🔐 Advanced Palo Alto SSL Forward Proxy Troubleshooting & PCNSE Guide
1. Overview of SSL Forward Proxy
SSL Forward Proxy on Palo Alto Networks firewalls decrypts outbound SSL/TLS traffic from clients to external servers. This allows inspection for threats, data loss prevention, and policy enforcement. It acts as a "man-in-the-middle," re-signing server certificates with a Forward Trust CA certificate trusted by clients.
Key Goal: Gain visibility into encrypted outbound traffic for security inspection.
2. Configuration Steps (Brief Recap)
A successful SSL Forward Proxy deployment involves these core steps:
- Certificate Management: Generate/Import Forward Trust and Forward Untrust CA certificates.
- Forward Trust CA Distribution: Deploy the Forward Trust CA to client devices' trusted root stores.
-
Decryption Profile:
Configure profiles under
Objects > Decryption Profileto define SSL/TLS parameters, certificate checks, and actions for unsupported modes or failures. -
Decryption Policy:
Create rules under
Policies > Decryptionto specify what traffic to decrypt (Action: Decrypt, Type: SSL Forward Proxy), and attach the Decryption Profile. - Commit Changes.
A phased rollout is highly recommended, starting with a small group of clients and non-critical URL categories to identify and resolve potential issues before broader deployment.
3. In-Depth Troubleshooting SSL Forward Proxy
Troubleshooting SSL Forward Proxy requires a systematic approach, leveraging firewall logs, CLI commands, and an understanding of the SSL/TLS handshake. The primary log source is
Monitor > Logs > Decryption
.
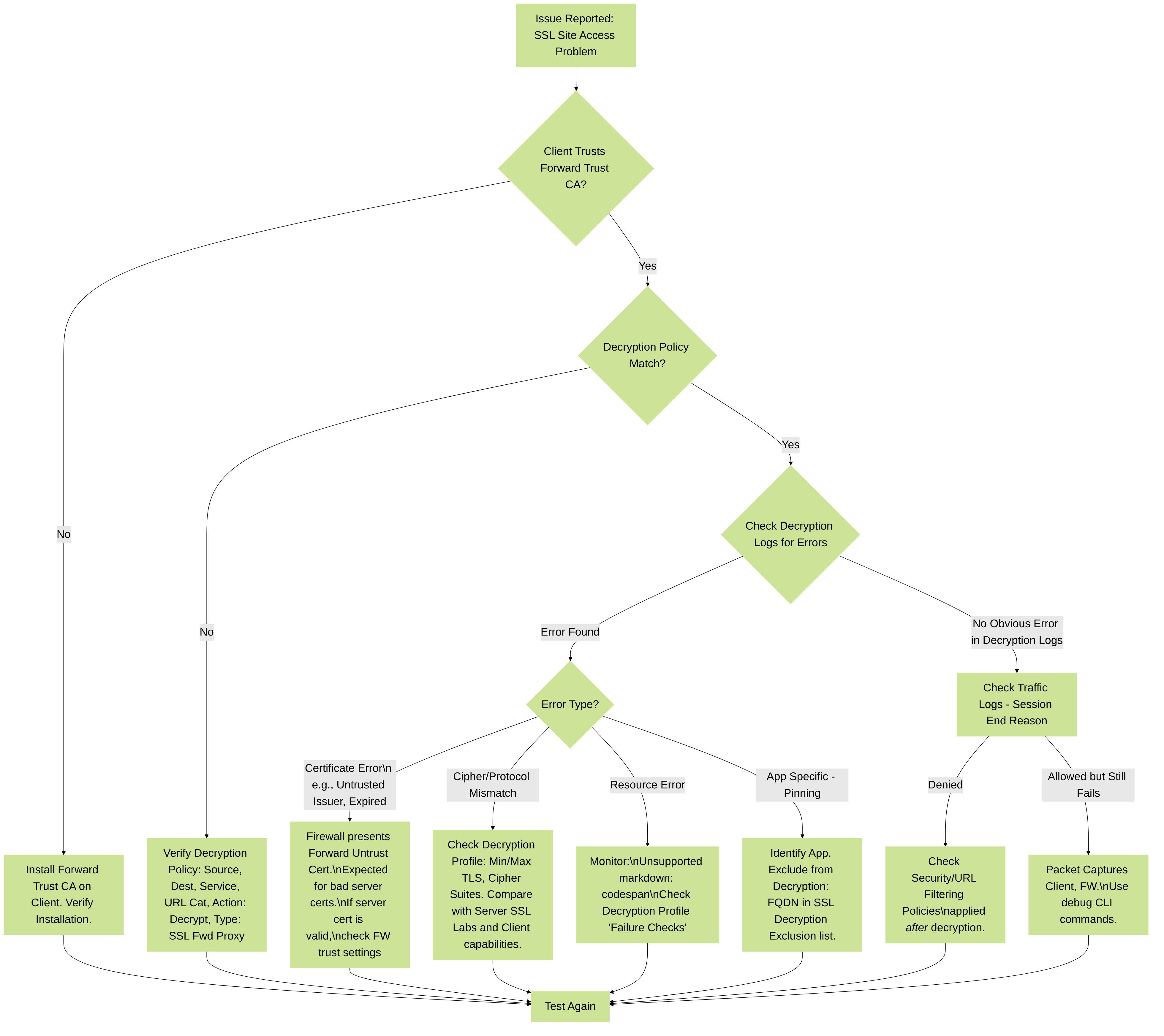
Figure 1: SSL Forward Proxy Troubleshooting Flowchart
3.1. Initial Checks & Log Analysis
-
Verify Policy Hit:
Ensure the traffic is matching the intended Decryption policy rule.
