What is WildFire?
WildFire® is Palo Alto Networks' cloud-based (or on-premise appliance-based) advanced threat analysis service. Its primary role is to identify and prevent unknown, zero-day threats that traditional signature-based security mechanisms might miss. These threats include sophisticated malware, exploits targeting vulnerabilities, command-and-control (C2) activity, and phishing attempts embedded in files or links.
Traditional security often relies on recognizing known bad patterns (signatures). WildFire complements this by taking unknown files and web links, analyzing them in a controlled sandbox environment using multiple techniques, and then generating a verdict (e.g., benign, malware, phishing). If a threat is identified, WildFire automatically creates new protections (signatures and other threat intelligence) that are distributed globally to subscribed Palo Alto Networks firewalls and other security products, typically within minutes.
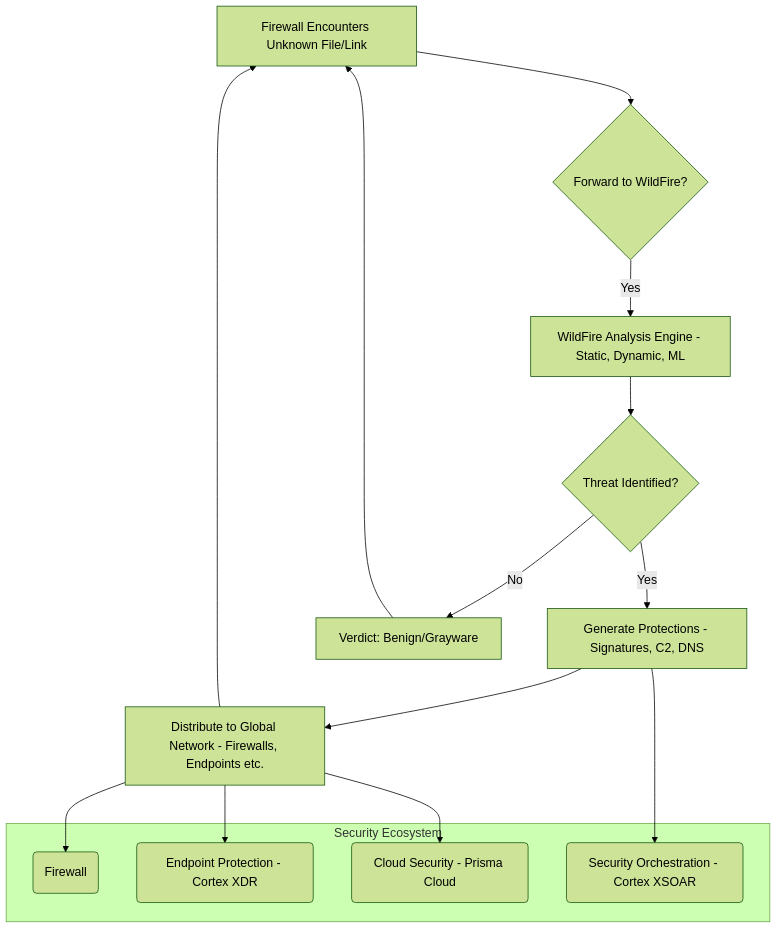
High-level overview of WildFire's role in the threat detection and prevention lifecycle.
By analyzing unknown threats, WildFire helps organizations stay ahead of attackers who constantly evolve their tactics. It provides a critical layer of defense against targeted attacks and emerging malware campaigns.
Threats Detected & Analyzed Content
WildFire is designed to detect a wide array of cyber threats by analyzing various file types and activities. Its multi-faceted analysis approach allows it to uncover threats that might otherwise go unnoticed.
What types of files and activities are analyzed by WildFire?
WildFire analyzes a broad range of file types commonly used in attacks, as well as suspicious web links and network activities. Key categories include:
- Executable Files: Windows PE (Portable Executable) files like
.exe,.dll,.sys. Also, macOS executables (Mach-O) and Linux ELF files. - Productivity Documents: Microsoft Office files (Word, Excel, PowerPoint -
.doc,.docx,.xls,.xlsx,.ppt,.pptx, etc.), including those with macros. - Adobe PDF Files:
.pdfdocuments, often used to carry exploits or malicious links. - Archive Files:
.zip,.rar,.7z,.tar,.gz. WildFire attempts to extract and analyze contents (unless password-protected with an unknown password). - Script Files: JavaScript (
.js), VBScript (.vbs), PowerShell (.ps1), Python (.py), and others. - Android APK Files:
.apkfiles for Android mobile devices. - Java Archives:
.jarfiles. - Flash Files:
.swf(less common now but still supported). - Email Links and Attachments: WildFire can analyze URLs and attachments from emails submitted via SMTP or email security gateways.
- Web Content: URLs are analyzed for phishing, drive-by downloads, and connections to malicious infrastructure.
Beyond file types, WildFire observes activities during dynamic analysis (sandboxing), such as:
- Network connections (C2 callbacks, data exfiltration attempts).
- File system modifications (dropping files, encrypting data).
- Registry changes (persistence mechanisms).
- Process behavior (injection, evasion techniques).
- API calls and system interactions.
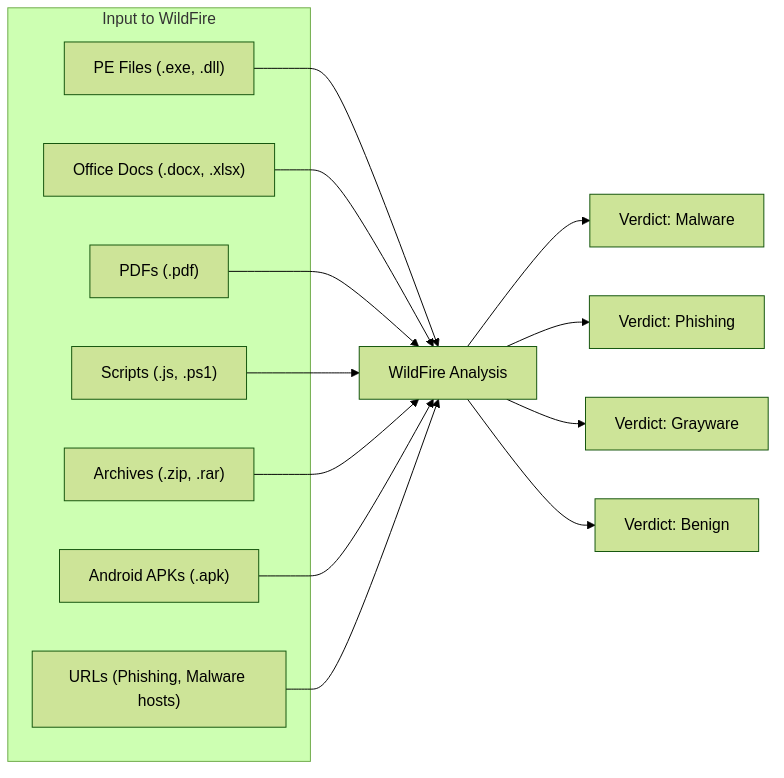
Common file types and URLs analyzed by WildFire.
Submission Triggers & Protocols
File submission to WildFire is not arbitrary; it's triggered by specific conditions and occurs over defined protocols when a Palo Alto Networks firewall (or other integrated product) encounters an unknown file or link.
How does file submission to WildFire occur?
The process generally involves these steps:
- Policy Match: Traffic passes through the firewall and matches a Security Policy rule that has an
Allowaction. - WildFire Analysis Profile: This Security Policy rule must have an attached WildFire Analysis Profile. This profile defines *what* to submit (file types, applications, direction).
- Unknown Verdict Check: The firewall checks its local cache and the WildFire cloud/appliance for a pre-existing verdict for the file's hash or URL.
- Submission Criteria: If the verdict is unknown AND the file type, application (e.g., web-browsing, smtp, smb), and traffic direction (upload, download, both) match the WildFire Analysis Profile settings, the firewall forwards a copy of the file or the URL to the configured WildFire service (public cloud or private appliance).
Which traffic types support WildFire submission?
WildFire submission is supported across various common application protocols where files are typically transferred. These include, but are not limited to:
- HTTP/HTTPS: Web downloads and uploads. SSL Decryption (Forward Proxy) is crucial for HTTPS visibility.
- SMTP/SMTPS, IMAP/IMAPS, POP3/POP3S: Email attachments.
- SMB/CIFS: File sharing over Windows networks.
- FTP/FTPS: File transfers.
The firewall identifies files based on their content (true file type identification) rather than just file extensions, making it more robust against evasion.
