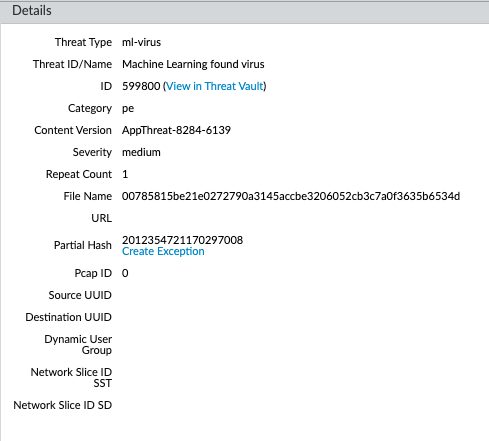
Why it's important for PCNSE: Recognize the specific Threat Log subtype (`ml-virus`) associated with Inline ML detections.
You can configure the NGFW to hold the transfer of a sample while the real-time signature cloud performs a signature lookup . When the lookup is completed, the file is released to the requesting client (or blocked), based on your organization's security policy for specific WildFire verdicts, preventing the initial transfer of known malware. You can configure hold mode on a per antivirus profile basis and apply a global setting for the signature lookup timeout and the associated action.
Why it's important for PCNSE: Understand the concept of "hold mode" - pausing file delivery during a real-time signature check for immediate blocking if known malicious.
This feature is available to all users with an active WildFire or Advanced WildFire license running PAN-OS 11.0.2 or later.
Why it's important for PCNSE: Know the license and OS requirements for this specific hold mode feature.
Even when the firewall is configured to use real-time signatures, supplemental signature packages are still installed on a regular basis. This provides an up-to-date signature source when you experience connectivity issues, as well as a speed benefit, where signatures are available locally.
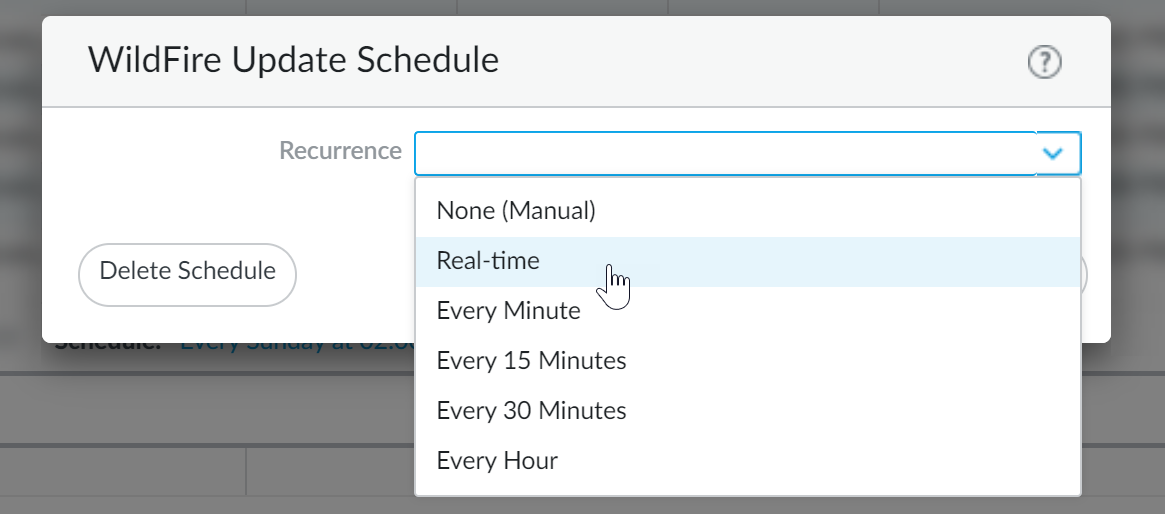
You must enable hold mode globally before you enable hold mode for WildFire real-time signature lookups on a per-Antivirus profile basis.