-
CLI:
show session all filter sourceand inspect flags and decryption status.destination destination-port 443
-
CLI:
-
Decryption Logs (
Monitor > Logs > Decryption): This is your primary source.-
Look for
Session Derypted: Indicates successful decryption. If issues persist, it's likely post-decryption (Security policy, Threat, URL filtering). -
Look for
Session Blockedor errors like:-
ssl-cert-server-issuer-untrusted: Server's CA is not trusted by the firewall. FW presents Forward Untrust cert. This is expected if the server cert is genuinely bad. If server cert is good, check if the issuing CA is in the firewall's trust store (Device > Certificate Management > Certificates). -
ssl-cert-status-expired: Server's certificate is expired. FW presents Forward Untrust. -
ssl-decrypt-unsupport-cipher/ssl-decrypt-unsupport-protocol: Client/Server and Firewall could not negotiate common parameters. Check Decryption Profile settings. -
ssl-server-hello-failed-handshake: Generic handshake failure. Needs deeper investigation. -
ssl-out-of-resources: Firewall resource exhaustion. -
ssl-decrypt-certvalidate-failed: Certificate validation failed for other reasons.
-
-
Look for
-
Traffic Logs (
Monitor > Logs > Traffic): CheckSession End Reason. If traffic is decrypted and then blocked by a Security policy, it will show here. -
System Logs (
Monitor > Logs > System): May show critical errors related to decryption processes (e.g.,sslmgr,devsrvr).
3.2. Certificate Issues
-
Client-Side Errors ("Your connection is not private"):
- Forward Trust CA Not Installed/Trusted: The most common issue. Ensure the Forward Trust CA certificate (the one used by the firewall to sign re-generated certs) is correctly installed in the client's OS and/or browser "Trusted Root Certification Authorities" store.
- Forward Untrust Certificate Presented: If the firewall encounters a server certificate it deems invalid (expired, untrusted issuer, self-signed), it will present the "Forward Untrust" certificate to the client. This is expected behavior to warn the client. The client should NOT trust the Forward Untrust CA. The issue is with the original server certificate.
- Certificate Chain Issues: The server might not be sending the complete certificate chain. The firewall needs to be able to build a path to a trusted root CA. Check the server's configuration (e.g., using SSL Labs' SSL Test).
-
Firewall Certificate Validation:
-
Verify the Forward Trust and Untrust certificates are correctly configured on the firewall (
Device > Certificate Management > Certificates) and that the Forward Trust is marked as a "CA". - Check the Decryption Profile for settings like "Block sessions with expired certificates" or "Block sessions with untrusted issuers."
-
CLI:
show certificateto inspect certificate properties on the firewall.detail
-
Verify the Forward Trust and Untrust certificates are correctly configured on the firewall (
3.3. Cipher Suite & Protocol Mismatches
-
Symptom:
Decryption logs show
ssl-decrypt-unsupport-cipherorssl-decrypt-unsupport-protocol. Connection fails. -
Diagnosis:
-
Check the Decryption Profile (
Objects > Decryption Profile > SSL Protocol Settings) for minimum/maximum TLS versions and allowed cipher suites. - Use an external tool like SSL Labs SSL Server Test to check the cipher suites and protocols supported by the external server.
- Client capabilities can also be a factor, though modern browsers are usually quite flexible.
-
Check the Decryption Profile (
- Solution: Adjust the Decryption Profile to allow compatible secure protocols/ciphers. Avoid enabling old/weak ciphers (e.g., SSLv3, TLS 1.0/1.1, RC4) unless absolutely necessary and with full understanding of the risks.