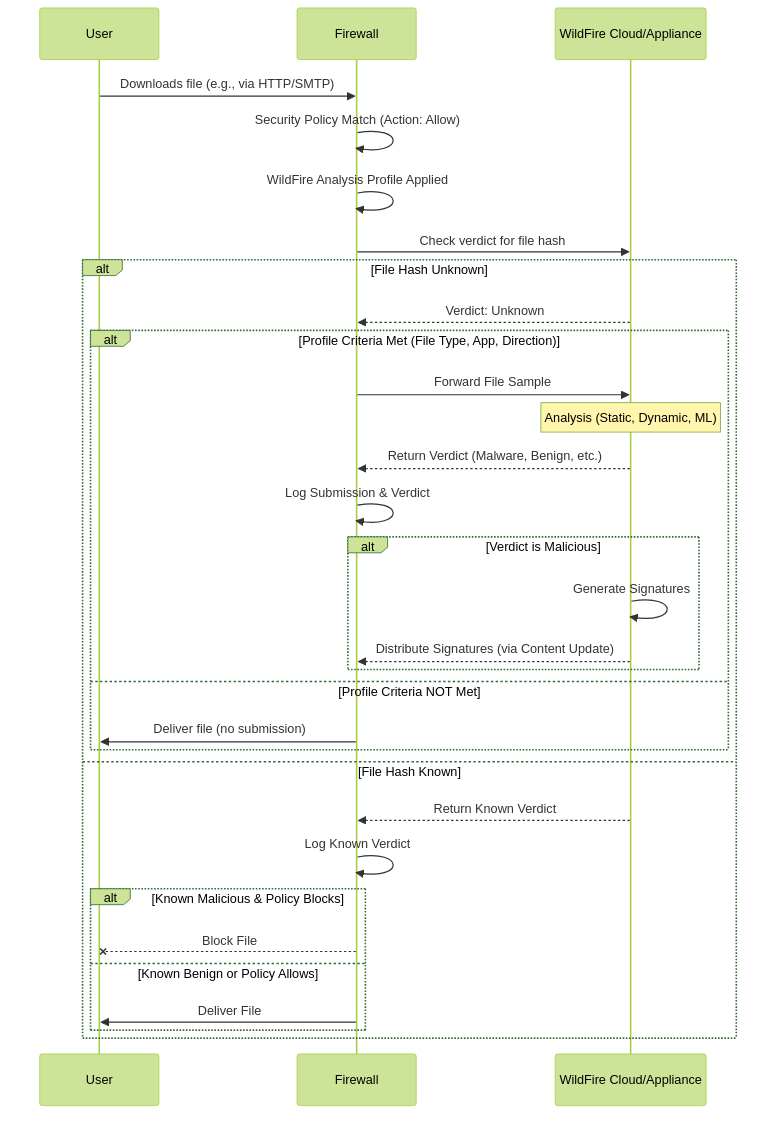
WildFire file submission sequence.
WildFire Deployment Options
Palo Alto Networks offers flexible WildFire deployment options to suit different organizational needs regarding data privacy, performance, and management overhead.
What's the difference between public cloud, private cloud, and on-prem appliances?
-
Public WildFire Cloud:
- How it works: Unknown files are submitted to a global network of Palo Alto Networks-managed WildFire cloud services. Regional clouds (Americas, Europe, Asia, etc.) are available to help with data residency and latency.
- Pros: No on-premise hardware to manage, scalable, benefits from global threat intelligence rapidly, cost-effective for many.
- Cons: Files leave the organization's network, which may be a concern for highly sensitive data or strict data sovereignty regulations.
-
Private WildFire Cloud (WF-500 / WF-500B Appliance or VM-Series in WildFire Analysis Mode):
- How it works: An organization deploys a dedicated WildFire appliance (physical WF-500/WF-500B or virtual VM-Series configured for analysis) within their own datacenter. Unknown files are sent to this on-premise appliance for analysis.
- Pros: Files do not leave the organization's control, addressing data privacy and sovereignty concerns. Potentially lower latency for analysis for internal users if geographically closer than public cloud.
- Cons: Requires purchasing, deploying, and managing the appliance (including updates, capacity planning). Does not directly benefit from the global intelligence seen by the public cloud in real-time unless configured in a hybrid setup. The appliance has finite analysis capacity.
-
Hybrid WildFire Cloud:
- How it works: Combines an on-premise private WildFire appliance with the public WildFire cloud. Typically, organizations might send most files to their private appliance and can optionally forward certain file types (e.g., PE files, or files not deemed overly sensitive) or samples that the private cloud cannot analyze to the public cloud for broader analysis or to contribute to the global threat intelligence network. It can also receive signature updates generated from the global cloud.
- Pros: Balances privacy with access to broader threat intelligence. Offers flexibility.
- Cons: More complex to configure and manage than a single option.
When would I use each option?
- Public Cloud: Default choice for most organizations unless specific data privacy, sovereignty, or regulatory requirements prevent files from leaving the network. Offers the most comprehensive and up-to-date threat intelligence.
- Private Cloud: Organizations with strict data confidentiality policies (e.g., government, healthcare, finance) or data residency laws that forbid data transfer outside national borders. Also for environments with no or limited internet access for file submission.
- Hybrid Cloud: Organizations that need on-premise analysis for most files due to privacy but want to leverage the global cloud for specific file types, for enhanced detection efficacy, or to contribute samples and receive global protections faster.
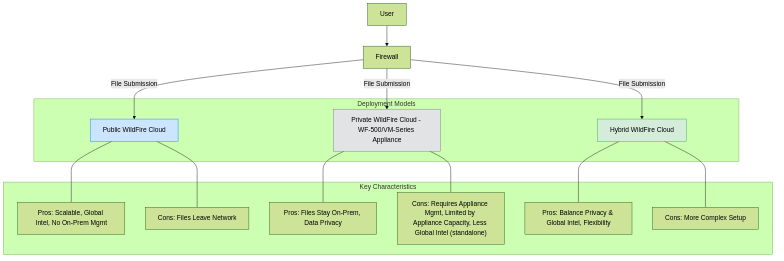
Comparison of WildFire Deployment Options.
WildFire Analysis & Detection Workflow
Once a file is submitted to WildFire, it undergoes a sophisticated multi-stage analysis process to determine if it's malicious.
How does WildFire determine if something is malicious? What engines are used?
WildFire employs several analysis techniques in a pipeline:
-
Static Analysis:
- Examines the file without executing it.
- Looks for known malicious signatures, suspicious file structures, embedded scripts, packer identification, metadata anomalies, and code patterns.
- Fast, but can be evaded by polymorphic or heavily obfuscated malware.
- Engines: Antivirus engines, file format parsers, heuristic scanners.
-
Dynamic Analysis (Sandboxing):
- The file is executed in a secure, instrumented virtual environment (sandbox) that mimics actual operating systems (Windows, macOS, Linux, Android).
- WildFire observes the file's behavior: network connections it attempts, files it creates/modifies, registry changes, processes it spawns, API calls, memory usage, etc.
- Effective against zero-day threats and evasive malware that only reveal malicious behavior upon execution.
- Engines: Custom-built hypervisors and sandboxing technology with advanced evasion detection (e.g., detecting sandbox awareness).
-
Machine Learning (ML):
- Uses algorithms trained on vast datasets of known benign and malicious files.
- Identifies subtle patterns and characteristics indicative of malware that may not be caught by traditional signatures or simple behavioral rules.
- Can be applied both pre-execution (on static features) and post-execution (on behavioral data).
- Helps in detecting new malware variants and previously unseen threats.
- Engines: Proprietary ML models developed by Palo Alto Networks.
-
Bare Metal Analysis (Advanced WildFire):
- For highly evasive threats that can detect virtualization, Advanced WildFire offers analysis on actual physical hardware (bare metal).
- This makes it extremely difficult for malware to realize it's being analyzed.
The results from these engines are correlated to reach a final verdict. If malicious activity is confirmed, WildFire generates signatures and threat intelligence.