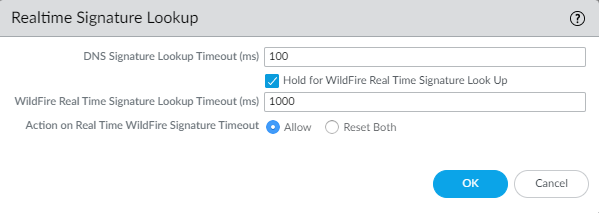
Palo Alto Networks recommends using the default value of 1000ms unless you experience repeated timeouts during testing.
Why it's important for PCNSE: Know the global configuration location (Device > Setup > Content-ID) for enabling hold mode and setting the timeout/action.
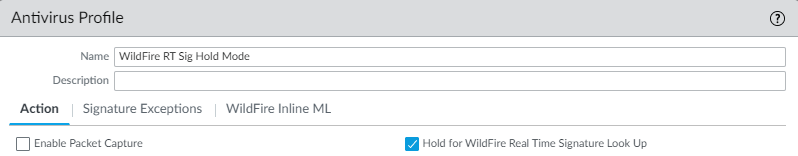
Why it's important for PCNSE: Know that hold mode is activated *per-profile* within the Antivirus profile's Action tab, after being enabled globally.
Here's a sequence diagram illustrating Hold Mode:
sequenceDiagram
participant UserPC as User PC
participant NGFW as Palo Alto NGFW
participant WFCloud as WildFire Cloud (Real-time Sig Service)
UserPC->>NGFW: Request File Download
NGFW->>NGFW: File matches Policy/Profile (Hold Mode Enabled in AV Profile)
NGFW->>UserPC: Hold File Transfer (temporarily pause)
activate NGFW
NGFW->>WFCloud: Real-time Signature Lookup (File Hash/Metadata)
activate WFCloud
WFCloud-->>NGFW: Signature Verdict (Malicious / Benign / Unknown / Timeout)
deactivate WFCloud
alt Verdict is Malicious
NGFW->>NGFW: Apply AV Profile Action (e.g., Block)
NGFW-->>UserPC: Reset Connection / Block Page
else Verdict is Benign or Unknown or Timeout Reached
NGFW->>NGFW: Apply Timeout Action (Allow / Reset)
alt Timeout Action is Allow
NGFW-->>UserPC: Release Held File Transfer
else Timeout Action is Reset
NGFW-->>UserPC: Reset Connection
end
Note over NGFW: If file was unknown, forward full sample for standard analysis
end
deactivate NGFW
You can specify the cloud content Fully Qualified Domain Name (FQDN) used by the NGFW to handle Advanced WildFire service requests. The default FQDN connects to
hawkeye.services-edge.paloaltonetworks.com
and then resolves to the closest cloud services server. You can override the automatic server selection by specifying a regional cloud content server that best meets your data residency and performance requirements.
Keep in mind, the cloud content FQDN is a globally used resource and affects how other services that rely on this connection sends traffic payloads.
Why it's important for PCNSE: Understand this setting impacts more than just WildFire and changing it requires careful consideration of all cloud-connected services.
In some cases, the cloud content FQDN might not fully support the functionality of a particular Palo Alto Networks product in certain regions. Verify that the product is fully supported before changing the cloud content FQDN.
Depending on which services you use, the cloud content FQDN facilitates analysis service requests, including traffic payloads, which sends data to the servers in the selected region. If you specify a content cloud FQDN that is outside of your region (for example, if you are in the EU region but you specify the APAC region FQDN), you may be in violation of your organization’s privacy and legal regulations. Please refer to the specific product documentation for information about how the cloud content FQDN is used by your Palo Alto Networks products.
Why it's important for PCNSE: Be aware of the data residency and compliance implications when selecting a non-default Content Cloud FQDN.
If you are experience service connectivity issues, verify that the configured cloud content FQDN is not being blocked.
Test your deployment using malware test samples, and also verify that the firewall is correctly forwarding files for WildFire analysis.
Palo Alto Networks provides sample malware files that you can use to test an Advanced WildFire configuration. Take the following steps to download the malware sample file, verify that the file is forwarded for Advanced WildFire analysis, and view the analysis results.
