🔐 Palo Alto SSL Inbound Decryption & User-ID Guide for PCNSE
This guide provides a comprehensive overview of SSL Inbound Decryption on Palo Alto Networks firewalls, its importance for security, troubleshooting tips, and key considerations for the PCNSE exam. It also includes a section on User-ID concepts and a quiz to test your knowledge.
1. Overview of SSL Inbound Decryption
SSL Inbound Inspection (often called SSL Inbound Decryption) is a critical feature on Palo Alto Networks Next-Generation Firewalls (NGFWs) that provides visibility into encrypted SSL/TLS traffic destined for your organization's internal servers (e.g., web servers, application servers, email servers).
Unlike SSL Forward Proxy (which decrypts outbound traffic from internal clients), SSL Inbound Inspection focuses on traffic originating from external clients (the internet) and terminating on servers within your protected network. The core requirement for SSL Inbound Inspection is that the firewall must possess a copy of the server's certificate and its corresponding private key.
Key Goal: To enable deep packet inspection of encrypted inbound connections to internal servers, allowing the NGFW's security services (Threat Prevention, WildFire, URL Filtering with PAN-DB, App-ID, Data Filtering) to detect and block threats hidden within SSL/TLS.
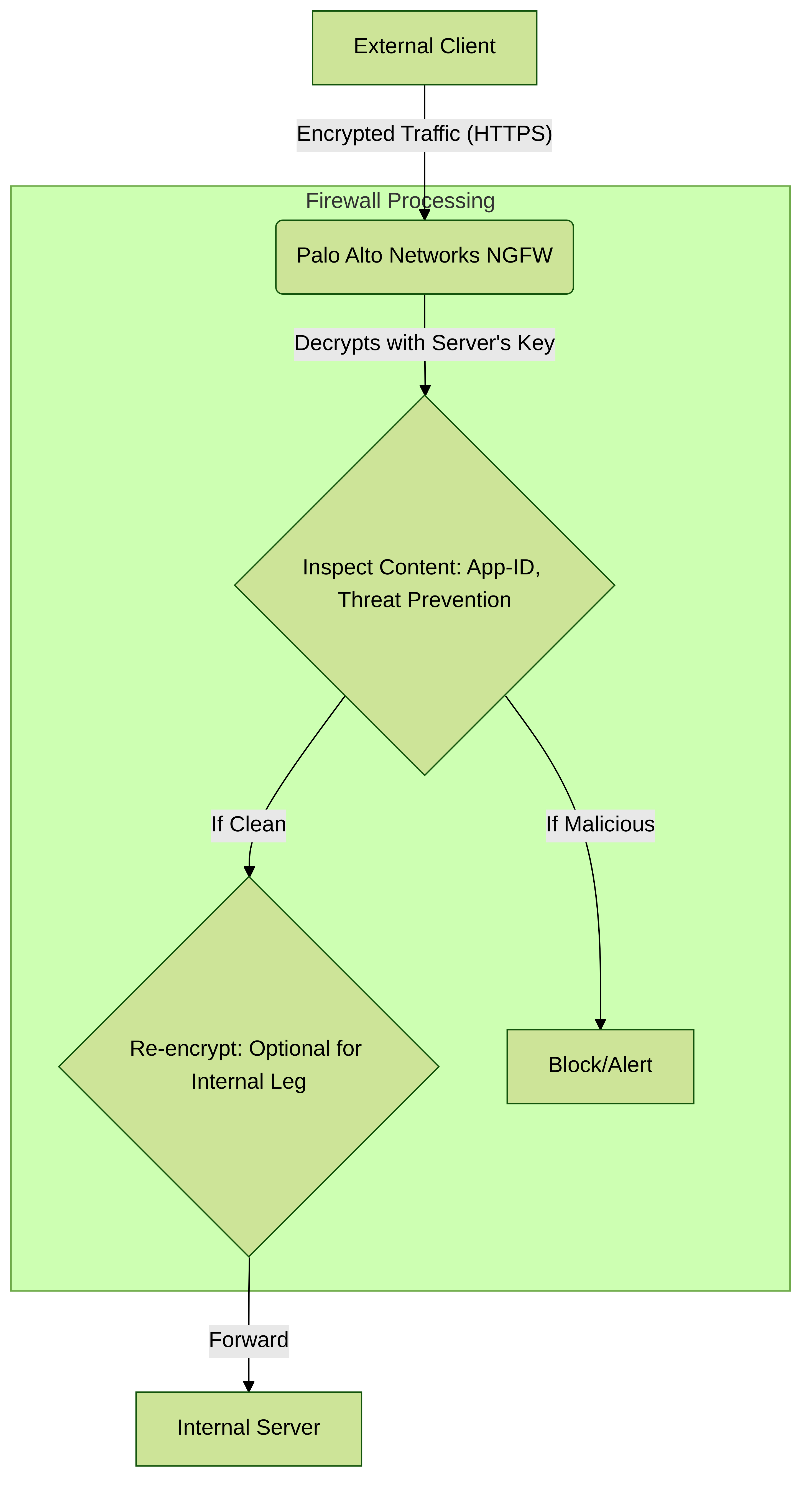
High-Level SSL Inbound Decryption Process
Crucial Role for NGFW Content Identification and Threat Prevention
Without SSL Inbound Decryption, the NGFW can only see encrypted data streams destined for your servers. While it can perform some checks based on IP addresses, port numbers, and perhaps the Server Name Indication (SNI) in the TLS handshake, it cannot inspect the actual payload. This means:
- App-ID Limitations: Application identification might be limited to generic "ssl" or "web-browsing" for encrypted traffic. Decryption allows App-ID to accurately identify the specific application within the encrypted tunnel (e.g., distinguishing between different web applications sharing the same server or identifying specific SaaS application components).