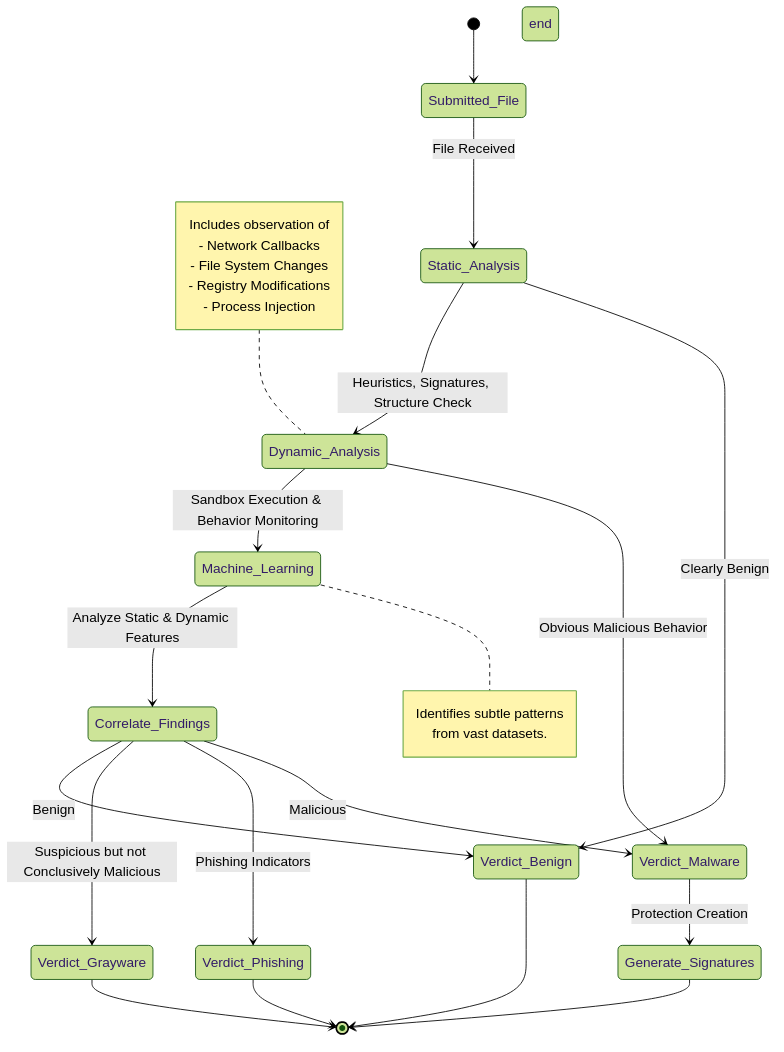
WildFire Analysis Pipeline State Diagram.
WildFire Verdicts & Speed
WildFire provides timely verdicts to enable rapid response to threats. Understanding the types of verdicts and typical turnaround times is important.
What are the typical turnaround times for initial and final verdicts?
WildFire aims for rapid analysis. Turnaround times can vary based on file complexity, current load on the WildFire cloud/appliance, and the analysis techniques required.
- Initial Verdicts (from Static Analysis & ML on static features): Often available within seconds to a few minutes. If a file is quickly identified as known-bad or known-good, or if static analysis flags it as high-confidence malware, a verdict can be very fast.
- Final Verdicts (often requiring Dynamic Analysis): Typically available within 5 to 15 minutes. Some highly complex or evasive samples might take longer. The goal is to provide comprehensive analysis quickly. Palo Alto Networks often quotes "new protections in as little as 5 minutes."
The firewall can be configured with session hold settings. For example, it can hold the first few packets of a download while waiting for a quick verdict from WildFire, potentially blocking the entire file transfer if a malicious verdict is returned rapidly.
WildFire Verdict Types:
WildFire assigns one of the following verdicts to analyzed samples:- Malware: The file or link exhibits confirmed malicious behavior (e.g., ransomware, trojan, spyware, C2 communication). Protections are generated.
- Phishing: The URL is identified as a phishing site attempting to steal credentials or sensitive information. DNS and URL Filtering signatures are generated.
- Grayware: The file exhibits suspicious or undesirable behavior but is not definitively malicious. This could include adware, potentially unwanted programs (PUPs), or software with aggressive data collection. Organizations can choose how to handle grayware (allow, alert, or block).
- Benign: The file or link is deemed safe and does not exhibit any malicious or noteworthy suspicious behavior.
It's important to review Grayware verdicts, as what one organization considers acceptable, another might want to block.
Sharing Results with Firewalls
Once WildFire analyzes a sample and generates a verdict (especially a malicious one), this intelligence needs to be disseminated to firewalls and other security components to provide protection.
How does a firewall get verdict updates or signatures from WildFire?
There are several mechanisms:
- Real-time Verdict Lookups: When a firewall encounters an unknown file, it first queries the WildFire cloud/appliance for an existing verdict for that file's hash. This is a fast, real-time check.
-
Content Updates (Dynamic Updates):
- For newly discovered malware or phishing sites, WildFire automatically generates various types of signatures:
- Antivirus Signatures: To detect and block known malicious files.
- DNS Signatures: To identify and block queries to malicious domains (e.g., C2 servers, phishing sites).
- URL Filtering Signatures (PAN-DB): Malicious URLs are added to the PAN-DB URL filtering database.
- Anti-Spyware Signatures: For C2 communications and other spyware-related activity.
- These new signatures are packaged into Content Updates (also known as Dynamic Updates).
- Subscribed firewalls regularly download these Content Updates (e.g., every 15 mins, hourly, daily, depending on configuration and license). The Advanced WildFire license allows for near real-time signature updates, often within minutes of verdict.
- For newly discovered malware or phishing sites, WildFire automatically generates various types of signatures:
-
WildFire Signature Feed (Advanced WildFire):
- With an Advanced WildFire license, firewalls can receive WildFire signatures via a specialized feed that provides updates much more frequently than standard content updates, often within 5-minute intervals or even faster. This significantly reduces the window of exposure to newly discovered threats.
Is there a delay or batch process?
- Verdict for submitting firewall: The firewall that submitted the sample typically receives the verdict directly and relatively quickly once analysis is complete.
- Global propagation via Content Updates: There is a short processing and distribution time for newly generated signatures to be included in Content Updates and made available globally. Standard content updates are typically batched and released at regular intervals (e.g., daily for base AV, more frequently for WildFire-specific updates).
- Advanced WildFire Signature Streaming: This aims to minimize delay, providing signature updates in near real-time (minutes).
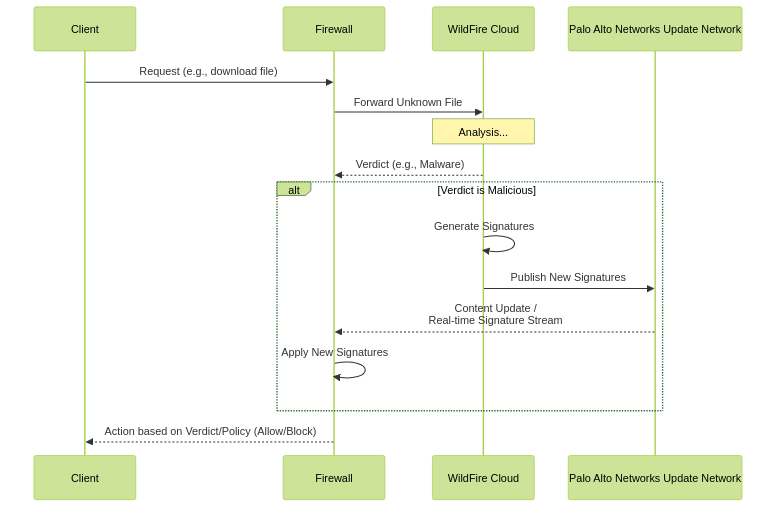
WildFire verdict and signature distribution flow.
Testing or Simulating WildFire Submissions
It's important to verify that WildFire submissions are working correctly in your environment. You can do this by using benign test files or observing logs for actual unknown file submissions.
Can I generate benign test files (like EICAR) to validate WildFire behavior?
Yes, Palo Alto Networks provides methods to test WildFire functionality:
-
WildFire Test File:
Palo Alto Networks provides a specific benign PE (Portable Executable) file designed to test the WildFire submission mechanism. When this file is downloaded through a firewall configured for WildFire, it should be submitted, and WildFire will return a "benign" verdict for it. This confirms the submission path and basic analysis is working.
You can typically find this test file by searching "WildFire test file" on the Palo Alto Networks support portal or community forums.
Unlike EICAR which is detected by Antivirus, the WildFire test file is specifically for testing the WildFire *submission and analysis* process, not basic AV detection.
- Generating a Custom Test File: You could technically create a unique, harmless file (e.g., a text file renamed to .exe or a simple compiled benign executable) that WildFire has never seen before. If your WildFire Analysis Profile is set to forward that file type, it should be submitted. However, using the official Palo Alto Networks WildFire test file is generally preferred as it's designed for this purpose.
-
Checking Logs:
Monitor the
Monitor > Logs > WildFire Submissionslog on the firewall. Successful submissions of the test file (or any other unknown files matching your profile) will appear here with details like filename, session ID, verdict, etc.
