🔒 Palo Alto Networks: Decryption Exclusions Guide
SSL/TLS decryption is a cornerstone of modern network security, allowing firewalls to inspect encrypted traffic for threats. However, not all traffic can or should be decrypted. This guide explores why decryption exemptions are necessary, how to configure them, methods for automation, troubleshooting techniques, and key considerations for the PCNSE exam.
Why Do We Need Decryption Exemptions?
Decryption exemptions (or exclusions) are crucial for maintaining application functionality, user privacy, and legal compliance. Attempting to decrypt certain traffic can lead to broken applications, failed authentications, or violations of privacy regulations. These reasons generally fall into two categories: technical limitations and policy/compliance mandates.
Key Takeaway: Decryption exemptions are not a security loophole if implemented correctly, but a necessary mechanism to balance security inspection with operational and compliance requirements.
1. Traffic That Cannot Be Decrypted (Technical Limitations)
Certain types of traffic are technically incompatible with decryption due to the inherent nature of their security mechanisms or protocols:
- Certificate Pinning: Applications like Snapchat, Dropbox, and many mobile banking apps use pinned certificates. This means the application is hard-coded to expect a specific server certificate. If the firewall presents its own certificate (as it does during decryption), the application will detect a man-in-the-middle (MitM) attempt and terminate the connection. Attempting to decrypt such traffic will break the application.
- Mutual Authentication (Client Certificates): Some servers, particularly in high-security environments (e.g., B2B portals, government sites), require clients to present their own SSL/TLS certificate for authentication. SSL Forward Proxy decryption, the most common type, breaks this process because the firewall terminates the client's SSL session and initiates a new one to the server, without forwarding the original client certificate. Exemption is required for these sites to function.
- Unsupported Protocols and Cipher Suites: Traffic using outdated or non-standard SSL/TLS versions (e.g., SSLv2, SSLv3), or exotic/weak cipher suites that the firewall's decryption engine does not support, cannot be decrypted. The firewall might be configured to block such sessions or allow them to pass through undecrypted.
- QUIC Protocol: Developed by Google and increasingly used by its services (YouTube, Google Search) and other web properties, QUIC (Quick UDP Internet Connections) operates over UDP and uses TLS 1.3 for encryption. While Palo Alto Networks firewalls can identify and control QUIC traffic, its inherent encryption (often combined with certificate pinning characteristics) makes it generally non-decryptable by traditional proxy-based methods. Blocking QUIC can force applications to fall back to TCP/TLS, which can then be decrypted.
- Non-SSL/TLS Traffic Using SSL/TLS Ports: Some applications might use standard SSL/TLS ports (e.g., TCP/443) for proprietary, non-SSL/TLS encrypted protocols. The firewall will attempt to treat this as SSL/TLS, leading to decryption failures.
2. Traffic That Should Not Be Decrypted (Policy, Privacy, Legal Reasons)
Beyond technical infeasibility, there are strong policy, privacy, legal, and business reasons to exclude certain traffic from decryption:
-
Sensitive Categories:
Traffic related to:
- Financial Services: Online banking, stock trading platforms. Decrypting such traffic may violate terms of service or raise privacy concerns.
- Healthcare: Access to patient portals, medical records systems. Regulations like HIPAA (Health Insurance Portability and Accountability Act) in the US impose strict data privacy rules.
- Government: Access to secure government services or internal systems.
- Executive or Privileged Users: To maintain confidentiality or due to internal policy, traffic from high-level executives, legal departments, or human resources groups may be exempted from decryption. This is a delicate balance, as these users can also be high-value targets.
- Specific Applications: Some business-critical applications, even if technically decryptable, might be known to have intermittent issues or performance degradation when subjected to decryption. A risk assessment might lead to a decision to exempt them to ensure stability. Examples include some voice/video conferencing tools or specialized enterprise software.
- Ethical Considerations: Decrypting traffic to sites like internal whistleblower hotlines, union websites, or sites offering mental health support could be ethically problematic and deter their use.