- Threat Prevention Ineffectiveness: Signatures for viruses, malware, spyware, command-and-control (C2) traffic, and vulnerability exploits are designed to match patterns in the payload. If the payload is encrypted, these threats pass through the firewall undetected. SSL Inbound Decryption exposes the payload to the Threat Prevention engine, enabling it to find and block these hidden threats.
- WildFire Analysis: For unknown files being uploaded to your servers (e.g., via a web application), WildFire needs access to the actual file to perform dynamic analysis. Decryption is necessary to extract these files from encrypted streams.
- Data Filtering: To prevent exfiltration of sensitive data (e.g., credit card numbers, social security numbers) from your servers or to prevent certain data patterns from being uploaded, Data Filtering profiles require access to the cleartext data stream.
- URL Filtering: While primarily for outbound traffic, if internal servers are compromised and attempt to communicate with malicious URLs, or if policies need to be applied to specific URI paths requested on your internal servers, decryption provides this level of granularity.
In essence, SSL Inbound Decryption unlocks the full potential of the NGFW's security services for traffic targeting your protected servers. It transforms the firewall from a device that merely allows or denies encrypted blobs into an intelligent security gateway that understands and protects your server communications.
Should URLs/URIs Be Logged When SSL Inbound Decryption Is Occurring?
Yes, it is generally highly recommended to log detailed information, including requested URIs (Uniform Resource Identifiers), when SSL Inbound Decryption is active.
- Forensics and Troubleshooting: If a security incident occurs or if there are application issues, having logs of the specific resources (URIs) requested on your servers can be invaluable for understanding the attack vector or diagnosing the problem. For example, logs might show repeated attempts to access a vulnerable script path.
- Threat Analysis: Knowing which specific URIs were targeted can provide context to threat alerts. For instance, an alert on a specific URI might indicate an attempt to exploit a known vulnerability in a particular web application component.
- Policy Refinement: Observing the URIs being accessed can help in refining security policies. For example, you might identify legitimate but rarely used application paths that could be further restricted.
- User Behavior (if applicable): For internal applications, understanding which parts of an application are being accessed (via URI logging) can sometimes be useful, though this is less common for purely external-to-internal server traffic.
When SSL Inbound Decryption is configured, the firewall has access to the cleartext HTTP requests. The URL Filtering logs (if a URL Filtering profile is applied, even in an "alert-only" mode) and Threat logs (which often include URL/URI context for web-based threats) will contain this information. Ensure your log forwarding settings are configured to send these logs to a SIEM or log management system for retention and analysis.
Logging provides the necessary audit trail and visibility. While there's a slight increase in log volume, the security benefits typically far outweigh this consideration for inbound server traffic.
2. SSL Inbound Decryption: Capabilities and Limitations
Capabilities
- Visibility into Encrypted Traffic: Decrypts SSL/TLS traffic to internal servers, allowing inspection.
- Threat Prevention: Enables detection and blocking of malware, C2, exploits, etc., hidden in SSL/TLS.
- Application Identification (App-ID): Accurate identification of applications running over SSL/TLS.
- Data Filtering: Prevents sensitive data exfiltration from servers or blocks unwanted uploads.
- WildFire Integration: Allows submission of files transferred over SSL/TLS to WildFire for analysis.
- Support for Various Protocols: Primarily HTTPS, but can also apply to other SSL/TLS-TUNNELED protocols like SMTPS, POP3S, IMAPS if correctly configured with decryption port profiles.
- Granular Policy Control: Decryption policies can be defined based on source/destination zones, addresses, services (ports), and URL categories.
- Certificate and Key Management: Supports importing server certificates and private keys.
- HSM Integration: For enhanced security, private keys can be stored on a Hardware Security Module (HSM) to prevent their direct exposure on the firewall.
Limitations
- Private Key Requirement: The firewall must have the server's private key and certificate. This can be a security concern if the firewall itself is compromised, though HSMs mitigate this.
- Performance Overhead: Decryption and re-encryption are CPU-intensive. Proper sizing of the firewall is crucial. The impact varies based on traffic volume, cipher suites, key lengths, and the number of concurrent sessions.
- Unsupported Cipher Suites/Protocols: The firewall might not support all cipher suites or newer TLS versions that clients or servers try to negotiate. This can lead to connection failures or traffic bypassing decryption if not handled correctly in the Decryption Profile.
- Certificate Management Complexity: Managing certificates and keys (renewals, distribution if keys are shared) for multiple servers can be administratively challenging.
- Client-Side Pinning: If external clients use certificate pinning or public key pinning (HPKP) specifically for your server's certificate, SSL Inbound Inspection (which involves the firewall effectively presenting its own session to the client, albeit using the server's identity) might break these connections. This is less common for public-facing websites but can occur.