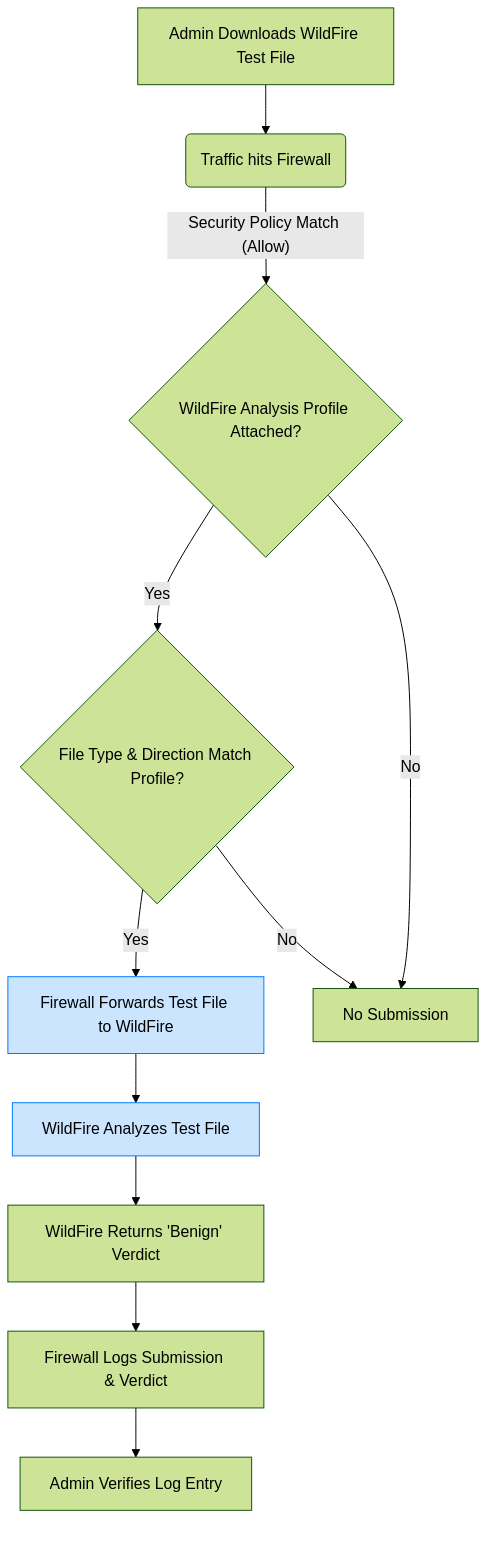
Flowchart for testing WildFire submission with a test file.
Troubleshooting WildFire Submissions
If you suspect WildFire submissions are failing, there are several common areas to investigate and tools to help debug.
What are common reasons submissions don’t reach WildFire?
- Licensing: A valid WildFire subscription is required and must be active on the firewall.
- Connectivity:
- The firewall must be able to resolve the FQDN of the WildFire cloud (e.g.,
wildfire.paloaltonetworks.comor regional FQDNs) via DNS. - The firewall needs network reachability to the WildFire cloud service IPs/ports (typically HTTPS over TCP port 443). Check routing, Security Policies allowing egress traffic to WildFire services, and any intermediate network devices.
- For private WildFire appliances, ensure connectivity from the firewall to the appliance's IP address and port.
- The firewall must be able to resolve the FQDN of the WildFire cloud (e.g.,
- WildFire Analysis Profile Configuration:
- The profile might not be configured to forward the specific file type, application, or direction of traffic.
- The file size might exceed the maximum configured in the profile or the WildFire service limits.
- Security Policy Configuration:
- The WildFire Analysis Profile must be attached to a Security Policy rule with an
Action = Allow. Files in denied sessions are not submitted. - The traffic might be matching a different Security Policy rule that doesn't have a WildFire profile attached.
- The WildFire Analysis Profile must be attached to a Security Policy rule with an
- SSL Decryption Not Enabled: This is a very common issue. If files are transferred over HTTPS, SSL Forward Proxy Decryption must be enabled for the relevant traffic. Without decryption, the firewall cannot see the file to submit it.
- Content Updates Not Current: While not directly a submission failure, outdated content can mean the firewall isn't aware of the latest WildFire cloud FQDNs or IPs.
- WildFire Cloud/Appliance Issues: Rarely, there might be temporary issues with the WildFire service itself. Check the Palo Alto Networks status page.
- Device Certificate: Ensure the firewall's device certificate is valid and trusted for communication with the WildFire cloud.
- Service Route Configuration: If specific service routes are used, ensure they correctly route WildFire traffic through the intended interface.
Which CLI or GUI tools can help debug WildFire submission?
- GUI - Monitor Tab:
Monitor > Logs > WildFire Submissions: This is the primary log to check if files are being submitted, their status, and verdicts. Look for successful submissions, failures, or missing entries.Monitor > Logs > Traffic: Check if sessions are matching the correct Security Policy rule with the WildFire profile.Monitor > Logs > System: May contain logs related to WildFire connectivity or service issues.
- GUI - Device Tab:
Device > Setup > Services > WildFire: Verify the WildFire cloud region or private appliance IP is correctly configured.Device > Licenses: Check WildFire license status.Device > Support > WildFire Test(or similar path depending on PAN-OS version): Some versions have a built-in test option.
- CLI Commands:
show wildfire status: Displays the status of the WildFire connection, configured cloud/appliance, statistics on submissions, etc.show wildfire statistics: Provides detailed counters for submitted files, verdicts, errors.test wildfire registration: Tests connectivity and registration with the WildFire cloud.test dns-proxy dns-resolve hostname wildfire.paloaltonetworks.com(or relevant regional FQDN): Tests DNS resolution for the WildFire service.show session all filter C2S-Wildfire-file-uploading(or similar, specific PBF tags might exist if enabled): Can help identify active submission sessions.debug device-server reset GCS_CLIENT_CERTIFICATE: (Use with caution, under guidance) Can help if there are certificate-related issues with cloud connectivity.show counter global | match wildfire: Shows various global counters related to WildFire.- Packet captures (
tcpdumpor GUI captures) filtered for traffic to/from WildFire cloud IPs can also be very useful.
show wildfire status. The WildFire Submissions log is crucial.
Introduction to User-ID
User-ID is a Palo Alto Networks PAN-OS feature that enables administrators to gain visibility into network traffic based on user and group identity, rather than just IP addresses. This allows for more granular security policies, improved threat analysis, and more meaningful logging and reporting.
In modern networks, users often have dynamic IP addresses (DHCP) or multiple devices, and IP addresses can be shared (e.g., Terminal Servers, Citrix). Relying solely on IP addresses for security policy and monitoring is insufficient. User-ID addresses this challenge by mapping IP addresses to usernames.
Core Benefits of User-ID:
- User-Based Policies: Create Security, QoS, Decryption, and other policies based on individual users or Active Directory (or other directory service) groups. For example, allow access to specific applications only for the "Engineering" group.
- Enhanced Visibility & Reporting: Logs and reports show usernames associated with traffic, making it easier to understand user activity and investigate incidents.
- Granular Threat Prevention: Apply specific threat prevention profiles (Antivirus, Anti-Spyware, Vulnerability Protection) based on user roles or risk levels.
- Simplified Forensics: When a threat is detected, quickly identify the affected user(s) instead of just an IP address.
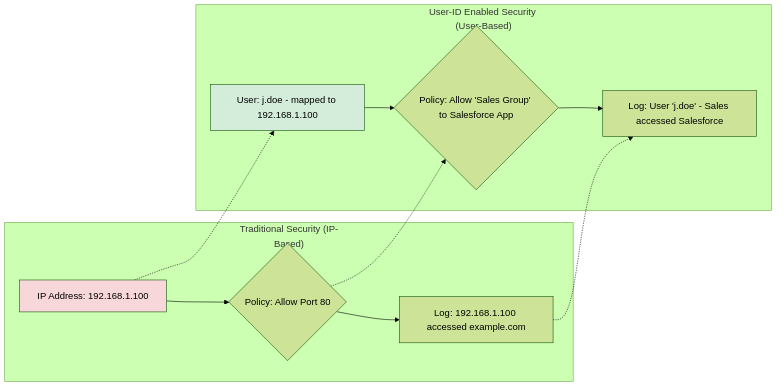
Contrast between IP-based and User-ID based visibility and policy.
Sharing User-to-IP Mappings
In a distributed Palo Alto Networks environment (e.g., multiple firewalls, Panorama, Log Collectors), User-ID information (IP-to-user mappings) needs to be shared effectively between components to ensure consistent policy enforcement and visibility.
Methods of Sharing Mappings:
-
Panorama-based Redistribution:
- Panorama can act as a central hub for User-ID information. Firewalls and User-ID agents can send their mappings to Panorama.
- Panorama then redistributes these mappings to other managed firewalls that require them. This is particularly useful for ensuring consistent User-ID information across a large deployment.
- Configuration is done via User-ID settings in Panorama templates or template stacks.
- Benefit: Centralized management and distribution of mappings.
-
Direct Firewall-to-Firewall Redistribution (User-ID Agent or PAN-OS Integrated):
- Firewalls can be configured to share User-ID mappings directly with each other. This is often done via the User-ID agent (where one agent collects and shares with multiple firewalls) or through PAN-OS integrated User-ID redistribution features.
