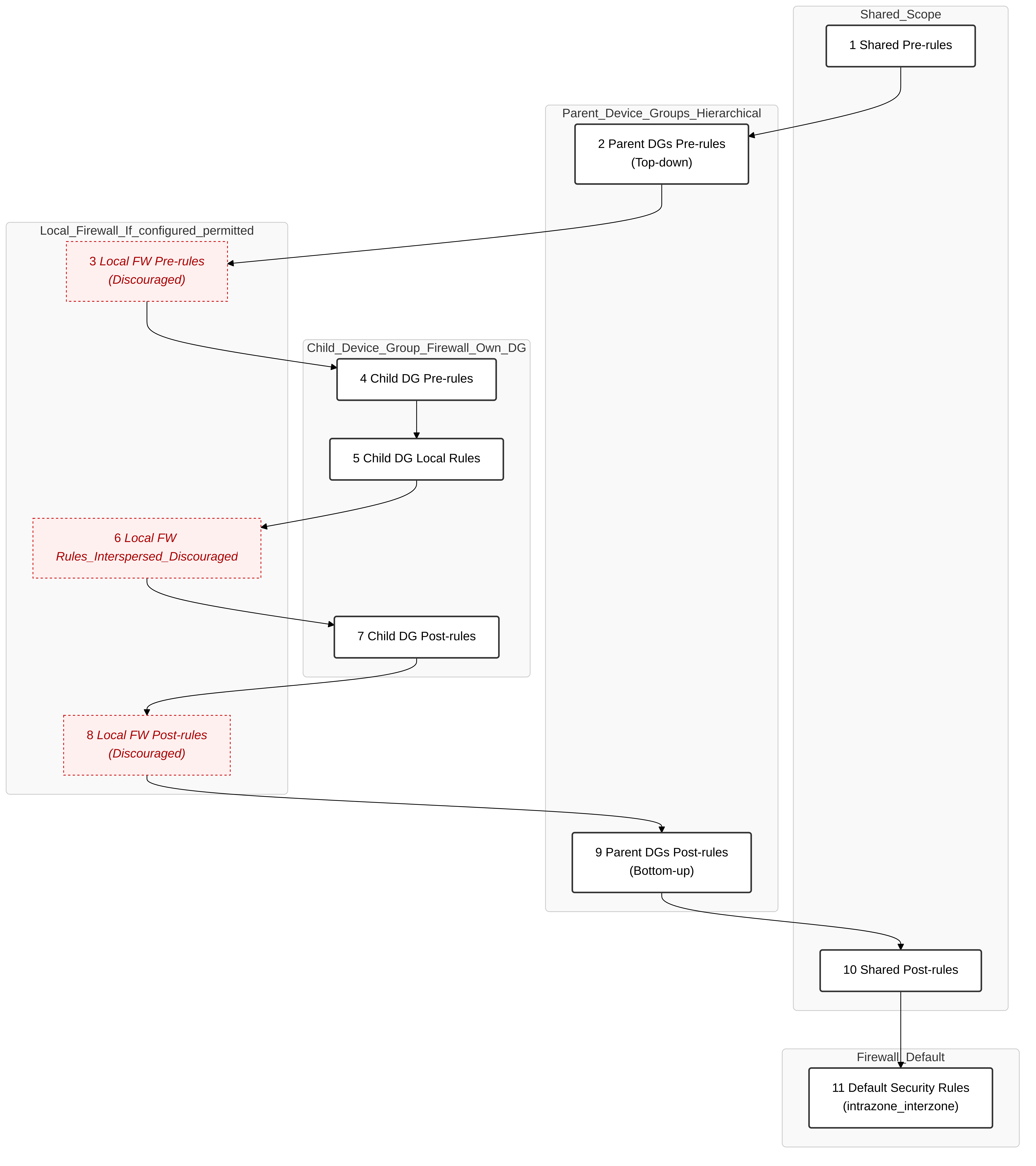
Within each Device Group (including 'Shared'), policies are further divided into Pre-rules and Post-rules . These designations, along with the Device Group hierarchy and any local firewall rules, dictate the final sequence in which security policies are evaluated by the firewall.
- Pre-rules: Evaluated first within their respective scope (Shared, Parent DG, Child DG). They are typically used for global block rules, universal allow rules for infrastructure services, or policies that must take precedence over more specific rules defined later in the evaluation sequence.
- Post-rules: Evaluated last within their respective scope. They are typically used for default deny/cleanup rules or broad allow rules that should only match if no specific rules higher up in the full evaluation order (including local firewall rules and rules from the firewall's own Device Group) match.
Comprehensive Firewall Policy Evaluation Order:
When Panorama pushes the merged policy configuration, the firewall evaluates Security Policy rules in this strict order:
- Panorama 'Shared' Scope Pre-rules
- Parent Device Group(s) Pre-rules (Evaluated top-down in the hierarchy, from the highest-level parent DG down to the parent DG just above the firewall's own DG)
- (Local Firewall Pre-rules - if manually configured on the firewall before its own DG's rule block. This is generally not a Panorama-managed practice and is discouraged.)
- Child Device Group Pre-rules (Pre-rules from the specific Device Group the firewall is a direct member of)
- Child Device Group "Local" Rules (These are the main body of rules, not designated as Pre or Post, within the Device Group the firewall is a direct member of. They are evaluated top-down as they appear in that Device Group's rulebase.)
- (Local Firewall Rules - if manually configured directly on the firewall's GUI, their evaluation point relative to the Child DG Local Rules depends on where they were inserted by the local admin. This practice is generally discouraged in a Panorama-managed environment for maintaining consistency and can be overridden by Panorama pushes.)
- Child Device Group Post-rules (Post-rules from the specific Device Group the firewall is a direct member of)
- (Local Firewall Post-rules - if manually configured on the firewall after its own DG's rule block. Also discouraged.)
- Parent Device Group(s) Post-rules (Evaluated bottom-up in the hierarchy, from the parent DG just above the firewall's own DG up to the highest-level parent DG)
- Panorama 'Shared' Scope Post-rules
-
Firewall Default Security Rules (e.g.,
intrazone-defaultwhich defaults to 'allow', andinterzone-defaultwhich defaults to 'deny'. These apply only if no explicit rule above has matched the traffic.)
This explicit order ensures that broader, inherited rules (especially cleanup rules in Post-rules) don't inadvertently override more specific rules defined closer to the device (Child DG or potentially Local FW rules if permitted). Template Stacks, which manage Network and Device settings, operate distinctly from this policy evaluation order.
- Policy Reusability and Inheritance: Define common security policies (e.g., block known bad IPs, allow DNS) once at a higher level (parent DG or Shared) and have them automatically apply to all child groups.
- Role-Based Administration: Different administrative teams can potentially manage policies within specific device groups relevant to their responsibilities (though Panorama RBAC is the primary tool for admin control).
- Scalability: Easily apply baseline policies to hundreds of firewalls by placing them in appropriate device groups within the hierarchy.
- Logical Organization: Structure policies based on geography, function (e.g., Datacenter, Branch, Perimeter), or compliance requirements (e.g., PCI-DSS zone firewalls).
- Simplified Changes: Update a common policy once in a parent DG, and the change propagates to all inheriting child DGs and their firewalls upon push.