3.4. Application-Specific Issues (Certificate Pinning, etc.)
- Symptom: Specific applications (e.g., Dropbox, some banking apps, custom software) fail to connect or function correctly when SSL Forward Proxy is enabled for their traffic, even if browser access to other sites works.
- Cause: Certificate Pinning (HPKP or proprietary methods): The application expects the server to present a specific public key or a certificate signed by a hardcoded CA. SSL Forward Proxy breaks this trust model by re-signing the certificate.
-
Solution:
- Identify the FQDNs/IPs used by the application.
-
Exclude these FQDNs/IPs from decryption:
-
Recommended:
Add to SSL Decryption Exclusion list:
Device > Certificate Management > SSL Decryption Exclusion. This bypasses decryption based on the SNI in the Client Hello. - Alternatively, create a separate Decryption policy rule placed *before* the main decryption rule, matching this traffic and setting the action to "No Decrypt".
-
Recommended:
Add to SSL Decryption Exclusion list:
- Non-Standard TLS Usage: Some applications might use TLS in non-standard ways that the proxy doesn't handle well. Exclusion is often the only remedy.
3.5. Performance & Resource Issues
-
Symptom:
Slow browsing, intermittent connection drops for SSL sites, decryption logs show
ssl-out-of-resources, high CPU on firewall. -
Diagnosis:
-
CLI:
show system resources follow(monitor CPU/memory). -
CLI:
show counter global filter aspect ssl(look for error counters, resource drops). -
CLI:
show counter global filter delta yes aspect ssl(to see changes in counters). -
CLI:
show dataplane pool statistics | match ssl(check SSL-specific resource pools). - Check Decryption Profile "Failure Checks" (e.g., "Block sessions if resources not available").
-
CLI:
-
Solution:
- Reduce the scope of decryption: Only decrypt necessary URL categories or traffic.
- Upgrade firewall hardware if consistently overloaded.
- Optimize Decryption Profile settings (e.g., use less CPU-intensive ciphers if security policy allows, but prioritize security).
- Consider using hardware security modules (HSMs) for offloading cryptographic operations on supported platforms.
3.6. CLI Commands for Troubleshooting
Beyond those mentioned above, here are more useful CLI commands:
| Command | Description |
|---|---|
show session info
|
General session information, can be filtered. |
show session all filter ssl-decrypt yes count yes
|
Count of currently decrypted sessions. |
show running decryption-policy
|
Displays configured decryption policies. |
show running decryption-profile
|
Displays configuration of a specific decryption profile. |
show system setting ssl-decrypt
|
Displays global SSL decryption settings and status. |
show system setting decryption status
|
Overall decryption status. |
show certificate all
|
Lists all certificates on the firewall. |
debug sslmgr view stats
|
View SSL manager statistics (use with caution). |
debug sslmgr view certcache [fqdn
|
View SSL certificate cache entries (use with caution). |
debug sslmgr view sesscache
|
View SSL session cache (use with caution). |
request system ssl-decrypt-certchain-check host
|
Checks the certificate chain for a given host from the firewall's perspective. |
less mp-log sslmgr.log
|
Management plane SSL manager logs. |
less dp-log pan_sslmgr_diag.log
|
Dataplane SSL manager diagnostic logs (may vary by PAN-OS). |
less mp-log devsrv.log
|
Device server logs, can contain cert/key related messages. |
3.7. Debug Commands (Use with Extreme Caution)
Warning: Debug commands are resource-intensive and can severely impact firewall performance. Use them only during a maintenance window or under the guidance of Palo Alto Networks support. Always turn off debugs after use.
3.8. Packet Captures
- Client-Side (Wireshark): Capture on the client machine to see the TLS handshake from its perspective, including the certificate presented by the firewall.
-
Firewall (GUI or CLI):
-
GUI:
Monitor > Packet Capture. Filter for relevant traffic. -
CLI: Use
debug dataplane packet-diag ...commands as shown above. Capture at `receive` (ingress), `firewall` (post-policy), and `transmit` (egress) stages to see how the packet is transformed.
-
GUI:
- Analyze captures for TLS handshake messages, alert protocols (errors), and certificate details.
4. PCNSE Exam Insights & Troubleshooting Focus
- Log Interpretation: Be prepared to interpret Decryption log entries and determine likely causes (e.g., "untrusted issuer" vs. "unsupported cipher").
- Certificate Roles: Understand the precise function of Forward Trust and Forward Untrust certificates and when clients see each. Know that the Forward Trust CA must be trusted by clients.
- Exclusion Scenarios: Recognize situations requiring decryption exclusion (certificate pinning, sensitive data categories like financial/health, problematic apps). Know *how* to configure exclusions (SSL Decryption Exclusion list vs. "No Decrypt" policy).