- A firewall acting as a "collector" can gather mappings from various sources and then redistribute them to other "client" firewalls.
- Benefit: Can be useful in smaller deployments or specific network segments without Panorama, or when Panorama is not used for User-ID redistribution.
-
User-ID Agent as a Broker:
- A dedicated Windows User-ID agent can be configured to collect mappings from various sources (Domain Controllers, Exchange, Syslog, etc.) and then share these mappings with multiple firewalls and/or Panorama.
- The agent acts as a central collection and distribution point.
- Benefit: Offloads mapping collection from firewalls, centralizes agent management.
-
XML API:
- External systems (e.g., NAC, custom scripts, third-party identity solutions) can push IP-to-user mappings to firewalls or Panorama using the PAN-OS XML API.
- Benefit: Integration with diverse identity sources.
-
Log Collectors & Cortex Data Lake (CDL):
- While not direct real-time redistribution for policy, Log Collectors and CDL store logs containing User-ID information. This is crucial for centralized reporting, threat analysis, and forensics across the entire deployment. Panorama often queries these for reporting.
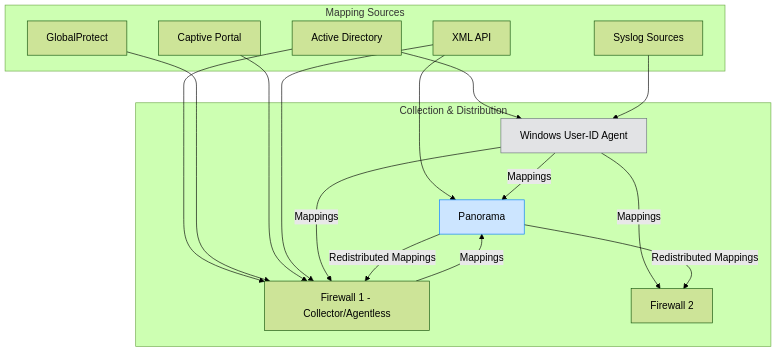
User-ID mapping collection and redistribution flow. Panorama or a User-ID Agent can act as central brokers.
User-ID Sources & Agents
PAN-OS User-ID can gather IP-to-user mapping information from a variety of sources, both agent-based and agentless. Choosing the right sources depends on your network environment and requirements.
Agent-Based User-ID:
This typically involves the Windows User-ID Agent installed on a Windows server (member server or domain controller).
- Windows User-ID Agent:
- Server Monitoring (Event Log Scraping): Monitors security event logs on domain controllers for user login events (e.g., Event ID 4624 for successful logon). This is a primary method. Requires appropriate permissions for the agent's service account to read event logs.
- Client Probing (NetBIOS Probing): If event log scraping doesn't provide a mapping for an IP, the agent can probe Windows clients using NetBIOS to query for the logged-in user. Less reliable and can be blocked by personal firewalls.
- Server Session Monitoring: For environments like Microsoft Terminal Server or Citrix, the agent can monitor active sessions to map users to IPs within those shared environments. Requires specific configuration on the agent and potentially on the terminal servers.
- Syslog Integration: The agent can act as a syslog listener to receive mappings from other network devices or identity sources that can send syslog messages in a specific format.
- Exchange Server Monitoring: Can monitor Exchange server logs to map users to IPs based on email activity.
- eDirectory Monitoring: Supports Novell eDirectory for user mapping.
- Distribution: The agent distributes the collected mappings to configured Palo Alto Networks firewalls and/or Panorama.
Agentless User-ID (PAN-OS Integrated):
The firewall itself can gather IP-to-user mappings without a separate software agent.
- Server Monitoring (PAN-OS Integrated): The firewall can directly query Domain Controllers (Windows AD) or Novell eDirectory servers for user login events from security logs. Similar to agent-based server monitoring but performed by the firewall. Requires service account credentials on the firewall.
- Port Mapping (via GlobalProtect or VPN Client): When users connect via GlobalProtect VPN, the firewall automatically learns the mapping between the VPN-assigned IP and the authenticated username.
- Captive Portal: When users attempt to access network resources, they can be redirected to a web page (Captive Portal) where they must authenticate. Upon successful authentication, the firewall maps their IP to their username. Useful for guest networks or unmanaged devices. Supports various authentication backends (LDAP, RADIUS, Kerberos, SAML).
- GlobalProtect Client Authentication: For internal users with GlobalProtect client, it can provide user information even when not connected via VPN (HIP checks).
- XML API: The firewall can receive mappings pushed from external systems (e.g., NAC, Aruba ClearPass, Cisco ISE) via its XML API.
- Syslog Integration (PAN-OS Integrated): The firewall can parse syslog messages from various sources (e.g., wireless controllers, VPN concentrators, 802.1X authentication servers) to extract IP-user mappings. Requires creating Syslog Parse Profiles.
- VM Information Sources (VMware ESXi, NSX, AWS, Azure, GCP): For virtualized environments, User-ID can gather IP-to-VM and tag information, which can then be associated with users if other mapping methods are also in place for those VMs.
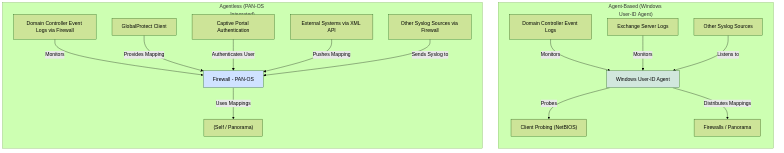
Comparison of Agent-based vs. Agentless User-ID Sources.
Use Cases for IP-User Mapping (User-ID)
User-ID's ability to map IP addresses to users unlocks numerous powerful use cases for enhancing security posture, simplifying operations, and meeting compliance requirements.
-
Granular, User-Based Security Policies:
- Application Access Control: Allow or deny access to specific applications (e.g., Salesforce, SharePoint, financial apps) based on Active Directory user groups (e.g., "Sales," "HR," "Finance") rather than IP subnets. This ensures least-privilege access.
- URL Filtering by Group: Apply different URL filtering profiles to different user groups. For instance, be more restrictive for contractors or guests than for full-time employees.
- Threat Prevention Tailoring: Assign more stringent Antivirus, Anti-Spyware, and Vulnerability Protection profiles to high-risk user groups or users handling sensitive data.
- Decryption Policies: Selectively decrypt SSL/TLS traffic for specific user groups for inspection, while potentially excluding others for privacy reasons (e.g., HR or legal discussions, if policy dictates).
-
Enhanced Threat Hunting and Incident Response:
- Identifying Affected Users: When a threat (malware, C2) is detected from an IP address, User-ID immediately links it to a specific username, speeding up incident response and containment.
- User Behavior Analysis: Track user activity across the network for anomalous behavior detection, which can be an indicator of compromised accounts or insider threats.
- Forensic Investigations: Logs enriched with usernames provide a clear audit trail of user actions, simplifying forensic analysis.
-
Improved Logging, Reporting, and Compliance:
- Meaningful Reports: Generate reports on application usage, web activity, and threats attributed to specific users or departments, providing actionable insights for capacity planning, security awareness, and policy adjustments.
- Compliance Audits: Easily demonstrate compliance with regulations that require tracking and controlling user access to sensitive data and systems.
-
Control Over Unmanaged or BYOD Devices:
- Using Captive Portal or GlobalProtect, organizations can identify and apply policies to users on unmanaged devices (BYOD, guest devices) connecting to the network.
-
Controlling Access to Sensitive Network Segments:
- Restrict access to critical servers, databases, or PCI-compliant zones based on authenticated user identity, adding a strong layer of internal segmentation.
-
GlobalProtect VPN User Identification:
- Automatically identify users connecting via GlobalProtect VPN and apply appropriate policies based on their identity and group memberships.
Scenario: Securing Financial Data Access
A company wants to ensure only members of the "Finance_Team" Active Directory group can access the internal accounting application server (IP 10.1.5.20). All other users should be blocked.
With User-ID:
- Configure User-ID to map AD users to IPs.
- Create a Security Policy rule:
- Source Zone: Trust
- Source User: Finance_Team (from AD)
- Destination Zone: Servers
- Destination IP: 10.1.5.20
- Application: accounting-app (custom or App-ID)
- Action: Allow
- A default deny rule or a more specific block rule for other users to this server would prevent unauthorized access.
This is far more secure and manageable than an IP-based rule, which could be circumvented if an unauthorized user gains access to an IP address that was previously permitted.
User-ID Configuration & Verification
Setting up User-ID involves configuring mapping sources and then using that information in policies. Verifying that mappings are being learned correctly is crucial.
Key Configuration Steps (General Overview):
-
Define User-ID Agents / PAN-OS Agentless Sources:
- Windows User-ID Agent: Install the agent, configure it to monitor Domain Controllers (DCs), specify DCs, service account credentials, and the firewalls/Panorama to send mappings to.