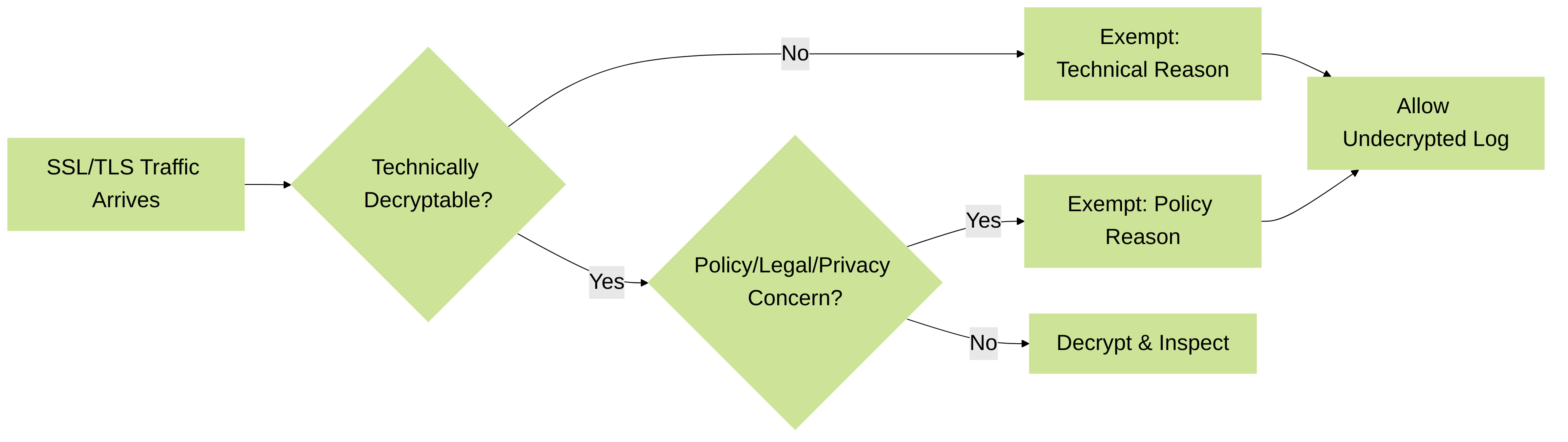
Figure 1: Basic Decryption Exemption Decision Flow
3. Configuring Decryption Exclusions
Palo Alto Networks firewalls offer several mechanisms to manage decryption exclusions. Effective configuration involves leveraging these options appropriately.
3.1 Predefined SSL Decryption Exclusion List
Palo Alto Networks maintains a list of domains known to break decryption due to technical reasons (e.g., certificate pinning, client authentication). This list is part of the application and threat intelligence updates (content updates).
-
Located at:
Device > Certificate Management > SSL Decryption Exclusions - This list is enabled by default and it is highly recommended to keep it enabled.
- You can view the list and see the reason for exclusion (e.g., "pinned-certificate", "client-authentication").
- Entries can be individually disabled, but this is generally discouraged unless you have a very specific reason and have thoroughly tested the impact.
3.2 Local SSL Decryption Exclusion Cache (Server Certificate Verification Failures)
When the firewall attempts to decrypt traffic to a site and encounters specific SSL handshake errors related to server certificate validation failures (e.g., untrusted issuer, expired certificate) , it can temporarily add the site's Server Name Indication (SNI) to a local dynamic exclusion cache. This prevents repeated decryption attempts that are doomed to fail and could impact user experience.
-
This behavior is controlled by settings within the Decryption Profile (
Objects > Decryption > Decryption Profile > SSL Forward Proxy > SSL Protocol Settings > Server Certificate Verification). - If "Block sessions with untrusted issuers" or "Block sessions with expired certificates" is enabled, the firewall blocks the session.
- If these block options are not selected, and the firewall is configured to allow sessions with these errors, it may add the site to this temporary exclusion for a default of 12 hours .
- This cache is not directly viewable or editable by administrators through the GUI in the same way as the predefined or custom lists. Its primary purpose is to prevent resource drain from repeated failed decryption attempts on problematic sites.
Important: This is distinct from exclusions due to client authentication or pinned certificates, which are handled by the predefined list or require manual custom/policy exclusion.