- Session Resumption: As noted, full SSL/TLS session resumption (where client and server reuse previously negotiated parameters) is generally not supported with SSL Inbound Inspection. Some forms of abbreviated handshakes might work, but full resumption can cause issues. Disabling session resumption on the server might be necessary.
- HA Limitations for Decrypted Sessions: After a failover, firewalls do not support High Availability (HA) sync for decrypted SSL sessions. The firewall does not resume decrypted SSL Inbound Inspection sessions. New sessions started after failover will be decrypted based on policy.
- Traffic to Firewall Itself: SSL Inbound Inspection is for traffic *passing through* the firewall to an internal server. It's not for decrypting traffic to the firewall's own management interface or other services hosted directly on the firewall (that's handled differently).
- Perfect Forward Secrecy (PFS) Impact: While the firewall can negotiate PFS with the external client and separately with the internal server (if both support it), the end-to-end PFS property is broken because the firewall is a man-in-the-middle. However, the firewall *does* support decrypting sessions that use PFS cipher suites, provided it has the server's private key for the initial key exchange.
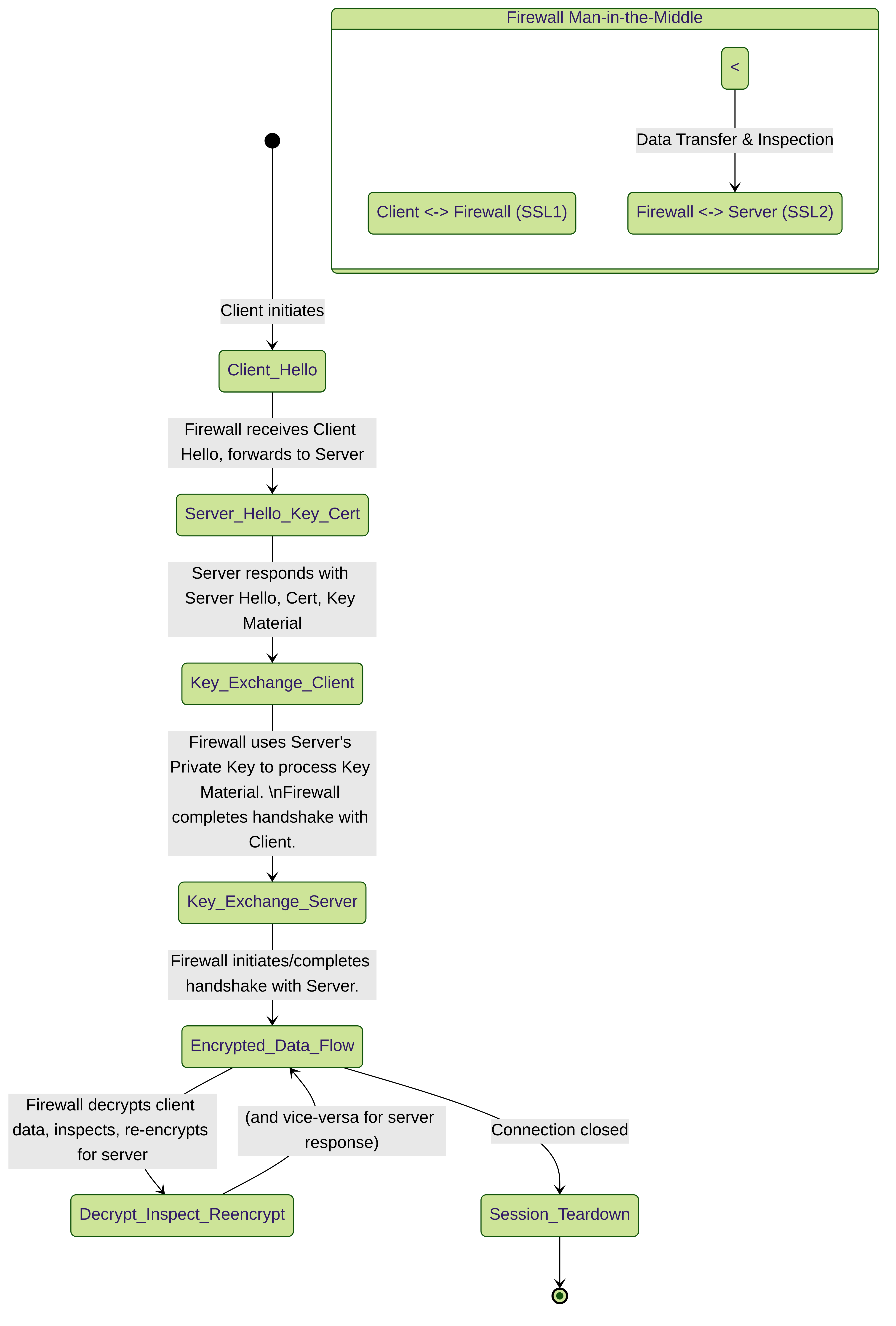
Simplified State Diagram of an SSL Inbound Decrypted Session
3. Common Issues and Troubleshooting Steps (Expanded)
-
Certificate Mismatch / Private Key Issues:
Ensure the certificate and private key installed on the firewall exactly match those on the internal server.-
Verification:
Use OpenSSL or similar tools to compare the modulus of the certificate on the firewall with the modulus of the private key and the certificate on the server. They MUST match.
openssl x509 -noout -modulus -in server.crt | openssl md5
openssl rsa -noout -modulus -in server.key | openssl md5 - Private Key Password: If the private key is encrypted with a passphrase, ensure the correct passphrase was entered when importing it onto the firewall.
