🔐 Palo Alto Networks Tunnel Monitoring
Tunnel monitoring in Palo Alto Networks firewalls ensures the reliability and availability of IPSec VPN tunnels. It works by sending ICMP probes (pings) to a specified destination IP address across the tunnel. If the destination becomes unreachable after a configured number of probes, the firewall can take predefined actions such as waiting for recovery or failing over to a backup path. This mechanism is crucial for maintaining uninterrupted VPN services and for detecting issues that traditional Dead Peer Detection (DPD) might not catch, as DPD primarily checks the peer's aliveness based on IKE messages, not end-to-end path usability.
⚙️ Configuration
Tunnel monitoring is configured in two main parts on a Palo Alto Networks firewall:
-
Create a Monitor Profile:
This profile defines the monitoring parameters.
Navigate to Network > Network Profiles > Monitor > Add .
- Name: A descriptive name for the profile.
-
Action:
What the firewall does if the destination IP becomes unreachable. Options are:
- **Fail Over:** Disables the tunnel interface, effectively removing its routes from the routing table and forcing traffic to an alternative path (if configured). [5, 8]
- **Wait Recover:** The firewall logs the failure and continues probing but keeps the tunnel interface enabled. It waits for the destination to become reachable again. [8]
- Interval (sec): How often the ICMP probe is sent (e.g., every 3 seconds). [1, 8, 15]
- Threshold: The number of consecutive failed probes before the configured action is triggered (e.g., 5 failed probes). [1, 8, 15]
-
Attach the Monitor Profile to the IPSec Tunnel:
This links the monitoring parameters to a specific VPN tunnel.
Navigate to Network > IPSec Tunnels > [Your Tunnel Name] > General tab .
- Under Advanced Options, enable Tunnel Monitor . [1, 8]
- Specify the Destination IP : This is the IP address across the tunnel that the firewall will ping. It could be the remote peer's tunnel interface IP or an IP address of a host behind the remote peer. [2, 8, 12]
- Select the Profile : Choose the Monitor Profile created in the previous step. [8]
Note: The tunnel interface associated with the VPN tunnel *must* have an IP address assigned to it for tunnel monitoring to function, as this IP is used as the source for the ICMP probes. [2, 3, 5, 11, 12, 19, 20]
🔬 Verification and Troubleshooting CLI Commands
Use the following CLI commands to check the status of tunnel monitoring:
-
Check overall VPN flow and monitor status:
show vpn flowLook at the 'monitor' column in the output. It will show 'up' if monitoring is active and the destination is reachable, or 'down' if the threshold has been met and the tunnel action triggered (or would be triggered if Fail Over is configured). 'off' means monitoring is not configured for that tunnel. [2, 9] -
Check detailed tunnel monitoring statistics:
show vpn flow tunnel-idReplace `` with the ID of the tunnel (seen in `show vpn flow`). This command provides detailed information including the monitor status (up/down), interval, threshold, and counts of packets sent and received for monitoring probes. [2] monitor: on monitor status: up monitor interval: 3 seconds monitor threshold: 5 probe losses monitor packets sent: 739180 monitor packets recv: 732283(Example output snippet adapted from search result [2]) -
Check the status of the tunnel interface itself:
show interface tunnel.If the Monitor Profile action is "Fail Over" and the tunnel monitor has failed, the tunnel interface state will show as down. [6] -
Check routing table:
show routing routeIf the Monitor Profile action is "Fail Over" and the tunnel monitor has failed, routes pointing to this tunnel interface should disappear or become inactive, allowing traffic to be routed via an alternative path if available. [5, 8]
📈 Visual Representation: Tunnel Monitoring Process
This flowchart illustrates the general process of tunnel monitoring and the actions taken upon failure.
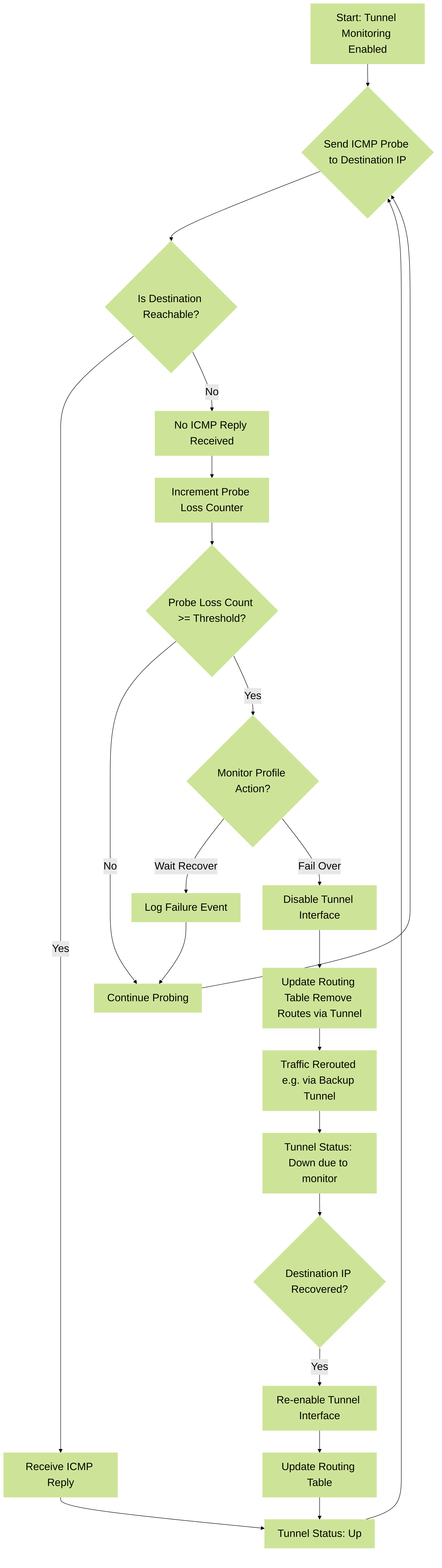
Tunnel Monitoring Process Flow
🔄 Visual Representation: Tunnel Monitoring and Failover Sequence
This sequence diagram shows the interaction between the firewall and the monitored destination, and the sequence of events during a failover.
