🛡️ Advanced Palo Alto SSL Inbound Inspection Troubleshooting & PCNSE Guide
1. Overview of SSL Inbound Inspection
SSL Inbound Inspection on Palo Alto Networks firewalls enables the decryption and inspection of SSL/TLS traffic destined for an organization's internal servers (e.g., web servers, application servers). This allows the firewall to identify and block threats, such as malware or intrusion attempts, embedded within encrypted traffic before it reaches the protected server.
Key Goal: Protect internal servers by decrypting and inspecting incoming SSL/TLS traffic for threats.
Unlike SSL Forward Proxy (which inspects outbound traffic), SSL Inbound Inspection requires the server's actual certificate and its corresponding private key to be loaded onto the firewall. The firewall then acts as the SSL endpoint for the client, decrypts the traffic, inspects it, and if clean, re-encrypts it (or sends it in clear text if configured) to the internal server.
2. Configuration Steps (Brief Recap)
A successful SSL Inbound Inspection deployment involves these core steps:
-
Import Server Certificate and Private Key:
-
Navigate to
Device > Certificate Management > Certificates. -
Import the end-entity server certificate (e.g., for `www.yourcompany.com`) and, critically, its
private key. The private key must be exportable from your CA or server. - Ensure the full certificate chain (intermediate CAs, root CA) for your server certificate is also present on the firewall or that the firewall can otherwise validate it.
-
Navigate to
-
Create Decryption Profile:
Configure profiles under
Objects > Decryption Profile. For Inbound Inspection, you might configure options like server certificate verification checks (though less common as you provide the cert), SSL protocol versions, and cipher strengths to offer to clients. -
Create Decryption Policy Rule:
-
Navigate to
Policies > Decryption. - Create a new rule.
- Source Zone/Address: Typically your external/untrust zone.
- Destination Zone/Address: The zone where your server resides and the Public IP address (VIP) that clients use to access the server.
-
Service/Application:
Typically
service-httpsor specific application. -
Under the
Optionstab:-
Action:
Decrypt -
Type:
SSL Inbound Inspection - Certificate: Select the server certificate (imported in step 1) that matches the public FQDN clients are accessing.
-
Action:
- Attach the Decryption Profile.
-
Navigate to
- Security Policies: Ensure you have Security policies that allow the (now decrypted) application traffic from the source zone to the destination zone and internal server. These policies will apply threat prevention profiles.
- NAT Policy (if applicable): If you are NATing a public IP to your internal server's private IP, ensure the NAT policy is correctly configured. Decryption often occurs before DNAT.
- Commit Changes.
Testing with a specific client IP or a test FQDN/server first is a good practice before rolling out for production servers.
3. In-Depth Troubleshooting SSL Inbound Inspection