- Format: Ensure certificates and keys are in a supported format (typically PEM).
- Gotcha: Using the wrong private key is a very common issue. Always verify.
-
Verification:
Use OpenSSL or similar tools to compare the modulus of the certificate on the firewall with the modulus of the private key and the certificate on the server. They MUST match.
-
Unsupported Cipher Suites:
Verify that the cipher suites proposed by the client and supported by the server have common ciphers supported by the firewall's decryption capabilities and profile.-
Check Decryption Profile:
Under
Objects > Decryption > Decryption Profile, review the SSL Protocol Settings. You can set min/max TLS versions and block sessions with unsupported ciphers/versions. - Packet Captures: Take packet captures on the client, firewall (pre and post-NAT if applicable), and server to examine the Client Hello and Server Hello messages to see which ciphers are being offered and selected.
- Gotcha: Overly restrictive Decryption Profiles can block legitimate traffic. Start with broader settings and narrow down if needed, or ensure your servers and clients use strong, modern, but supported ciphers.
-
Check Decryption Profile:
Under
-
Incomplete Certificate Chain:
Ensure that the full certificate chain (server certificate, all intermediate CA certificates) is installed on the firewall AND correctly configured on the internal server.- Firewall Import: When importing the server certificate, you typically import it along with its private key. The firewall needs to be able to present this chain to the client. The firewall itself should also trust the CA that issued your server certificate.
- Server Configuration: The internal server must be configured to send the complete chain (its cert + intermediates) to the firewall. If the server only sends its leaf cert, the firewall might not be able to properly validate it or proxy the connection correctly.
- Gotcha: Missing intermediate certificates is a frequent cause of client-side trust errors or decryption failures. Use online SSL checker tools against your public-facing server to verify its chain. The firewall needs this same chain.
-
Session Resumption Issues:
As mentioned, SSL Inbound Inspection generally does not support SSL/TLS session resumption.- Server Configuration: If issues arise, consider disabling session resumption (session IDs and session tickets) on the internal server for services being decrypted by the firewall.
- Symptoms: Intermittent connection failures or errors after an initial successful connection.
-
Decryption Profile Settings:
Check the decryption profile (Objects > Decryption > Decryption Profile) for settings that might block certain protocols, cipher suites, or certificate statuses (e.g., expired, untrusted issuer for server cert). Adjust these settings as needed.- Block settings: Be aware of options like "Block sessions with expired certificates," "Block sessions with untrusted issuers," etc. While good for security, they can cause issues if certificates are mismanaged.
-
Decryption Policy Scope:
- Ensure the Decryption Policy rule correctly matches the intended traffic (source/destination zones, IP addresses, service/port).
- Gotcha: A common mistake is to forget to apply the Decryption policy to the correct Security policy rule or to have an overly broad/narrow scope. The service object in the decryption policy should match the application's port (e.g., service-https for TCP 443).
-
NAT Interactions:
- If Destination NAT (DNAT) is used to forward traffic to the internal server, ensure the Decryption policy is applied correctly in relation to the NAT policy. Typically, decryption happens based on the post-NAT destination IP if the server is internal.
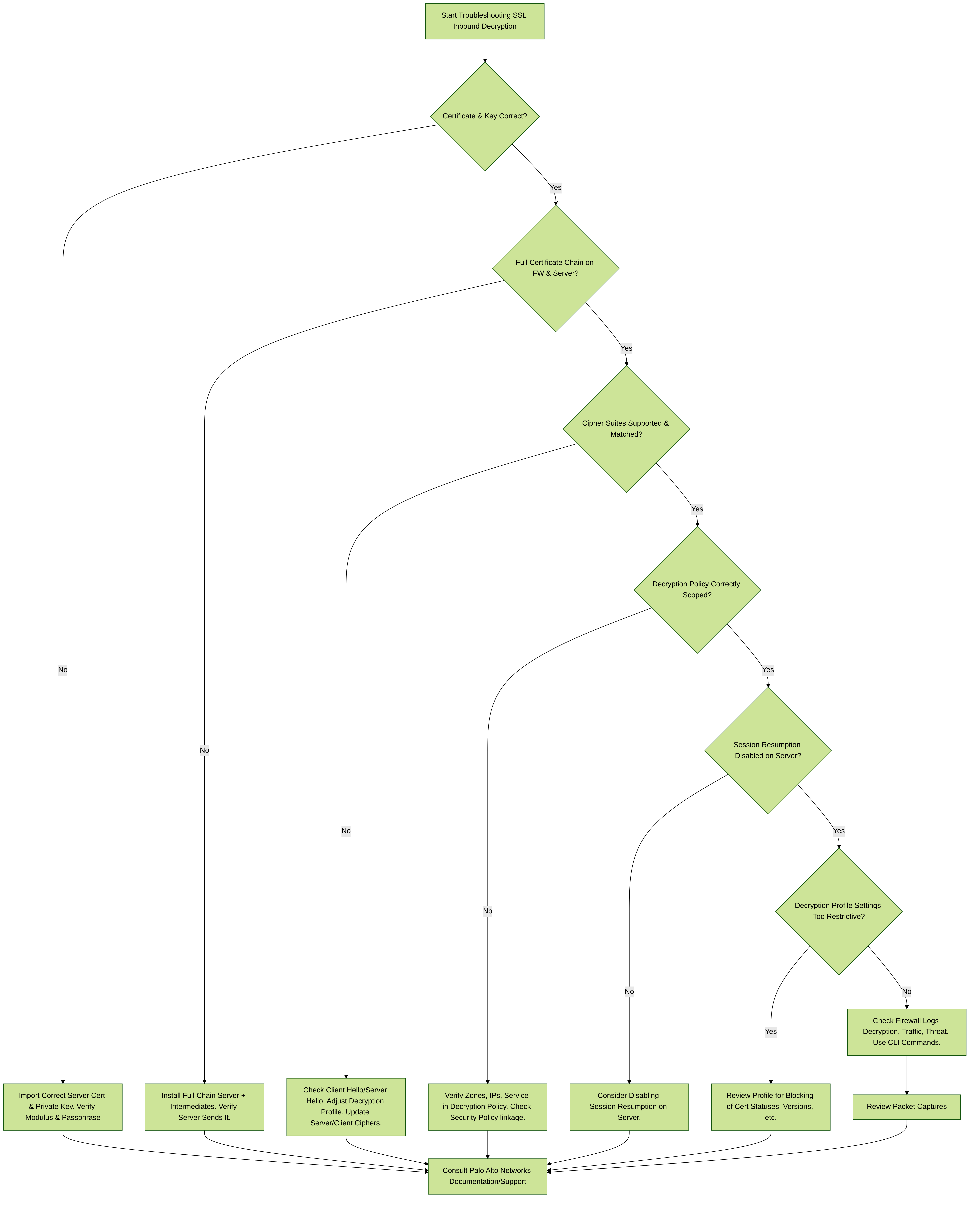
Troubleshooting Flowchart for SSL Inbound Decryption
4. Useful CLI Commands (Expanded)
These commands are essential for diagnosing SSL Inbound Decryption issues from the firewall's command line.
show system setting ssl-decrypt certificate
show system setting ssl-decrypt certificate-cache
debug dataplane show ssl-decrypt ssl-stats
show counter global filter delta yes aspect ssl_decrypt_info
show counter global filter aspect ssl_decryption_certs
show session all filter ssl-decrypt yes
show session id
debug dataplane packet-diag set filter match source destination dport
debug dataplane packet-diag set capture stage firewall file
debug dataplane packet-diag set capture on
debug dataplane show ssl-decrypt session id
tail follow yes mp-log appweb3-l4ssl.log (Example log for L4 SSL processing, specific log may vary)
tail follow yes mp-log devsrv.log (Device server logs, may show cert/key import issues)
Explanation of Key Commands:
-
show system setting ssl-decrypt certificate: Lists all certificates that have been imported and are available for SSL decryption purposes, including their names, expiration dates, and if they are marked for "SSL Inbound Inspection." Crucial to verify your server certificate is listed and correctly configured. -
show system setting ssl-decrypt certificate-cache: Displays certificates that are currently cached in memory by the SSL decryption process. Can help see if the correct certificate is being actively used. -
debug dataplane show ssl-decrypt ssl-statsorshow counter global filter delta yes aspect ssl_decrypt_info: Provides statistics related to SSL decryption, such as number of sessions decrypted, sessions bypassed, errors encountered (e.g., unsupported ciphers, handshake failures, cert errors). Excellent for seeing error counters increment. -
show counter global filter aspect ssl_decryption_certs: Shows counters related to specific certificates used in decryption, which can help pinpoint issues with a particular server's certificate. -
show session all filter ssl-decrypt yes: Shows all active sessions that are being subjected to SSL decryption processing. -
show session id: Provides detailed information about a specific session, including whether decryption was successful and which decryption profile/policy was applied. Look for the"decrypted: yes"flag. -
debug dataplane packet-diag ...: A powerful set of commands to perform packet captures on the firewall's dataplanes. Essential for deep-dive analysis of the TLS handshake. Remember to turn off capture (debug dataplane packet-diag set capture off) when done. -
debug dataplane show ssl-decrypt session id: Dumps detailed SSL decryption state information for a specific session ID. Can reveal handshake states and errors. -
Various log files (e.g.,
appweb3-l4ssl.log,devsrv.logaccessed vialess mp-log appweb3-l4ssl.logortail follow yes mp-log ...) can provide lower-level details, especially if issues occur during certificate import or initial SSL processing.
CLI Gotcha:
Always use filters (like
delta yes
for counters or specific session IDs) to narrow down CLI output. Running broad commands on a busy firewall can produce overwhelming amounts of data.
5. SSL Inbound Decryption Packet Flow Diagram (Refined)
This diagram illustrates the key exchange process when the firewall performs SSL Inbound Inspection.