- HA Failover Impact: Decrypted SSL Forward Proxy sessions are NOT synced and will be dropped on failover. New sessions will be decrypted.
- Resource Management: Understand that decryption is resource-intensive and how Decryption Profiles can manage behavior under load.
- Troubleshooting Steps: Be familiar with a logical troubleshooting flow, from checking client trust to analyzing firewall logs and policy.
- Common CLI for Verification: Know basic `show` commands to verify certificate status, policy hits, and session status.
Exam Gotcha: Distinguish between issues caused by the firewall's decryption process (e.g., client doesn't trust Forward Trust CA) versus issues with the original server's certificate (e.g., server cert expired, triggering Forward Untrust).
5. Packet Flow Diagram (Recap)
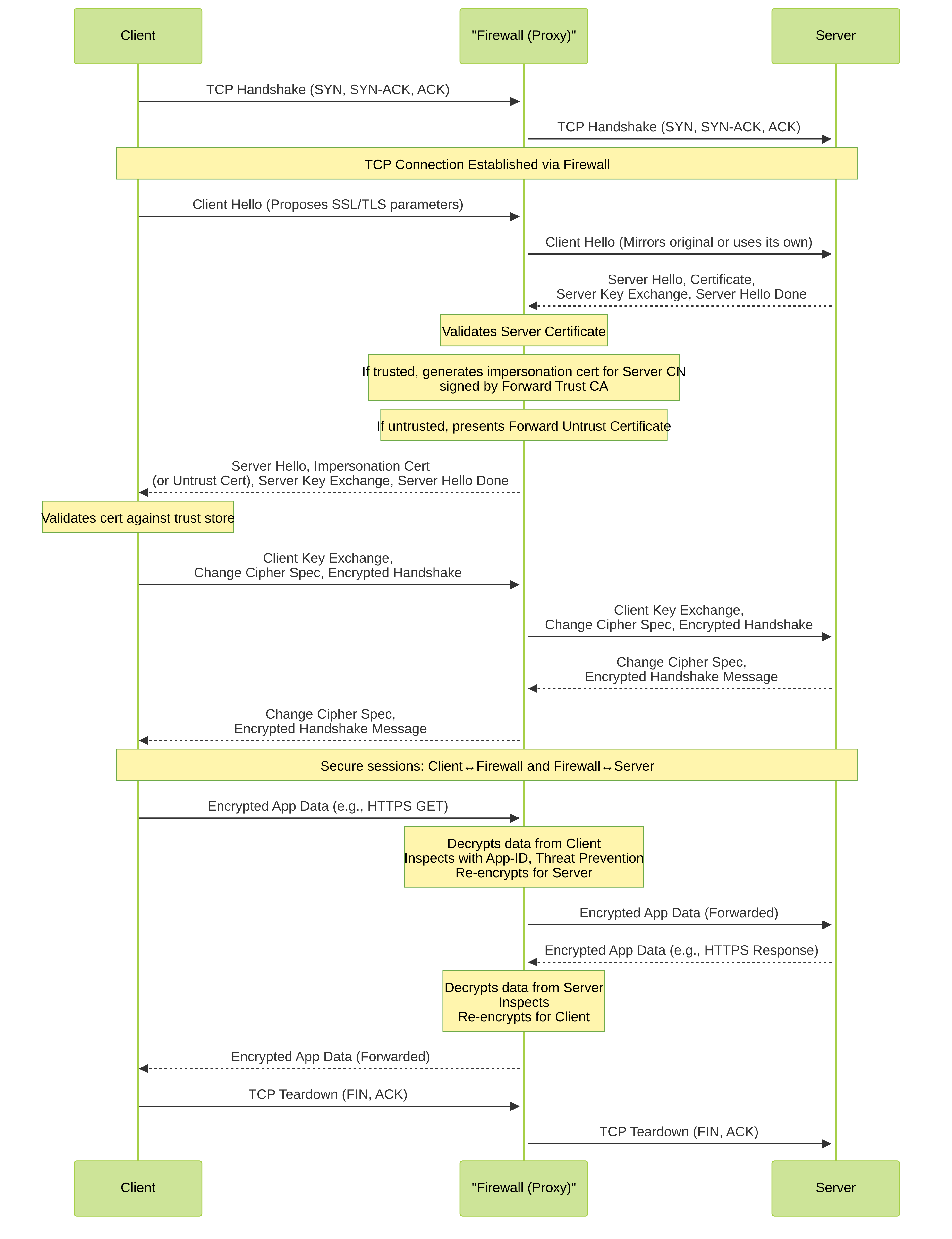
Simplified SSL Forward Proxy Packet Flow. Client connects to Firewall, Firewall connects to Server. Firewall re-signs server certificate with Forward Trust CA.