Route-Based vs. Policy-Based VPNs
🔄 Route-Based VPNs on Palo Alto Networks
Palo Alto Networks firewalls exclusively support route-based VPNs and do not natively support policy-based VPNs . However, they can interoperate with policy-based VPN peers by configuring appropriate Proxy IDs .
In a route-based VPN:
- A tunnel interface is created and assigned to a security zone.
- Traffic is directed into the VPN tunnel based on routing decisions, typically using static or dynamic routes.
- The firewall makes forwarding decisions based on the destination IP address.
- Dynamic routing protocols (e.g., OSPF, BGP) can operate over the VPN tunnel.
This approach provides flexibility and scalability, especially in complex network topologies.
🔐 Interoperability with Policy-Based VPNs
While Palo Alto Networks firewalls do not support policy-based VPNs, they can establish VPN tunnels with policy-based peers by configuring Proxy IDs that match the remote peer's traffic selectors. This ensures that both ends of the VPN tunnel agree on the traffic to be encrypted and transmitted through the tunnel.
For detailed guidance on configuring Proxy IDs for interoperability with policy-based VPNs, refer to the following resource:
📊 Comparison: Route-Based vs. Policy-Based VPNs
| Feature | Route-Based VPNs | Policy-Based VPNs |
|---|---|---|
| Tunnel Interface | Required | Not used |
| Routing Decision | Based on routing table | Based on security policy/access list |
| Dynamic Routing Support | Supported | Not supported |
| NAT Support | Supported | Limited |
| Scalability | High | Limited due to multiple SAs/policies |
| Configuration Complexity | Moderate (routing + tunnel setup) | Can be higher with many specific policies |
| Vendor Support Examples | Palo Alto Networks, Juniper SRX, Cisco (VTI) | Cisco ASA (pre-9.7 without VTI), Check Point (traditional mode) |
🛠️ Troubleshooting VPNs
Troubleshooting VPNs involves checking connectivity, IKE (Internet Key Exchange) phases, IPsec SAs (Security Associations), routing, and security policies. Below are common commands for different VPN types and vendors.
Route-Based VPN Troubleshooting (Palo Alto Networks Focus)
On Palo Alto Networks firewalls, troubleshooting typically involves CLI commands and reviewing logs in the WebUI.
-
Check IKE SAs (Phase 1):
show vpn ike-sa gatewayThis command displays the status of IKE Phase 1 Security Associations. Look for a `ST_ACTIVE` state. -
Check IPsec SAs (Phase 2):
show vpn ipsec-sa tunnelThis command shows the status of IPsec Phase 2 SAs. Verify SPIs (Security Parameter Index) and encapsulation/decapsulation counters. -
Test VPN tunnel connectivity (Palo Alto Networks):
test vpn ike-gatewaytest vpn ipsec-sa tunnelThese commands can help diagnose negotiation issues. -
Check Tunnel Interface Status:
show interface tunnel.Ensure the tunnel interface is up and configured correctly. -
Verify Routing:
show routing routeConfirm that routes are directing traffic destined for the remote network through the tunnel interface. -
Packet Diagnostics:
debug ike pcap startThese commands can help capture and analyze IKE and IPsec packet flows.
debug ike pcap stop
view-pcap debug-pcap ikemgr.pcap
debug flow basic
show counter global filter packet-filter yes delta yes | match tunnel - System Logs: Review system logs in the WebUI (Monitor > Logs > System) for IKE and IPsec related messages.
- Traffic Logs: Review traffic logs in the WebUI (Monitor > Logs > Traffic) to see if traffic is matching the security policies and being sent through the tunnel.
Policy-Based VPN Troubleshooting (General Examples)
Policy-based VPNs often rely on crypto maps or specific VPN policies. Commands vary significantly by vendor.