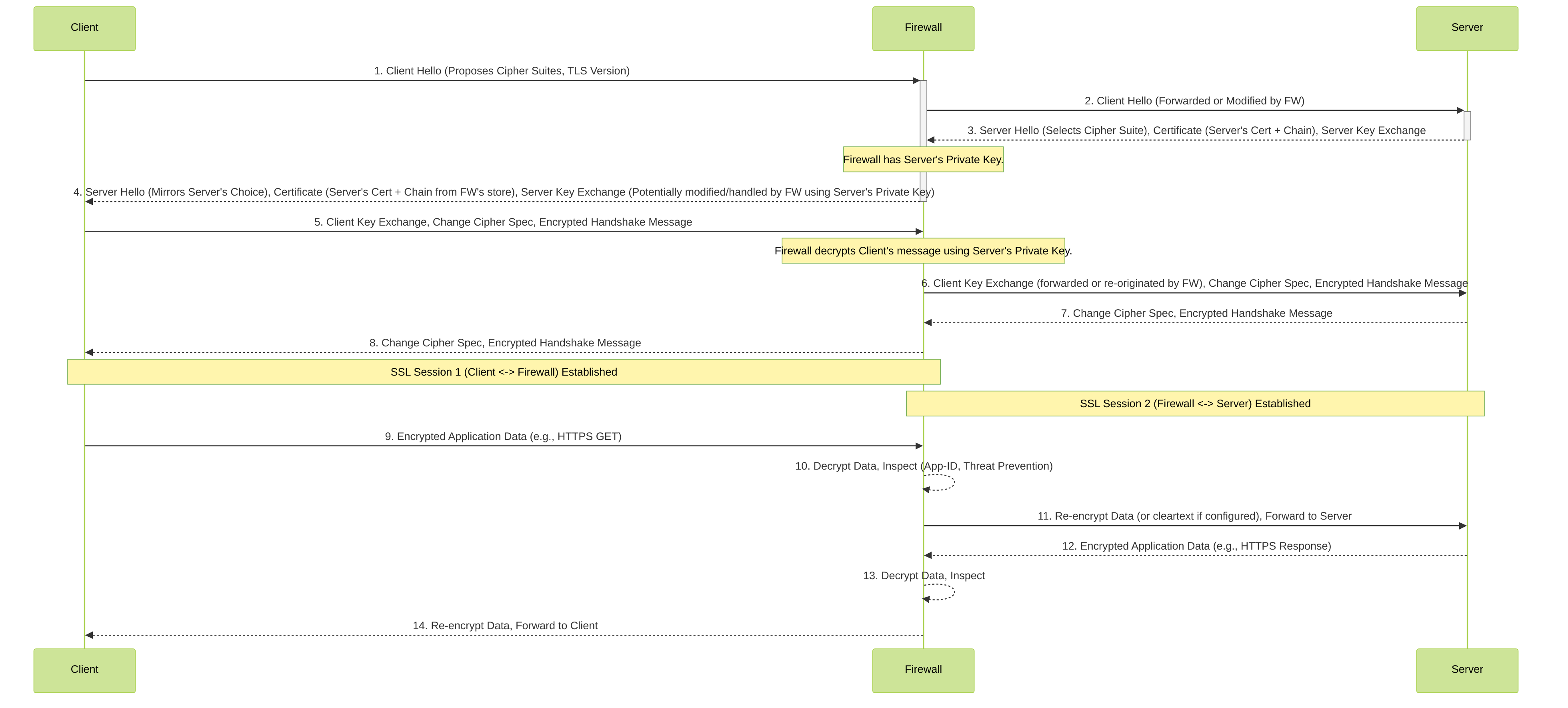
Refined SSL Inbound Decryption Packet Flow
Key difference from Forward Proxy: In SSL Inbound Inspection, the firewall uses the actual server's certificate and private key to interact with the client. It's not impersonating an unknown server with a CA certificate it generated; it's acting *as* the known server for the client-facing part of the connection.
6. Best Practices for SSL Inbound Decryption
- Use Certificates from Trusted Certificate Authorities (CAs): While self-signed certificates can be used for internal testing, for production public-facing servers, always use certificates issued by well-known, trusted CAs. This ensures clients will trust your server's certificate without manual intervention.
-
Secure Private Keys:
The private key is the most critical component.
- Limit access to the private key.
- Use strong passphrases if the key is encrypted.
- Consider using a Hardware Security Module (HSM) to store private keys. The firewall communicates with the HSM for cryptographic operations, so the private key never resides on the firewall itself. This is a significant security enhancement.
- Regularly Update Firewall and Server: Keep PAN-OS, server operating systems, and server application software updated to support the latest secure TLS/SSL protocols and cipher suites, and to patch vulnerabilities.
-
Monitor Decryption Logs Regularly:
Actively monitor decryption logs (
Monitor > Logs > Decryption), traffic logs, and threat logs to identify issues, analyze decrypted traffic patterns, and respond to threats promptly. - Test Decryption Policies Thoroughly: Before deploying new or modified decryption policies into a production environment, test them in a controlled lab or staging environment if possible, or during a maintenance window with a limited scope.