Troubleshooting SSL Inbound Inspection often involves verifying certificate and key integrity, policy configuration, and network path. The primary log source is
Monitor > Logs > Decryption
.
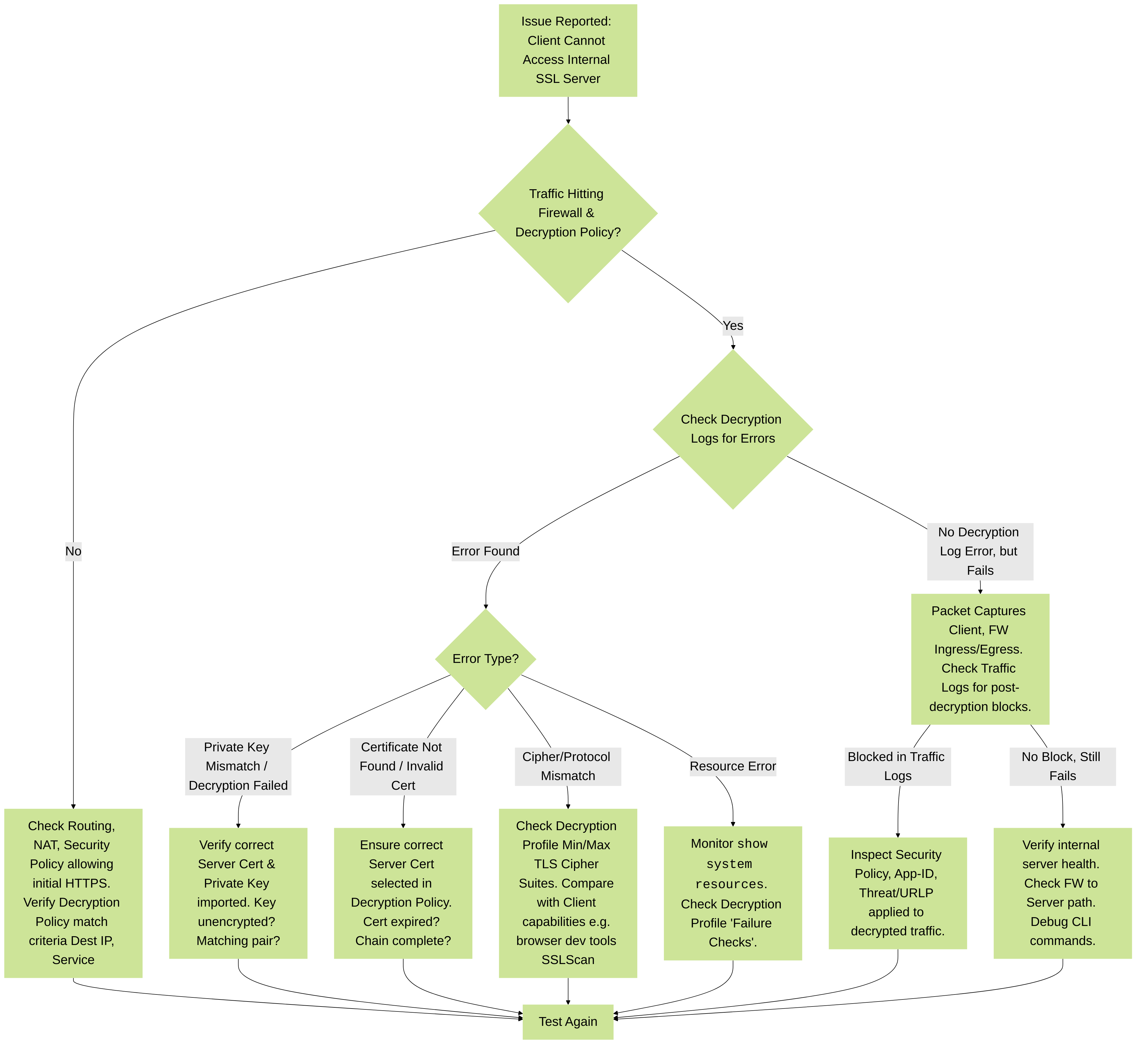
Figure 1: SSL Inbound Inspection Troubleshooting Flowchart
3.1. Initial Checks & Log Analysis
-
Verify Policy Hit:
Ensure client traffic to the server's public IP on port 443 is matching the SSL Inbound Inspection Decryption policy.
-
CLI:
show session all filter destinationand inspect flags for decryption.destination-port 443 application ssl
-
CLI:
-
Decryption Logs (
Monitor > Logs > Decryption):-
Look for
Session Derypted: Indicates successful decryption by the firewall. If issues persist, it's likely post-decryption (e.g., Security policy blocking the clear text app, server not responding). -
Look for
Session Blockedor errors like:-
ssl-inbound-decrypt-failed-private-key-mismatch: The imported private key does not match the public key in the selected server certificate. This is a very common issue. -
ssl-inbound-decrypt-failed-no-private-key: Private key for the certificate is missing or not accessible. -
ssl-inbound-decrypt-failed-cert-not-found: The certificate specified in the Decryption policy rule could not be found on the firewall. -
ssl-decrypt-unsupport-cipher/ssl-decrypt-unsupport-protocol: Client and Firewall (acting as the server) could not negotiate common SSL/TLS parameters. -
ssl-out-of-resources: Firewall resource exhaustion.
-
-
Look for
-
Traffic Logs (
Monitor > Logs > Traffic): Essential for seeing what happens *after* successful decryption. Decrypted traffic is then processed by Security policies. Check for blocks by App-ID, service, or Threat Prevention. -
System Logs (
Monitor > Logs > System): May show errors related tosslmgr,devsrvr, or certificate loading issues.
3.2. Certificate and Private Key Issues
-
Private Key Mismatch:
-
Symptom:
Decryption log shows
ssl-inbound-decrypt-failed-private-key-mismatch. Client connection fails. - Cause: The private key imported into the firewall does not correspond to the public server certificate selected in the Decryption Policy.
-
Verification:
- Re-export the certificate and private key from the original source (server/CA). Ensure they are a matched pair.
-
Use OpenSSL on a separate machine to verify:
openssl x509 -noout -modulus -in server.crt | openssl md5 openssl rsa -noout -modulus -in server.key | openssl md5 # The two MD5 hashes MUST match
- Ensure the private key is not encrypted with a passphrase when imported, or if it is, that the passphrase was correctly entered during import (though unencrypted is often simpler for firewall use).
- Solution: Import the correct, matching, unencrypted (preferably) private key for the server certificate.
-
Symptom:
Decryption log shows
-
Certificate Chain / Intermediate CA Issues:
- Symptom: Clients might report trust errors if the firewall doesn't present the full chain, or the firewall itself may fail to load/use a certificate if its intermediates aren't present.