- PAN-OS Agentless Server Monitoring: Under
Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup, add Server Monitors. Provide DC IP/FQDN, credentials, and select monitoring type (e.g., "Active Directory Security Log"). - GlobalProtect: Configure Gateways and Portals. User mapping is inherent.
- Captive Portal: Under
Device > User Identification > Captive Portal Settings, configure redirect host, authentication profile, etc. Apply Captive Portal policy in Security rules. - Syslog Integration: Create Syslog Parse Profiles under
Device > User Identification > User Mapping > Palo Alto Networks User-ID Agent Setup > Syslog Filters. - XML API: Ensure API key is generated and external system is configured to push mappings.
-
Group Mapping (Optional but Recommended):
- Under
Device > User Identification > Group Mapping Settings, configure connections to LDAP/AD servers to retrieve user-to-group associations. This allows policies based on groups.
- Under
-
Enable User-ID on Zones:
- In
Network > Zones, select the zones where you want User-ID to be active (i.e., where users whose traffic transits these zones should be identified). Typically enabled on internal/trusted zones.
- In
-
Use User/Group in Policies:
- In Security Policy rules (and other policy types), specify users or groups in the "Source User" field.
-
Configure Redistribution (if needed):
- In Panorama or on individual firewalls, configure settings for sharing/receiving User-ID mappings.
Verification - CLI Commands:
These are essential for troubleshooting and verifying User-ID operation:
show user ip-user-mapping all: Displays all current IP-to-user mappings known by the firewall.- Variations:
show user ip-user-mapping ip <IP_ADDRESS>,show user ip-user-mapping user <DOMAIN\USERNAME>
- Variations:
show user group list: Lists all groups known by the firewall from Group Mapping.show user group name "<GROUP_NAME>": Shows users belonging to a specific group.show user server-monitor state all: Shows the status of configured server monitors (agentless).show user user-id-agent state all: Shows the status of connected User-ID agents.show user captive-portal-redirect host <IP_ADDRESS>: Checks if an IP is subject to Captive Portal redirect.show counter global | match user_id_: Displays various global counters related to User-ID processing.debug user-id dump [ip-user-mapping | group-mapping]: Dumps detailed User-ID cache information (use for advanced troubleshooting).test user-id user-id-agent status agent-name <AGENT_NAME>: Tests connection to a specific User-ID Agent.test authentication authentication-profile <PROFILE_NAME> username <USERNAME> password: Tests an authentication profile used by Captive Portal or GlobalProtect.
GUI Verification:
Monitor > Logs > Traffic(ensure "Source User" column is displayed).Monitor > User-ID(on Panorama or firewall) shows learned mappings and agent status.Device > User Identificationvarious tabs show configured mappings and agent status.
show user ip-user-mapping all and show user group list) is critical for the PCNSE exam. Understanding where to configure different User-ID sources in the GUI is also important.
User-ID Gotchas & Best Practices
While User-ID is powerful, some configurations and environments require special attention to ensure accurate and reliable mappings.
Common Gotchas:
-
Terminal Servers / Citrix Environments:
- Multiple users share the same IP address. Standard IP-to-user mapping won't work correctly.
- Solution: Requires the Palo Alto Networks Terminal Services Agent (or Citrix XenApp Agent) installed on the terminal servers. This agent assigns a unique port range to each user session and communicates this (user, IP, port range) information to the firewall or User-ID agent. The firewall then uses this port-based mapping for policy.
-
Mapping Timeouts:
- Stale mappings can lead to incorrect policy enforcement if a user logs off and another user quickly reuses the IP.
- Solution: Configure appropriate User-ID timeouts (
Device > User Identification > User Mapping > User-ID Timeout Settings). Timeouts should be shorter than DHCP lease times. Frequent polling by Server Monitors also helps keep mappings fresh.
-
Service Account Permissions:
- User-ID Agent or firewall (for agentless) needs proper permissions to read security event logs from Domain Controllers or query directory services. Insufficient permissions lead to failed mapping collection.
- Solution: Ensure the service account is a member of "Event Log Readers" and potentially "Distributed COM Users" on DCs, or has specific delegated permissions. Follow Palo Alto Networks documentation for least privilege.
-
Group Mapping Latency:
- Changes in AD group memberships might not reflect immediately in firewall policies if group mapping refresh intervals are too long.
- Solution: Configure an appropriate "Update Interval" in Group Mapping settings (
Device > User Identification > Group Mapping Settings).
-
Multiple Domain Environments:
- User-ID agent or firewall needs to be configured to monitor/query all relevant domains.
- Solution: Ensure all Domain Controllers for all user domains are configured as sources.
-
Non-Windows Environments:
- Event log scraping is Windows-specific.
- Solution: Utilize XML API, Syslog integration, Captive Portal, or GlobalProtect for non-Windows clients or RADIUS/802.1x accounting logs for broader coverage.
-
Firewall Not Receiving Mappings:
- Check connectivity between User-ID agent and firewall, firewall and DCs (agentless), or Panorama redistribution.
- Solution: Verify IP connectivity, port numbers (User-ID agent typically uses TCP/5007 to send to firewall), and that the firewall is configured to accept mappings from the agent's IP.
-
Captive Portal Certificate Issues:
- If using HTTPS for Captive Portal, users might see certificate warnings if the certificate is not trusted by their browsers.
- Solution: Use a publicly trusted certificate or ensure internal clients trust the internal CA certificate used for Captive Portal.
Best Practices:
- Use Multiple Sources: Combine several User-ID methods (e.g., Server Monitoring, GlobalProtect, Captive Portal) for the most comprehensive coverage.
- Dedicated Service Account: Use a dedicated service account for User-ID with the principle of least privilege.
- Secure User-ID Agent Communication: Ensure communication between User-ID agents and firewalls/Panorama is secured (e.g., over trusted networks, consider SSL if an option).
- Regularly Monitor Mappings: Use CLI commands and GUI logs to check the health and accuracy of User-ID mappings.
- Keep PAN-OS and Agent Software Updated: Benefit from bug fixes and new features.
- Plan for Scale: In large environments, consider multiple User-ID agents or dedicated Panorama for User-ID redistribution.
- Understand User-ID Timeout vs. Authentication Timeout vs. Idle Timeout: These are different. User-ID timeout is for how long a mapping is valid. Authentication Timeout (e.g. for Captive Portal) is how long an authentication itself is valid. Idle Timeout is for inactivity on a session.
Configuring WildFire Analysis Profiles
WildFire Analysis Profiles are crucial configuration objects on the Palo Alto Networks firewall. They define *which* unknown files and links should be submitted to the WildFire service for analysis, and under what conditions.
Location and Parameters:
- GUI Path:
Objects > Security Profiles > WildFire Analysis - Click
Addto create a new profile.
Key Parameters (Analysis Tab):
| Parameter | Description | Best Practice Recommendation |
|---|---|---|
| Name | Descriptive name for the profile (e.g., WF-Forward-Exec-Office-PDF). |
Required. Make it descriptive of its purpose. |
| Applications | Specify applications for which files/links should be forwarded. Can be any or a selection (e.g., web-browsing, smtp, smb). |
any - Maximizes visibility as threats can be delivered via various applications. If more granular control is needed, select specific common threat-bearing applications. |
| File Types | Select specific file types to forward (e.g., PE, PDF, Office, APK, Scripts) or any. |
Select common threat vectors (PE, PDF, MS Office, Scripts, APK, Flash, Java Archives, etc.). Avoid any unless there's a specific need and understanding of volume/privacy implications, as it can forward many benign files. |
| Direction | Choose upload, download, or both. Defines the direction of traffic flow for which files are submitted. |
both - Catches threats entering via downloads and potential data exfiltration or malicious uploads. |
| Maximum File Size | Defines the max size (MB) for submitted files. Cloud limits vary (e.g., up to 100MB for PE, often lower for other types like Office docs or PDFs). On-prem appliances also have limits. | Leave defaults unless specific reason to change; ensure it's within WildFire cloud/appliance limits for the specific file types. |
| Report Benign Files / Report Grayware Files | Forward files even if previously determined benign/grayware by WildFire (e.g., for re-analysis or more comprehensive logging). | Usually leave unchecked unless needed for specific forensic, research, or high-security analysis purposes, as it can significantly increase submission volume. |
Cloud Settings Tab:
- WildFire Public Cloud: Choose the Public Cloud region geographically closest to the firewall for best performance and potential data residency considerations (e.g.,
Americas,Europe,Asia,Japan,UK,Canada,Australia). - Private Cloud (WildFire Appliance): Enter the IP address or FQDN of your on-premise WF-500 appliance or VM-Series configured for WildFire analysis.
Applying the Profile to Security Policy Rules:
A WildFire Analysis Profile only takes effect when applied to Security Policy rules.