- Implement Strong Cipher Suites: Configure your internal servers to use strong, modern cipher suites and TLS versions (e.g., TLS 1.2, TLS 1.3). Configure your Decryption Profiles on the firewall to align with these, potentially blocking older/weaker protocols.
- Phased Rollout: If implementing inbound decryption for many servers, consider a phased rollout. Start with less critical servers or applications to gain experience and identify potential issues before moving to more critical ones.
- Complete Certificate Chains: Always ensure your servers are configured to send the complete certificate chain (their leaf certificate and all necessary intermediate CA certificates). The firewall also needs these intermediates if it's to build the chain presented to clients correctly.
-
Understand Performance Impact:
Be mindful of the CPU load decryption adds. Monitor firewall resource utilization (
show system resources, dashboard widgets) and plan capacity accordingly. - Selective Decryption: While the goal is broad visibility, you might have specific legitimate reasons to exclude certain trusted, high-volume, or problematic traffic from decryption using "no-decrypt" rules in your Decryption policy. However, any exclusion reduces visibility and should be carefully considered.
7. PCNSE Exam Insights for SSL Inbound Decryption
For the PCNSE exam, a solid understanding of SSL Inbound Decryption is crucial. Expect questions covering:
- Core Requirement: Knowing that the server's private key and certificate must be on the firewall is fundamental.
- Purpose: Why SSL Inbound Decryption is used (visibility into traffic to internal servers, threat prevention for servers).
-
Configuration Steps:
- Importing the server certificate and private key.
- Creating a Decryption Profile (and its key settings like cipher/version checks).
- Creating a Decryption Policy rule (matching criteria: source/dest zone, address, service) and linking it to a Security Policy rule that allows the traffic.
-
Troubleshooting Common Issues:
- Certificate/key mismatch.
- Incomplete certificate chain.
- Unsupported cipher suites.
- Session resumption problems.
- Key Differences from SSL Forward Proxy: Understand that Forward Proxy decrypts outbound traffic and uses a CA certificate on the firewall to impersonate external sites, while Inbound Inspection uses the actual server's key pair.
-
CLI Commands:
Familiarity with basic troubleshooting commands like
show session id ...,show counter global ..., and logs for decryption. - HA Behavior: Knowing that decrypted sessions are not synchronized upon HA failover.
- HSM Integration: Understanding the benefit of using an HSM for private key protection.
- Impact on Security Services: How decryption enables App-ID, Threat Prevention, WildFire, etc., for inbound traffic.
PCNSE Exam Gotchas for SSL Inbound Decryption:
- Confusing SSL Inbound Inspection with SSL Forward Proxy. They serve different purposes and are configured differently regarding certificates.
- Forgetting the necessity of the private key of the server on the firewall.
- Misunderstanding certificate chain requirements (server needing to send it, firewall potentially needing intermediates).
- Overlooking that session resumption is generally not supported and can cause issues.
- Not realizing that even with PFS ciphers, the firewall needs the server's private key for the initial handshake in an inbound decryption scenario. The firewall isn't just passively observing a PFS exchange; it's terminating the client's SSL and initiating a new one to the server.
- The order of operations: Security policy allows, then Decryption policy applies.
8. User-ID: Agent vs. Agentless (PCNSE Focus)
While slightly off-topic from SSL Inbound Decryption directly, User-ID is a critical component of Palo Alto Networks security posture and frequently tested on the PCNSE. User-ID allows the firewall to enforce policies based on users and groups rather than just IP addresses.
Key Goal of User-ID: To map IP addresses to usernames, enabling user-based visibility, policy enforcement, logging, and reporting.
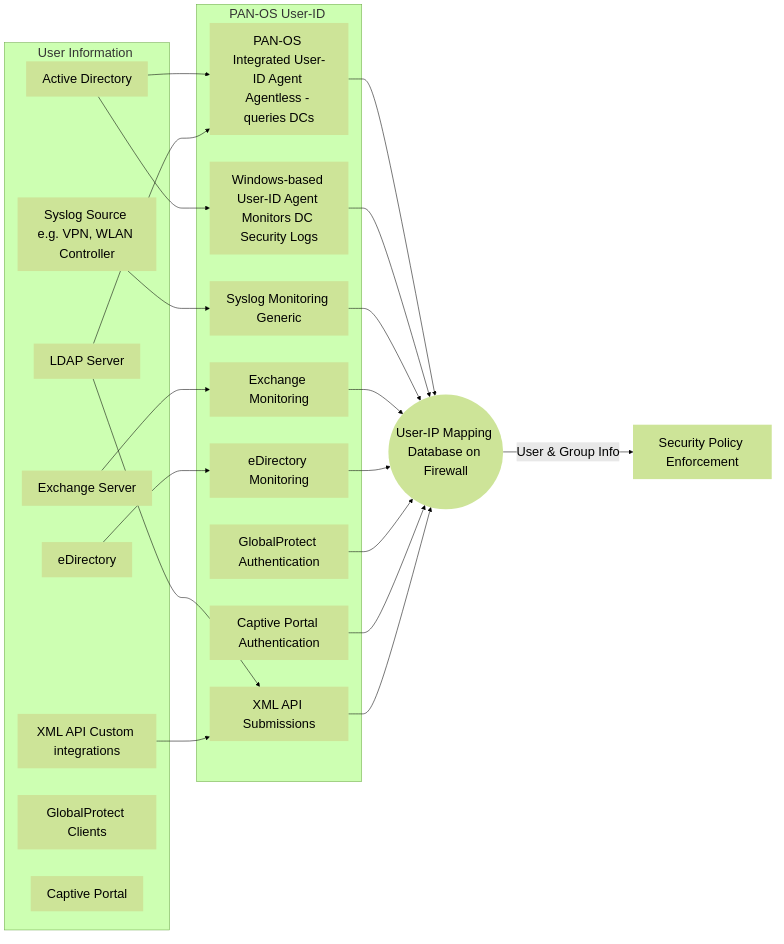
User-ID Information Sources and Mapping Methods
User-ID Agent vs. Agentless
The terms "agent" and "agentless" primarily refer to how the firewall (or a component acting on its behalf) gathers user mapping information from Microsoft Active Directory environments.