3.3 Custom Decryption Exclusion List
For sites not covered by the predefined list that you need to exclude globally for technical reasons (e.g., an internal application with client certificate authentication not recognized by Palo Alto Networks):
-
Navigate to
Device > Certificate Management > SSL Decryption Exclusions -
Click "Add" and enter the hostname (e.g.,
app.internal.example.com) or use wildcards. -
Use wildcards for broader matches (e.g.,
*.problematic-vendor.comto cover all subdomains). Be cautious with overly broad wildcards. - This list is for technical exclusions. For policy-based exclusions (e.g., financial, healthcare categories), use Decryption policies.
3.4 Policy-Based Decryption Exclusions
This is the most flexible and common method for excluding traffic based on various criteria, aligning with organizational policies.
-
Go to
Policies > Decryption - Create a new rule.
-
Match criteria can include:
- Source/Destination Zone
- Source/Destination Address (or Address Group)
- Source User/Group (requires User-ID)
- URL Category (e.g., financial-services, health-and-medicine)
- Service (e.g., specific application ports if not standard ssl)
- Application (e.g., quic, specific known problematic apps)
- Set the action to "No Decrypt" .
- Optionally, attach a "No Decryption" profile (a Decryption Profile with only "SSL Protocol Settings" and "No Decryption" selected in the SSL Forward Proxy tab). This profile can still enforce certain checks like blocking sessions with expired certificates or untrusted issuers even for non-decrypted traffic, providing a layer of security.
Best Practice: Place "No Decrypt" rules at the top of your Decryption rulebase . Decryption policies are evaluated top-down, first match. If an explicit "Decrypt" rule is matched before a "No Decrypt" rule for the same traffic, decryption will be attempted.
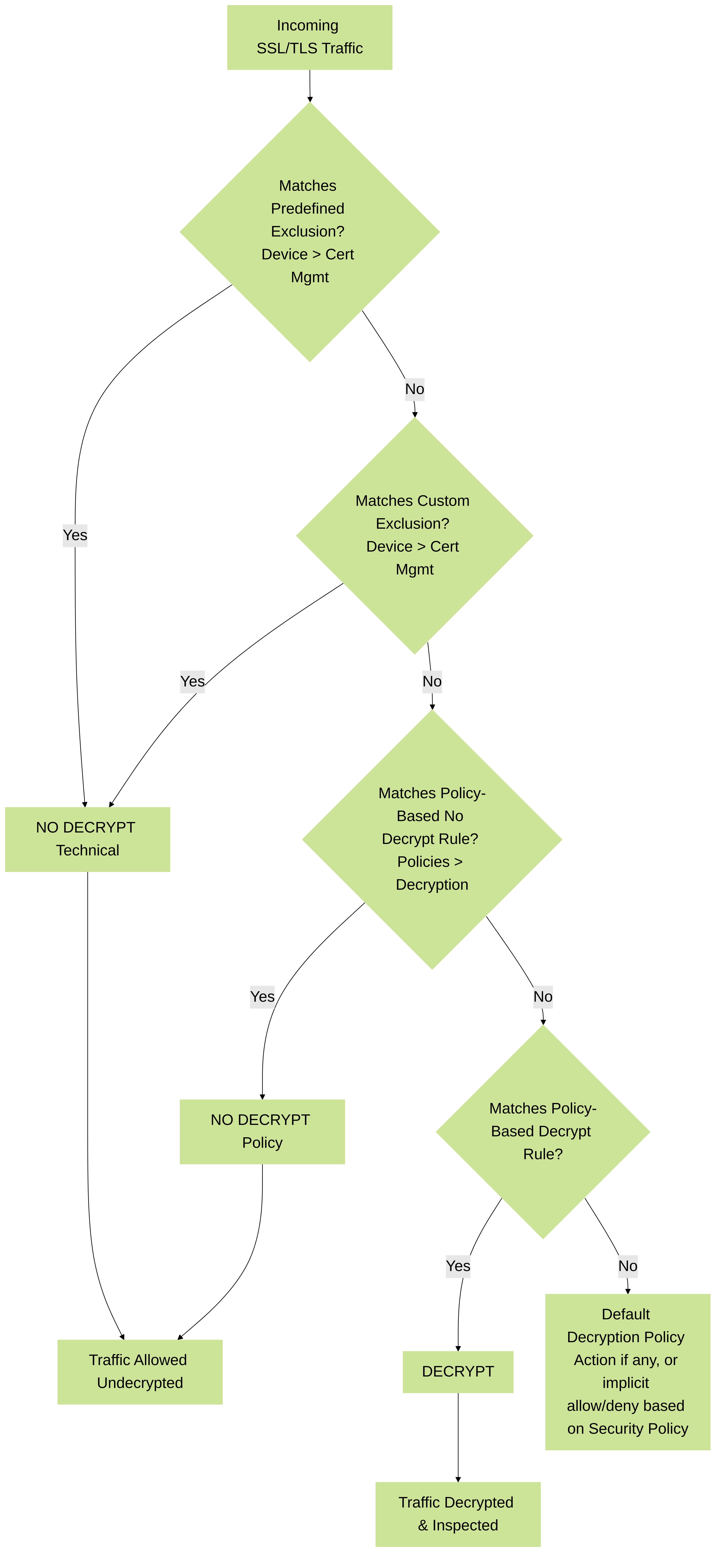
Figure 2: Decryption Exclusion Evaluation Order
4. Automating Decryption Exemptions with Auto-Tagging
Manually identifying and adding every problematic site to an exclusion list can be time-consuming and reactive. Automating this process, especially for sites causing SSL errors, can significantly improve operational efficiency. This typically involves log analysis, tagging, and dynamic policy updates.
Concept:
The core idea is to:
- Detect SSL Errors: Monitor firewall logs (specifically Decryption logs) for patterns indicating problematic SSL/TLS sessions that consistently fail decryption (e.g., due to unrecognized certificate pinning, unsupported ciphers after multiple attempts).
- Extract SNI/Hostname: From these logs, extract the Server Name Indication (SNI) or hostname of the problematic site.
- Tag IP/Hostname: Use an external system (SIEM, SOAR, custom script) to automatically tag the associated IP address or register the hostname with the Palo Alto Networks firewall or Panorama.
- Dynamic Policy Update: Leverage Dynamic Address Groups (DAGs) or External Dynamic Lists (EDLs) that are populated based on these tags/registered names. A "No Decrypt" policy rule would use this DAG/EDL as a destination.
Components & Workflow:
- Log Forwarding: Configure the firewall to forward Decryption logs (and potentially Traffic logs) via syslog or the PAN-OS XML API to a log management system or SIEM.
-
Log Analysis & Correlation Engine:
- A SIEM (Security Information and Event Management) system (e.g., Splunk, QRadar, Elastic Stack) or a custom script (e.g., Python) parses the logs.
- The engine looks for specific decryption failure reasons (e.g., `ssl-decrypt-error`, specific error messages in threat logs if decryption failure leads to threat log entries).
- It might implement thresholds (e.g., if site X fails Y times in Z minutes from multiple sources) to avoid false positives.
-
Tagging/Registration Mechanism:
-
PAN-OS XML API / Panorama API:
The analysis engine makes an API call to the firewall or Panorama to:
- Register an IP address with a specific tag (e.g., "Auto-NoDecrypt-SSL-Error").
- Register a hostname to an External Dynamic List (EDL) that the firewall consumes.
-
PAN-OS XML API / Panorama API:
The analysis engine makes an API call to the firewall or Panorama to:
-
Dynamic Address Group (DAG) / External Dynamic List (EDL):
- Create a DAG in PAN-OS that includes IP addresses based on the tag (e.g., "Auto-NoDecrypt-SSL-Error").
- Alternatively, configure an EDL that points to a web server hosting the list of problematic hostnames/IPs, updated by the automation script.
-
Decryption Policy Rule:
- Create a "No Decrypt" rule in the Decryption policy.
- Set the destination to the DAG or EDL created above.
- Place this rule appropriately in the rulebase (typically high up, but below very specific mandated exclusions).