- Solution: When importing the server certificate, ensure any necessary intermediate CA certificates are also imported onto the firewall and correctly linked if your CA provides them as separate files. Ideally, the server certificate file you import should contain the full chain (server cert followed by intermediates).
-
CLI:
show certificateto inspect certificate properties and chain information known to the firewall.detail
- Incorrect Certificate Selected in Policy: Ensure the Decryption policy rule (Type: SSL Inbound Inspection) points to the correct server certificate that clients are trying to access.
3.3. Cipher Suite & Protocol Mismatches
-
Symptom:
Decryption logs show
ssl-decrypt-unsupport-cipherorssl-decrypt-unsupport-protocol. Client connection fails. -
Diagnosis:
-
Check the Decryption Profile (
Objects > Decryption Profile > SSL Protocol Settings) for minimum/maximum TLS versions and allowed cipher suites offered by the firewall *to the client*. -
Client capabilities are key here. Use browser developer tools (Network tab, security details) or tools like
sslscanor OpenSSL's `s_client` from a test machine to see what ciphers the client is offering and what the firewall (as the server endpoint) is negotiating.# Example using openssl s_client to test connection to firewall's public IP for the server openssl s_client -connect:443 -servername
-
Check the Decryption Profile (
- Solution: Adjust the Decryption Profile on the firewall to support secure and compatible protocols/ciphers that the majority of your clients support. Prioritize strong ciphers and protocols (e.g., TLS 1.2, TLS 1.3 with AEAD ciphers).
3.4. Network Path & Post-Decryption Issues
-
Traffic Not Hitting Decryption Policy:
- Verify NAT policies (DNAT) are correctly sending external traffic destined for the public IP to the firewall (or to an internal IP that the firewall is then proxying for via Decryption policy).
- Ensure Security policies allow the initial HTTPS (port 443) traffic from the external zone to the public IP address/zone where decryption is configured.
- Symptom: Decryption logs show "Session Decrypted," but client still can't access the application.
-
Cause:
The issue lies after decryption.
- Security Policy Block: The decrypted application (e.g., `http`, `ms-rd-gateway`) is being blocked by a Security Policy. Check Traffic logs.
- Threat Prevention Block: A threat signature (IPS, Anti-Malware) is triggered on the decrypted content. Check Threat logs.
- URL Filtering Block: If URL filtering is applied after decryption. Check URL logs.
- Internal Server Issue: The internal server might be down, misconfigured, or not responding to the traffic from the firewall.
- Routing to Internal Server: Firewall may not have a route or correct path to the actual internal server after decryption.
3.5. Performance & Resource Issues
-
Symptom:
Slow application response for inbound SSL, intermittent connection drops, decryption logs show
ssl-out-of-resources, high CPU on firewall. -
Diagnosis:
-
CLI:
show system resources follow(monitor CPU/memory). -
CLI:
show counter global filter aspect ssl(look for error counters, resource drops). -
CLI:
show dataplane pool statistics | match "ssl|decrypt"(check relevant resource pools).
-
CLI:
-
Solution:
- Ensure firewall is appropriately sized for the expected inbound decryption load.
- Optimize Decryption Profile (e.g., disable unnecessary checks if security posture allows).
- Offload SSL processing to dedicated hardware (HSMs) if supported and load is very high.
3.6. CLI Commands for Troubleshooting SSL Inbound Inspection
| Command | Description |
|---|---|
show session all filter destination
|
Check if sessions to the server's public IP are being processed as SSL and potentially decrypted. |
show session id
|
Detailed information for a specific session ID found in logs. Look for decryption flags and status. |
show running decryption-policy rule
|
Verify configuration of the specific SSL Inbound Inspection rule. |
show certificate
|
Crucial for checking properties of the imported server certificate, its CA status, and if a private key is associated. |
show counter global filter aspect ssl | match inbound
|
(Aspect might vary) Look for counters related to SSL inbound processing, errors, successes. |
request certificate verify name
|
Attempts to verify the certificate chain for the imported server certificate. |
less mp-log sslmgr.log
|
Management plane SSL manager logs, may show issues with cert loading or private key handling. |
less dp-log pan_sslmgr_diag.log
|
Dataplane SSL manager diagnostic logs (content and availability may vary by PAN-OS). |
show system setting ssl-decrypt server-cert-validation gpc-url-timeout
|
(Less common for direct troubleshooting) View specific global settings. |
3.7. Debug Commands (Use with Extreme Caution)
Warning: Debug commands are resource-intensive. Use only during a maintenance window or under Palo Alto Networks support guidance. Always turn off debugs after use.
3.8. Packet Captures
- Client-Side (Wireshark): See the TLS handshake from client to firewall (public IP). Verify SNI, offered ciphers.
- Firewall Ingress (before decryption): Capture on firewall's external interface for traffic destined to the server's public IP.