- Location:
Policies > Security - Edit the relevant Security Policy rule(s).
- Action Tab: Under 'Profile Setting', select 'Profiles'.
- WildFire Analysis Dropdown: Choose the WildFire Analysis Profile you created.
- Rule Action Requirement: WildFire analysis (and other Security Profile actions) only apply to rules with Action = Allow. Files in sessions denied by policy are not submitted.
- Commit the changes to the firewall.
Typically, apply WildFire Analysis profiles to rules allowing traffic ingress from untrusted zones (like the internet) and potentially egress to untrusted zones to catch both malicious downloads and uploads/exfiltration attempts.
Best Practices for WildFire Analysis Profiles:
- Enable WildFire Globally: Ensure the WildFire license is active and Content Updates are scheduled regularly.
- Apply Profiles Broadly (but Wisely): Attach a WildFire Analysis profile to all relevant
Allowrules, especially for traffic to/from the internet or less trusted zones. - Forward Common Threat Vectors: Prioritize PE, Office docs, PDFs, scripts, Java, Flash, APKs. Avoid `any` file type unless essential.
- Forward for 'Any' Application: Maximizes visibility.
- Forward in 'Both' Directions: Catches downloads and uploads.
- Choose Correct Cloud Region/Appliance: For performance and compliance.
- Ensure Firewall Connectivity: Verify DNS, routing, and Security Policy allowing egress to WildFire.
- Enable SSL Decryption: Crucial for effectiveness. WildFire cannot analyze files in encrypted sessions unless decrypted.
- Monitor Submissions: Regularly check
Monitor > Logs > WildFire Submissions. - Review Verdicts: Investigate Malware, Phishing, and Grayware verdicts.
Caveats and Considerations:
- License Requirement: Valid WildFire subscription needed.
- Internet Connectivity: Required for Public WildFire Cloud.
- SSL Decryption Dependency: WildFire cannot see inside encrypted traffic without decryption. This significantly reduces effectiveness if not implemented for relevant traffic.
- File Size Limits: Files exceeding limits won't be submitted.
- Password-Protected Archives: Generally cannot be analyzed if the password is unknown.
- Submission Volume & Bandwidth: Forwarding `any` file type or many large files can consume bandwidth.
- Privacy (Public Cloud): Files leave organizational control. Consider a Private WildFire Appliance for strict data confidentiality/residency.
- Private Cloud Appliance: Requires purchase, deployment, management, and updates.
- Verdict Latency: Analysis takes time (seconds to minutes). Initial packets might pass before a verdict. Blocking often relies on subsequent signature updates.
WildFire Security & Privacy Considerations
When submitting files to WildFire, especially the public cloud, security and privacy are important considerations.
How is sensitive information protected during submission?
- Secure Transmission: File submissions to the WildFire public cloud are encrypted using HTTPS (TLS) to protect data in transit.
- Isolated Analysis: Files are analyzed in isolated sandbox environments. These environments are reset after each analysis to prevent cross-contamination.
- Data Handling Policies: Palo Alto Networks has data handling policies and security measures in place for its cloud services. Information on these can typically be found in their trust center or service agreements.
- Regional Clouds: Using a regional WildFire cloud (e.g., Europe, Canada) can help with data sovereignty requirements by keeping analysis within a specific geographic region.
For organizations with extreme sensitivity or regulatory prohibitions against files leaving their premises, a Private WildFire Appliance (WF-500 or VM-Series) is the recommended solution, as analysis occurs entirely on-premise.
Can I control what files are submitted (e.g., data filtering or opt-out)?
Yes, you have several layers of control:
-
WildFire Analysis Profiles: This is the primary control.
- File Types: You can select specific file types to forward (e.g., PE, PDF, Office) and exclude others that might be sensitive and low-risk (e.g., plain text files, internal log files). Avoid using "any" unless absolutely necessary.
- Applications: Limit submissions to files from specific applications.
- Direction: Control submissions for uploads, downloads, or both.
-
Data Filtering Profiles (General Security Feature):
- While not specific to WildFire opt-out, Data Filtering profiles can be used in Security Policies to detect and block the transfer of sensitive data patterns (e.g., credit card numbers, social security numbers) *before* a file might be considered for WildFire submission. If a file transfer is blocked by Data Filtering, it won't be submitted to WildFire.
-
SSL Decryption Policies:
- You can selectively decrypt traffic. If traffic to/from a specific sensitive internal server is not decrypted, files transferred over HTTPS in those sessions will not be submitted to WildFire.
-
Source/Destination Control in Security Policies:
- WildFire Analysis Profiles are applied to Security Policy rules. You can choose not to apply WildFire profiles to rules governing traffic between highly sensitive internal zones or to specific trusted servers.
-
WildFire Private Cloud:
- As mentioned, using a private appliance keeps all submitted files on-premise.
-
Forwarding of Benign/Grayware Files:
- In the WildFire Analysis Profile, you can choose *not* to forward files that WildFire has previously identified as benign or grayware. This can reduce the volume of re-submissions.
WildFire Logging, Reporting, and Integration
Effective logging and reporting are essential for monitoring WildFire activity, understanding threat landscapes, and integrating WildFire intelligence into broader security operations.
Where can I see WildFire submission and verdict logs?
Key log types on the PAN-OS firewall and Panorama include:
-
WildFire Submissions Log:
- Location (Firewall/Panorama):
Monitor > Logs > WildFire Submissions - Content: This is the primary log for WildFire activity. It records details for each file and URL submitted, including:
- Timestamp
- Source/Destination IP and User (if User-ID is enabled)
- Application, Filename, File Type, File Size
- Submission Status (e.g., pending, success, failure)
- WildFire Verdict (benign, malware, phishing, grayware)
- Threat ID (if malicious)
- Session ID (links to Traffic log)
- Crucial for verifying submissions and tracking verdicts.
- Location (Firewall/Panorama):
-
Threat Log:
- Location (Firewall/Panorama):
Monitor > Logs > Threat - Content: When WildFire (or Antivirus, Anti-Spyware) detects and acts on a threat based on a signature, an entry is generated here.
- For WildFire-derived threats, you'll see entries with Threat Type "wildfire-virus" or "wildfire-spyware" or related to DNS/URL signatures generated by WildFire.
- Shows action taken (e.g., alert, block, reset).
- Location (Firewall/Panorama):
-
URL Filtering Log:
- Location (Firewall/Panorama):
Monitor > Logs > URL Filtering - Content: If WildFire identifies a URL as phishing or hosting malware, and PAN-DB is updated, attempts to access that URL will be logged here (and potentially blocked) according to URL Filtering policies.
- Location (Firewall/Panorama):
-
Traffic Log:
- Location (Firewall/Panorama):
Monitor > Logs > Traffic - Content: Provides context for sessions that involved a WildFire submission. Can be correlated with WildFire Submission logs using the Session ID.
- Location (Firewall/Panorama):
Can I forward WildFire logs to Panorama or a SIEM?
Yes:
- Panorama: Firewalls automatically forward logs (including WildFire Submissions, Threat, etc.) to their configured Panorama if log forwarding is enabled in the firewall's Log Forwarding Profile and Panorama is set as a destination. Panorama provides centralized logging and reporting.
-
SIEM (Security Information and Event Management):
- Log Forwarding Profiles on the firewall or Panorama can be configured to send logs to external SIEM systems (e.g., Splunk, QRadar, ArcSight).
- Supports formats like Syslog or CEF (Common Event Format).
- This allows for correlation of WildFire data with other security events in your environment.
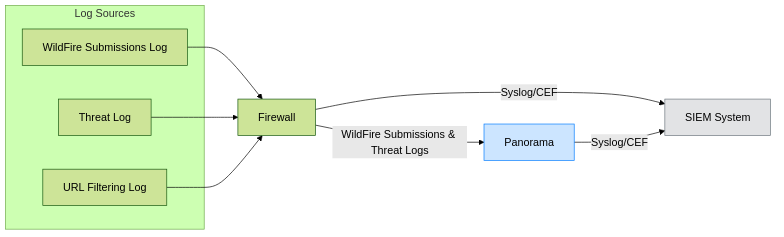
WildFire log forwarding options.
Policy Creation & Integrations with WildFire
WildFire's value extends beyond just detection; its verdicts and intelligence can be actively used to create security policies and integrate with other security tools for automated response.
How do I create a security rule to block files with malicious WildFire verdicts?
Blocking files based on WildFire verdicts primarily relies on Antivirus profiles and Security Policies:
-
Ensure WildFire Signatures are Active:
- Make sure your firewall is licensed for WildFire and is receiving regular Content Updates (which include WildFire-generated antivirus signatures).
-
Configure an Antivirus Profile:
- Go to
Objects > Security Profiles > Antivirus. - Create or edit an Antivirus profile.