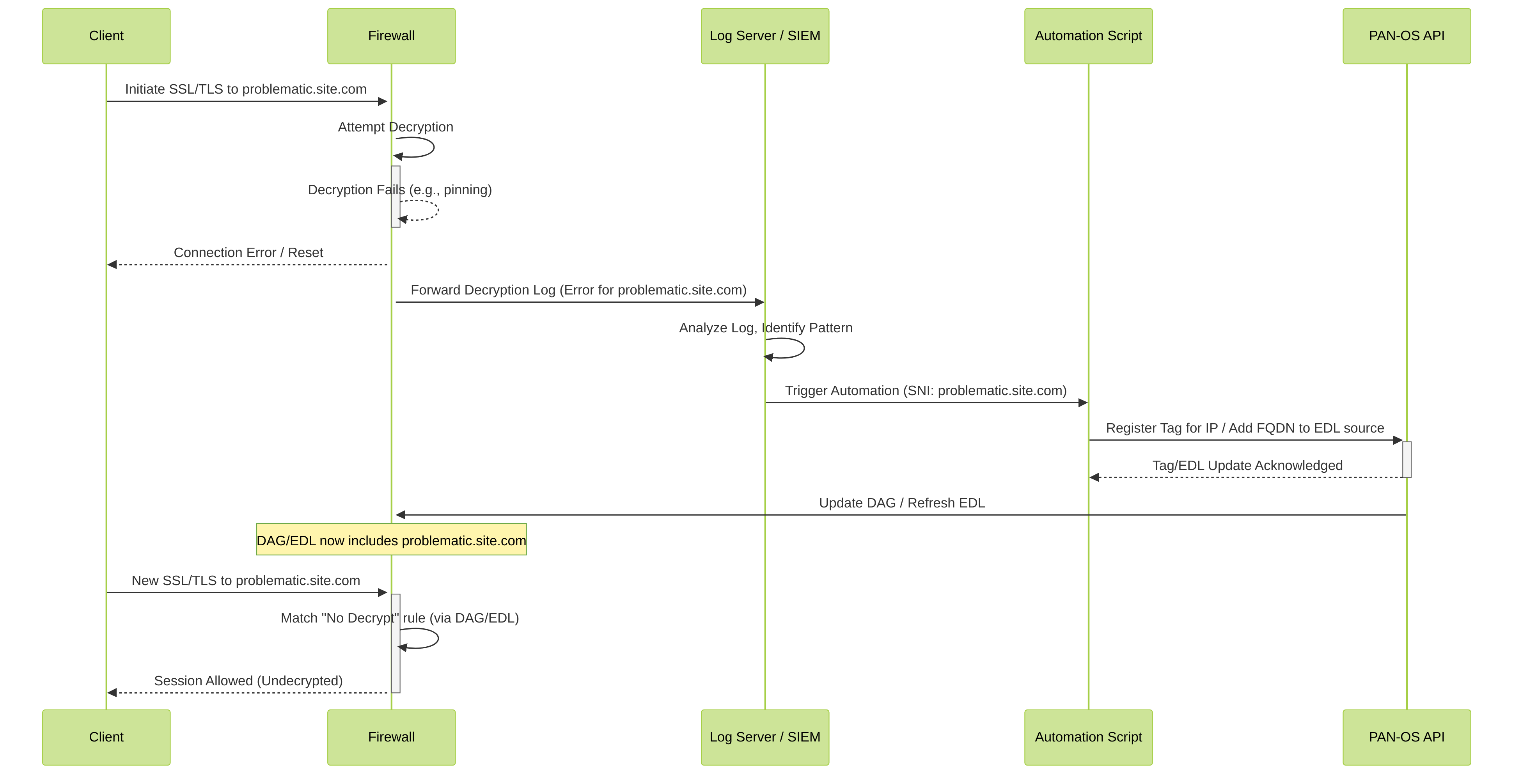
Figure 3: Automated Decryption Exemption Workflow
Considerations for Automation:
- Accuracy of Detection: The logic to identify "problematic" sites must be robust to avoid incorrectly excluding legitimate traffic that should be decrypted. Focus on persistent, specific error types.
- Aging/Stale Entries: Implement a mechanism to age out or re-evaluate tagged IPs/hostnames. A site causing issues today might be fixed tomorrow.
- Monitoring & Alerting: Monitor the automation process itself. Alert administrators if the script fails or if an unusually high number of sites are being added.
- Manual Review: Periodically review the auto-generated exclusion list for auditing and to catch potential misconfigurations.
