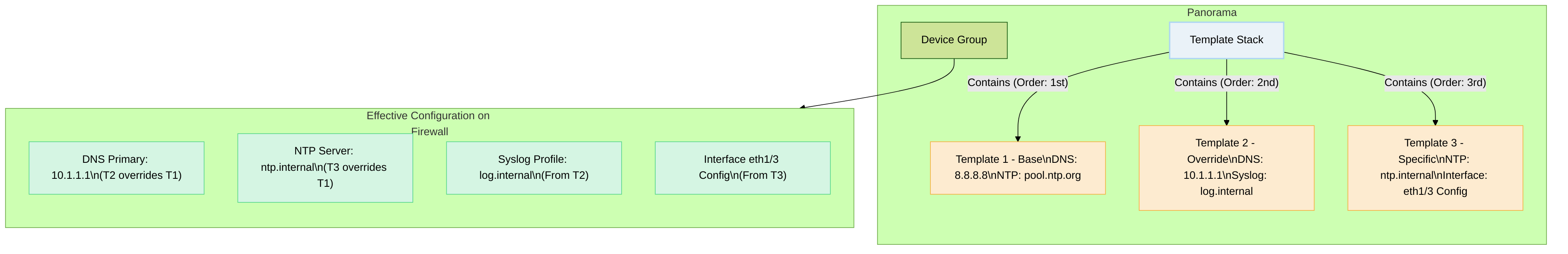
How Precedence Works (Within a Template Stack for Network/Device Settings):
- Panorama processes the templates in a stack sequentially, from the first template listed (often considered the "bottom" or base layer) to the last template listed (the "top" or final layer).
- When configuring a specific Network or Device setting (like `Device > Setup > Services > Primary DNS`), Panorama checks each template in the stack in order.
- If Template 1 sets Primary DNS to `8.8.8.8`.
- If Template 2 (listed after Template 1) sets Primary DNS to `10.1.1.1`.
- If Template 3 (listed after Template 2) does *not* define a Primary DNS server.
- The final value pushed to the firewall for Primary DNS will be `10.1.1.1` , because Template 2 was the *last* template in the stack order to define that specific Network/Device setting, overriding the value from Template 1.
- Network or Device settings defined in only one template within the stack are simply included in the final configuration for those parameters.
Purpose of Overrides (for Network/Device Settings):
- Standardization with Exceptions: Define common baseline Network/Device settings in base templates (lower in the stack) and use specific templates (higher in the stack) to override these settings for particular device types, regions, or functions.
- Modularity: Create templates for specific features (e.g., a "GlobalProtect-Settings" template). If a specific device group needs a slightly different GP Network/Device setting, you can create a small overriding template placed later in its stack.
- Hardware Differences: Have a base template for general Network/Device settings, then specific templates higher in the stack for different firewall models that might require unique interface configurations or resource settings.