Before downloading an encrypted WildFire sample malware file, you must temporarily disable the
*.wildfire.paloaltonetworks.com
entry from the exclude from decryption list on the
Device > Certificate Management > SSL Decryption Exclusion
page, otherwise the sample will not download correctly. After conducting a verification test, be sure to re-enable the
*.wildfire.paloaltonetworks.com
entry on the SSL decryption exclusion page.
The test file is named
wildfire-test-file_type-file.exe
and each test file has a unique SHA-256 hash value.
You can also use the WildFire API to retrieve a malware test file. See the WildFire API Reference for details.
Please wait at least five minutes for analysis results to be displayed for the file on the WildFire Submissions page. The verdict for the test file will always display as malware.
Why it's important for PCNSE: Know how to test the WildFire setup using the provided test files and where to look for the results (WildFire Submissions Log).
After the firewall is set up to Forward Files for Advanced WildFire Analysis, use the following options to verify the connection between the firewall and the Advanced WildFire public or WildFire private cloud, and to monitor file forwarding.
Several of the options to verify that a firewall is forwarding samples for analysis are CLI commands; for details on getting started with and using the CLI, refer to the PAN-OS CLI Quick Start Guide.
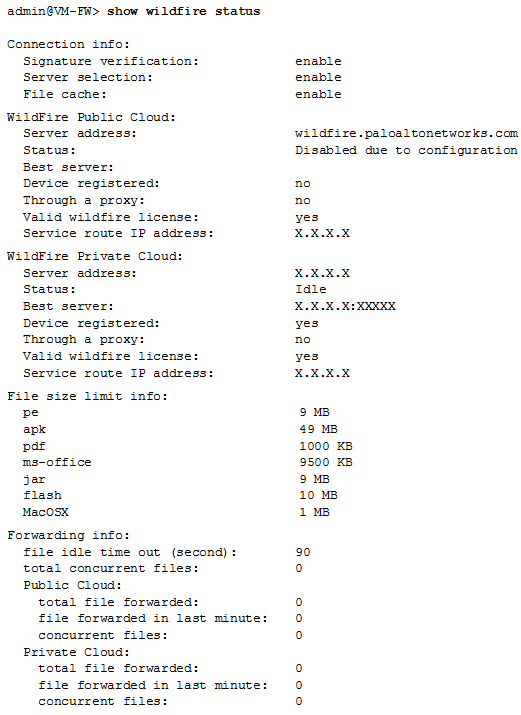
Use the
show wildfire status
command to:
Why it's important for PCNSE: Know this fundamental CLI command for checking WildFire connectivity and basic forwarding statistics.
The following example shows the
show wildfire status
output for a firewall in a WildFire private cloud deployment:
To view forwarding information for only the Advanced WildFire public cloud or WildFire private cloud, use the following commands:
show wildfire status channel public
show wildfire status channel private
Use this option to confirm that email links are being forwarded for analysis, since only email links that receive a malicious or phishing verdict are logged as WildFire Submissions entries on the firewall, even if logging for benign and grayware samples is enabled. This is due to the sheer number of WildFire Submissions entries that would be logged for benign email links.
Use the
show wildfire statistics
command to confirm the file types being forwarded to the Advanced WildFire public or WildFire private cloud:
Why it's important for PCNSE: Know this CLI command to see detailed counts per file type being forwarded, useful for verifying profile rules.
This option can be helpful when troubleshooting to:
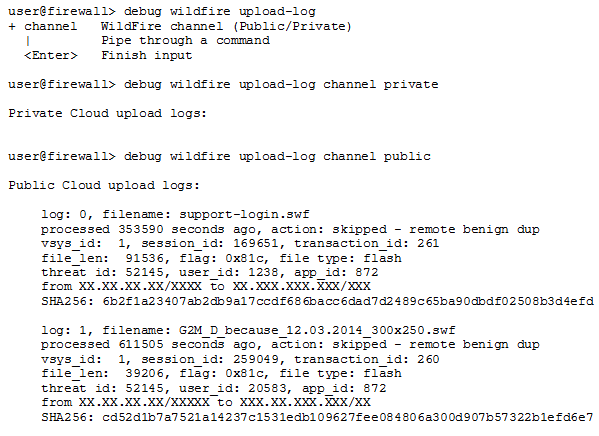
Execute the following CLI commands on the firewall to view samples the firewall has forwarded for analysis:
debug wildfire upload-log
.
debug wildfire upload-log channel public
.
debug wildfire upload-log channel private
.