- Security of the Automation System: Ensure the SIEM/scripting host and API credentials are secure.
Auto-tagging can significantly reduce the administrative burden of maintaining decryption exclusions, making the security posture more adaptive. However, it requires careful planning and ongoing monitoring.
5. Debugging and Troubleshooting Decryption Exemptions
When decryption isn't behaving as expected (e.g., traffic that should be exempt is being decrypted, or vice-versa, or applications are breaking), a systematic approach to troubleshooting is essential.
Common Issues:
- Incorrect Decryption Policy Order: A "Decrypt" rule is placed above a "No Decrypt" rule for the same traffic.
- Mismatched Policy Criteria: The criteria in the "No Decrypt" rule (IP, URL category, user) do not accurately match the traffic in question.
- Misunderstanding of Exclusion Lists: Expecting the predefined list to cover a policy-based scenario or vice-versa.
- Caching: Browser or OS caching of certificates or session information.
- Client-Side Issues: Problems with the client's trust store (if Forward Trust certificate is not installed/trusted). This is more for general decryption failure than exemption failure.
- SNI Mismatch: The SNI in the Client Hello doesn't match the common name or SANs in the certificate, or doesn't match the URL being typed by the user, leading to incorrect policy evaluation if URL filtering is involved.
- Dynamic Content/CDNs: A website might pull content from multiple domains. The primary domain might be excluded, but content from a CDN might not be, leading to partial loading or errors.
Troubleshooting Steps:
-
Verify Client Experience & Gather Information:
- What application is failing? What is the exact URL?
- What is the error message seen by the user (e.g., browser certificate warning, application-specific error)?
- What is the source IP of the client?
- When did the issue start?
-
Check Firewall Logs:
-
Traffic Logs:
Filter by the client IP and server IP/hostname.
- Look for the session. Note the application, port, and whether it was allowed/denied.
- Crucially, check the "Decrypted" column. If 'yes', it was decrypted. If 'no', it wasn't.
- If 'no', was it due to a "No Decrypt" policy or another reason (e.g., unsupported cipher if not blocked)? The session end reason might give clues.
-
Decryption Logs:
(
Monitor > Logs > Decryption) Filter by client IP, server IP, or SNI.-
These logs are invaluable. They show:
- SNI requested.
- Whether decryption was attempted.
- Reason for non-decryption if traffic was exempted (e.g., "ssl-decryption-policy", "ssl-exclude-local", "ssl-exclude-cache", "ssl-exclude-certificate", "pinned-certificate").
- Errors if decryption failed (e.g., "unsupported cipher suite", "untrusted certificate issuer", "handshake failure").
- Certificate information.
- The "Error / Status" column in Decryption logs is key.
-
These logs are invaluable. They show:
- URL Filtering Logs: If exemptions are based on URL categories, check these logs to ensure the site is being categorized correctly and matching the intended "No Decrypt" rule.
-
Traffic Logs:
Filter by the client IP and server IP/hostname.
-
Review Decryption Configuration:
-
Decryption Policies:
(
Policies > Decryption)- Verify the order of rules. "No Decrypt" rules for specific exemptions should be at the top.
- Double-check the source, destination, user, URL category, and service criteria of the relevant "No Decrypt" rule. Ensure it's not too broad or too narrow.
- Check if the rule is enabled.
-
SSL Decryption Exclusions:
(
Device > Certificate Management > SSL Decryption Exclusions)- Is the problematic FQDN on the predefined list (and is that list entry enabled)?
- Is it on your custom exclusion list?
- Remember these are for technical exemptions , not policy ones.
-
Decryption Profile Settings:
(
Objects > Decryption > Decryption Profile)- Check settings for handling unsupported protocols/modes and certificate errors. These can influence whether a session is blocked, allowed undecrypted, or temporarily excluded.
-
Decryption Policies:
(
- Use CLI Commands (see next section).
-
Packet Captures (PCAPs):
- On the firewall: Capture traffic pre-decryption (ingress) and post-decryption (egress) if needed.
- On the client: Use Wireshark to see what the client is sending and receiving, especially the TLS handshake messages and certificate presented.
- Test with a Different Browser/Client: To rule out client-specific issues (e.g., browser extension, corrupted certificate store).