- In the profile, for various decoders (e.g., http, smtp, smb), set the Action for WildFire Virus signatures to
block(orreset-both,reset-client,reset-serverdepending on the desired behavior). You can also choosealertif you only want to log. - The "WildFire Action" in the Antivirus profile typically refers to actions taken based on signatures tagged as originating from WildFire.
- Go to
-
Apply the Antivirus Profile to a Security Policy Rule:
- Go to
Policies > Security. - Create or edit a Security Policy rule that allows the relevant traffic (e.g., internet downloads).
- In the rule's
Actionstab, under Profile Setting, select the Antivirus profile you configured. - Remember, this rule itself should have Action "Allow" for the Antivirus profile (and other security profiles) to inspect and take action on the traffic.
- Go to
-
WildFire Inline ML (Advanced WildFire):
- With an Advanced WildFire license, you can enable WildFire Inline ML features directly in Security Profiles (like Antivirus or a dedicated WildFire Analysis profile setting). This allows the firewall to make a real-time blocking decision based on local machine learning models for certain file types (like PE files) even before a cloud verdict is received. Action for inline ML can also be set to block.
When a file with a known WildFire malicious signature (received via content updates) attempts to transit the firewall, the Antivirus profile will trigger the configured block action.
Does WildFire integrate with other Palo Alto products or third parties?
Yes, WildFire intelligence is leveraged across the Palo Alto Networks ecosystem and can be integrated with third-party tools:
- Cortex XDR: Endpoints running Cortex XDR agents can submit unknown files to WildFire. WildFire verdicts and threat intelligence are shared with XDR to enhance endpoint detection and response (EDR) capabilities, allowing for automated blocking or isolation of malicious files/processes on endpoints.
-
Cortex XSOAR (Security Orchestration, Automation and Response):
- WildFire verdicts can be a trigger for XSOAR playbooks.
- For example, a "malware" verdict from WildFire can trigger an XSOAR playbook to:
- Create a ticket in a helpdesk system.
- Quarantine the affected endpoint using Cortex XDR.
- Block the file hash on other security tools via API.
- Notify security analysts.
- XSOAR can also use the WildFire API to submit files for analysis or retrieve reports programmatically.
- Panorama: Provides centralized management and visibility for WildFire configurations, logs, and reporting across multiple firewalls.
- Prisma Access (SASE): Leverages WildFire for threat analysis for remote users and branch offices.
-
Third-Party Tools (via API):
- WildFire offers an API that allows third-party security tools, SIEMs, or custom scripts to:
- Submit files or URLs for analysis.
- Retrieve analysis reports and verdicts.
- Query for verdict history.
- This enables integration of WildFire's advanced threat analysis capabilities into broader security workflows and toolchains.
- WildFire offers an API that allows third-party security tools, SIEMs, or custom scripts to:
- Threat Intelligence Platforms (TIPs): WildFire-generated threat intelligence (hashes, domains, IPs) can be exported or fed into TIPs for broader threat correlation and dissemination.
WildFire License Comparison
The capabilities and speed of protection offered by WildFire can differ based on the type of WildFire subscription an organization has. A standard WildFire license provides core functionality, while an Advanced WildFire (or Threat Prevention) license unlocks enhanced features and faster protections.
Below is a general comparison. Specific features and naming can evolve, so always refer to the latest Palo Alto Networks documentation for precise details.
| Feature / Capability | Standard WildFire License | Advanced WildFire License (or equivalent top-tier Threat Prevention) |
|---|---|---|
| Core Cloud Sandbox Analysis (Static, Dynamic for common types) |
Yes | Yes |
| Signature Update Frequency (WildFire-generated) | Regular content updates (e.g., daily for AV, more frequent for basic WildFire signatures but not real-time) | Near Real-time (e.g., every 1-5 minutes) signature streaming for fastest protection. |
| Supported File Types for Analysis | Broad range (PE, Office, PDF, APK, scripts, etc.) | Potentially broader or deeper analysis for certain advanced types. Includes Bare Metal Analysis for highly evasive threats. |
| WildFire API Access (for submission/reports) | Limited or Basic API access (check specific license terms) | Full API access for submissions, report retrieval, and integration. Higher API rate limits. |
| Inline ML (Machine Learning on the Firewall) | Limited or no Inline ML for real-time blocking of unknown PE files based on local models. | Full Inline ML capabilities for PE files and potentially other types, allowing for immediate blocking of unknown threats based on local ML, even before cloud analysis completes. |
| Bare Metal Analysis | No | Yes, for highly evasive malware that can detect virtualized sandbox environments. |
| URL Analysis for Phishing & Malware | Yes | Yes, potentially with more advanced link analysis capabilities. |
| WildFire Report Detail | Standard reports | More detailed analysis reports, potentially including advanced forensics data. |
| Private Cloud (WF-500/VM) Support | Yes (appliance purchased separately) | Yes (appliance purchased separately, license enhances its capabilities) |
The "Threat Prevention" license from Palo Alto Networks often bundles Advanced WildFire capabilities along with Antivirus, Anti-Spyware, and Vulnerability Protection. The exact entitlements can vary, so it's crucial to check the specifics of your purchased license.
For more detailed information, refer to the official Palo Alto Networks documentation on Advanced WildFire Subscription.
PCNSE Exam Focus Summary: WildFire & User-ID
This section summarizes key areas related to WildFire and User-ID that are important for the PCNSE exam.
WildFire PCNSE Focus:
- Purpose of WildFire: Analyzing unknown files/links for zero-day threats (malware, exploits, phishing).
- Configuration Object: WildFire Analysis Profile (configured under
Objects > Security Profiles > WildFire Analysis). - Application: Attached to Security Policy rules with Action = Allow.
- Key Profile Settings: Applications, File Types, Direction, Cloud selection (Public/Private). Understand the implications of "any" vs. specific selections.
- Deployment Options: Public Cloud, Private Appliance (WF-500/VM), Hybrid. Know when to use each (privacy vs. global intel).
- Analysis Process: Basic understanding of Static, Dynamic (sandboxing), and Machine Learning analysis stages.
- Verdicts: Benign, Grayware, Malware, Phishing.
- Protection Delivery: Via Content Updates (signatures for AV, AS, DNS, URL Filtering). Advanced WildFire provides faster, near real-time signature streaming.
- SSL Decryption Dependency: WildFire cannot inspect files within encrypted (HTTPS) sessions unless SSL Forward Proxy Decryption is enabled for that traffic. This is a critical point.
- Logging: WildFire Submissions Log (
Monitor > Logs > WildFire Submissions) is primary for tracking submissions and verdicts. Threat Log shows actions based on signatures. - Troubleshooting: Common reasons for submission failure (licensing, connectivity, profile config, SSL decryption). Key CLI:
show wildfire status,test wildfire registration. - Licensing: WildFire subscription is required. Advanced WildFire offers enhanced features (Inline ML, faster sigs, API).
- Gotcha: Forgetting SSL Decryption, misconfiguring WildFire Analysis Profiles (e.g., wrong file types/direction), or Security Policy application.
User-ID PCNSE Focus:
- Purpose of User-ID: Map IP addresses to usernames for user-based visibility, policy enforcement, and reporting.
- Mapping Sources:
- Agent-based (Windows User-ID Agent): Server Monitoring (DC event logs), Client Probing, Exchange monitoring, Syslog.
- Agentless (PAN-OS Integrated): Server Monitoring (firewall queries DCs), GlobalProtect, Captive Portal, XML API, Syslog (firewall parses).
- Know the mechanisms for each (e.g., event log scraping, web auth, VPN auth).
- Configuration Components:
- User-ID Agent setup (if used).
- Server Monitor configuration (agentless or agent).
- Group Mapping Settings (connecting to LDAP/AD for group info).
- Enabling User-ID on Zones.
- Policy Application: Using users/groups in the "Source User" field of Security Policies.
- Redistribution: How mappings are shared (Panorama, firewall-to-firewall, User-ID agent).
- Verification & Troubleshooting CLI:
show user ip-user-mapping all(and its variants for specific IP/user).show user group list/show user group name "...".show user server-monitor state all.show user user-id-agent state all.
- Terminal Services / Citrix: Requires the Palo Alto Networks Terminal Services Agent for port-based user mapping due to shared IPs. This is a common exam topic.
- Timeouts: User-ID timeout vs. Authentication timeout. Importance of keeping mappings fresh.
- Gotchas: Service account permissions for DC log reading, Terminal Server environments, stale mappings, Captive Portal certificate issues, firewall not receiving mappings.
- Group Mapping: Essential for creating policies based on directory service groups.
- Captive Portal: Modes (Transparent, Redirect), authentication methods, use cases (guest, BYOD).
WildFire & User-ID Comprehensive Quiz
Test your knowledge on Palo Alto Networks WildFire and User-ID concepts. Select the best answer for each question.