Why it's important for PCNSE: Know this `debug` command is used to see logs of files *currently* being uploaded or queued, before a verdict appears in the GUI logs. Crucial for troubleshooting forwarding issues.
The following example shows the output for the three commands listed above when issued on a firewall in an Advanced WildFire public cloud deployment:
Using the firewall web interface, select Monitor > Logs > WildFire Submissions . All files forwarded by a firewall to the Advanced WildFire public or WildFire private cloud for analysis are logged on the WildFire Submissions page.
Why it's important for PCNSE: Know the primary GUI location to view completed analysis results and verdicts from WildFire.
Unique samples sent to the Advanced WildFire cloud for analysis can be deleted at the discretion of the user. This allows users who are subject to data protection policies, including those who must comply with GDPR, to permanently dispose of sample data based on their organization’s retention policies. Sample data includes session / upload data and the sample file itself.
Only files that are unique to your environment can be deleted. If files are found to be available in other public or private feeds, only the session and upload data for a given account is removed.
Why it's important for PCNSE: Understand the limitation of sample removal - only truly unique files submitted by the user can be fully deleted from the cloud backend.
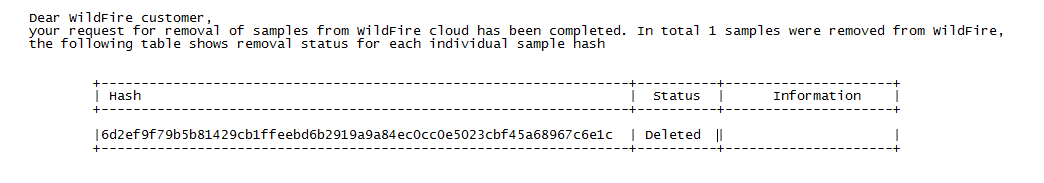
Samples that do not exist or are not unique to your environment will return statuses of Not found and Rejected , respectively.
File-forwarding capacity is the maximum rate per minute at which each Palo Alto Networks firewall model can submit files to the Advanced WildFire® cloud for analysis. If the firewall reaches the per-minute limit, it queues any remaining samples.
The Reserved Drive Space in the following table represents the amount of drive space on the firewall that is reserved for queuing files. If the firewall reaches the drive space limit, it cancels forwarding of new files to WildFire until more space in the queue is available.
The speed at which the firewall can forward files to the Advanced WildFire cloud also depends on the bandwidth of the upload link from the firewall.
Why it's important for PCNSE: Be aware that forwarding limits exist per firewall model and can impact analysis if capacity is exceeded. Specific numbers are less likely, but the concept is important.
You can Monitor Activity on the firewall, with the WildFire portal, Strata Cloud Manager, or with the WildFire API.
For each sample WildFire analyzes, WildFire categorizes the sample as malware, phishing, grayware, or benign and details sample information and behavior in the WildFire analysis report. WildFire analysis reports can be found on the firewall that submitted the sample and the WildFire cloud (public or private) that analyzed the sample, or can be retrieved using the WildFire API:
Access Advanced WildFire analysis reports on the firewall, the WildFire portal, and the WildFire API.
Advanced WildFire analysis reports display detailed sample information, as well as information on targeted users, email header information (if enabled), the application that delivered the file, and all URLs involved in the command-and-control activity of the file. Advanced WildFire reports contain some or all of the information described in the following table based on the session information configured on the firewall that forwarded the file and depending on the observed behavior for the file.