-
Cisco ASA (Policy-Based):
-
show crypto ipsec sa: Displays IPsec SAs. Look for active SAs matching your crypto map, and check #pkts encaps/decaps. -
show crypto ikev1 saorshow crypto ikev2 sa: Displays IKE SAs. Check for QM_IDLE (Phase 1 complete, Phase 2 active) or MM_ACTIVE (Phase 1 active). -
debug crypto condition peer -
debug crypto ikev1ordebug crypto ikev2(use with caution, can be very verbose) -
packet-tracer input inside tcp: Simulates traffic flow.detailed
-
-
Check Point:
-
vpn tu: (TunnelUtil) Utility to manage and view VPN tunnels and SAs. -
fw monitor -e 'accept host(: Captures traffic to/from the VPN peer (use specific filters).);' - SmartView Tracker: Review VPN logs for negotiation details and errors.
-
-
General Checks for Policy-Based VPNs:
- Verify that the "interesting traffic" defined in the policy (e.g., access list in Cisco, VPN domain in Check Point) exactly matches on both sides (source/destination subnets, protocols, ports). Mismatched proxy IDs/traffic selectors are a common cause of Phase 2 failures.
- Ensure security policies or ACLs permit the VPN traffic (both IKE and IPsec).
Common VPN Troubleshooting Steps (Both Types)
-
Verify Phase 1 Completion:
- Are IKE SAs established?
- Check for matching IKE proposals (encryption, hashing, DH group, authentication method, lifetime).
- Ensure pre-shared keys match or certificates are valid.
- Check firewall logs for IKE negotiation messages. Common issues include "NO_PROPOSAL_CHOSEN".