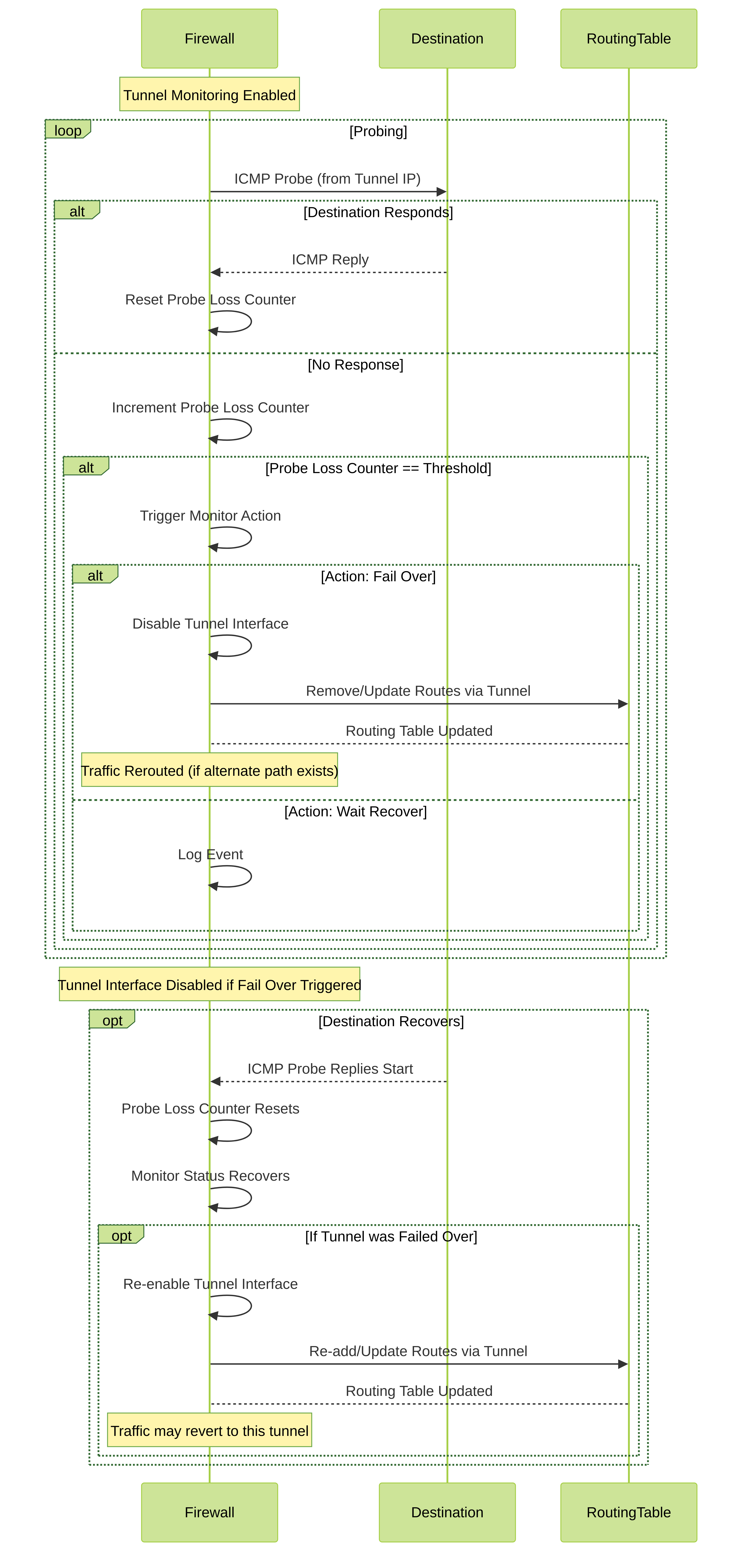
Tunnel Monitoring and Failover Sequence
📌 Key Points
- Proactive Monitoring: Tunnel monitoring proactively checks the health of the VPN tunnel by sending periodic ICMP probes to a specified destination IP address.
- Requires an IP address configured on the tunnel interface to source the ICMP probes. [2, 3, 5, 11, 12, 19, 20]
- Immediate Action: Upon detecting a failure (reaching the configured threshold of lost probes), the firewall can immediately take action based on the configured monitor profile (Fail Over or Wait Recover). [1, 5, 8]
- Enhanced Reliability: Tunnel monitoring goes beyond just checking if the peer is alive (like DPD); it verifies end-to-end reachability through the tunnel, providing a more robust VPN solution.
- Integration with Routing: The "Fail Over" action directly impacts the routing table by disabling the tunnel interface, facilitating automatic path switching. [5, 8, 9]
- Logging and Alerts: Failures detected by tunnel monitoring are logged as critical system events, which can trigger alerts for prompt administrative attention. [2]