When viewing an Advanced WildFire report for a file that was manually uploaded to the WildFire portal or by using the WildFire API, the report will not show session information because the traffic did not traverse the firewall. For example, the report would not show the Attacker/Source and Victim/Destination.
A WildFire submissions log is an automatically generated, time-stamped file that provides an audit trail to track events when a Palo Alto Networks network security platform forwards samples (files and emails links) to the WildFire cloud for analysis based on WildFire Analysis profile settings (Objects > Security Profiles > WildFire Analysis). WildFire Submissions log entries are generated for each sample forwarded to the WildFire cloud that has completed static and/or dynamic analysis of the sample. WildFire Submissions log entries include the Action taken on the sample (allow or block), the WildFire verdict for the submitted sample as determined through WildFire analysis, the severity level of the sample, and other details.
By default, WildFire submissions logs are created for Benign and Malicious samples; while Grayware and Benign samples generate no logs. You can change the WildFire submission log settings to include Grayware and Benign samples as well as additional session information contained in email links.
Enable the following options for WildFire Submissions logs
Logging for benign and grayware samples is disabled by default. Email links that receive benign or grayware verdicts are not logged.
Why it's important for PCNSE: Know that logging benign/grayware files (not links) is optional and configured under Device > Setup > WildFire. Useful for troubleshooting forwarding.
Use the following steps to include email header information—email sender, recipient(s), and subject—in WildFire logs and reports.
Session information is forwarded to the WildFire cloud along with the sample, and used to generate the WildFire analysis report. Neither the firewall nor the WildFire cloud receive, store, or view actual email contents.
Session information can help you to quickly track down and remediate threats detected in email attachments or links, including how to identify recipients who have downloaded or accessed malicious content.
Why it's important for PCNSE: Understand that including email header info is optional (privacy) and configured under Device > Setup > WildFire > Session Information Settings.
You can configure a Palo Alto Networks firewall to send an alert when WildFire identifies a malicious or phishing sample. You can configure alerts for benign and grayware files as well, but not for benign and grayware email links. This example describes how to configure an email alert; however, you could also configure log forwarding to set up alerts to be delivered as syslog messages, SNMP traps, or Panorama alerts.
In this example you will set up email logs for when a sample is determined to be malicious. You can also enable Benign and Grayware logs to be forwarded, which will produce more activity if you are testing.
The firewall does not forward WildFire logs for blocked files to an email account.
WildFire-Log-Forwarding
. Optionally, you can add a
Description
of the log forwarding profile.
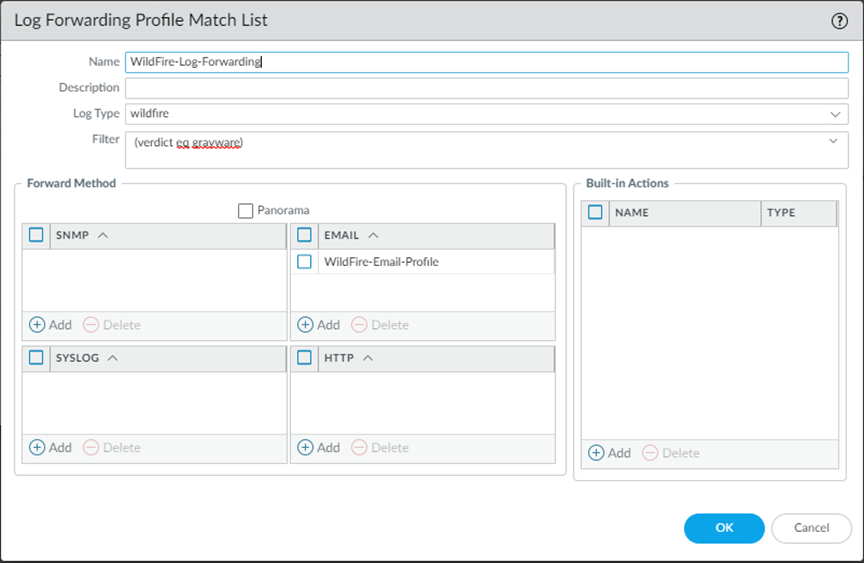
(verdict eq malicious)
query.