-
Verify Phase 2 Completion:
- Are IPsec SAs established?
- Check for matching IPsec proposals (encryption, authentication, ESP/AH, lifetime, PFS).
- For route-based VPNs with Proxy IDs (like Palo Alto to a policy-based peer), ensure Proxy IDs match the remote peer's traffic selectors.
- For policy-based VPNs, ensure traffic selectors (ACLs, VPN domains) are exact mirrors.
- Check firewall logs for IPsec negotiation messages.
-
Check Routing (Especially for Route-Based):
- Is there a route pointing traffic destined for the remote subnet(s) to the tunnel interface?
- If using dynamic routing, are adjacencies formed over the tunnel?
-
Check Security Policies/Firewall Rules:
- Are there policies allowing traffic from your local network to the remote network (and vice-versa) through the VPN?
- Ensure policies allow IKE (UDP 500, UDP 4500 if NAT-T is used) and ESP (protocol 50) or AH (protocol 51) traffic between the VPN peers.
- NAT Traversal (NAT-T): If a NAT device is between VPN peers, ensure NAT-T is enabled and working. Traffic will be encapsulated in UDP 4500.
- Packet Captures: Use packet capture tools on the firewalls or end hosts to see if IKE and ESP packets are being sent and received.
📈 Visual Representation
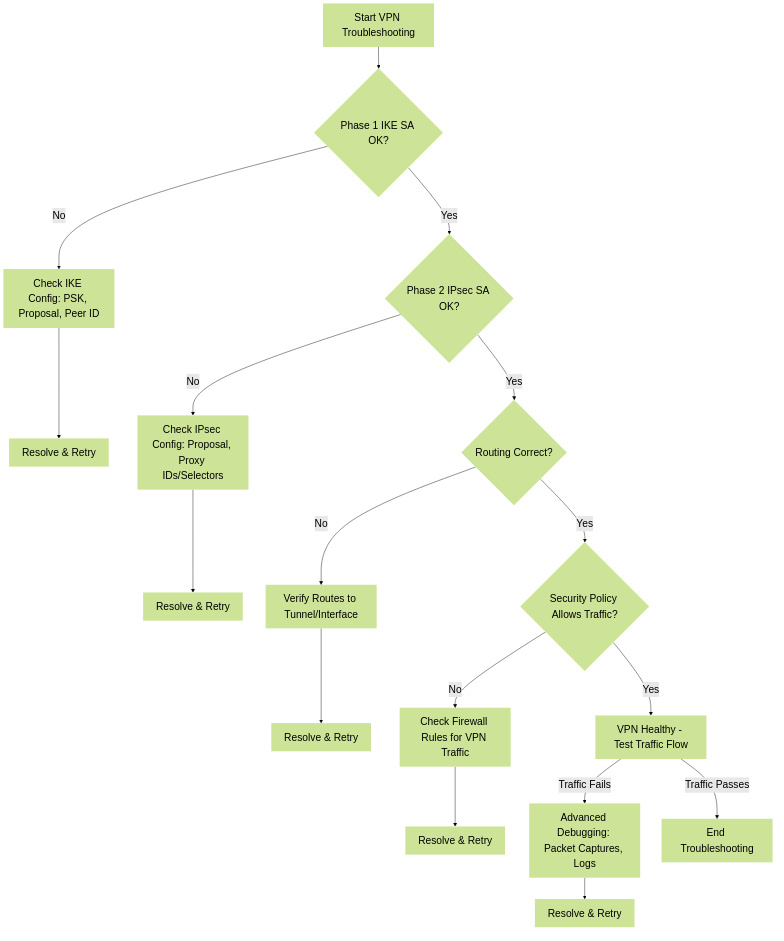
General VPN Troubleshooting Flow
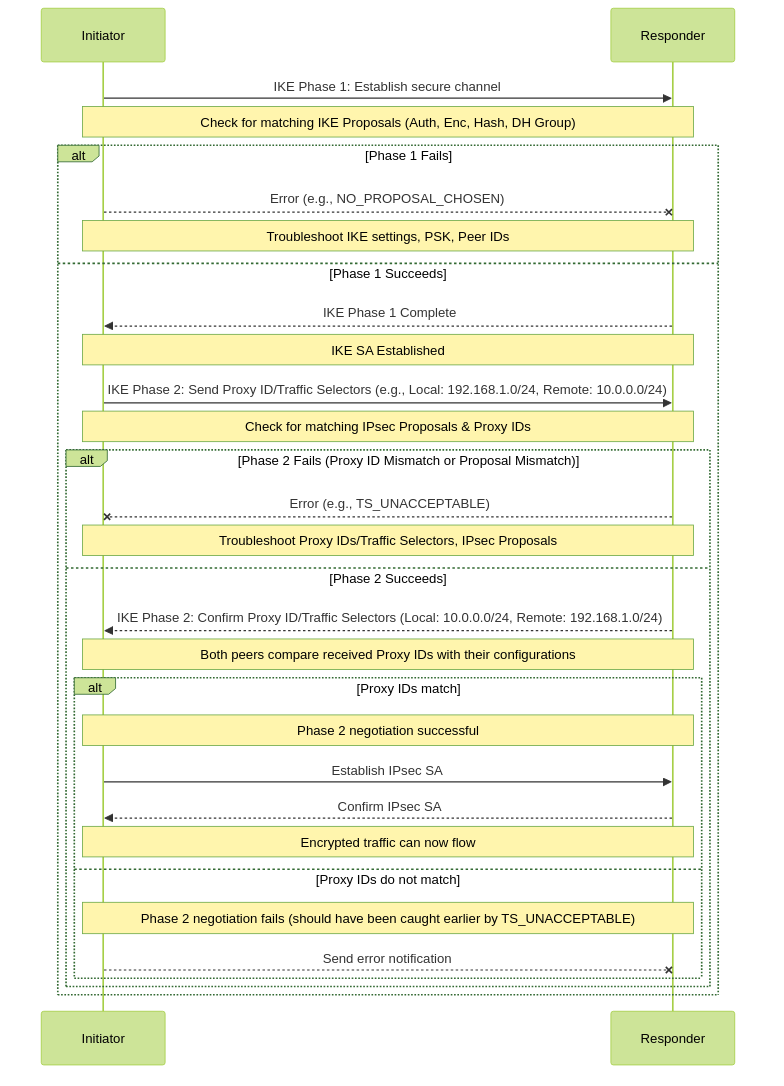
VPN IKE Phase 1 & Phase 2 Negotiation with Troubleshooting Notes