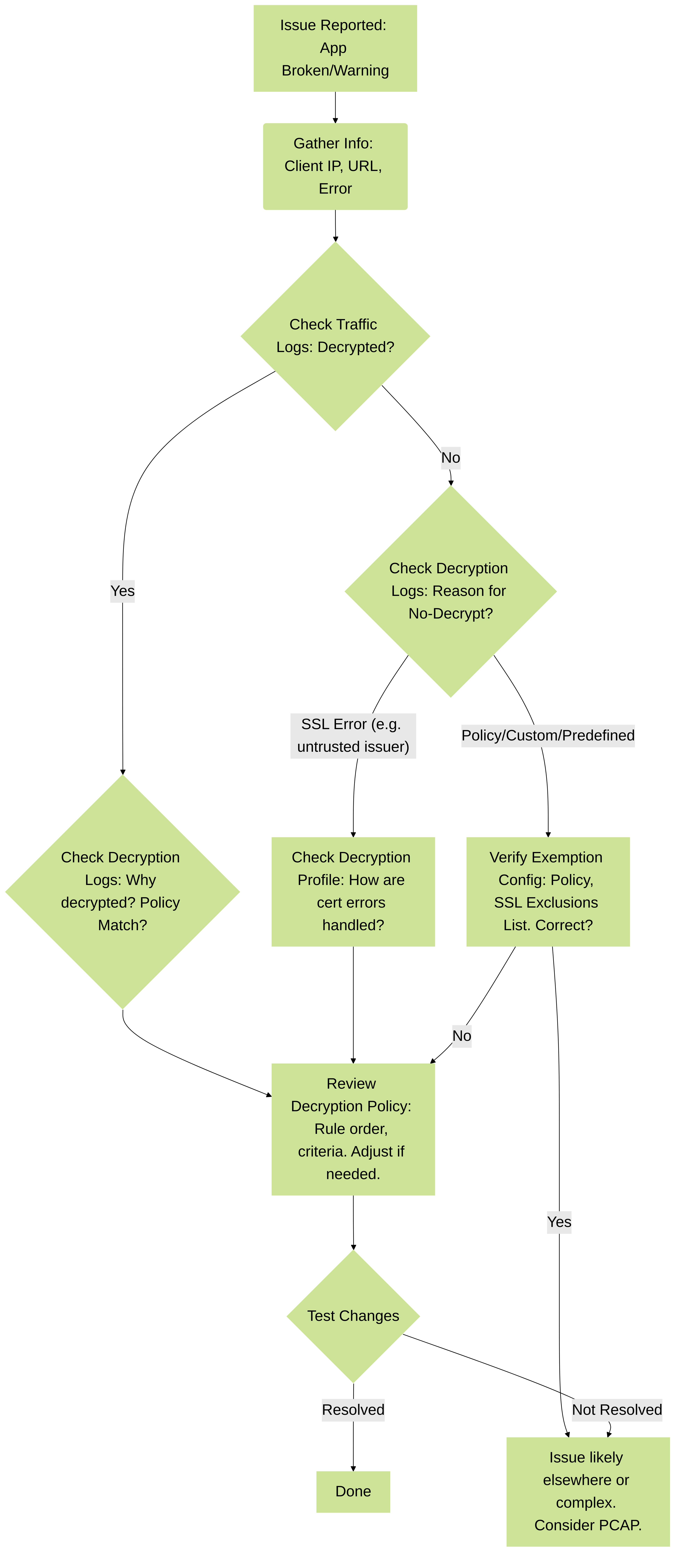
Figure 4: Simplified Decryption Exemption Troubleshooting Flow
Key PAN-OS CLI Commands for Troubleshooting:
Always check the Decryption logs first. They often provide the exact reason why traffic was or was not decrypted, or why an error occurred.
6. PCNSE Exam Considerations
For those preparing for the Palo Alto Networks Certified Network Security Engineer (PCNSE) exam, understanding decryption and its exclusions is critical.
- Understand Decryption Exclusions: Know the difference and use cases for predefined, local (dynamic cache for cert validation failures), and custom decryption exclusions (Device > Certificate Management). Differentiate these from policy-based "No Decrypt" rules. Predefined/Custom are for technical infeasibility; Policy-based is for organizational requirements.