WildFire-Email-Profile
), and click
OK
to save the match list updates.
Why it's important for PCNSE: Know how to use Log Forwarding Profiles (Objects > Log Forwarding) to trigger actions based on WildFire log attributes like the verdict. Understand the filter syntax.
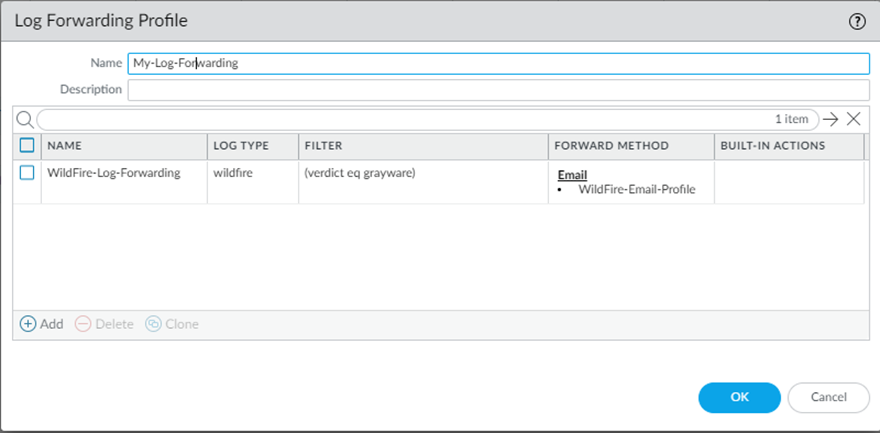
The WildFire Analysis profile defines the traffic that the firewall forwards for Advanced WildFire analysis. To set up a WildFire analysis profile and attach it to a security policy rule, see Forward Files for Advanced WildFire Analysis.
Why it's important for PCNSE: Understand that the Log Forwarding profile is applied within the Security Policy rule's Actions tab, similar to security profiles, to trigger the forwarding for matched traffic.
WildFire logs contain information on samples (files and email links) uploaded to the WildFire cloud for analysis. It includes artifacts, which are properties, activities, or behaviors associated with the logged event, such as the application type or the IP address of an attacker as well as WildFire-specific qualities, such as high-level analysis results including categorization of the sample as malware, phishing, grayware, or benign and details sample information. Reviewing the WildFire Submissions logs can also indicate whether a user in your networks downloaded a suspicious file. The WildFire analysis report displays detailed sample information, as well as information on targeted users, email header information (if enabled), the application that delivered the file, and all URLs involved in the command-and-control activity of the file. It informs you if the file is malicious, if it modified registry keys, read/wrote into files, created new files, opened network communication channels, caused application crashes, spawned processes, downloaded files, or exhibited other malicious behavior.
WildFire logs are displayed as WildFire submissions logs on NGFW firewalls, while on Cloud Management platforms, you must first configure log forwarding to upload relevant logs to Strata Logging Service, which will then show the WildFire logs as threat logs (type WildFire).
Samples that firewalls submit for WildFire analysis are displayed as entries in the WildFire Submissions log on the firewall web interface. For each WildFire entry, you can open an expanded log view which displays log details and the WildFire analysis report for the sample.
Mozilla Firefox users: The WildFire Analysis Report displays correctly only in Firefox v54 and earlier releases. If you experience issues viewing the report, consider using a different web browser such as Google Chrome. Alternatively, you can download and open the PDF version or view the report through the WildFire portal.
Why it's important for PCNSE: Know the primary GUI location for viewing WildFire results and understand the meaning of the Verdict, Action, and Severity columns.
The values for the following severity levels are determined by a combination of verdict and action values.