- Firewall Egress (after decryption, to internal server): Capture on firewall's internal interface for traffic from firewall to the actual internal server. This will show if traffic is being sent clear-text or re-encrypted to the server.
4. PCNSE Exam Insights & Troubleshooting Focus (SSL Inbound Inspection)
-
Private Key Requirement:
This is fundamental. SSL Inbound Inspection
requires the server's private keyon the firewall. Forward Proxy does not. - Certificate Matching: The certificate selected in the Decryption policy rule must match the FQDN the client is accessing.
- Policy Type: Know to select `SSL Inbound Inspection` as the Decryption Policy type.
- Log Interpretation: Be ready to identify common errors in Decryption logs like "private key mismatch."
- Traffic Flow: Understand that after decryption, traffic is subject to Security Policies, App-ID, and Threat Prevention. An issue might be post-decryption.
- HA Failover: Similar to Forward Proxy, decrypted SSL Inbound Inspection sessions are typically NOT synchronized and will be dropped on failover. New connections will be decrypted.
- Cipher Suite Negotiation: The firewall negotiates with the client (acting as the server) and separately (if re-encrypting) with the internal server. The Decryption Profile influences the client-facing negotiation.
Exam Gotcha: Don't confuse the certificate requirements for Inbound Inspection (server cert + private key) with Forward Proxy (Forward Trust CA).
5. Packet Flow Diagram (SSL Inbound Inspection)
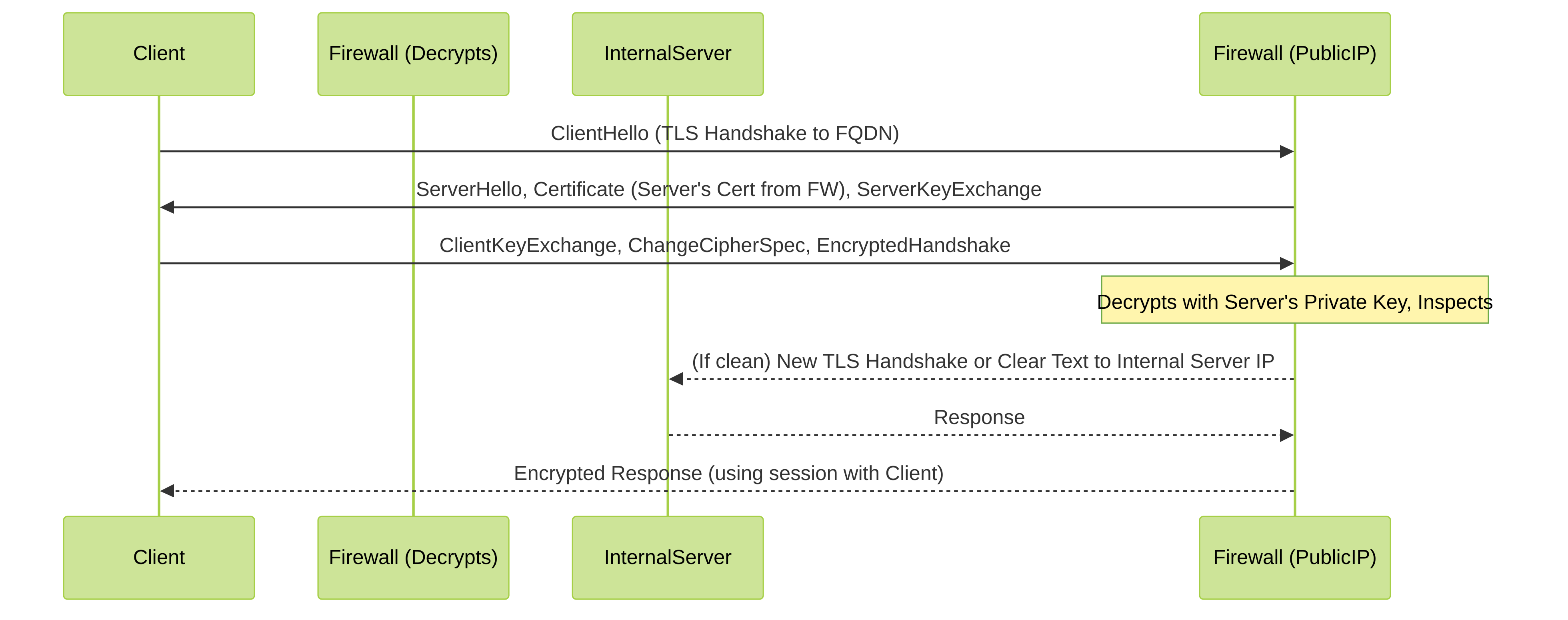
Simplified SSL Inbound Inspection Packet Flow. Firewall uses the imported server certificate and private key.