Windows-based User-ID Agent (External Agent)
- Mechanism: A separate piece of software installed on a Windows member server (not typically a Domain Controller itself, but can be).
-
Information Gathering:
- Primarily monitors Domain Controller (DC) security event logs for user login events (Event IDs vary by Windows Server version).
- Can also use WMI probing or client probing to verify mappings or discover new ones.
- Can monitor Exchange Server logs (for Outlook Web Access, ActiveSync).
- Communication: The User-ID agent forwards the collected IP-to-user mappings to the firewall(s).
-
Pros:
- Can offload some processing from the firewall.
- Can be more flexible in environments with many DCs or complex AD topologies.
- Supports features like client probing.
-
Cons:
- Requires a separate server to install and maintain the agent software.
- Permissions for the agent service account on DCs need to be correctly configured (read security logs, WMI access).
- PCNSE Gotcha: Knowing the required permissions for the User-ID agent's service account is crucial (e.g., member of "Event Log Readers" and "Distributed COM Users" for security log monitoring and WMI).
PAN-OS Integrated User-ID Agent (Agentless - on Firewall)
- Mechanism: Functionality built directly into PAN-OS on the firewall.
-
Information Gathering:
- The firewall itself queries Domain Controllers directly for security event logs using WMI or the newer Windows Management Framework (WinRM) for specific event IDs.
- Can also monitor Syslog messages from various sources (e.g., VPN concentrators, wireless controllers) if configured with parsing profiles.
- Can query LDAP servers for group memberships.
- Communication: Direct communication between the firewall and DCs/LDAP servers.
-
Pros:
- No separate agent software to install or maintain.
- Simpler setup for smaller environments.
-
Cons:
- Can increase processing load on the firewall's management plane, especially with many DCs or high login rates.
- Firewall needs direct network connectivity and appropriate credentials to query DCs.
- PCNSE Gotcha: For PAN-OS integrated agent (agentless) to query DCs, the firewall needs credentials with sufficient permissions (e.g., permissions to read security logs via WMI/WinRM).
Other User-ID Mapping Methods (Often considered "Agentless" from the DC perspective):
- Server Monitoring (Syslog): The firewall listens for syslog messages from network devices (e.g., VPNs, 802.1X authenticators, wireless controllers) that contain IP-user mapping information. Requires creating regex-based parsing profiles.
- GlobalProtect: VPN clients (GlobalProtect) authenticate with the firewall (or Prisma Access), providing direct IP-to-user mapping.
- Captive Portal: For users not identified by other means, Captive Portal can force web browser authentication, mapping the IP to a user.
- XML API: External systems can push IP-to-user mappings to the firewall via the PAN-OS XML API. Useful for custom integrations or third-party NAC solutions.
- VM Information Sources (Panorama Plugin): For virtualized environments (AWS, Azure, GCP, VMware NSX, Cisco ACI), Panorama plugins can gather IP-to-tag mappings, which can be used in Dynamic Address Groups for policy. While not direct user-to-IP, it's related to dynamic policy.
- Client Probing (via Windows Agent or PAN-OS): Actively checks if a user is still logged into a machine by querying NetBIOS, WMI, or other methods. Helps validate existing mappings.
- Session Information (from Terminal Servers/Citrix): The firewall can integrate with terminal server environments to map individual user sessions originating from a shared IP address to different user identities (requires specific configuration and often a plugin/agent on the terminal server).
Key User-ID Takeaway: The goal is to get reliable IP-to-User mappings. The "best" method depends on the environment. Often, a combination of methods is used for comprehensive coverage.
Common PCNSE Exam Questions/Topics for User-ID:
- Distinguishing between the Windows-based agent and the PAN-OS integrated agent (agentless).
- The flow of information (e.g., DC -> Agent -> Firewall vs. DC -> Firewall).
- Required permissions for service accounts used by User-ID agents or the firewall.
-
Troubleshooting steps (e.g., checking agent connectivity to firewall, firewall connectivity to DCs, User-ID logs on firewall
show user user-id-agent state all,show user ip-user-mapping all). - Configuration of different User-ID sources (AD, Syslog, Captive Portal).
- How Group Mapping is configured and used in policies (LDAP server profiles).
- The purpose of Client Probing and WMI probing.
- Syslog parsing profile configuration basics.
- Understanding which User-ID method to use in different scenarios.