-
Policy-Based Exclusions:
Be deeply familiar with creating decryption policies (
Policies > Decryption) that exclude traffic based on URL categories (e.g., financial-services, health-and-medicine), users/groups, source/destination IPs, and applications. Understand that "No Decrypt" rules must be ordered correctly (typically at the top) to be effective. - Technical Limitations: Recognize traffic types that cannot be decrypted due to technical constraints: certificate pinning, client certificate authentication, unsupported protocols/ciphers, and QUIC.
-
Decryption Profiles:
(
Objects > Decryption > Decryption Profile) Understand how to configure decryption profiles, especially the "SSL Forward Proxy" and "SSL Inbound Inspection" sections.- Unsupported Modes: Know how settings for "Unsupported Protocol Versions" (e.g., TLS 1.0, SSLv3) and "Unsupported Cipher Suites" (e.g., RC4) impact traffic (allow undecrypted or block).
- Certificate Validation: Understand the impact of options under "Server Certificate Verification" (e.g., "Untrusted Issuer", "Expired Certificate", "Unknown Status (OCSP/CRL)") and how they can lead to blocking or temporary exclusion.
- Failure Checks: Be aware of "Hardware Security Module (HSM)" options if applicable.
- Logging and Monitoring: Be adept at interpreting Traffic logs (Decrypted column) and especially Decryption logs (Error/Status column) to identify issues related to decryption failures, policy matches, and exclusions. Know what common error messages signify.
- Forward Trust vs. Forward Untrust: Understand the role of these two key certificates in SSL Forward Proxy decryption. Forward Trust is used to re-sign certificates for sites being decrypted. Forward Untrust is used for sites that fail validation (e.g., untrusted issuer) to present a clear blocking page to the user if configured to block.
- Decryption Broker: Know the concept of Decryption Broker, where the firewall decrypts traffic and can forward it (decrypted) to third-party security tools for inspection.
- Decryption Mirroring: Understand that decrypted traffic can be mirrored to an interface for passive analysis. This is different from Decryption Broker as it's a copy, not inline.
- Impact of "Block sessions with unsupported versions/cipher suites": This is a critical setting in Decryption Profiles. If checked, non-compliant sessions are blocked. If unchecked, they may be allowed undecrypted (if no other policy blocks them).
- Certificate Revocation Checking (CRL/OCSP): Understand how failures in CRL/OCSP checks can impact decryption decisions based on profile settings (e.g., allow, block, or allow undecrypted).
PCNSE Exam Gotchas for Decryption Exemption:
- 🚨 Rule Order is Paramount: Decryption policies are processed top-down, first match. A "No Decrypt" rule placed below a broader "Decrypt" rule that matches the same traffic will NOT take effect for that traffic.
-
🚨
"No Decrypt" Action vs. Global Exclusions:
Policy-based "No Decrypt" is for policy reasons (e.g., URL category). Global exclusions (
Device > Certificate Management > SSL Decryption Exclusions) are primarily for *technical* reasons (e.g., pinned certs, client auth). Don't confuse their primary use cases. - 🚨 Action for "No Decrypt" rules: The action is simply "No Decrypt". You can attach a Decryption Profile to a "No Decrypt" rule, but its primary purpose in this context is to control SSL protocol settings (like blocking sessions with expired certs) for traffic that is *not* being decrypted.
- 🚨 Implicit vs. Explicit: If no decryption rule explicitly matches, traffic is NOT decrypted by default. Decryption is an *active* process requiring a "Decrypt" rule.
- 🚨 QUIC Handling: Remember that simply creating a "No Decrypt" rule for QUIC might not be enough if the goal is to inspect the underlying application (e.g., Google services). You might need to *block* QUIC (in Security Policy) to force a fallback to TLS/TCP, which can then be decrypted.
- 🚨 Source User/Group in Decryption Policy: This requires User-ID to be correctly configured and operational. If User-ID is not mapping the user, the rule won't match based on user criteria.
- 🚨 Local Exclusion Cache Behavior: Understand this is automatic for certain *server certificate validation failures* if not blocked, and it's temporary (default 12 hours). It's not for general application incompatibility.