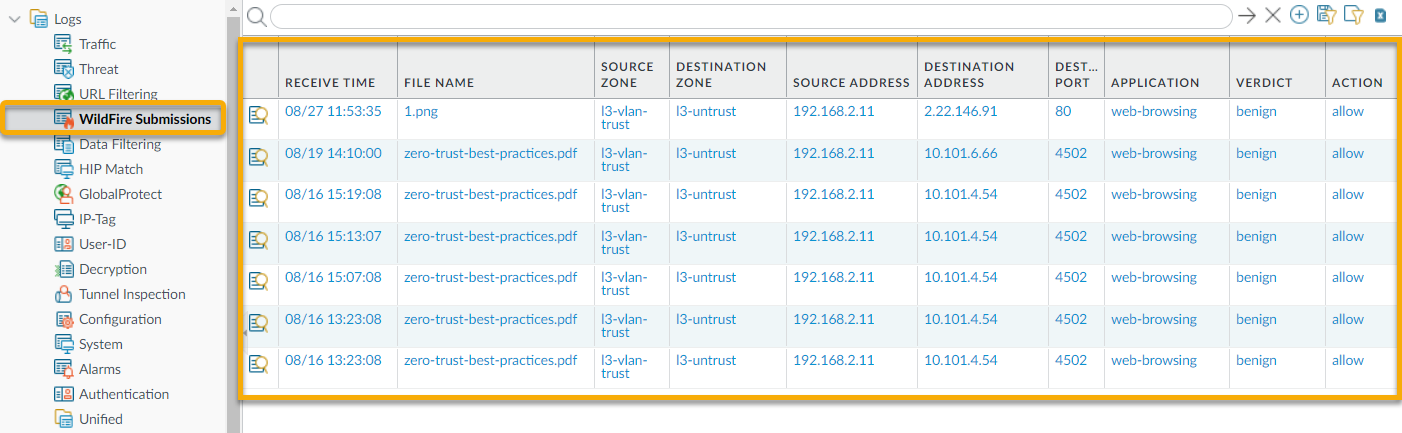
The detailed log view displays Log Info and the WildFire Analysis Report for the entry. If the firewall has packet captures (PCAPs) enabled, the sample PCAPs are also displayed.
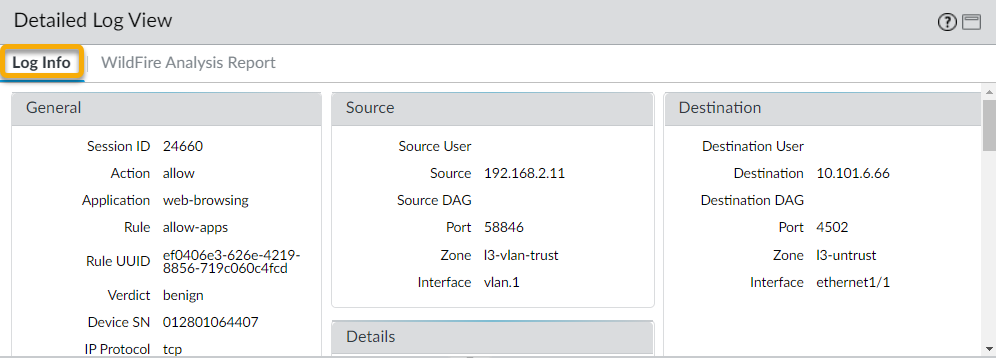
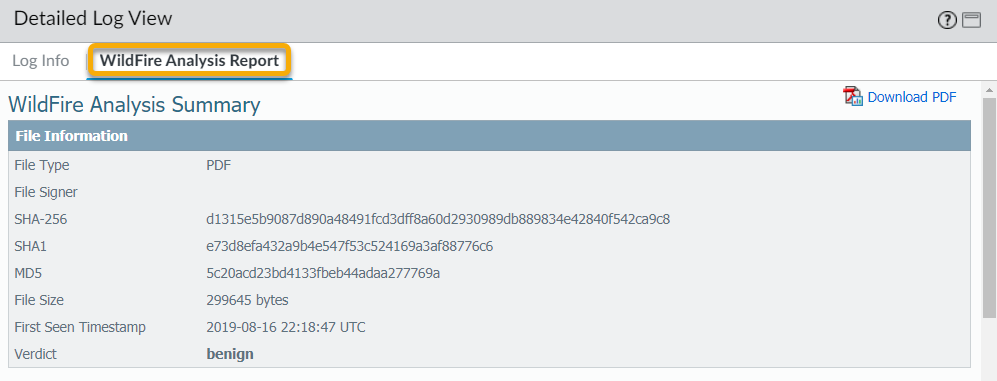
For all samples, the WildFire analysis report displays file and session details. For malware samples, the WildFire analysis report is extended to include details on the file attributes and behavior that indicated the file was malicious.
Log in to the Palo Alto Networks WildFire portal using your Palo Alto Networks support credentials or your WildFire account. The portal opens to display the dashboard, which lists summary report information for all of the firewalls associated with the specific WildFire subscription or support account. For each device listed, the portal displays statistics for the number of malware samples that have been detected, benign samples that have been analyzed, and the number of pending files that are waiting to be analyzed. Your WildFire portal account displays data for all samples submitted by firewalls on your network that are connected to the WildFire public cloud, as well as data for samples manually submitted to the portal. Additionally, if you have enabled a WildFire appliance to forward malware to the WildFire public cloud for signature generation and distribution, reports for those malware samples can also be accessed on the portal.
See the following sections for details on using the WildFire portal to monitor WildFire activity:
This section describes the settings that can be customized for a WildFire cloud account, such as time zone and email notifications for each firewall connected to the account. You can also delete firewall logs stored in the cloud.
Select a time zone from the Set Time Zone drop-down and Update Time Zone to save the change.
The time stamp that appears on WildFire analysis reports is based on the time zone configured for the WildFire cloud account.
The WildFire portal does not send alerts for blocked files that the firewall forwarded for WildFire analysis.
WildFire portal accounts are created by a super user (the registered owner of a Palo Alto Networks device) to give additional users the ability to log in to the WildFire cloud and view device data for which they are granted access by the super user. A WildFire user can be a user associated with an existing Palo Alto Networks account or a user not associated with a Palo Alto Networks support account, to whom you can allow access to just the WildFire public clouds and a specific set of firewall data.
WildFire portal users can view data for all firewalls associated with the support account.
The only restriction when adding a user is that the email address cannot be from a free web-based email account (such as Gmail, Hotmail, and Yahoo). If an email address is entered for a domain that is not supported, a pop-up warning is displayed.
Select the firewall(s) by serial number for which you want to grant access and fill out the optional account details.
Users with an existing support account will receive an email with a list of the firewalls that are now available for WildFire report viewing. If the user does not have a support account, the portal sends an email with instructions on how to access the portal and how to set a new password.
The new user can now log in to the WildFire cloud and view WildFire reports for the firewalls to which they have been granted access. Users can also configure automatic email alerts for these devices in order to receive alerts on files analyzed. They can choose to receive reports on malicious and/or benign files.
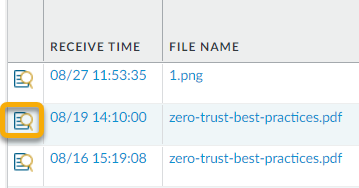
The Wildfire portal displays reports for samples that are submitted from firewalls, manually uploaded, or uploaded using the WildFire API. Select Reports to display the latest reports for samples analyzed by the WildFire cloud. For each sample listed, the report entry shows the date and time the sample was received by the cloud, the serial number of the firewall that submitted the file, the file name or URL, and the verdict delivered by WildFire (benign, grayware, malware, or phishing).
Use the search option to search for reports based on the file name or the sample hash value. You can also narrow the results displayed by viewing only reports for samples submitted by a specific Source (view only results submitted manually or by a specific firewall) or for samples that received a specific WildFire Verdict (any, benign, malware, grayware, phishing, or pending).
To view an individual report from the portal, click the Reports icon to the left of the report name. To save the detailed report, click the Download as PDF button on the upper right of the report page. For details on WildFire analysis reports, see WildFire Analysis Reports—Close Up.
The following shows a list of sample files submitted by a specific firewall:
